Author: Bitrace
Tether (Tether USD, hereinafter referred to as USDT) is a centralized stablecoin issued by Tether Limited, which is anchored to the value of the US dollar through smart contracts on the blockchain network. In addition to possessing the characteristics of anonymous transfer and permissionless use of other cryptocurrencies, USDT also grants the issuer significant control rights, allowing developers to selectively issue, destroy USDT tokens for specific addresses, or restrict specific addresses' operational permissions for USDT, commonly known as "Tether freezing."
Such centralized freezing activities are usually triggered by law enforcement requests from various government departments around the world or temporary major cryptocurrency security incidents, aimed at preventing known illegal activities using USDT and intercepting damaged assets to prevent further harm. As the adoption of USDT in the real financial system increases, incidents of illegal cryptocurrency-related activities have become more frequent, leading to a widespread occurrence of Tether freezing activities, causing significant negative business impact on a large number of web3 enterprises that inadvertently accept high-risk encrypted funds, and even bringing legal risks.
This article will analyze and explain the case of Huione Group in Cambodia being frozen 29.62 million USDT by Tether.
Overview of Huione's Business Scale
Huione Group is a large financial group located in Cambodia, with business segments including cryptocurrency wallets, payments, trade guarantees, insurance, and cryptocurrency exchanges. Its core payment and guarantee business heavily utilize USDT. According to the address tagging data on Bitrace's DeTrust risk fund monitoring and management platform, the official and user addresses of HuionePay and HuioneGuarantee exceed 180,000, making it the largest-scale cryptocurrency enterprise in the region, with influence extending to the entire Southeast Asia and even East Asia.
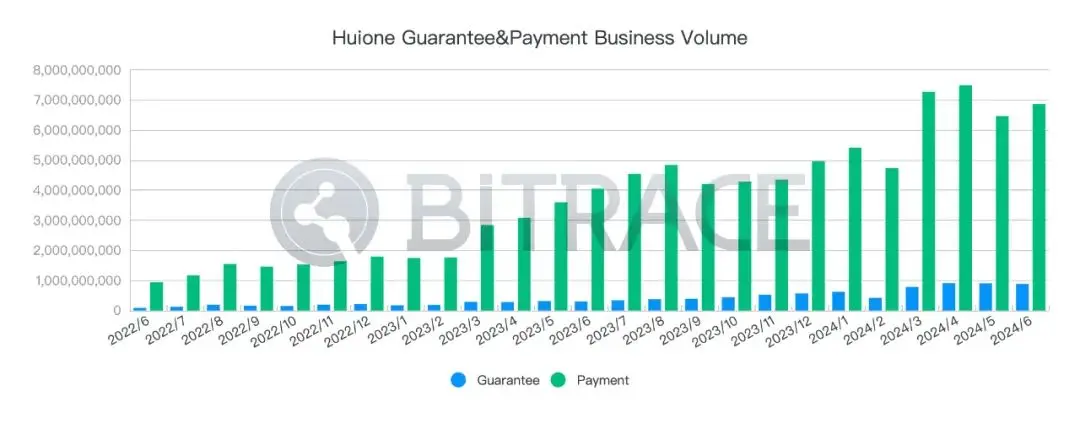
According to Bitrace's monitoring, from June 2022 to June 2024, the monthly fund scale of all known HuionePay and HuioneGuarantee business addresses has maintained an upward trend, from a minimum of 1.03 billion USDT in June 2022 to a peak of 8.39 billion USDT in April 2024, with a total fund scale of 102.397 billion USDT over two years.
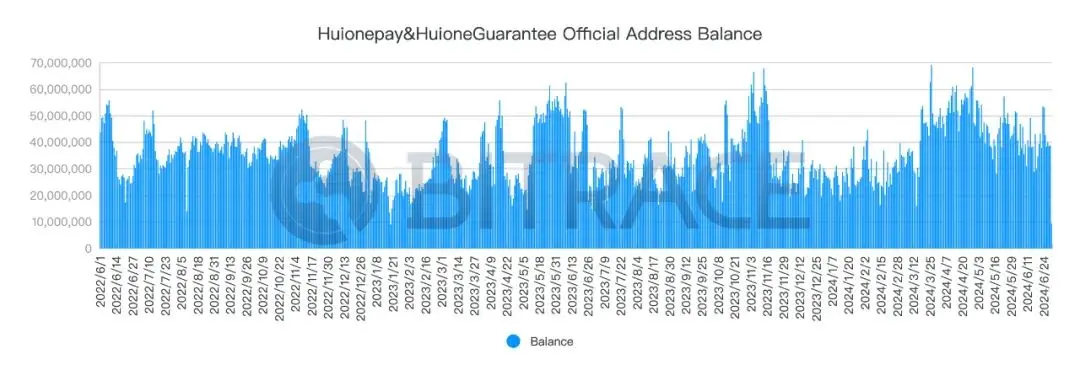
During this period, Huione's related business addresses also maintained a significant amount of reserves. Between June 2022 and June 2024, the daily average balance of all known HuionePay and HuioneGuarantee business addresses reached 35.68 million USDT.
