Ten years have passed since Tether launched the world's first mainstream stablecoin, USDT, pegged to the US dollar in 2014. After more than a decade of development, the total market value of stablecoins surpassed $250 billion in 2025, with an expected annual transaction volume of $36.3 trillion, exceeding the combined total of Visa and Mastercard. Stablecoins, with their characteristics of being pegged to specific assets (such as fiat currencies, gold, or other stable assets) and maintaining relatively stable value, have been widely used in various scenarios such as cross-border trade settlement, corporate fund management, and daily consumption payments: the annual payment scale in the B2B sector reached $36 billion, P2P transfers covered small and frequent fund exchanges, and physical merchants like Singapore's Metro and global retail giant SPAR have adopted stablecoin payments.
However, due to their inherent anonymity advantages, USDT has also been regarded as a "preferred tool" for money laundering by black and gray market groups. The "Xinkangjia" scam that caused a stir in 2025 relied on USDT for fund collection and transfer, ultimately leading to asset losses for thousands of investors. Next, we will delve into the new criminal methods employed by black and gray markets using USDT and explore strategies for enterprises and users based on practical experience in the blockchain security field.
1. USDT Issuance on Mainstream Blockchains
The deployment characteristics of USDT across multiple public chains facilitate cross-chain fund transfers and evasion of tracking for black and gray markets. The current issuance status of USDT on several major mainstream blockchains is as follows:
- Tron: The issuance of TRC20-USDT based on the TRC-20 protocol exceeds 75.8 billion, becoming a common choice for small and frequent transfers in black and gray markets due to its high throughput and low transaction fees;
- Ethereum: The issuance of ERC20-USDT exceeds 79 billion, often used as a vehicle for funds disguised as "normal investment transactions" due to its vast DeFi ecosystem;
- BNB Chain: The issuance of BEP20-USDT exceeds 7.4 billion, closely linked to the exchange ecosystem, making it an important channel for cross-border fund laundering;
- Solana: The issuance of SPL-USDT reaches 2.3 billion, with fast transaction confirmation speeds helping black and gray markets shorten fund transfer cycles;
- Polygon: The issuance of USDT based on the ERC-20 protocol reaches 1.4 billion, often used to divert large amounts of illegal funds as an Ethereum scaling solution.
This characteristic of "multi-chain distribution" allows black and gray market funds to switch quickly between different public chains, increasing the difficulty of regulation and tracking. BlockSec's Phalcon and MetaSleuth products have achieved comprehensive monitoring of mainstream chains such as Ethereum, BNB Chain, and Polygon, as well as tracking over 20 cross-chain bridges, providing technical support for fund tracking and compliance review.
2. Six New Criminal Methods of Black and Gray Markets Using USDT
Method 1: Fake U Forgery
Fake U refers to counterfeit USDT, typically created by tampering with on-chain data or forging transaction records, making it appear highly similar to real USDT but lacking actual value support. Common tactics used by black and gray markets include:
- At niche exchanges or peer-to-peer trading platforms, using "5%-10% below market price" as bait to attract users for private trading;
- Forging USDT transfer record screenshots to deceive victims into believing "the funds have arrived," inducing them to pay fiat currency or other assets in advance;
- Developing fake wallet apps with a built-in "fake U generation function," leading victims to mistakenly believe they hold real USDT, thereby stealing their wallet private keys.
Such scams are difficult for ordinary users to identify, but can be easily verified with professional tools. Commonly used blockchain explorers (like Etherscan) and BlockSec's MetaSuites plugin can quickly identify the "anomalous transaction characteristics" of fake U through on-chain data verification, helping users and enterprises avoid such risks. This capability relies on BlockSec's years of comprehensive risk monitoring, enabling real-time identification and data capture, resulting in hundreds of millions of risk contract address labels.
