Quantum computers are quietly rising, and once mature, they will launch a fatal attack on Bitcoin and the entire blockchain ecosystem.
Written by: On-Chain Revelation
Introduction: Bitcoin's "Dark Forest" Crisis
In the world of blockchain, each node is like a star in the universe, independent yet interconnected, collectively building a decentralized financial world. Bitcoin, as the pioneer of this network, relies on powerful cryptographic algorithms to protect its security. However, this security system is not unbreakable. A technology from the future—quantum computers—is quietly emerging. It is like the Trisolaran fleet in "The Three-Body Problem," possessing the ability of "dimensionality reduction strike," and once mature, it will launch a fatal attack on Bitcoin and the entire blockchain ecosystem.
So, if quantum computers are going to crack Bitcoin in the near future, what should we do? Is there still a possibility of counterattack in this "Dark Forest" survival battle on-chain?

Chapter 1: Bitcoin Will Face a "Dimensionality Reduction Strike" from Quantum
The most terrifying weapon in the "Three-Body Problem" novel is not the laser cannon, but the "dimensionality reduction strike"—a higher-dimensional civilization does not fight you in the same dimension but directly compresses three-dimensional space into two dimensions. All your defenses, all your fortresses, instantly collapse into a piece of paper. The mathematical "impossibility" that Bitcoin relies on becomes "very easy" in the face of quantum computing.

IBM Quantum System One located in Erlangen, Germany. Source: Wikipedia
1.1 Bitcoin's "Technical Barrier" vs. Quantum Computer's "Droplet" Weapon
Bitcoin: 1980s Cryptographic Standard
The core security of Bitcoin relies on the ECDSA algorithm, a cryptographic standard first proposed in 1985. In this system, each user has a pair of keys: the private key is the user's "thought," known only to themselves; the public key is the public "identification," used to verify the legitimacy of transactions.
It is easy to generate a public key from a private key through a mathematical one-way function, but deriving a private key from a public key is nearly impossible under traditional computing power. Because the Bitcoin network uses a 256-bit key, even the most powerful traditional computers would require a time longer than the age of the universe to brute-force crack it. It is this mathematical "impossibility" that protects the security of the Bitcoin network.
Quantum Computers: The "Droplet" New Technology for Cracking Encryption
Quantum computers are a completely different type of computing device from traditional computers, utilizing properties such as superposition and entanglement in quantum physics to perform calculations, theoretically offering exponential growth in computational power for certain problems.
The emergence of quantum computers changes the rules of the game—theoretically, through Shor's algorithm, a sufficiently powerful quantum computer could derive a private key directly from a public key in a reasonable time. This is like the Trisolaran "droplet" probe, capable of easily penetrating humanity's most robust defenses. Its attack method has the following characteristics:
Concealment: Once the attacker obtains the private key, they can legally sign forged transactions, and the entire network will believe this is a normal operation by the asset owner. Just like the monitoring of the sophon in "The Three-Body Problem," it is completely silent.
Selectivity: The easiest targets are wallets whose public keys have already been exposed, especially addresses used in early Bitcoin transactions. Kapil Dhiman, CEO of Quranium, warned: "Satoshi's coins will become easy targets for attack. If these coins are moved, people's confidence in Bitcoin will completely collapse before the system crashes."
"Steal First, Decrypt Later": Attackers can copy the public data on the blockchain now and wait until quantum computing technology matures to decrypt it. Even if the existing network upgrades to switch to more secure algorithms, old addresses, long-dormant wallets, and some smart contract models may become vulnerable.
1.2 Trust Crisis and Timeline: Satoshi's Over One Million Bitcoins
The UK's National Cyber Security Centre recommends that organizations determine their quantum-safe cryptography upgrade path by 2028 and complete the migration by around 2035. For blockchain systems designed to last decades, preparations must begin now.
Some early estimates suggest that the point at which quantum computers will truly take effect may be around 2030. This means that the blockchain industry has little time left.
In this scenario of quantum computer attacks, the blockchain itself will continue to operate normally—blocks will continue to be mined, and the ledger will remain intact, but the ownership of assets will have quietly changed. This situation is more terrifying than a technical failure because it will destroy people's trust in the entire system.
Once Satoshi's over one million Bitcoins start to move, the market will panic. Even if the blockchain remains secure technically, prices could plummet, triggering a chain reaction that affects traditional financial markets that have already heavily adopted cryptocurrencies.
If Bitcoin cannot solve the quantum mechanics problem within the next year, gold will forever outperform Bitcoin. This was stated by the founder of the quantitative Bitcoin and digital asset fund Carpriole in a post on X last month.
Part Two: Layer 1's "Wallfacer" Plan
There is a brilliant setting in "The Three-Body Problem": when humanity discovers that alien civilizations are monitoring everything on Earth through "sophon," all defense plans will be prematurely exposed. What to do? The United Nations proposed the "Wallfacer Plan"—selecting a few "Wallfacers" and granting them the power to mobilize global resources to prepare for the impending invasion.

