Overview of Cross-Chain Bridge Theft Incidents
From 2022 to 2024, the cross-chain bridge sector experienced several major security incidents that shocked the industry. The most notable include: the Ronin Bridge attack in March 2022 with a loss of $625 million, the Binance Bridge attack in October of the same year with a loss of $570 million, the Wormhole Bridge attack in February with a loss of $320 million, the Nomad Bridge attack in August with a loss of $190 million, the Harmony Horizon Bridge attack in June with a loss of $100 million, and the Orbit Chain attack in January 2024 with a loss of $81.5 million.
These figures clearly illustrate a harsh reality: 2022 became the "darkest hour" for cross-chain bridge security, with losses exceeding $1.8 billion in a single year. These attacks not only resulted in massive economic losses but, more importantly, exposed fundamental flaws in the security architecture design of current cross-chain infrastructure.
| Time | Bridge Protocol Name | Loss Amount (Million USD) | Affected Blockchain | Attack Type | Fund Recovery Status | |---------------|----------------------|---------------------------|---------------------------|----------------------------------|----------------------| | March 2022 | Ronin Bridge | 625 | Ethereum ↔ Ronin | Private Key Theft (Social Engineering) | Partially Recovered | | October 2022 | Binance Bridge | 570 | BSC ↔ Beacon Chain | Merkle Proof Forgery | Mostly Frozen | | February 2022 | Wormhole Bridge | 320 | Ethereum ↔ Solana | Smart Contract Vulnerability | Jump Trading Compensated | | August 2022 | Nomad Bridge | 190 | Ethereum ↔ Moonbeam | Trust Root Configuration Error | Small Amount Returned | | June 2022 | Harmony Horizon | 100 | Ethereum ↔ Harmony | Multi-Signature Private Key Leak | Not Recovered | | January 2024 | Orbit Chain | 82 | Multi-Chain Support | Private Key Theft | Partially Frozen |
Ronin Bridge: The Perfect Crime of Social Engineering
On March 23, 2022, the Ronin Bridge, which supports the world's most popular blockchain game Axie Infinity, suffered the most severe cross-chain bridge attack in crypto history. The attackers successfully stole 173,600 ETH and 25.5 million USDC, totaling over $625 million, through a meticulously planned social engineering attack. This attack not only set a historical record for a single loss but also demonstrated the vulnerability of traditional multi-signature mechanisms when faced with organized and premeditated attacks.
Precision Strike of Advanced Phishing
According to the official post-incident report from Sky Mavis, the origin of the attack can be traced back to a sustained advanced phishing attack on Sky Mavis employees. The attackers targeted Sky Mavis employees through various social channels and ultimately succeeded in breaching the system of one employee. Sky Mavis explicitly stated in the official report: "Sky Mavis employees were continuously subjected to advanced phishing attacks across various social channels, and one employee was compromised. That employee is no longer with Sky Mavis."
The attackers successfully infiltrated Sky Mavis's entire IT infrastructure through this initial access point and gained access to the validation nodes. This method of attack showcased the professional level and persistent threat capabilities of state-level hacker organizations.
The Forgotten Temporary Permission: A Fatal Management Oversight
The key to the attack's success lay in a forgotten temporary authorization. Sky Mavis detailed the complete timeline of this fatal oversight in the official report:
November 2021: Due to a surge in Axie Infinity user load, Sky Mavis requested Axie DAO's assistance in distributing free transactions. As a result, Axie DAO whitelisted Sky Mavis, allowing it to sign various transactions on behalf of Axie DAO.
December 2021: Although this special arrangement officially ceased in December, the critical whitelisted access was never revoked.
March 23, 2022: The attackers discovered and exploited this forgotten permission. At that time, Sky Mavis controlled four validation nodes, which alone were insufficient to forge withdrawal transactions. However, the attackers abused the unretracted whitelisted permissions through Sky Mavis's free RPC nodes to obtain signatures from Axie DAO validation nodes, thus assembling the required five validation nodes.
Sky Mavis acknowledged: "This traces back to November 2021, when Sky Mavis requested Axie DAO's help in distributing free transactions… This stopped in December 2021, but the whitelisted access was not revoked. Once the attackers gained access to the Sky Mavis system, they were able to obtain signatures from Axie DAO validators using the free RPC."
