With the growing demand for privacy protection, TEE has once again become the focus of discussion. Although TEE has been discussed for several years, it has not been widely adopted due to hardware security issues. However, with the challenges faced by MPC and ZK technologies in terms of performance and technical requirements, many researchers and developers have rekindled their interest in TEE.
This trend has also sparked discussions on Twitter about whether TEE will replace ZK technology. Some users believe that TEE and ZK are complementary rather than competitive because they address different issues and neither is perfect. Some users have pointed out that the security provided by AWS and Intel is higher than the multi-signature protection of Rollup. Considering the scalability of TEE in design space, which ZK cannot achieve, this trade-off is worthwhile.
What is TEE?
TEE is not a new concept. The Apple devices we commonly use apply TEE technology, namely "Secure Enclave," which primarily functions to protect users' sensitive information and perform encryption operations. Secure Enclave is integrated into the system-level chip, isolated from the main processor to ensure high security. For example, whenever you use Touch ID or Face ID, Secure Enclave verifies your biometric information and protects it from being leaked.
TEE stands for Trusted Execution Environment, which is a secure area within a computer or mobile device that runs independently of the main operating system. Its main features include isolation from the main operating system, ensuring data and execution security even if the main operating system is attacked; prevention of tampering with internal code and data during operation through hardware support and encryption technology; and protection of sensitive data using encryption to prevent leakage.
Currently, common TEE implementation methods include:
- Intel SGX: Provides hardware-supported isolated execution environment, creating a secure memory area (enclave) to protect sensitive data and code.
- ARM TrustZone: Creates a secure world and a normal world within the processor, with the secure world running sensitive operations and the normal world handling regular tasks.
- AWS Nitro Enclaves: Based on the AWS Nitro TPM security chip, it provides a trusted execution environment in the cloud, designed specifically for handling confidential data in cloud computing scenarios.
In the encryption market, TEE technology is most commonly used for off-chain computation in a trusted and secure environment. Additionally, TEE's remote attestation function allows remote users to verify the integrity of the code running in TEE, ensuring the security of data processing. However, TEE also has the drawback of lacking decentralization because it relies on centralized suppliers such as Intel and AWS. If these hardware components have backdoors or vulnerabilities, the system's security may be compromised. Nevertheless, as an auxiliary means, TEE technology is easy to build and has low costs, making it suitable for applications requiring high security and privacy protection. These advantages also enable TEE technology to be applied to various encryption applications, such as privacy protection and enhanced Layer2 security.
TEE Project Inventory
Flashbots: Implementing Privacy Transactions and Decentralized Block Building with SGX
Flashbots began exploring privacy technologies related to trusted execution environments such as SGX in 2022 and has positioned them as important building blocks for trustless collaboration in the transaction supply chain. In March 2023, Flashbots successfully ran a block builder in the Intel-developed trusted execution environment SGX enclave, taking a step towards achieving privacy transactions and decentralized block building. With SGX enclave, block builders and other infrastructure providers cannot see the content of user transactions. Builders construct verifiable valid blocks within the enclave and truthfully report their bids, potentially eliminating the need for mev-boost relays. Additionally, this technology helps reduce the risk of exclusive order flow, allowing transactions to remain private while still being accessible to all block builders running within the enclave.
Although TEE can indeed provide external resource access and privacy protection, its performance is not as high as non-TEE technologies, and there are some centralization risks. Flashbots found that relying solely on TEE cannot solve all problems; it also requires the integration of other security measures and the introduction of other entities to verify TEE computations and code to ensure system transparency and trustworthiness. Therefore, Flashbots envisioned a network composed of TEEs (Kettles), along with a trusted permissionless public chain (SUAVE Chain) responsible for managing this network and hosting programs to be run in TEEs. This is the basic concept of SUAVE.
SUAVE (Single Unified Auction for Value Expression) is an infrastructure designed to address MEV-related challenges, focusing on separating the roles of the mempool and block generation from existing blockchains to form an independent network (ordering layer) that can serve as a plug-and-play mempool and decentralized block builder for any blockchain.
(For more information on SUAVE, refer to ChainFeeds' previous article.)
