This article will interpret the core content of the report, helping readers quickly grasp key information and enhance their understanding and response capabilities regarding these complex security threats.
Source: United Nations Office on Drugs and Crime (UNODC)
Written by: Lisa
Edited by: Liz
On October 7, 2024, the United Nations Office on Drugs and Crime (hereinafter referred to as "UNODC") released a report titled Southeast Asia's Transnational Organized Crime and the Convergence of Cyber Fraud, Underground Banking, and Technological Innovation: An Evolving Threat Landscape. UNODC thanked SlowMist for the information, data, and analytical support provided in the report, and our partner Bitrace was also acknowledged.
This report is the latest analysis by the United Nations Office on Drugs and Crime (UNODC) on transnational organized crime in Southeast Asia, continuing the comprehensive report released in 2019 titled Transnational Organized Crime in Southeast Asia: Evolution, Growth, and Impact. The latest report mainly includes three aspects: an overview of developments in Southeast Asia, underground banking and money laundering activities, and technological innovations that facilitate criminal activities. Specifically, the report focuses on the characteristics and evolution of organized crime in Southeast Asia, particularly drug trafficking and money laundering activities related to casinos and special economic zones; it also provides a detailed analysis of the major threats and risks posed by the proliferation of casinos and the complex money laundering methods employed by organized crime groups, such as how the rise of online gambling and electronic betting has changed the landscape of underground banking and money laundering; the report also offers a series of recommendations aimed at assisting national governments and international partners in better addressing the rapid development of casinos and organized crime in Southeast Asia. This article will interpret the core content of the report, helping readers quickly grasp key information and enhance their understanding and response capabilities regarding these complex security threats.
Key Point 1: Overview of Developments in Southeast Asia
Southeast Asia is facing unprecedented challenges from transnational organized crime and the illegal economy. The rapid development of physical, technological, and digital infrastructure in the region has provided organized crime networks with more opportunities to expand, covering a variety of activities including drug production and trafficking, illegal gambling, forced labor trafficking, prostitution, and money laundering. Places such as casinos, hotels, and special economic zones have become "hotbeds" for these illegal activities, further exacerbating governance challenges in border areas.
1. Gambling and Criminal Activities
Over the past decade, the casino industry in Southeast Asia has experienced exponential growth, with more than 340 licensed and illegal casinos currently in operation. Although increased regulatory efforts in Macau, China, have led to the closure of some casinos, the gambling market in Southeast Asia remains active, especially in online gambling. The vast majority of casinos in the lower Mekong countries are located in border areas adjacent to China, Thailand, and Vietnam, where gambling activities are mostly illegal. Speaking of gambling intermediaries, they play a significant role in Southeast Asia's gambling industry. However, due to the pandemic and increased law enforcement, many intermediaries are facing challenges with declining profits. The founders of the two largest gambling intermediaries, Sun City and Tak Chun, were sentenced for money laundering and organized crime, marking one of the most serious money laundering and underground banking cases in recent years, with sentences of 18 years and 14 years respectively, on hundreds of charges related to organized crime and illegal gambling, having processed over $100 billion through casinos, online gambling platforms, and underground banks.
Despite enhanced law enforcement efforts, online fraud remains rampant, with estimated economic losses from scams targeting East Asian and Southeast Asian victims ranging from $18 billion to $37 billion in 2023. With the rise of high-risk virtual asset service providers (VASPs), cybercriminals are increasingly using cryptocurrencies for money laundering, commonly exchanging illicit proceeds for cash or converting them into USDT as a stable intermediary currency on over-the-counter trading markets. This activity involves massive transaction volumes and is linked to various criminal activities, posing significant challenges for governments in regulating and combating money laundering. It was found that a high-risk VASP located in the Mekong region processed a total cryptocurrency transaction volume of $49 billion to $64 billion from 2021 to 2024, making it the largest service provider of its kind in the Asia-Pacific region, and it has conducted transactions with OFAC-sanctioned entities and multiple wallets associated with the Lazarus Group, a notorious hacking organization that plays a significant role in cryptocurrency-related money laundering activities. According to SlowMist's analysis, the money laundering methods of North Korean hackers in the Lazarus Group are complex and varied, with new laundering methods emerging periodically; for more details, refer to SlowMist: 2024 First Half Blockchain Security and Anti-Money Laundering Report (https://www.slowmist.com/report/first-half-of-the-2024-report(CN).pdf).
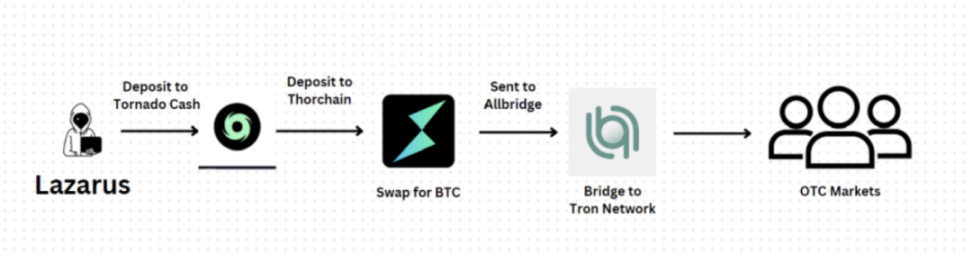
The report also mentions that in recent years, stablecoins have become increasingly popular not only among legitimate users but also among criminal groups, particularly those involved in cyber fraud. This aligns with findings from East Asian and Southeast Asian authorities: stablecoins, especially Tether (USDT) on the TRON (TRX) blockchain, are the preferred choice for Asian criminal groups engaged in cyber fraud and money laundering activities.
