TON (The Open Network), as a rapidly developing blockchain project, has attracted widespread attention due to its advanced technology and rapidly growing user base. However, participating in such a phenomenon-level project requires in-depth analysis, judgment, and interpretation of its risks. This report aims to provide in-depth risk analysis and compliance interpretation for users and potential participants in the TON ecosystem.
Background Introduction
With the popularization and development of blockchain technology, TON has rapidly attracted global users and developers' attention due to its unique technical architecture and extensive application prospects. TON is committed to establishing a decentralized internet platform, providing efficient, transparent, and secure blockchain services. However, due to the complexity of blockchain technology and the differences in laws and regulations in various countries, TON faces many compliance and technical challenges in its development. By analyzing in detail the current situation and challenges of TON in terms of legal compliance, technical implementation, user experience, and cross-chain interoperability, this report aims to help users make wiser decisions when participating in the TON ecosystem.
Technical Risk Analysis
1. Smart Contract Vulnerabilities
Smart contract vulnerabilities are one of the main risks faced by TON blockchain technology. Common vulnerabilities include reentrancy attacks, integer overflow, and access control issues. We will decompose and analyze the technical risks of TON for each potential risk and vulnerability to assess whether TON's ecosystem, while thriving, also faces threats.
1.1 Language Complexity
FunC Issues:
- Design of FunC language: FunC is a Lisp-like low-level language, serving as the primary programming language for TON smart contracts. FunC emphasizes efficiency and flexibility. This low-level programming language allows developers to directly manipulate memory and perform fine-grained resource management.
- Increased complexity: Due to FunC's low-level nature, developers need to manually manage memory and handle low-level operations, which places high demands on developers' programming abilities and security awareness. Carelessness may lead to issues such as memory leaks and buffer overflows, resulting in potential security vulnerabilities in smart contracts.
- Risks:
- Memory management errors: Manual memory management increases the likelihood of introducing errors, such as memory leaks and buffer overflows. These errors may be exploited by malicious attackers, leading to unexpected behavior in smart contract execution.
- Code complexity: FunC's low-level programming characteristics increase code complexity, making debugging and maintenance more challenging, thereby increasing the likelihood of vulnerabilities.
Tact Language:
- Higher-level programming language: In response to the issues with FunC, the community has introduced and supported a higher-level programming language, Tact. This language is similar to TypeScript and Rust, providing higher-level abstractions and simpler syntax, making it easier to learn and use than FunC.
- Advantages: By providing a more user-friendly development environment, Tact lowers the barrier to smart contract development, helping to attract more developers to join the TON ecosystem.
Fift Language
- Characteristics: Fift is a low-level assembly and debugging language used to interact directly with the TON Virtual Machine (TVM), suitable for low-level debugging and testing of smart contracts.
- Challenges: As Fift is still in its early stages, its tools and documentation may not be comprehensive, and developers may encounter more challenges and issues during its use.
1.2 Smart Contract Vulnerabilities Faced by TON
- Reentrancy attacks: This is a common vulnerability in smart contracts, where a malicious contract can recursively call the same function before a previous function call is completed, leading to resource exhaustion or data tampering.
- Example: The classic DAO attack occurred due to the exploitation of a reentrancy vulnerability, resulting in the theft of a large amount of funds.
Preventive Measures
- Check-Effects-Interactions Pattern: The TON official documentation emphasizes the use of this pattern to ensure that all state updates are completed before any external calls, thereby avoiding reentrancy attacks. The core of this pattern is to first check conditions (Check), then perform state updates (Effects), and finally interact (Interactions), ensuring that the internal state of the contract is updated before any external calls.
1.3 Integer Overflow and Underflow Issues
- Integer overflow and underflow: In smart contracts, arithmetic operations that exceed the representation range of data types can lead to integer overflow or underflow, resulting in incorrect calculation results.
- Example: Some DeFi projects have suffered from fund theft due to integer overflow vulnerabilities.
Preventive Measures
- Secure arithmetic operation libraries: Unlike Solidity's SafeMath library, TON does not have a similar library. However, developers can use standard libraries (such as stdlib.fc) to simplify development and ensure the security of arithmetic operations. Despite the lack of a dedicated SafeMath library, developers should still customize secure functions, perform strict input validation, and conduct boundary checks to prevent integer overflow and underflow.
1.4 Access Control Issues
- Access control issues: Improperly designed access control in smart contracts may allow unauthorized users to access sensitive functions or data.
- Example: Some contracts have been exploited by malicious users due to access control vulnerabilities, leading to unauthorized operations.
Preventive Measures
- Access control policies: TON provides detailed permission management and access control policies to ensure that only authorized users can execute critical operations. Developers should implement strict access control policies and conduct regular access control audits to ensure the security of contracts and prevent unauthorized access.
In addition, we note that the TON developer documentation also mentions other technical safeguards:
- Rigorous testing: TON encourages developers to conduct comprehensive unit testing, integration testing, and stress testing, and provides corresponding testing frameworks and tool support.
- Formal verification: Although TON does not mandate formal verification, it encourages developers to use formal verification tools to prove the correctness and security of smart contracts.