Disastrous Consequences of Monitoring Blind Spots
Shockingly, the largest cross-chain bridge attack in history went completely undetected for six days. Sky Mavis admitted to serious flaws in its monitoring system in the official report: "We did not have an appropriate tracking system to monitor large outflows from the bridge, which is why the vulnerability was not immediately detected."
It wasn't until March 29, 2022, when a user reported being unable to withdraw 5,000 ETH from the Ronin bridge, that the Sky Mavis team realized they had been attacked. The attackers exploited this six-day window to complete the withdrawal of 173,600 ETH and 25.5M USDC through two transactions.
Comprehensive Upgrade of Subsequent Security Measures
Following the incident, Sky Mavis implemented a comprehensive security upgrade plan:
Validation Node Expansion: Increase from 9 validation nodes to 11, with a goal of reaching 21 within three months and a long-term goal of over 100.
Zero Trust Architecture: Establish a fully anti-fragile, zero-trust organizational framework.
Professional Security Collaboration: Partner with top security firms such as CrowdStrike and Polaris Infosec.
High Bounty for Vulnerabilities: Offer a bounty program of up to $1 million for vulnerabilities.
Strict Internal Procedures: Implement stricter internal security procedures and employee training.
This incident perfectly illustrated the vulnerability of traditional multi-signature mechanisms when faced with meticulously planned social engineering attacks. Over-centralized control of validation nodes, improper permission management leading to unretracted temporary authorizations, lack of real-time anomaly transaction monitoring mechanisms, and insufficient employee security awareness training were all key factors that enabled the attackers' success.
- Wormhole Bridge: The Fatal Consequences of Abandoned Code
On February 2, 2022, at 5:58 PM UTC, the popular cross-chain bridge Wormhole, connecting Ethereum and Solana, suffered a severe blow when attackers exploited an abandoned but unremoved function in the smart contract, successfully bypassing the signature verification mechanism and minting 120,000 uncollateralized wETH tokens, valued at approximately $320 million. This attack not only showcased the severe consequences of code management oversights but also revealed the significant challenges complex cross-chain protocols face in security maintenance.
Professional Preparation Before the Attack
According to on-chain data analysis, the attackers conducted meticulous preparations before executing the attack, demonstrating a high level of professionalism:
Funding Preparation: The attackers obtained 0.94 ETH from the privacy mixer Tornado Cash as the transaction fee needed to execute the attack, while transferring an additional 0.1 ETH to an address associated with a well-known international cryptocurrency exchange, indicating a complete funding transfer and money laundering plan.
