In addition to investing in on-chain security and gradually improving the overall security of our industry, there are no other solutions to address these issues.
Author: Mitchell Amador
Translation: DeepTechFlow
Abstract
As of now, no one can accurately estimate the expected losses from on-chain hacker attacks, which is regrettable. However, we can estimate the on-chain hacker attack's true cost by analyzing the hacker attacks from the past few years! I analyzed hacker attacks from 2021 to 2023 to derive a representative estimate of the true cost of on-chain hacker attacks. We call it Amador's Hacker Impact Estimate.
Amador's Hacker Impact Estimate: If your protocol is hacked, you are expected to lose about $16 million, your token price will drop by 52% of its market value, the depressed token price is expected to persist for at least 6 months (and possibly longer), and recovery will take 3 months of time and effort.
If your product is a platform (whether it's an L1/L2 blockchain or a financial base protocol), it is expected that your protocol and its dependencies will be destroyed, as demonstrated by precedents such as Terra-Luna.
We have summarized these findings here. Check it out! When they are available, we will add more statistical data and data points there.
How high are the actual losses from on-chain hacker attacks?
So far, no one really knows. But predictive estimates can be found by analyzing historical hackers. In this article, we will review historical data from the past few years to predict typical future hacker attacks across impact categories (not just stolen funds). From here, we will create a heuristic method to estimate the typical cost of a hacker attack on your favorite protocol, which I call Amador's Hacker Impact Estimate.
Surprisingly, despite hundreds of hacker attacks on the crypto industry in the past three years, we do not have a good estimate of the impact of hacker attacks today. For this, we must blame the difficulty of measuring the real impact of hacker attacks.
In fact, the net theft value (i.e., widely used standard data) severely underestimates the damage caused. It overlooks all other ways in which hacker attacks cause damage, many of which result in financial losses even greater than the hacker attack itself, although these damage methods are more difficult to quantify. The least recognized contributing factors to the total hacker damage for non-security professionals include:
Market Impact: Market impact refers to the damage caused by hacker attacks to the public trading of tokens (or assumed equities), which may last a long time. This impact is far less known than the immediate value of the hacker attack, and most security professionals still underestimate its importance.
Dependency Impact: Dependency impact refers to the secondary effects originating from the original hacker attack, causing damage to other assets. There are three major categories of dependency impact: platform dependency, financial dependency, and reputation impact. The blockchain itself being attacked by hackers, to the extent that it damages all assets/contracts built on that blockchain, is an example of platform dependency impact. The drop in Luna price destroyed the value of Terra stablecoins, which is a good example of financial dependency impact (although it is not the kind of hacker attack that most DeFi hacker attacks are). The lack of security of a platform (such as BNB Chain) leads to a decline in user growth and adoption, which is an example of reputation impact.
Talent and Organizational Impact: The damage here is difficult to quantify and usually manifests as time, money, and talent loss due to the response and recovery after a hacker attack. Considering that a single hacker attack and its recovery may consume a small startup team for several months, organizational impact is always costly, sometimes even fatal. All organizations must deal with this impact after a hacker attack, except for the most prepared ones.
In other words, the typical hacker attack causes far more damage than can be indicated by stolen funds alone!
The rest of this article will describe estimates of each impact type in a typical hacker attack scenario by looking at historical medians, or estimating based on my firsthand experience when data is not available.
Impact of Funds Being Stolen
Data shows that there were 107 hacker attacks in 2021, 134 in 2022, and 247 in 2023, totaling 488 publicly known hacker attacks (2021-2023).