In the face of the future quantum computing dimensionality reduction strike, the blockchain world also needs "Wallfacers." The U.S. National Institute of Standards and Technology (NIST) plays this role. From 2022 to 2024, NIST selected and initiated the standardization of the first batch of post-quantum cryptographic algorithms, which, like the interstellar weapons developed in "The Three-Body Problem," come with costs such as larger signature sizes and increased complexity of use, but indeed provide a realistic and feasible solution for blockchain to resist quantum attacks.
Facing the same threat, different L1 blockchains have chosen different survival strategies.
2.1 Strategy One: Multi-Path Exploration (Wallfacer Experiment)
The Wallfacers in "The Three-Body Problem" can experiment in multiple directions simultaneously without needing to explain to anyone, as no one knows which path will succeed. Some mainstream blockchain projects have adopted a similar strategy: simultaneously trying multiple technical solutions to find the optimal solution in practice.
Ethereum: Comprehensive Technical Exploration
The Ethereum research team is developing a post-quantum migration task list, including new transaction types, rollup experiments, and zero-knowledge-based wrappers. They are not betting on a single solution but are advancing in multiple directions simultaneously to see which path is the most feasible and efficient.

Source: pqcee.github.io
Solana: Optional Security Sanctuary
Solana has launched an optional quantum-resistant vault, specifically, the "Solana Winternitz Vault" solution implements a complex hash-based signature system that generates new keys with each transaction.
Source: @deanmlittle
Sui: Gradual Upgrade Path
The Sui research team has released a dedicated quantum security upgrade path, proposing an upgrade path that avoids destructive hard forks in collaboration with academic partners. This is a gradual strategy that minimizes the impact on existing users as much as possible.
Source: @kostascrypto
The core of this strategy is "choice": not forcing everyone to upgrade, but providing multiple options for the market and users to decide for themselves.
2.2 Strategy Two: Transforming the Old World (Shelter Plan)
The "Shelter Plan" in "The Three-Body Problem" is not about tearing down and rebuilding but about constructing shelters behind giant planets—the old world continues to operate while new defense systems are gradually established. Some blockchain projects have adopted a similar strategy: adding quantum security layers to existing systems, allowing new and old systems to coexist, and enabling users to migrate gradually.
Algorand: Adding Defense at Key Nodes
Algorand is a typical example of post-quantum technology being applied in a production environment. In 2022, it introduced "State Proofs," using the NIST-standardized lattice-based signature scheme FALCON. These proofs verify the state of the Algorand ledger every few hundred blocks, providing quantum-safe verification services for other chains. Recently, Algorand also demonstrated complete post-quantum transactions on the mainnet, showcasing logic signatures based on Falcon.