Timing of Vulnerability Discovery: Ironically, on the day of the attack, the Wormhole development team pushed a code update to GitHub that fixed a known security vulnerability. However, this patch was only updated on GitHub and was not promptly deployed to the production environment, providing the attackers with a critical window of opportunity.
Six-Step Precision Attack Process
The attackers executed a highly technical six-step attack process:
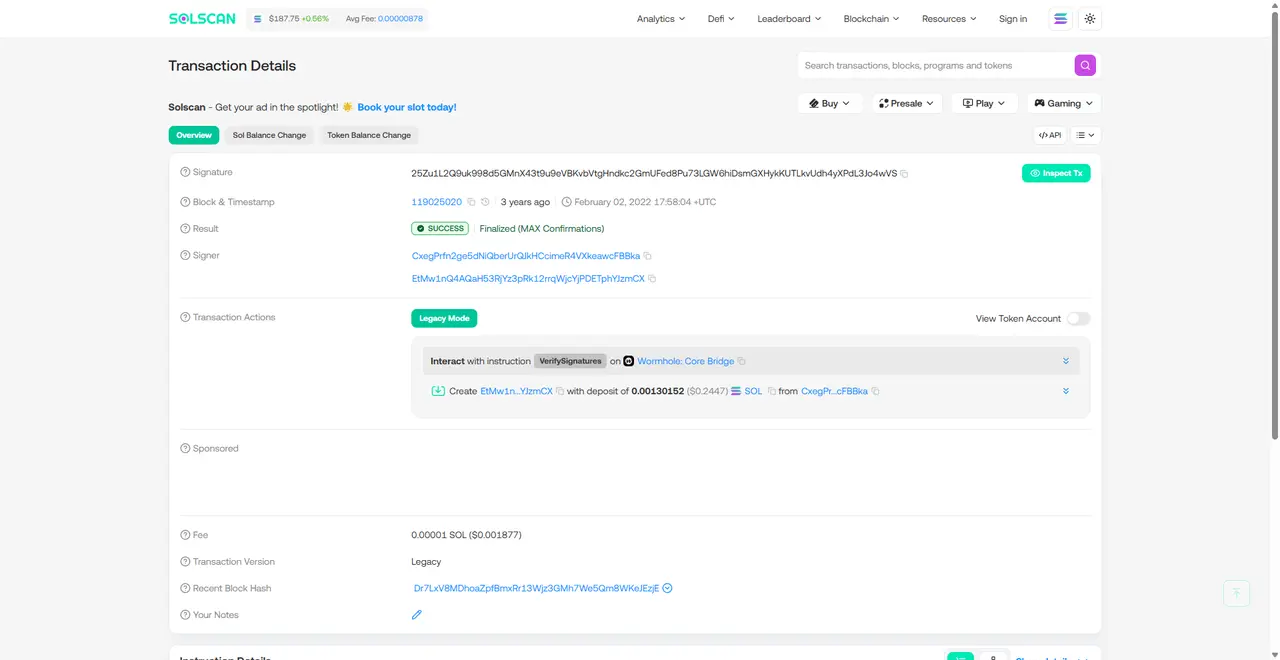
Step 1: Forging Signature Verification Function The attackers first called the verify_signatures function, which is the core function of the verification process responsible for ensuring the authenticity of transactions. Within this function, the attackers introduced a malicious "Sysvar account" to deceive the system. Specific transaction: https://solscan.io/tx/25Zu1L2Q9uk998d5GMnX43t9u9eVBKvbVtgHndkc2GmUFed8Pu73LGW6hiDsmGXHykKUTLkvUdh4yXPdL3Jo4wVS
Step 2: Deploying Forged Verification Function The attackers used the injected malicious "sysvar account" to run the forged verify_signatures function, aiming to subvert the verification process and gain unauthorized access.
Step 3: Exploiting Abandoned Function Vulnerability The key vulnerability appeared in the abandoned load_current_index function. This function failed to verify whether the injected "Sysvar account" corresponded to a real "system sysvar." Since the data retrieved from "sysvar" (L92) was under the control of the attackers, they were able to manipulate the verification process without restriction.
Step 4: Creating Malicious Message After compromising the verification process, the attackers called the post_vaa function, using the "verified" signature obtained in previous steps to create a malicious message account, specifying the minting of 120,000 wETH. Specific transaction: https://solscan.io/tx/2SohoVoPDSdzgsGCgKQPByKQkLAXHrYmvtE7EEqwKi3qUBTGDDJ7DcfYS7YJC2f8xwKVVa6SFUpH5MZ5xcyn1BCK
Step 5: Executing Malicious Minting The attackers called the complete_wrapped function, processing the data contained in the malicious message account created in the post_vaa step, ultimately successfully minting 120,000 wETH tokens. Specific transaction: https://solscan.io/tx/2zCz2GgSoSS68eNJENWrYB48dMM1zmH8SZkgYneVDv2G4gRsVfwu5rNXtK5BKFxn7fSqX9BvrBc1rdPAeBEcD6Es
Step 6: Complex Fund Diversion After minting wETH, the attackers immediately began complex fund transfer operations:
16,879.39 ETH converted to 269,356.66 SOL
1,866 ETH exchanged for 4.9 million USDC
7,504 ETH exchanged for 18 million USDC
18,044,852.11 USDC converted to 122,049 SOL
Unprecedented Rescue by Jump Trading
Within 24 hours of the attack being discovered, Jump Trading (the parent company of Wormhole) made a stunning decision: to inject 120,000 ETH into the Wormhole protocol to cover all losses, ensuring the safety of all wETH holders' funds. Jump Trading stated: "We believe in a multi-chain future, and Wormhole is important infrastructure. That’s why we replaced 120,000 ETH to make community members whole and support Wormhole's continued development."