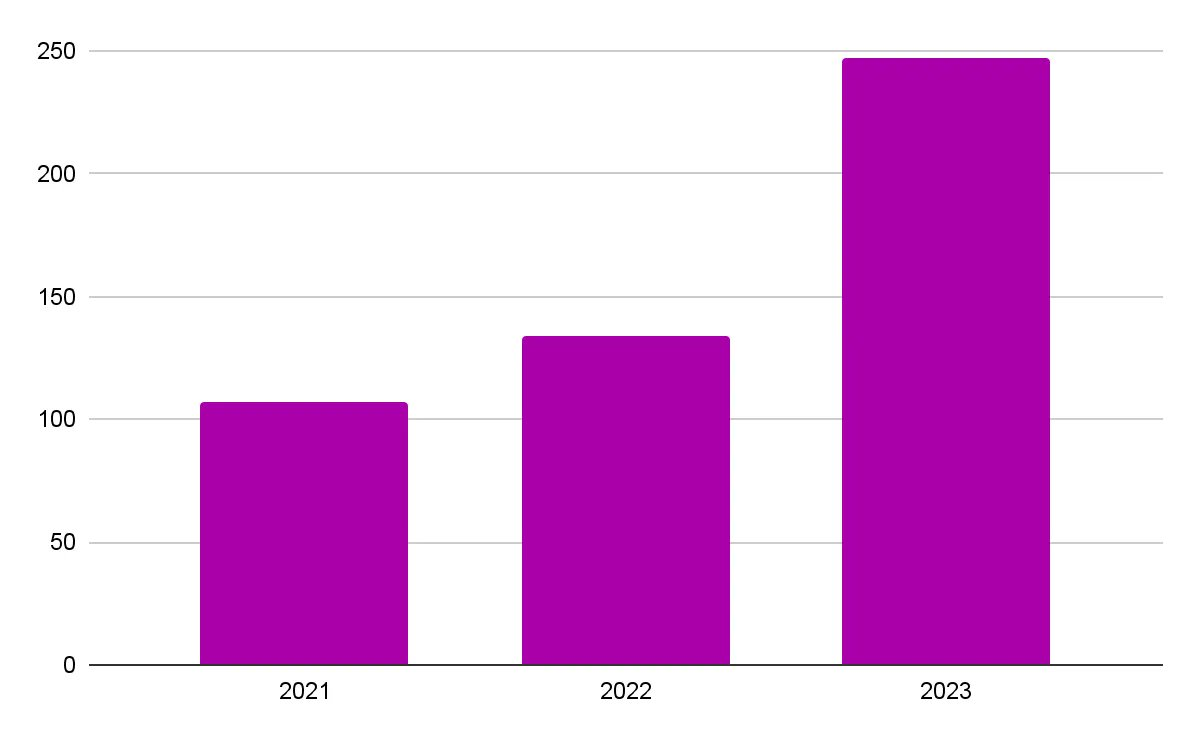
x-axis: year, y-axis: number of hacker attacks
These hacker attacks affected $2,334,863,067 in 2021, $3,773,906,837 in 2022, and $1,699,632,321 in 2023, totaling $7,808,402,225 in funds affected from 2021 to 2023.
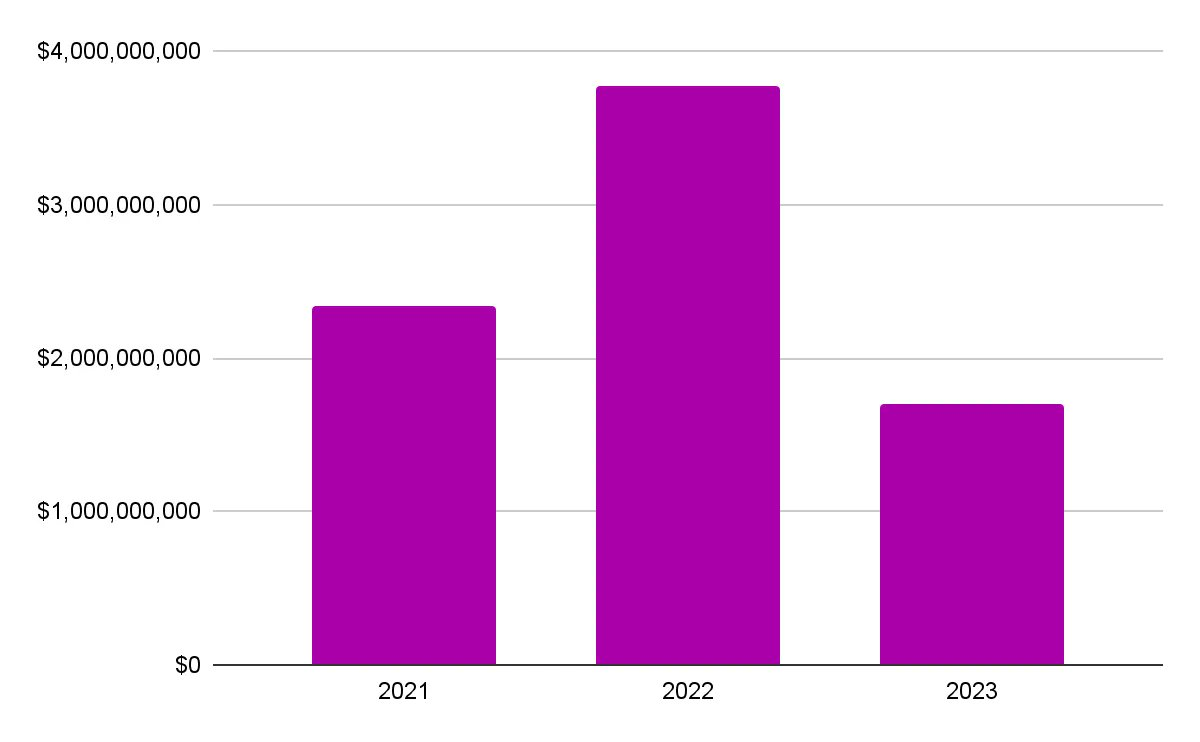
x-axis: year, y-axis: amount of funds stolen (in USD)
To be clear, the affected funds refer to funds that were hacked, stolen, or lost in other ways, but do not include funds returned or recovered by white-hat hackers and investigators.
Based on this data, some simple mathematical calculations for the 2021 to 2023 dataset yield the following insights:
The average amount of funds stolen per hacker attack is $16,000,824.
The median amount of funds stolen per hacker attack is $1,000,000.
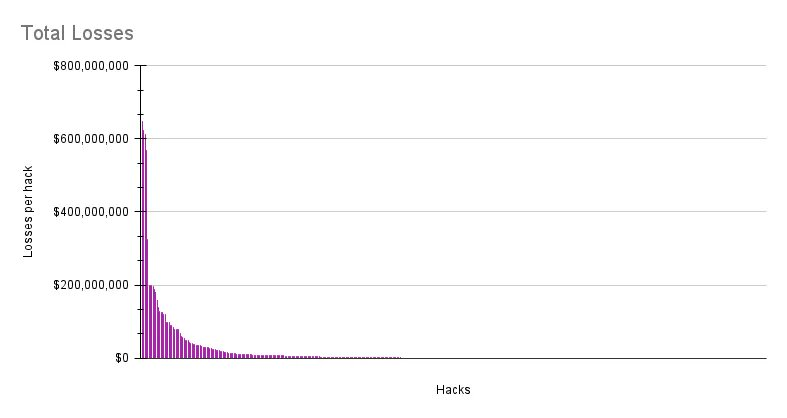
Hacker attacks follow a power-law distribution; while many hacker attacks are small in scale, when large-scale attacks occur, their losses are over a hundred times that of the median attack.
Market Impact
Estimating market impact has always been a historical challenge. Immunefi produced the first report of its kind, which reviewed the 2022 hacker attacks and their impact on a sample of 63 hacker attacks in 2022. The sample shows that the base token price dropped an average of 13% two days after the hacker attack, and an average of 19.5% five days after the attack.
To enrich our review, we decided to update this dataset with as much data as possible from hacker attacks in 2021, 2022, and 2023. We will reference median price changes. The expanded dataset makes the median a more predictable estimate, considering the possibility of extreme outliers.