2. Regional Cyber Fraud
In recent years, independent scam gangs have been replaced by larger, more unified criminal groups that often disguise themselves as industrial or technology parks, forming stable networks. For example, KK Park in Myanmar has shown signs of development since early 2020 and has become one of the largest and most active crime hubs in the region over the past four years. At the same time, the popularity of cryptocurrencies has made cross-border transactions more convenient, allowing cyber fraud activities to expand globally, especially by exploiting law enforcement's lack of understanding of their operational methods, engaging in activities such as "pig butchering" scams, investment fraud, job scams, and asset recovery scams; for more details, refer to Report Interpretation | FBI Releases 2023 Cryptocurrency Fraud Report.
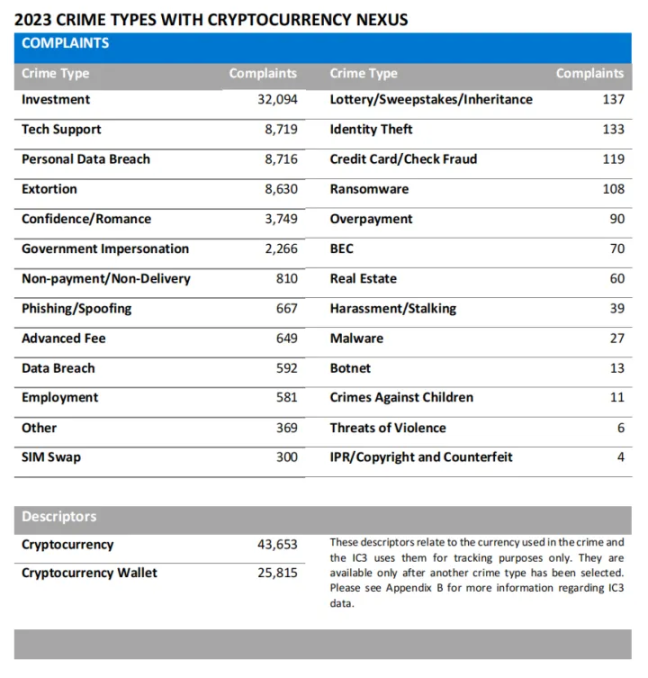
The targets of scammers are becoming increasingly broad, especially focusing on young people and the Chinese community. Scam organizations typically have a complex pyramid structure, including multiple departments such as recruitment, finance, and operations, requiring collaboration among various parties for their operations. Over the past year, the landscape of scams has also changed, with data showing that 43% of the inflow of scams this year has gone to newly active wallets, compared to only 29.9% in 2022, indicating a rapid increase in new types of scams.
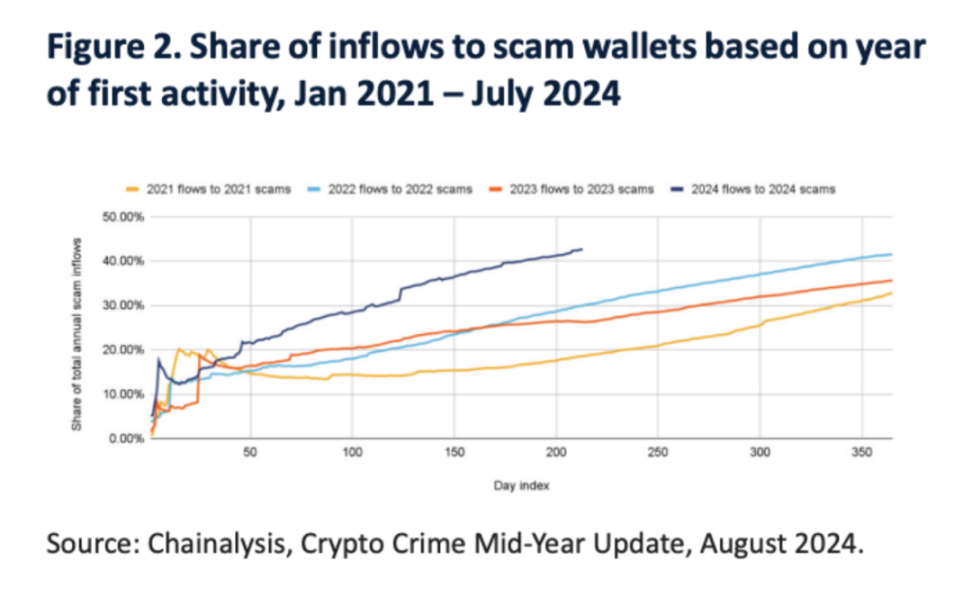
From 2020 to the present, the average active days of scam activities have significantly decreased, from an average of 271 days in 2020 to 42 days in the first half of 2024.
