Written by: imToken
As the Lunar New Year approaches, it is also a time to bid farewell to the old and welcome the new, marking a point for reflection:
In the past year, did you encounter any pitfalls from Rug Pull projects? Did you buy in and "stand guard" because of the hype from KOLs? Or did you suffer losses from increasingly rampant phishing attacks due to misclicking links or signing contracts?
Objectively speaking, the Spring Festival does not create risks, but it can very likely amplify them—when the frequency of fund flow increases, when attention is distracted by holiday arrangements, and when the trading pace accelerates, any small mistake is more likely to be magnified into a loss.
Therefore, if you are planning to adjust your positions or organize funds around the holidays, you might as well conduct a "pre-holiday safety check" on your wallet. This article will systematically outline several real and high-frequency risk scenarios and what specific actions ordinary users can take.
1. Be cautious of "AI deepfakes" and voice simulation scams
The recent viral SeeDance 2.0 has once again made everyone aware of a fact: in the era of rapidly penetrating AGI, "seeing is believing, hearing is believing" is becoming ineffective.
It can be said that starting from 2025, AI-based video and voice fraud technologies will become significantly mature, including voice cloning, face swapping in videos, real-time expression imitation, and tone simulation, all entering a "industrialized stage" with low barriers and scalable replication.
In fact, with AI, it is now even possible to accurately restore a person's voice, speech speed, pausing habits, and even micro-expressions, which means that during the Spring Festival, this risk is particularly likely to be magnified.
For example, you are on your way home, or in between gatherings with friends and family, when your phone pops up a message from a "friend" in your contacts, sent via Telegram or WeChat, urgently stating that your account is restricted, that red packets are in transit, or requesting you to temporarily advance a small amount of tokens, asking you to transfer funds immediately.
The voice sounds perfectly normal, and the video even features a "real person," so how would you determine its authenticity with your attention distracted by holiday arrangements?
If in previous years, verifying identity via video was almost the most reliable method, today, even if the other party is speaking to you on camera, it is no longer 100% trustworthy.
In this context, merely relying on a glance at the video or listening to a voice message is no longer sufficient for verification. A more prudent approach is to establish a verification mechanism independent of online communication with your core circle (family, partners, long-term collaborators), such as offline codes known only to each other, or details that cannot be inferred through public information.
Additionally, it is essential to reassess a common path-related risk, which involves clicking links forwarded by acquaintances. After all, according to common practice, during the Spring Festival, "on-chain red packets" and "airdrop benefits" can easily become entry points for viral dissemination within the Web3 circle. Many people are not scammed by strangers, but rather trust acquaintances who forwarded them and then clicked on a meticulously disguised authorization page.
Therefore, everyone also needs to remember a simple yet extremely important principle: do not directly click on any links of unknown origin on social platforms, let alone authorize, even if it comes from an "acquaintance."
It is best for all on-chain operations to return to official channels, save URLs, or trustworthy entry points, rather than completing them in chat windows.
2. Conduct a "year-end cleanup" of your wallet
If the first type of risk comes from trust being impersonated by technology, then the second type of risk comes from hidden risk exposures that we have accumulated over time.
It is well-known that authorization is the most fundamental and easily overlooked mechanism in the DeFi world. When you operate in a certain DApp, you are essentially giving the contract a right to manage your tokens, which may be one-off permissions, unlimited allowances, short-term validity, or permissions that remain effective long after you have forgotten about their existence.
In essence, it may not necessarily be an immediate risk point, but it is a continually existent risk exposure. Many users mistakenly believe that as long as their assets are not stored in the contract, there are no security issues. However, during bull market cycles, everyone often tries various new protocols frequently, participates in airdrops, staking, mining, and on-chain interactions, and authorization records accumulate continuously. When the heat subsides, many protocols are no longer in use, yet the permissions remain.
Over time, these excess historical authorizations are like a pile of uncleaned keys; if a protocol you have long forgotten experiences a contract vulnerability, it can easily lead to losses.
And the Spring Festival serves as a natural sorting point, making it very worthwhile to check one's authorization records systematically during the relatively stable time window before the holiday:
Specifically, you can revoke authorizations that are no longer in use, especially unlimited authorizations; apply limited access to large assets you hold daily, rather than keeping all balance permissions open indefinitely; at the same time, separate the management of long-term stored assets from daily operational assets, creating a structure that distinguishes hot wallets from cold wallets.
In the past, many users needed to use external tools (such as revoke.cash and other websites) to complete such checks, but now mainstream Web3 wallets have integrated authorization detection and revocation capabilities, enabling direct viewing and management of historical authorizations within the wallet.