The new dataset covers 176 hacker attacks. The results are quite shocking:
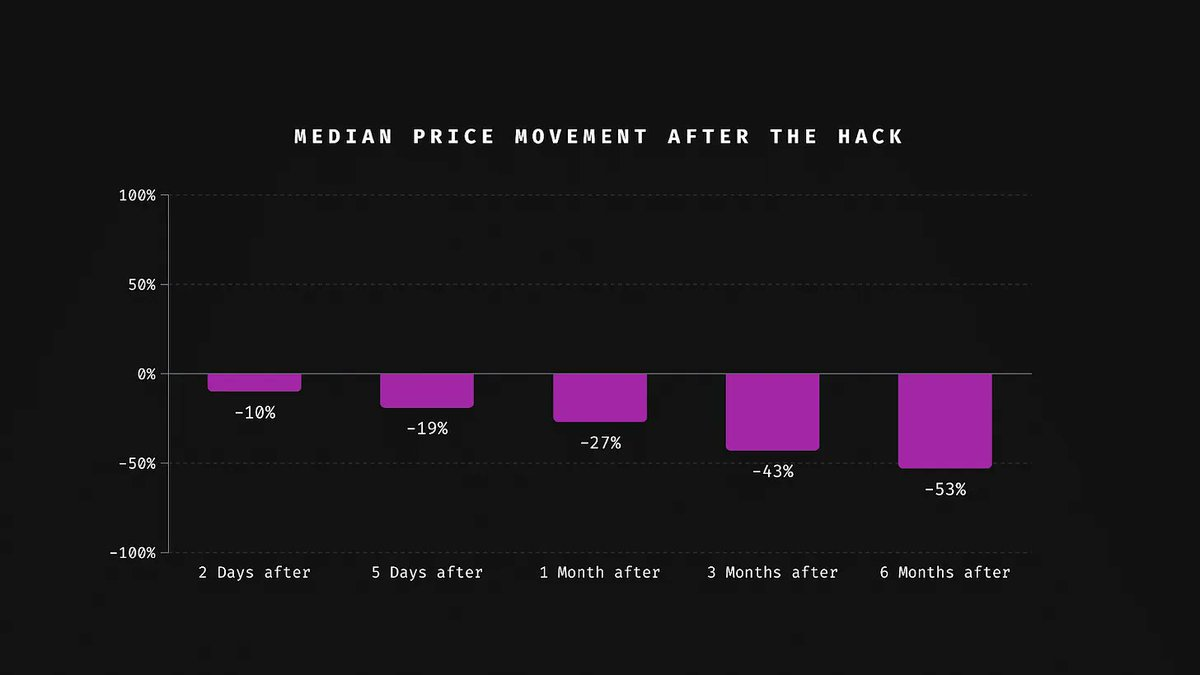
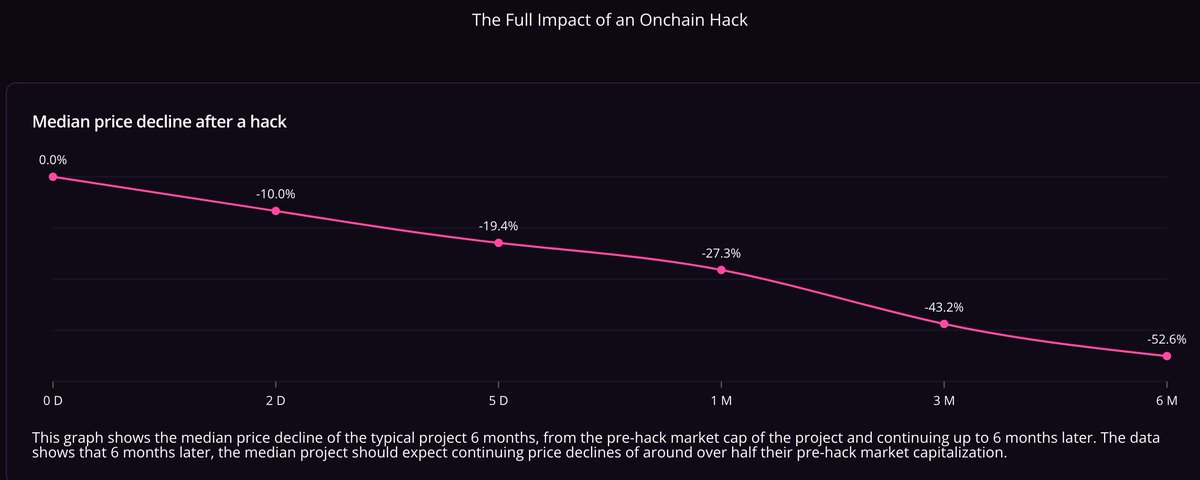
Median token price drops from the day of the hacker attack to two days after the attack to six months after the attack:
The data indicates that the median price drops and long-term price suppression after a hacker attack are as follows:
10% drop two days after the hacker attack,
19% drop five days after the hacker attack,
27% drop one month after the hacker attack,
43% drop three months after the hacker attack,
53% drop six months after the hacker attack.