- Security audits: TON recommends that developers conduct third-party security audits before contract deployment to ensure contract security. The official documentation provides advice on how to select audit services and conduct audits.
2. Node Attacks
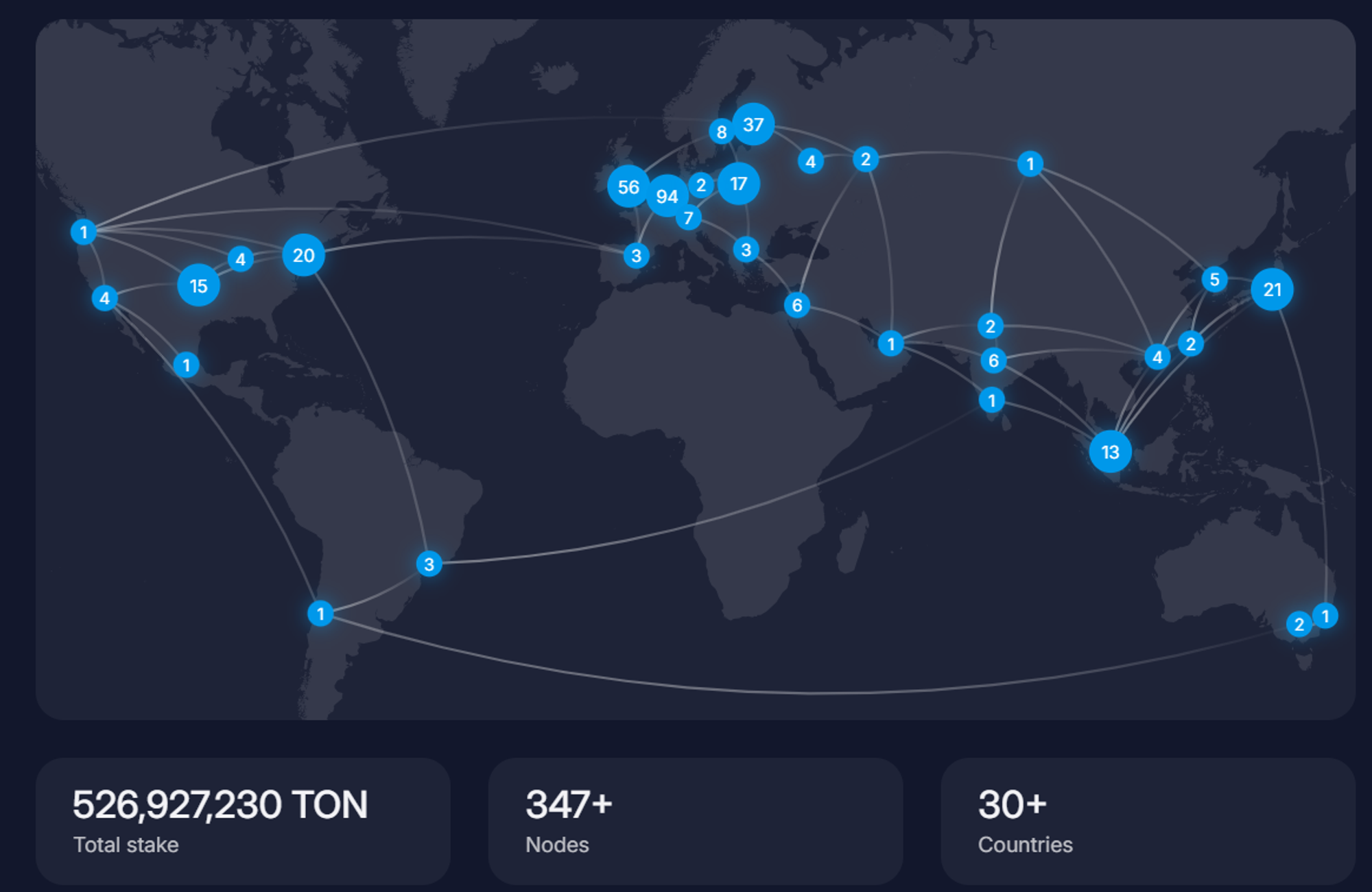
TON Node Distribution Map Source: TON Official Website
TON network adopts a Proof of Stake (PoS) consensus mechanism. As of June 3, there are a total of 347 nodes distributed in over 30 countries worldwide, with a concentration in Europe and the United States. The total staked amount exceeds 526 million TON, accounting for nearly 20% of the total circulation. A minimum of 300,000 TON is required for staking, and at least 400,000 TON is required for elections. It also has a penalty mechanism, where any network participant can lodge a complaint against a validator's behavior, and other validators vote on whether to hold them accountable.
In this context, TON's node technology safeguards the security of the chain:
- TON's high staking requirements and validator election mechanism reduce the risk of Sybil attacks.
- TON's global node distribution and network monitoring mechanisms help resist DDoS attacks.
- TON ensures each node maintains connections with a sufficient number of other nodes through diversified node connection strategies, reducing the risk of isolation and Eclipse attacks.