SUAVE will be rolled out in two phases. The first version, SUAVE Centauri, includes Privacy Order Flow Auction (OFA) and SUAVE Devnet (testnet) and does not involve cryptography and TEE technology. The second version, Andromeda, will run execution nodes in a trusted execution environment (such as SGX). To ensure that computations and code on TEE nodes run offline as expected, Flashbots uses TEE's remote attestation function to enable smart contracts to verify messages from TEE. Specific steps include adding new precompiled functions to Solidity code to generate remote attestations, using SGX processors to generate attestations, fully verifying attestations on-chain, and using the Automata-V3-DCAP library to verify these attestations.
In summary, SUAVE will replace current third parties by integrating TEE. Applications running in the SUAVE system, such as order flow auctions or block builders, will run within TEEs and ensure the integrity of TEE computations and code through on-chain remote attestations.
Taiko: Building a Multi-Proof System Raiko with SGX
The concept of TEE can also be extended to Rollup to build a multi-proof system. Multi-proof refers to generating multiple types of proofs for a block, similar to Ethereum's multi-client mechanism. This mechanism ensures that even if one proof has a vulnerability, other proofs remain valid.
In a multi-proof mechanism, any user interested in generating proofs can run a node, extract transaction and all state access Merkle proofs, and use this data to generate different types of proofs. These proofs are then submitted together to a smart contract for verification of their correctness. For proofs generated by TEE, it is necessary to check if the ECDSA signature is signed by the expected address. Once all proofs are verified and the block hash is confirmed to be consistent, the block will be marked as proven and recorded on the chain.
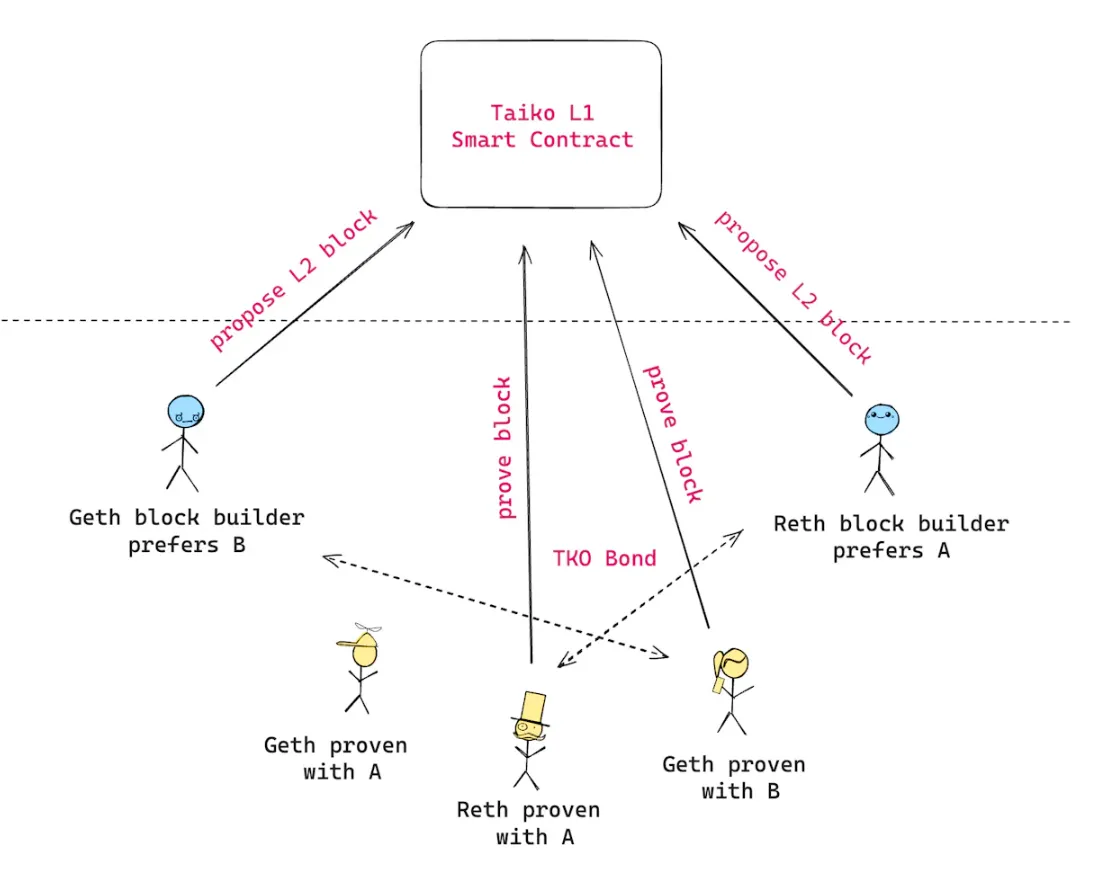
Taiko is leveraging Intel SGX technology to build a multi-proof system, Raiko, for verifying Taiko and Ethereum blocks. By using SGX, Taiko can ensure data privacy and security when performing critical tasks, and even if there are potential vulnerabilities, TEE can provide additional protection to prevent attackers from compromising the proof system. SGX proofs can run on a single computer and can be completed in a few seconds without affecting the efficiency of proof generation. Additionally, Taiko has introduced a new architecture that supports compiling client programs into formats that can run in both ZK and TEE, ensuring the correctness of block state transitions, and evaluating performance and efficiency through benchmark testing and monitoring.
