The encryption application is the main beneficiary of the transformation of infrastructure construction methods.
Author: Adrian
Translation: Deep Tide TechFlow

Alt L1s - Speeding up again?
In each encryption cycle, the most successful investments are often early bets on new basic layer infrastructure primitives (such as PoW, smart contracts, PoS, high throughput, modularity, etc.). If you look at the top 25 assets on Coingecko, only two tokens are not native tokens of L1 blockchains (excluding anchored assets), they are Uniswap and Shiba Inu. Joel Monegro first explained this phenomenon in 2016, proposing the "Fat Protocols Theory". The theory points out that the biggest difference in value accumulation between Web3 and Web2 is that the value accumulated by the encrypted basic layer exceeds the total value obtained by the applications built on it. This value comes from:
The blockchain provides a shared data layer for settling transactions, which promotes positive competition and supports permissionless composability.
The positive cycle driven by token appreciation is: Token appreciation > attracting speculators to participate > converting speculators into actual users > increasing users and token appreciation attracting more developers and users, forming a continuously expanding ecosystem.
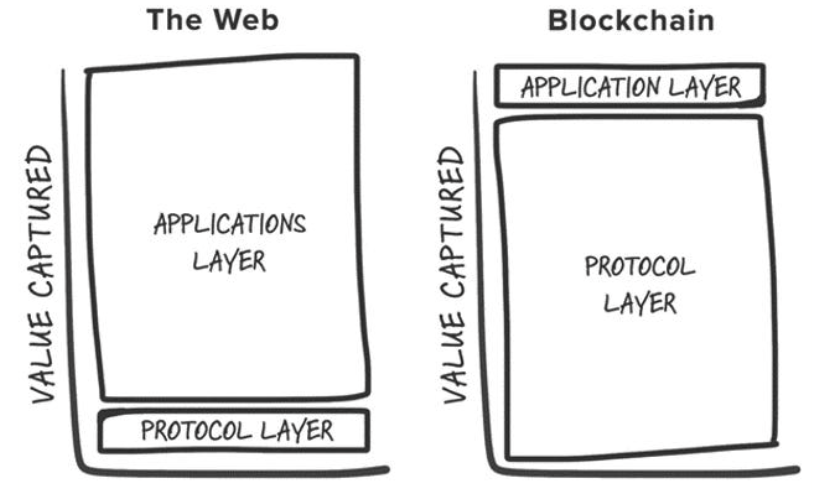
Original Fat Protocols Theory
By 2024, the original Fat Protocols Theory has undergone multiple industry debates and has been challenged with structural changes in the industry dynamics:
1. Commodification of block space - With the realization of infrastructure premiums, the emergence of successful alternatives to L1 (such as Solana in high throughput, Celestia in data availability) has made them "category definers", attracting builders and investors to participate in alternative L1 investments in each cycle. Each cycle has new blockchains that excite investors and users with their differentiated features, but may ultimately become "ghost chains" (such as Cardano), i.e., blockchains lacking actual users and application support. Overall, this has led to an oversupply of block space in the market, but a lack of sufficient users and applications to utilize these resources.

2. Modularity of the basic layer - With the emergence of more and more specialized modular components, the definition of the "basic layer" has become increasingly complex, not to mention how to decompose the value accumulated by each layer of the stack. However, I believe that in this transformation, it is clear that:
In a modular blockchain, value is dispersed throughout the entire stack. For a single component (such as Celestia) to be valued more than the integrated basic layer, that component (such as data availability DA) must become the most valuable part of the stack, and the "applications" (modular blockchains) built on it need to generate more usage and fees than the integrated system;
Competition between modular solutions drives more economical execution and data availability solutions, further reducing user costs.
3. Towards the future of "chain abstraction" - Modularity has led to the fragmentation of the ecosystem, making the user experience cumbersome. For developers, this means facing too many choices to decide where to deploy applications; for users, it means overcoming many obstacles when switching from application A on chain X to application B on chain Y. Fortunately, many smart people have already realized this problem and are working hard to build a future where users do not need to understand the underlying blockchain when interacting with encrypted applications. This vision is called "chain abstraction," a theory that excites me. The question now is, how will value accumulate in the future of chain abstraction?
I believe that encryption applications are the main beneficiaries of the transformation of infrastructure construction methods. In particular, intent-centered transaction supply chains, as well as the exclusivity of order flow and user experience, branding, and other intangible assets, will increasingly become the competitive barriers of these applications, enabling them to achieve profitability more effectively than existing models.
