Users must not click on suspicious links disguised as rewards, airdrops, or other positive news.
Author: SharkTeam
Web3 phishing is a common attack method targeting Web3 users, aiming to steal users' authorization, signatures, or induce users to make mistakes in various ways in order to steal their encrypted assets.
In recent years, Web3 phishing incidents have continued to occur, and a black industry chain of phishing as a service (DaaS) has emerged, making the security situation severe.
In this article, SharkTeam will systematically analyze common Web3 phishing methods and provide security prevention suggestions for reference, hoping to help users better identify phishing scams and protect their encrypted assets.
I. Analysis of Common Phishing Methods
1. Permit Off-chain Signature Phishing
Permit is an extension function for authorization under the ERC-20 standard, which allows you to sign to authorize other addresses to move your tokens. The principle is that by signing, you indicate that the authorized address can use your tokens through this signature. The authorized address then uses your signature to interact with the permit on-chain and gains the authorization to transfer your assets. Permit off-chain signature phishing usually consists of three steps:
(1) Attackers forge phishing links or phishing websites to induce users to sign through their wallets (no contract interaction, not on-chain).
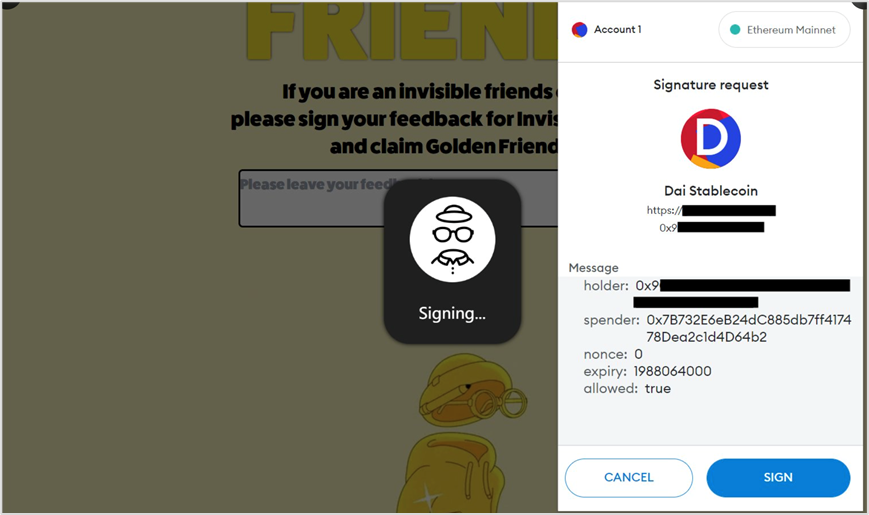
Signature object: DAI/USDC/WETH and other ERC20 tokens (here it is DAI)
holder:// Signature address
spender:// Phishing address
nonce:0
expiry:1988064000 // Expiration time
allowed:true
If the signature is obtained, the phisher obtains the signature (a set of r, s, v values, which the phisher needs to use when interacting with the permit function) for stealing DAI/USDC/WETH and other ERC20 tokens (here it is DAI) from the victim.
(2) Attackers call the permit function to complete the authorization.
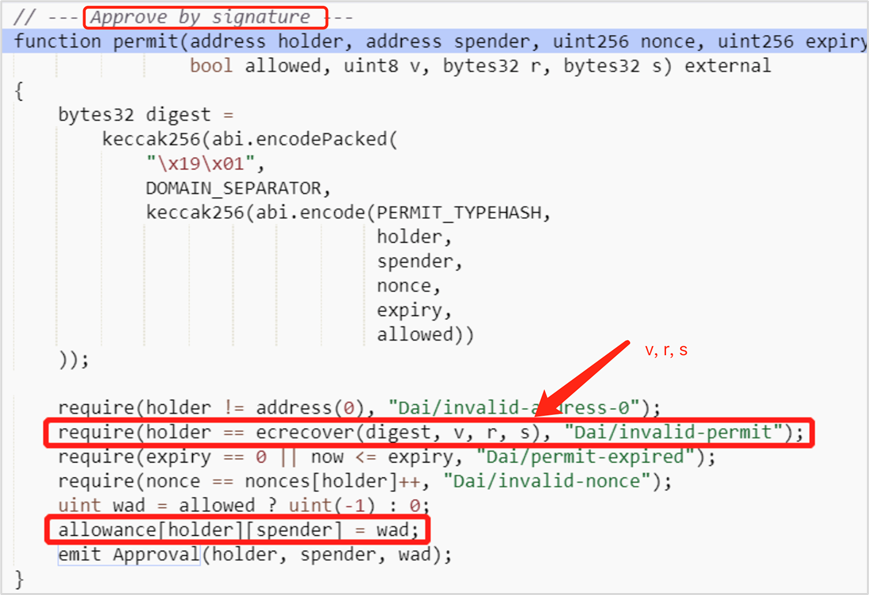
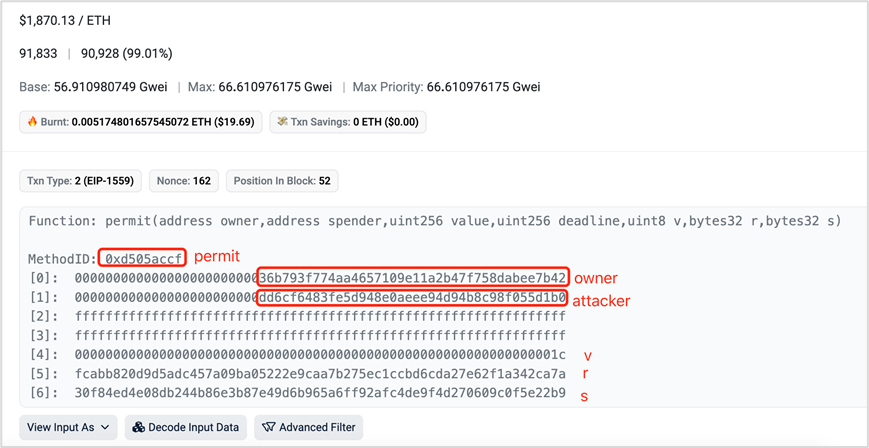
https://etherscan.io/tx/0x1fe75ad73f19cc4c3b658889dae552bb90cf5cef402789d256ff7c3e091bb662
(3) Attackers call the transferFrom function to transfer the victim's assets and complete the attack.
Here, it should be noted that there is a difference between transfer and transferFrom. When we directly transfer ERC20 tokens, we usually call the transfer function in the ERC20 contract, while transferFrom is usually used when authorizing a third party to transfer ERC20 tokens from our wallet to another address.