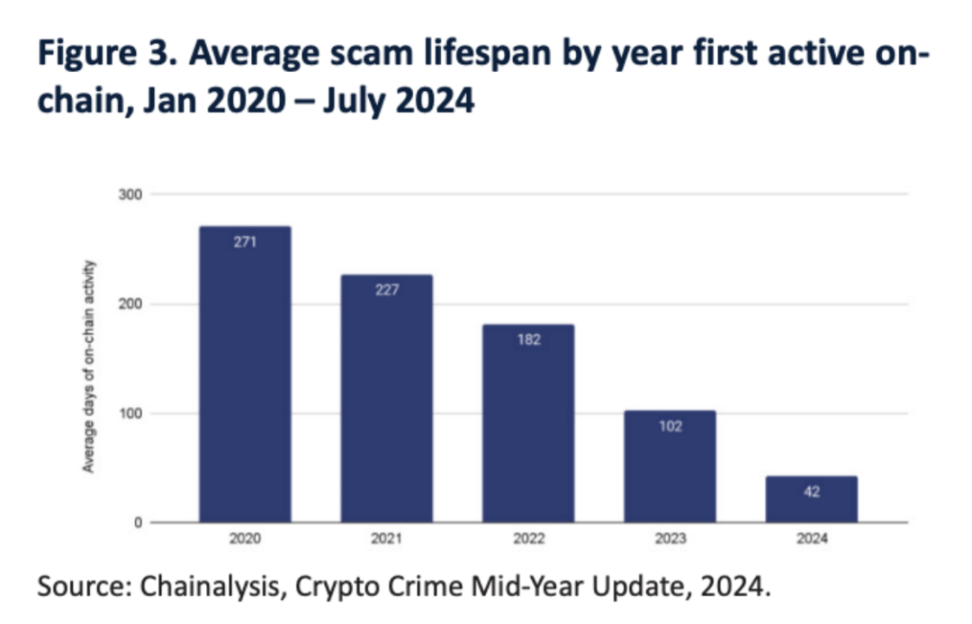
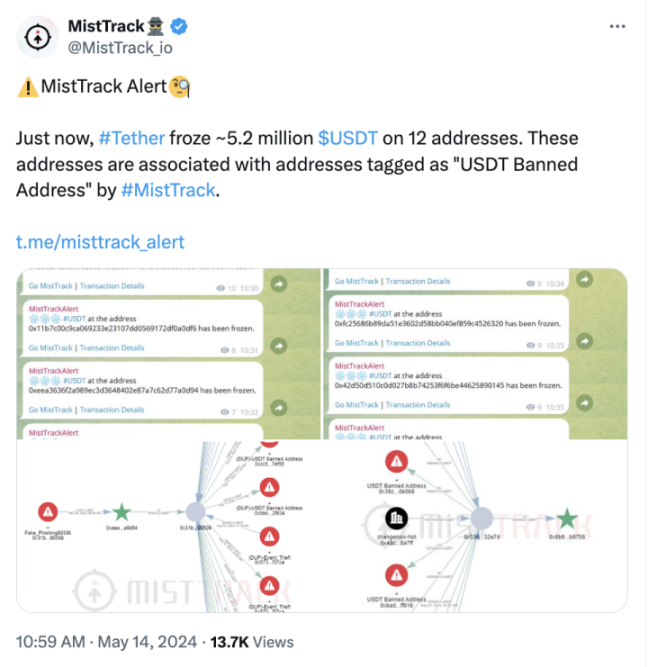
This macro trend aligns with the shift of scammers from meticulously planned large-scale scams to more targeted activities, partly due to increased law enforcement efforts and the growing number of stablecoin issuers blacklisting scam addresses. For instance, on May 14, the on-chain tracking and anti-money laundering platform MistTrack detected that Tether, the world's largest stablecoin issuer, froze 5.2 million USDT related to phishing.
3. Human Trafficking and Forced Labor
Traffickers deceive and coerce victims into participating in criminal activities for economic gain. Victims are often deprived of their freedom after being trafficked, with their passports confiscated and facing violence and various threats. Although the nature of forced trafficking has not changed, the professionalization of the industry has blurred the lines between victims and voluntary participants, creating multiple categories of related individuals.
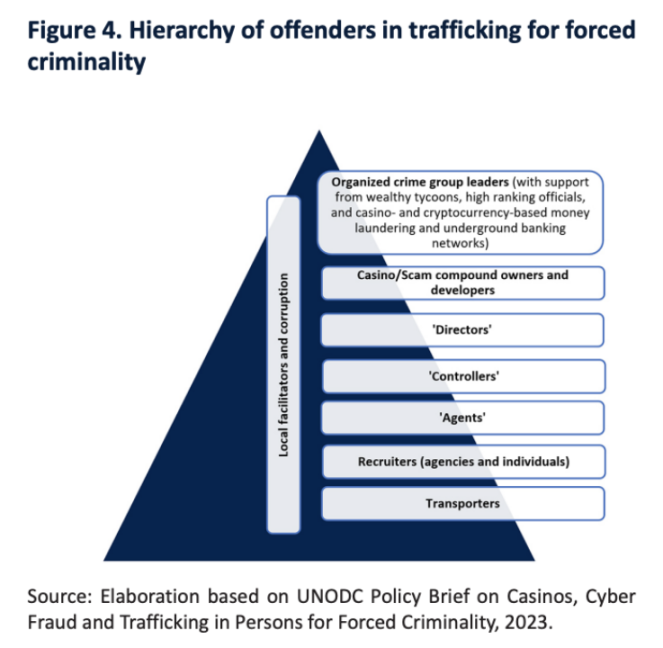
In some areas, especially in Myanmar, victims are often forced to sign false contracts and work to repay high "debts"; these contracts are not legally binding and conceal the traffickers' criminal activities. Many victims still face legal risks after escaping or being rescued, potentially facing prosecution or intimidation.
4. Law Enforcement Actions
Although countries have taken a series of measures to combat these activities, online gambling and fraud remain prevalent. Moreover, the intensity and effectiveness of law enforcement vary among countries, with measures including the arrest of suspects, freezing of accounts, and blocking of websites. Cross-border cooperation has led to the seizure of some assets, and the number of convictions of criminals has increased, particularly with the rise in raid actions targeting scam centers and gambling operators.
The table below compiles some of the most prominent law enforcement actions taken against illegal online gambling and cyber fraud activities since January 2023, based on statements from law enforcement agencies in various regions. These raid actions are led by local law enforcement agencies, sometimes in collaboration with regional law enforcement. Chinese public security authorities have played a significant role in several of these actions.