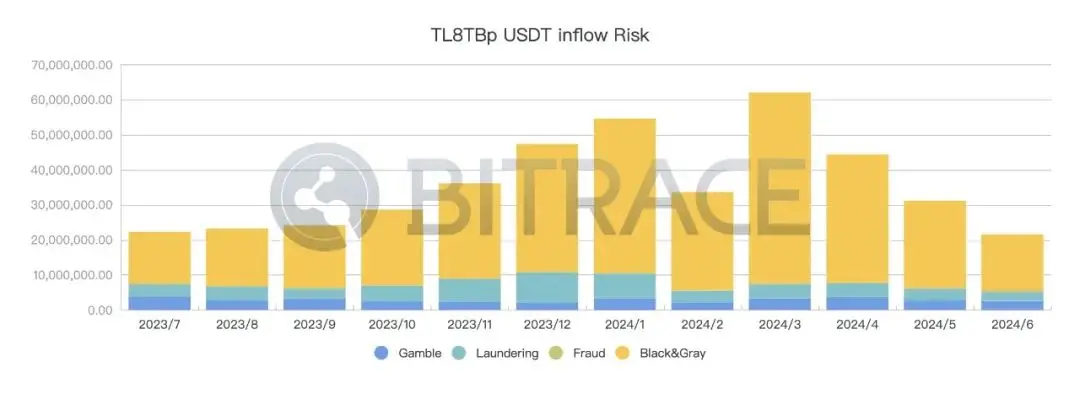
Due to the high incidence of illegal activities using cryptocurrency in Southeast Asia, Huione's business addresses have been affected to some extent. Taking the core business address TL8TBp currently used by HuioneGuarantee as an example, according to Bitrace's monitoring, from July 1, 2023, to June 30, 2024, a total of 2.158 billion USDT flowed into this address, including 0.35 billion for high-risk funds related to online gambling, accounting for 1.62%; 3.39 billion for high-risk funds related to illicit transactions in the black and gray markets, accounting for 15.71%; 0.54 billion for high-risk funds related to money laundering, accounting for 2.50%; and 0.02 billion for high-risk funds related to fraud, accounting for 0.09%.
Analysis of Frozen Funds in Huione
On July 13, 2024, Tronscan showed that the Tron network address TNVaKW was restricted by Tether Limited, with a staggering 29.62 million USDT frozen and unable to be transferred. Bitrace immediately intervened in the investigation.
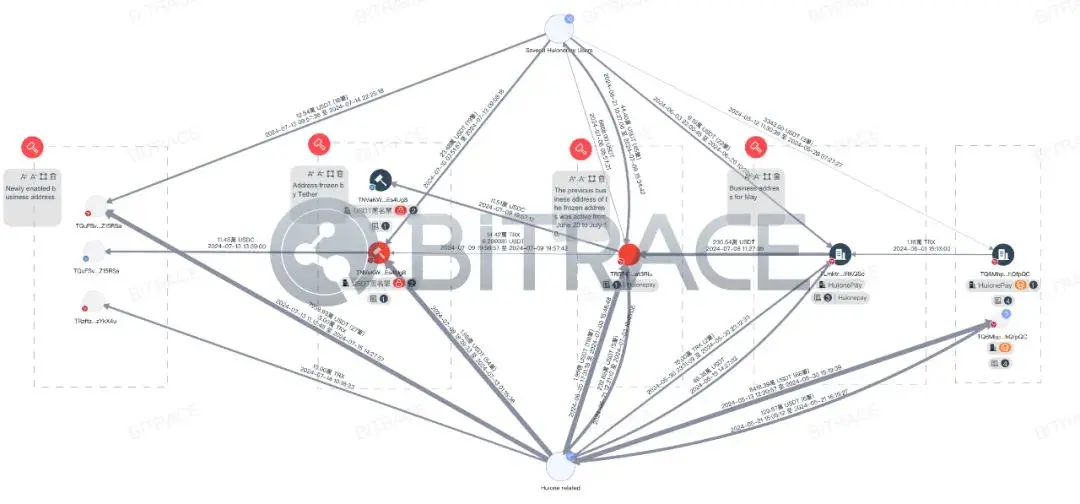
Preliminary investigation results showed that just five days after the creation of TNVaKW, the total transaction scale of funds exceeded 1 billion USDT, receiving deposits from a large number of Tron addresses marked as HuionePayUser, as well as funds from other official HuionePay and HuioneGuarantee addresses. Therefore, Bitrace confirmed that this address is an official business address of Huione and judged that the reason for the freeze was the receipt of a large amount of stolen encrypted funds.
