# I. Outlook
## 1. Macroeconomic Summary and Future Predictions
Last week, there were some significant changes in the macroeconomic landscape in the United States. Gold prices fell by more than 1% and experienced a downward trend throughout the week, marking the first weekly decline since the announcement of reciprocal tariffs. Additionally, due to the impact of U.S. tariff policies, several American companies were affected, with Stellantis and General Motors suspending their profit growth forecasts for 2025 on April 30 and April 29, respectively. These signs indicate that the current macroeconomic environment in the U.S. is facing certain challenges.
In the future, the market is still trying to find certain investment opportunities. Moreover, it is expected that this uncertainty triggered by tariffs may affect corporate profit forecasts and could lead more companies to reassess their annual guidance. At the same time, considering that the IMF has recently lowered its global economic growth forecast to 2.8%, this suggests that global economic growth, including that of the U.S., may remain at a lower level for some time.
## 2. Market Movements and Warnings in the Crypto Industry
Last week, the crypto industry experienced several important changes. Although Bitcoin experienced some volatility, it remained relatively stable overall, continuing to oscillate at high levels. However, for altcoins, the performance this week was more differentiated, with only a few projects achieving significant price increases, while most were in a state of oscillating decline.
As we enter this week, market participants should focus on the latest interest rate decision to be announced by the Federal Reserve early Thursday morning, as well as the subsequent remarks from Fed Chair Powell. This interest rate decision and Powell's statements may provide new guidance for the future monetary policy path and become an important barometer affecting global financial markets and crypto asset prices.
3. Industry and Sector Hotspots
Inco has achieved a $5 million lead investment from A16z and Coinbase, utilizing FHE technology for a modular L1 chain; Catalysis is building the first security abstraction layer, providing a seamless, unified solution for developers and node operators by abstracting the complexity of shared security mechanisms; Symbiotic is a shared security protocol aimed at creating an economically secure market. It allows networks in need of security to obtain security guarantees from parties holding assets for staking, thereby creating an efficient ecosystem.
# II. Market Hotspot Sectors and Potential Projects of the Week
## 1. Performance of Potential Sectors
1.1. How Inco, with a $5 million lead investment from A16z and Coinbase, is Achieving Web3 Democratization Using FHE Technology
Inco is a modular Layer-1 blockchain that uses Fully Homomorphic Encryption (FHE) to provide confidential computing, enhancing on-chain privacy and scalability for developers and users within the Ethereum ecosystem. Inco focuses on democratizing liquidity acquisition and promoting the adoption of Web3, providing a seamless, privacy-focused experience for creating innovative decentralized applications (dApps) across various fields, including gaming, DeFi, payments, governance, and identity management.
Inco has two core protocols: Inco Lightning and Inco Atlas. Inco Lightning uses Trusted Execution Environments (TEEs) to provide verifiable confidential computing and operates at high speed. It introduces new private data types, operations, and access controls, allowing smart contracts to securely handle sensitive data. There is no need to create a new chain or a new wallet. Developers can start building privacy-protecting dApps simply by importing our Solidity library.
Inco Atlas is supported by Fully Homomorphic Encryption (FHE) and Multi-Party Computation (MPC) and is expected to be released in the near future.
Architecture Overview
The architecture of Inco consists of four main components that work together to provide confidential computing capabilities:
- Smart Contract Library
- Confidential Compute Nodes
- Decryption Nodes + Callback Relayer
- Client-side JavaScript Library
These components work together to provide developers with a seamless experience, enabling them to build privacy-protecting applications on the blockchain. The system handles encrypted data types, performs confidential computing, and manages secure decryption processes while maintaining compatibility with existing EVM blockchains.
- Component Introduction
Smart Contract Library
This library extends the EVM to support encrypted data types and operations. Deployed on the main chain, it provides the following functionalities:
- Encrypted Data Types: ebool, eaddress, estring, euint32
- Arithmetic Operations: add, e.sub, e.mul
- Comparison Operations: eq, e.le, e.gt
- Conditional Operations: select
- Decryption Operations: asyncDecrypt
This library enables developers to write smart contracts that support encrypted data processing directly without modifying the underlying blockchain.
Confidential Compute Nodes
Confidential compute nodes operate in Trusted Execution Environments (TEEs) and are responsible for executing encrypted computing tasks. Each node has the following functionalities:
- Run Inco's computing binary in a secure TEE environment
- Handle encrypted operations based on blockchain events
- Verify access control before executing decryption
Decryption Nodes + Callback Relayer
Multiple decryption nodes operate under a TEE consensus mechanism to ensure the security and verifiability of the decryption process. The entire decryption process is as follows:
- Listen for on-chain decryption requests
- Forward requests to the TEE decryption network
- Collect signed decryption results from the network
- Write the decryption results back to the chain via callback transactions
The on-chain verification mechanism ensures that all decryption proofs come from a trusted set of decryption nodes.
Client-side JavaScript Library
This library provides user-side functionalities to interact with the main chain and the Inco network:
- Encrypt user input data using the network public key
- Handle ephemeral key and EIP-712 signature generation (for re-encryption requests)
- Locally decrypt and display computation results for users
Through these four components, Inco has built a complete end-to-end privacy-protecting computing framework that is EVM-compatible, enabling Web3 developers to easily implement privacy-protecting dApps.
- Decryption Mechanism
Inco provides two types of decryption mechanisms:
Re-encryption: For Private Viewing of Data
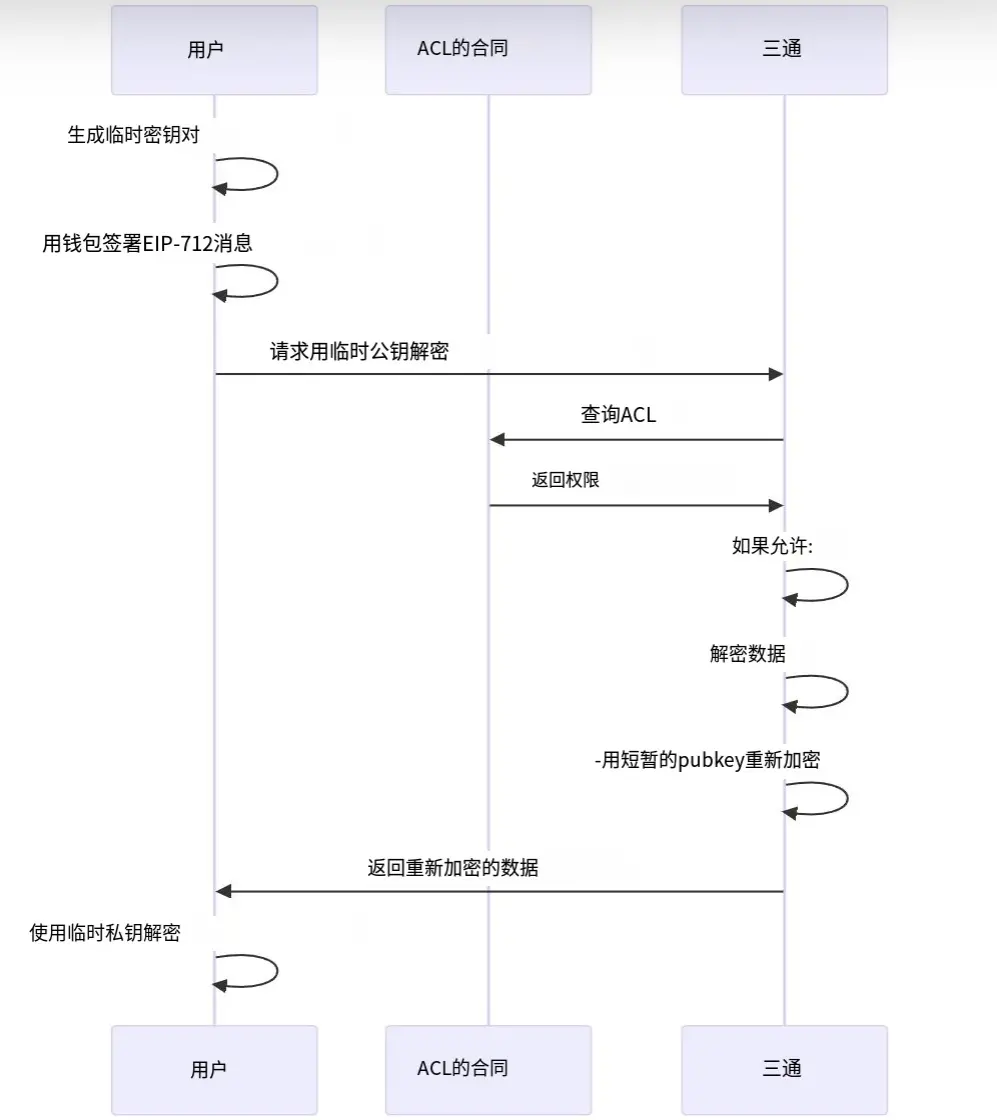
This is suitable for scenarios where users wish to privately view their confidential data:
- The user signs an EIP-712 message to prove wallet ownership
- The client generates a temporary key pair (ephemeral keypair)
- The user sends a decryption request containing the signed message and temporary public key
- The decryption node verifies the signature and checks access control
- The decryption node uses the user's provided temporary public key to re-encrypt the data, ensuring that no information is leaked during transmission
- The user completes the decryption locally using the temporary private key and views the result
On-chain Decryption (Public Decryption)
This is suitable for scenarios where the decryption result needs to be made public on-chain:
- The smart contract calls asyncDecrypt(encryptedValue) to initiate a decryption request
- The decryption network listens for decryption events on the blockchain
- The decryption network queries the Access Control List (ACL) to verify permissions
- Each decryption node decrypts the ciphertext and signs the decryption result
- The callback relayer collects enough signatures and submits the result to the smart contract via callback transactions
- The smart contract verifies these signatures and continues executing logic using the decrypted value
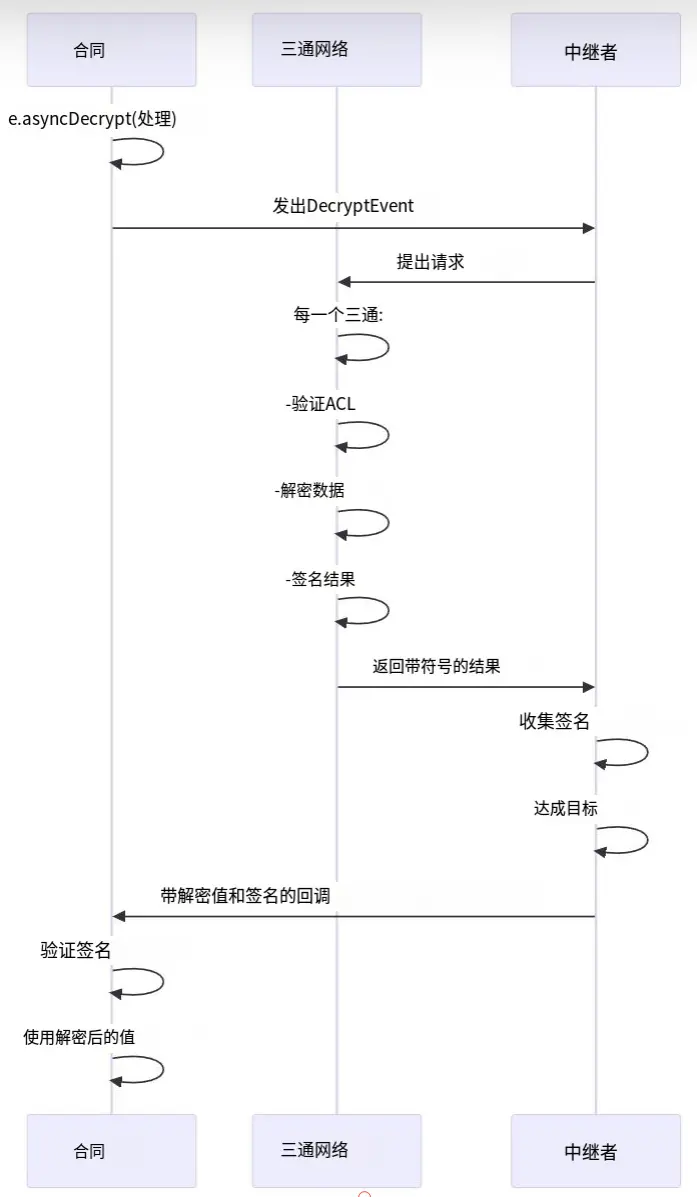
This mechanism is suitable for scenarios where data needs to be made public to the entire network, such as on-chain voting results, fair game logic, or public financial information.