Exclusivity of order flow
Since Ethereum completed the merge and introduced Flashbots and MEV-Boost, its MEV (Maximum Extractable Value) landscape has undergone significant changes. The once searcher-dominated "dark forest" has evolved into a market-oriented order flow market. In this market, the current MEV supply chain is mainly dominated by validators, who receive about 90% of the generated MEV through the form of bidding from each participant in the supply chain.
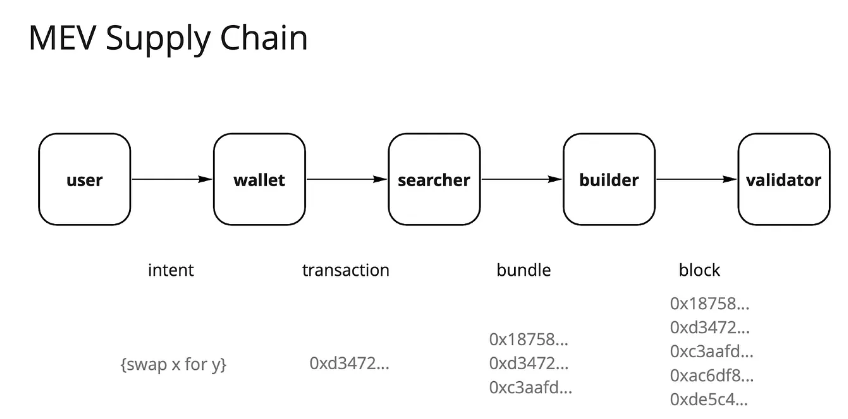
Ethereum's MEV supply chain
Validators occupy most of the extractable value, which has left many participants in the transaction supply chain dissatisfied. Users hope to be compensated for generating order flow, decentralized applications (dapps) hope to retain the value brought by user order flow, and searchers and builders hope to increase profits. Therefore, participants eager to capture value have begun to try various strategies to extract excess returns, one of which is the integration of searchers and builders - the core of this strategy is that by increasing the determinism of the searcher package, higher profit rates can be achieved. A large amount of data and literature shows that in a competitive market, exclusivity is the key to capturing value, and applications with the most valuable traffic will have pricing power.
This phenomenon is also reflected in retail stock trading conducted through brokers such as Robinhood. Robinhood maintains "zero-cost" trading by selling order flow to market makers and profits by capturing rebates. Market makers like Citadel are willing to pay for these order flows because they can profit from arbitrage and information asymmetry.
In addition, more and more transactions are being conducted through private memory pools, reaching a historical high of 30% on Ethereum. Decentralized applications (dapps) realize that the value of user order flow is being extracted and leaked into the MEV supply chain, and private transactions provide more opportunities for customization and monetization around high-stickiness user flows.
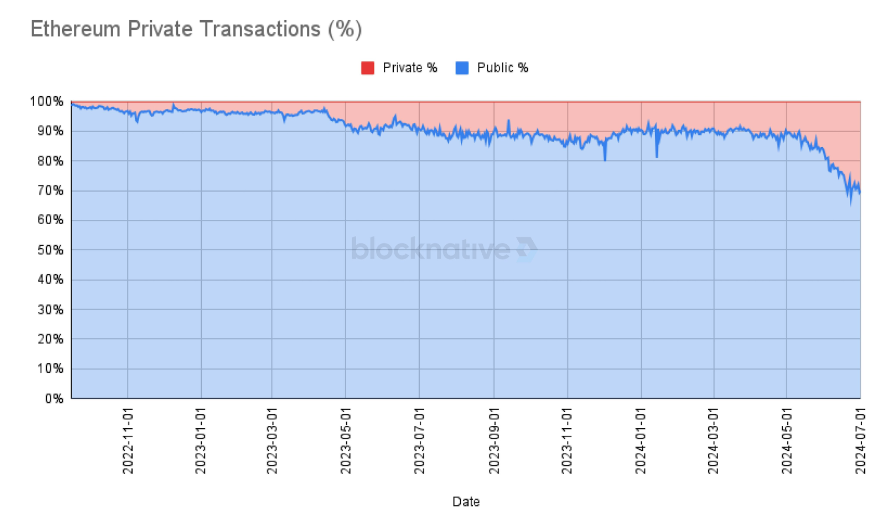
(Chart source X)
As we move towards a future of chain abstraction, I expect this trend to continue. Under an intent-centered execution model, the transaction supply chain may become more fragmented, and applications will restrict their order flow to solver networks that can provide the most competitive execution, which will intensify competition among solvers and thus lower profit margins. However, I believe that most value capture will shift from the basic layer (i.e., validators) to the user-facing level, where middleware components, while valuable, have lower profit margins - in other words, front-ends and applications that can generate valuable order flow will have pricing power over searchers and solvers.