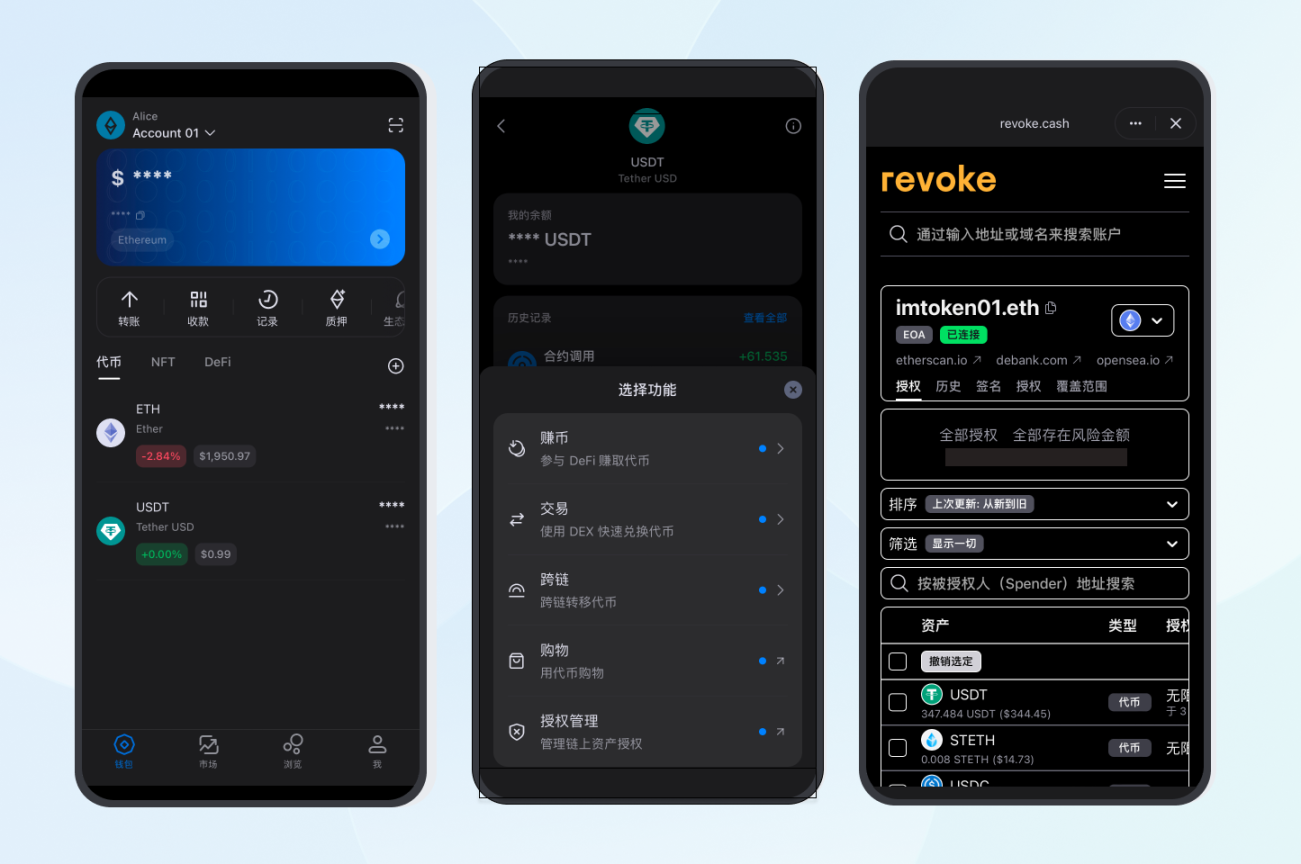
Ultimately, wallet security does not mean never authorizing, but rather adhering to the principle of least privilege—grant only the necessary permissions for the present moment and retract them promptly when they are no longer needed.
3. Travel, socializing, and daily operations: do not become complacent
If the first two types of risks come from technological upgrades and permission accumulation, then the third type of risk arises from environmental changes.
Traveling during the Spring Festival (returning home, traveling, visiting relatives and friends) often means frequent device switches, complex network environments, and intense social scenarios. In such environments, the vulnerabilities of private key management and daily operations are significantly magnified.
Mnemonic phrase management is a typical example. Storing screenshots of mnemonic words in phone albums, cloud drives, or forwarding them to oneself through instant messaging tools is often done out of convenience. Still, in mobile scenarios, this convenience poses the biggest hidden danger.
So remember, mnemonic phrases must be kept physically isolated, avoiding any networked storage methods. The bottom line for private key security is to be offline.
Social scenarios also require boundary awareness. Displaying pages of large assets or discussing specific holding sizes during holiday gatherings is often unintentional but may lay the groundwork for subsequent risks. What is even more concerning is the behavior of guiding users to download disguised wallet applications or plugins under the guise of "sharing experiences" or "teaching guidance."
All wallet downloads and updates should be completed through official channels, not by switching through social chat windows.
In addition, always confirm three things before transferring: network, address, and amount. After all, there have been too many instances of whales suffering significant asset losses due to mistakenly addressing attacks with similar prefix and suffix numbers, and similar phishing attacks have already industrialized in the past six months:
Hackers often generate massive amounts of on-chain addresses with different prefix and suffix numbers as a seed library. Once a certain address engages in a fund transfer with the outside world, they will immediately find an address with the same prefix and suffix in the seed library and then use the contract to execute a related transfer, casting a wide net to wait for catches.
Because some users sometimes directly copy target addresses from transaction records while only checking the first and last few digits, they fall into traps. According to the founder of Slow Mist, Yucan, regarding prefix and suffix phishing attacks, "what hackers play is a fishing net attack, willing fish hook, a probability game."