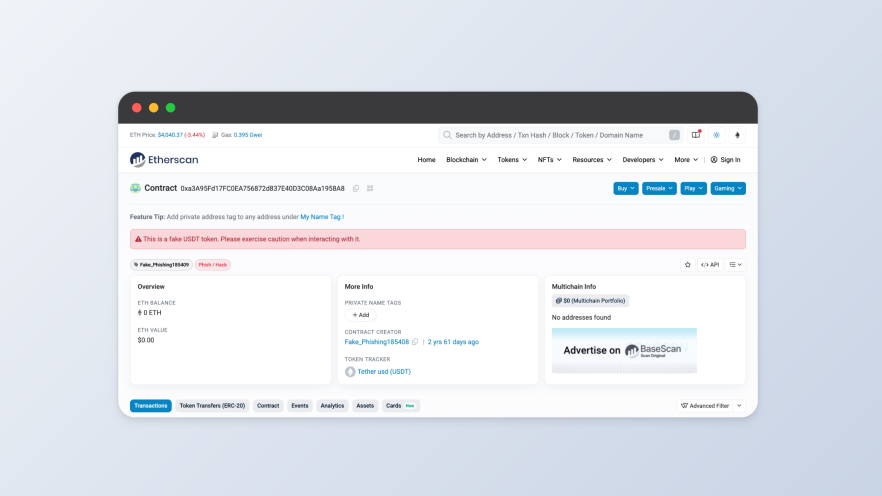
Method 2: Black U Circulation
Black U refers to USDT obtained through illegal activities such as telecom fraud, online gambling, theft, human trafficking, and terrorism financing, with the core risk being "compliance of fund sources." Black and gray markets typically allow black U to flow into the normal market through the following methods:
- "Score running" platform distribution: Building a fake "digital currency trading agency" platform to attract ordinary users to become "score runners," using personal bank cards to receive fiat currency exchanged from black U, which is then transferred to designated accounts to complete "fund splitting";
- DeFi protocol mixing: Utilizing DeFi platform features like "anonymous lending" and "liquidity mining" to mix black U with other compliant assets, increasing the difficulty of fund tracing and obscuring fund flows;
- Cross-border OTC trading: Exchanging black U for other virtual currencies through overseas anonymous OTC merchants, then transferring it to domestic exchanges for cashing out.
For enterprises (especially exchanges and payment institutions), the inflow of black U can lead to wallet freezes at best, and at worst, result in license revocation, hefty fines, or even criminal imprisonment. BlockSec's Phalcon Compliance product can identify "high-risk addresses" and "anomalous transaction patterns" associated with black U in real-time through address risk scoring, fund chain tracing, and AI risk behavior analysis, helping enterprises intercept illegal funds during user deposits and transactions, thus meeting anti-money laundering (AML) and compliance review requirements.
Method 3: Theft U Upgrade
The methods of theft U have evolved from simple "phishing links" and "address poisoning" to more covert technical attacks, mainly including:
- Malicious plugin hijacking: Implanting plugins in browsers to monitor user wallet operations and steal private keys or transfer authorizations;
- Exploiting smart contract vulnerabilities: Attacking DeFi platform contract vulnerabilities to transfer users' staked USDT (e.g., a lending protocol lost 120 million USDT in 2024 due to a "reentrancy vulnerability");
- Supply chain attacks: Infiltrating third-party tools (like wallet SDKs, trading APIs) and implanting "backdoors" in the code to steal user assets in bulk.
The $1.5 billion theft from Bybit was an organized, targeted on-chain attack initiated by a sovereign state, where attackers deceived multiple operators of the Safe wallet into signing a Safe wallet upgrade transaction, successfully taking over the Safe wallet. Detailed analysis of the attack event: Analysis of the Bybit theft incident.
- Malicious upgrades: Deceiving project parties into signing transactions through new blockchain features like 7702, taking over project party privileged accounts to complete asset theft. For example, the recent theft of SeedifyFund and Griffin_AI projects was accomplished using this method.