Despite offering many advantages, TEE still faces some challenges in implementation. For example, SGX settings need to support CPUs from different cloud providers and optimize gas costs during the verification process. Additionally, a secure channel needs to be established to verify the correctness of computations and code. To address these challenges, Taiko uses Gramine OS to encapsulate applications running in trusted enclaves and provides user-friendly Docker and Kubernetes configurations, allowing users with SGX-enabled CPUs to easily deploy and manage these applications.
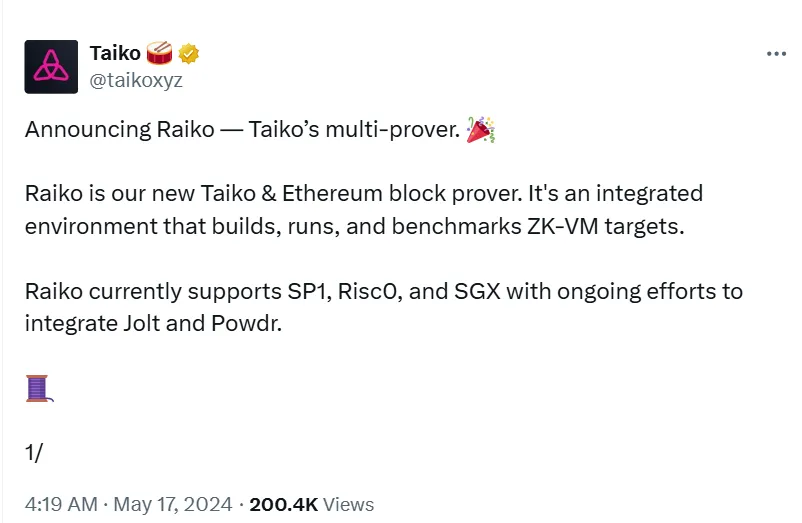
According to Taiko's announcement, Raiko currently supports SP1, Risc0, and SGX, and is continuously working to integrate Jolt and Powdr. In the future, Taiko plans to integrate more Riscv32 ZK-VM, expand Wasm ZK-VM, integrate directly with Reth for real-time block proofs, and adopt a modular architecture to support multi-chain block proofs.