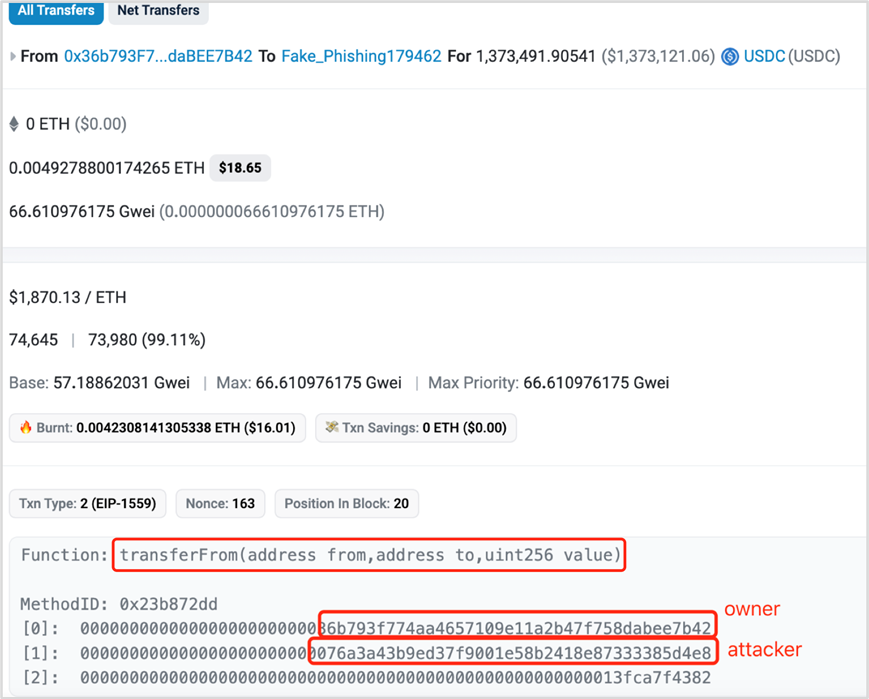
https://etherscan.io/tx/0x9c02340896e238fc667c1d84fec78af99b1642c986fe3a81602903af498eb938
Additional note: This signature is an off-chain signature without gas. After obtaining it, the attacker will execute on-chain interactions with the permit and transferFrom, so there will be no authorization record in the victim's on-chain records, but it can be seen in the attacker's address. Generally, this type of signature is one-time and does not pose a continuous phishing risk.
2. Permit2 Off-chain Signature Phishing
Permit2 is a smart contract launched by Uniswap at the end of 2022 to facilitate user usage. It is a token approval contract that allows token authorization to be shared and managed in different DApps. With more projects integrating with Permit2 in the future, the Permit2 contract can achieve a more unified authorization management experience in the DApp ecosystem and save user transaction costs.
Although Permit2 improves the user experience, it also brings phishing attacks targeting Permit2 signatures. Similar to Permit off-chain signature phishing, Permit2 is also an off-chain signature phishing. This type of attack mainly consists of four steps:
(1) The prerequisite is that the user's wallet has previously authorized the token balance to Uniswap's Permit2 contract before being phished (Permit2 defaults to allowing users to authorize the entire balance of the token).
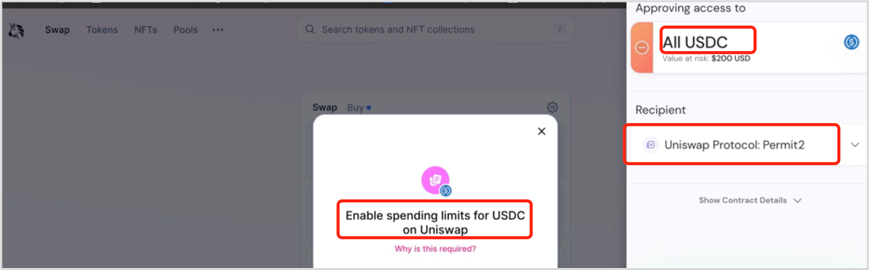
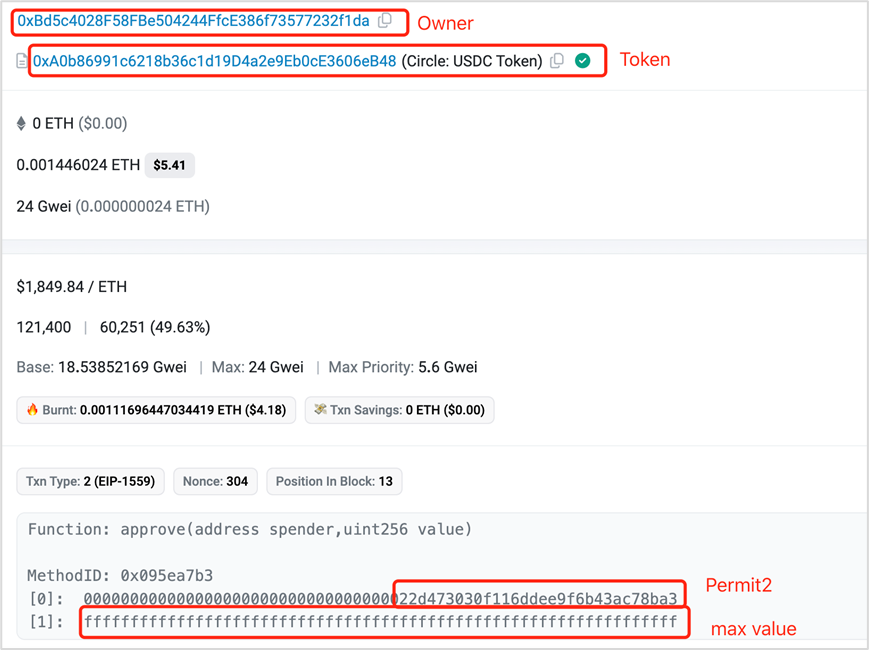
https://etherscan.io/tx/0xd8f0333b9e0db7175c38c37e490379bde5c83a916bdaa2b9d46ee6bff4412e8f
(2) Attackers forge phishing links or pages to induce users to sign, and the phishing attacker obtains the required signature information, similar to Permit off-chain signature phishing.
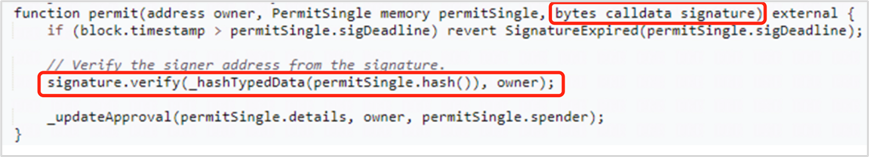
(3) Attackers call the permit function of the Permit2 contract to complete the authorization.
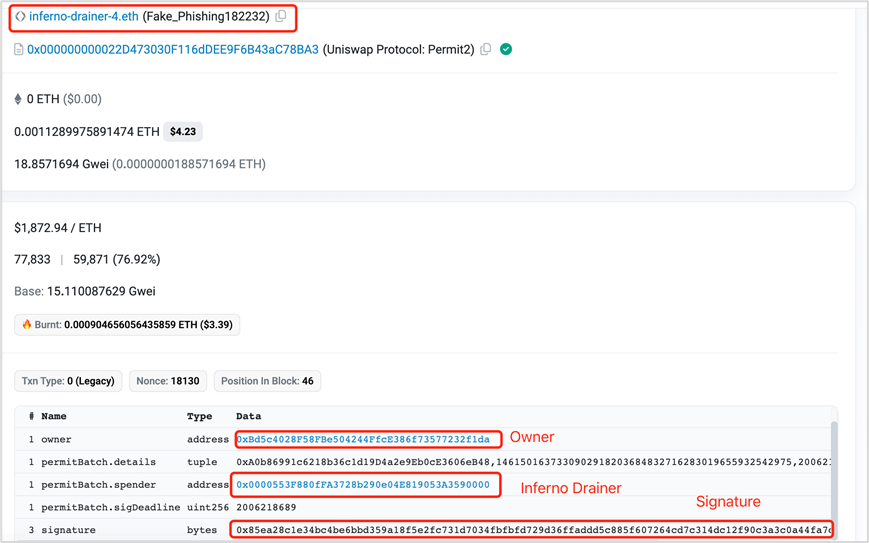
https://etherscan.io/tx/0xd8c3f55dfbc8b368134e6236b296563f506827bd5dc4d6c0df39851fd219d658
(4) Attackers call the transferFrom function of the Permit2 contract to transfer the victim's assets and complete the attack.
