Author: Fu Shaoqing, SatoshiLab, Wanwudao BTC Studio
The rise of Bitcoin inscriptions has brought new vitality to the Bitcoin ecosystem, causing more people to start paying attention to Bitcoin again. Some people even say that it has opened Pandora's box for the Bitcoin ecosystem. Among the many technological developments in the Bitcoin ecosystem, the construction of the Bitcoin second layer is of paramount importance. In this regard, I have drawn on some well-known articles on the internet, exchanged ideas with many friends, and summarized a basic knowledge article on the Bitcoin second layer based on our team's exploration in Web3 product design and development. This approach is conducive to summarizing and learning, and due to the limitations of individual cognition, I hope to stimulate more people to improve related ideas and promote better development in this field.
The world of blockchain starts with Bitcoin and ends with the Bitcoin ecosystem (a summary by Shuidi Capital's Dashan, which I personally agree with). Ethereum is also an exploration of Bitcoin's side-chain technology.
In this article, we will use the terms "second layer construction" or "second layer network construction". Usually, the term "second layer network construction" is relatively narrow, while "second layer construction" is a broader concept. However, in order to adapt to the commonly discussed first-layer network, second-layer network, and other commonly used explanations in the industry, we will also use the concept of "second layer network construction". In this article, these two terms represent the same concept.
1. Common missions to be accomplished by Layer 2
In order to understand what basic problems need to be solved in the construction of the Bitcoin second layer, we need to start by understanding the basic characteristics of blockchain systems.
1.1 Basic characteristics and basic requirements of blockchain
In this article, we use a concept proposed by Vitalik: "Blockchain is a 'world computer'". Understanding the various characteristics of blockchain from this perspective will provide a clearer understanding. In the following chapters, we will also analyze the potential development of this "world computer" based on the Von Neumann architecture in computing.
First, let's summarize some basic characteristics:
Note:
The requirements generated to maintain the normal operation of this "world computer" are referred to as internal requirements;
The requirements to meet the needs of users using this "world computer" are referred to as external requirements.
Public transparency: This is a characteristic of the data storage and instruction execution of this "world computer", and it is also a characteristic that requires the participation of distributed nodes globally for internal cooperation. This characteristic precisely meets the users' right to information about the data, which is the common result of the internal cooperation requirements of this "world computer" and the external requirements of users. The privacy feature mentioned later meets the external requirements of users while not undermining the internal cooperation requirements of this "world computer".
Decentralization: This characteristic is the architectural feature of this "world computer", and the degree of decentralization and fault tolerance are theoretically supported by the Byzantine Generals' Problem (i.e., situations where collaborators may be dishonest, i.e., not following the protocol). Non-Byzantine fault-tolerant systems are not blockchain systems in theory, and we will see two cases of non-blockchain systems in the construction of the second layer later. The degree of decentralization is an important indicator of blockchain security and the basis of certain characteristics.
Security: Security is composed of the internal requirements generated by the architectural characteristics of this "world computer" and the external requirements of users. At the micro level, security is ensured by cryptographic technologies, and at the macro level, it is ensured by the decentralized architecture, thereby ensuring the security of this "world computer" against the forgery of micro-level data or the destruction of macro-level architecture.
Computing power: One of the main functions of this "world computer" is computing power. To measure this indicator, we generally examine whether it is Turing complete. Some chains intentionally design themselves to be Turing incomplete in order to maintain their main characteristics. For example, in the Bitcoin network, Satoshi Nakamoto not only made its code instructions Turing incomplete, but also intentionally deleted some instruction sets during development to maintain its stability and security. All Turing complete technologies are designed to expand the computing power of the blockchain. From the perspective of layered design, simple systems are more suitable for the bottom layer.
Performance: Under the same computing power, performance is another major capability of this "world computer". It is generally measured by TPS, i.e., the number of transactions processed per second.
Storage: If blockchain is described as a "world computer", then it must have a storage function, which is the ability to record data. Currently, most storage is within the block, and more professional on-chain storage outside the block is still under development.
Privacy: Privacy is a specific requirement within this "world computer", which requires maintaining the permission scope of data producers and users during computation and storage (we also include resistance to censorship in the privacy section). This is mainly driven by the external requirements of users.
There is also a comprehensive indicator, scalability, which generally refers to the scalability of the entire architecture. This characteristic affects most of the basic characteristics, and at the architectural level, the scalability of the system is a very important indicator. There are also some other capabilities such as connectivity or specific scenario capabilities, which will not be discussed in detail here, and will be analyzed in detail when encountering these special scenarios.
Among these basic characteristics of blockchain, most are constrained by the impossible triangle in their mutual development. For example, the DSS conjecture, which refers to decentralization (D), security (S), and scalability (S). As shown in the figure below:

In distributed systems, a similar impossible triangle is the CAP theorem, where CAP refers to the impossibility of achieving Consistency, Availability, and Partition tolerance in a distributed system. Blockchain systems have Byzantine Generals' Problem, so the CAP theorem also applies to them.
The CAP theorem is shown in the figure below:
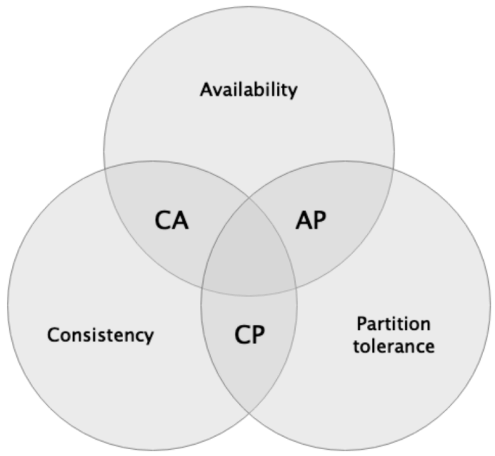
1.2 The role of second layer construction
What roles need to be fulfilled by second layer construction? What functions does it need to provide? Second layer construction must expand the deficiencies of the first layer system and accomplish tasks that are not suitable for completion on the first layer system.
