In the face of powerful national-level adversaries, no technological means can guarantee absolute security.
Introduction: Ghost Code
In December 2020, a staggering 127,000 bitcoins (worth approximately $3.5 billion at the time) mysteriously disappeared from a Chinese mining pool address known as "LuBian." The pool owner desperately pleaded on the blockchain for the "hacker" to return the assets, promising a reward, staging a public digital asset recovery drama.
After that, this vast sum lay dormant for several years. Until October 14, 2025, when an announcement from the U.S. Department of Justice (DOJ) shocked the world: they had successfully seized this bitcoin, which had now skyrocketed in value to an astonishing $15 billion.
However, this was not a routine hacking or capture operation. The reason U.S. law enforcement was able to obtain the private key to this enormous wealth was that they uncovered a ridiculous yet fatal secret—the fortress supporting this criminal empire's treasury was not an impregnable cryptographic stronghold, but a small lie about "random numbers."
This story not only reveals the inside story of the largest cryptocurrency seizure in history but also sounds the alarm for all of us regarding digital security.
Part One: The Illusion of Randomness—Analysis of the "Milk Sad" Vulnerability
The Cornerstone of Cryptographic Security: Private Keys and Randomness
To understand this $15 billion vulnerability, we first need to grasp the core of bitcoin security: private keys. It is not just a string of ordinary passwords but an extremely large 256-bit number. The total number of possibilities (2^256) is vastly greater than the total number of atoms in the known universe (approximately 10^80). Therefore, as long as your private key is truly randomly generated, it is physically impossible to crack it through brute force guessing.
For user convenience, modern wallets typically use a "seed phrase" (usually 12 to 24 words) to generate all private keys. This process relies on an algorithm known as pseudo-random number generator (PRNG). The quality of this generator directly determines the life and death of your digital assets. A PRNG used for cryptography must be "cryptographically secure" (CSPRNG) to ensure its output cannot be predicted.
Using a weak, non-cryptographically secure PRNG to generate private keys is like using a cardboard wall to protect the world's strongest bank vault door.
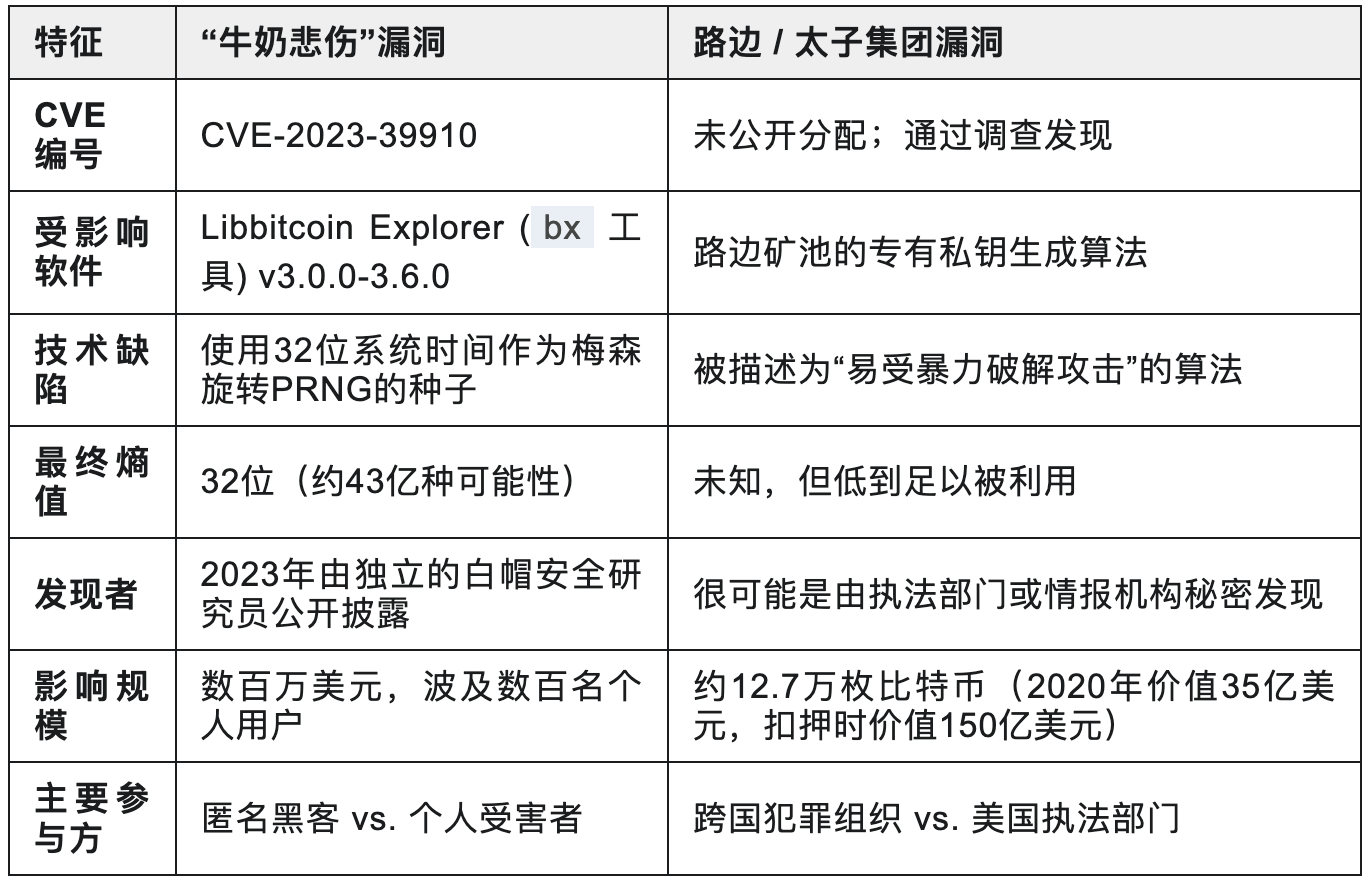
The "Milk Sad" Vulnerability (CVE-2023-39910): A 32-bit Catastrophe
The "Milk Sad" vulnerability is a textbook case. This vulnerability exists in a command-line tool called Libbitcoin Explorer, which many developers and advanced users have used to generate wallets.
The technical error is shockingly simple: the tool used a PRNG algorithm called "Mersenne Twister" to generate random seeds. This algorithm is not suitable for cryptographic scenarios, and more critically, the developers only used the system's 32-bit timestamp as its initialization "fuel."