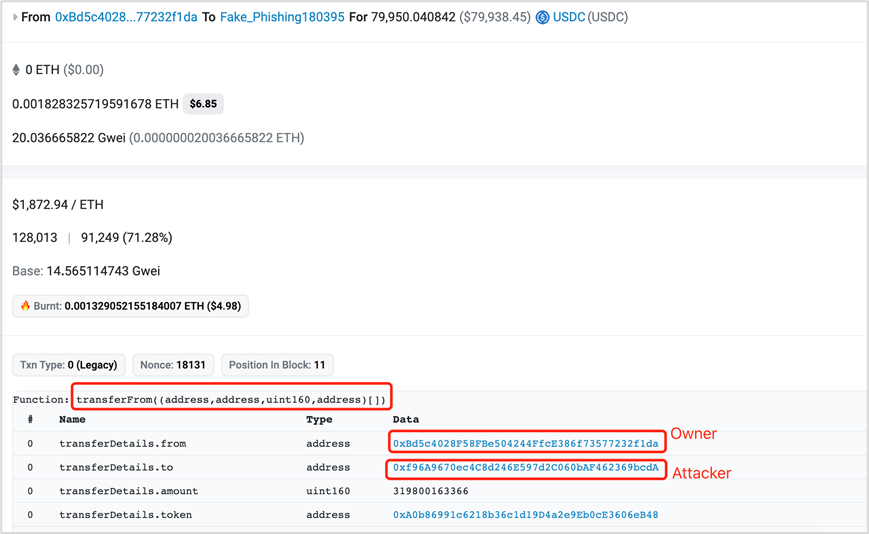
https://etherscan.io/tx/0xf6461e003a55f8ecbe919a47b3c0dc6d0f068e48a941658329e35dc703138486
Additional note: In this case, the address receiving the assets is usually multiple. Typically, one of the largest recipients is the attacker implementing the phishing, while the others are addresses providing phishing as a service (DaaS) such as PinkDrainer, InfernoDrainer, AngelDrainer, etc.
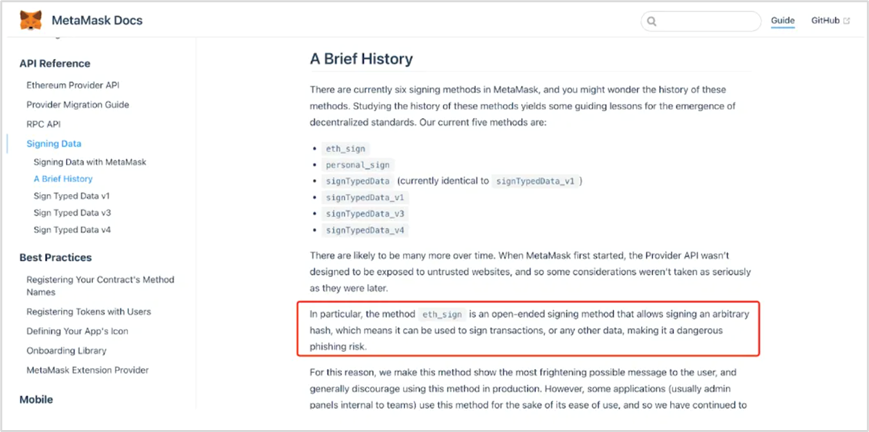
3. eth_sign On-chain Blind Signature Phishing
ethsign is an open signature method that can be used to sign any hash. Attackers only need to construct any malicious data requiring a signature (such as token transfers, contract calls, authorization retrieval, etc.) and induce users to sign through ethsign to complete the attack.
MetaMask provides a risk warning when signing with eth_sign. Web3 wallets such as imToken, OneKey have either disabled this function or provided risk warnings. It is recommended that all wallet manufacturers disable this method to prevent users from being attacked due to lack of security awareness or necessary technical knowledge.
4. personal_sign/signTypedData On-chain Signature Phishing
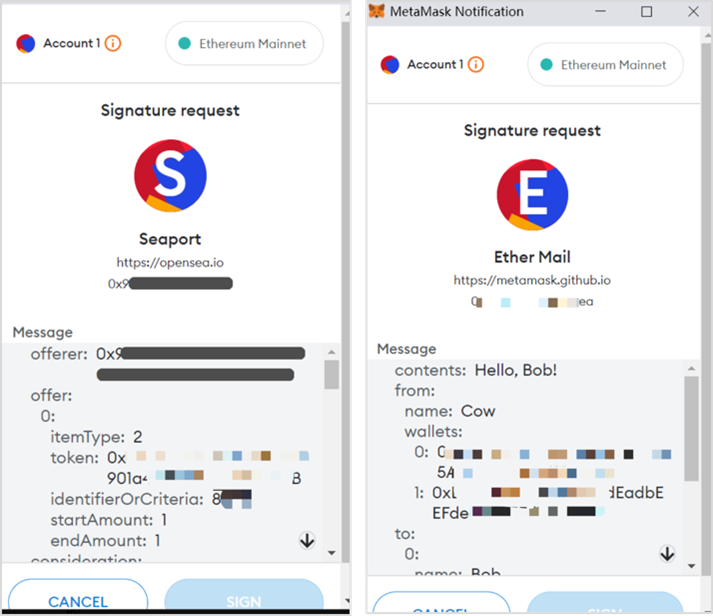
personal_sign and signTypedData are commonly used signature methods. Users usually need to carefully verify the initiator, domain, signature content, etc. for security. If there is a risk, extra caution should be taken.
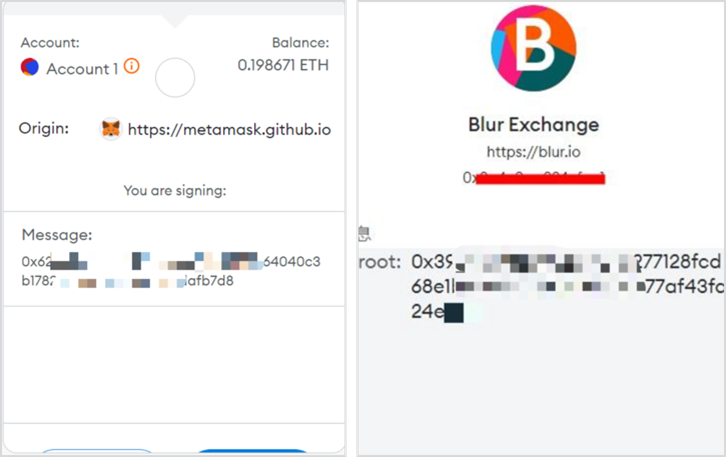
In addition, if personal_sign and signTypedData are used as "blind signatures" as in the above case, where the user cannot see the plaintext, it is easy for phishing groups to exploit and increases the phishing risk.
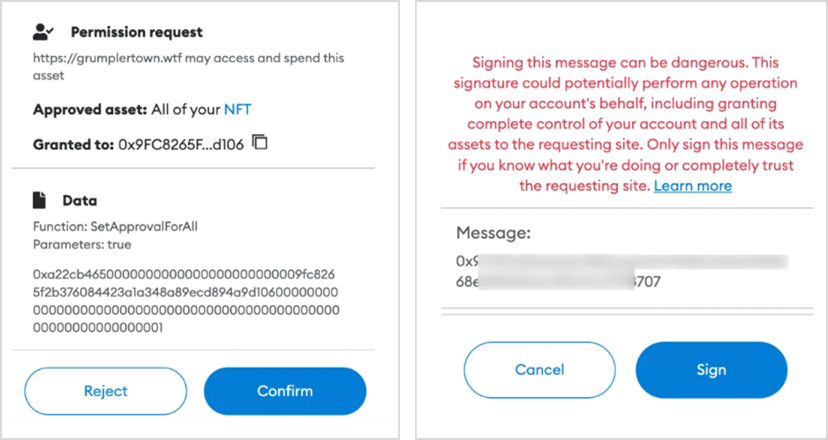
5. Authorization Phishing
Attackers create malicious websites or inject malware into project official websites to induce users to confirm operations such as setApprovalForAll, Approve, Increase Approval, Increase Allowance, etc., to obtain authorization for users' assets and carry out theft.