Commentary
Inco is a modular Layer-1/Layer-2 scaling solution designed with privacy as a core principle. Through TEE and future FHE support, it empowers developers to build truly private smart contracts while ensuring EVM compatibility.
It is particularly suitable for Web3 application scenarios that require handling sensitive data, but attention should still be paid to its reliance on TEE, performance optimization, and further improvement of the decryption governance mechanism.
1.2. What Makes Catalysis, with $1.25 Million in Funding and a Focus on Building a Security Abstraction Layer, Special?
Catalysis is building the first Security Abstraction Layer to aggregate and unify the economic security of various shared security protocols.
By abstracting the complexity of shared security mechanisms, Catalysis provides developers and node operators with a seamless, unified solution to help them build and manage decentralized networks, such as AVS (Active Verification Service), BVS (Basic Verification Service), and DVN (Decentralized Verification Network).
Feature Analysis
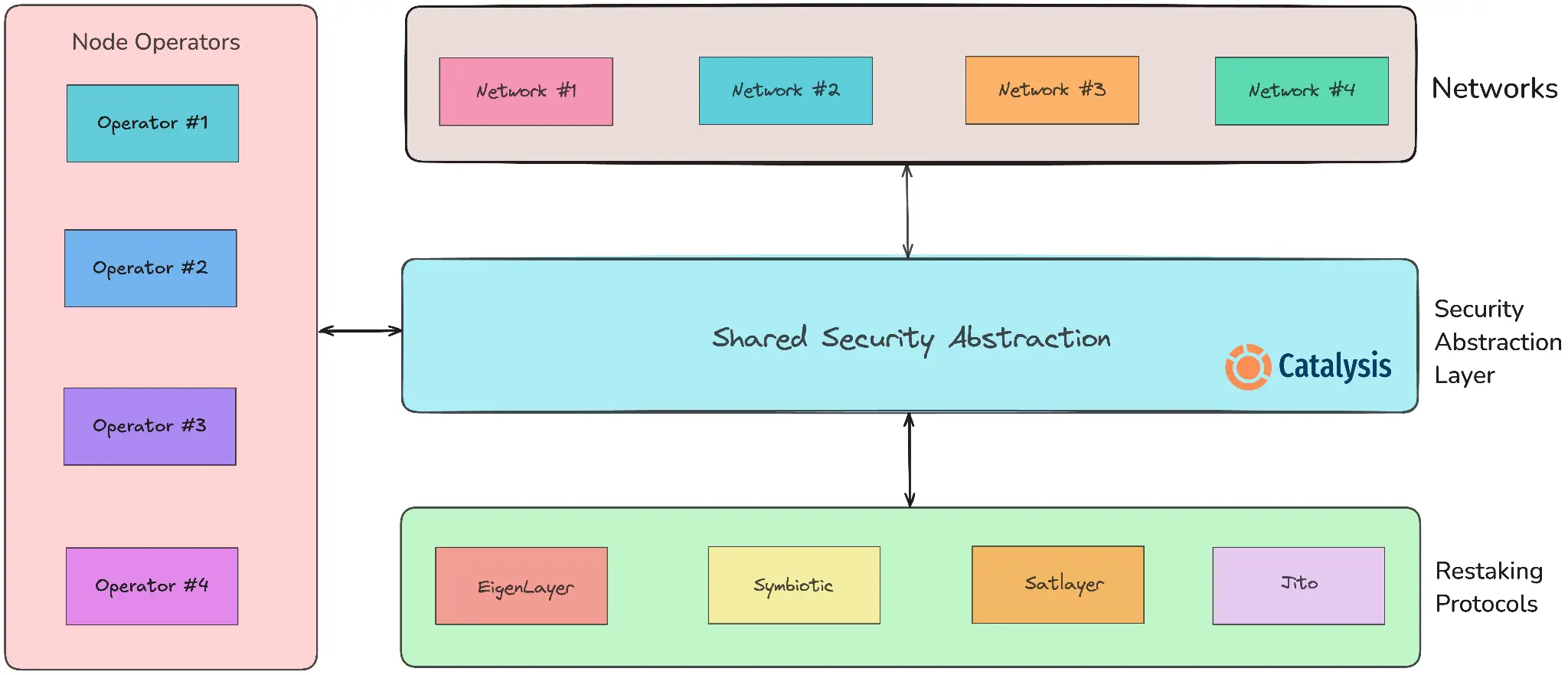
The Catalysis Network is built on three core components:
- Networks: Decentralized services, protocols, and applications (AVS) that utilize shared security for verification and decentralized operation.
In the Catalysis ecosystem, Network refers to any decentralized protocol that provides a custom off-chain operation verification mechanism. A Network consists of on-chain verification contracts and an off-chain operator network. The off-chain part includes client software run by network operators and verification logic specific to that network.
Operators represent the Network to execute services and submit evidence of their execution to the on-chain network contracts. Operators play a crucial role in ensuring the integrity of the network:
- If operators perform tasks correctly, the Network can issue rewards;
- If operators engage in malicious behavior, the assets staked by their agents may be penalized by the Network (penalty reduction, i.e., slash).
Different restaking ecosystems refer to these Networks by different names:
EigenLayer: Autonomous Verifiable Service (AVS)
Symbiotic: Network
Satlayer: Bitcoin Validated Service (BVS)
Jito: Node Consensus Network (NCN)
Kernel: Dynamic Validation Network (DVN)
Node Operators: Entities that run network software and perform validation tasks, using the Catalysis tech stack to ensure network security through restaking protocols.
Node operators are the backbone of the Catalysis Network. They are the "engines" that run the AVS infrastructure, providing economic security for the entire network.
Catalysis brings significant advantages to node operators by streamlining the management of AVS infrastructure across multiple restaking platforms, making operations more efficient. With the Catalyst-CLI tool, operators can seamlessly manage their AVS configurations through a unified interface. This integrated solution eliminates the need to deploy infrastructure separately for each platform, saving a considerable amount of time and effort.
A key advantage of Catalysis is its substantial reduction in DevOps engineering costs, which not only lowers development expenses but also enables node operators to easily scale their AVS management capabilities, supporting thousands of services with almost no additional investment.
Moreover, Catalysis allows node operators of all sizes to participate in the operation of AVS infrastructure, no longer exclusive to large institutions. This inclusivity enhances the decentralization of the node operator collective, effectively addressing the increasingly prominent centralization issues in the current restaking ecosystem.
- Restaking Protocols: Also known as shared security protocols, these allow stakers to restake assets (such as LST, ERC-20 tokens, etc.) to provide security for network validation. These protocols function like a market, connecting networks, node operators, and stakers.
Shared Security Protocols (SSP), also known as restaking protocols, create a market for economic security, enabling decentralized networks to obtain security guarantees from stakers.
They act as a coordinating layer, connecting three core participants:
- Stakers → Provide economic security by delegating assets and maximizing returns.
- Node Operators → Operate network infrastructure and expand into high-value decentralized service areas.
- Networks → Obtain security guarantees through restaked assets.
Catalysis brings significant advantages to shared security protocols: by aggregating demand and acting as a distribution channel, it creates a more competitive and equitable environment for these platforms. One key feature is that Catalysis breaks down barriers between platforms, allowing various restaking protocols to compete fairly based on their cost and performance advantages. This also creates opportunities for the rise of emerging protocols.
Catalysis encourages more projects to deploy as Networks by simplifying the access process, thereby promoting the development of the entire ecosystem. As more Networks are attracted, both the Network teams and SSPs can benefit from the increasing participation, achieving a win-win situation.
In addition to driving adoption rates, Catalysis also helps SSPs provide better functionalities and more reliable economic security guarantees, making their platforms more attractive to Networks seeking robust security. The influx of high-quality Networks further enhances the robustness and value of these protocols, laying a solid foundation for building a vibrant and competitive ecosystem in the future.
Commentary
Catalysis is a highly innovative coordinating protocol dedicated to bridging and optimizing the multi-chain restaking ecosystem. Its greatest highlight is the enhancement of AVS scalability, manageability, and decentralization, while opening new growth channels for SSPs. Although it still faces challenges in technology and ecosystem building, its design philosophy aligns with the key pain points and future trends in the current restaking field, demonstrating strong development potential.
## 2. Detailed Focus Projects of the Week
2.1. Detailed Analysis of How the Shared Security Protocol Symbiotic, Led by Pantera with Follow-on Investments from Coinbase and Aave of $29 Million, Attracts VC Interest
Introduction
Symbiotic is a shared security protocol aimed at creating an economically secure market. It allows networks in need of security to obtain security guarantees from parties holding assets for staking, thereby creating an efficient ecosystem where staking can be shared and utilized across multiple networks. Through its flexible architecture, staking providers can maximize their returns while networks can obtain the necessary security guarantees.
Architecture Overview
- Core Participants
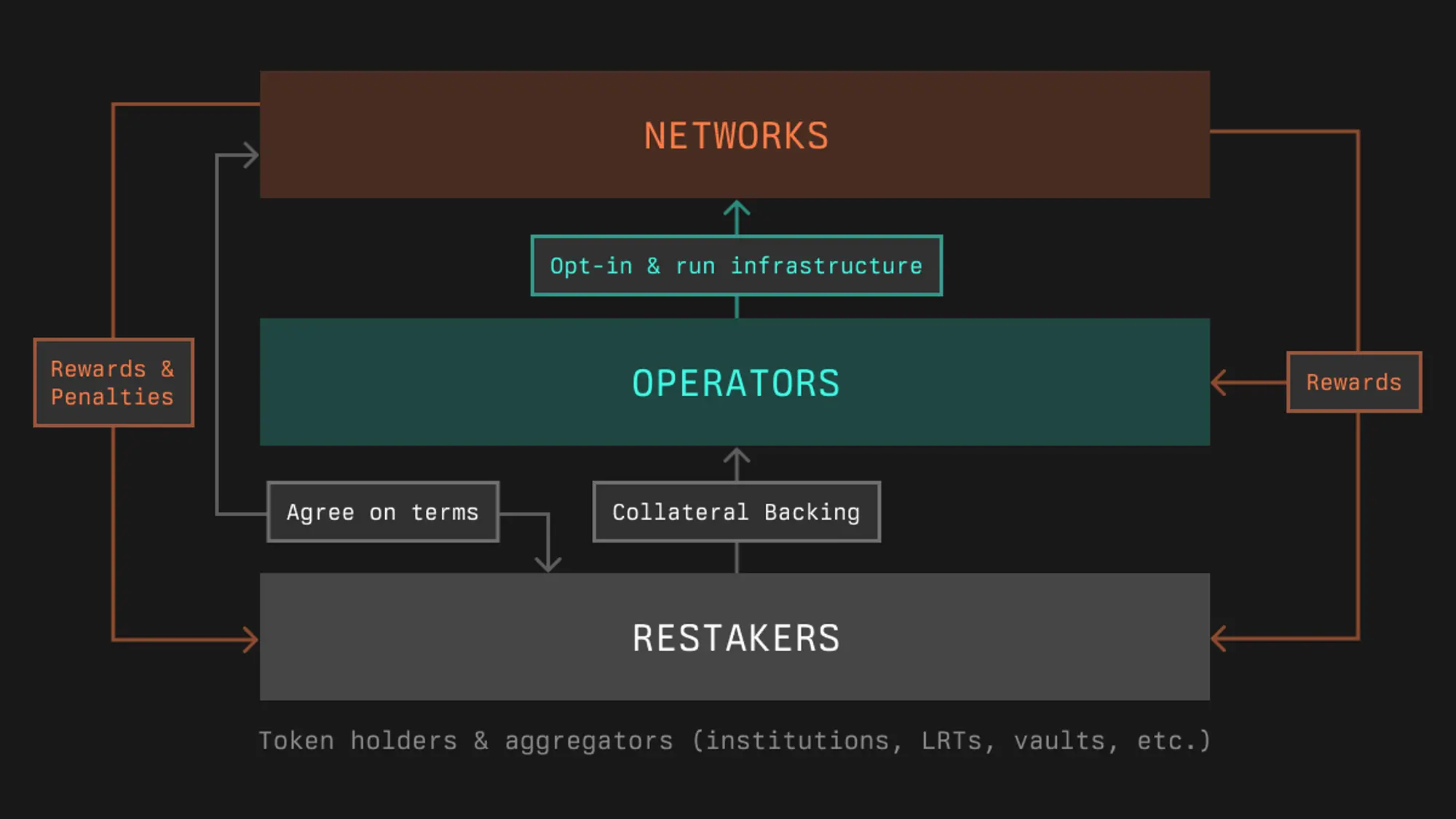
- Stakers - Entities that provide assets to earn rewards through staking deposits. They can be individual token holders, institutions, or liquidity (re)staking protocols. Stakers deposit funds into a dedicated smart contract (staking vault) managed by curators, who are responsible for managing delegation decisions.