This means that no matter how complex the private key generated, the true source of "randomness" behind it is only 32 bits. How large is a 32-bit number space? Just 2^32, approximately 4.3 billion. For modern computers, traversing these 4.3 billion possibilities would take at most a day. A problem that should be universally unbreakable instantly turned into a guaranteed lottery win.
The name of this vulnerability comes from the fact that when the system timestamp is "0.0," the generated mnemonic phrase happens to start with "milk sad," becoming its unique "fingerprint." On July 12, 2023, attackers exploited this vulnerability to launch a large-scale coordinated theft, stealing millions of dollars in assets from unsuspecting user wallets.
The "Milk Sad" incident clearly demonstrates: while cryptographic algorithms themselves may be rock-solid, a tiny flaw in their software implementation can be enough to collapse the entire security system.
Part Two: A Criminal Empire Built on Vulnerabilities—LuBian Mining Pool and Prince Group
Ghost Mining Pools and a Carefully Orchestrated "Theft"
As the "Milk Sad" vulnerability was publicly analyzed in the tech community, a much larger and darker story was quietly unfolding. In December 2020, the aforementioned LuBian mining pool, which once controlled nearly 6% of the global bitcoin hash rate, had approximately 127,000 bitcoins "stolen." In the aftermath, the mining pool operators left hundreds of messages on the blockchain, pleading for the "hacker" to return the funds and promising a reward.
By February 2021, the LuBian mining pool had vanished without a trace.
Years later, research by blockchain analysis firms Arkham Intelligence and Elliptic indicated that this "theft" was likely due to the LuBian mining pool using a flawed proprietary algorithm to generate private keys, making it susceptible to brute force attacks—similar to the principle behind the "Milk Sad" vulnerability.
The Mastermind: Chen Zhi and the Prince Group
On October 14, 2025, the DOJ's indictment revealed the ultimate truth. The mastermind behind it all was a man named Chen Zhi (also known as "Vincent"), the chairman of a multinational conglomerate called the "Prince Group."
On the surface, the Prince Group operates in over 30 countries in sectors like real estate and finance, appearing glamorous. However, it is actually a large and violent transnational criminal organization (TCO) recognized by the U.S. Treasury. Its core business is industrial-scale fraud, particularly scams known as "pig butchering" (Sha Zhu Pan).
The indictment painted a hellish picture: the Prince Group has multiple forced labor camps in places like Cambodia, surrounded by high walls and electric fences. Thousands of trafficked workers are forced to engage in "pig butchering" scams, working long hours each day, and if they do not comply or meet performance standards, they face beatings and abuse. At the peak of this criminal network, illegal profits could reach $30 million a day.