Scroll: Collaborating with Automata to Develop TEE Prover
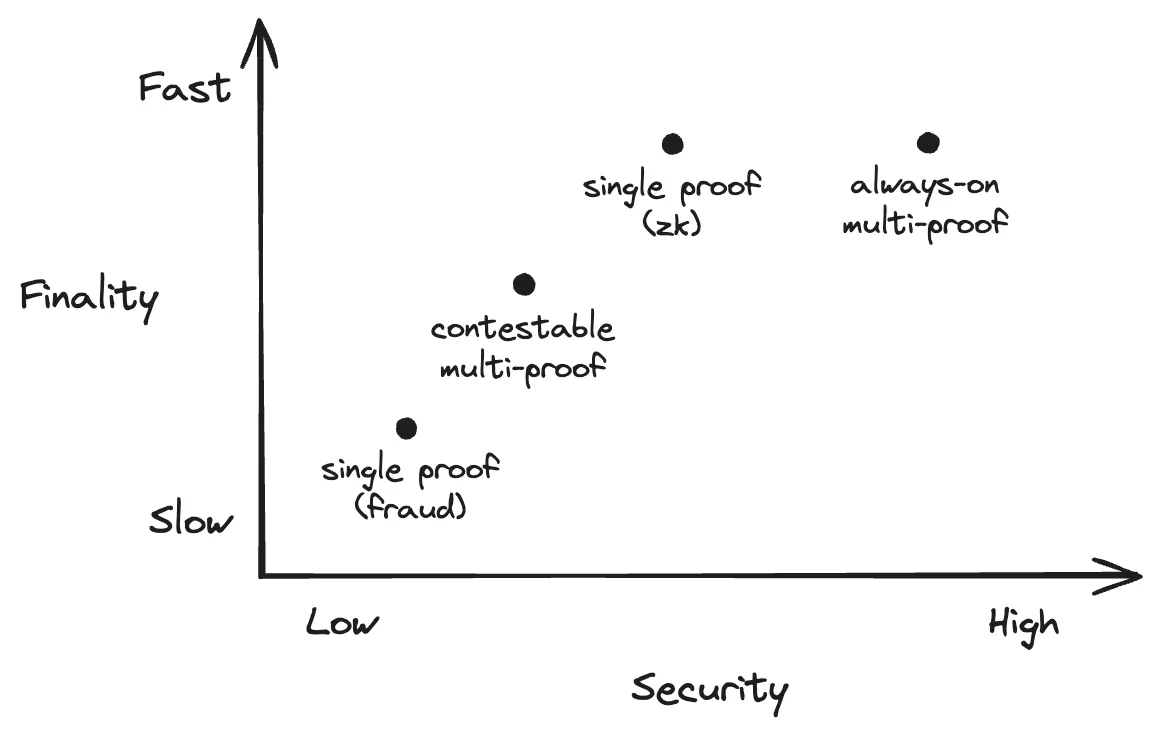
Scroll's multi-proof mechanism aims to achieve three goals: enhance L2 security, not increase finality time, and introduce marginal costs only for L2 transactions. Therefore, in addition to ZK proofs, when choosing auxiliary proof mechanisms, Scroll needs to balance finality and cost-effectiveness. While fraud proofs offer high security, they have long finality times. Although zkEVM validators are powerful, they have high development costs and complexity. Finally, Scroll chose to use the TEE Prover proposed by Justin Drake here as an auxiliary proof mechanism.
The TEE Prover runs in a protected TEE environment, allowing for quick transaction execution and proof generation without increasing finality. Another important advantage of the TEE Prover is its efficiency, with negligible overhead related to the proof process.
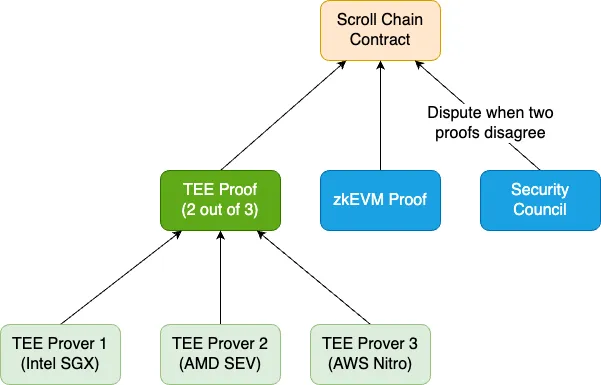
Currently, Scroll is collaborating with the modular proof layer Automata to develop the TEE Prover for Scroll. Automata is a modular verification layer aimed at extending machine-level trust to Ethereum through TEE coprocessors. Scroll's TEE Prover consists of two main components:
SGX Prover: A off-chain component running in an enclave, used to check if the state root after executing a block in the enclave matches the existing state root, and then submit the execution proof (PoE) to the SGX Verifier.
