Anoma is a privacy-centric architecture that introduces a new paradigm for building infrastructure layers and a new operating system for decentralized applications, with the core idea being that users only need to express their desired results (intent) without needing to be concerned about the specific execution process (transactions). Through smart contracts or protocols, Anoma can automatically find the best transaction solution for users and ensure the reliability and privacy of transactions. At the same time, it can facilitate the complete decentralization of existing web2.5 dApps, such as optimistic and ZK rollups, DEX, NFT markets, or public product financing applications like Gitcoin.
Author
JUMPENG, Senior Researcher at Shi Lian. Holds a Master's degree in Finance from Huazhong University of Science and Technology, with 7 years of industry experience. Specializes in areas such as Layer1, DeFi, NFT, Layer2, and Gamefi, having researched over 2000 projects and produced over 500 in-depth research reports.
1. Research Highlights
1.1. Core Investment Logic
Anoma Network is an intent-centric, privacy-protecting protocol for decentralized transaction discovery, negotiation, and multi-chain atomic settlement. The project is innovative, forward-looking, and practical, with the potential to become a new paradigm for Web3 interaction, providing users with a simpler, smarter, and more secure blockchain application experience.
Disruptive technological concept, strong core team: Anoma, with its "intent-oriented" concept, aims to disrupt the traditional design thinking of existing DApps, demonstrating the disruptive thinking and technological innovation capabilities of the core Anoma team. Additionally, Anoma is developed by the Heliax development team, whose core members all come from COSMOS, possessing strong research and development capabilities and extensive industry experience, laying a solid foundation for Anoma's rapid product iteration and long-term technological accumulation. Anoma's disruptive technological concept and strong core team will be an important core investment logic, as it has the potential to change the landscape of existing blockchain applications.
Recognition from top institutions and support from multiple rounds of financing: In the highly competitive Layer 1 field, Anoma Foundation has gained recognition from top institutions such as Polychain and Coinbase for its intent-centric architecture and projects like Anoma and Namada. It has completed seed, Series A, and Series B financing rounds, with a total funding amount of $57.8 million, ranking 7th among unlisted Layer 1/Layer 2 projects. This demonstrates that Anoma's business model and development potential have gained broad recognition in the capital market. The substantial funding support enhances the project's confidence in sustainable development and will strongly drive its technological accumulation and ecosystem development.
Early layout of intent concept, accumulation of deep technical genes: The Anoma team has long been considering and laying out the field of intent-oriented blockchain architecture, accumulating deep technical genes and conceptual deposits. Anoma's white paper can be traced back to 2018, and after years of incubation and evolution, it holds absolute time and technical advantages in the field of intent. Anoma foresaw the importance and future direction of intent interaction at the beginning of the emergence of blockchain applications, accumulating a deep understanding of industry foresight and technological essence. This has allowed Anoma to accumulate significant technical and time advantages, which will be a key factor in maintaining its leadership in the competition. Its early layout and long-term accumulation in the field of intent give it deep technical and conceptual genes, making it a core investment logic point for Anoma and positioning it to potentially become a leader in this emerging field.
Strong technical capabilities, fast product iteration, forming a complete technical ecosystem: Anoma has a strong research and development team with independently developed core technologies such as Taiga, Typhon, MASP, Vamp-IR, and Juvix, covering various aspects such as privacy computing, cross-chain communication, and circuit programming, demonstrating Anoma's deep accumulation in distributed systems and cryptography. Additionally, Anoma's product iteration speed is fast, enabling it to quickly respond to market demands and continuously launch new products. For example, Anoma is developing the privacy partition ledger Namada, which will be compatible with Ethereum and IBC chains, providing asset-independent inter-chain privacy communication. Anoma has formed a complete technical system, establishing a solid technical foundation that will guarantee its continued leadership in cutting-edge areas such as intent computing.
1.2. Valuation
Anoma's total financing scale is approximately $57.8 million, with a successful $26 million Series A financing completed in November 2021, valuing the project at approximately $260 million during the Series A financing. Although Anoma is still in its early stages, its intent-driven architecture is a more forward-looking and innovative design approach among many types of blockchains. If it can successfully establish a complete developer and application ecosystem in the future, its potential valuation space will be enormous.