The Truth Revealed: The Treasury of the Criminal Empire
The DOJ's civil forfeiture complaint ultimately connected all the dots: the 127,000 bitcoins "stolen" from the LuBian mining pool in 2020 were indeed the illegal proceeds accumulated by the Prince Group through fraud and human trafficking, and Chen Zhi had always controlled these assets.
The LuBian mining pool itself was one of the "legitimate" fronts used by the Prince Group for money laundering. Through mining, they could continuously generate "clean" bitcoins with no transaction history, mixing them with the "dirty" money obtained from victims to obscure their bloody origins. Chen Zhi even boasted to his accomplices that his mining business was highly profitable, "because there are no costs"—essentially admitting that all his capital came from the sweat and blood of victims.
Thus, the truth behind the 2020 "theft" incident became clear: this was not a hacker attack at all, but a carefully orchestrated scheme of the thief shouting to catch the thief. Leaving messages on the blockchain was meant to create a false record of theft, to "clean" the source of this massive loot and sever its ties to heinous crimes like human trafficking and fraud.
Sadly, the vast treasury used by this enormous criminal empire to hide its wealth was also built on a weak random number generation flaw similar to "Milk Sad."
Part Three: The Digital Sky Net—Historic Actions by Law Enforcement
Tracking on the Immutable Ledger
Although cryptocurrencies are often misunderstood as anonymous havens for crime, their public and immutable characteristics also provide investigators with powerful tracking tools. The U.S. Department of Justice, the Federal Bureau of Investigation (FBI), the Secret Service, and the Treasury Department, along with international partners like the UK, launched an unprecedented multinational digital manhunt.
Using advanced blockchain forensic tools, investigators were able to sift through vast amounts of transaction records to reconstruct the Prince Group's complex money laundering network. From June to July 2024, the long-dormant bitcoins suddenly began to transfer en masse. Subsequent analysis revealed that this was not the criminals moving assets, but rather U.S. authorities transferring the funds to government-controlled wallets after gaining control of the private keys.
The Ultimate Puzzle: How Did the U.S. Government Obtain the Private Keys?
The most intriguing and unresolved question in the entire case is: how did the U.S. government obtain the private keys to the $15 billion worth of bitcoin while the main perpetrator, Chen Zhi, remained at large?
This is starkly different from previous cases. For example, in the Silk Road and Bitfinex hacking cases, the recovery of funds heavily relied on the arrest of suspects to seize the physical devices storing their private keys.
Currently, several possible scenarios are speculated:
Human Intelligence: Investigators may have turned high-level personnel within the Prince Group who had access to the private keys.
Physical Seizure: Law enforcement may have secretly seized hardware wallets, computers, or papers containing the private keys or mnemonic phrases through raids without arresting Chen Zhi.
Direct Technical Exploitation: This is the boldest and most intriguing speculation. U.S. intelligence agencies (like the NSA) may have independently discovered the algorithmic vulnerability in the LuBian mining pool's private key generation. With their powerful computational resources, they may have directly attacked this vulnerability, reproducing the private keys in a "black eat black" style remote seizure.
Regardless of the specific method, this case marks a significant shift in law enforcement strategies: from "arrest first, find the money later" to remotely and proactively stripping criminal organizations of their financial capabilities. This undoubtedly fundamentally changes the risk landscape of cryptocurrency crime.
Conclusion: Lessons from the Abyss
From "Milk Sad" to the downfall of the Prince Group, two seemingly unrelated stories ultimately point to the same origin: neglect of random number generation. Whether it is ordinary users who lost their life savings or crime lords whose billion-dollar empires collapsed, they all fell victim to the failure of "entropy." This proves that the strength of the cryptographic security chain depends on its weakest link.
This unprecedented case has also completely shattered the myth of bitcoin's "non-seizability." It sends a clear message to criminal organizations worldwide: in the face of powerful national-level adversaries, no technological means can guarantee absolute security.
These painful lessons provide clear insights for every participant in the digital economy:
For ordinary users: Always use reputable, audited open-source wallet software and hardware. Stay away from obscure or unknown technological tools.
For developers: Bear a tremendous responsibility. In any security-related application, always use rigorously validated, cryptographically secure random number generators.
For the public: Be vigilant against scams like "pig butchering," which involve both emotional and financial fraud. Any investment promising unrealistic returns may hide a bottomless abyss.
Ultimately, the ghosts in the machine are not abstract technical concepts but real threats. Whether personal wealth or criminal empires, their establishment or destruction may hinge on the quality of a small random number.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



