The Bitcoin community needs to quickly research post-quantum cryptography and reach a consensus to address the potential "quantum liquidation" crisis that could lead to a collapse of trust and market turmoil.
Written by: Luke, Mars Finance
As night falls in Las Vegas, at a private lunch during the Bitcoin 2025 conference, seasoned cryptocurrency experts rarely show a serious demeanor. The air is filled not with the revelry of excess, but with a deeper concern: quantum computing, a disruptive technology once thought to be far in the future, is approaching at an astonishing speed, casting its cold light on Bitcoin's seemingly indestructible cryptographic barriers. Warnings claim that powerful quantum computers could crack Bitcoin's private keys within a few years, putting approximately $42 billion worth of Bitcoin at risk and potentially triggering a "liquidation event" that could affect the entire market.
This is not alarmism. Recent research from Google's Quantum AI team has added fuel to the fire, indicating that the quantum resources required to break the widely used RSA encryption algorithm have decreased by a factor of 20 compared to previous estimates. Although Bitcoin uses the Elliptic Curve Digital Signature Algorithm (ECDSA) rather than RSA, both face potential threats from quantum algorithms based on their mathematical foundations. Jameson Lopp, co-founder of Casa, has echoed the urgent call: "The Bitcoin community needs to reach a consensus on mitigating the quantum threat before it truly evolves into a survival crisis."
How far are we from a future that could be "destroyed" by quantum computing? This is not just a technical issue; it concerns trust, wealth, and the fate of an emerging industry.
How does the quantum specter knock on Bitcoin's cryptographic door?
To understand the threat of quantum computing to Bitcoin, we first need to examine the cornerstone of Bitcoin's security—ECDSA. Simply put, when you create a Bitcoin wallet, a pair of keys is generated: a private key (which you must keep secret) and a public key (which can be shared). The public key undergoes a series of hash operations to generate a Bitcoin address. When transacting, you use the private key to digitally sign the transaction, and others in the network can use your public key to verify that the signature indeed comes from you and that the transaction information has not been tampered with. For classical computers, deriving the private key from the public key is mathematically considered infeasible, which is the foundation of Bitcoin's security.
However, the advent of quantum computers, particularly with Peter Shor's algorithm proposed in 1994, has completely changed this landscape. Shor's algorithm can efficiently solve large number factorization and discrete logarithm problems, which are the mathematical foundations of the security of public key cryptosystems like RSA and ECDSA. Once a sufficiently powerful quantum computer is built and operates stably, it could theoretically use Shor's algorithm to quickly compute the corresponding private key from a known public key.
Which Bitcoins are most exposed to quantum firepower? The first to be at risk are those addresses that directly expose the public key. The most typical are the P2PK (Pay-to-Public-Key) addresses used in Bitcoin's early days, where the address itself or related transactions directly reveal the public key. It is estimated that millions of Bitcoins (one estimate suggests about 1.9 to 2 million) still lie dormant in such addresses, including some of the legendary early "genesis" Bitcoins attributed to Satoshi Nakamoto. Furthermore, the more common P2PKH (Pay-to-Public-Key-Hash) addresses, while the address itself is a hash of the public key and relatively secure, expose the public key in transaction data once a spending transaction occurs. If these addresses are reused (i.e., multiple transactions are sent from the same address), their public keys remain exposed, facing similar risks. According to earlier analyses by firms like Deloitte, the number of Bitcoins at risk due to public key exposure from address reuse could also reach millions. Even newer Taproot (P2TR) addresses, despite introducing optimizations like Schnorr signatures, may still allow the public key or its variants to be inferred in certain situations, leaving them not entirely immune to quantum threats.
Overall, the total amount of Bitcoin stored in various vulnerable addresses could represent a significant proportion of Bitcoin's total supply. Earlier estimates (such as in 2022) suggested that around 4 to 6 million Bitcoins are at high risk. If we roughly calculate based on the current Bitcoin price (for example, assuming $70,000 per coin), the value of this portion could reach $280 billion to $420 billion. This may provide a more reasonable explanation for the "risk warning of $42 billion"—it refers not to an exact figure but to a warning about the exposure of vast wealth to potential risks.
Even more concerning is the so-called "short-range attack." When you initiate a Bitcoin transaction, your public key is broadcast along with the transaction information, waiting for miners to package and confirm it. This process typically takes 10 to 60 minutes. If a quantum computer can crack the private key from the broadcast public key within this brief time window, it could construct a new transaction with a higher fee to preemptively transfer your Bitcoins. If such an attack becomes a reality, nearly all types of Bitcoin transactions would face immediate threats.