1.3. Project Risks
Anoma's project risks mainly manifest in aspects such as technological implementation risk, ecosystem development risk, and competitive risk, as detailed in the 5.2 SWOT analysis section of the report.
2. Project Overview
2.1. Project Introduction
Anoma, developed by the Heliax development team, is a new generation decentralized application architecture based on the "intent-oriented" concept, achieving counterpart discovery, resolution, and settlement through a black box architecture, and building a full-stack decentralized application.
2.2. Team Overview
2.2.1. Overall Situation
Anoma was co-founded by Brink, Awa Sun Yin, and Christopher Goes, who met while working at the blockchain technology company All in Bits (also known as Tendermint), which established the Cosmos network. The three of them are the co-founders of the Anoma project. Prior to this, they had also jointly participated in the founding of the Swiss proof-of-stake validator Cryptium Labs and the blockchain development company Metastate, and co-founded Helia. The Anoma team consists of Heliax and Cryptium Labs, both leading institutions focused on blockchain research and engineering.
1) Heliax
Founded in 2020, with 37 interdisciplinary members, dedicated to driving the development of the next generation of the Web. The team has a strong technical background, with rich experience in areas such as distributed systems, programming language theory, and zero-knowledge cryptography. They have participated in the construction and maintenance of first-tier protocols such as Cosmos and Tezos, as well as the design of the inter-blockchain communication protocol IBC. Although Heliax has made slow progress, it has already formed a complete innovative ecosystem:
① Anoma: Intent-oriented protocol
② Namada: Privacy settlement Layer1 of the Anoma ecosystem, using a PoS mechanism and used for asset-independent inter-chain privacy, and will be compatible with Ethereum and IBC chains in the future.
③ Typhon: Consensus mechanism. Initially developed based on Tendermint and using Byzantine Fault Tolerance (BFT) consensus mechanism, Anoma later turned to another PoS proof-of-stake consensus mechanism "Typhon" developed by Heliax, to allow consensus partitioning between independent chains.
④ Taiga: Provides a unified execution environment for composable privacy. Taiga defines three types of intents: transparent intent, shielded intent, and private intent.
⑤ AnomaVM: Anoma's virtual machine, simplifying DApp application development on Anoma, using Juvix (an intent-centric programming language) and VampIR (circuit programming language).
2) Cryptium Labs
A provider of secure and highly available digital signature services, supporting various proof-of-stake (PoS) networks such as Tezos, Cosmos, and Polkadot. Cryptium Labs is also dedicated to innovative research in blockchain governance, security, and scalability.
3) Anoma Foundation
Established in 2020, headquartered in Zurich, Switzerland, it manages the blockchain Namada and privacy protection protocol Anoma, focusing on multi-chain privacy. It is a non-profit organization aimed at promoting and ensuring the development and long-term sustainability of the Anoma ecosystem.
2.2.2. Core Members
Adrian Brink: Co-founder and Chief Operating Officer of Heliax, as well as co-founder and Chief Operating Officer of Anoma. He holds a Bachelor's degree in Computer Science from King's College London and has previously served as a core developer and community manager at Tendermint and the Cosmos Network.
Awa Sun Yin: Co-founder and Chief Executive Officer of Heliax, as well as co-founder and Project Lead of Anoma. She holds a Master's degree in Computer Science from ETH Zurich and has conducted research in distributed systems and cryptography at IBM Research - Switzerland.
Christopher Goes: Co-founder and Chief Technology Officer of Heliax, as well as co-founder and Chief Architect of Anoma. He holds dual Bachelor's degrees in Mathematics and Computer Science from the University of Chicago and has previously served as a core developer and researcher at Tendermint and the Cosmos Network.

2.3. Financing Situation
• On April 28, 2021, Anoma Network completed a $6.75 million private placement financing, led by Polychain Capital, with participation from Electric Capital, Coinbase Ventures, FBG Capital, CMS Holdings, Lemniscap, Cygni Labs, Walden Bridge Capital, and others.