3. Technical Complexity and Implementation Risks
3.1 Complexity of Multi-Chain Architecture
- Implementation and Coordination Complexity: TON blockchain enhances flexibility and scalability through a multi-chain architecture, but efficient and reliable mechanisms are needed to ensure seamless interoperability and data synchronization. Developers need to create cross-chain communication protocols to ensure real-time and accurate data transmission and consistent consensus mechanisms.
- Security Risks: The frequent interaction of the multi-chain architecture increases security risks, as malicious actors may exploit these interactions to find system vulnerabilities. Therefore, the security of each blockchain and interaction interface is crucial.
- Solutions: TON introduces reliable consensus algorithms (such as BFT) and strict verification mechanisms, adopts efficient data synchronization protocols and optimized cross-chain communication mechanisms (such as instant hypercube routing), and implements dynamic sharding mechanisms to enhance scalability and performance.
3.2 Sharding Technology Challenges
- Security and Integrity: Sharding technology improves scalability, but shards may become targets for attacks, requiring robust security measures to protect each shard. TON adopts a bottom-up infinite sharding paradigm, treating each account or smart contract as an independent shard and enabling communication between shards through a messaging system.
- Load Balancing and Transaction Routing: Each shard needs to process its own transactions and coordinate transactions with other shards. TON introduces strict sharding conditions and merging rules to automatically shard during high loads and merge during low loads, determining global state through the hash value of main chain blocks to ensure data consistency and security.
- Data Consistency and Availability: Cross-shard data synchronization and coordination issues need to be addressed to avoid data inconsistency or latency issues. TON utilizes instant hypercube routing technology to achieve efficient message delivery and cross-shard communication, ensuring rapid data synchronization to the target shard.
TON's multi-chain architecture and sharding technology bring significant technical challenges and risks. TON aims to enhance network flexibility, scalability, and security by introducing efficient consensus algorithms, dynamic sharding mechanisms, and optimized cross-chain communication strategies. These measures to some extent ensure the stability and reliability of the TON network.
4. Network Performance and Scalability
4.1 Transaction Throughput Limitations
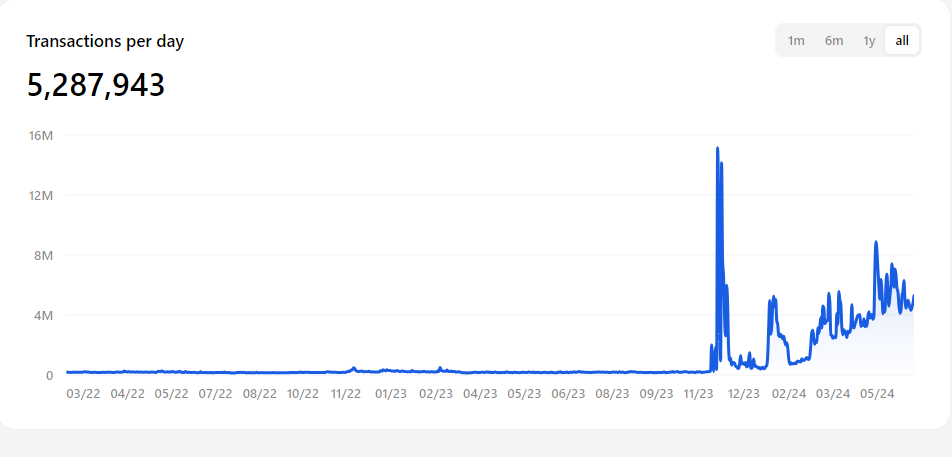
Daily Transaction Volume on TON Source: tonstat
- Transaction Volume: The TON network processes over 5 million transactions per day. This demonstrates TON's capability in handling high-frequency transactions but also indicates the need for efficient processing and scalability.
- Transaction Throughput Limitations: Despite the current high transaction volume, the pressure on transaction throughput will increase with the growth of users and applications. Continuous optimization and innovative solutions are needed to ensure that the network can handle higher transaction volumes and maintain its performance and stability.
- Network Congestion: When transaction volume sharply increases, network congestion may occur, affecting overall performance. Despite TON's dynamic sharding mechanism and instant hypercube routing technology, there is still a risk of resource limitations. High transaction volume and complex sharding may lead to resource exhaustion in certain nodes, hindering efficient processing of all requests.
- Protocol Limitations: The design of the TON protocol may have bottlenecks, such as the efficiency of the consensus mechanism and the overhead of inter-node communication. As transaction volume increases, these bottlenecks may become more prominent, affecting overall network performance.
- Scalability Challenges: To cope with the increasing transaction volume, TON needs to expand its network architecture. This includes increasing the number of nodes and improving consensus algorithms, but these improvements need to ensure that they do not compromise the stability and security of the existing system.
4.2 Network Latency and Stability
TON blockchain aims for low latency, real-time transactions to support live applications, but achieving this goal presents various challenges and potential bottlenecks:
- Network Latency: In a decentralized network, the geographical dispersion of nodes inevitably affects network transmission times. Synchronization delays between nodes and the reliability of data transmission can cause transaction delays.