The race for quantum hardware: a rapid march from theory to reality
For a long time, building a quantum computer capable of running Shor's algorithm to crack actual cryptographic systems was considered unattainable. However, recent advancements have been remarkable, especially in improving the quality, quantity, and error correction capabilities of qubits. The true measure of a quantum computer's ability to break encryption is not merely the number of physical qubits, but the number and quality of "logical qubits" that can reliably execute complex algorithms.
Craig Gidney, a researcher at Google's Quantum AI team, noted in an early 2025 update that breaking 2048-bit RSA encryption (commonly used in traditional cybersecurity) may no longer require the previously estimated tens of millions of physical qubits, but rather "fewer than one million noisy qubits," and could potentially be completed in "less than a week." This significant reduction in estimates is attributed to advancements in algorithm optimization and error correction techniques, such as approximate remainder computation, more efficient logical qubit storage, and the application of "magic state" purification techniques. Although Gidney emphasized that such a quantum computer would still need to meet stringent conditions (such as stable operation for five consecutive days with an extremely low gate error rate), far exceeding current technological levels, it undoubtedly shortens the "quantum security distance" as perceived by us. For ECDSA used by Bitcoin (secp256k1 curve), while there is no equally precise and widely accepted public data on the quantum resources required for specific cracking compared to RSA-2048, the general consensus in the cryptographic community is that due to its mathematical structure, breaking ECDSA may be easier for quantum computers than breaking RSA.
On the hardware front, several major players are racing to catch up. IBM's quantum roadmap is ambitious, with its "Osprey" processor reaching 433 physical qubits, and "Condor" achieving an experimental 1121 physical qubits. More importantly, IBM focuses on improving qubit quality and error correction capabilities, with its "Heron" processor (133 qubits) becoming a current development priority due to its lower error rates, and plans to launch the "Kookaburra" system with 1386 physical qubits in 2025, achieving larger scales through multi-chip connections. Its longer-term goal is to achieve a "Starling" system with 200 high-quality logical qubits by 2029, expected to perform up to 100 million quantum gate operations.
Google is also making continuous efforts, with its "Willow" chip (reportedly with 105 physical qubits) debuting in early 2025, described by its team as "a compelling prototype for scalable logical qubits," and achieving "sub-threshold" progress in quantum error correction, a key step toward achieving fault-tolerant quantum computing.
Meanwhile, Quantinuum made a "bombshell" announcement in 2025, stating that its "Helios" quantum computing system would be commercially available later that year and capable of supporting "at least 50 high-fidelity logical qubits." If fully realized, this statement would mark an important milestone in quantum computing's transition from experimental research to practical computational capabilities (especially in specific application areas). The company also demonstrated record-breaking fidelity in logical qubit teleportation in May 2025, further proving its leading position in building high-quality logical qubits.
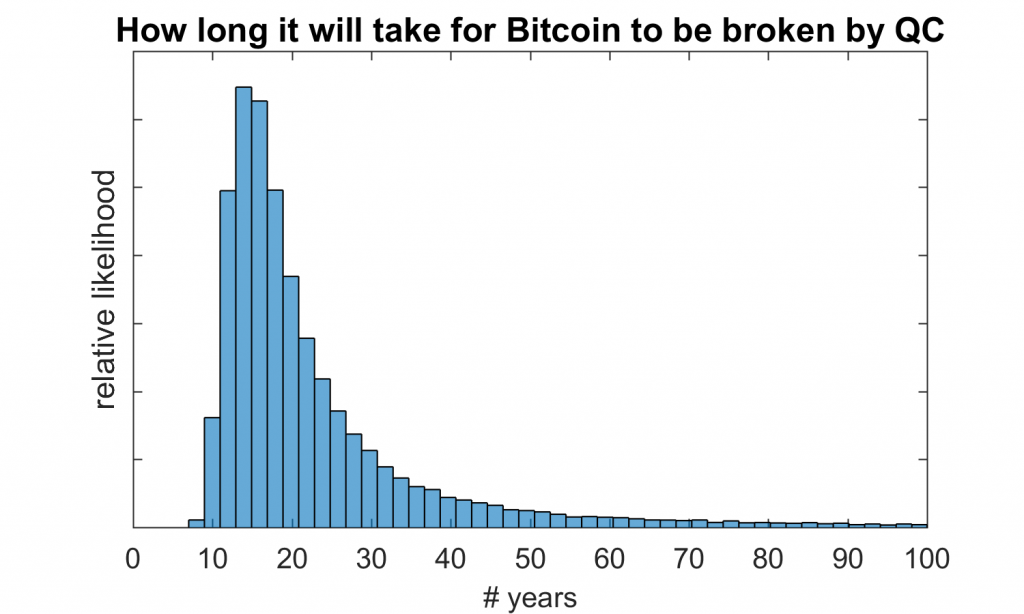
Nevertheless, experts still have differing predictions on how far we are from the emergence of fault-tolerant quantum computers that could threaten Bitcoin. Some optimistic (or pessimistic, depending on the stance) estimates suggest that they may appear within the next 3 to 5 years, while others believe it will take at least another decade or longer. Importantly, the quantum threat is not a binary "on/off" mutation but a gradually increasing probability. Every advancement in hardware and every optimization in algorithms quietly shortens the countdown.