• On November 17, 2021, Anoma Network completed a $26 million (24 million Swiss francs) financing round, led by Polychain Capital, with participation from Fifth Era, Maven 11 Capital, Zola Capital, Electric Capital, and CMCC. Anoma Network will use the funding to advance its proof-of-stake (PoS) blockchain.
• On May 31, 2023, Anoma Foundation completed a $25 million financing round, led by CMCC Global. Other investors in this round include Electric Capital, Delphi Digital, Dialectic, KR1, Spartan, NGC, MH Ventures, Bixin Ventures, No Limit, Plassa, Perridon Ventures, Anagram, and Factor. Anoma Foundation currently manages the Namada blockchain, which focuses on multi-chain privacy, and the privacy protection protocol Anoma.

2.4. Past Development and Roadmap
2.4.1. Past Development
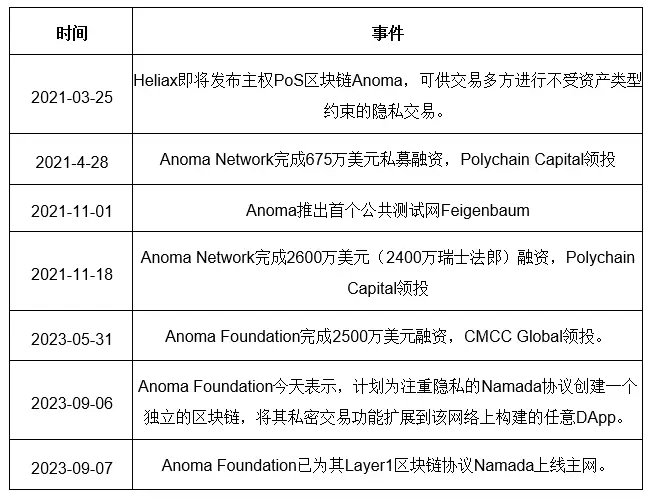
2.4.2. Current Progress
Anoma's first version, v0.1.0 of the testnet, has been launched within the year, with main features including chunked ledgers and simple transaction functionality. Additionally, the development team has deployed the Namada mainnet to explore the technical roadmap for privacy protection. In terms of technical progress, the team is slightly behind compared to similar projects in achieving the initial version. However, the project places emphasis on accelerating the launch and improvement of the mainnet in the next phase, while also focusing on attracting application ecosystem connections. This will help Anoma solidify its core technical foundation and truly realize the vision of a decentralized trading platform. Overall, Anoma adheres to the principle of steady development, and the current progress is considered normal. The main focus going forward will be on whether the project can timely enhance its product capabilities and create a healthy ecosystem.
2.4.3. Development Plans and Roadmap
In addition to completing the ongoing development of technical features, Anoma's main plans include:
• Advancing the development and application of the intent-driven framework and related protocols to achieve privacy protection and intelligent matching between users through zero-knowledge proof technology.
• Introducing more foundational applications, such as block explorers, to provide users with a better network experience and data analysis.
• Continuously enriching the application ecosystem, attracting more partners to join and creating a universal decentralized interaction platform.
• Improving community governance mechanisms and gradually achieving community autonomy, allowing users to participate in network decision-making and management.
2.5. Social Media Data
Anoma's Twitter account serves as the main external communication channel, currently with 26,500 followers. It has a high update frequency and timely releases the latest project developments, including core product progress, participation in industry events, partnerships, and coverage in globally renowned media. This comprehensively reflects the real-time dynamics of the project. Additionally, the project operates its own forum for community interaction, but the Discord and Telegram groups have not been disclosed, indicating room for optimization in online social interaction. Despite rapid follower accumulation, Anoma's influence on social platforms still needs further expansion compared to similar projects.
3. Project Analysis
3.1. Project Background
1) Development Background
With the development and innovation of blockchain technology, an increasing number of assets and applications are being created and operated on different chains. The interoperability and connectivity between these chains have become an important requirement and challenge (the "island effect"). Currently, there are some solutions in the market, such as cross-chain bridges, relay chains, and side chains, but they all have limitations and drawbacks, such as centralization risks, performance bottlenecks, security vulnerabilities, and poor user experience. Additionally, existing chain transaction models also have some issues, such as high complexity, poor privacy, and low flexibility, requiring users to be concerned about many technical details and execution processes rather than the results they want to achieve. Therefore, Anoma Network has emerged to provide an intent-centric, privacy-protecting protocol for decentralized transaction discovery, negotiation, and multi-chain atomic settlement.