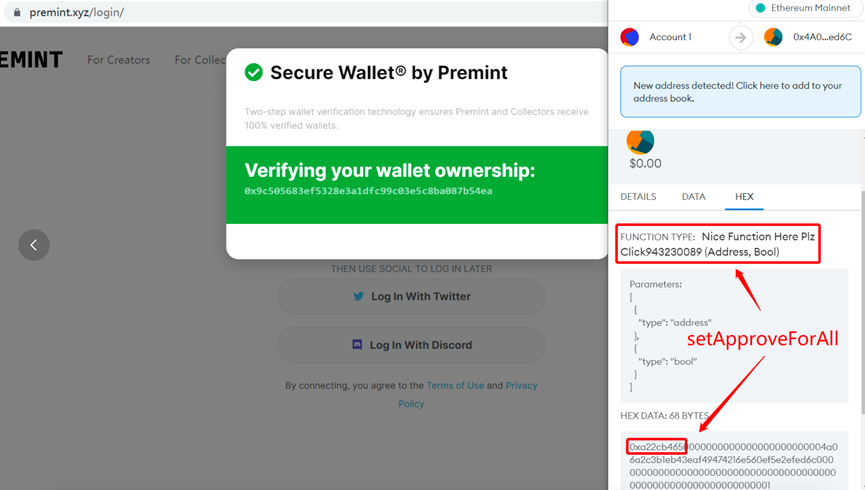
(1) setApprovalForAll
Taking the PREMINT malware injection phishing incident as an example, a JavaScript file on the project's website (https://s3-redwood-labs.premint.xyz/theme/js/boomerang.min.js) was injected with malicious code, which dynamically creates an injected malicious JavaScript file (https://s3-redwood-labs-premint-xyz.com/cdn.min.js?v=1658050292559). The attack is initiated by this malicious script.
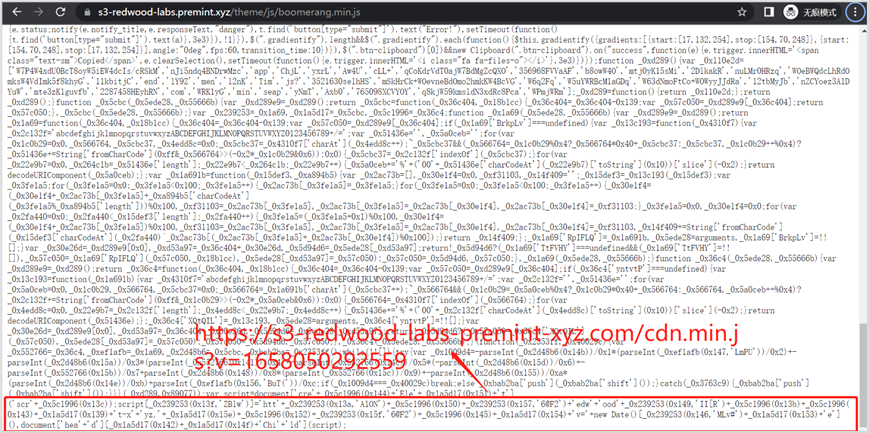
Due to not promptly identifying the risk, the user confirmed the setApprovalForAll operation, inadvertently leaking authorization for asset operations, resulting in asset theft.
(2) Approve
Similar to setApprovalForAll, the user confirmed the Approve operation, leaking authorization for asset operations, resulting in asset theft.
Misauthorized Approve:
https://etherscan.io/tx/0x4b0655a5b75a9c078653939101fffc1d08ff7e5c89b0695ca6db5998214353fa
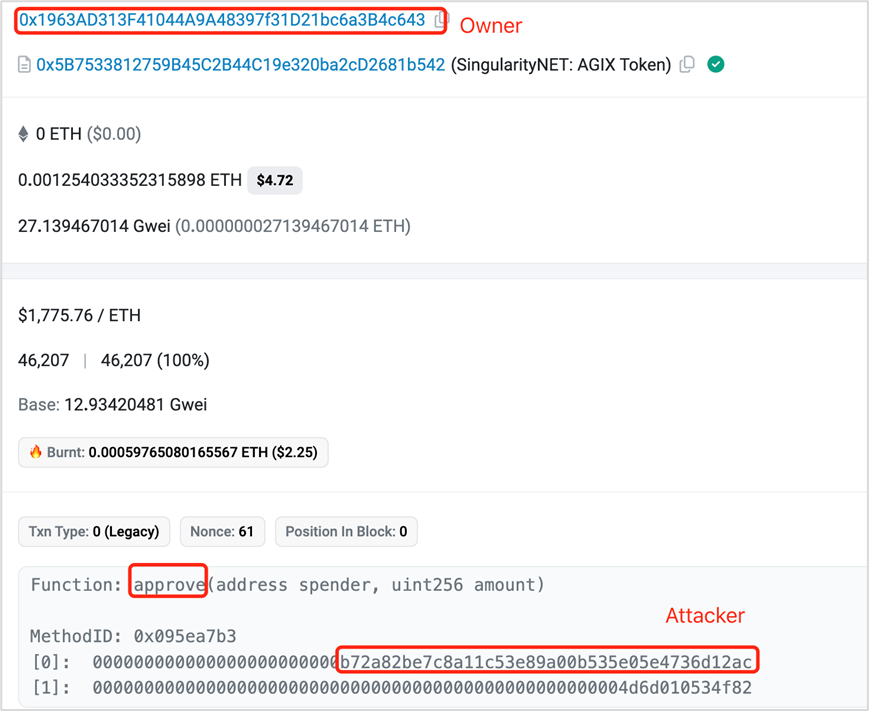
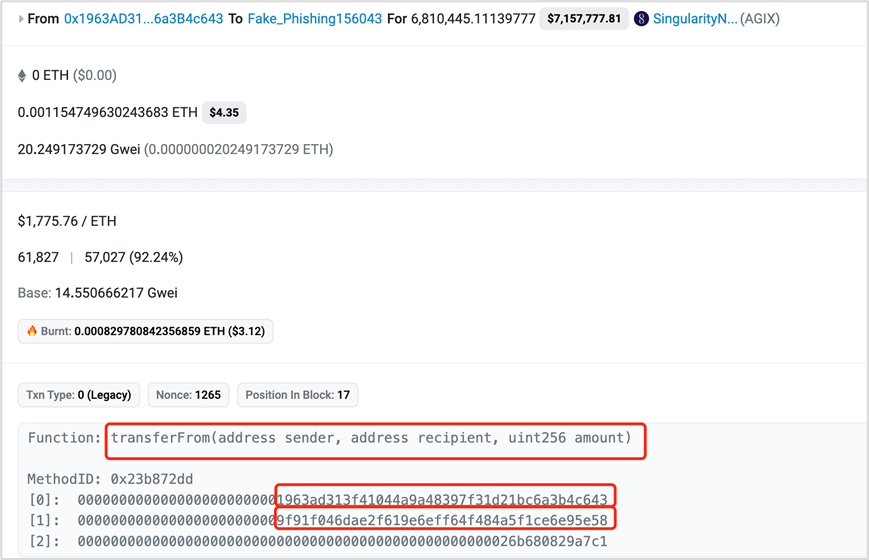
The attacker transferred assets through transferFrom:
https://etherscan.io/tx/0x0dedf25777ff5483bf71e70e031aacbaf50124f7ebb6804beb17aee2c15c33e8
The attack principles of Increase Approval and Increase Allowance functions are similar. By default, the attacker's upper limit for the victim's token operations is 0, but after authorizing through these two functions, the attacker increases the upper limit for the victim's tokens and can then transfer the tokens within that limit.