SGX Verifier: This is a smart contract deployed on L1 chain, responsible for verifying the state transitions proposed by SGX Prover and the correctness of the proof reports submitted by Intel SGX enclave.
The SGX Prover monitors batches of transactions submitted by the sequencer on L1, ensuring the data used for executing state transitions is complete and unaltered. Then, the SGX Prover generates a block proof (PoB) containing all necessary information to ensure all participating nodes use the same dataset for verification and execution. After completion, the SGX Prover submits the execution proof (PoE) to L1. Subsequently, the SGX Verifier checks if the PoE is signed by a valid SGX Prover.
SGX Prover is written in the Rust programming language and uses SputnikVM as its EVM engine for executing smart contracts. This implementation can be compiled and run on machines supporting SGX hardware mode, and can also be debugged in non-SGX environments. The SGX Verifier uses the open-source DCAP v3 verification library from Automata, which can verify the entire block history of the Scroll test network.
In addition, to reduce the trust issue in TEE implementation and hardware manufacturers, Scroll is also researching a protocol to aggregate TEE Provers from different hardware and clients. This protocol will incorporate a threshold signature scheme, which is a cryptographic technique that allows multiple participants to collectively generate a signature that is only valid when at least a specific number of participants agree. Specifically, the TEE Prover requires a consensus of at least T out of N TEE Provers to generate consistent proofs.
Automata: Enhancing Blockchain Security and Privacy with TEE Coprocessors
Automata Network is a modular verification layer that uses hardware as a common Root of Trust, enabling various use cases including multi-validator systems based on TEE validators, providing fairness and privacy for RPC relays, and building blocks in encrypted enclaves.
As mentioned earlier, the multi-proof system of Scroll is developed in collaboration with Automata. In addition, Automata has introduced TEE coprocessors as part of the multi-proof AVS on EigenLayer mainnet. TEE coprocessors are hardware designed to perform specific computational tasks, complementing or extending the capabilities of the main chain. Automata Network's TEE coprocessors extend the functionality of the blockchain by performing secure computations within TEE isolated areas.
Specifically, the Multi-Prover AVS serves as a task control center, responsible for coordinating and managing multiple independent validators according to the requirements of different protocols. Protocols can publicly announce tasks that need to be verified, and a committee of long-term reward-incentivized TEE validators can be organized. Nodes (operators) actually performing the verification can register to participate in these tasks and can collaborate to ensure security. Token holders willing to support protocol security act as stakers, delegating their staking rights to trusted operators. This staking enhances the economic security required in the early stages of the protocol, as the staked funds serve as a guarantee, incentivizing operators to work honestly and efficiently. EigenLayer creates a permissionless market, allowing stakers, operators, and protocols to participate freely.
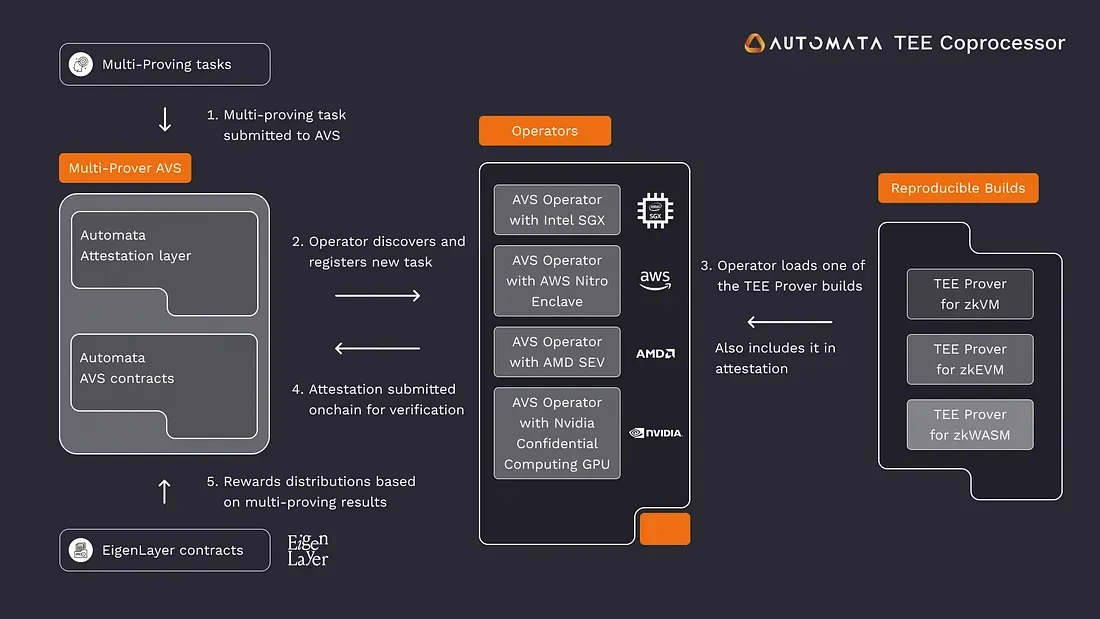
Secret Network: Implementing Privacy Protection with SGX Technology
The privacy-focused public chain Secret Network primarily achieves data privacy protection through Secret Contracts and TEE. To achieve this, Secret Network adopts Intel SGX Trusted Execution Environment (TEE) technology and only allows the use of Intel SGX chips to ensure network consistency, not supporting other TEE technologies.