- Networks - Systems that require economic security to operate safely. These can be Layer 1 blockchains, Layer 2 solutions, or other decentralized systems that need staking-based security guarantees.
- Operators - Professional entities that maintain network infrastructure, responsible for running validators, nodes, or other required systems. Operators receive staking allocations based on their responsibilities and are responsible for the operation of the network.
- Links Between Participants
The three core participants - stakers, networks, and operators - are connected through a complex infrastructure layer. At the core of this connection are the staking vaults, which serve as the primary interface among all participants.
Symbiotic coordinates and manages interactions within this ecosystem in the following ways:
- Allowing stakers to deposit their assets into staking vaults, where curators manage delegation strategies and approve qualified operators.
- Facilitating network access to security by linking networks with staking vaults and their associated staking.
- Allowing operators to receive staking allocations through curator-managed staking vaults to fulfill their network responsibilities.
This interconnected system is monitored by resolvers, which validate activities and ensure the security of all connections.
- System Relationships
The Symbiotic protocol facilitates several key interactions among participants, creating a robust and efficient security market. Here’s how these key components work together:
- Staking Account Management
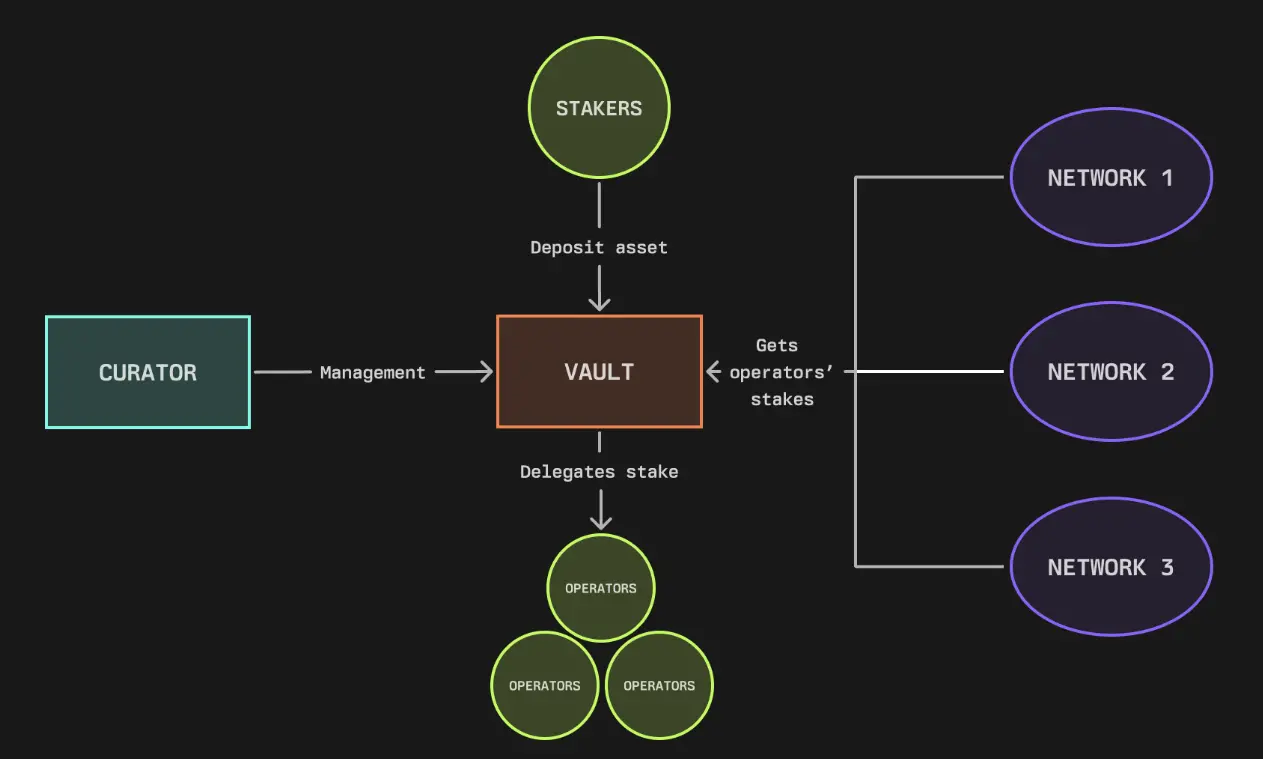
- Stakers deposit their assets into the vault
- Each vault is managed by a guardian, who controls the staking allocation
- The guardian delegates staking to qualified operators, who are responsible for running the network infrastructure
- A vault can serve multiple networks simultaneously, enabling efficient staking allocation among different operators
The staking delegation system has the following important features:
Assets remain securely locked in the vault and do not actually transfer
Staking delegation is conducted solely through an accounting system
Assets can only leave the vault through:
- Withdrawals by the original staker
- Verification penalty events from the network
Network Operations
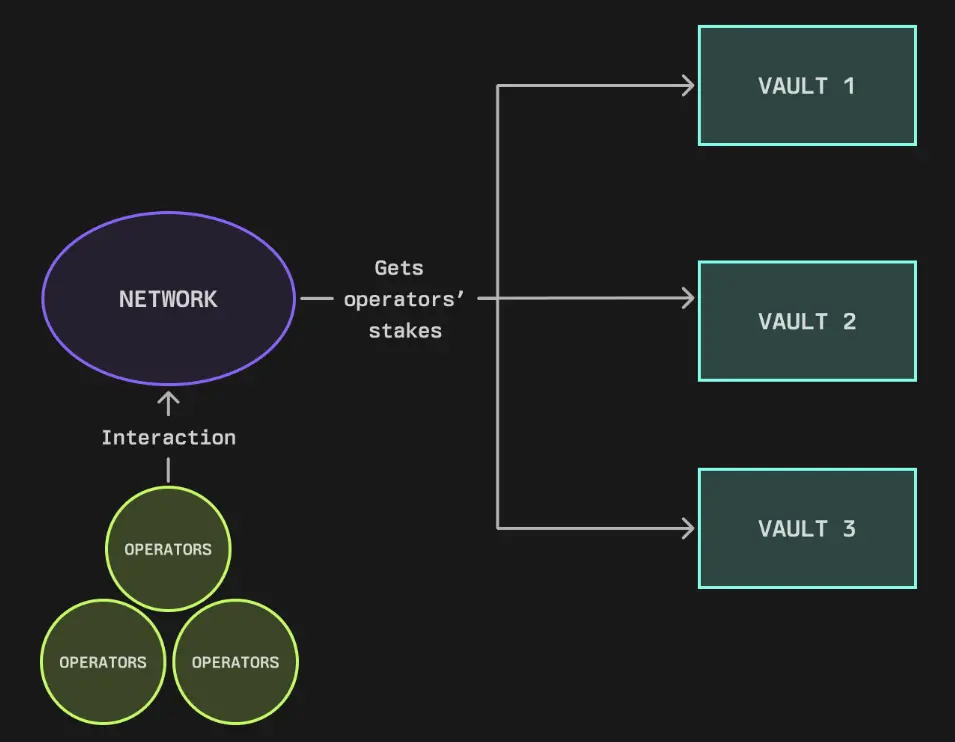
Networks utilize multiple vaults simultaneously, allowing them to aggregate security from different sources. This flexible architecture enables operators to accumulate staking across different vaults, while networks can calculate their total staking by combining delegations from various vault sources.
- Penalty Process
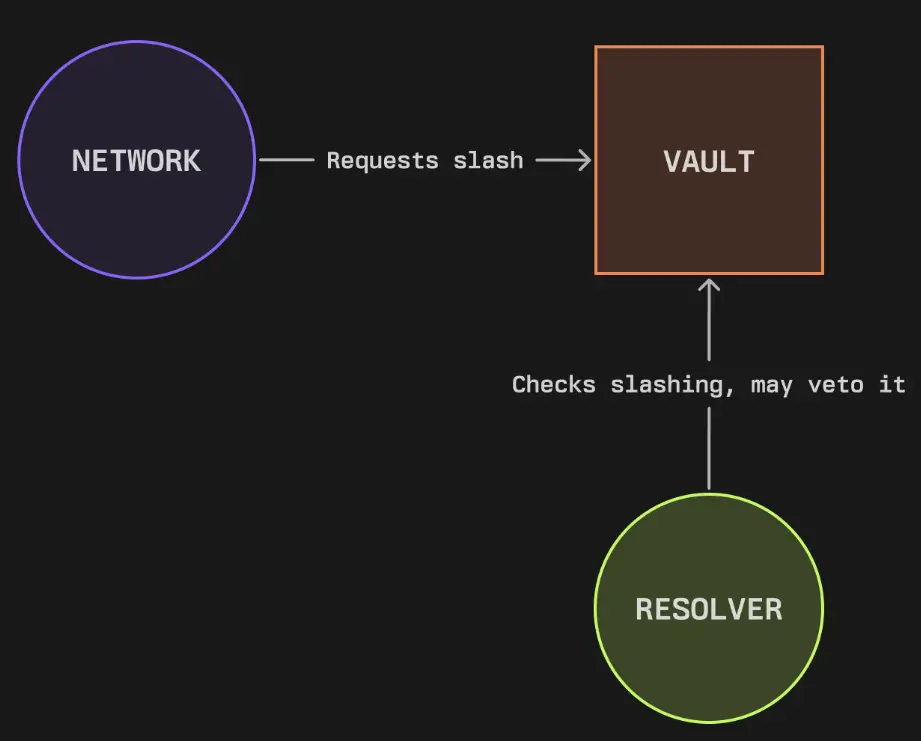
- The network can initiate penalties (slashing) against operators by interacting with the vaults holding the staked assets.
- If an operator has staked assets in multiple vaults, the network can choose from which vaults to impose penalties.
- Resolvers act as validators of penalty events and have veto power.