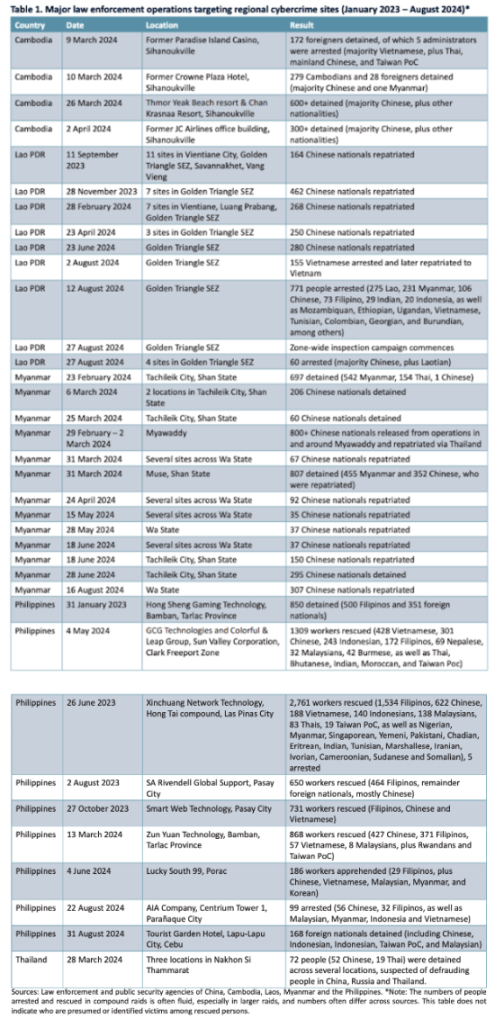
According to statistics from the Ministry of Public Security of China, from January to November 2023, a total of 391,000 telecom network fraud cases were cracked, with 79,000 criminal suspects arrested, including 263 main offenders. In 2023, more than 50,000 people were prosecuted for telecom network fraud. The new "Anti-Telecom Network Fraud Law," enacted in 2022, stipulates the responsibilities of service providers in telecommunications, the internet, and finance, including raising customer awareness and monitoring, preventing, and reporting suspicious activities.

Over the past year, Chinese media have extensively reported on the legal proceedings of individuals suspected of participating in illegal online gambling and cyber fraud, with cases occurring both domestically and abroad. Prosecutorial agencies have also released multiple reports, including summaries of typical cases involving individuals voluntarily or forcibly repatriated from Cambodia, the Philippines, Laos, Myanmar, Malaysia, and other countries. In China, law enforcement actions have focused on individuals providing support to overseas organizations, including those developing software, maintaining websites, and providing technical support, as well as underground banking networks facilitating the transfer of funds obtained from cybercrime and individuals selling account information to money laundering groups for use as mule accounts. Law enforcement actions have also targeted gangs smuggling Chinese citizens across borders by land and sea.
Key Point 2: The Rise of Underground Banking, Money Laundering, and Crime-as-a-Service
Transnational organized crime groups in East Asia and Southeast Asia have almost become market leaders in underground banking, informal cross-border value transfer, and money laundering. These groups are becoming increasingly sophisticated, adapting to and exploiting changes in the political and business environment as well as technological innovations, particularly in the fields of casinos and online gambling. They have established complex underground money laundering networks by integrating information, finance, and blockchain technology.
In addition, insufficient regulation and the rise of unauthorized virtual asset service providers (VASPs) have exacerbated the current situation. More specifically, the surge of high-risk exchanges, over-the-counter (OTC) services, large peer-to-peer (P2P) traders, and other related businesses controlled and promoted by transnational organized crime has fundamentally changed the criminal landscape in Southeast Asia, driving the expansion of the illegal economy and attracting new types of service providers and business models. Large transnational crime groups based in Hong Kong, Macau, and Taiwan, in particular, dominate the money laundering industry, closely collaborating with intermediaries to circumvent capital controls by utilizing credit services provided by intermediaries while relying on unregulated payment companies for fund transfers.
In recent years, law enforcement agencies in East Asia and Southeast Asia have also strengthened their monitoring of third-party payment providers, but many cases show that cyber fraud still has a significant impact on this industry. In the online gambling industry, unregulated casinos and gambling intermediaries have become important infrastructures for money laundering. They obscure the sources of funds through "custodial" transactions and "investments," forming complex money laundering methods. Due to the anonymity of online gambling and the non-face-to-face nature of transactions, the flow of funds becomes very difficult to trace, facilitating organized crime.