While this move saved user funds, it also exposed the serious reliance of current cross-chain bridge infrastructure on centralized entities. The ultimate solution still depended on the capital injection from centralized entities, which starkly contrasts with the concept of decentralization.
Root Causes of the Vulnerability
The core issues exposed by this attack include:
Code Management Oversight: Continued use of the known vulnerable abandoned function
load_current_indexInsufficient Input Validation: Failure to verify the authenticity of key account addresses
Deployment Process Flaws: Security patches not promptly deployed to the production environment
Architectural Dependency Risks: Over-reliance on centralized entities for final guarantees
The attackers' success hinged on exploiting functions in the Solana SDK that had been marked as "deprecated." These functions lacked verification of the authenticity of account addresses when handling sysvar:instructions accounts, allowing attackers to create fake Sysvar accounts and bypass the entire verification system.
- Harmony Horizon Bridge: Total Collapse of Multi-Signature Keys
On June 23, 2022, the Harmony Horizon Bridge, which connects Ethereum, BSC, and Harmony, suffered a devastating attack resulting in a loss of $100 million. This attack was later confirmed by the FBI to be carried out by North Korea's Lazarus Group (APT38), the same organization responsible for the earlier Ronin Bridge attack. The success of the attack was largely attributed to fundamental flaws in the multi-signature architecture design.
The Harmony Horizon Bridge employed a seemingly secure but fundamentally flawed multi-signature design: 5 validation nodes, requiring only 2 to agree to execute a transaction. This 2-of-5 design significantly lowered the attack threshold, allowing attackers to fully control bridged assets by controlling just 2 validation nodes. The attack officially began at 11:06 UTC on June 23, 2022. According to subsequent investigations by Harmony, the attackers obtained the private keys of 2 validation nodes through unknown means.
In a post-incident statement, Harmony revealed: "The private keys were stored encrypted, double-encrypted via a passphrase and key management service, with no single machine able to access multiple plaintext keys. The attackers were able to access and decrypt several keys, including those used to sign unauthorized transactions." Despite seemingly robust encryption protection measures, the attackers successfully cracked the critical private key information.
Using the 2 controlled private keys, the attackers executed 14 cross-chain withdrawal transactions within hours, spanning Ethereum and Binance Smart Chain. The stolen assets included approximately 85,000 wETH, 41 million USDC, 11 million USDT, 6 million DAI, 6.4 million BUSD, and other tokens worth millions of dollars, such as SUSHI and AAVE. The attackers first concentrated the stolen assets at address 0x0d043128146654c7683fbf30ac98d7b2285ded00, then began a complex money laundering process.
The attackers immediately exchanged various tokens for ETH through decentralized exchanges, then dispersed approximately 18,000 ETH to 14 different addresses, ultimately washing about 85,700 ETH in batches through Tornado Cash. In January 2023, the FBI officially confirmed that this attack was carried out by North Korea's Lazarus Group, further validating that state-level hacker organizations have targeted cross-chain bridges as significant attack vectors.
The core issue exposed by this attack was the excessively low threshold for multi-signature settings. The 2-of-5 setup allowed attackers to fully control bridged assets by controlling only 40% of the validation nodes, a threshold that is relatively easy for organized attackers to achieve. Additionally, despite employing multiple encryption protections, key management was still compromised by the attackers, indicating fundamental flaws in the current private key protection mechanisms. The 14 abnormal transactions did not trigger any automatic alerts, further exposing serious deficiencies in the monitoring mechanisms.
- Binance Bridge: Fatal Flaw in Merkle Proof
On October 6, 2022, the BSC Token Hub cross-chain bridge under the world's largest cryptocurrency exchange, Binance, suffered a highly technical attack, with attackers successfully stealing 2 million BNB tokens valued at approximately $570 million. The technical complexity of this attack was extremely high, involving deep exploitation of the Merkle proof verification system, showcasing the attackers' profound understanding of underlying cryptographic principles.
The BSC Bridge connects the BNB Beacon Chain (BEP2) and BNB Smart Chain (BEP20), utilizing a Merkle proof verification system based on the Cosmos IAVL (Immutable AVL) tree. The attackers first registered as a relayer on the BSC Token Hub, staking 100 BNB as collateral, which allowed their relayer requests to be accepted by the BSC network, laying the groundwork for the subsequent attack.