Based on the basic characteristics of blockchain summarized above, we can draw a preliminary conclusion that it must expand these basic capabilities: public transparency, decentralization, security, computing power, performance (throughput), storage, privacy, etc. In addition to these basic technical capabilities, there is also a very important economic issue that needs to be addressed, which is reducing costs. Generally, the comprehensive cost of executing transactions on the first layer network is relatively high, and the second layer network is needed to reduce these costs.
In summary, the purpose of second layer construction is to increase capacity, reduce costs, and customize features. Regarding customized features, it is currently not very obvious, or often concealed within the first two features, which can be puzzling. We can understand it as follows: the degree to which the characteristics of the first layer network are needed for many applications may vary, and various characteristics can be readjusted for certain applications on the second layer.
In second layer construction, the basic capabilities of blockchain will be traded off, some characteristics will be reduced, and even some characteristics will be discarded in exchange for significant improvements in certain characteristics. For example: in order to improve performance, some second layers will reduce the degree of decentralization and security; some second layers, such as the Lightning Network, will change the system's structure and settlement methods in order to increase throughput. There are also some second layers that, without reducing the basic characteristics, enhance a certain characteristic, such as the processing method of RGB, which significantly increases privacy and resistance to censorship, but also increases the difficulty of technical implementation. In the following case studies, we will see second layer constructions that simultaneously reduce or change several characteristics.
Reducing costs should be a basic requirement for all second layer constructions. (Have I seen a second layer that does not reduce costs? I have not seen one yet.)
1.3 Why do layered designs?
Layered design is a method and methodology for humans to deal with complex systems, by dividing the system into multiple hierarchical structures and defining the relationships and functions between layers to achieve modularity, maintainability, and scalability of the system, thereby improving the design efficiency and reliability of the system.
For a widely used and extensive protocol system, using a layered approach has obvious benefits. This makes it easy to understand, easy to implement division of labor, and easy to improve in modular increments. For example, the seven-layer model design of ISO/OSI in computer networks, but in specific implementations, some layers can be combined, such as the specific network protocol TCP/IP, which is a four-layer protocol. As shown in the figure below:
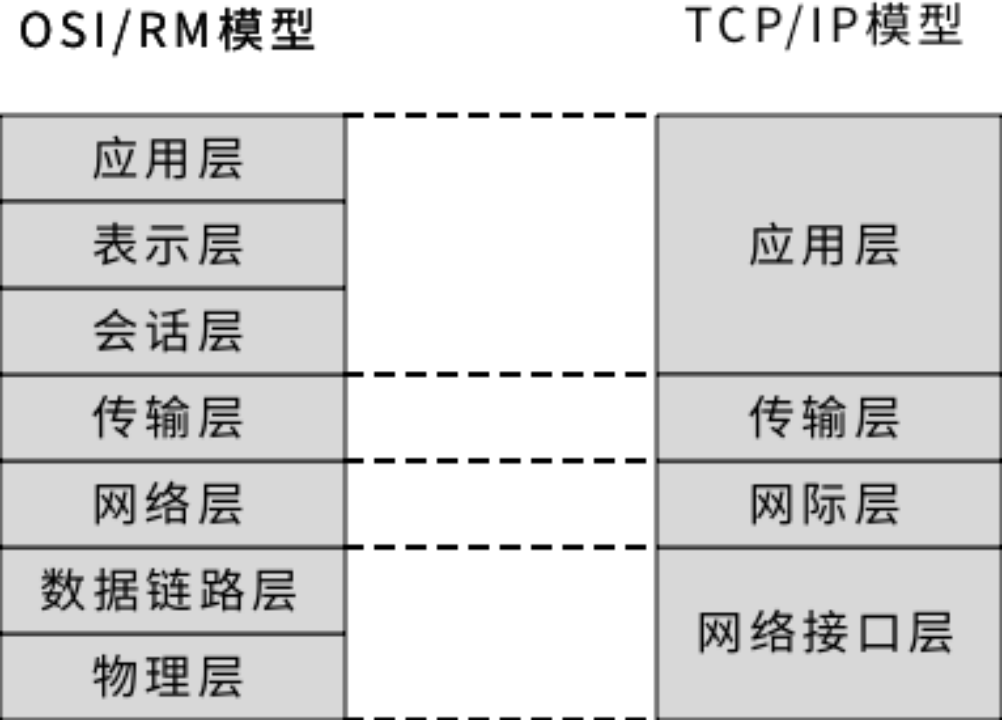
Figure 3-2 ISO seven-layer model and TCP/IP four-layer model
Specific advantages of protocol layering:
Independence between layers: Each layer does not need to know how the next layer is implemented, but only needs to know the services provided through the inter-layer interface. This reduces the complexity of the entire system. In other words, the work of the upper layer does not affect the work of the lower layer, so when designing the work of each layer, as long as the interface remains unchanged, the internal work of the layer can be adjusted as needed.
Flexibility: When any layer changes, as long as the inter-layer interface relationship remains unchanged, it will not affect the layers above or below. When a layer undergoes technological innovation or encounters problems in its work, it will not affect the work of other layers, and when troubleshooting, only the specific layer's problem needs to be considered.
Structurally separable: Each layer can use the most suitable technology for implementation. Technological development is often asymmetrical, and hierarchical division effectively avoids the "weakest link" effect, ensuring that the inefficiency of a certain technology does not affect the overall work efficiency.