(3) Increase Approval
Misauthorized Increase Approval:
https://etherscan.io/tx/0x7ae694080e2ad007fd6fa25f9a22ca0bbbff4358b9bc84cc0a5ba7872118a223
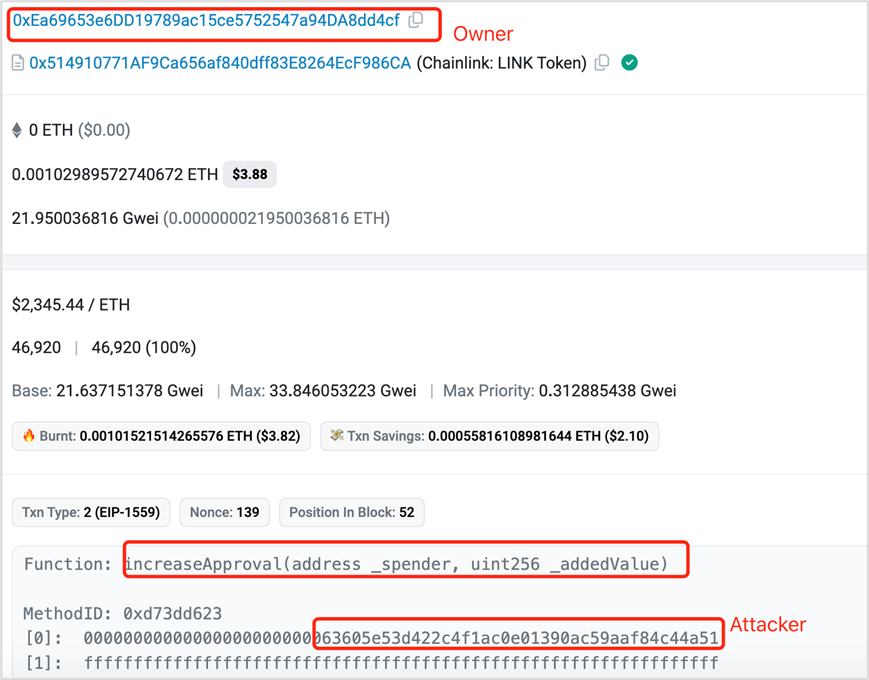
The attacker transferred assets through transferFrom:
https://etherscan.io/tx/0x15bc5516ed7490041904f1a4c594c33740060e0f0271cb89fe9ed43c974a7a69
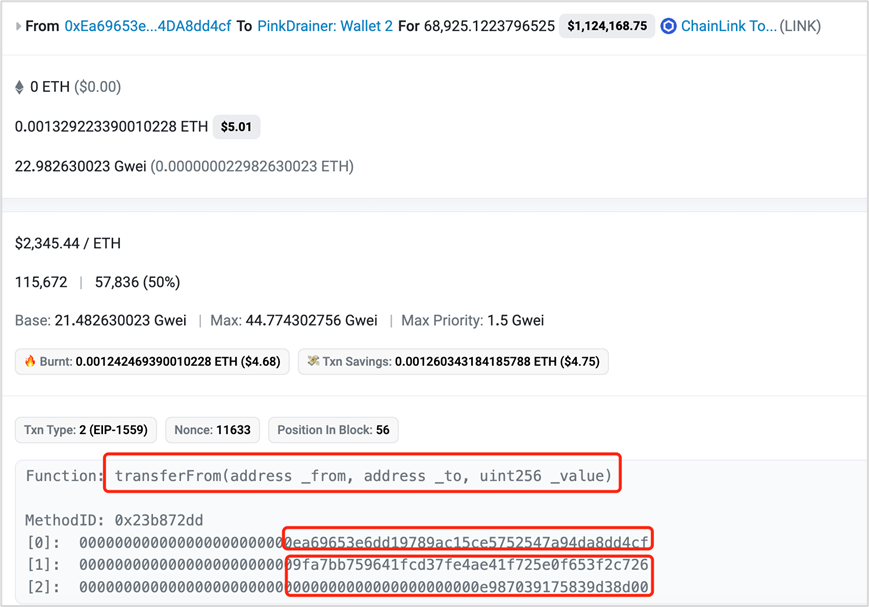
(4) Increase Allowance
Misauthorized Increase Allowance:
https://etherscan.io/tx/0xbb4fe89c03d8321c5bfed612fb76f0756ac7e99c1efaf7c4d99d99f850d4de53
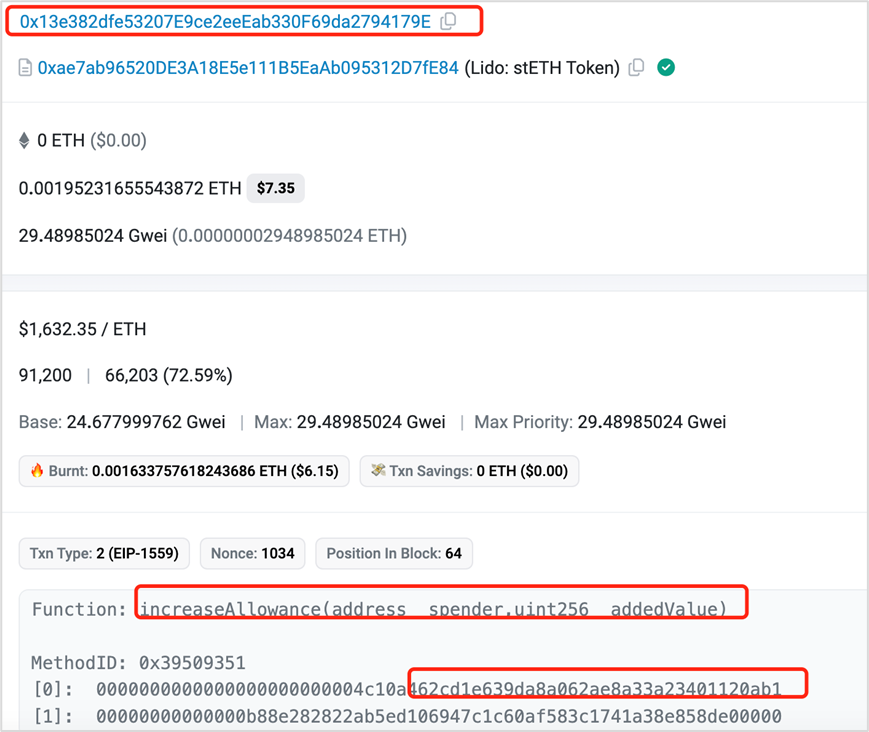
The attacker transferred assets through transferFrom:
https://etherscan.io/tx/0xb91d7b1440745aa07409be36666bc291ecc661e424b21b855698d488949b920f
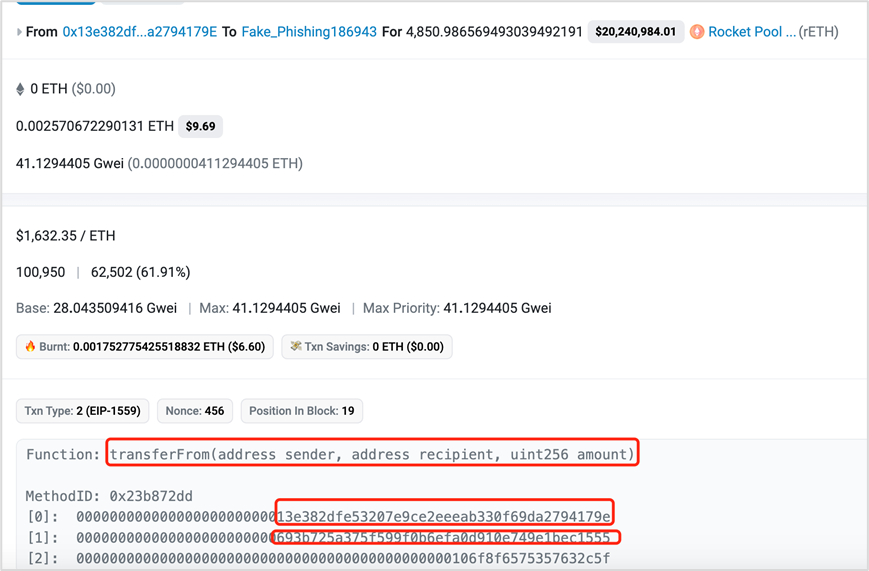
6. Address Pollution Phishing
Address pollution phishing is also one of the rampant phishing methods recently. Attackers monitor on-chain transactions and then create malicious addresses based on the opponent addresses in the target user's transaction history. Typically, the first 4-6 digits and the last 4-6 digits of the malicious addresses are the same as the correct opponent's address. These maliciously created addresses are then used to make small transfers or transfers of worthless tokens to the target user's address.