The core of the attack lay in a subtle flaw in the IAVL library's handling of Merkle proofs. In the IAVL tree, the hash calculation of nodes depends on the ordering of child nodes, typically following specific rules. However, in the implementation of the Binance Bridge, when a node has both left and right child node properties, the system fails to correctly handle this edge case. The attackers exploited this subtle implementation flaw to successfully forge the Merkle proof for block 110217401.
Using the forged proof, the attackers withdrew 1 million BNB in two transactions, totaling 2 million BNB (approximately $570 million), with the funds transferred to address 0x489A8756C18C0b8B24EC2a2b9FF3D4d447F79BEc. Upon discovering the attack, Binance took unprecedented measures: contacting all 26 validation nodes and pausing the entire BSC network for about 9 hours, which is extremely rare in blockchain history. Through rapid response, Binance successfully froze approximately $460 million of the stolen funds, limiting actual losses to about $110 million.
The technical issues exposed by this attack included the IAVL tree implementation not considering the edge case of dual node properties, proof verification logic flaws leading to incomplete verification of the path from the Merkle tree to the root hash, and excessive reliance on external cryptographic libraries without fully understanding their limitations. System-level issues included reliance on centralized decision-making to pause the entire network, and the response speed of the 26 validation nodes constrained emergency handling efficiency. This incident illustrates that even large exchanges with strong technical capabilities may have blind spots when facing complex cryptographic attacks.
- Nomad Bridge: The Butterfly Effect of Trust Root Configuration
On August 1, 2022, the Nomad Bridge, connecting Ethereum and Moonbeam, experienced one of the most peculiar attack events in crypto history. This attack was triggered by a seemingly trivial configuration error, ultimately evolving into a "community participation" fund heist, resulting in losses of $190 million. This event perfectly illustrates the enormous consequences that small errors can trigger in complex systems and showcases the double-edged sword effect of blockchain's permissionless characteristics.
Nomad employed an optimistic verification mechanism, validating cross-chain messages through a "trusted root" system. Each valid cross-chain message would update the trusted root, while invalid messages were marked as "untrusted." During a routine protocol upgrade, the development team made a seemingly trivial but catastrophically consequential error: setting the "trusted root" value to 0x00. The problem was that 0x00 was also the default value for "untrusted root," meaning the system could not distinguish between valid and invalid messages, and all messages were automatically marked as "verified."
On August 1, 2022, a user (later confirmed to be an attacker) discovered an anomaly: sending 0.01 WBTC from Moonbeam to the bridge, but receiving 100 WBTC from the Ethereum side. This 1:10,000 exchange rate immediately exposed a serious vulnerability in the system. Once the first successful attack transaction was discovered, the situation quickly spiraled out of control. First, technicians who understood the vulnerability began manually constructing attack transactions, then other users realized they could profit by simply copying successful transactions and modifying the receiving address, and finally, MEV (Maximum Extractable Value) bots joined in, automating similar transactions.
In this "attack feast" lasting about 4 hours, over 300 addresses participated in thousands of attack transactions, nearly exhausting the Nomad bridge's liquidity pool. In this "community participation" fund heist, some white-hat hackers also participated, later voluntarily returning about $32 million in funds, receiving a 10% reward. The Nomad team also requested other users who received funds to voluntarily return them, promising to keep 10% as a reward, but responses were few.
This attack exposed direct issues including configuration value conflicts that led to the trusted root and untrusted root using the same default value, insufficient testing coverage before upgrades that failed to identify edge cases, and a lack of adequate code review for seemingly simple configuration changes. Deeper issues lie in the systemic risks of the optimistic verification mechanism's over-reliance on a single trust root, while the permissionless nature of blockchain amplifies losses during system failures. This event has become a classic case in blockchain security history, illustrating that any seemingly minor error in complex systems can lead to catastrophic consequences.