Bitcoin's "quantum counteroffensive": preparing for the worst or closing the barn door after the horse has bolted?
In the face of the increasingly clear quantum threat, the Bitcoin community is not helpless. The cryptographic community has long begun researching "post-quantum cryptography" (PQC), which refers to new cryptographic algorithms believed to be resistant to known quantum algorithm attacks. The U.S. National Institute of Standards and Technology (NIST) has published the first batch of standardized PQC algorithms after years of selection, mainly including CRYSTALS-Kyber for key encapsulation, and CRYSTALS-Dilithium, FALCON, and SPHINCS+ for digital signatures.
For Bitcoin, hash-based signature schemes (HBS), such as SPHINCS+, are considered strong contenders because their security does not rely on mathematical problems (like lattice cryptography) that are yet to be widely tested, but rather on the collision resistance of well-studied hash functions. SPHINCS+ is stateless (unlike its predecessors like XMSS), which is particularly important for the distributed nature of blockchain. However, hash-based signatures typically face challenges such as larger signature sizes and longer key generation and verification times, which could put pressure on Bitcoin's transaction efficiency and blockchain storage. Integrating these PQC algorithms without sacrificing Bitcoin's core characteristics is a significant technical challenge.
A greater challenge lies in how to transition Bitcoin from the existing ECDSA to the new PQC standards. This involves not just code-level modifications but also fundamental upgrades to the Bitcoin protocol, as well as a smooth transition for millions of users and hundreds of billions of dollars in assets globally.
First, there is the choice of upgrade method: soft fork or hard fork? A soft fork is compatible with old nodes and is generally considered to carry lower risk, but the freedom to implement complex PQC features may be limited. A hard fork, on the other hand, is incompatible with old rules, requiring all participants to upgrade; otherwise, it could lead to a split in the blockchain, which has often been accompanied by significant controversy and risks of community division in Bitcoin's history.
Secondly, there is the migration mechanism. How can users safely transfer their Bitcoins stored in old addresses (ECDSA) to new quantum-resistant (QR) addresses? This process needs to be designed to be both secure and convenient while preventing new attack vectors from emerging during the migration window.
Bitcoin thought leader Jameson Lopp provided profound insights on this issue in his widely discussed article "Against Allowing Quantum Computers to Recover Bitcoin." He argues that allowing those with quantum computing power to "recover" (essentially steal) Bitcoins that are not protected by PQC would amount to a wealth redistribution favoring a small group of technological oligarchs, severely undermining Bitcoin's fairness and credibility. He even proposed a controversial idea: setting a "final migration deadline" (drop-dead date), after which Bitcoins not migrated to QR addresses could be considered "burned" or permanently unspendable by the protocol. Lopp acknowledges that this is a difficult trade-off that could lead to asset losses for some users (especially those with long-dormant addresses or lost private keys) and could even trigger a hard fork, but he believes it is a "bitter pill" that must be considered to protect the long-term integrity and core value proposition of the Bitcoin network.
Another developer, Agustin Cruz, proposed a specific hard fork called QRAMP (Quantum Resistant Address Migration Protocol). This proposal advocates for a mandatory migration period, after which un-migrated Bitcoins would also be considered "burned," thereby "forcing" the entire ecosystem to quickly transition to a quantum-safe state. Such radical proposals highlight the potential divisions within the community regarding the path to addressing quantum threats and the challenges of reaching consensus under a decentralized governance model.