- Node Synchronization: Nodes need to maintain consistent ledger states, requiring frequent communication and data synchronization. Any delay or failure in a node can affect the overall network response time.
- High Transaction Load: As transaction volume increases, the difficulty of processing transactions in real-time also increases. The system may require more time to verify and confirm transactions, increasing the risk of latency.
- Potential Attacks: Faced with potential network attacks, such as DDoS attacks, maintaining low latency and high stability becomes more challenging. Attackers may deliberately cause network congestion by sending a large number of transactions, affecting service quality.
- Reliability Assurance: Ensuring network stability and reliability under high loads and potential attacks is a significant challenge, requiring complex monitoring and rapid response mechanisms.
In conclusion, while the TON blockchain has many innovations in its design, it still needs to address challenges in transaction throughput, network latency, and stability to truly achieve its intended high performance and scalability goals.
5. Technical Upgrades and Maintenance
5.1 Upgrade Compatibility
Technical upgrades are crucial for maintaining the security, performance, and meeting new feature requirements of the TON blockchain system. However, compatibility issues may bring a series of technical risks:
- Version Compatibility Issues: Technical upgrades need to ensure that new versions seamlessly connect with old versions. Any interface changes, data structure adjustments, or protocol updates may trigger compatibility issues. If backward compatibility cannot be ensured, nodes may experience network splits (i.e., forks) due to version inconsistencies.
- Data Migration Risks: Data migration is an important task during technical upgrades. During the migration process, data loss or inconsistency issues may arise, affecting user experience and even causing trust crises. Strict data backup and verification mechanisms are needed to ensure the reliability of data migration.
- Node Restart and Network Stability: Technical upgrades often require node restarts. Frequent node restarts may cause temporary network instability, affecting real-time and continuous transaction processing. Detailed restart plans need to be formulated, upgrades should be performed during low system loads, and robust rollback mechanisms should be in place to quickly restore stability in case of unexpected situations.
- Planning and Coordination: Large-scale technical upgrades of blockchain systems require meticulous planning and coordination. Involving numerous nodes in synchronous operations, any mistakes in any part of the process may lead to irreversible consequences. Therefore, the details of each step must be clear, and all stakeholders need to be fully communicated and trained.
5.2 Code Quality and Audits
TON's GitHub Interface Source: Github
As an open-source project, the code quality and audit mechanisms of the TON blockchain directly impact the system's security and stability. Based on the current status of TON's GitHub, we can see how its code quality and audit mechanisms contribute to the maintenance of system security and stability.
Code Quality and Audits
- Code Readability and Maintainability: TON's GitHub repository is active, regularly updated, and maintained. The code is clear, well-structured, and extensively commented, making it easy for developers to understand and maintain. The use of static code analysis tools (such as stdlib.fc) and automated testing tools further enhances code quality.
- Internal Audits: TON's development team implements a multi-level code review mechanism, requiring peer reviews and approval from senior developers for each code submission. This allows for the timely discovery and resolution of potential issues, reducing the occurrence of vulnerabilities.
- Third-Party Security Audits: TON regularly invites professional third-party security organizations to conduct comprehensive code audits. This helps identify issues that the internal team may have overlooked, ensuring system security. The audit reports are transparent and publicly available, enhancing community trust.
- Open Source Community Feedback: TON collects and addresses community suggestions and vulnerability reports in a timely manner through bug bounty programs and open community governance mechanisms, continuously improving code quality.
TON has adopted multi-level and multi-perspective measures to ensure code quality and audits, including strict coding standards, internal multi-level audits, third-party security audits, and active feedback from the open-source community. These measures work together to ensure the security and stability of the TON blockchain system, enabling it to cope with complex technical environments and evolving security threats. Additionally, the use of static code analysis and automated testing tools further enhances code quality assurance and reduces potential security risks.
6. Decentralization Risks
6.1 Node Centralization
The TON network adopts a Proof of Stake (PoS) consensus model to ensure its security and stability. Here is an in-depth analysis of its decentralization:
Global Distribution
The number of nodes is an important indicator of the degree of decentralization of a blockchain network. A higher number of nodes means a wider distribution of power and control, representing greater decentralization. However, the quality and geographical distribution of nodes are also important. If nodes are highly concentrated in a specific geographical area or controlled by a few entities, it may weaken the effect of decentralization. The distribution of TON validation nodes in over 30 countries globally, with a significant concentration in Europe and the United States, helps resist geopolitical risks and physical attacks, enhancing the network's reliability and resilience.