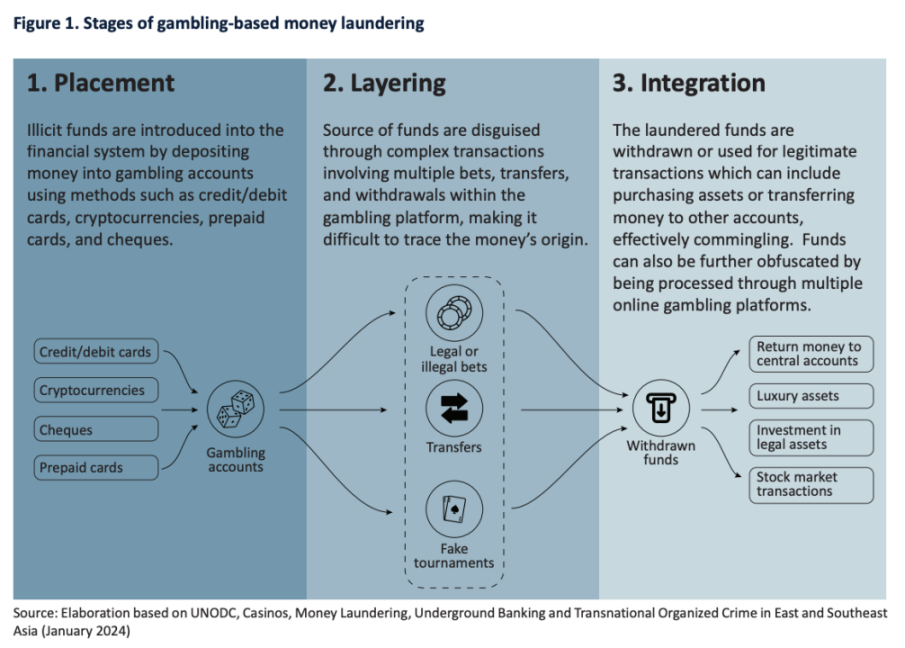
At the same time, Southeast Asia's offshore online gambling industry is developing rapidly, especially in regions with relatively weak regulation. Intermediaries leverage this trend to help organized crime generate profits, disguising illegal funds as legitimate earnings through money laundering. Although regulatory and enforcement efforts are gradually strengthening, many online gambling platforms continue to thrive in the "gray" or "black" markets. Transnational organized crime has also begun to integrate cryptocurrencies into their operations, particularly evident in high-risk exchanges and OTC transactions. Due to the lack of regulation, these platforms have become hotbeds for money laundering, allowing criminal networks in East Asia and Southeast Asia to easily evade oversight and further support their illegal activities.
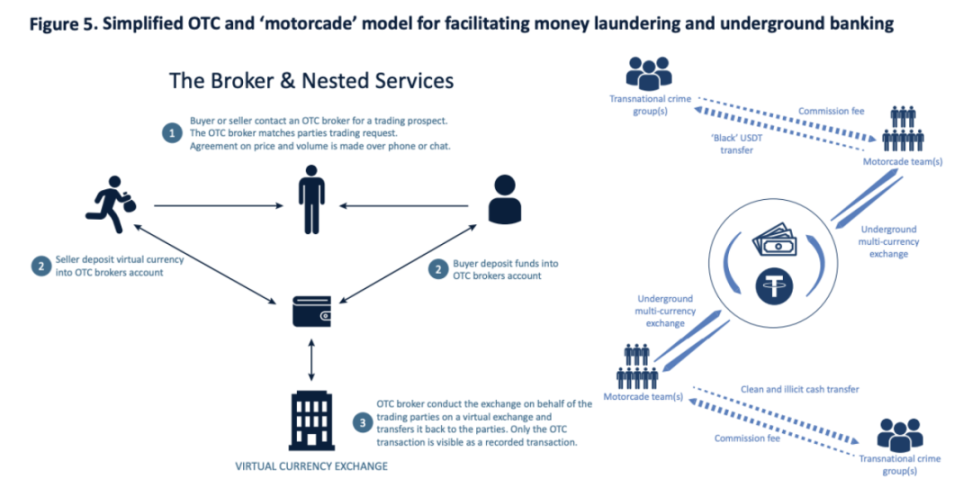
Key Point 3: The Development of Cyber Fraud and Technological Innovation
In recent years, cybercrime activities in East Asia and Southeast Asia have significantly increased, particularly with the rising activity of transnational organized crime groups. Cybercriminals not only behave like legitimate businesses in developing and selling criminal services but also adopt a "Crime-as-a-Service" (CaaS) model, outsourcing various criminal activities to others, thereby lowering the barriers to committing crimes.
1. Underground Data Markets and Information Theft Malware
Underground data markets have also become an important part of cyber fraud groups, providing a large amount of stolen data, including banking information, credit card details, and personal identification information. Among these, information required for Know Your Customer (KYC) is particularly popular in underground markets, with criminals using this data for identity theft, commercial fraud, and money laundering activities.
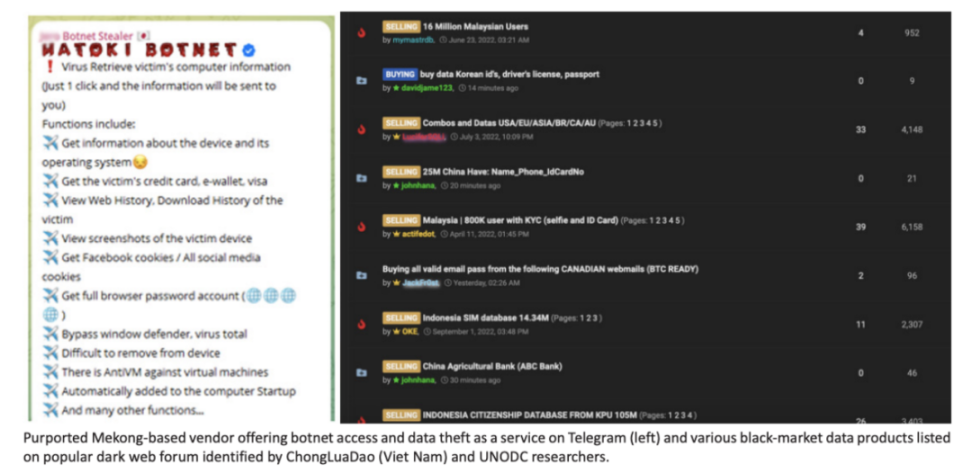
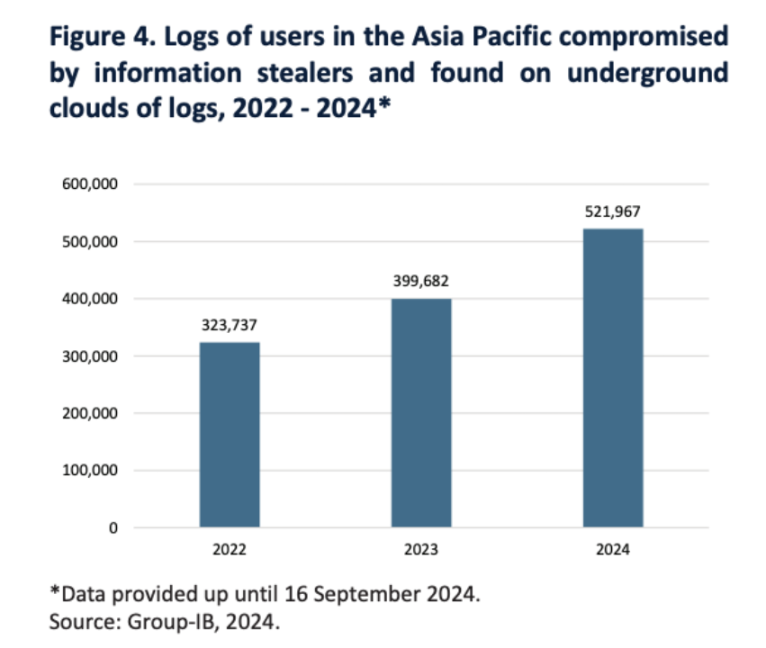
There is strong evidence that underground data markets are shifting to Telegram, with the surge of information theft malware and underground logging cloud (UCL) services at the core of this transition in the thriving criminal ecosystem in Southeast Asia. The simplicity, availability, and low cost of information theft programs make them particularly popular among criminals in the region. These tools are typically accessed through a Malware-as-a-Service (MaaS) model, where developers provide licenses to others. This growing data channel creates numerous new opportunities for transnational organized crime in the region, which in turn diversifies the strategies, techniques, targets, and criminal groups involved in cyber fraud. Relevant data shows that the number of infected hosts with information theft programs for sale in the Asia-Pacific region continues to increase, consistent with the trend of a surge in cyber fraud incidents in the region.
2. Search Engine Optimization and Fraudulent Advertising
While many cyber fraud schemes require detailed target analysis and direct contact between fraudsters and potential victims, some simple scams can easily deceive victims with just an enticing advertisement, a fake webpage, or a phishing link. These criminals widely exploit search engine optimization (SEO) poisoning and deceptive advertising to achieve these goals, and both methods have proven effective with the increasing use of global search engines and social media. In terms of scale, Google alone blocked or removed 206.5 million ads in 2023 that violated its paid advertising false statement policy, including ads related to cyber fraud and scams, an increase from 142 million ads in 2022.
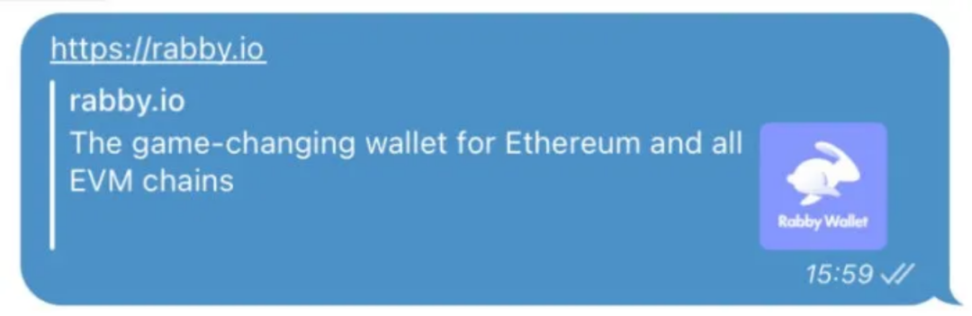
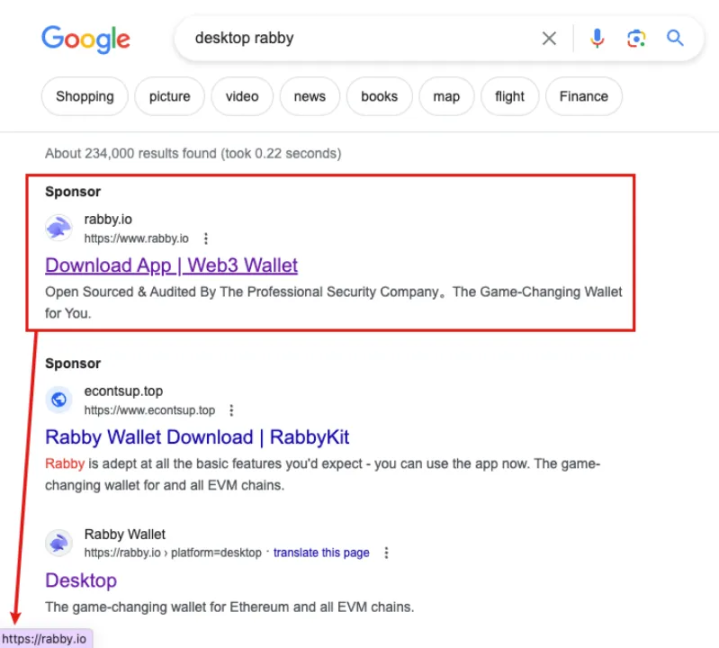
In March of this year, the SlowMist security team and the Rabby Wallet team disclosed a phishing attack technique that utilizes Google Ads. Specifically, the Rabby Wallet team did not purchase any Google ads; however, fake ads redirected to the legitimate official website. According to the keyword search results on Google, the top two search results were phishing ads, but the link of the first ad was unusual, showing the official website address of Rabby Wallet, rabby[.]io. Tracking revealed that phishing ads sometimes redirected to the actual official address rabby[.]io, while after multiple proxy changes to different regions, they redirected to the phishing address rebby[.]io, which would update and change. Analysis found that the key operation involved the phishing gang exploiting Google’s own Firebase short link service's 302 redirection to deceive Google’s display. Similar phishing tactics have also appeared on various chat software. For example, in the Telegram chat application, when a URL link is sent during a chat, Telegram's backend fetches the URL link's domain name, title, and icon for preview display.