Easy to implement and maintain: This structure makes it easier to implement and debug a large and complex system, as the entire system has been broken down into several relatively independent subsystems. During debugging and maintenance, each layer can be debugged separately, avoiding situations where problems cannot be found or the wrong problems are solved.
Promotes standardization work: Because the functions and services of each layer are precisely defined. The benefit of standardization is that a layer can be easily replaced, which is very convenient for use and research.
The modular design concept of layering is a common method in the technical field for handling large-scale projects that require collaboration among multiple people and continuous improvement. It has been proven effective through practice.
2. Bitcoin Layer 2 Construction Approaches
We will use the construction of Bitcoin's second layer as a case study for analysis. There are three significant approaches to the construction of Bitcoin's second layer:
(1) One is the chain-based expansion approach, similar to the EVM, and is a blockchain structure.
(2) Another is the distributed approach, represented by the Lightning Network, which is a distributed structure.
(3) There is also a centralized system-based approach, represented by centralized indexing, which is a centralized structure.
The first two approaches have distinct characteristics, and there are already products in use and under exploration. For the first approach, due to the vigorous development of Ethereum and the exploration of other Bitcoin imitating chains, chain-based second-layer expansion is relatively easier and has more reference cases. The second approach, based on a distributed system, is generally more challenging and develops more slowly, as represented by the Lightning Network. The third approach is controversial because it does not seem like a second-layer construction, but it appears to fulfill the functions of second-layer construction.
Which second-layer construction approach is better? We can use market validation as a measure. The approach with the highest Total Value Locked (TVL) in the second-layer network will be the optimal approach. As time and technology develop, the optimal approach will change.
For the definition of Bitcoin's second-layer network, as long as it is based on the Bitcoin network and has technical relevance to the Bitcoin network, and some features are superior to those of the first-layer Bitcoin network, it can be considered as Bitcoin's second-layer network construction. In the words of Dashan: as long as it consumes BTC as gas, uses BTC as the underlying asset, and expands the performance of Bitcoin, it is considered second-layer construction. Based on this judgment, we should recognize the third type of second-layer network construction, which is the centralized structure of second-layer construction.
The development of Bitcoin's technology itself, such as the modification of OP_RETURN, Taproot, Schnorr signatures, MAST, and Tapscript, should be designed for the purpose of connecting the first layer and the second layer, and should not be used to excessively develop functionality. No matter how the first-layer network expands, there will be no qualitative breakthrough, and second-layer construction must be carried out. However, in the absence of better Bitcoin second-layer products, the technical capabilities for connecting the first layer and the second layer will be excessively used for a period of time.
2.1 Chain-based Second Layer Construction
Early Bitcoin imitating chains made various explorations, such as "Colorcoin," "CovertCoins," and "MasterCoin"; various Bitcoin imitating chains for expansion, such as BCH (Bitcoin Cash), BSV (Bitcoin SV), BTG (Bitcoin Gold); and various sidechain technologies are all examples of chain-based expansion construction, which can be considered a broad definition of the second layer.
This includes Ethereum, which is also an improvement exploration based on Bitcoin. When Vitalik failed to convince other project teams and faced the imperfections of Bitcoin: the accountless system of UTXO, the non-Turing complete execution language, poor scalability, etc., he formed his own team, published a white paper, and developed a new generation of blockchain systems. Although Ethereum's exploration is not directly second-layer construction on Bitcoin, it is a form of chain-based construction exploration in a broad sense.
Ethereum's improvement exploration of Bitcoin's imperfections, as well as the development and validation of second-layer solutions on Ethereum, provided reference cases for the development of chain-based second-layer networks on Bitcoin. Various rollup solutions, cross-chain solutions, message channel technologies, and Ethereum's own sharding technology (from the perspective of layered thinking for handling complex systems, perhaps the approach of solving multiple problems at one layer is wrong), have made the Ethereum ecosystem vibrant, leading many to believe that the development direction and future of public chains have been determined, and the ecosystem represented by Ethereum has already won. In fact, this is also a relatively mature performance of chain-based second-layer construction. However, chain-based second-layer construction is just one approach to second-layer construction, and it has its own advantages and disadvantages, and other second-layer technologies are needed to complete the entire second-layer ecosystem.
Chain-based second-layer construction in Bitcoin generally includes two typical chain types: one is a compatible EVM account model, and the other is a UTXO model similar to Bitcoin. Existing cases (using a broad definition of the second layer) include: EVM account model examples such as Ethereum, Polygon, BSC, Arbitrum, and UTXO model examples such as CKB (Nervos), Chia.
In the following chapters, detailed introductions of certain cases from existing operational Bitcoin second-layer projects will be provided.
In addition, successful second-layer projects on Ethereum will also be integrated into chain-based Bitcoin second-layer construction. For these Ethereum-based second-layer projects, the effort and challenges of transforming them into second-layer projects on Bitcoin will be somewhat reduced. With the maturity and modular development and theoretical achievements of rollups on Ethereum, this approach to second-layer construction will become the mainstream of scalability discussions and the most effective solution.
The success of this transformation remains to be seen. Preliminary judgments can be made about the advantages and disadvantages of this chain-based second-layer construction approach.
Advantages and disadvantages of chain-based second-layer construction:
The disadvantage of this approach is that chain-based second layers are generally limited by the constraints of the blockchain, with limited performance improvements. It either makes the system more centralized or reduces block generation intervals and increases block capacity, generally leading to reduced security. This has led to second-layer construction on top of the second layer, also known as Layer 3 or Layer 4.
The advantage is that this approach maintains most of the basic characteristics of the blockchain and generally solves the problem of Turing completeness. Transaction costs are significantly reduced, and it expands the capabilities of the first-layer network to a certain extent. This approach has a rich history of construction cases, relatively easy technical implementation, and many exploration cases. The migration of upper-layer applications is also very convenient, making it a faster implementation method. It is believed that this approach will generate a considerable number of second-layer networks.