- Resolvers can be automated contracts, penalty committees, dispute resolution frameworks, multi-signature wallets, or DAO governance systems. The network and vault curators agree on which resolvers to use (or not use at all) and the terms of penalties. During the penalty process, the network selects which vaults to penalize, and resolvers review events and can veto invalid penalty attempts.
Technical Details
- Collateral
Collateral is a concept introduced by Symbiotic, aimed at achieving capital efficiency and scalability by allowing assets used to secure the Symbiotic network to be held outside the Symbiotic protocol (e.g., in DeFi positions on other networks).
Symbiotic achieves this by separating the slashing operations of assets from the underlying assets themselves, similar to the tokenized representation of underlying staking positions created by liquid staking tokens. Technically, the collateral assets in Symbiotic are ERC-20 tokens with extensibility to handle situations if a slashing event occurs. In other words, if the collateral token is intended to support a slashing mechanism, it should be able to create a Burner contract responsible for correctly destroying that asset.
For example:
- If the asset is an ETH liquid staking token (LST), it can be used as collateral as long as a Burner contract can be created to extract ETH from the Beacon chain and destroy it.
- If the asset is a native governance token, it can be used as collateral because the Burner can be implemented as a "black hole" contract or address.
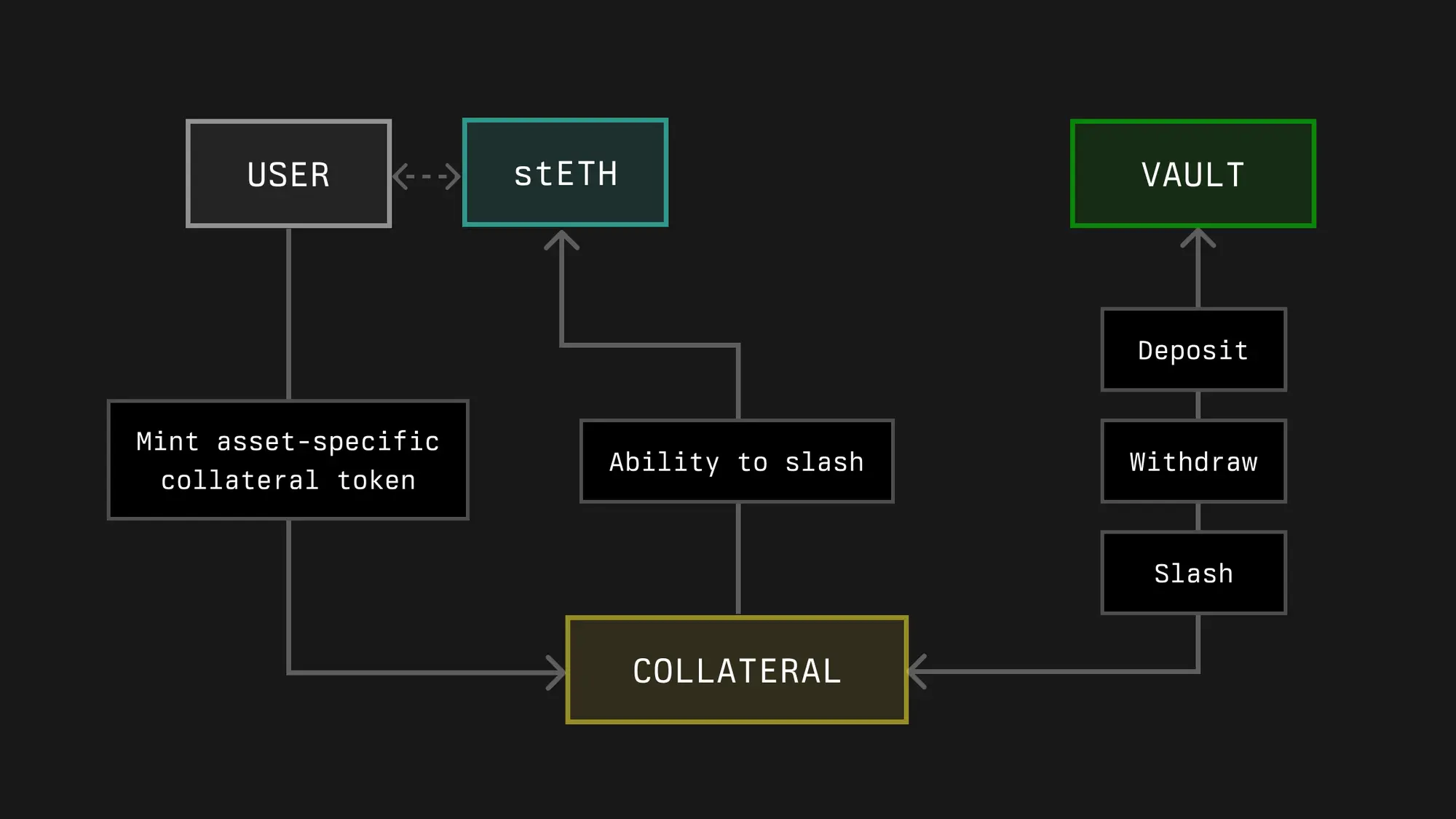
Symbiotic allows collateral tokens to be deposited into vaults, which will guarantee asset delegation to operators within the Symbiotic network. The vaults define acceptable collateral assets and their Burners (if the vault supports a slashing mechanism), and the network needs to accept these and other vault terms, such as slashing limits, in order to receive staking.
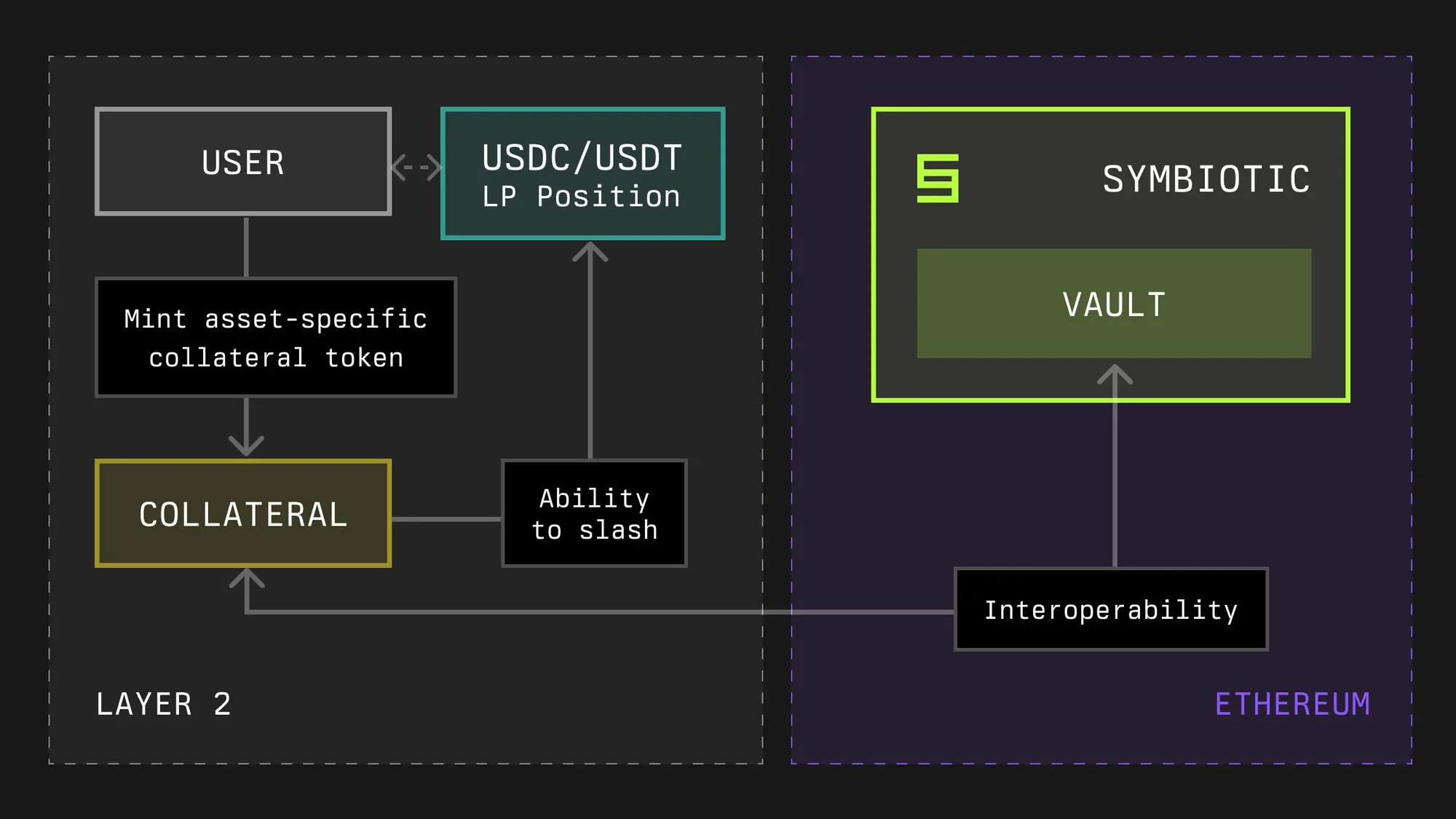
- Vaults
Vaults are the delegation and restaking management layer of Symbiotic. They handle three key parts of the Symbiotic economy:
- Accounting: Vaults manage deposits, withdrawals, and slashing operations of collateral assets, and subsequently handle their underlying assets.
- Delegation Strategies: Vault deployers/owners define delegation and restaking strategies, delegating to operators within the Symbiotic network, which must choose to accept these strategies.
- Slashing Handling: Vaults provide a mechanism to maintain the economic security of the network through slashing operations.
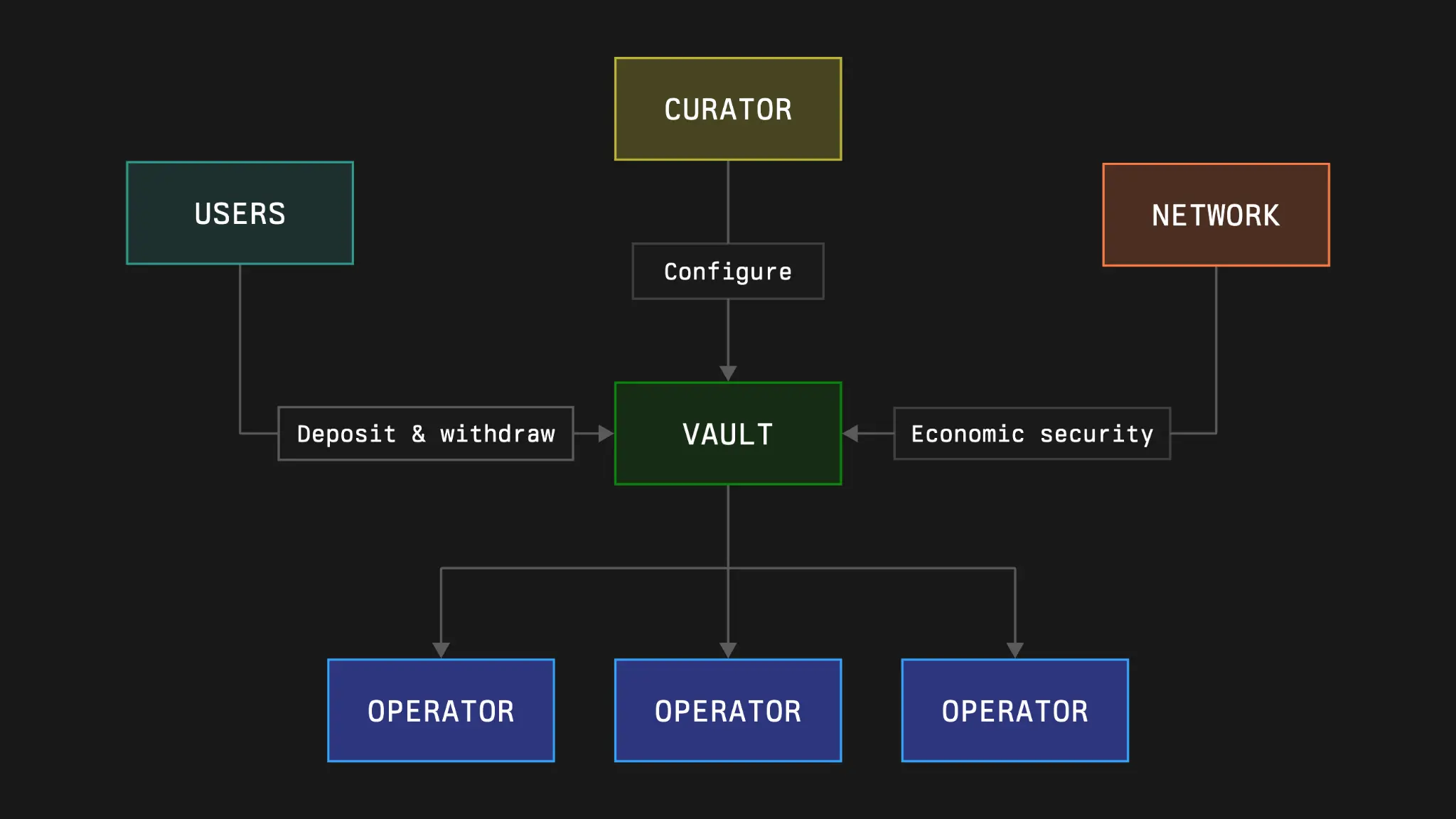
Vaults are configurable and can be deployed in an immutable pre-configured manner, or an owner can be specified to allow updates to vault parameters. Vaults are expected to be used by operators and curators (such as crypto institutions or liquidity (re)staking protocols) to create differentiated products, such as:
- Operator-Specific Vaults: Operators can create vaults to restake collateral assets into their infrastructure, applicable to any configured network. An operator can create multiple vaults with different configurations to serve their clients without additional node infrastructure.