Beyond the median, observing the most severe cases yields even more astonishing results. Three months after the hacker attack, 32% of the attack cases experienced a token price drop of over 50%, and 11% of the cases dropped over 90%. Six months after the hacker attack, 35% of the attacked projects continued to experience a price drop of over 50%, and 16% of the projects dropped over 90%.
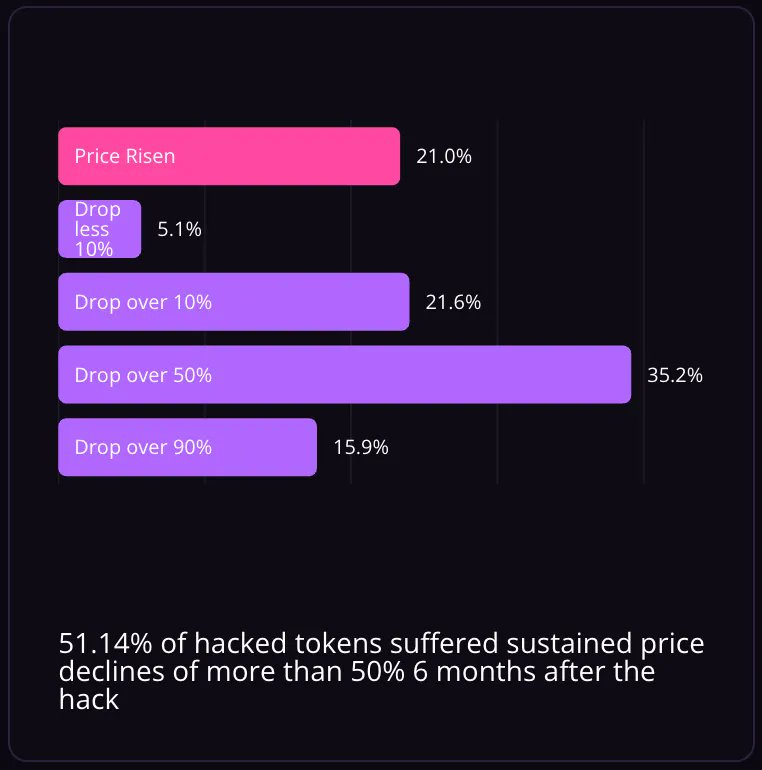
Distribution of price changes six months after the hacker attack. Historical data shows strong and sustained price suppression after a hacker attack.
This demonstrates a power-law distribution of hacker impact, indicating that a single severe hacker attack could be fatal. Additionally, it shows that hacker impact intensifies over time, with sustained effects on the market for at least six months after the attack.
Market impact may continue to intensify over a year, but since our dataset only covers three years of hacker attacks, we need to wait until the data for 2024 is fully aggregated to verify this assumption.
It is important to note that we cannot be 100% certain that this impact is caused by the hacker attack. Many factors may exert downward pressure on token prices, including some factors that we may not be aware of in this study. The most obvious confounding factor is the correlation between token prices and macro market conditions. However, these data are so severe and significant that they seem to be primarily due to hacker attacks, so we take this position.
Taking all the data into account, we expect a typical hacker attack to cause a market impact of approximately -19% in the first five days, intensifying to -53% over the next six months (potentially indefinitely), with a 16% chance of this damage exceeding 90% of the project's market value.