Source: Algorand
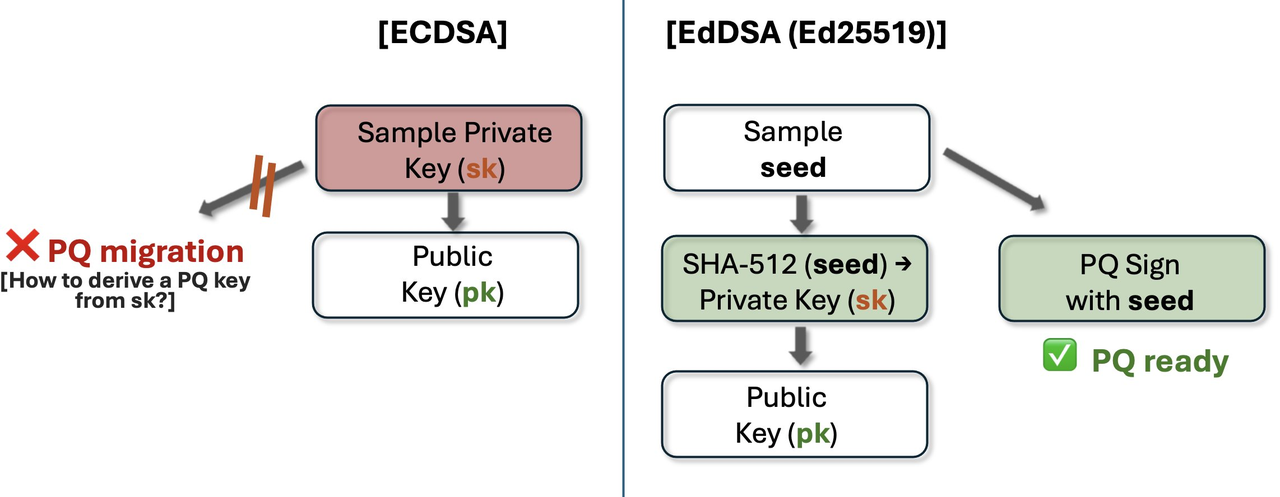
Cardano: Long-Term Planning with Dual Tracks
Although Cardano currently still uses Ed25519 signatures, its team views quantum preparedness as a long-term differentiating advantage. Founder Charles Hoskinson outlined a plan that combines independent proof chains, Mithril certificates, and NIST-compliant post-quantum signatures.
Source: @IOHK_Charles
2.3 Strategy Three: Building a New World (Star Ring Cities)
In the later stages of "The Three-Body Problem," humanity no longer attempts to defend Earth but instead builds a completely new civilization in space—free from historical burdens and compromises, designed from the first brick for the new environment. Some new blockchain projects have chosen this path: building completely quantum-resistant systems from scratch.
Naoris Protocol: Mentioned in a proposal submitted to the U.S. Securities and Exchange Commission, focusing on post-quantum infrastructure.
Quranium: Utilizes the NIST-approved stateless hash-based digital signature algorithm (SPHINCS+), designed from the protocol level for the quantum era.
Quantum Resistant Ledger (QRL): Launched in 2018, built on hash-based XMSS signatures, one of the earliest quantum-resistant blockchains.
These projects do not need to consider backward compatibility, do not need to migrate old users, and do not need to struggle to balance performance and security. They directly establish colonies in the "new universe," waiting for the arrival of the quantum era.
Part Three: The Dark Forest Law—Everyone Must Make a Choice

3.1 Individual User Response Strategies
Avoid Long-Term Inactivity: Regularly check and update wallets to avoid becoming a "preferred" target for quantum attacks.
Prepare for Key Upgrades: In the coming years, new account types, hybrid signature options, and wallet prompts are expected to encourage users to upgrade keys for high-value assets.
Focus on Cryptographic Agility: Choose ecosystems that can add and rotate cryptographic primitives without performing destructive hard forks.
3.2 Investor Due Diligence
Roadmap Transparency: Does the project have a clearly documented post-quantum roadmap?
Practical Implementation: Are there prototypes or actual functionalities, or is it just marketing hype?
Timeline Planning: Has the project already begun preparing for quantum threats in the 2030s?
Conclusion: Granting Time for On-Chain Evolution
In "The Three-Body Problem," the "Sword Holder" can decide the fate of humanity alone, but there is no such role in the blockchain world. Each project is exploring its own path; whose solution will work? No one knows. But this is the essence of decentralized resilience—no single point of failure and no single answer.
The threat of quantum computing is not the end but the beginning. Blockchain may not be able to preserve all of the past, but as long as the core principles remain—decentralization, censorship resistance, and trustlessness—civilization will continue.
Grant civilization to time, grant on-chain evolution to time—only prepared civilizations can enter the next dimension.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