2) Technical Background
From a technical perspective, the Anoma team deeply understands that existing public chain protocols have some problems in their underlying architecture. Early Bitcoin's scriptable settlement architecture had limited functionality and could not support complex applications. Ethereum's proposal of programmable settlement improved expressive capabilities but still could not achieve transaction counterpart discovery and problem resolution. This has led to the current stage where DApp protocols need to rely on at least one Web2 component to complete these functions, unable to achieve full decentralization. Anoma addresses this pain point by proposing a third-generation DApp architecture centered around intent, allowing users to define desired result states and achieve efficient and customizable private transactions. It can also accomplish counterpart discovery and problem resolution at the intent level, meaning DApps based on Anoma will truly have the capability for comprehensive decentralized and high-performance private computing. The intent-driven architecture marks a new stage in blockchain protocol development, and Anoma may lead the future direction of blockchain applications.
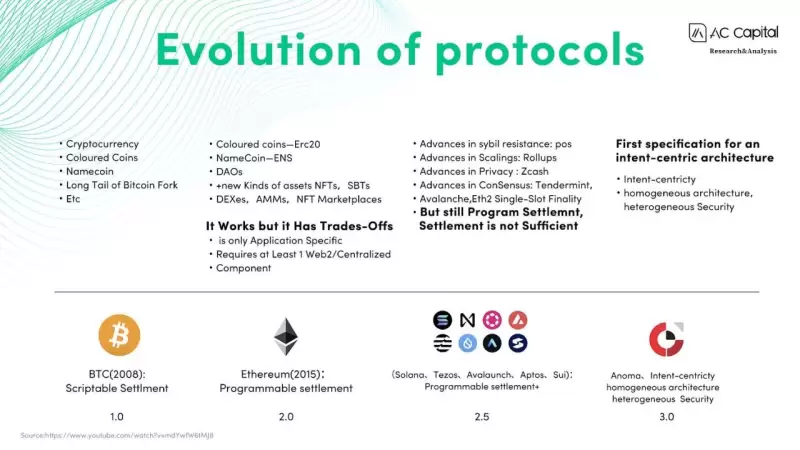
Source: AC Capital
3.2. Intent Definition
To facilitate our understanding of Anoma, let's first have a rough understanding of the definition of intent. The concept of intent originated from the Web2 era. When search engines like Google appeared, they supported users in expressing their information query intent by entering keywords and returned relevant search results. With the rise of e-commerce platforms like Amazon and eBay, users could express their intent to purchase a certain product on these platforms, and the platform would handle order processing, payment, logistics, and other subsequent details, greatly simplifying the shopping process. In the Web2 era, intent was mainly applied in the fields of networking and e-commerce, primarily to simplify user interactions and enhance user experience. As Web2 evolved into Web3, the definition of intent in Web3 is not yet fully clear, but there are some consensuses: Intent is a declarative commitment that authorizes future states without specifying an execution path. Users share their intent through signatures, allowing the recipient to choose the computation path on behalf of the user. It has the following characteristics:
Intent is a binding commitment to a preferred state space, represented by signed off-chain messages, authorizing one or more future states.
Intent does not specify a fixed computation path, allowing any path that meets specific conditions. Signing an intent authorizes the recipient to choose the path on behalf of the user.
Intent focuses on results rather than the implementation process, defining only the starting point and endpoint without specifying the execution path.
Different preferences of intent can be matched through solvers, known as the process of transaction counterpart discovery and resolution.
Intent is more flexible than transactions, allowing users to achieve their intent through multiple pathways, typically resulting in a better user experience.
Intent allows users to express the desired result without concerning themselves with the implementation process, reducing the complexity of on-chain interactions.
In simple terms, intent is a flexible off-chain signed message that authorizes specific future states without specifying an execution path. By matching different intents, it simplifies on-chain interactions and focuses on user experience.