The BlockSec team has repeatedly monitored such attacks and assisted project parties in preemptively blocking attacks through the Phalcon Security threat monitoring and attack interruption platform, automating the attack blocking process at the moment of the attack. Additionally, Phalcon Compliance's "vulnerability-related address database" can help enterprises preemptively mark "malicious addresses" that have participated in attacks, preventing them from laundering funds through the platform. Currently, BlockSec has completed over 20 white hat rescues, recovering over $20 million in losses and safeguarding over $50 billion in digital assets on-chain in real-time.
Method 4: USDT Money Laundering
Current money laundering in black and gray markets has formed a model of "multi-chain jumping + DeFi tool nesting," with a typical process as follows:
- Black and gray markets exchange illegal funds for USDT, dispersing them into 10-20 "intermediate wallets";
- Transferring USDT to different public chains through cross-chain bridges (e.g., from Ethereum to Polygon) and conducting a "lending - collateral - exchange" cycle on DeFi platforms;
- Transferring the laundered USDT to offshore exchanges, converting it into fiat currency or other assets, completing the fund outflow.
In this model, the fund chain is cut into dozens of segments, making traditional tracking methods difficult to penetrate. BlockSec, through its "full-link fund mapping" technology, can restore cross-chain fund flows and identify "anomalous cycle characteristics" in DeFi operations, providing enterprises with compliance reports that meet FATF (Financial Action Task Force) standards, helping them meet cross-border fund regulatory requirements.
Method 5: USDT Score Running Platforms
USDT score running platforms are a typical model used by black and gray markets to "launder" funds through ordinary user accounts, with a hidden operation logic that is highly deceptive:
Black and gray market groups first build a fake "digital currency trading assistance platform," using "part-time work from home, earning hundreds a day" as a gimmick to attract unemployed individuals, students, and other groups to register as "score runners." The platform requires score runners to bind personal bank cards or virtual currency wallets, then splits the USDT obtained from overseas telecom fraud and online gambling, distributing it to score runners in the form of "platform tasks" — after receiving USDT, score runners must transfer an equivalent amount of fiat currency to a designated account according to platform instructions, completing a "score running" process, with the platform paying a commission of 1%-3% of the transaction amount.
This model breaks down large illegal funds into hundreds of small transactions, using ordinary users' "legitimate accounts" to obscure the source of funds, creating significant difficulty for regulatory tracking. Phalcon Compliance can quickly identify the core fund pool addresses of score running platforms by analyzing "multiple accounts pooling funds to the same address" and "small, high-frequency transfers."
Method 6: Virtual Currency Pyramid Schemes
Virtual currency pyramid scheme groups often use "blockchain innovation" and "stable returns" as a guise, packaging USDT as an "investment target" or "entry threshold" to attract users to join and develop downlines. Their tactics mainly consist of three steps:
- Persona packaging: Creating false personas such as "crypto tycoons" or "overseas investment experts" on social platforms, sharing fake cases of "20% monthly returns on USDT investments," creating an illusion of "low risk and high return";
- Hierarchical recruitment: Setting "investment thresholds" — users must recharge 1,000-10,000 USDT to become members, developing three downlines to upgrade to "agents," earning a "referral reward" of 5% of the downline's investment amount, with higher levels receiving higher commission rates;
- Fund pool collapse: Initially using new users' USDT to pay "returns" to old users to maintain the scam; when new user growth slows and fund inflow is insufficient, the group directly shuts down the platform and absconds with all users' USDT.
Investors should fully recognize the high risks of the virtual currency market, especially the widespread use of USDT in black and gray markets. Do not trust so-called "guaranteed profits" investment promises, and remain highly vigilant towards investment projects with excessively high returns and extremely low risks.
3. Conclusion
As an important asset in the blockchain ecosystem, USDT itself has no inherent good or evil in its "tool attributes," but its abuse by black and gray markets poses a serious threat to financial security and user assets. From fake U forgery to multi-chain money laundering, the technical and covert nature of criminal methods requires enterprises to build risk defenses using professional compliance tools (such as Phalcon Compliance) and for users to enhance their security awareness.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