In general, due to the limitations of this approach to expansion, there may be numerous projects based on chain structures in each vertical field, each of which may have one or more second layers to meet the needs of certain applications. Its value will also be determined by the number and total value of applications on the upper layer.
2.2 Second Layer Construction Based on Distributed Systems
In second-layer construction, there are also some based on distributed systems. In this approach, the structure and framework of the second layer are no longer a blockchain structure, but a distributed system based on channels. The Lightning Network is a typical representative.
A distributed system consists of a finite set of processes and a finite set of channels. In a distributed system, controlling data, events, and channels to transmit messages is a complex problem. Here, the term "channel" refers to the concept of channels at the upper layer, such as payment channels in the Lightning Network and message channels in Nostr, rather than the underlying concept of specific technical channels in a distributed network.
In the construction of the second layer in a distributed system, it can be divided into two categories:
(1) Only for value transfer, similar to the Lightning Network.
(2) Both for value transfer and Turing-complete technology, such as RGB.
In distributed-based second-layer construction, due to the value transfer, there are many challenges beyond traditional message passing, such as the total value capacity within channels, transaction rigor, and prevention of double spending, which surpass the difficulty of message passing. Therefore, the development of distributed-based second-layer construction is not as fast as that of chain-based second-layer construction, and there are not many mature cases.
If Turing-complete computation is to be completed on such a second layer, i.e., establishing a Turing-complete virtual machine system on a channel, it will be even more challenging. For example, the RGB protocol achieves Turing-complete computation in a distributed system through client verification and one-time sealing.
Existing cases of distributed-based second-layer construction in Bitcoin include the Lightning Network, RGB, and possibly other well-known cases. If we consider the broad definition of second-layer construction, does Nostr also belong to the distributed system's second-layer construction based on the channel mechanism? While organizing Ethereum materials, I saw examples of channel usage in Ethereum documentation, such as Connext, Raiden, and Perun, which could be exploration directions for in-depth researchers.
In the following chapters, detailed introductions of the Lightning Network and RGB will be provided from existing operational Bitcoin second-layer projects.
Advantages and Disadvantages of Distributed-based Distributed System Construction:
The advantage of this approach is that the system is more decentralized, can accommodate countless nodes in the second layer, and has better privacy and resistance to censorship. It also has unlimited scalability, making performance theoretically greatly improved.
The disadvantage is that the technical implementation is complex, and the routing algorithms and value splitting and encapsulation algorithms in a large distributed system are quite complex. In terms of value transfer, there is still a lack of engineering experience and infrastructure compared to information transfer. This is also one of the reasons why the development of the Lightning Network has been considered slow.
Additionally, implementing a Turing-complete system in such a system is a significant challenge, i.e., Channel + computation. While it can theoretically be achieved, it is still in the early experimental stage in practice. RGB is a typical representative of this situation.
Once breakthroughs are made in the construction of distributed-based second layers, it will greatly drive the development of upper-layer applications. The decentralized capability formed by the large distributed nodes and the ability to execute Turing-complete code will better support the next generation of Internet applications, which is what everyone refers to as the "Mass Adoption" scenario.
In general, distributed-based second-layer construction is expected to have only a few parallel projects, for two main reasons: the unlimited scalability of such systems and the technical difficulty of implementation. Therefore, such systems require a more open design and concept to accommodate more people and teams. Furthermore, application development teams based on this second-layer infrastructure will also drive the development of this second layer, such as the BiHelix project based on RGB.
2.3 Second Layer Construction Based on Centralized Systems
Should this classification be included? It may be controversial.
Centralized indexing structures like Ordinals, or indexers for certain functional nodes, are also a form of second-layer construction. However, this approach is less recognized because the second layer is overly centralized and has very limited expansion of the first-layer network. In this centralized structure of second-layer construction, all the basic blockchain features depend on the first-layer network, and the second layer only serves as a simple computing and statistical function. Sometimes, the second layer seems to be a temporary existence that can be replaced at any time, and its importance does not seem to be as high. However, from the perspective of On-Chain and Off-Chain, and from the perspective of enhancing the capabilities of the first-layer network, this centralized structure is also a form of second-layer expansion.
Cases of this system include Ordinals and possibly other centralized exchanges. Projects of this nature will not be covered in the upcoming case studies.
Advantages and Disadvantages of Second Layer Construction Based on Centralized Systems:
The advantage is that centralized systems are very mature, with countless available cases and optimization solutions, and they offer complete Turing completeness and excellent performance.
The disadvantage is that the second layer is extremely centralized, and all blockchain features depend on the first-layer network.
In general, there are expected to be relatively few projects based on centralized structures for the second layer, and they may even be temporary. After the maturity and perfection of chain-based and channel-based distributed structures, most second-layer constructions based on centralized structures will either disappear or only leave behind a few centralized second layers for specific scenarios. At the current stage, because centralized systems are very mature and can write data onto the underlying chain, they can easily meet the scenarios of On-Chain data and Off-Chain computation, and are widely used in the early applications of the Bitcoin ecosystem.
2.4 A Broader Concept of Second Layer and Higher-Level Applications
Analyzing the structure of second-layer construction from the above, there are blockchain-based structures, distributed system structures, and centralized system structures. This is a common classification of system structures: Centralized, Decentralized, Distributed. From this perspective, it is easier to understand the characteristics and applicable scenarios of each type. Each type of second layer has its own advantages and disadvantages, and in the complete Bitcoin ecosystem in the future, all three types should have their own distribution according to different scenarios.