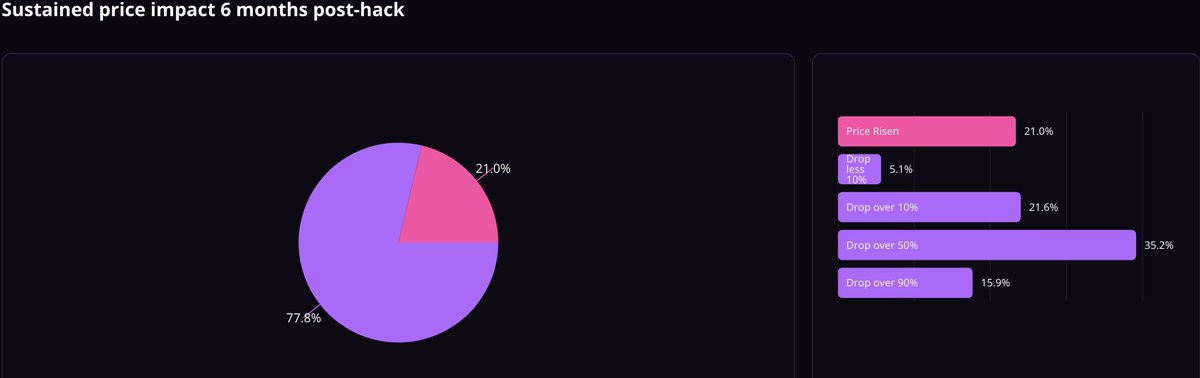
Distribution of price changes six months after the hacker attack shows that 77.8% of the attacked projects experienced sustained price suppression after six months.
Clearly, the market impact can be quite terrifying!
Once you realize that most token projects use their liquid tokens as treasuries and growth fuel, you can understand why security professionals are so concerned about market impact. Even if a hacker attack does not cause direct damage, excessive market impact can be equally fatal.
Dependency Impact (or Secondary Impact)
There is a major underappreciated hacker impact that we call dependency impact, or occasionally secondary impact. It describes the cascading damage caused by the initial hacker attack. Here are some examples of this impact:
Platform dependency impact refers to the damage caused by the downtime of the underlying platform (such as in a denial-of-service attack on a blockchain, which affects currency markets or perpetual markets running on the affected platform), which may disrupt all applications running on that platform. While this situation is common (there are countless platforms in the crypto space), the limited connection between on-chain and off-chain economies has so far limited the frequency of this impact, and blockchain technology itself has proven to be remarkably resilient. With the connection between on-chain and off-chain economies, we should expect this impact to become more common and severe.
Financial dependency impact refers to the secondary impact on dependent assets caused by hacker attacks. Assets with financial dependency risk include stablecoins (such as MakerDAO, CDP liquidation), liquid staking tokens (such as LIDO, Rocketpool, etc.), derivative protocols (such as Pendle), and almost all tokens paired in liquidity pools. Financial dependency impact is one of the most difficult categories to assess because it may be easily overlooked; almost any hacker attack involving token theft will directly or indirectly lead to dependencies on other tokens.
A typical example of dependency impact is the collapse of Terra-Luna. A financial attack on stablecoin protocol equity tokens led to the stablecoin decoupling, creating an unrecoverable downward spiral. The collapse of Terra-Luna not only destroyed the $40 billion Luna equity but also the $1 billion unredeemed UST Terra stablecoin, as well as all decentralized finance (DeFi) value associated with Terra-Luna, such as the $1.5 billion equity value of Anchor Protocol and countless other protocols based on Terra. The damage to the Terra ecosystem was almost complete; the value of the Terra ecosystem has fallen by 99% today and is essentially non-existent.
Some colleagues and I are actively researching to understand the real occurrence of dependency impact. As this research is ongoing, we will not draw premature conclusions by incorporating typical dependency impact into our hacker impact rules. Once the research is completed, we will share our findings here and update this article. Preliminarily, dependency impact seems to be far more severe than commonly understood.
Talent and Organizational Impact
Talent and organizational impact typically take two forms: talent loss and operational or program changes.
Talent impact involves the loss of personnel after a hacker attack, which may be due to perceived fault or incompetence, the need for new security talent, or morale decline due to the hacker event. In any case, it is not uncommon for security projects to lose their previous security leaders.
The problem is further complicated by the fact that hacker events make it more difficult to recruit new security leaders, as it indicates weaknesses in the organization.
The second form is unexpected operational or program investments (almost always related to security) made due to the hacker attack. While these investments are positive, they divert valuable attention, slowing progress on core products.
Quantifying the impact here is challenging, but I do have firsthand experience collaborating with multiple projects in a war room, and I will make estimates based on this experience.