- Curated Multi-Operator Vaults: These vaults configure restaked networks and delegation strategies as a diverse set of operators. Curated vaults can also set custom slashing limits to restrict the amount of collateral that specific operators or networks can be slashed. These committed terms need to be accepted by the networks that will accept the management services provided by the vaults.
- Immutable Pre-Configured Vaults: Vaults can be deployed using pre-configured rules that cannot be updated, providing additional protection for users who are unwilling to accept the risk of vault managers being able to add additional restaking networks or otherwise change configurations.
The vault contract consists of three main modules:
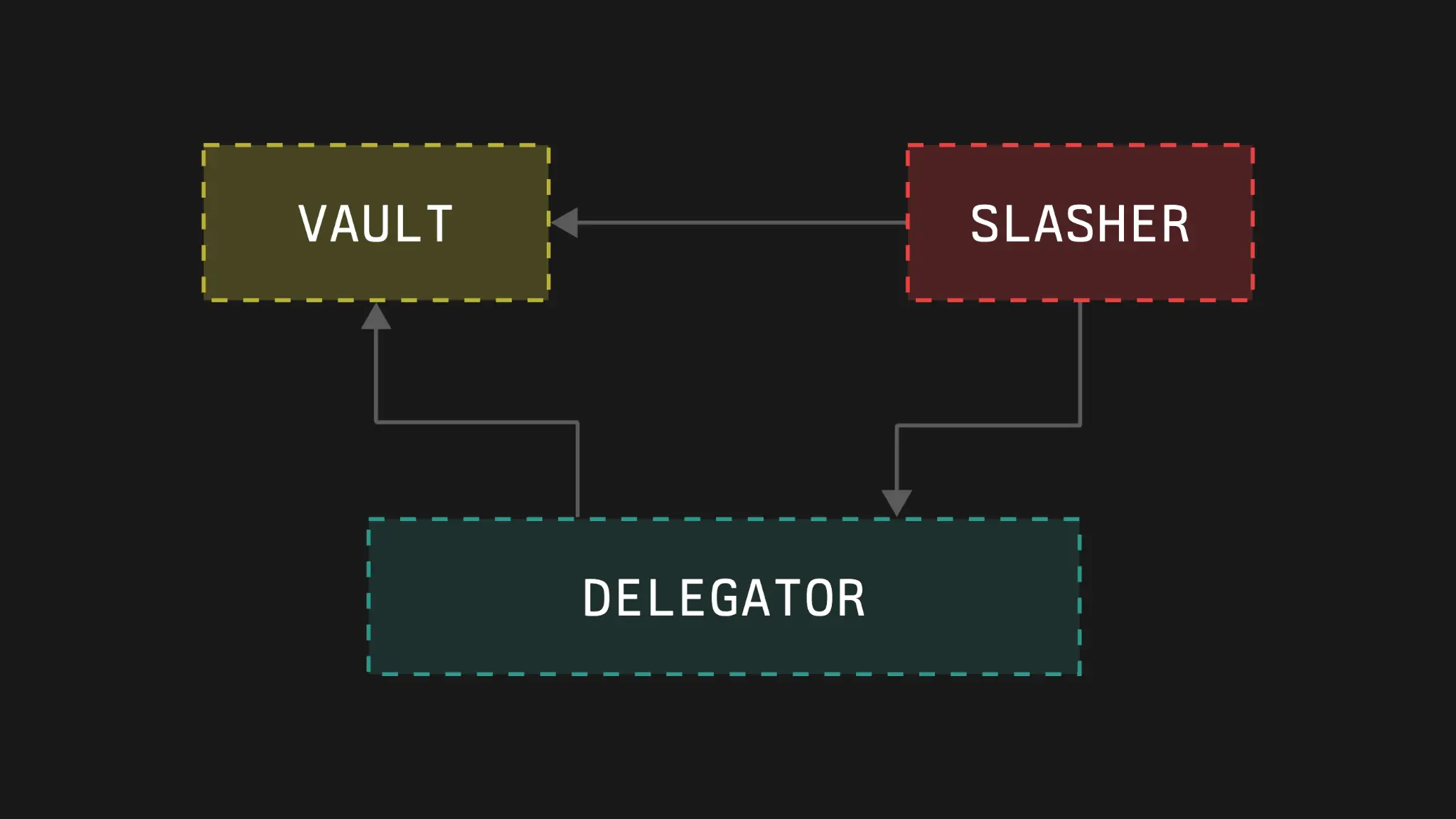
Accounting Module (Vault) This module is responsible for handling the financial transactions of the vault, including:
- Processing user deposits and tracking balances
- Managing withdrawal requests and claims
- Implementing periodic slashing accounting
All operations are conducted within a single predefined collateral token.
Limits and Delegation Logic Module (Delegator) The Delegator is responsible for handling the distribution of vault funds between the network and operators. It achieves this by:
- Allowing the network to execute staking gating (i.e., how much staking the network is prepared to obtain from the vault) without implementation on the network side
- Handling operations on staking allocations by managers
- Providing staking allocation data at any point in time
Slashing Logic Module (Slasher) The slashing module is responsible for executing penalties. Its functions include:
- Validating the validity of slashing requests
- Implementing different slashing logic processes (e.g., immediate slashing and veto slashing)
Inter-module Interaction
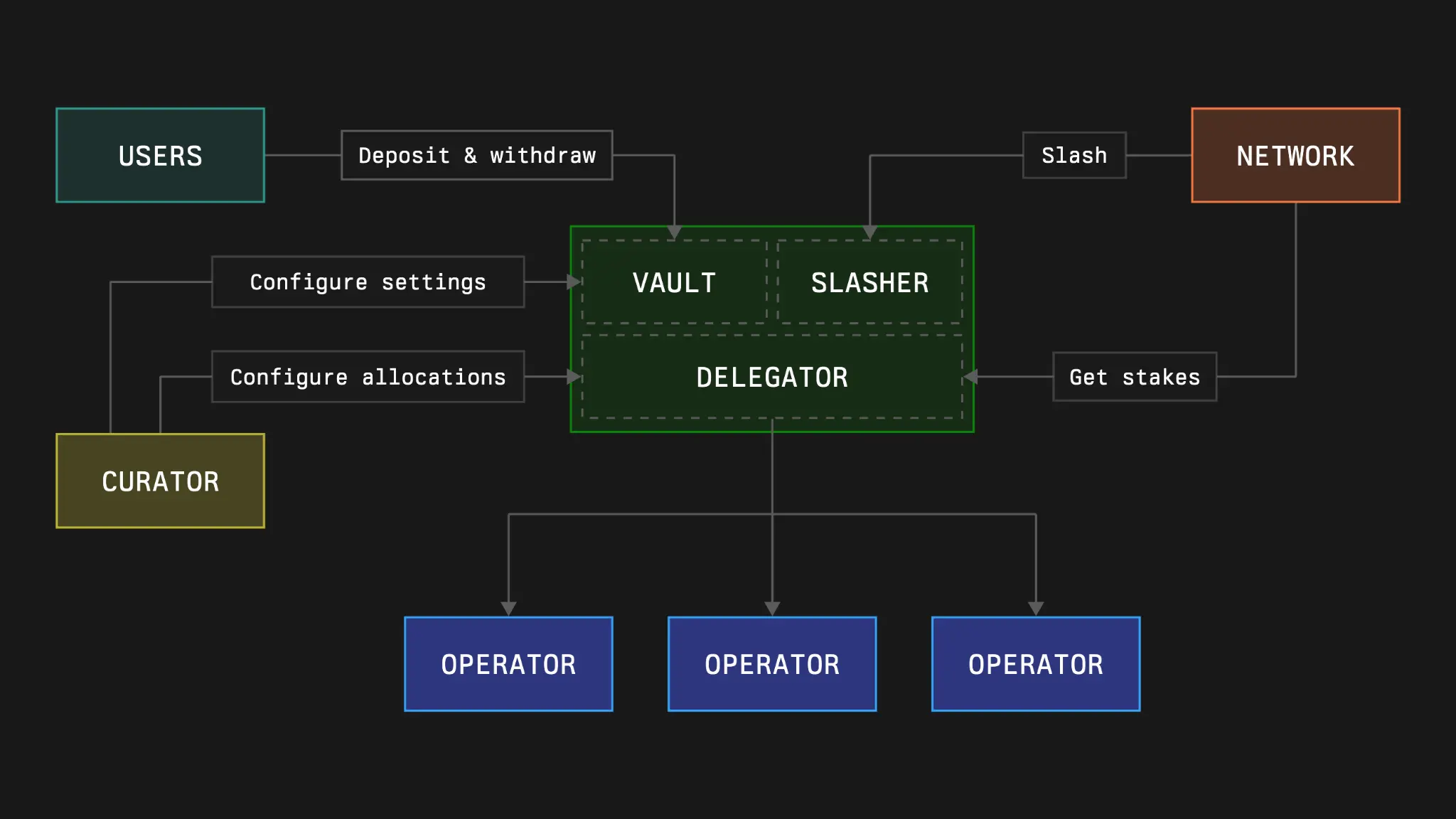
The vault module does not directly interact with other modules. However, it serves as a connection registry for other modules.
Delegation Module utilizes deposit information from the vault. This data is crucial for determining accurate staking limits and ensuring that the slashing process aligns with the current state of the vault.
When a slashing event is triggered, the slashing module queries the delegation module for the staking allocation information of the relevant operators and networks. This information is used to verify whether the proposed slashing amount exceeds the allocated staking. The slashing module then interacts with the vault to proceed with the destruction operation of the slashed funds.