Additionally, the blockchain community often discusses Layer 3 and even Layer 4 on top of second-layer construction, which is a broad concept of the second layer. This is completely different from the concept of Layer 3 and Layer 4 in Gavin Wood's Web3 technology stack, which is a classification of application protocols.
These second-layer constructions will have what kind of impact on upper-layer applications? With the basic features provided by the blockchain system: transparency, decentralization, security, computing power, throughput, storage, and privacy, upper-layer applications will be built on the extensions of these second layers and will interact on these second layers. The extensions based on blockchain-based structures, distributed system structures, centralized system structures, and some centralized applications will generate truly large-scale Web3.0 applications.
3. Related Matters of Second Layer Construction
With the first layer network and second-layer construction, what is the connection between them? Or how are they directly related? One type of connection is the direct technical connection, such as through bidirectional locking or bridge technology. Another type is the external relevance, such as Bitcoin and Ethereum. Although they are not directly related, people convert BTC into WBTC to circulate on Ethereum, or even adjust the positions of Bitcoin and Ether based on price fluctuations, which is a form of external relevance.
Here, we will only discuss the technical relevance, which is closely related to the structure and characteristics of the second layer. Later, we will make judgments on the development of the entire blockchain-related ecosystem from a more macro perspective, referring to the von Neumann architecture.
3.1 Connection Technologies between the First Layer and Second Layer
2.2 Second Layer Construction Based on Distributed Systems
In second-layer construction, there are also some based on distributed systems. In this approach, the structure and framework of the second layer are no longer a blockchain structure, but a distributed system based on channels. The Lightning Network is a typical representative.
A distributed system consists of a finite set of processes and a finite set of channels. In a distributed system, controlling data, events, and channels to transmit messages is a complex problem. Here, the term "channel" refers to the concept of channels at the upper layer, such as payment channels in the Lightning Network and message channels in Nostr, rather than the underlying concept of specific technical channels in a distributed network.
In the construction of the second layer in a distributed system, it can be divided into two categories:
(1) Only for value transfer, similar to the Lightning Network.
(2) Both for value transfer and Turing-complete technology, such as RGB.
In distributed-based second-layer construction, due to the value transfer, there are many challenges beyond traditional message passing, such as the total value capacity within channels, transaction rigor, and prevention of double spending, which surpass the difficulty of message passing. Therefore, the development of distributed-based second-layer construction is not as fast as that of chain-based second-layer construction, and there are not many mature cases.
If Turing-complete computation is to be completed on such a second layer, i.e., establishing a Turing-complete virtual machine system on a channel, it will be even more challenging. For example, the RGB protocol achieves Turing-complete computation in a distributed system through client verification and one-time sealing.
Existing cases of distributed-based second-layer construction in Bitcoin include the Lightning Network, RGB, and possibly other well-known cases. If we consider the broad definition of second-layer construction, does Nostr also belong to the distributed system's second-layer construction based on the channel mechanism? While organizing Ethereum materials, I saw examples of channel usage in Ethereum documentation, such as Connext, Raiden, and Perun, which could be exploration directions for in-depth researchers.
In the following chapters, detailed introductions of the Lightning Network and RGB will be provided from existing operational Bitcoin second-layer projects.
Advantages and Disadvantages of Distributed-based Distributed System Construction:
The advantage of this approach is that the system is more decentralized, can accommodate countless nodes in the second layer, and has better privacy and resistance to censorship. It also has unlimited scalability, making performance theoretically greatly improved.
The disadvantage is that the technical implementation is complex, and the routing algorithms and value splitting and encapsulation algorithms in a large distributed system are quite complex. In terms of value transfer, there is still a lack of engineering experience and infrastructure compared to information transfer. This is also one of the reasons why the development of the Lightning Network has been considered slow.
Additionally, implementing a Turing-complete system in such a system is a significant challenge, i.e., Channel + computation. While it can theoretically be achieved, it is still in the early experimental stage in practice. RGB is a typical representative of this situation.
Once breakthroughs are made in the construction of distributed-based second layers, it will greatly drive the development of upper-layer applications. The decentralized capability formed by the large distributed nodes and the ability to execute Turing-complete code will better support the next generation of Internet applications, which is what everyone refers to as the "Mass Adoption" scenario.
In general, distributed-based second-layer construction is expected to have only a few parallel projects, for two main reasons: the unlimited scalability of such systems and the technical difficulty of implementation. Therefore, such systems require a more open design and concept to accommodate more people and teams. Furthermore, application development teams based on this second-layer infrastructure will also drive the development of this second layer, such as the BiHelix project based on RGB.
2.3 Second Layer Construction Based on Centralized Systems
Should this classification be included? It may be controversial.
Centralized indexing structures like Ordinals, or indexers for certain functional nodes, are also a form of second-layer construction. However, this approach is less recognized because the second layer is overly centralized and has very limited expansion of the first-layer network. In this centralized structure of second-layer construction, all the basic blockchain features depend on the first-layer network, and the second layer only serves as a simple computing and statistical function. Sometimes, the second layer seems to be a temporary existence that can be replaced at any time, and its importance does not seem to be as high. However, from the perspective of On-Chain and Off-Chain, and from the perspective of enhancing the capabilities of the first-layer network, this centralized structure is also a form of second-layer expansion.
Cases of this system include Ordinals and possibly other centralized exchanges. Projects of this nature will not be covered in the upcoming case studies.
Advantages and Disadvantages of Second Layer Construction Based on Centralized Systems:
The advantage is that centralized systems are very mature, with countless available cases and optimization solutions, and they offer complete Turing completeness and excellent performance.
The disadvantage is that the second layer is extremely centralized, and all blockchain features depend on the first-layer network.