- Orbit Chain: Systemic Collapse of Multi-Signature Private Keys
On January 1, 2024, the first day of the new year brought an ominous start to cross-chain bridge security. The multi-chain supporting cross-chain bridge protocol Orbit Chain was attacked, resulting in losses of $81.5 million, marking the first major cross-chain bridge security incident of 2024. This attack once again exposed the vulnerability of traditional multi-signature mechanisms in the face of systemic attacks, as even the seemingly more secure 7-of-10 multi-signature architecture struggled to withstand organized attacks.
Orbit Chain employs a multi-signature architecture with 10 validation nodes, requiring the agreement of 7 nodes to execute transactions. This 7-of-10 design theoretically should provide sufficient security, as attackers would need to control 70% of the validation nodes to successfully attack. However, on the first day of 2024, attackers obtained the private keys of 7 out of the 10 validation nodes through undisclosed means, precisely reaching the minimum threshold required to execute arbitrary transactions.
Stolen assets included $48.1 million in USDT, $16.7 million in USDC, $8.3 million in DAI, $5.4 million in WBTC, and $3 million in ETH, among various mainstream crypto assets. The attackers employed a laundering strategy similar to that of the Harmony bridge attack, first rapidly transferring funds to multiple addresses for dispersion, then using mixing services like Tornado Cash to obscure the fund trails, and finally utilizing other cross-chain services to continue transferring funds to evade tracking.
The key issue in this attack was the simultaneous leak of 7 private keys, exposing systemic flaws in Orbit Chain's private key management. Despite employing a multi-signature architecture to disperse risk, private key management still faced the risk of centralized single points of failure. Insufficient internal security controls allowed attackers to simultaneously obtain private keys from multiple validation nodes, while the lack of real-time monitoring for abnormal transactions and an automatic pause mechanism provided attackers ample time to complete fund transfers.
This incident illustrates that even a higher-threshold multi-signature architecture cannot effectively withstand organized attacks if there are flaws in key management and internal security controls. Traditional multi-signature mechanisms, while somewhat dispersing risk, fundamentally rely on the assumption that "most validators will not be compromised simultaneously," a premise that often fails in the face of systemic attacks.
Deep Causes of Cross-Chain Bridge Vulnerabilities
Through an in-depth analysis of the six major cases mentioned above, we can see that cross-chain bridge security issues are not random events but rather the inevitable result of fundamental flaws in current technological architecture and security models. These issues can be summarized into several main systemic defects.
Private key management flaws are the most prominent issue across all cases, accounting for approximately 55% of the factors contributing to attack success. Whether it is the social engineering attack on Ronin Bridge, the key cracking of Harmony Horizon, or the systemic leak in Orbit Chain, they all point to the same core problem: the current multi-signature architecture overly relies on human operations and centralized key management systems. Validation node private keys are often stored centrally or managed by the same team, multi-signature thresholds are generally set too low (such as 2-of-5, 7-of-10, etc.), lacking effective key rotation mechanisms, and there is clearly insufficient protection against social engineering attacks. The root of these problems lies in the fact that traditional multi-signature solutions, while dispersing risk to some extent, still cannot completely eliminate the influence of human factors, especially in cross-chain scenarios that require rapid responses, where operational efficiency is often prioritized over security.
Smart contract verification vulnerabilities account for about 30% of the factors contributing to attack success, with cases like Wormhole and Binance Bridge falling into this category. The characteristics of such vulnerabilities include the possibility of bypassing signature verification logic, insufficient input validation allowing malicious data injection, the use of deprecated or known-risk functions, and risks arising from third-party library integration. Cross-chain bridges need to handle different signature algorithms, data formats, and consensus mechanisms across various blockchains, which significantly increases the likelihood of logical vulnerabilities. Moreover, the complexity of cross-chain protocols makes comprehensive security audits extremely difficult, with some edge cases often overlooked until discovered and exploited by attackers.
Configuration management errors, while relatively less common (about 10%), can have catastrophic impacts, with the Nomad Bridge case being a typical example. Such issues include configuration errors during protocol upgrades, improper permission settings or failure to timely revoke temporary permissions, conflicts in key parameter configurations, and insufficient testing coverage. These seemingly minor errors are often overlooked by development teams but can trigger chain reactions in complex cross-chain environments, leading to massive losses.