- Counterparties
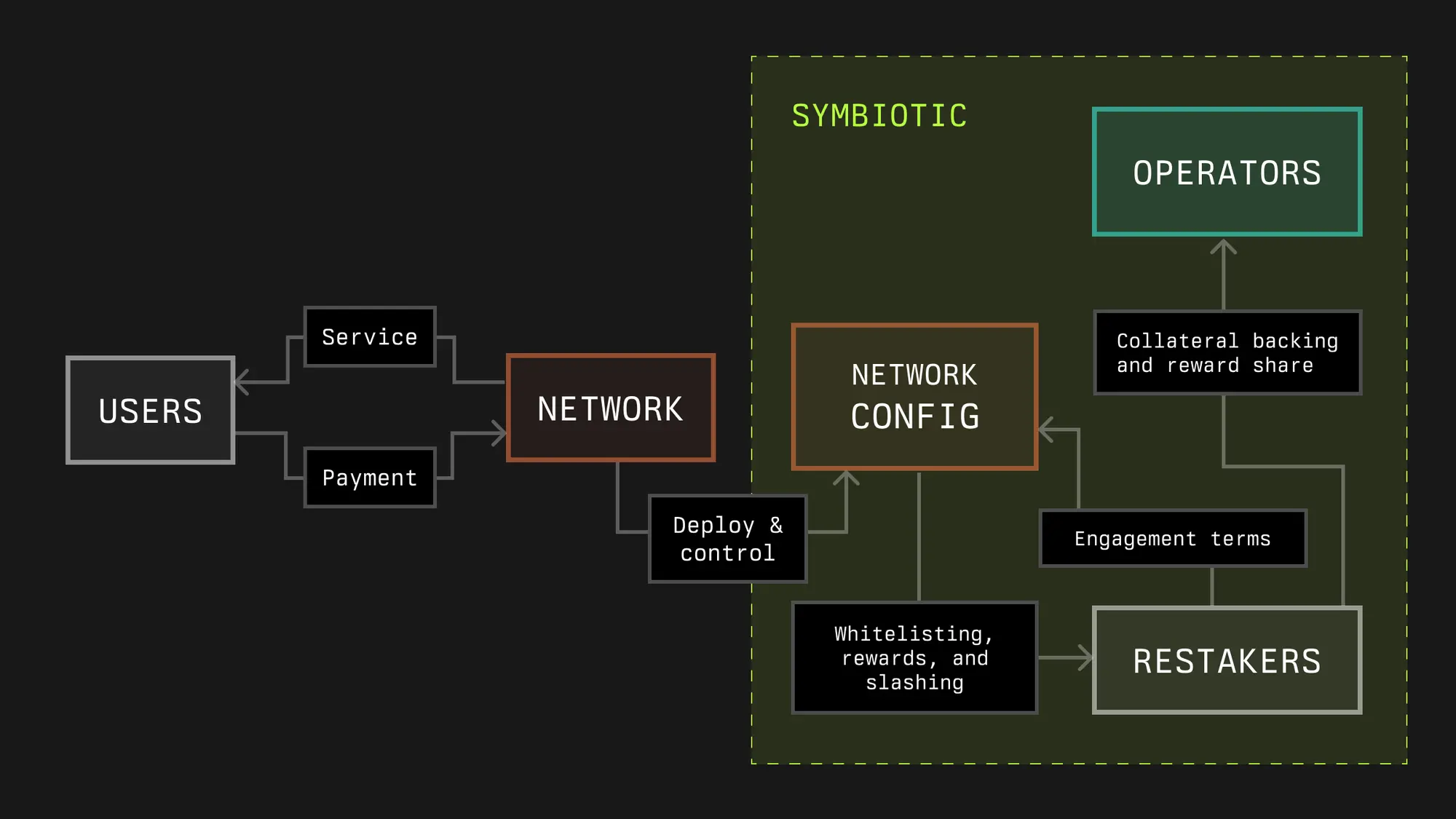
In Symbiotic, we define the network as any protocol that requires decentralized infrastructure to provide cryptoeconomic services, such as processing validation and ordering transactions, providing off-chain data to applications in the cryptoeconomy, or ensuring user interactions across networks.
Decentralized infrastructure networks can flexibly obtain security guarantees through operators and economic support via Symbiotic. In some cases, protocols may consist of multiple sub-networks, each taking on different infrastructure roles. The modular design of the Symbiotic protocol allows developers of these protocols to define the rules that participants need to choose to join, accommodating any of these sub-networks.
Summary
The advantages of Symbiotic lie in its flexibility, decentralization, security, and customizability. By introducing modular design and cross-network collateral asset management, Symbiotic provides an efficient and scalable solution for decentralized infrastructure networks. However, the complexity of its system, risk management challenges, and cross-protocol compatibility issues cannot be overlooked. Developers and operators need to fully understand the interactions and potential risks of each module when using Symbiotic to maximize its advantages and avoid possible operational errors.
## Industry Data Analysis
1. Overall Market Performance
1.1 Spot BTC & ETH ETF
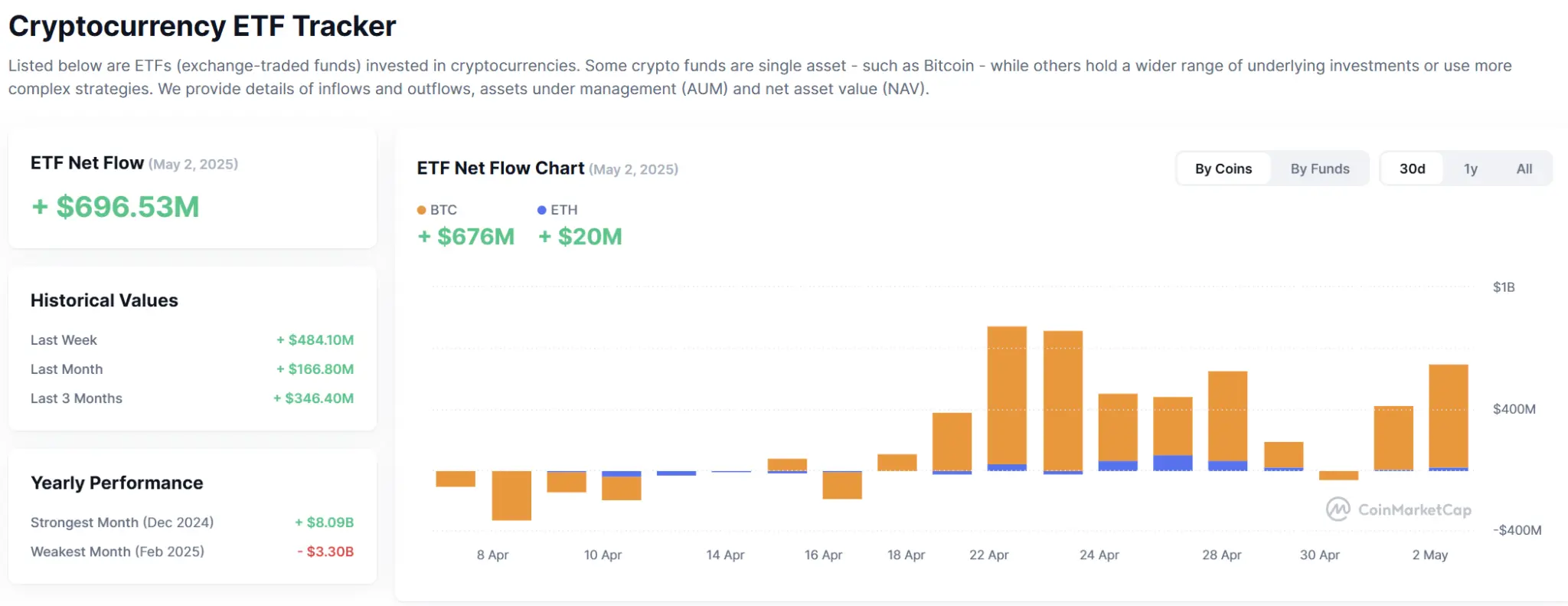
As of November 1 (Eastern Time), the total net outflow of Ethereum spot ETFs was $10,925,600.
1.2. Spot BTC vs ETH Price Trends
BTC
Analysis
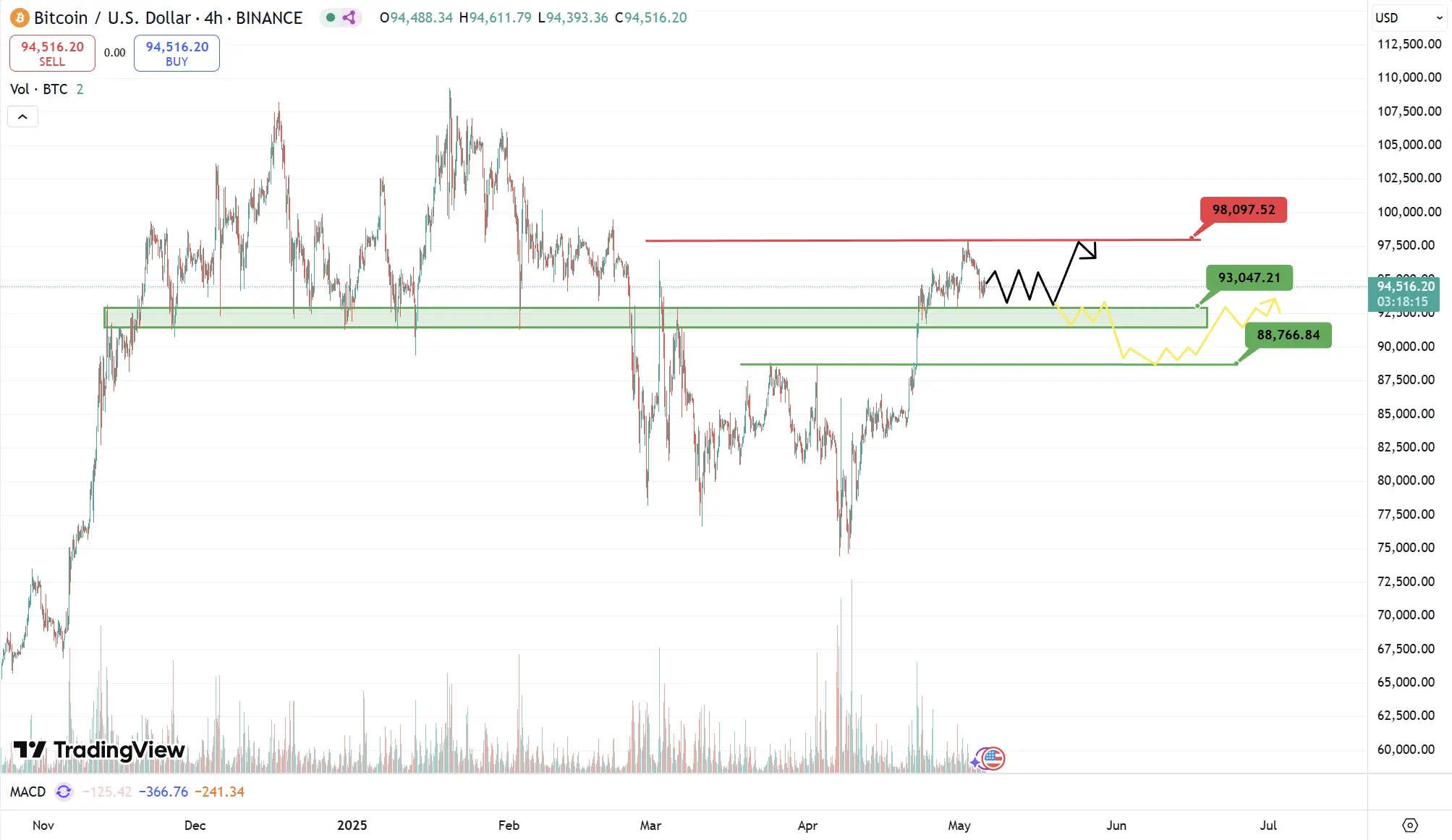
Last week, BTC entered a period of weak upward movement after a volume-reduced rebound to around $98,000. The subsequent pullback below the short-term support of $95,800 indicates that the 4H level upward pattern has been damaged. The current trend is expected to enter a narrow range of $93,000 to $97,000 in the first half of this week, with the latter half potentially breaking below $93,000 to seek support at the lower boundary of the $91,500 range, possibly stimulated by fundamentals.
