
Source/Elliptic
Compiled by/Nick
The North Korean hacker group Lazarus seems to have increased its activity recently, with 4 confirmed attacks on the encryption industry since June 3. It is suspected that they have carried out a fifth attack, as 23pds, Chief Information Security Officer of SlowMist, tweeted that the $55 million hacker attack on the cryptocurrency exchange CoinEx was carried out by a North Korean state-sponsored hacker.
It is worth noting that according to the National Intelligence Service (NIS) of South Korea, which was cited by the Associated Press, North Korean-sponsored hackers have stolen approximately $1.2 billion in cryptocurrency from around the world since 2017. The NIS believes that North Korea is one of the most motivated countries in the world to steal cryptocurrency, as the country shifted its focus to cybercrime after the United Nations strengthened economic sanctions in 2017 in response to its nuclear and missile tests.
In addition, in the past 104 days, the North Korean hacker group Lazarus has been confirmed to have stolen nearly $240 million in cryptocurrency assets from Atomic Wallet ($100 million), CoinsPaid ($37.3 million), Alphapo ($60 million), and Stake.com ($41 million).
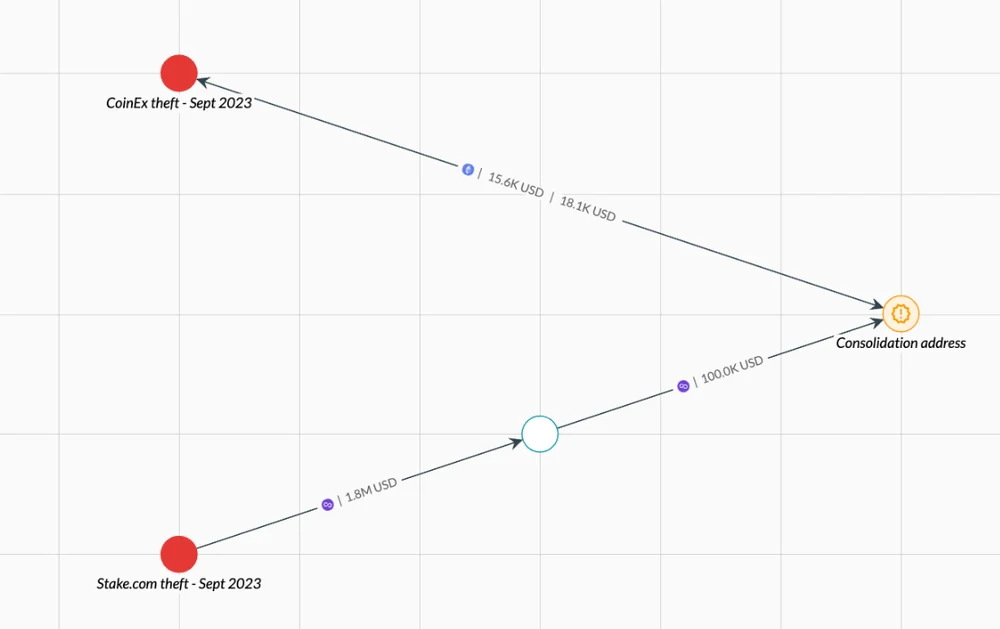
As shown in the above image, analysis by Elliptic indicates that a portion of the funds stolen from CoinEx was sent to an address used by the Lazarus group to store funds stolen from Stake.com, despite being on different blockchains. Subsequently, the funds were cross-chained to Ethereum through a cross-chain bridge previously used by Lazarus, and then sent back to an address controlled by the CoinEx hacker.
Elliptic has observed this mixing of funds from different hackers in the Lazarus incident, with the most recent instance being a mixing of cryptocurrency stolen from Stake.com and funds stolen from Atomic Wallet. These mixed funds from different hackers are represented in the image below in orange.