Node Count and Staked Amount
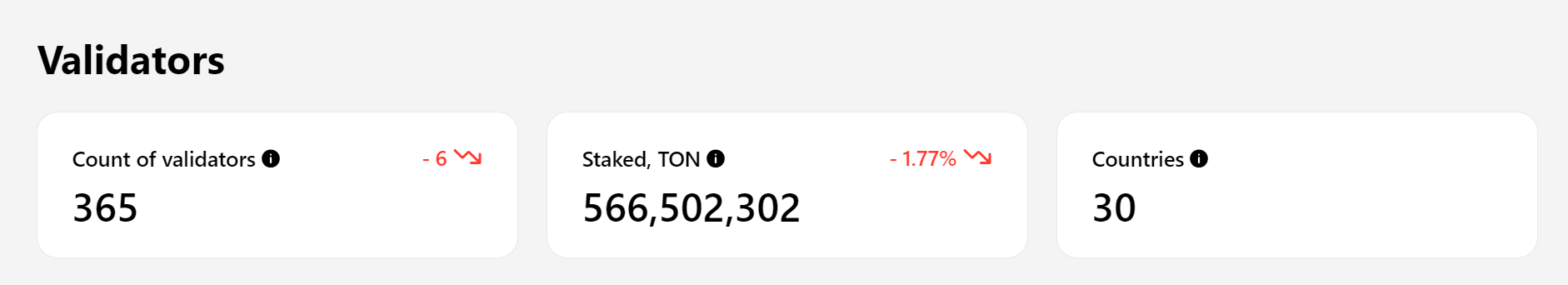
Validation Node Data Source: Tonstat
As of July 5th, there are over 365 nodes with a total staked amount exceeding 566 million TON, accounting for nearly 20% of the total circulation. The widespread distribution of node count and staked amount is an important indicator of a decentralized network, as it means no single entity can easily control or attack the entire network.
- Compared to mature networks like Bitcoin or Ethereum, which have thousands of nodes, the number of nodes in TON may seem relatively small. However, for a relatively young or continuously developing network, the current number of nodes is a reasonable starting point.
Validator Threshold and Election
Anyone with enough Toncoin (at least 300,000 TON) and winning the election (requiring at least 400,000 TON) can become a validator. While the high staking requirement ensures the sincerity and contribution of participants, it may reduce the likelihood of ordinary users' participation. This high threshold enhances security but may also limit the growth of the node count, so a balance needs to be found between attracting more participants and maintaining network security.
However, despite this threshold not being low, it still maintains a certain level of openness compared to some other blockchain systems. Additional validator election processes further prevent the monopoly of a few nodes.
Rewards and Inflation
Validators earn rewards by validating transactions and generating new tokens, with an average daily income of approximately 120 TON and an overall annual inflation rate of about 0.5%. Reasonable reward mechanisms and a relatively low inflation rate help ensure the motivation of validators and the economic stability of the network.
Penalty Mechanism
The penalty mechanism for validators includes penalties for not participating in block creation and malicious behavior, ensuring the honesty and active participation of validators. Additionally, any network participant can file a complaint against a validator, providing encrypted evidence, and other validators vote on whether to pursue the complaint. This self-regulating mechanism further enhances the fairness and transparency of the network.
The TON network demonstrates good decentralization in terms of globally distributed nodes, a high validator threshold, reasonable reward mechanisms, and strict penalty mechanisms. These factors work together to ensure the security, stability, and fairness of the network, preventing power from being concentrated in the hands of a few. However, further research and confirmation are needed regarding the authenticity of the data information about TON's node validators.
6.2 Governance Mechanism Risks
To maintain the stability and sustainable development of the network, a good governance mechanism needs to address risks such as decision transparency, conflicts of interest, and governance deadlock. From the interpretation of TON's governance mechanism, it is evident that TON has taken various measures to address these challenges, ensuring the system's security and stability:
- Public voting and recording functions, as well as the automatic execution of smart contracts, ensure transparency in the governance process.
- A multi-level governance structure and a reasonable proposal and voting mechanism balance the interests of different stakeholders, reducing conflicts.
- Setting proposal and voting time limits and using smart contracts for automatic arbitration help avoid governance deadlock, ensuring a smooth decision-making process.
These measures work together to maintain the effectiveness and fairness of TON's governance mechanism, safeguarding the healthy development of the project and ensuring relatively fair governance operations.
Legal and Compliance Regulatory Risks
1. Current Status and Regional Risk Analysis of TON
After undergoing legal litigation between Telegram and the SEC, the TON (The Open Network) public chain was taken over by community members for continued development. Despite its enormous potential for development, TON still faces significant compliance challenges in various jurisdictions worldwide. The following analysis examines the regulatory environment and related risks in several major regions:
> United States
- Regulatory Agencies: SEC, CFTC, FTC, IRS, FinCEN
- Key Regulations: Securities Act, Commodity Exchange Act, Anti-Money Laundering (AML) laws, etc.
- Risk Analysis: Due to strict regulations in the United States, TON's tokens (such as Gram) may be considered securities and require registration and compliance with relevant laws and regulations. The previous SEC lawsuit demonstrated its compliance risks, and TON needs to ensure that future token issuance and trading comply with US securities laws, AML regulations, and other requirements.
> Singapore
- Regulatory Agency: Monetary Authority of Singapore (MAS)
- Key Regulations: Securities and Futures Act, Payment Services Act
- Risk Analysis: Singapore is relatively friendly to Web3 projects, but TON needs to clarify whether its tokens fall under MAS-defined digital asset products and comply with relevant regulations. Due diligence and AML measures need to be strictly enforced to ensure compliant operations.