If the target user, out of personal habit, copies the opponent's address from the transaction history to make a transfer in subsequent transactions, there is a high likelihood of mistakenly transferring assets to the malicious address due to carelessness.
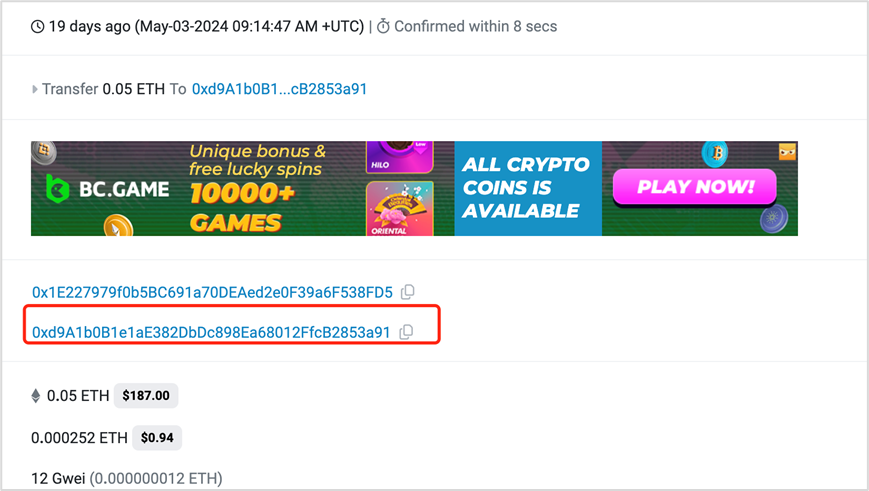
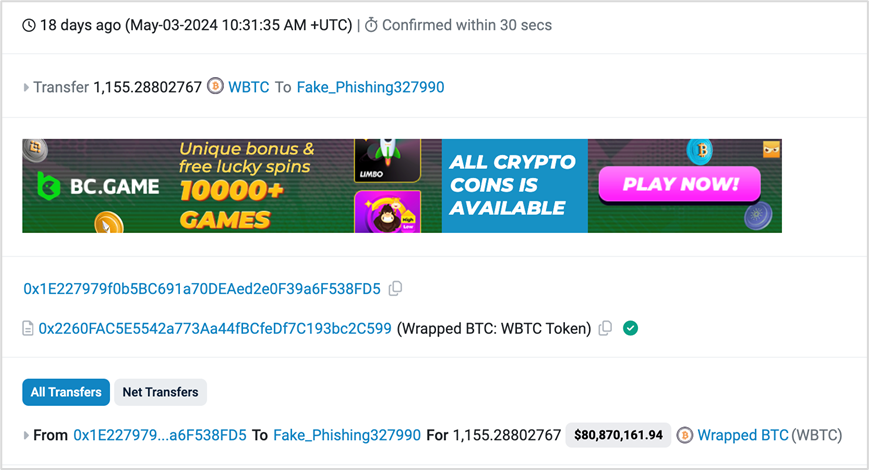
On May 3, 2024, 1155WBTC was phished due to this address pollution phishing method, with a value exceeding 70 million US dollars.
Correct address: 0xd9A1b0B1e1aE382DbDc898Ea68012FfcB2853a91
Malicious address: 0xd9A1C3788D81257612E2581A6ea0aDa244853a91
Normal transaction:
https://etherscan.io/tx/0xb18ab131d251f7429c56a2ae2b1b75ce104fe9e83315a0c71ccf2b20267683ac
Address pollution:
https://etherscan.io/tx/0x87c6e5d56fea35315ba283de8b6422ad390b6b9d8d399d9b93a9051a3e11bf73
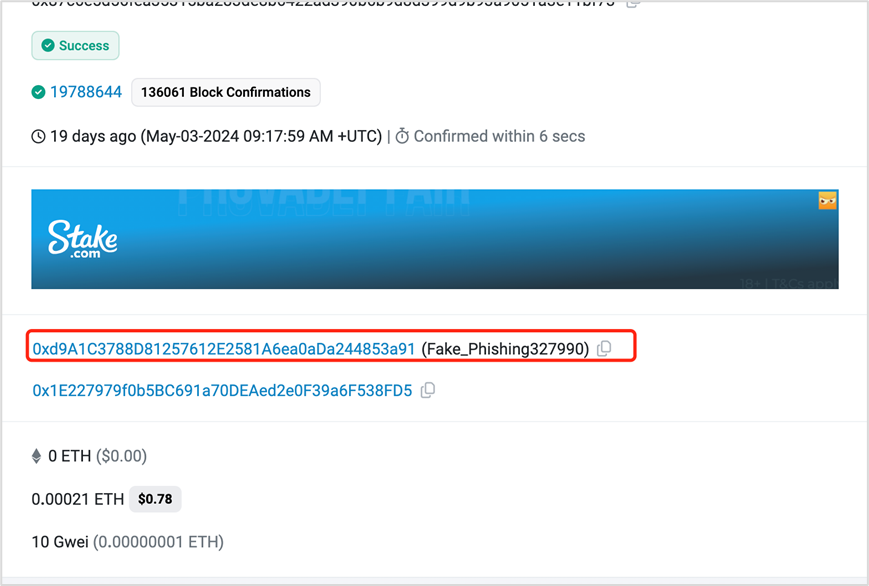
Mistaken transfer:
https://etherscan.io/tx/0x3374abc5a9c766ba709651399b6e6162de97ca986abc23f423a9d893c8f5f570
7. More Concealed Phishing, Using CREATE2 to Bypass Security Checks
Currently, various wallets and security plugins have gradually implemented visual risk warnings for phishing blacklists and common phishing methods, and the display of signature information has become more complete, enhancing the ability of ordinary users to recognize phishing attacks. However, the techniques of attack and defense are constantly evolving, and more concealed phishing methods are also emerging, requiring increased vigilance. Using CREATE2 to bypass wallet and security plugin blacklists is a relatively common method recently.
Create2 is an opcode introduced during the Ethereum 'Constantinople' upgrade, allowing users to create smart contracts on the Ethereum network. The original Create opcode generated a new address based on the creator's address and nonce, while Create2 allows users to calculate the address before deploying the contract. Create2 is a very powerful tool for Ethereum developers, enabling advanced and flexible contract interactions, precalculated contract addresses based on parameters, flexible deployment and adaptation for off-chain transactions, and specific distributed applications.
