Author: Fairy, ChainCatcher
Editor: TB, ChainCatcher
During the bear market of 2022, GMX was one of the few highlights, representing on-chain perpetual contract trading and even once held an almost monopolistic position.
However, as the market recovered and competition intensified, its brilliance was gradually overshadowed by emerging players. Now, a hacker attack amounting to $42 million has once again brought GMX back into the public eye.
What is even more disheartening is that this incident has not garnered widespread attention in the Chinese community. A project that once held significant influence in the industry is quietly exiting the main stage.
Former King Faces Heavy Blow
Since its launch in September 2021, GMX's TVL rapidly grew to $350 million before the LUNA collapse and reached a peak of about $700 million in May 2023. Its token price also soared, peaking at $91 in April 2023.
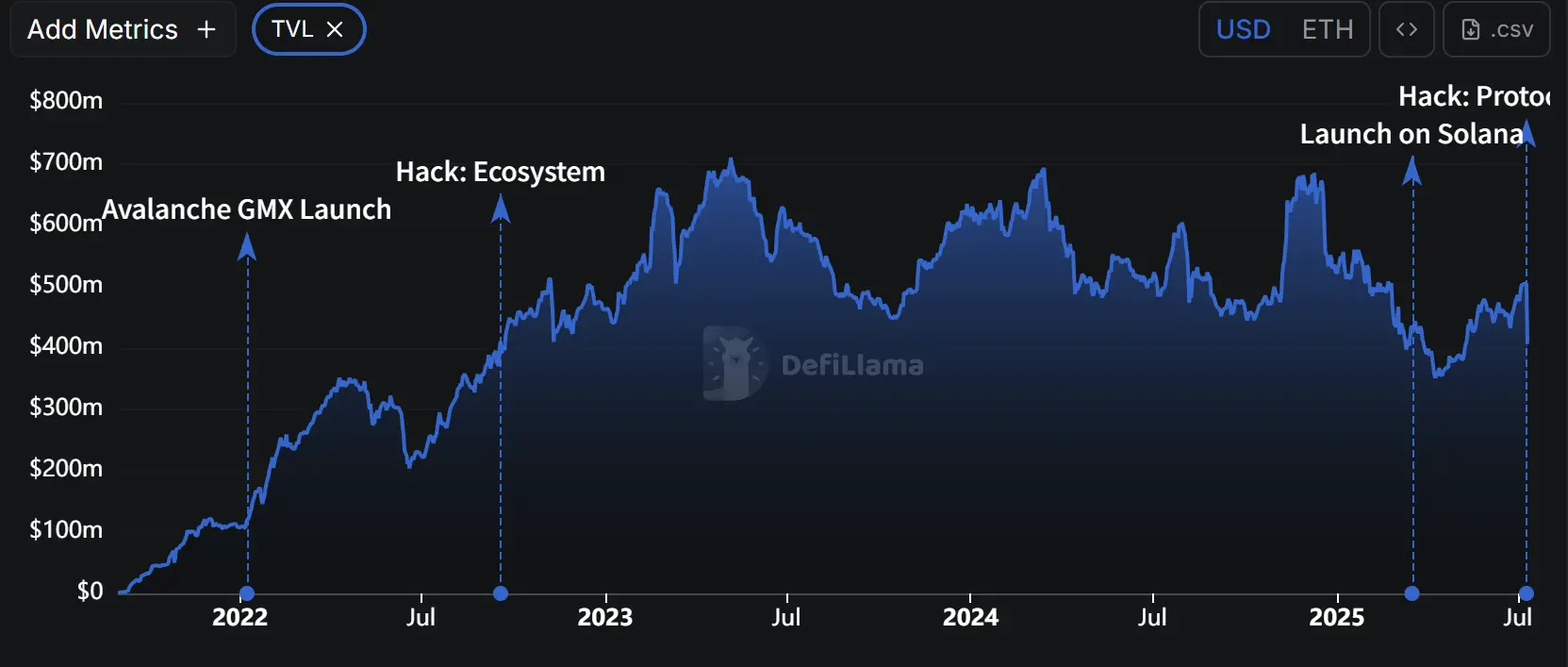
Image source: Defillama
However, with the rise of new protocols, the market share of established projects like GMX has been continuously eroded. The recent hacker attack on GMX has further compounded the challenges amid declining traffic.
This attack caused GMX's token price to drop by 17.3%, with TVL evaporating by about $100 million, a decline of up to 20%. The hacker stole over $42 million in crypto assets, involving various mainstream tokens, including WBTC, WETH, UNI, FRAX, LINK, USDC, and USDT.
After the incident, the GMX team immediately left a message on the hacker's address, offering a 10% white hat bounty. However, according to monitoring by YuJin, the attacker has converted most of the stolen assets into about 11,700 ETH and dispersed them into four wallets. This operation essentially means the attacker has rejected the bounty proposal put forth by the project team.
It is worth noting that this is not the first time GMX has faced an attack. As early as September 2022, its v1 protocol deployed on Avalanche was exploited by hackers, resulting in a loss of about $560,000.