In general, there are expected to be relatively few projects based on centralized structures for the second layer, and they may even be temporary. After the maturity and perfection of chain-based and channel-based distributed structures, most second-layer constructions based on centralized structures will either disappear or only leave behind a few centralized second layers for specific scenarios. At the current stage, because centralized systems are very mature and can write data onto the underlying chain, they can easily meet the scenarios of On-Chain data and Off-Chain computation, and are widely used in the early applications of the Bitcoin ecosystem.
2.4 A Broader Concept of Second Layer and Higher-Level Applications
Analyzing the structure of second-layer construction from the above, there are blockchain-based structures, distributed system structures, and centralized system structures. This is a common classification of system structures: Centralized, Decentralized, Distributed. From this perspective, it is easier to understand the characteristics and applicable scenarios of each type. Each type of second layer has its own advantages and disadvantages, and in the complete Bitcoin ecosystem in the future, all three types should have their own distribution according to different scenarios.
Additionally, the blockchain community often discusses Layer 3 and even Layer 4 on top of second-layer construction, which is a broad concept of the second layer. This is completely different from the concept of Layer 3 and Layer 4 in Gavin Wood's Web3 technology stack, which is a classification of application protocols.
These second-layer constructions will have what kind of impact on upper-layer applications? With the basic features provided by the blockchain system: transparency, decentralization, security, computing power, throughput, storage, and privacy, upper-layer applications will be built on the extensions of these second layers and will interact on these second layers. The extensions based on blockchain-based structures, distributed system structures, centralized system structures, and some centralized applications will generate truly large-scale Web3.0 applications.
3. Related Matters of Second Layer Construction
With the first layer network and second-layer construction, what is the connection between them? Or how are they directly related? One type of connection is the direct technical connection, such as through bidirectional locking or bridge technology. Another type is the external relevance, such as Bitcoin and Ethereum. Although they are not directly related, people convert BTC into WBTC to circulate on Ethereum, or even adjust the positions of Bitcoin and Ether based on price fluctuations, which is a form of external relevance.
Here, we will only discuss the technical relevance, which is closely related to the structure and characteristics of the second layer. Later, we will make judgments on the development of the entire blockchain-related ecosystem from a more macro perspective, referring to the von Neumann architecture.
3.1 Connection Technologies between the First Layer and Second Layer
```
2. Liquid (Chain-based Second-layer Construction)
Liquid, launched by Blockstream in 2015, is a sidechain solution for Bitcoin. As the first sidechain of Bitcoin, Liquid aims to provide a faster, more secure, and private transaction solution to meet the needs of professional users such as financial institutions and exchanges.
One of Liquid's main features is its fast transaction confirmation time. Compared to Bitcoin's confirmation time of approximately 10 minutes, Liquid's transaction confirmation time is only 2 minutes. This allows users to conduct transactions more quickly and complete fund transfers rapidly when needed. Another important feature is the transaction privacy of Liquid. Liquid utilizes Confidential Transactions technology, which hides the transaction amount, allowing only the transaction participants to view the specific amount, thus protecting the privacy of the transaction participants.
Liquid also boasts higher transaction throughput. By using Federated Peg technology, Liquid can support a large number of parallel transactions and anchor them on the Bitcoin network, achieving interoperability with Bitcoin. This enables Liquid to handle a higher transaction volume and improve the overall system throughput.
Since its launch, Liquid has gradually gained traction in the cryptocurrency industry. More and more exchanges, financial institutions, and enterprises are adopting Liquid as their transaction and fund settlement solution. Meanwhile, Blockstream continues to introduce new features and improvements to further enhance the performance and security of Liquid.
In summary, Liquid is a Bitcoin sidechain solution introduced by Blockstream to provide fast, private, and high-throughput transactions. It meets the needs of professional users by shortening transaction confirmation times, providing transaction privacy, and increasing transaction throughput. Over time, Liquid has gained widespread adoption and development in the cryptocurrency industry.
3. Rootstock (RSK) (Chain-based Second-layer Construction)
Rootstock (RSK) is a smart contract platform built on the Bitcoin blockchain, aiming to provide Ethereum-like functionality to the Bitcoin ecosystem. Rootstock was first proposed in 2015 and officially launched in 2018.
One of Rootstock's main features is its two-way anchoring with Bitcoin and smart contract functionality. Through its two-way anchoring with Bitcoin, Rootstock can use Bitcoin as its primary asset, ensuring security and stability. Additionally, Rootstock supports smart contract functionality, allowing developers to build and execute smart contracts with automated features on its platform.
Since its introduction, Rootstock has gradually gained recognition and adoption within the Bitcoin ecosystem. It provides Bitcoin users and developers with more functionality and flexibility, enabling Bitcoin to support a wider range of use cases such as decentralized finance (DeFi), digital asset issuance, and supply chain management.
However, compared to other smart contract platforms, Rootstock's development has been relatively slow. It still requires more effort in expanding its user and developer community. Nevertheless, the future development prospects of Rootstock are considered positive, and it has the potential to become one of the important smart contract platforms within the Bitcoin ecosystem.
4. RGB (Distributed + Turing-complete Second-layer Construction)
The story of RGB dates back to 2016 when Giacomo Zucco aimed to develop a better colored coins using Peter Todd's client-side validation and single-use-seals concepts and bring these tokens into the Lightning Network (hence the name "RGB"). It is an open protocol built on the Bitcoin blockchain, designed to provide richer functionality for the creation, trading, and management of digital assets. RGB is a scalable and confidential Bitcoin and Lightning Network smart contract system developed by the LNP/BP Standards Association. It adopts the concepts of private and common ownership and is a Turing-complete, trustless distributed computing form that does not require the introduction of tokens in a non-blockchain decentralized protocol.