While Create2 brings benefits, it also introduces new security risks. Create2 can be abused to generate new addresses without a history of malicious transactions, bypassing wallet blacklist checks and security alerts. When the victim signs a malicious transaction, the attacker can deploy a contract at the precalculated address and transfer the victim's assets to that address, which is an irreversible process.
Characteristics of this attack:
(1) Allows predictive creation of contract addresses, enabling attackers to deceive users into granting permissions before deploying the contract.
(2) Since the contract has not been deployed at the time of authorization, the attack address is a new address, and detection tools cannot provide warnings based on historical blacklists, making it more concealed.
Here is an example of phishing using CREATE2:
https://etherscan.io/tx/0x83f6bfde97f2fe60d2a4a1f55f9c4ea476c9d87fa0fcd0c1c3592ad6a539ed14
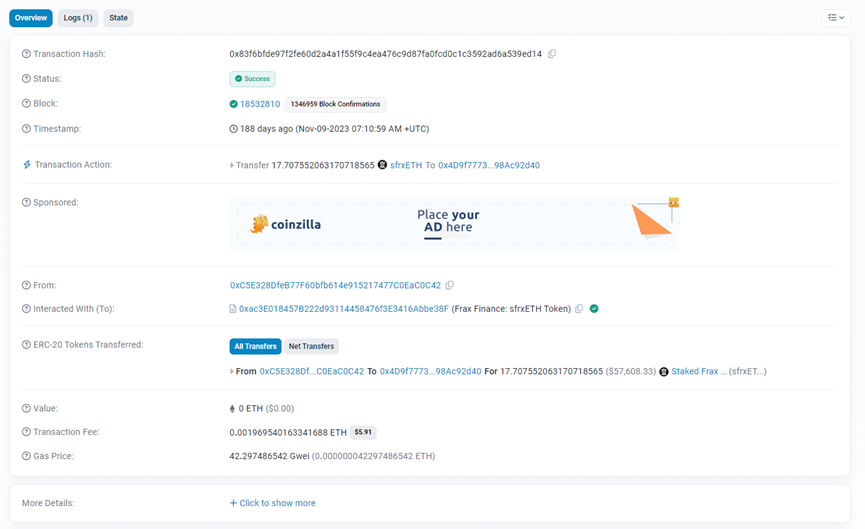
In this transaction, the victim transferred sfrxETH to a malicious address (0x4D9f77), which is a new contract address with no transaction history.
However, examining the creation transaction of this contract reveals that the contract simultaneously carried out a phishing attack, transferring assets from the victim's address.
https://etherscan.io/tx/0x77c79f9c865c64f76dc7f9dff978a0b8081dce72cab7c256ac52a764376f8e52
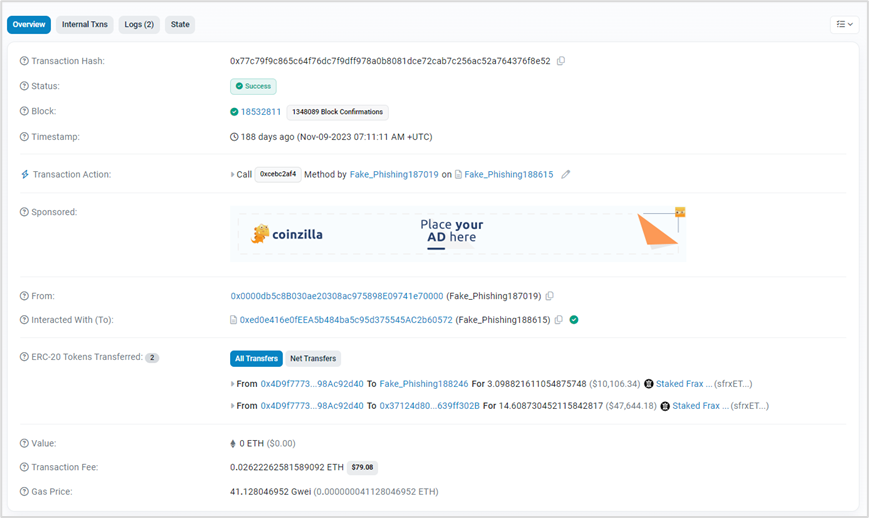
Examining the execution of this transaction, it can be seen that 0x4d9f7773deb9cc44b34066f5e36a5ec98ac92d40 was created after the invocation of CREATE2.
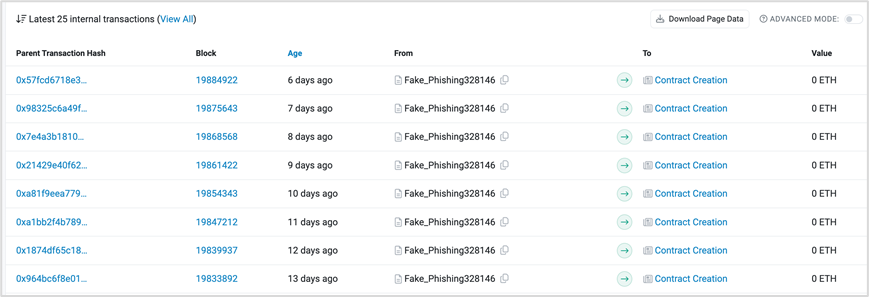
Furthermore, analysis of the relevant addresses of PinkDrainer reveals that this address creates new contract addresses for phishing every day using CREATE2.
https://etherscan.io/address/0x5d775caa7a0a56cd2d56a480b0f92e3900fe9722#internaltx
II. Phishing as a Service
Phishing attacks are increasingly rampant and have become a lucrative illegal industry, gradually developing into a black market chain known as Drainer as a Service (DaaS). Active participants include Inferno/MS/Angel/Monkey/Venom/Pink/Pussy/Medusa, among others. Phishing attackers purchase these DaaS services to quickly and easily build thousands of phishing websites, fraudulent accounts, etc., flooding into this industry and threatening the security of users' assets.
Using Inferno Drainer as an example, this is a notorious phishing group that implements phishing by embedding malicious scripts on different websites. For example, they disguise themselves as popular Web3 protocol functionalities (Seaport, WalletConnect, and Coinbase) by spreading seaport.js, coinbase.js, and wallet-connect.js, enticing users to integrate or click on them. Once the user confirms, their assets are automatically transferred to the attacker's address. Currently, over 14,000 websites containing malicious Seaport scripts, over 5,500 websites containing malicious WalletConnect scripts, over 550 websites containing malicious Coinbase scripts, and over 16,000 malicious domains related to Inferno Drainer have been discovered, affecting over 100 encrypted brand names. Below is an example of a phishing website related to Inferno Drainer.