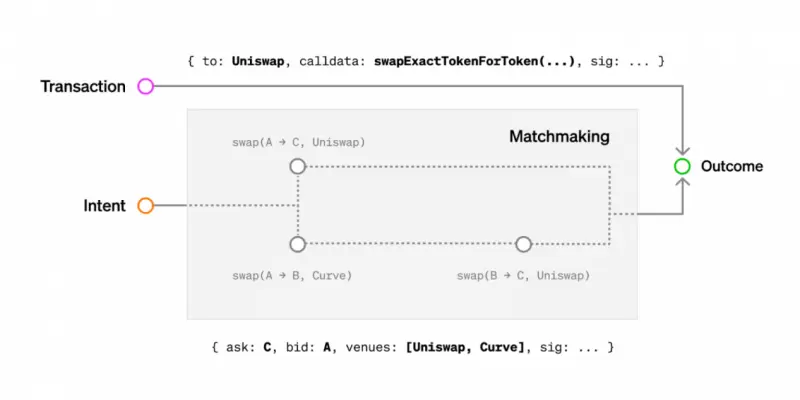
Source: paradigm
3.3. Project Principles
The core principle of Anoma Network is to achieve decentralized counterpart discovery and resolution through modules such as the intent propagation layer and solvers, and to use distributed ledgers for settlement, realizing a full-stack decentralized application. In other words, users only need to express their desired results (intent) without concerning themselves with the specific execution process (transaction). Through smart contracts or protocols, Anoma Network can automatically find the best transaction solution for users and ensure the reliability and privacy of transactions. The core transaction process of intent interaction is as follows:
• User Interaction: Users can send transparent, private, or protected intents to the Anoma network through the intent propagation layer. Intents are a way for users to express their transaction needs and conditions, such as the desire to exchange a certain amount of assets at a specific price.
• Intent Collection and Matching: Anoma's solver is responsible for collecting intents, performing balanced state transitions to match transaction counterparts. The solver is a smart contract that, based on user intents and network state, finds the optimal transaction solution and generates the corresponding transaction data.
• Transaction Processing: Matched transactions are submitted to the encrypted mempool for temporary storage, awaiting the consensus module's determination of the execution order.
• Consensus Module: The consensus module uses the Typhon algorithm to achieve consensus on the network's transactions.
• Execution Environment: Sorted transactions enter the execution environment for processing. The execution environment supports transparent, secret, and encrypted data types, as well as cross-application data interaction.
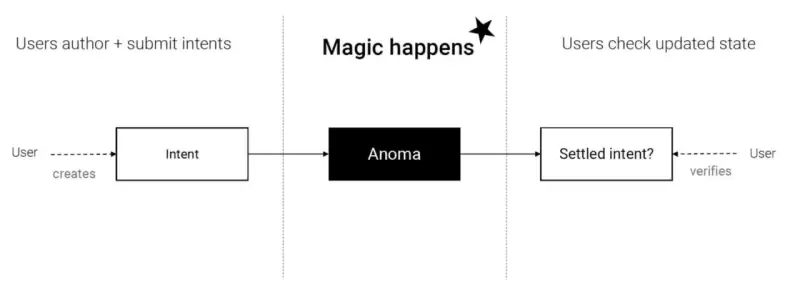
Specifically, the execution process of Anoma Network is as follows:
① The network layer implements communication and transmission functions between nodes, operating a peer-to-peer intent propagation layer where users can publish intent messages for transactions or services, describing their needs or conditions.
② Solver nodes are responsible for matching complementary intents to find transaction counterparts that meet both parties' requirements. Once a successful match is made, a transaction is generated.
③ The generated transactions enter the transaction mempool for temporary storage, awaiting the consensus module's determination of the execution order.
④ The consensus module uses the Typhon algorithm to achieve consensus on the network's transactions.
⑤ Sorted transactions enter the execution environment for processing. The execution environment supports cross-application data interaction and isolates transparent, shielded, and private data operations from different applications.
⑥ Finally, the settlement of transactions is allocated to different fractal instances for processing. The fractal scaling solution provides users with a secure and performance-adjustable small-scale operating environment, helping to improve the overall performance and scalability of the Anoma system.