Attack Path Breakdown
In GMX, GLP is the liquidity provider token, representing a share of the treasury assets (such as USDC, ETH, WBTC). When the enableLeverage function is activated, users can open leveraged positions, including long or short operations.
According to security company BlockSec, the root cause of this issue lies in the incorrect invocation of the executeDecreaseOrder function.
The first parameter of this function was supposed to be an external account (EOA), but the attacker passed in a smart contract address, thereby executing a reentrancy attack.
Specifically, before redeeming GLP, the attacker opened a large short position in WBTC. Since the short position increased the global short size upon opening, and the price had not yet changed, the system defaulted this short as a loss, and this unrealized loss was counted as "assets" of the treasury, artificially inflating the AUM.
Although the treasury did not actually gain additional value, the redemption calculation was based on this inflated AUM, allowing the attacker to obtain assets far exceeding what they were entitled to.
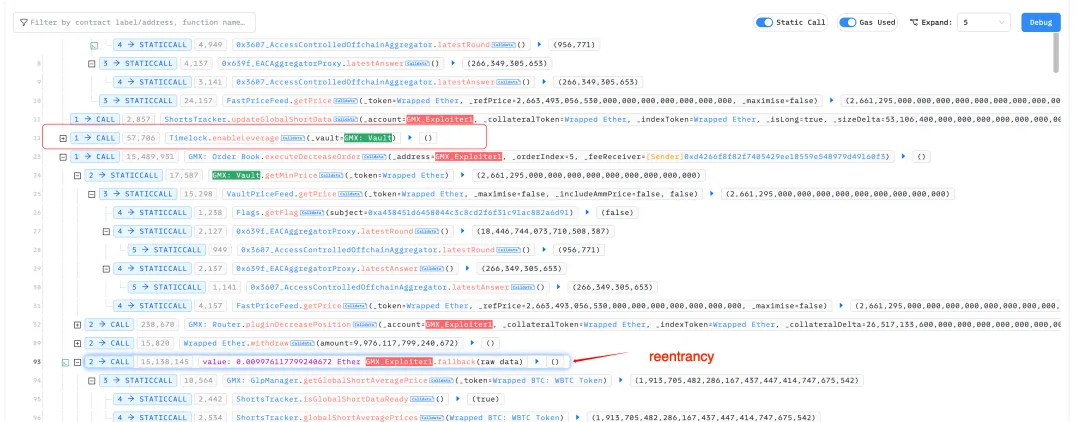
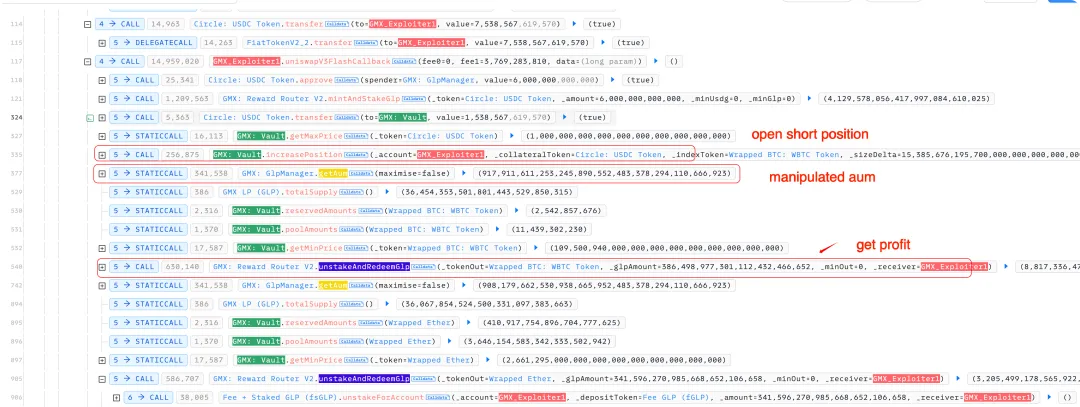
Image source: BlockSec
$27 Million in Funds May Face Chain Reaction?
GMX's early success sparked a wave of "forks," where numerous projects copied its open-source code, making slight modifications or deploying it on other blockchains. Security company PeckShield warned that the vulnerability exploited in GMX v1 may also exist in these replicated protocols.
It is estimated that approximately $27 million in funds are still exposed to such risks. Data from DeFiLlama shows that 64 related projects have been identified, but only 13 of them have a TVL exceeding $100,000.