Cryptographic proof system flaws account for about 5%, but the technical complexity is extremely high, with the Merkle proof forgery of Binance Bridge belonging to this category. Such attacks require attackers to have a deep understanding of underlying cryptographic principles, enabling them to discover and exploit subtle flaws in the proof system. Although this category represents a smaller proportion, these attacks are often difficult to defend against because they exploit vulnerabilities at the mathematical and cryptographic levels rather than simple implementation errors.
Industry Status and Technological Evolution
From the distribution of loss scale over time, cross-chain bridge security shows a clear trend of evolution. The year 2022 was the "darkest hour" for cross-chain bridge security, with total losses of approximately $1.85 billion, accounting for over 65% of total losses in nearly three years. Total losses in 2023 were about $680 million, a decrease from the previous year but still at a high level. Total losses in 2024 were approximately $240 million, indicating a gradual improvement in industry security awareness and protective capabilities.
Attack methods are also continuously evolving. The characteristic of 2022 was large-scale, high-loss single-point attacks, where attackers often targeted a single high-value target for concentrated attacks. The characteristic of 2023 was the diversification of attack methods, with a noticeable increase in the proportion of social engineering attacks, indicating that attackers began to exploit human factor weaknesses more. The characteristic of 2024 is more covert and precise targeted attacks, with attackers' technical levels and organizational capabilities significantly improving.
In the face of a severe security situation, the industry is exploring various technological solutions. Zero-knowledge proof bridges utilize ZK-SNARKs/STARKs technology to achieve trustless verification, fundamentally eliminating reliance on centralized validation nodes. Multi-party computation (MPC) architecture significantly raises the threshold for single-point attacks through private key sharding storage and distributed signing. Formal verification employs mathematical methods to prove the correctness of smart contract logic, eliminating the possibility of verification bypass at the code level. Real-time monitoring and automatic pause systems leverage AI-driven abnormal transaction detection and automated emergency response mechanisms to greatly shorten the time for attack discovery and response.
Conclusion: Redefining the Future of Cross-Chain Security
Through a detailed analysis of six major cross-chain bridge attack events, we can clearly see the fundamental flaws in the security architecture design of current cross-chain infrastructure. The cumulative loss of $2.8 billion is not just a number; it represents the real asset losses of thousands of users and reflects the systemic issues in the security of the entire Web3 infrastructure.
The fundamental problem facing current cross-chain bridges lies in the flaws of the trust model. The vast majority of cross-chain bridges rely on the assumption that "a few validators will not act maliciously," a model that is extremely vulnerable to organized and premeditated attacks. The contradiction between complexity and security is also becoming increasingly prominent, as cross-chain bridges need to handle the heterogeneity of multiple blockchains, which inherently increases security risks. Meanwhile, the potential gains for attackers far exceed the costs of security measures, creating an asymmetric game relationship that strongly incentivizes attack behavior.
Real solutions need to address the issues from three levels: technology, governance, and economics. On the technical level, cryptographic methods must be employed to completely eliminate reliance on human trust, ensuring the mathematical correctness of code logic through formal verification, and establishing a multi-layered defense system rather than relying on a single security mechanism. On the governance level, industry-wide security standards and best practices need to be established, promoting regulatory bodies to formulate targeted compliance frameworks and enhancing cross-project security information sharing and collaboration. On the economic level, more reasonable economic incentive mechanisms should be designed, establishing industry-level security insurance and compensation funds to increase attack costs and reduce attack gains.
The future of cross-chain bridges should not be built on the fragile foundation of "praying for honest validators," but rather on cryptographic guarantees that "even if all participants attempt to act maliciously, they cannot succeed." Only by fundamentally redesigning cross-chain security architecture and breaking free from reliance on centralized trust can we truly achieve secure and reliable multi-chain interoperability. In this challenging era, those who can provide truly decentralized, mathematically provable secure cross-chain solutions will become the guiding lights leading the industry out of the security shadow.
The future of Web3 depends on the choices we make today regarding security architecture. History has already taught us a painful lesson with a cost of $2.8 billion: traditional security models can no longer meet the needs of decentralized finance. It is time to thoroughly rethink and design cross-chain security architecture, and let us work together to build a truly secure and trustworthy multi-chain ecosystem.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