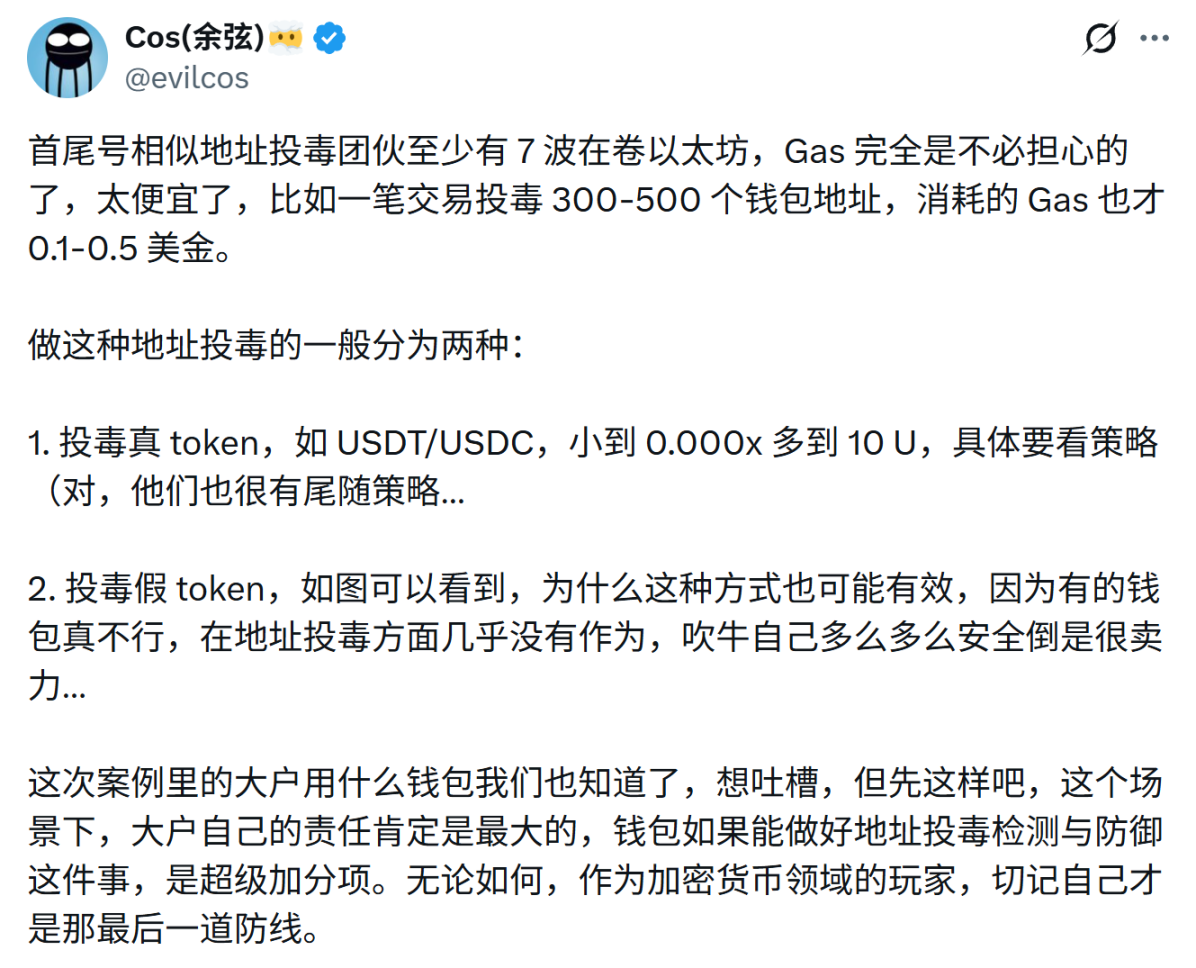
Since gas costs are extremely low, attackers can batch poison hundreds or even thousands of addresses, waiting for a few users to err in copying and pasting. A successful attack yields returns far exceeding the costs.
And these issues do not stem from how complex the technology is, but rather from everyone's daily operational habits:
- Completely verify address characters, instead of just checking the beginning and end;
- Do not copy transfer addresses directly from transaction history without verification;
- When transferring to a new address for the first time, conduct a small test transfer first;
- Prioritize using address whitelist functions to manage frequently used addresses;
In the currently decentralized system dominated by EOA accounts, users are always their own primary responsible party and the last line of defense.
In conclusion
Many people always feel that the on-chain world is too dangerous and not user-friendly for ordinary users.
To be realistic, Web3 indeed struggles to provide a zero-risk world, but it can transform into an environment where risks are manageable.
For example, the Spring Festival is a moment of slowed rhythm and is the best time window for reorganizing risk structures in the year. Rather than rushing to operate during the holiday, it is better to complete safety checks in advance; instead of remedying after the fact, it is wiser to optimize permissions and habits beforehand.
Wishing everyone a safe and smooth Spring Festival, and wishing everyone's on-chain assets to remain stable and worry-free in the new year.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