Secret Network uses remote attestation to verify the integrity and security of the SGX secure enclave. Each full node creates an attestation report before registration, proving that its CPU has the latest hardware upgrades and undergoes verification on the chain. New nodes receive a consensus shared key, enabling them to process computations and transactions in the network in parallel, ensuring overall network security. To reduce potential attack vectors, Secret Network chooses to use SGX-SPS (Server Platform Services) instead of SGX-ME (Management Engine).
In implementation, Secret Network uses SGX for computations with encrypted inputs, outputs, and state. This means that data remains encrypted throughout its lifecycle, preventing unauthorized access. Additionally, each validation node in Secret Network uses a CPU supporting Intel SGX to process transactions, ensuring that sensitive data is decrypted only within the secure enclave of each validation node and inaccessible to external parties.
Oasis: Building Privacy Smart Contracts with SGX
The privacy computing network Oasis adopts a modular architecture, separating consensus and smart contract execution into the consensus layer and ParaTimes layer, respectively. As the smart contract execution layer, ParaTimes consists of multiple parallel ParaTimes, each representing a computing environment with shared state. This allows Oasis to handle complex computational tasks in one environment and simple transactions in another.
ParaTimes can be categorized into privacy and non-privacy types, run different virtual machines, and can be designed as permissioned or permissionless systems. As one of Oasis's core value propositions, Oasis has introduced two privacy smart contracts, Cipher and Sapphire, combining TEE technology from Intel SGX. Encrypted data and smart contracts enter the TEE together, where the data is decrypted and processed by the smart contract, and then re-encrypted upon output. This process ensures that the data remains confidential throughout the processing and is not exposed to node operators or application developers. The difference is that Sapphire is a privacy EVM-compatible ParaTime, while Cipher is a privacy ParaTime for executing Wasm smart contracts.