> Hong Kong, China
- Regulatory Agency: Securities and Futures Commission of Hong Kong (SFC)
- Key Regulations: Securities and Futures Ordinance
- Risk Analysis: Hong Kong has introduced a series of policies to support Web3 projects in recent years, but TON needs to obtain the necessary licenses and ensure that its exchanges and related businesses comply with Hong Kong's regulatory requirements. Additionally, attention needs to be paid to compliance with data protection and privacy regulations.
2. Legal Compliance and Regulatory Risks in TON Operations
2.1 Securities Law Compliance
- Risk Description: TON's token issuance and trading may be considered securities transactions, requiring compliance with registration and disclosure requirements of securities laws in various countries.
- Detailed Analysis: In the United States, the Gram token was deemed a security by the SEC and required registration or exemption. TON needs to clarify the legal nature of its tokens in various countries to ensure compliance with securities laws. By using legitimate issuance methods, such as registration or obtaining exemptions, the legal risks associated with unregistered securities issuance can be reduced.
- Current Measures: TON has explicitly stated that its token issuance and trading comply with the legal requirements of various countries. Although Gram tokens have not been issued, the compliance of Toncoin used by TON in different jurisdictions is still closely monitored. TON ensures that its token issuance and trading comply with securities laws through a legal advisory team.
2.2 Anti-Money Laundering (AML) and Know Your Customer (KYC)
- Risk Description: Countries around the world have strict anti-money laundering (AML) and know your customer (KYC) requirements, and TON needs to ensure that its platform is not used for money laundering and terrorist financing activities.
- Detailed Analysis: As a decentralized platform with users from around the world, TON needs to implement AML and KYC measures in various jurisdictions. Specific measures include establishing user identity verification mechanisms, transaction monitoring systems, and conducting regular risk assessments and reporting to ensure that the platform is not exploited for illegal activities.
- TON has implemented strict AML and KYC measures, using advanced machine learning and AI technology for transaction monitoring and risk assessment to ensure real-time identification and prevention of suspicious activities. TON has established a globally unified KYC standard to meet the legal requirements of different countries.
2.3 Data Protection and Privacy
- Risk Description: Global data privacy regulations are becoming increasingly strict, and TON needs to ensure that the processing of user data complies with data protection laws in various countries.
- Detailed Analysis: In the EU, TON needs to comply with the General Data Protection Regulation (GDPR), and in the US, it needs to comply with the California Consumer Privacy Act (CCPA). TON should take measures to ensure the security of user data, including encryption and anonymization, establishing data protection policies, and conducting regular security audits to prevent data breaches and misuse.
- TON has implemented the latest data encryption technology and anonymization measures to ensure the security of user data during transmission and storage. Regular data protection audits are conducted, and independent security assessments and vulnerability fixes are carried out in collaboration with third-party security companies to prevent data breaches and misuse.
2.4 Investor Protection
- Risk Description: TON needs to ensure that investors receive sufficient disclosure of information to avoid legal disputes due to insufficient information.
- Detailed Analysis: TON needs to ensure transparent disclosure of user information, including the project's financial status, risk factors, etc. By establishing effective investor protection mechanisms, such as transparent investment information disclosure, investor education, and advisory services, legal risks can be reduced.
- TON has established a dedicated investor relations team and regularly publishes project updates and financial reports. Through the official website and social media channels, transparent and timely information disclosure is ensured. TON also provides a multilingual investor education platform to help investors understand project risks and returns.
3. Compliance Recommendations
3.1 Framework Construction
Although the later TON chain was taken over by the foundation and developed independently from TG, its token distribution mechanism is still not clear.
Furthermore, global data privacy regulations are becoming increasingly strict, such as the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA). These regulations may affect advertisers' data collection and advertising strategies, requiring them to pay more attention to compliance and user privacy. However, data on TON can be protected through encryption and anonymization, ensuring the privacy of users during ad interactions. This allows advertisers to place ads without exposing users' personal identities. TON provides secure digital identity verification, allowing advertisers to better understand user interests and behavior without directly collecting personal data. Smart contracts can automatically execute ad revenue distribution and payments. This transparent and traceable mechanism can reduce the risk of data breaches, protecting the interests of users and advertisers. TON's decentralized advertising platform allows direct interaction between advertisers and content creators or users, reducing intermediaries. This model can improve the accuracy of ad placement and reduce excessive collection of user data.
3.2 Legal Risk Management Strategy
TON has a sufficient user base and traffic, but continued development still needs to follow a compliant path. TON's headquarters have been moved to Zug, Switzerland, which is widely seen as related to the generally positive attitude of Swiss authorities towards the cryptocurrency industry.
Regulatory risks are still a factor. However, it is believed that, given the previous experience with the SEC, the foundation and investors have experience and expectations regarding risks. Although not much has been disclosed publicly, it is clear that Telegram is making efforts to integrate the token system into the platform. It is reasonable to expect that Telegram has negotiated and taken compliance measures to ensure that its current and future TON operations comply with necessary legal requirements.