If fundamental indicators continue to suggest high inflation, the probability of further decline to $88,700 will increase. Therefore, users are reminded to pay attention to the risks brought by the short-term volatility from non-farm payroll data this week.
ETH
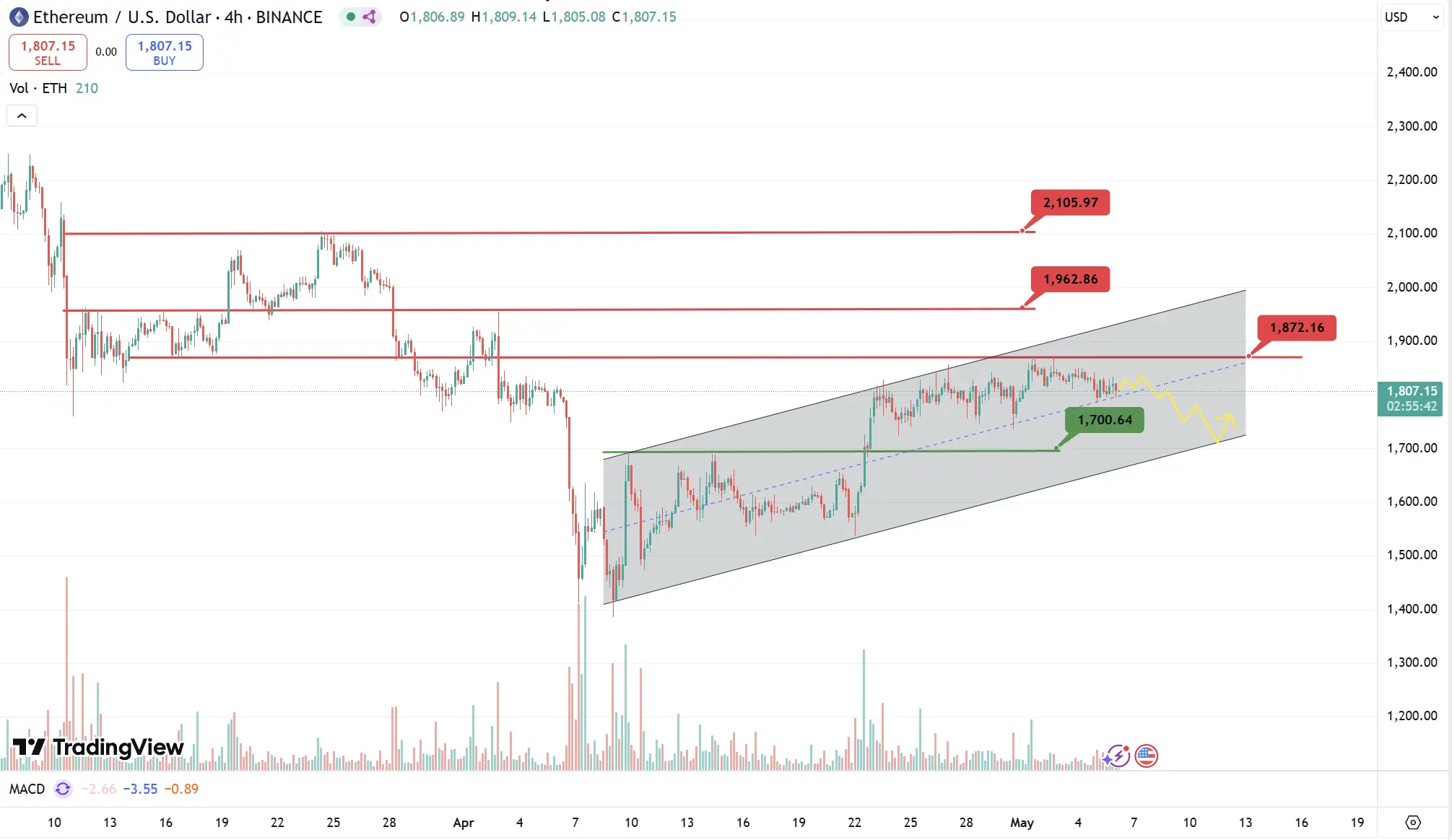
Analysis
Although ETH continued to operate along the upper half of the rising channel last week, it has shown clear signs of stagnation under the strong resistance of $1,870. Despite the price still being supported by the mid-track of the channel, the upward momentum is gradually depleting. Even if a rebound is organized later, the probability of effectively breaking through $1,870 or testing the second resistance at $1,960 is low. Conversely, if the fundamentals weaken, the likelihood of the trend breaking below the mid-track and approaching the support near $1,700 increases. However, regardless, the current rising channel pattern has not been broken, so users can still operate based on the support and resistance of the upper, middle, and lower tracks.
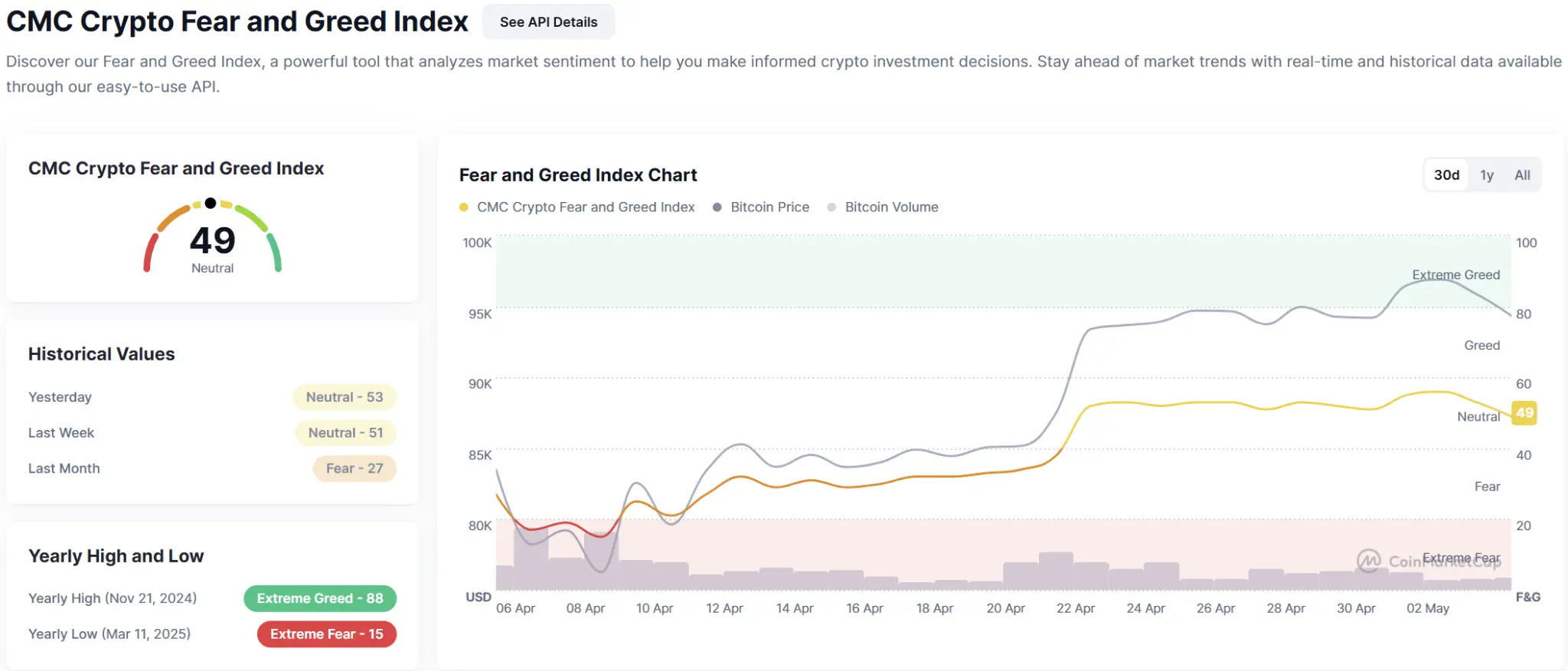
1.3. Fear & Greed Index
2. Public Chain Data
2.1. BTC Layer 2 Summary
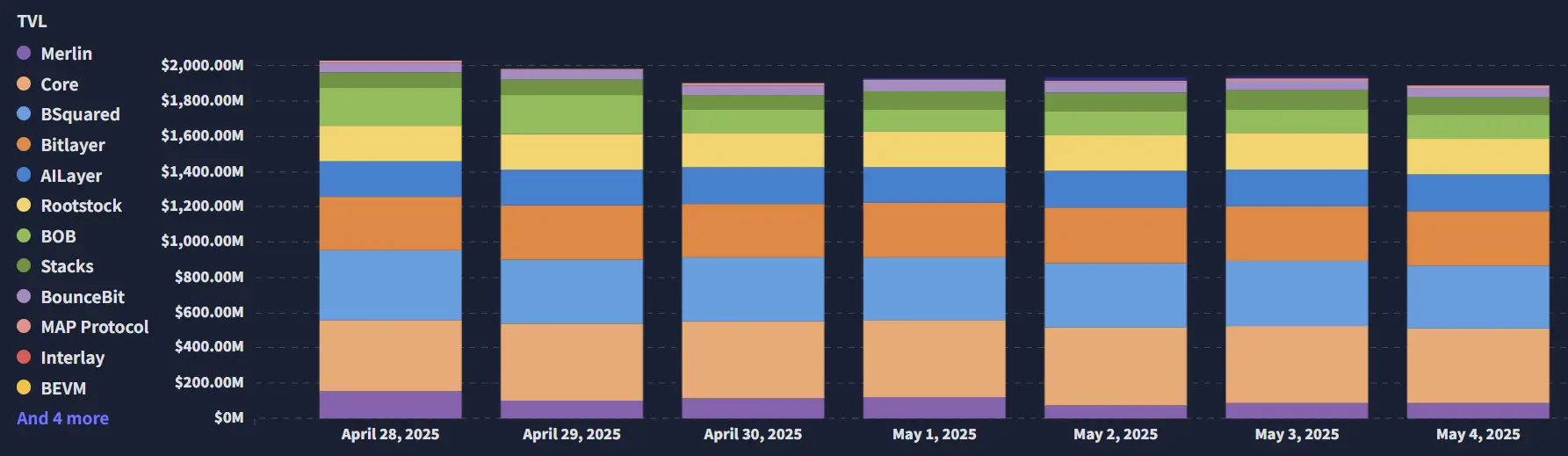
Analysis
- Stacks "Nakamoto Upgrade": Enhancing Bitcoin Layer 2 Performance
The key upgrade of the Stacks network—Nakamoto Upgrade—is scheduled to officially launch between May 15 and May 29, 2025, with core changes including:
- Finality Enhancement: Transactions on Stacks will achieve 100% finality on the Bitcoin main chain, with security consistent with Bitcoin itself, making it nearly impossible to roll back.
- Significant Throughput Improvement: Block time will be reduced from 10–30 minutes to approximately 5 seconds, greatly accelerating transaction speed and on-chain interaction experience.
- Launch of sBTC: A new asset, sBTC, pegged 1:1 to Bitcoin, will be launched, allowing Bitcoin to seamlessly participate in smart contracts and DeFi applications on Stacks.
This upgrade aims to establish Stacks as a native Bitcoin smart contract platform, further enhancing its scalability and programmability.