The next day, well-known blockchain detective ZachXBT further stated on social media that in the earlier theft incident at the Japanese exchange DMM, the stolen assets had entered HuionePay through cross-chain exchanges.
Based on the addresses publicly disclosed by ZachXBT, Bitrace uncovered more addresses related to money laundering activities and conducted a retrospective analysis of the entire fund chain. Among them—
>165BTC crossed to Avalanche via AvalancheBridge
>182BTC crossed to Ethereum via ThorChainBridge
>263BTC crossed to Ethereum via ThresholdBirdge
The obtained assets such as tBTC, BTC.b, etc., were exchanged for assets equivalent to 31.82 million US dollars, such as USDT, USDC, DAI, etc., on Avalanche, Ethereum, and other chains, and then cross-chain exchanged to the TRON network, with approximately 14 million eventually entering TNVaKW.
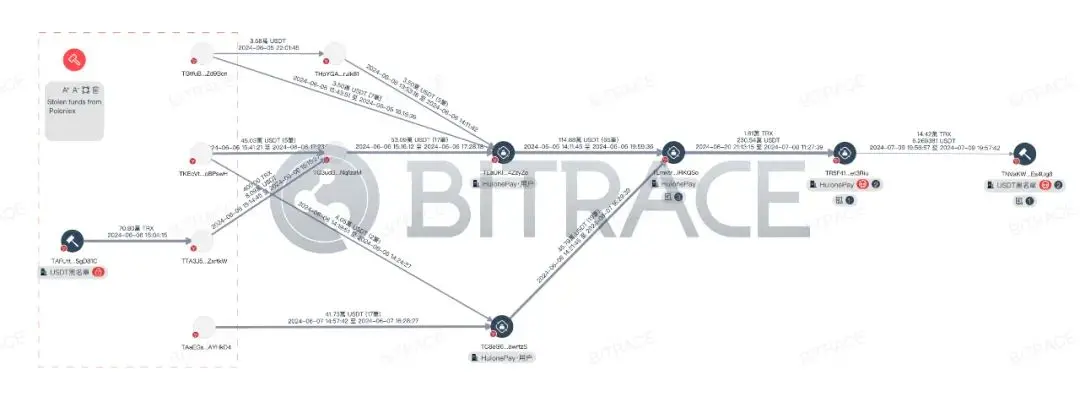
It is worth noting that the DMM incident is just one of the publicly disclosed security incidents involving funds flowing into Huione addresses. While investigating other incidents, it was found that some of the funds from the Poloniex exchange theft incident were also related to Huione. Between June 5 and 7, 2024, at least 1.05 million USDT related to the case flowed into HuionePay user addresses, and subsequently flowed into multiple official HuionePay business addresses, including TLmktr, TR5F41, and TNVaKW.
Currently, there is no direct evidence to indicate that the freezing of TNVaKW is related to the funds from these two security incidents. However, considering that other business addresses of Huione have not been frozen, this at least indicates that this freezing action is not specifically targeting the Huione group itself.
Analysis of HuionePay's Run on the Bank
As mentioned earlier, the daily average balance of all known HuionePay and HuioneGuarantee business addresses is 35.68 million USDT, and in the three months before the freezing incident, this value had been maintained at around 40 million USDT. The frozen 29.63 million USDT is equivalent to 75% of its reserves, indicating a certain withdrawal pressure.
An analysis was conducted on the latest HuionePay business address TQuFSv—
This address was activated 2.5 hours after TNVaKW was frozen, and began processing deposits and withdrawals for HuionePay users, receiving a legacy of 11.48 thousand USDC from TNVaKW. As of 9:34:39 on July 16, 2024, its transaction scale had reached 733 million USDT.