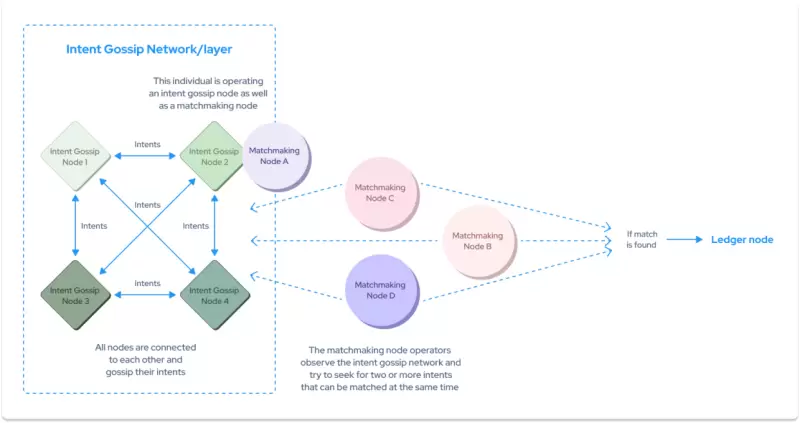
Source: Anoma
Through this collaborative approach, Anoma has implemented a decentralized mechanism for coordination and transaction execution, ensuring transparent and efficient transaction handling. Users do not need to find transaction counterparts themselves or master complex transaction technology; they only need to express their intent, and the system will help complete the subsequent matching and settlement. This has established a full-stack decentralized application system.
3.4. Technical Architecture
Based on Anoma's execution principles, we can understand that the Anoma technical architecture mainly includes the following components, which together form a fully functional and secure decentralized network platform, supporting secure computation, automatic scaling, cross-application interoperability, and other features.
1) Propagation System
Anoma's propagation system supports path authentication and propagation incentives between nodes, providing data availability. It is responsible for propagating various transactions and application-level message data throughout the network, and defines strict message validity verification rules to prevent the spread of illegal data. To incentivize node participation in message propagation, it has designed a transparent incentive mechanism that allocates rewards based on each node's propagation contribution, recorded in the transaction chain. The propagation system is an important part of the Anoma network that ensures user privacy and data availability.
2) Consensus Engine
The consensus engine abstracts multiple substantive nodes into a virtual node, maintaining correctness as long as more than 2/3 of the substantive nodes are running normally. This achieves fault tolerance, allowing the system to resist the failure of some nodes. The Typhon algorithm, based on the BFT algorithm, enables each substantive node to reach consensus through information exchange. The Typhon algorithm also has its own innovations, such as using an asynchronous network model and a transaction-oriented processing approach, which improve the scalability and performance of the Typhon algorithm. The Typhon algorithm enables substantive nodes in the network to sort new transactions and collectively update the network state, ensuring the integrity and consistency of the Anoma network state. The Typhon algorithm is a highlight of Anoma's blockchain design, contributing to the creation of a secure and efficient decentralized environment.
3) Execution Environment
Taiga provides a secure and reliable operating platform for distributed applications and smart contracts, supporting transparent, secret, and encrypted data types, as well as cross-application data interaction. It can isolate different applications and contracts, while also providing state verification and message passing, enabling cross-application data interaction. The execution environment provides a standard, efficient, and powerful operating foundation for smart contracts. Developers can easily use different data types for complex secure computation, while avoiding interference from other applications. This greatly enhances the application friendliness and reliability of the Anoma network.
4) Compilation Stack
This includes the Juvix language, Anoma Virtual Machine (AVM), and VampIR compiler, helping developers to create secure and privacy-protecting distributed applications without concerning themselves with low-level details. It mainly consists of three parts:
The Juvix language is an advanced functional programming language that allows developers to easily express distributed program logic containing public, secret, and encrypted data.
The Anoma Virtual Machine (AVM) is an abstract distributed virtual machine that can compile Juvix-based programs into abstract categorized operations independent of specific encryption implementations.
The VampIR compiler then transforms AVM output into executable expressions for different system-specific implementations, such as zero-knowledge proof systems or homomorphic encryption. Developers can utilize these privacy computing capabilities without concerning themselves with low-level details.