Additionally, criminals also use SEO poisoning techniques to increase or enhance the visibility of their malicious websites, making them appear more legitimate in the eyes of unsuspecting users, as users perceive the hot rankings of search engines as credible. Criminals also employ various SEO poisoning techniques, such as so-called domain squatting, profiting from users inadvertently entering addresses or clicking on links with misspelled URLs. Social media platforms have also become their new battleground, with criminals deceiving users through ads disguised as legitimate promotional materials. In September 2023, Singaporean authorities confirmed that at least 43 victims lost $875,000 due to malware scams from social media ads.
3. AI-Driven Fraud
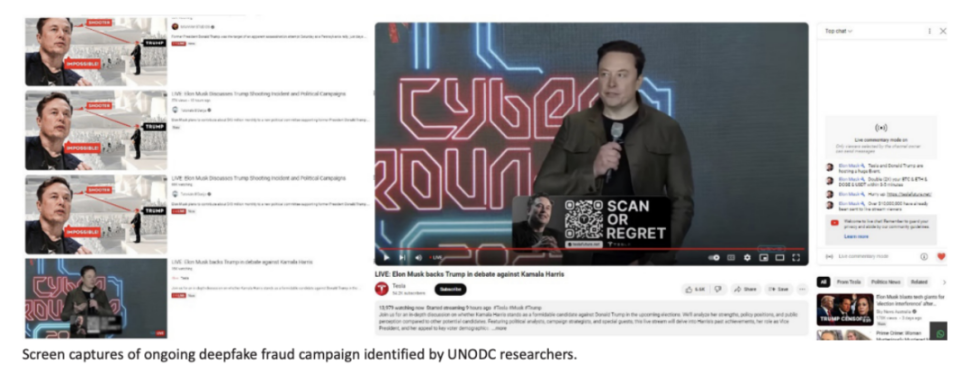
With the popularity of generative artificial intelligence, the complexity of criminal activities has increased, and issues such as identity theft and data privacy violations pose threats to national security. Criminal groups utilize AI for phishing, creating false identities, and personalized fraud, significantly lowering the technical barriers and increasing the speed and scale of fraud. Deepfake technology is widely used in cyber fraud, with criminals employing forged videos and audio for complex scams, leading to a substantial rise in corresponding criminal activities. Online fraud involving QR codes is also on the rise, with victims often being lured to visit malicious websites or disclose sensitive information. Overall, the widespread application of artificial intelligence has exacerbated the complexity and frequency of cybercrime.
4. Others
Although "pig butchering" scams remain popular, criminal groups are gradually adopting more complex strategies, such as phishing and malicious smart contracts, which can efficiently steal victims' funds and data.
This asset depletion technique requires victims to unknowingly connect their cryptocurrency wallets to malicious contracts, thereby transferring cryptocurrencies and NFTs to the criminals' wallets. A notable case is the phishing attack launched by criminals against users of the non-fungible token (NFT) marketplace OpenSea in 2022, resulting in the theft of over 250 NFTs valued at approximately $2 million. According to security researchers, criminals exploited an opportunity during an OpenSea system upgrade to send fake emails, luring users into actions that ultimately led to the transfer of their assets.
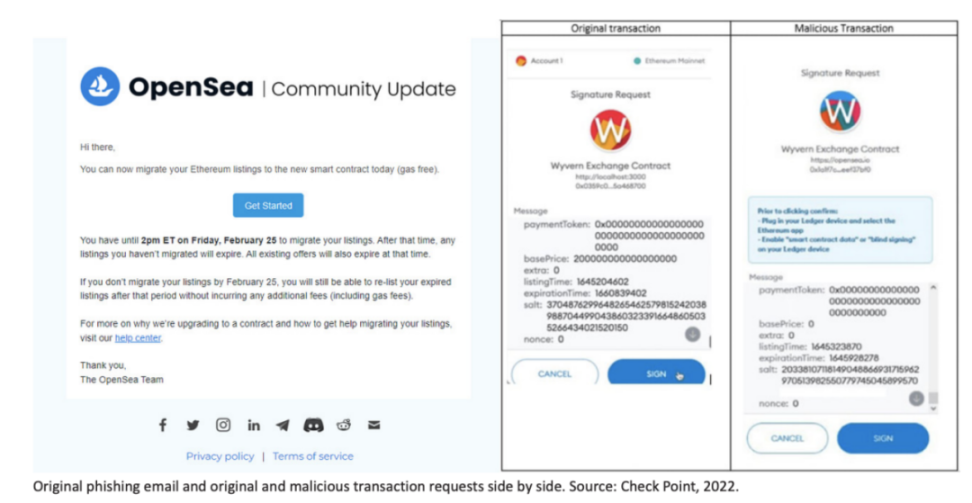
Additionally, an increasing number of criminals are using Drainer smart contracts targeting investors lacking knowledge of decentralized finance (DeFi). Specifically, this scam technique typically leads victims to connect to fake liquidity mining pools, draining their wallets. Various DeFi application suites can be easily found on underground markets and forums, which are advertised as legitimate applications but are actually used for scams.