Future Trends and Innovation Risks
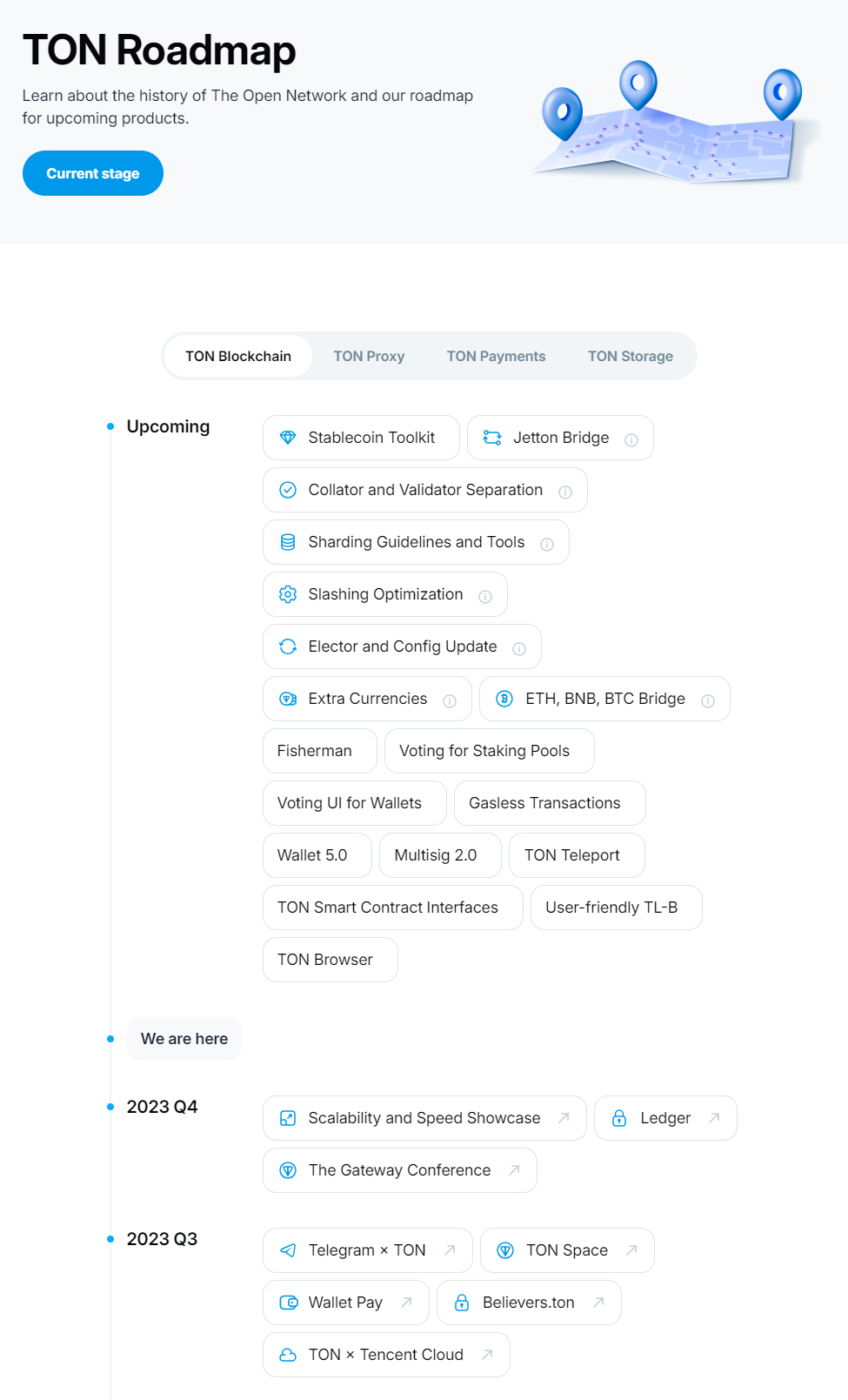
TON Development Roadmap Source: TON Official Website
Based on TON's roadmap and future development trends mentioned in blogs and other content, there are still some shortcomings in the current development of the TON ecosystem:
1. Lack of Ecosystem Diversity
Although the TON team has been developing and integrating various technical tools and applications, many core tools and services are still in the development stage. For example, key components such as the Stablecoin Toolkit, Jetton Bridge for cross-chain transactions, and support for multiple currencies (Extra Currencies) have not been fully implemented. This limits the availability and attractiveness of the ecosystem, hindering the rapid implementation and user participation of more applications and services.
- Technical Implementation Difficulty: Developing and integrating these core components requires addressing complex technical issues such as cross-chain protocols, asset exchange mechanisms, and multi-currency support. This not only requires high-level engineering input but also long-term iteration and optimization.
- Legal Compliance: Compliance with the requirements of different jurisdictions during the development process is necessary to ensure legality on a global scale.
2. Need for Improved User Experience
Many user interaction interfaces in the TON system, such as wallets and smart contract interfaces, still need improvement in terms of usability and user experience. The user experience for asset management, smart contract operations, and participation in decentralized applications may still not be intuitive and user-friendly. This requires the TON team to invest more effort in designing and optimizing user interfaces and user experience (UX/UI) to reduce the learning curve and usage barriers for users.