About the accumulation of future value
We have seen this trend manifest in certain types of order flow that utilize specific application sorting mechanisms, such as Oracle Extractable Value (OEV) auctions (such as Pyth, API3, UMA Oval), which provide a way for lending protocols to reclaim the liquidation bids that should rightfully belong to validators.
User experience and branding as sustainable moats
If we further analyze the 30% private transaction sources mentioned earlier, we can see that most of them come from the front end, such as Telegram bots, decentralized exchanges (Dexes), and wallets:

Breakdown of transaction sources through private memory pools
Although cryptocurrency users are generally considered to have short attention spans, we are finally seeing a certain level of user retention. Applications have shown that branding and user experience can be powerful moats—
User experience: Alternative front-end forms introduce a completely new experience, naturally attracting users with specific experience needs, starting from connecting wallets on web applications. A good example is Telegram bots like Bananagun and bonkbot, which have generated over 150 million USD in fees, allowing users to easily trade memes in Telegram chats.
Branding: In the cryptocurrency field, establishing a reputable brand can increase fees by winning user trust. While the exchange feature built into wallets is known for high fees, it is a successful business model because users are willing to pay for convenience. For example, the exchange feature of Metamask generates over 200 million USD in fees annually. Finally, Uniswap Lab's front-end fee switch has netted 50 million USD since its launch. Transactions interacting with Uniswap Labs contracts through unofficial front-ends do not incur this fee, but their revenue is still increasing.
This indicates that the Lindy effect also exists in applications, and may even be more significant than in infrastructure. Typically, the adoption of new technologies (including cryptocurrencies) follows some form of an S-curve, as we transition from early adopters to a more mainstream audience—the next wave of users may not be as tech-savvy and therefore less price-sensitive, allowing brands that reach critical mass to profit in creative (or simple) ways.
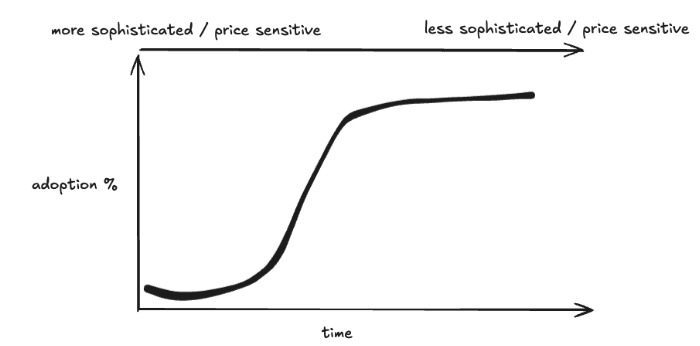
S-curve of cryptocurrencies
Conclusion
As someone primarily focused on infrastructure research and investment, this article is by no means meant to deny the status of infrastructure as an investable asset in cryptocurrencies, but rather to encourage a shift in mindset when thinking about new types of infrastructure that can support the next generation of applications. These applications will serve a more high-end user base on the S-curve. New infrastructure needs to showcase entirely new use cases at the application level to attract attention. Meanwhile, there is already enough evidence at the application level to show that user ownership directly promotes sustainable business models for value accumulation. Unfortunately, we may have passed a stage where every new hot L1 project brings exponential returns; however, projects with significant differentiation may still be worth attention and value.
Instead, I spend more time thinking about and understanding the "infrastructure," which includes the following aspects:
AI: This includes the AI Agent Economy, which can automate and improve end-user experiences; computation and reasoning markets, which continuously optimize resource allocation; and verification technologies that extend the computational capabilities of blockchain virtual machines.
CAKE Stack: Many of my previous points indicate that we should move towards a future of chain abstraction, and there is still a lot of design space for most components in the stack. As infrastructure supports chain abstraction, the design space for applications will naturally expand, potentially blurring the boundaries between applications and infrastructure.
DePIN: I have always believed that DePIN is a key application of cryptocurrencies in the real world, second only to stablecoins, and that view has not changed. DePIN leverages the advantages of cryptocurrencies: coordinating resources without permission through incentive mechanisms, launching markets, and decentralized ownership. While each network type still faces specific challenges, significant progress has been made in solving the cold start problem. I am very much looking forward to seeing founders with industry expertise use encryption technology to launch their products.
If you are developing a project related to the above content, please feel free to contact me, as I am happy to discuss with you. I also welcome all kinds of feedback or opposing views, because frankly, if I am completely wrong, investing will become simpler.
"The most exciting applications of the Ethereum blockchain are probably ones that we haven't even thought of yet." - Vitalik Buterin, 2014
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