The purpose of the RGB protocol is to run scalable, robust, and confidential smart contracts on UTXO blockchains (such as Bitcoin) to achieve all possibilities. Through RGB, developers can execute various types of smart contracts such as token issuance, NFT minting, DeFi, DAO, and more complex multi-category smart contracts.
The RGB protocol is based on the concepts of client-side validation and single-use-seals, enabling client-state validation and smart contract systems to run on the second and third layers (off-chain) of the Bitcoin ecosystem.
5. Stacks (Chain-based Second-layer Construction)
Stacks (formerly Blockstack) is a decentralized computing platform built on top of the Bitcoin blockchain. Stacks was first proposed in 2013 and conducted its initial token offering (ICO) in 2017. Its core features include providing decentralized identity verification, storage, and smart contract functionality.
The core feature of Stacks is to support the development and execution of decentralized applications using Bitcoin's security and stability. It adopts a consensus mechanism called "Stacking," which incentivizes users holding STX tokens to lock a certain amount of tokens and participate in network validation, thereby providing incentives to users and increasing network security.
In terms of development, Stacks has become an important platform in the decentralized application field. It has attracted a group of developers and projects to build numerous decentralized applications and has provided rich tools and development documentation. Stacks also collaborates with other blockchain projects to expand its ecosystem and application scenarios.
6. Other Bitcoin Second-layer Projects
With the popularity of Bitcoin, numerous new projects have emerged. Many of these new projects are initiated by Chinese individuals. These new projects, such as B² Network, BEVM, Dovi, Map Protocol, Merlin, and Bison, also have their own unique features.
B² Network, founded in 2022, is a Bitcoin second-layer network developed based on ZK-Rollup, compatible with EVM, and capable of seamless deployment of DApps in the EVM ecosystem. It is a typical case of transferring Ethereum's second-layer technology to the Bitcoin ecosystem.
The original team of BEVM was established in 2017 and explored various Bitcoin expansion applications. The concept of BEVM, proposed in 2023, is a decentralized Bitcoin L2 compatible with EVM. Leveraging the Schnorr signature algorithm and other technologies brought by the Taproot upgrade, BEVM allows BTC to cross-chain to the second layer in a decentralized manner. As BEVM is compatible with EVM, all DApps running in the Ethereum ecosystem can operate on BTC Layer 2 and use BTC as Gas. BEVM released its whitepaper on November 29, 2023.
Dovi, founded in 2023, is a Bitcoin Layer 2 compatible with EVM smart contracts. In November 2023, Dovi officially released its whitepaper. The whitepaper introduces Dovi's integration of Schnorr signatures and MAST structure to enhance transaction privacy, optimize data size, and verification processes, and implement flexible frameworks for issuing various asset types outside of Bitcoin.
The team behind Map Protocol was established relatively early and initially focused on cross-chain protocols, which are the connection technologies between the first layer and second layer as mentioned earlier. With the booming Bitcoin ecosystem, they quickly built chain-based second-layer construction. It can facilitate cross-chain transfer of current ciphertext assets and reduce transaction fees, attracting some projects and applications.
Merlin Chain, from its official website, is easily seen to have the attribute of its Bridge, which transfers assets from BTC to the second layer network, reducing transaction fees, and is a typical representative of solving pain points. According to the official website and some research reports, Merlin is a Bitcoin Layer 2 solution that integrates ZK-Rollup network, decentralized oracles, and on-chain BTC anti-fraud modules. The project is launched by Bitmap Tech, a distinctive team known for Bitmap.game and BRC-420 "Blue Box" Ordinals assets.
Bison, founded in 2023, is a Bitcoin-native zk-rollup that improves transaction speed and implements advanced features on native Bitcoin. Developers can use zk-rollup to create innovative DeFi solutions, such as trading platforms, lending services, and automated market makers. From its official website, Bridge is also an important feature. Cross-chain transfer of Bitcoin assets to complete upper-layer asset applications is the entry point for many projects.
Looking at the relatively new projects such as B² Network, BEVM, Dovi, Map Protocol, Merlin, and Bison, they have quickly reduced transaction fees to meet the trading needs of Bitcoin's first-layer assets. They all involve cross-chain assets. Teams with existing cross-chain protocols can move faster, while teams with experience in second-layer construction have an advantage in upper-layer applications. These newer projects are all based on chain-based second-layer construction, leveraging existing technological accumulation and short-term explosive advantages. These projects, while somewhat homogeneous, will require further observation to see how they develop in the future. How will they compete with service providers based on distributed second-layer construction? These are questions that require careful observation. Based on the experience of second-layer projects on Ethereum, many projects tend to plateau after token issuance. Will Bitcoin's second layer follow the same pattern?
From the currently running projects on Bitcoin's second layer, we can see that well-known Bitcoin second-layer projects were established relatively early and have explored related technologies for a long time. However, due to the lack of a mature Bitcoin ecosystem, most projects are not very exciting, or they are overshadowed by the Ethereum ecosystem. With the maturation of Bitcoin's underlying protocol, especially with the formation of foundational technologies such as Segregated Witness, Taproot, Schnorr signatures, MAST (Merkle Abstract Syntax Tree), Tapscript, the development of connection technologies between the first and second layers has improved. As a result, the Bitcoin ecosystem is becoming more diverse and rich. From the existing Bitcoin second-layer projects, we can see that some are original builders of the Bitcoin ecosystem, some are builders of the Ethereum second layer, and some are builders of connection technologies. Regardless of the direction of the project, they all need to use these newly emerging Bitcoin basic connection technologies. The more comprehensive and diverse the usage, the better the support for the second layer.