- Token Generation Event (TGE) of B² Network
On April 30, 2025, the Binance wallet platform hosted the TGE event for the B² Network (B2) Layer 2 solution. This network is based on ZK-Rollup technology and features:
- Scalability and Low Cost: The goal is to increase the processing capacity of the Bitcoin network by 300 times while reducing transaction costs by 50 times.
- EVM Compatibility: Supports the Ethereum Virtual Machine (EVM), enabling the deployment of smart contracts and dApps, expanding ecosystem flexibility.
- Cross-Chain and Ecosystem Integration: Collaborations with platforms like UniRouter and Particle Network enhance cross-chain interoperability and user engagement.
The TGE event received widespread market attention, with a total of 8.4 million B2 tokens allocated for future ecosystem incentives.
2.2. EVM & Non-EVM Layer 1 Summary
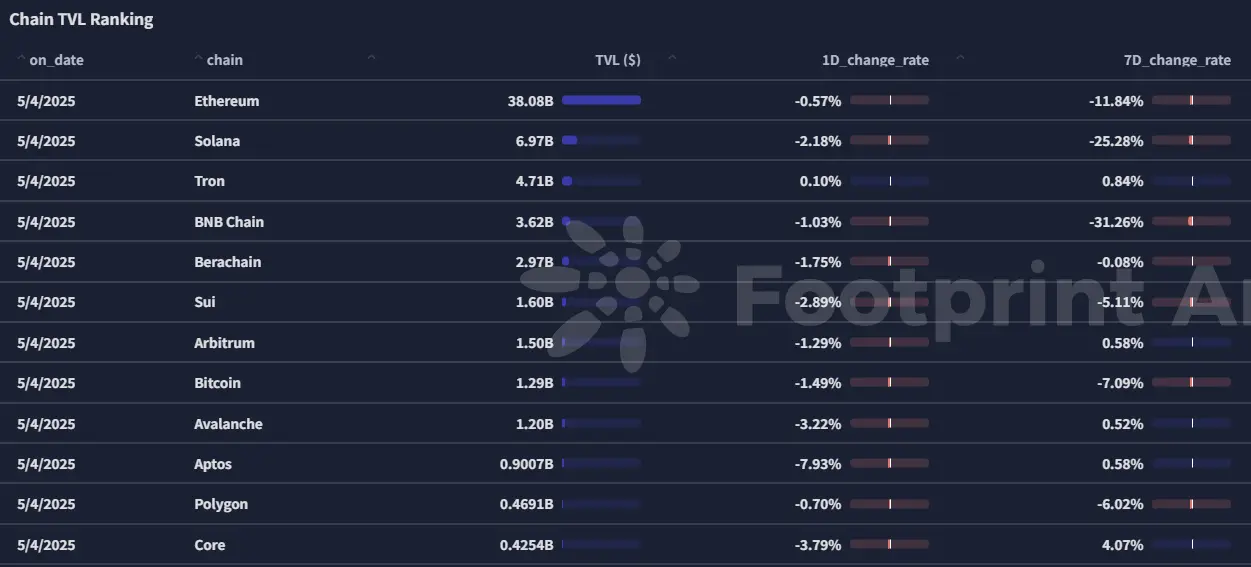
Analysis
Ethereum Ecosystem Upgrade
- Pectra Upgrade: Ethereum is implementing the Pectra upgrade, aimed at improving wallet infrastructure and addressing broader ecosystem challenges. This upgrade will redefine user interactions with Ethereum by enhancing chain abstraction and simplifying wallet experiences to improve user experience.
- Uniswap Labs Launches Unichain: Uniswap Labs has launched "Unichain," a Layer 2 solution designed to enhance user experience and address fragmentation issues on Ethereum. Unichain introduces "Rollup-Boost," a new block building mechanism aimed at speeding up transaction times and reducing MEV (Maximum Extractable Value) through a fair priority gas auction model. However, as of now, the project's appeal remains limited.
- Telos zkEVM Development
- SNARKtor Integration: The Telos Foundation announced its plan to integrate SNARKtor into zkEVM, expected to be completed by the end of 2025. This technology will leverage hardware acceleration for Rollup operations on Ethereum, enhancing scalability and efficiency.
- Ondo Chain Launch
- Institutional-Grade Blockchain: Ondo Finance has launched Ondo Chain, a Layer 1 PoS (Proof of Stake) blockchain that combines the openness of public chains with the compliance and security features of permissioned chains. This infrastructure aims to enable the tokenization of real-world assets for large-scale applications.
Non-EVM Layer 1 Highlights
- Agoric's Interoperability Breakthrough
- JavaScript Integration: Agoric simplifies blockchain development by integrating the widely used programming language JavaScript into its platform. This approach attracts a broader range of developers, fostering a more inclusive Web3 ecosystem.
- Cross-Chain Enhancements: The platform's Orchestration API reduces cross-chain USDC transfer times from 16 minutes to 2 minutes. Additionally, collaborations with Native and Union facilitate trustless bridging between Cosmos and major EVM chains like Ethereum and Arbitrum.
- Polkadot's 2025 Roadmap
- EVM and Solidity Support: Polkadot's 2025 roadmap includes support for EVM and Solidity, enhancing compatibility with Ethereum-based projects.
- XCM v5 and Elastic Scalability: The introduction of XCM v5 aims to improve cross-chain messaging, while a multi-core architecture will increase processing capacity to meet growing on-chain demands.
- SPID-Chain's Interoperability Solution
- DAG-Based Architecture: SPID-Chain employs a Directed Acyclic Graph (DAG) structure, facilitating seamless integration between multiple blockchains. This design enhances interoperability and scalability within the Web3 ecosystem.
2.3. EVM Layer 2 Summary
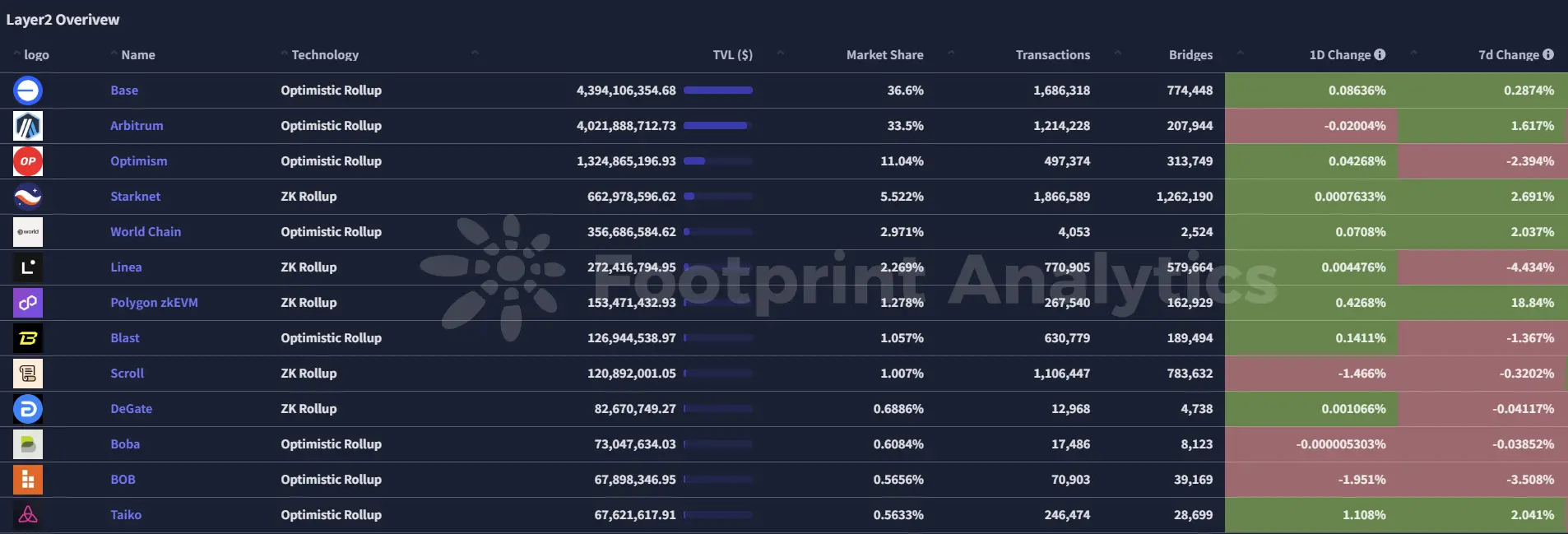
Analysis
Ethereum Pectra Upgrade Approaches: The Pectra hard fork for Ethereum is scheduled to go live on the mainnet on May 7. This upgrade will increase Layer 2 throughput, support more transaction processing, and optimize Blob data storage mechanisms to reduce transaction costs. Additionally, the Historical State Expiry feature will be enabled to alleviate node storage pressure.
Celo Completes Migration to Ethereum Layer 2: Celo has successfully migrated from an independent Layer 1 blockchain to the Ethereum Layer 2 network, utilizing Optimism's OP Stack and EigenDA protocol. This transition enhances its security, scalability, and interoperability with the Ethereum ecosystem.
DTVM Smart Contract Execution Framework Released: A research team has launched the Deterministic Virtual Machine (DTVM) framework, aimed at addressing performance and determinism issues in smart contract execution. This framework is compatible with EVM ABI and supports multi-language development, such as Solidity, Rust, and Go, significantly improving execution efficiency.
## Macroeconomic Data Review and Key Data Release Points for Next Week
The U.S. GDP for the first quarter of 2025 contracted at an annualized rate of 0.3% (actual year-on-year growth rate of 2%), marking the first negative growth in three years, primarily dragged down by a surge in imports and a marginal weakening in consumption. The expectation of tariffs led businesses to "rush imports," causing the annualized rate of imports to soar by 41.3%, with net exports dragging GDP down by 0.9 percentage points.
Important macroeconomic data points for this week (May 5 - May 9) include:
May 8: U.S. Federal Reserve interest rate decision (upper limit) as of May 7.
## Regulatory Policies
European Union (EU)
Establishment of the Anti-Money Laundering Authority (AMLA)
- April 28, 2025: The EU published a briefing document detailing the background, governance structure, and extensive regulatory powers of the AMLA. The AMLA is set to officially operate from January 2028.
- The AMLA will coordinate the regulatory authorities of member states, directly supervise high-risk entities, and establish binding technical standards to ensure a unified AML/CFT regulatory framework across Europe.
United Kingdom (UK)
Regulatory Draft for Crypto Exchanges and Dealers
- April 29, 2025: The UK government proposed a legislative draft under the Financial Services and Markets Act 2000, which for the first time includes cryptocurrency exchanges, dealers, and brokers under regulatory oversight, requiring them to comply with transparency, consumer protection, and operational resilience requirements.
Exemption Rules for Stablecoin Issuers
- April 29, 2025: Chancellor Rachel Reeves announced that the UK will only require "local stablecoin issuers" to obtain approval from the Financial Conduct Authority (FCA), while overseas issuers will be exempt, aiming to align with proposed regulations in the U.S.
Treasury Releases Draft of the Crypto Asset Order
- April 29, 2025: The UK Treasury released a draft bill titled "Financial Services and Markets Act 2000 (Regulatory Activities and Miscellaneous Provisions) (Crypto Assets) Order 2025," accompanied by a policy statement.
- This draft aims to bring crypto asset-related activities under regulatory oversight, requiring service providers and issuers to undergo suitability assessments, comply with prudential regulatory requirements, and be subject to sanctions authority granted by the FCA.
United States (USA)
SEC Clarifies Disclosure Requirements for Crypto Asset Securities
- April 29, 2025: The U.S. Securities and Exchange Commission (SEC) Division of Corporation Finance issued a statement clarifying that issuers of crypto asset securities must disclose detailed information, including network development progress, governance structure, and token holder rights (such as dividends, profit sharing, voting rights, etc.).
- This disclosure guideline aims to standardize market practices, enhance investor protection, and reduce legal uncertainties in the token issuance process.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