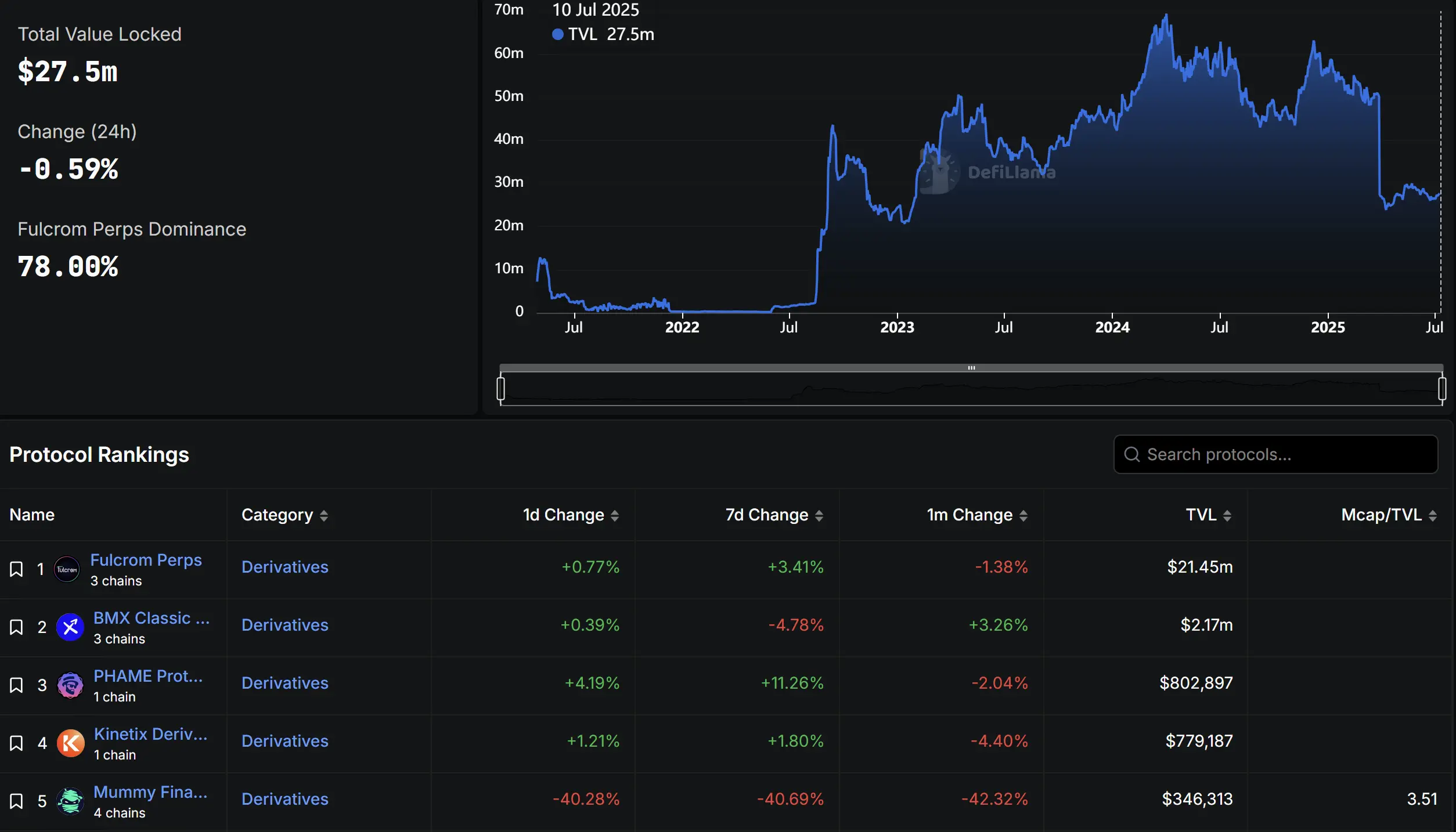
Image source: DeFiLlama
GMX has issued a warning on the X platform, urging these projects to take immediate countermeasures, including disabling leverage functions and pausing the minting of GLP tokens to prevent similar attacks from occurring again.
Circle's Slow Response Sparks Outrage
In this attack incident, the stablecoin issuer Circle also faced criticism for its slow response, which the community deemed "too slow." Several users pointed out that Circle had the opportunity to blacklist the hacker's address and freeze over $9 million in stolen USDC but failed to take timely action.
The attacker even used Circle's own cross-chain bridging tool CCTP to transfer 8 million USDC from Arbitrum to Ethereum, subsequently exchanging it for DAI. Despite this fund remaining on-chain for 1-2 hours, Circle did not respond at all.
On-chain analyst ZachXBT publicly criticized Circle's sluggishness, and this is not the first time ZachXBT has targeted Circle; he has repeatedly questioned co-founder Jeremy Allaire on Twitter about why they are always "a step behind" at critical moments. For instance, during the Bybit hack incident, Circle only froze the relevant address a day later.

GMX was once a pioneer in decentralized perpetual contract trading platforms, leading a golden wave. Looking back at the development of this sector, the first-generation project DYDX once shone brightly but now struggles in silence, while Perpetual Protocol is nearly "extinct"; the second-generation project GMX has been severely impacted by the hacker attack; now, only the third-generation project Hyperliquid is rising strongly, taking the lead.
The market landscape is ever-changing; security and evolution are the eternal paths for projects.
Recommended Reading:
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




