For DApp developers, the security of funds is a dimension that must be given special consideration.
Author: @Web3Mario
Abstract: There were quite a few major events last week. The Federal Reserve relatively aggressively cut interest rates by 50 basis points, and the Bank of Japan followed suit. This basically indicates that there will not be overly bearish information appearing in the next few weeks at least. There have been many articles analyzing this, so I won't go into detail here. In this process, as long as everyone focuses on two logics, it is relatively easy to grasp the risks. One is whether the job market is recovering as scheduled, and the other is the re-emergence of inflation risks. Apart from this, there was a piece of news that caught my attention, which is the announcement of the restart of V2 by Nirvana Finance, a stablecoin project on Solana. This project was suspended after being attacked by hackers for over $3.5 million in July 2022. I remember that the hacker who attacked the project was convicted before, and the recent restart should mean that the relevant judicial authorities have completed the transfer of the stolen funds. This means that the entire incident should be defined as the first case in the United States to be convicted of a smart contract attack, which has symbolic significance for the maritime legal system. Therefore, I spent some time over the weekend to detail the ins and outs of this case and share it with you.
Background of Nirvana Finance's Flash Loan Attack
I don't know how many of you are familiar with this project, so let me briefly describe the background of the entire event here. First of all, Nirvana Finance is an algorithmic stablecoin project on Solana, and I won't go into detail here. The project was launched at the beginning of 2022 and was attacked by hackers on July 28, 2022, stealing all the collateral of the stablecoin NIRV in the protocol, totaling approximately $3.5 million. The specific details of the attack are also interesting. Since the project's contract was not open source, the hacker was still able to profit from Solend's flash loan feature. At that time, the team also faced many accusations of self-theft.
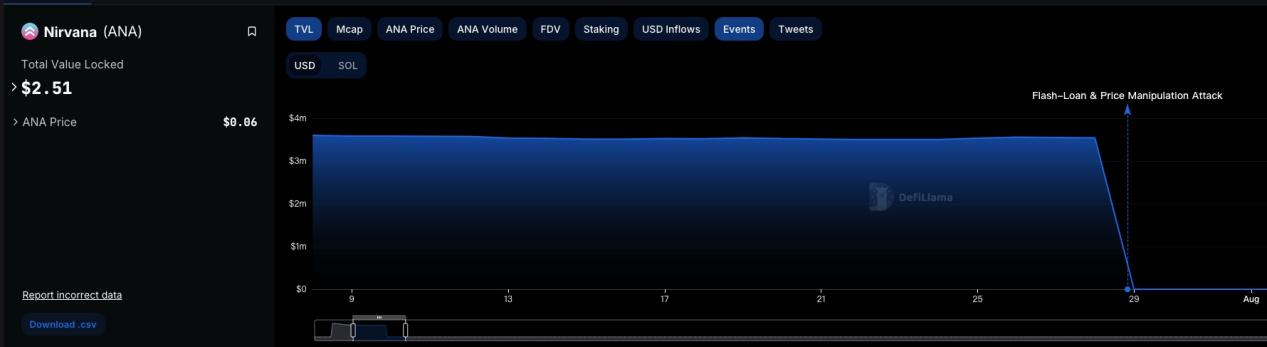
In addition, before being stolen, the project claimed to have completed an "automated audit," but in fact, this did not have any effect. Co-founder Alex Hoffman described in an interview with Cointelegraoh that the team had actually started the audit work the week the attack occurred. According to him, he did not expect Nirvana Finance to receive such a high level of attention at the beginning of the development, until it attracted the attention of several Chinese news media, leading to a significant increase in TVL. This is understandable, as it was a time when Luna was in its prime, and the algorithmic stablecoin track naturally received widespread attention. After the successful launch, Solana's CEO Anatoly Yakovenko personally urged him to conduct a smart contract audit and tried to expedite it in the audit company's schedule.
After the collateral was stolen, the project was at a standstill, but its Discord community has always been maintained by official personnel. During this process, the community has always kept an eye on the stolen funds, but due to the hacker's eventual isolation using tornado and Monero, there was actually no recovery. The situation took a turn on December 14, 2023, when Shakeeb Ahmed, a senior software security engineer who had previously worked at Amazon, admitted in the Southern District of New York court to a computer fraud charge related to the attack on Nirvana Finance and an unnamed decentralized cryptocurrency exchange. The U.S. Attorney's Office also stated that this was the first case in history to be convicted of a smart contract attack by a hacker.