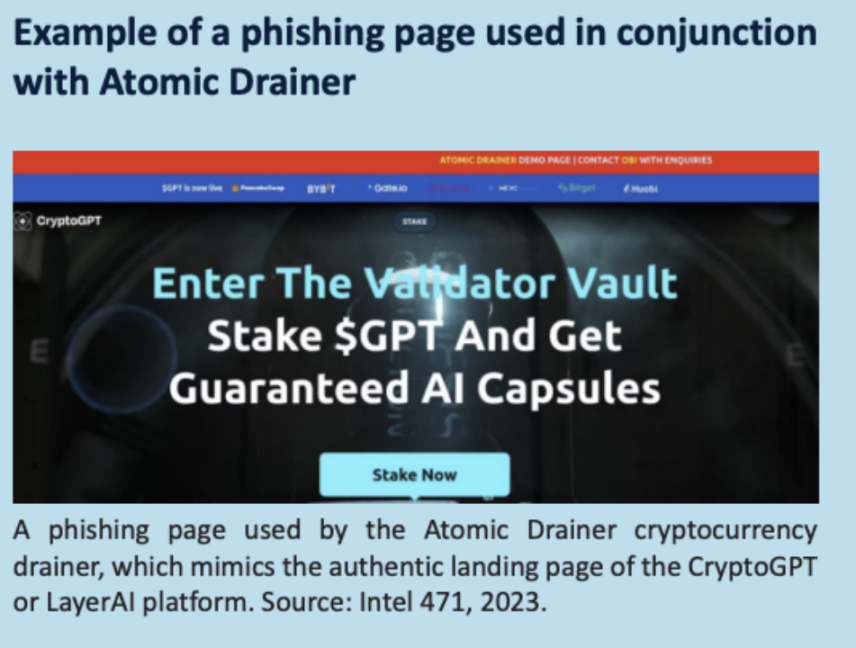
Liquidity mining scams exploit the complexities of DeFi cryptocurrency trading platforms to deceive users. These scammers often promise high returns by investing in "liquidity pools," which lend out cryptocurrencies to facilitate trading between different currencies. However, they create fake liquidity pools, easily accessing users' wallets through smart contracts, and may even deposit some cryptocurrency to create a false appearance of "profit," or introduce some worthless tokens. In these scams, the websites linking wallets display daily profit promises and false profit growth. Ultimately, the scammers use contract permissions to "steal" the money from users' wallets. Investors are often told they need to reach a certain staking "goal" to withdraw funds, but after enticing them with small returns, the money becomes unrecoverable; any additional funds deposited will also be stolen in the same manner. SlowMist has previously disclosed similar scams; interested readers can refer to the Web3 Security Beginner's Guide to Avoid Pitfalls | Fake Mining Pool Scams.
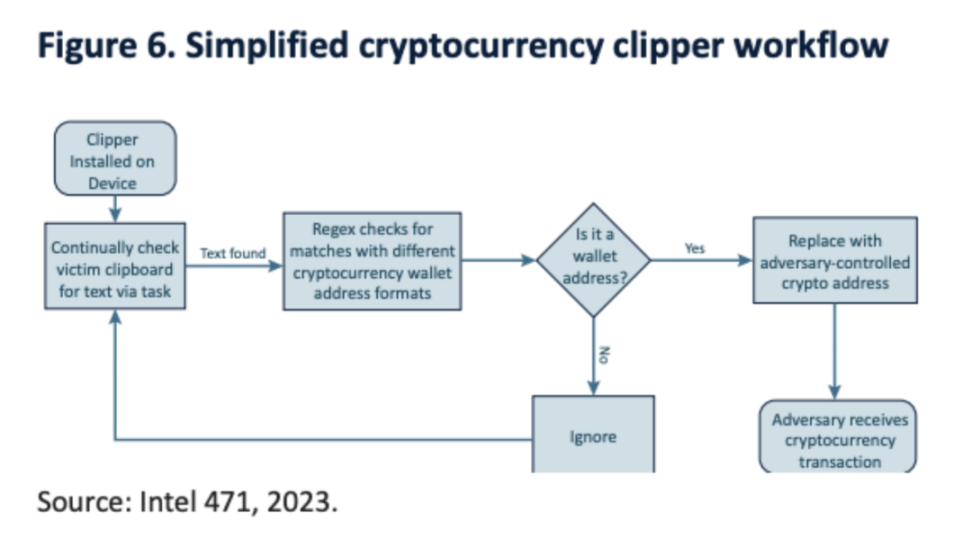
The report also mentions that a commonly used piece of malware by Southeast Asian criminal groups is a clipper. This software monitors the clipboard of infected systems, waiting to replace addresses in cryptocurrency transactions; once the victim inadvertently makes a transaction, funds are transferred to the attacker's address. Since cryptocurrency wallet addresses are usually long, users are less likely to notice changes in the receiving address, thereby increasing the effectiveness of the malware.
Conclusion
Overall, the threat of transnational organized crime in Southeast Asia is becoming increasingly complex and covert. To effectively address these challenges, law enforcement and regulatory agencies need to continuously enhance their capabilities. Southeast Asian countries should strengthen the capacities and coordination of governments, supervisory agencies, and law enforcement departments, develop comprehensive policies and action plans, and enhance cooperation with other countries and regions. Timely action will be key in the face of the rapidly evolving transnational organized crime environment. Close cooperation between Southeast Asian countries and their allies will help tackle this increasingly severe challenge and protect regional security and stability.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