4.2 Analysis of the Development of Bitcoin Second-layer Construction
Where there is capital, there is attention, and it will attract more capital. Bitcoin currently has a market value of approximately $800 billion, and its ecosystem is relatively weak but has explosive potential. Therefore, many projects claim to be involved in Bitcoin's second-layer construction. Here, we will not mention the specific names of these projects, but we will classify the entrants to these projects and examine their characteristics and respective advantages and disadvantages.
1. Original Bitcoin Second-layer Construction Projects
Original Bitcoin second-layer projects, especially those that have been developed for many years and have accumulated certain advantages, can leverage the current popularity of Bitcoin to rejuvenate themselves. Will they thrive? There is a lot of uncertainty.
There are two criteria for measurement: first, the second-layer network with the highest total value locked (TVL) will prevail in Bitcoin's second layer. The other criterion is the structural type of the second layer. Chain-based second-layer construction, due to its scalability, can accommodate more competitors, while distributed-based second-layer construction can only accommodate fewer competitors.
Original second-layer projects need to fully leverage their accumulated advantages and use new technologies to establish new advantages to attract more applications to their platform in order to rejuvenate themselves and gain more market share. If they cannot attract more applications, these older projects are likely to sink or transform. In fact, these projects can still collaborate or merge with projects that have no technical or community accumulation but have established community consensus through some form of cooperation, in exchange for greater development opportunities.
Furthermore, if these older projects have an advantage in the accumulation of distributed second-layer construction technology, they can fully engage in distributed second-layer construction and be more effective by providing guidance for upper-layer applications.
2. New Entrants to Bitcoin Second-layer Construction Projects
New entrants to Bitcoin second-layer construction projects generally do not have many accumulated advantages, but this gives them a latecomer advantage. They can research the latest technologies, address lightweight and attractive demands, and attract a certain number of applications. Teams with experience in second-layer construction in the Ethereum ecosystem or other ecosystems are more suitable for quickly entering Bitcoin's second-layer construction. These projects may consider chain-based second-layer construction, which will be faster and more advantageous.
Teams with no experience or advantages can consider the third scenario, whether they can use community consensus to select users and accumulate funds.
3. Bitcoin Second-layer Projects without Accumulation but Wanting to Enter
I used to have little understanding of projects that have no technical or community accumulation but claim to enter Web3.0. I mostly considered these projects as CX projects. However, through the phenomenon of ciphertext, communities that have generated significant community consensus, such as sats, ordi, rats, have not only accumulated many members but also raised a certain amount of funds. These projects can completely start a new second-layer construction from scratch, integrate upper-layer applications into the community through the power of the community, and possibly develop the second layer. Such a second layer will most likely be based on chain-based construction, as it is simple and fast. Through the power of the community, they can build DID (decentralized identity), DAO tools, DeFi applications, and other upper-layer applications in the community's second layer, without needing to build them themselves, but by introducing mature products and sharing revenue with them. This could potentially form a small ecosystem. Such projects place higher demands on community building, foundation management, and decision-making mechanisms.
4. Development of Upper-layer Applications
With the rapid development of Bitcoin's second layer, the vast amount of dormant funds on BTC is being reawakened, and due to the attention it attracts, it will bring in more new users to the Web3.0 field. Coupled with the rapid development of Bitcoin's second-layer technology, it will lay a solid foundation for mass adoption. The development of the second layer of Bitcoin will bring many opportunities and solid infrastructure to upper-layer applications. Once mature, it will bring more opportunities to Web3 teams that are not so native.
In any case, the Web3.0 era is just beginning and is still in its infancy and early stages. It requires a lot of exploration and construction, and many countries and regions have not fully opened up to many new things in Web3.0. Web3.0 requires a lot of construction and will provide more opportunities for various project teams. Teams that continuously perceive new developments and technologies, make adjustments, and actively participate in building Web3.0 will definitely reap rewards in a certain stage and field.
References
The writing of this article is based on reading a large number of industry articles and participating in various activities such as TwitterSpace and offline discussions. I have been inspired by the speeches of many people, and some prominent influencers and factors include:
(1) Dashan, a teacher from Waterdrop Capital, who has written many articles and has given several lectures at Wanwu Island. I have also participated in several Space events he was involved in.
(2) Some in-depth technical content is derived from listening to lectures by Hong Shuning and watching his videos, as well as discussions with him, such as routing issues in distributed systems and the Turing completeness of RGB.
(3) Numerous articles from www.btcstudy.org. This website provides a wealth of knowledge.
(4) Interviews with Jan Xie, Chief Architect of Nervos (CKB).
(5) Reading a lot of BIP protocols, Segwit, Taproot, ordinals, BRC20, Atomical, and other content.
(6) Other blockchain knowledge, including the comparison of layered design concepts and von Neumann architecture, comes from the knowledge accumulated while writing several books in the past few years. I have published five books, "Blockchain Knowledge - Popular Edition," "Blockchain Knowledge - Technical Edition," "Turing Blockchain," "Blockchain Economic Model," and "Web3.0: Building the Digital Future of the Metaverse." I have also written three books on Ethereum, some of which have been completed but not yet published. These contents have referenced many native protocols, whitepapers, and technical principles of blockchain. The output of these contents is the result of many people's efforts, and I have only collected and organized them. Over time, I have come to understand the underlying principles and the interrelationships between many technologies and their potential future application scenarios.
(7) Discussions and considerations with team members when designing related products for our project.
I am very grateful to Dashan from SatoshiLab, Elaine Yang, Hong Shuning, and other technical experts. They have provided a lot of feedback and suggestions for revision after reading this article, and they have rigorously checked the accuracy of the quoted concepts in the article, only confirming them as qualified when we could find the original references. I appreciate this rigorous habit!
I am very grateful to all the contributors and participants who have enriched my knowledge system.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