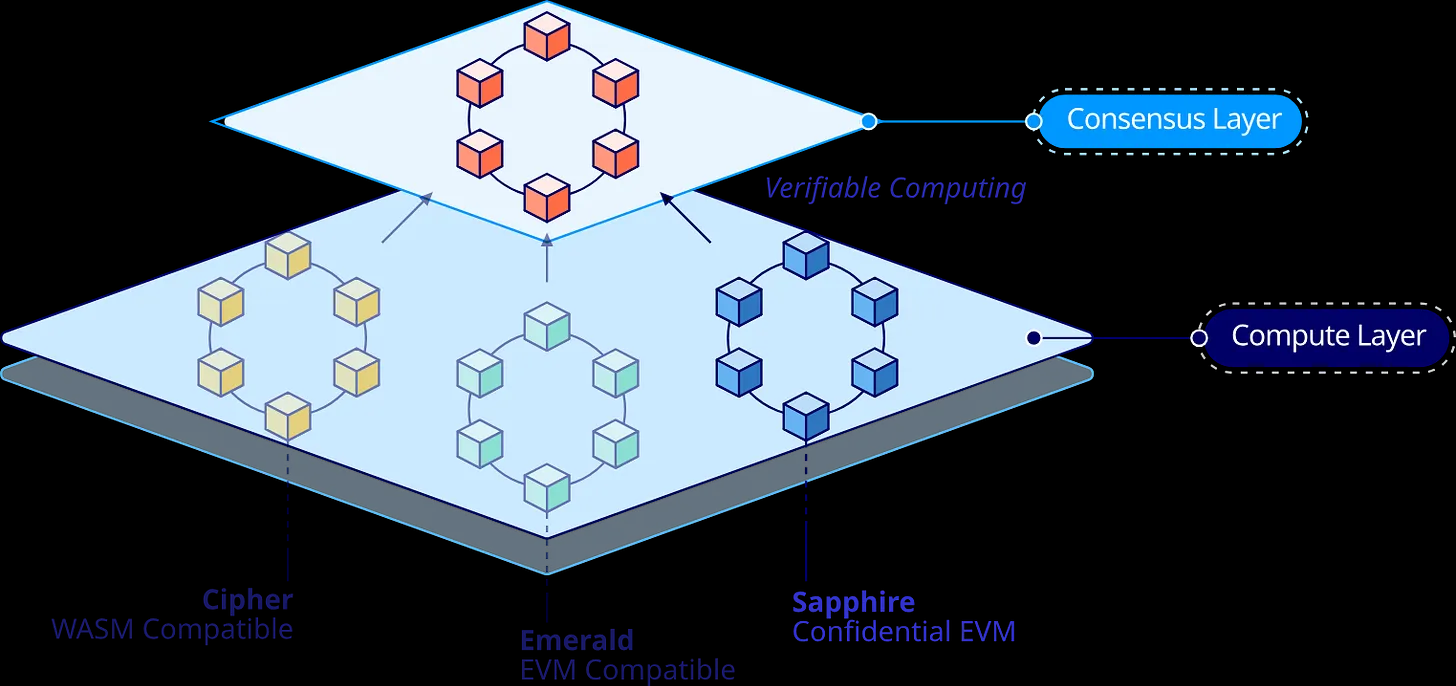
](https://substackcdn.com/image/fetch/fauto,qauto:good,flprogressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F73ad8ef9-15a7-4d71-a9d7-c532214ea7d61523x718.png)
Bool Network: Enhancing Bitcoin Verification Security and Decentralization with MPC, ZKP, and TEE Technology
Bool Network integrates MPC, ZKP, and TEE technologies to transform external validator clusters into Dynamic Hidden Committees (DHC) to enhance network security.
In the Dynamic Hidden Committee, to address the issue of private key exposure due to consensus signatures by external validation nodes, Bool Network introduces TEE technology. For example, using Intel SGX technology to encapsulate private keys in TEE, allowing node devices to operate within a secure area locally, inaccessible to other components in the system. Through remote attestation, witness nodes can present proofs to verify that they are indeed running in TEE and storing keys, which can be verified on-chain by other nodes or smart contracts.
Additionally, BOOL Network is completely open-access, allowing any entity with TEE devices to become validation nodes by staking BOOL.