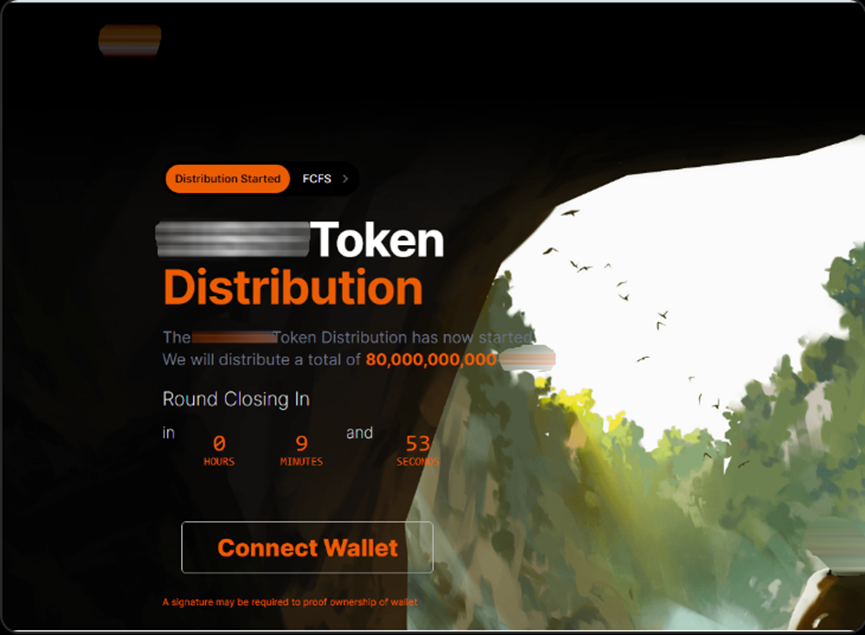
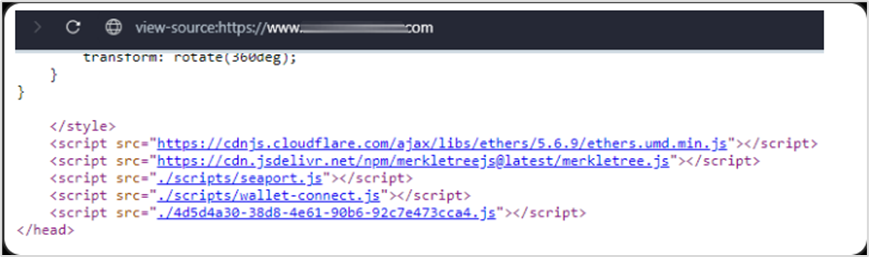
The head section of this website contains two malicious scripts, seaport.js and wallet-connect.js. Another typical feature of Inferno Drainer phishing websites is that users cannot open the website source code by right-clicking, making these phishing websites more concealed.
Under the phishing as a service framework, typically 20% of the stolen assets are automatically transferred to the organizer's address of Inferno Drainer, while the phishing implementer retains the remaining 80%. In addition, Inferno Drainer regularly provides free services for creating and hosting phishing websites. Sometimes, phishing services may also demand a 30% fee from the defrauded funds. These phishing websites are designed for phishing attackers who can attract victims but lack the technical ability to create and host websites or simply do not want to perform this task themselves.
So, how does this DaaS scam work? The following image describes the step-by-step process of Inferno Drainer's crypto scam:
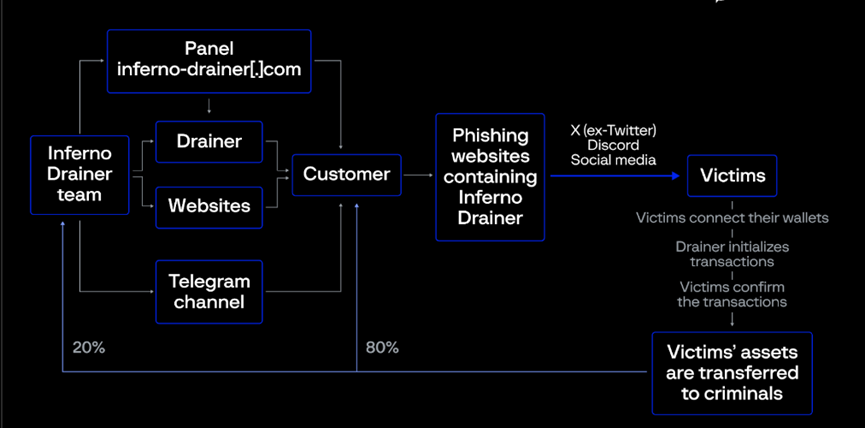
(1) Inferno Drainer promotes their services through a Telegram channel called Inferno Multichain Drainer, and sometimes attackers access this service through Inferno Drainer's website.
(2) Attackers use the DaaS service to set up and generate their own phishing websites and spread them through X (Twitter), Discord, and other social media.
(3) Victims are lured and scan the QR codes or other methods on these phishing websites to connect their wallets.
(4) The Drainer checks the most valuable and easily transferable assets of the victim and initializes malicious transactions.
(5) The victim confirms the transaction.
(6) The assets are transferred to the criminals. In the stolen assets, 20% is transferred to the Inferno Drainer developer, and 80% is transferred to the phishing attacker.
The following image shows the DaaS service page, where Inferno Drainer displays their statistics to customers: number of connections (victims who have connected their wallets to the phishing website), successful clicks (if the victim has confirmed the transaction), and the value of the stolen assets.
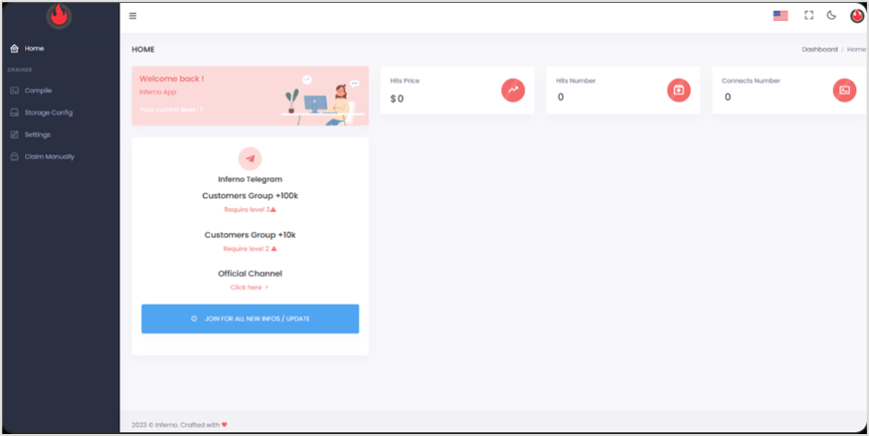
Each customer of the DaaS service can customize their own Drainer functionality:
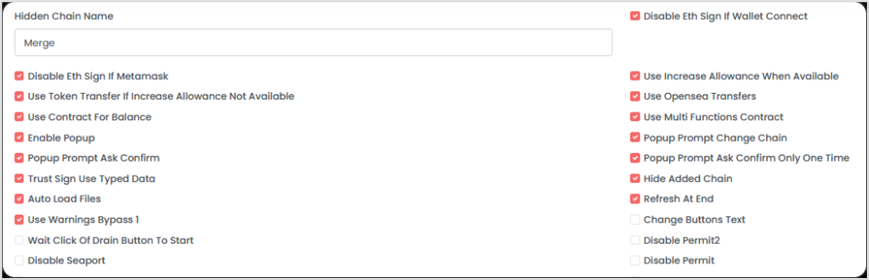
III. Security Recommendations
(1) First and foremost, users must not click on unknown links disguised as rewards, airdrops, or other positive messages.
(2) There are increasingly more incidents of official social media accounts being hacked, and messages posted by official accounts may also be phishing information. Official messages do not guarantee absolute safety.
(3) When using wallets, DApps, and other applications, users must be vigilant and beware of counterfeit websites and apps.
(4) Any transaction or message requiring confirmation or signature should be approached with caution. It is advisable to cross-verify information such as the target and content. Refuse blind signatures, stay vigilant, be suspicious of everything, and ensure that every operation is clear and secure.
(5) Additionally, users need to be aware of common phishing attack methods mentioned in this article and learn to actively identify phishing characteristics. They should understand common signature and authorization functions and their risks, as well as the contents of fields such as Interactive (URL), Owner (authorizing party address), Spender (authorized party address), Value (authorization amount), Nonce (random number), Deadline (expiration time), transfer/transferFrom, etc.
References
https://x.com/evilcos/status/1661224434651529218
https://x.com/RevokeCash/status/1648694185942450177
https://web3caff.com/zh/archives/63069
https://www.group-ib.com/blog/inferno-drainer/
https://blocksec.com/blog/how-phishing-websites-bypass-wallet-security-alerts-strategies-unveiled
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