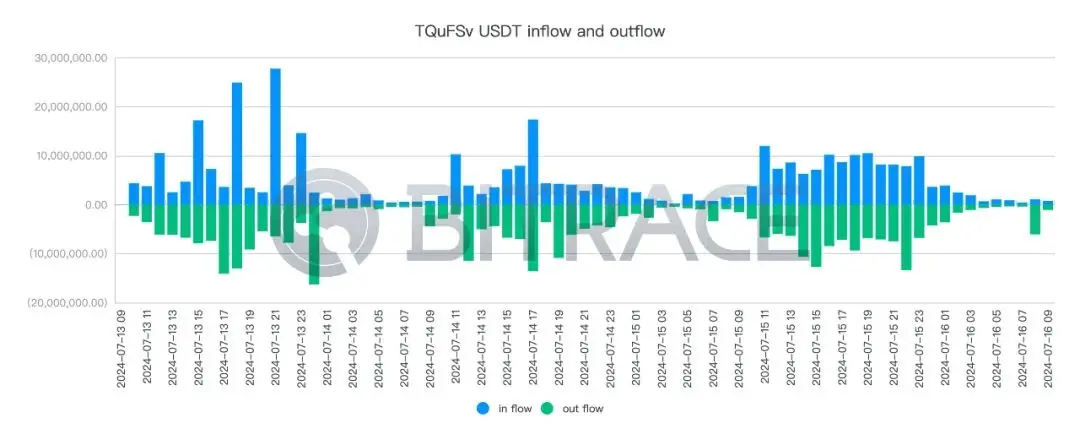
Income and expenditure of TQuFSv were statistically analyzed on an hourly basis, and no significant abnormal fund phenomena were found. The address currently still holds a balance of 12.88 million USDT.
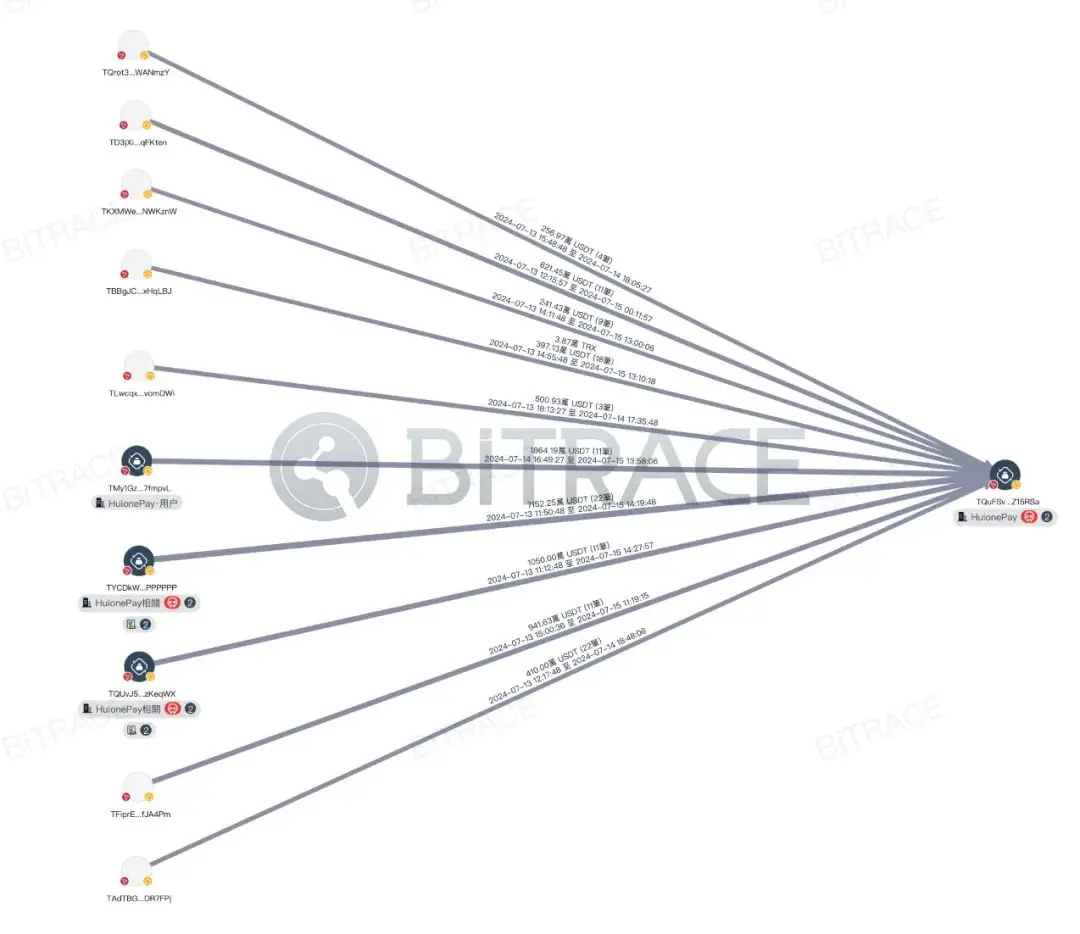
An analysis of the counterparties of TQuFSv shows that the top ten counterparties in terms of funds received have collectively transferred 147 million USDT, with two addresses marked as HuioneGuarantee addresses transferring 73 million USDT and 15 million USDT to TQuFSv, accounting for 23.64% of the total inflow. The top ten counterparties in terms of funds sent have collectively received 80 million USDT from TQuFSv, with three addresses marked as HuioneGuarantee addresses receiving 14 million USDT, 8 million USDT, and 6 million USDT, accounting for 7.76% of the total outflow.