[
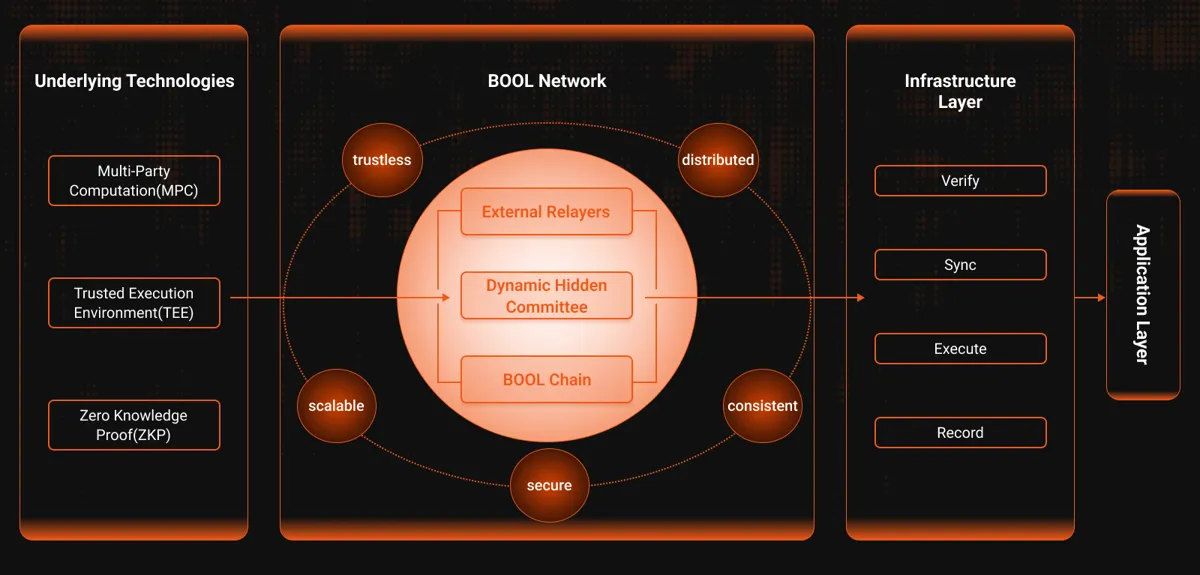
](https://substackcdn.com/image/fetch/fauto,qauto:good,flprogressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F90bed80c-3800-41e5-a4f2-25b4461b2b5a1200x575.png)
Marlin: Decentralized Cloud Computing with TEE and ZK Coprocessors
Marlin is a verifiable computation protocol that combines trusted execution environments and ZK coprocessors to delegate complex workloads to decentralized clouds.
Marlin includes various types of hardware and subnetworks. Its TEE technology is primarily applied on the Marlin Oyster subnetwork. Oyster is an open platform allowing developers to deploy custom computing tasks or services on untrusted third-party hosts. Currently, Oyster mainly relies on AWS Nitro Enclaves, which is a trusted execution environment based on AWS Nitro TPM security chips. To achieve its decentralized vision, Oyster may potentially be compatible with more hardware suppliers in the future. Additionally, Oyster allows DAOs to configure enclaves directly through smart contract calls, eliminating the need for specific members to manage SSH or other authentication keys. This approach reduces reliance on manual operations.
Phala Network: SGX-Prover, a Multi-Proof System Based on TEE
Phala Network is a decentralized off-chain computing infrastructure dedicated to achieving data privacy and secure computation through TEE. Currently, Phala Network only supports Intel SGX as its TEE hardware. Based on the decentralized TEE network, Phala Network has built the Phala SGX-Prover, a multi-proof system based on TEE. Specifically, the off-chain module sgx-prover generates TEE Proofs containing computation results after running state transition programs, and submits them to the on-chain sgx-verifier for verification.
To address concerns about centralization in SGX, Phala Network introduces two roles: Gatekeeper and Worker. Gatekeepers are elected by PHA token holders through NPoS and are responsible for managing network keys and supervising the economic model. Workers run on SGX hardware. By introducing a key rotation mechanism, Gatekeepers can ensure the security of the TEE network.
Currently, Phala Network has over 30,000 TEE devices registered and operated by users globally. Additionally, Phala Network is exploring TEE-based fast-finality solutions. In theory, fast finality can be achieved based on TEE proofs, providing ZK proofs only when necessary.
Conclusion
In response to the debate on Twitter, Uniswap CEO Hayden Adams also expressed his viewpoint, stating, "Negative evaluations of TEE all carry the implication that the pursuit of perfection hinders good results. Everything involves trade-offs. In the realm of protecting blockchain, the more available tools, the better."
Through the exploration of these use cases, it is evident that TEE technology holds potential applications in addressing privacy and security concerns. For example, Flashbots implements privacy transactions and decentralized construction through TEE, while Taiko and Scroll utilize TEE to establish a multi-proof system, ensuring the security of L2 transactions. However, most projects currently rely on a single centralized supplier, which may pose certain risks. In the future, it may be possible to be compatible with more hardware suppliers and ensure nodes run on different hardware by setting node ratios, further reducing the centralization risk associated with over-reliance on a single supplier.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