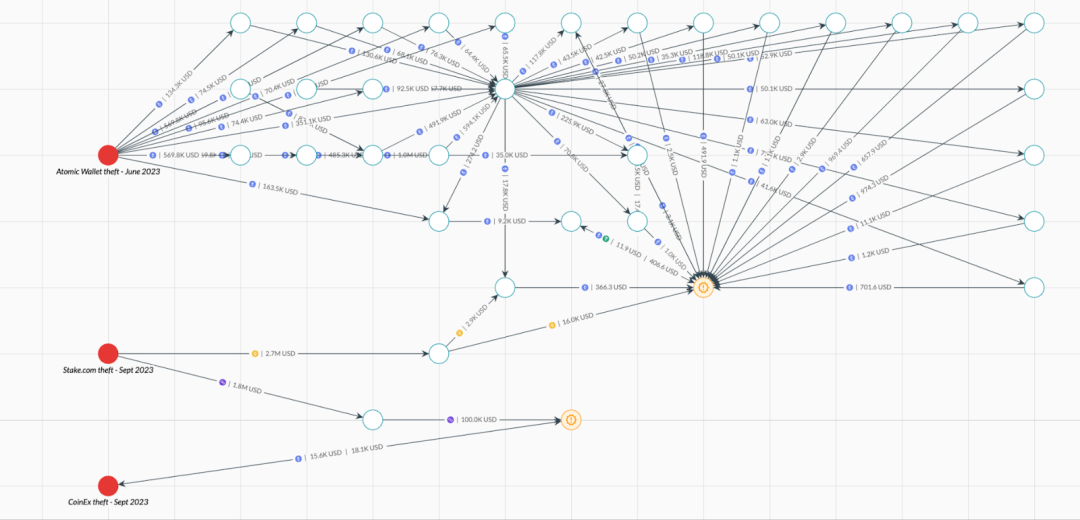
01. Lazarus conducted 5 attacks in 104 days
In 2022, several high-profile hacker attacks were attributed to Lazarus, including attacks on Harmony's Horizon Bridge and Axie Infinity's Ronin Bridge, both of which occurred in the first half of last year. From then until June of this year, no major cryptocurrency theft cases were publicly attributed to Lazarus. Therefore, the various hacker attacks in the past 104 days indicate an escalation in the activities of this North Korean hacker group.
On June 3, 2023, users of the non-custodial decentralized cryptocurrency wallet Atomic Wallet suffered losses exceeding $100 million. After determining multiple factors indicating the responsibility of the Lazarus group for this, Elliptic officially attributed this hacker attack to Lazarus on June 6, 2023, which was later confirmed by the Federal Bureau of Investigation (FBI).
On July 22, 2023, Lazarus gained access to the hot wallet of the cryptocurrency payment platform CoinsPaid through a social engineering attack. This access allowed the attacker to create authorization requests and extract approximately $37.3 million in cryptocurrency from the platform's hot wallet. On July 26, CoinsPaid released a report confirming Lazarus's responsibility for this attack, which was also confirmed by the FBI.
On the same day, July 22, Lazarus carried out another high-profile attack, this time targeting the centralized cryptocurrency payment provider Alphapo, stealing $60 million in cryptocurrency assets. The attacker may have gained access through previously leaked private keys. The FBI later confirmed that this attack was carried out by Lazarus.
On September 4, 2023, the online cryptocurrency gambling platform Stake.com was attacked, resulting in the theft of approximately $41 million worth of virtual currency, possibly due to a stolen private key. On September 6, the FBI announced that the Lazarus group was behind this attack.
Finally, on September 12, 2023, the centralized cryptocurrency exchange CoinEx was hacked, resulting in the theft of $54 million. As mentioned above, multiple pieces of evidence indicate that Lazarus was responsible for this attack.
02. Has Lazarus changed tactics?
Analysis of Lazarus's latest activities indicates that since last year, they have shifted their focus from decentralized services to centralized services. Four of the recent 5 hacker attacks discussed earlier targeted centralized cryptocurrency asset service providers. Before 2020, when the decentralized finance (DeFi) ecosystem was rapidly emerging, centralized exchanges were the main targets chosen by Lazarus.
There are several possible explanations for Lazarus's renewed focus on centralized services.
Increased difficulty of DeFi protocol attacks
Previous research by Elliptic on DeFi hacker attacks in 2022 found that an attack occurred on average every 4 days, with an average theft of $32.6 million per attack. Cross-chain bridges became one of the most frequently targeted types of DeFi protocols in 2022. These trends may have prompted improvements in smart contract auditing and development standards, thereby narrowing the scope for hackers to identify and exploit vulnerabilities.
Complexity of social relationships in centralized institutions
In many previous hacker attacks, the Lazarus Group's chosen method of attack was social engineering. For example, the $540 million hacker attack on the Ronin Bridge was caused by a former employee of the company being deceived by a false job on LinkedIn. However, decentralized services often have fewer employees, and projects are to some extent decentralized. Therefore, gaining malicious access to developers may not necessarily equate to gaining management access to smart contracts.
At the same time, centralized exchanges may employ relatively more staff, thereby expanding the potential target range. They may also use centralized internal information technology systems for operations, providing greater opportunities for Lazarus's malicious software to penetrate the business.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