This indicates that HuionePay experienced a significant outflow of funds after the freezing incident, but the official entity promptly replenished the reserves from other business addresses to meet user withdrawal requests.
Importance of KYT
For large-scale enterprises like Huione that heavily utilize cryptocurrencies, sufficient fund throughput often attracts the attention of money laundering groups. Under the increasingly comprehensive global enforcement actions related to cryptocurrency cases, the lack of the ability to identify the financial risks of platform user addresses may impact platform operations and even lead to the risk of the operator being investigated.
Therefore, the adoption of professional KYT tools to accurately identify the risks of encrypted funds and the implementation of necessary risk control procedures to handle platform risk events has become a matter that cryptocurrency-related enterprises must consider.
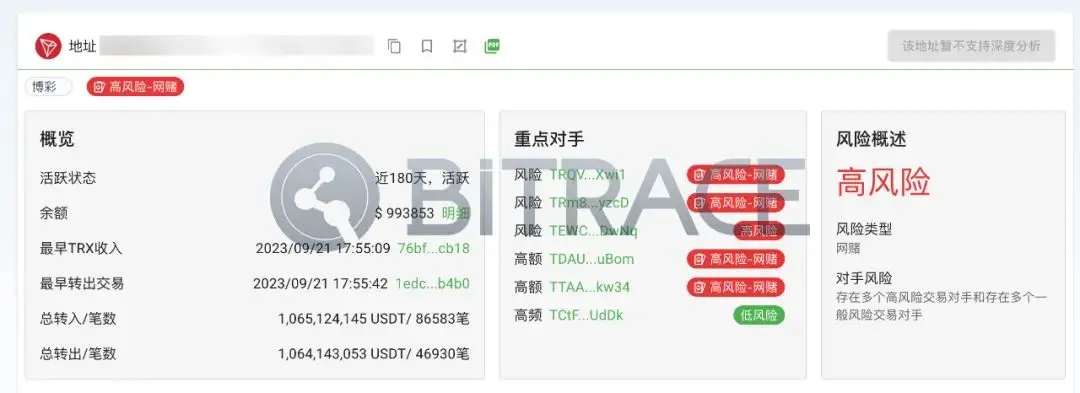
Based on long-term tracking and research of the cryptocurrency crime industry chain, Bitrace has established an exclusive data collection and processing system, constructed an analysis model for typical forms of cryptocurrency crime and industry chains, and dynamically expanded data labeling through machine learning and pattern recognition algorithms. It has accumulated a database of over 400 million address labels, including entity labels (exchanges, wallets, OTC, payment platforms, mining pools, DeFi, etc.) and exclusive risk labels (money laundering, online gambling, black and gray market, fraud, hacking, sanctions, freezing, terrorism financing, drug trafficking, etc.).
At the same time, its DeTrust on-chain risk fund monitoring and management platform can help cryptocurrency-related enterprises conduct round-the-clock transaction monitoring of important business addresses, perform real-time KYT and KYA on every new transaction and counterparty, and support custom strategies to dynamically assess transaction risks.
Compliance is the foundation of enterprise operations. By establishing appropriate KYT and KYC procedures, enterprises will be better able to meet the requirements of local regulatory authorities and gain a competitive advantage in the market.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