In my experience, it is common to lose previous security leaders after a hacker attack. This could be the Chief Information Security Officer (CISO), security engineers, or even engineering leaders serving in security roles. Their departure may be mutually agreed upon, as experiencing a hacker attack under their responsibility is a very discouraging event, or they may be dismissed for some reason. I believe they also tend to be prematurely dismissed because it takes organizations 1.5 to 4 months to recruit effective security replacements. This means a loss of time for the attacked project.
Hacker attacks often leave teams in a state of shock, far beyond the event itself. Organizations invest at least two weeks in damage assessment and control, as well as two to three months in remedial security work (suddenly the most important thing on everyone's to-do list), leading to a lower priority for the core product roadmap.
The numbers in the above example are relatively positive. Talent impact could be more severe, as it affects the project's financial sustainability, as demonstrated by the example of KyberSwap: in November 2023, KyberSwap suffered a hack of $49 million. Understandably, they wanted to compensate users, but to do so, the team had to lay off 50% of its staff to maintain operations and suspend its liquidity protocol plans and KyberAI project. Kyber's offer of a 10% bounty to the hacker ultimately did not help, as reported here.
Calculating these impact factors into a simple impact calculation is not feasible, so we can only summarize these unique impacts and keep them as they are: if you are hacked, expect to spend three months on remedial security work, lose three months of progress on the core product roadmap and goals, lose the current security leadership, and find a replacement in three months. It's like three months of effort disappearing into thin air. This is quite a significant blow to any startup, although not usually fatal.
So, what is the cost of a hacker attack?
After consolidating all the information, we now have the data needed to make estimates. Let's summarize based on quantifying the damage and severity:
The average hacker attack affects approximately $16 million when exploited.
The median hacker attack results in a drastic 52% drop in the base token market capitalization within six months. 79% of attacked projects continue to experience price suppression after six months, and the ultimate duration of this hacker-induced market impact is unknown and may be indefinite.
The median hacker attack does not cause financial or platform dependency impact, but when this impact occurs, it is often absolutely catastrophic, with the risk of assets dependent on the underlying platform being completely destroyed. In severe erroneous reports with dependency impact, the typical potential impact is the sum of the extractable value on the platform!
While more difficult to estimate, the median hacker attack should result in approximately three months of time and energy loss, including remedial security work, lost roadmap time, team attrition and replacement, loss of current security leadership, and extreme anxiety in ensuring you are never hacked again.
We now have all the information needed to create a simple rule to assess the true cost of on-chain hacker attacks. If your protocol is hacked:
The estimated stolen value is approximately $16,000,824.
Expect a 52% drop in your token market capitalization, with this price suppression lasting at least six months and possibly unrecoverable (77.8% of attacked tokens show sustained price suppression after six months).
Expect to lose three months of time and energy in the recovery and rebuilding process.
A real-life example that aligns with the above estimates is the hacker attack on Indexed Finance, which was stolen $16 million on October 14, 2021. The token market capitalization was $11 million at the time, dropping to $3.8 million six months later, showing sustained price suppression after the hacker attack. The team never fully recovered from this event, and Indexed Finance is essentially non-existent by mid-2022. Therefore, our estimation of hacker impact seems to effectively predict the impact of hacker attacks.
If your product is a platform (whether it's an L1/L2 blockchain or a financial primitive protocol) and you are hacked, the typical severity of a hacker attack is absolutely fatal: your protocol and its dependents face the risk of complete annihilation.
This is a very frightening prospect.
Final Thoughts
Being hacked is the starting point of the damage, not the endpoint. Losing millions of dollars due to a hacker attack means even greater losses, stemming from market impact and dependency impact, while also including months of time and energy spent rebuilding your emotionally battered team and operations. It's not fun.
There are no solutions to these problems other than investing in on-chain security and gradually improving the security of our entire industry.
Among these measures, bug bounties are the most effective way and have been proven to prevent hacker attacks and their impact on a large scale. I have quickly reviewed the impact of bug bounties in significantly preventing multi-billion dollar hacker attacks, which you can read more about in my Immunefi Retrospective.
But further, we need more and better code reviews from more excellent hackers, develop better security standards, and develop more advanced automated security technologies. Only by strengthening the entire tech stack can we effectively prevent hacker attacks.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