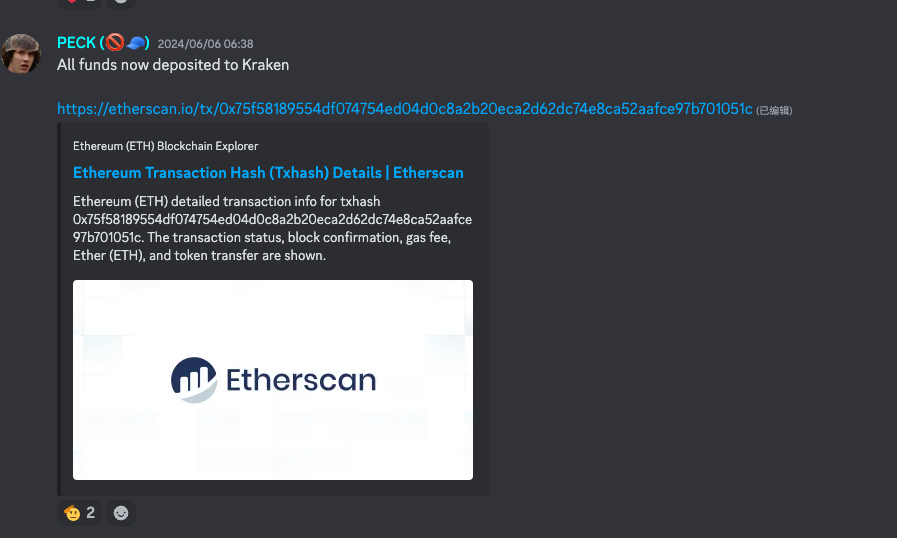
Of course, the founder did not stop after the project was attacked, but instead developed other projects, Superposition Finance and Concordia Systems. This is also the benefit of maintaining a certain level of anonymity, at least FUD will not be transferred. The case was then sentenced on April 15, 2024, and Shakeeb Ahmed was sentenced to three years in prison for intruding and defrauding two cryptocurrency exchanges. Then, on June 6, the stolen funds were transferred back to the team's designated account, meaning that the stolen funds of the project were officially recovered.
In fact, the origin of the entire case should be Crema Finance, and Nirvana Finance was locked in after being voluntarily disclosed by the hacker's capture
In fact, this 34-year-old software security engineer was a senior security engineer at an international technology company at the time of the attack, specializing in smart contract and blockchain audits. He was proficient in software reverse engineering, which explains why Nirvana was attacked before it was open source. Reverse engineering is the use of some decompilation software to reverse the compiled execution code back into the high-level language before compilation, making it readable by humans. Although the corresponding contract was not open source, the compiled code of the smart contract is actually stored on the chain, and developers proficient in this technology can easily obtain it.
According to documents later released by the U.S. Department of Justice, the origin of the entire case was a decentralized exchange that was attacked in July 2022 and lost nearly $9 million, which should be Crema Finance. On July 4, 2022, Shakeeb Ahmed also attacked the platform through a flash loan and proposed a $2.5 million "white hat bounty" to redeem other user assets and give up the pursuit of the hacker, and Crema Finance eventually agreed to accept a "white hat bounty" of about $1.68 million.
In the documents, it is described that Nirvana Finance was locked in after being voluntarily disclosed by the hacker's capture. As for the evidence of Shakeeb Ahmed's conviction, in addition to tracing his personal computer's browsing history, some related content was found, and it also described that after launching these attacks, he used many means, including some mixing protocols, Tornado, and Monero, to obfuscate. So, an interesting question arises: What did Shakeeb Ahmed do that ultimately led to his arrest?
There may be two possible answers. First, according to the analysis by SolanaFM at the time of the attack, the attacker either interacted with the address of the Huobi exchange or with a nested exchange address associated with Huobi. This is because the initial funding source for the attack address came from there. Secondly, regarding the misuse of Tornado Cash, the degree of obfuscation of funds is related to the duration of the funds being deposited and held in Tornado Cash, and the extent of redemption transactions occurring during this period. The degree of obfuscation will only increase if the funds are deposited for a long enough time and there are a significant number of redemption transactions during this period. Shortly after the attack, Ahmed deposited the funds into Tornado and within a short period of time, redemption transactions occurred, and the redeemed funds ultimately entered the centralized exchange Gemini. This seems to indicate that law enforcement located Shakeeb Ahmed and eventually arrested him in New York through cooperation with the aforementioned two centralized exchanges.
In any case, the recovery of stolen funds is a good thing, and it also reflects two issues. First, for DApp developers, the security of funds is a dimension that must be given special consideration. Secondly, such cases now have a blueprint for handling, and they should also have a certain deterrent effect on related behaviors.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