In addition to upgrading to PQC addresses, continuously advocating for and reinforcing the best practice of "not reusing addresses" can also reduce risks to some extent, but this is ultimately just a stopgap measure and cannot eliminate the threat that quantum algorithms pose to ECDSA itself.
Ecological Hesitation: Between Inertia and Change
In the face of such significant systemic risks, how prepared is the Bitcoin ecosystem? Some emerging public chain projects, such as Quantum Resistant Ledger (QRL), have built PQC features into their design from the outset, while projects like Algorand are actively exploring PQC integration solutions. They are like small boats attempting to navigate the waves of post-quantum cryptography.
However, Bitcoin, as a "ten-thousand-ton giant," faces extraordinary difficulty and slowness in making any core protocol changes due to its massive market capitalization, extensive user base, and deeply rooted principles of decentralization and censorship resistance. The developer community's awareness of quantum threats is deepening, and related discussions (such as Lopp's article, the QRAMP proposal, and sporadic discussions in the bitcoin-dev mailing list) are ongoing, but it seems there is still a long way to go before forming a clear, widely agreed-upon upgrade roadmap. Currently, there is a lack of clear public information from mainstream Bitcoin exchanges, wallet service providers, or large mining pools regarding their PQC transition plans, reflecting that Bitcoin's PQC transformation is still largely in the theoretical research and early discussion stages rather than imminent engineering implementation.
This state has put Bitcoin in a dilemma of being "too big to fail, yet too slow to evolve." Its strong network effects and brand recognition serve as its moat, but in the face of rapidly iterating technological innovations, this stability can sometimes translate into inertia.
"Quantum Liquidation": It's More Than Just Losing Keys
What would happen if Bitcoin fails to complete the PQC transition before quantum computers gain actual attack capabilities? This is not merely about some users losing their Bitcoins.
A large-scale quantum attack could first trigger a "liquidation event" in the market. Once confidence is shaken, panic selling could lead to a catastrophic collapse in Bitcoin's price. This shockwave would not be limited to Bitcoin itself; it could likely spread to the entire cryptocurrency market and even have ripple effects on traditional financial institutions with significant exposure to the crypto space.
The more profound impact lies in the collapse of trust. Bitcoin has been dubbed "digital gold" largely due to its purportedly "indestructible" cryptographic security. If this cornerstone is easily breached by quantum computing, then all value narratives and application scenarios built upon it will face severe challenges. Public trust in digital assets could plummet to an all-time low.
Compared to other known security risks for Bitcoin (such as 51% attacks, significant software vulnerabilities, and increasingly stringent global regulations), the uniqueness of the quantum threat lies in its disruptive nature. While a 51% attack can cause double spending or transaction censorship, it is difficult to directly steal private keys; software vulnerabilities can be patched; regulatory pressure mainly affects compliance and application boundaries. However, once a quantum attack is realized, it represents a "dimensionality reduction strike" against the existing cryptographic system, directly threatening the ultimate ownership of assets.
Looking back at the history of cryptography, from the upgrade from DES to AES to the gradual phasing out of the SHA-1 hash algorithm, each significant migration of cryptographic systems has been a lengthy process led by centralized institutions (such as governments and standard organizations), often taking years or even decades. While Bitcoin's decentralized governance model grants it strong resilience and censorship resistance, it may appear sluggish when rapid, unified action is needed to respond to global technological changes.
Conclusion: Exploring the Path Forward in the Quantum Fog
Quantum computing, the sword of Damocles hanging over Bitcoin, has an unclear timeline for its descent, but its chilling presence is already palpable. It poses the most profound long-term challenge to the entire cryptographic world, especially in the cryptocurrency sector represented by Bitcoin.
The Bitcoin community is facing an unprecedented test: how to complete a fundamental upgrade of its cryptographic system, which is vital for survival, while adhering to its core tenets of decentralization, censorship resistance, and code as law. This is not just a race against the development of quantum computers; it is a complex system engineering challenge involving PQC algorithm research, standardization, Bitcoin protocol innovation, community consensus building, and global ecosystem collaborative migration.
The road ahead is fraught with uncertainty. Will it successfully evolve, turning the quantum threat into a catalyst for technological innovation and stepping into a more secure post-quantum era? Or will it fade into obscurity in the dawn of quantum computing due to difficulties in consensus and migration? The wheels of history roll forward, and the answers may be hidden in every decision, every code submission, and every heated debate within the Bitcoin community over the next few years. This is destined to be an ongoing story about innovation, risk, and resilience, and each of us, whether participants or observers, stands on the eve of this grand transformation.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