- Technical Implementation Difficulty: Optimizing wallet and smart contract interfaces requires a deep understanding of user needs and the use of advanced interaction design and visualization technology. Additionally, implementing innovative features such as "gas-free" transactions requires significant changes to the consensus mechanism and transaction model.
- Legal Compliance: While optimizing user experience, it is essential to ensure the compliance of user data protection and privacy, adhering to data protection regulations such as GDPR.
3. Insufficient Cross-Chain Interoperability
Although TON has planned to introduce cross-chain bridges for assets transfer between different blockchain networks such as ETH, BNB, and BTC, the existing cross-chain interoperability still needs further enhancement. The complexity and security issues of cross-chain asset management and operations remain a significant challenge.
- Technical Implementation Difficulty: Developing cross-chain bridges requires addressing multiple technical challenges related to security, reliability, performance, and requires deep integration and coordination with multiple heterogeneous blockchain networks to ensure secure asset transfer and interoperability.
- Legal Compliance: Cross-chain operations involve cross-border financial activities and need to comply with financial regulatory requirements in various countries, especially in terms of payments and securities laws, to ensure the legality of cross-chain asset transfers.
4. Privacy Protection
Privacy protection technologies such as zero-knowledge proofs and homomorphic encryption have high technical difficulty. These technologies need to ensure user data privacy without affecting system performance and usability.
- Technical Implementation Difficulty: Implementing these technologies requires high-level research and development, involving complex mathematical algorithms and encryption technologies.
- Legal Compliance: The application of privacy technologies needs to comply with laws and regulations in different countries and regions to ensure compliance with data protection and privacy policies.
5. Performance Scalability
As user and transaction volumes increase, the TON blockchain needs to continuously improve its performance and scalability to support high concurrency and large-scale applications.
- Technical Implementation Difficulty: Performance scalability involves optimizing the underlying architecture and technological innovation to ensure stable operation under high loads.
- Network Security: While expanding network performance, potential network attacks and security vulnerabilities must be guarded against to ensure system stability and security.
6. Developer Support
Although TON provides a rich set of development tools and resources, continuous optimization and updates are needed to meet the evolving needs of developers.
- Tools and Resources: There is a need to provide more comprehensive and user-friendly development tools and documentation, supporting a wider range of programming languages and development environments.
- Education and Training: Increase developers' understanding and application capabilities of TON technology, provide effective education and training resources to help more developers master and utilize TON blockchain technology.
7. Insufficient Decentralization and Security
TON system still has some shortcomings in decentralization and security. For example, the mechanism for the separation of validators and collectors has not been fully implemented, which may lead to the system not being ideal in terms of decentralization and censorship resistance.
- Technical Implementation Difficulty: The design and implementation of mechanisms such as the separation of validators and collectors, Slashing Optimization, etc., require deep restructuring of the consensus protocol, involving complex network security and economic incentive system design.
- Legal Compliance: While transforming and optimizing the consensus mechanism, it is necessary to ensure compliance with financial security, anti-money laundering, and other regulations, to operate in a legal and secure manner.
Although TON has taken proactive measures in ecosystem diversity, user experience, cross-chain interoperability, privacy protection, performance scalability, developer support, decentralization, and security, there is still a need for further improvement and enhancement to address future challenges.
Summary and Recommendations
As an innovative and rapidly developing blockchain project, TON demonstrates tremendous potential. However, it still has shortcomings in ecosystem diversity, user experience, cross-chain interoperability, and compliance. Despite this, TON has shown strong adaptability and a spirit of continuous innovation in its development process.
As a project that has been shut down due to regulatory issues after running vigorously, it is evident that TON places a high emphasis on compliance after its restart. Through a series of measures, TON has made comprehensive arrangements in legal compliance, aiming to ensure the legal operation of its platform globally, reduce legal risks, and enhance user trust.
Although TON has taken proactive measures in compliance, the highly encrypted and anonymous nature of the Telegram platform itself has attracted a large number of illegal actors. Additionally, the privacy and decentralized financial nature of blockchain provide convenience for illegal activities, making it a potential breeding ground for gray and black industries. Although KYC is required for withdrawals from TON wallets, using only an ID may not completely eliminate illegal activities.
Future regulatory challenges remain severe, and TON must continue to monitor and adapt to the constantly changing global regulatory environment to avoid the risk of being shut down again. The more prosperous the ecosystem becomes, the greater the regulatory risks it faces. All projects must face the challenges of technical security, user privacy protection, and compatibility with traditional financial systems.
The risk road for TON is long and arduous.
Contributors: Mat / Riffi / Sylvia / Shawn / Darl / Biu
Editing and Proofreading: Punko
Special Thanks: Thanks to the above collaborating units and partners for their outstanding contributions to the content of this issue.
References
- Securities Act of 1933: https://www.law.cornell.edu/wex/securities_act_of_1933
- General Data Protection Regulation (GDPR) in Europe: https://gdpr.eu
- California Consumer Privacy Act (CCPA): https://oag.ca.gov/privacy/ccpa
- TON Open Network Documentation: FunC Language Guide
- TON Blockchain Development Documentation: Smart Contract Vulnerability Analysis
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