Through the compilation stack, developers can focus on business logic programming, and the compilation system will automatically optimize for different targets. Applications developed can achieve high performance while protecting privacy. Additionally, the AVM layer in the compilation stack also defines the billing mechanism for Anoma network resources, managing distributed application identity authentication and interaction protocols. This design makes the compilation stack an integral part of the Anoma architecture, facilitating the development and deployment of secure and efficient decentralized applications.
In summary, Anoma has built a comprehensive technical architecture covering from the transmission layer to the execution layer by defining a clear distributed computing model and the responsibilities of its various components. This architecture utilizes a series of secure computing technologies to protect user privacy, while using incentive mechanisms and governance mechanisms to ensure network integrity and reliable operation, aiming to establish a powerful and secure decentralized open computing platform.
3.5. Project Technical Features
The technical features of Anoma Network mainly include the use of an intent matching system and heterogeneous security models, support for data privacy protection, and fractal scaling expansion, as well as multi-chain support.
1) Intent Matching System
In Ethereum's EVM, transactions do not require future states but authorize specific execution paths. Anoma includes a matching system that allows users to broadcast transaction intents using Gossip. In simple terms, Anoma consists of two main parts: a distributed ledger and an intent matching system. They complement each other and can also run independently. By using Intent Gossip running nodes, Token exchange solvers, and RPC servers requesting new intents, transactions are submitted from matched intents to the distributed ledger, helping users automatically discover transaction counterparts.
2) Homogeneous Architecture, Heterogeneous Security Model
Anoma follows the principles of homogeneous architecture and heterogeneous security, similar to the TCP/IP protocol stack. This means that various levels of the Anoma network are standardized, but the choice of who to connect with and what data to trust is left to the users. Different users can make different choices while using the same protocol stack. Heterogeneous security means that different applications have different security features. Users can create local Anoma networks, known as fractal instances, based on their needs and transaction patterns. These local networks can interoperate with other networks, allowing users to flexibly transfer assets between different levels of security and throughput. Through architectural unity, Anoma provides a clear and reliable development system; through diverse security models, it gives users and application developers greater freedom of choice.
3) Data Privacy Protection
Anoma Network supports the processing of transparent, shielded, and private data. It uses cryptographic techniques such as zero-knowledge proofs to achieve the matching and execution of private intents, while protecting user privacy and security. Users can customize the mechanism for handling different types of data in the system. Data is divided into transparent, shielded, and private categories. Transparent data is publicly visible, shielded data is private and visible only to the user, and private data is encrypted within the system, ensuring privacy.
4) Fractal Scaling Expansion Solution
Anoma uses a fractal solution to address the scalability issue of blockchain, allowing users to create local instances to meet other transaction needs. Fractal refers to dividing Anoma into different application chains to handle different tasks, allowing each Anoma application chain to be highly customized to achieve scalability and address user growth (similar to supporting the IBC protocol for expansion purposes). In the future, its security will be enhanced by the ⅣInterchain Security, ⅣMesh Security, and ⅣInterchain Alliance projects. The inspiration for fractal instances comes from mathematical fractals, which are geometric shapes that can infinitely scale and repeat their own structure. The purpose of fractal scaling is to improve the performance, security, and scalability of the Anoma protocol, allowing users to choose the appropriate network for their transactions based on their actual situation. Fractal instances can be understood as small chains provided for application use.
5) Multi-Chain Support
Anoma uses the IBC protocol for cross-chain communication within the Cosmos ecosystem, enabling data transfer between blockchains through relayers, aiming to become a multi-chain privacy layer. Although relayers are typically operated by node operators, anyone with the capability can run them and earn fees in the process.
6) Flexible Programming Model
Anoma enables interaction coordination between different applications and users through standardized application components and rules. It protects user rights and supports flexible and diverse decentralized application development. Developers only need to implement the corresponding components according to the specifications to launch applications, while users have the highest level of permission control. This simplifies development and maximizes prevention of application abuse of user permissions.
3.6. Project Use Cases
Anoma provides several innovative original components for application developers, enabling them to build various cutting-edge decentralized applications and optimize existing application pain points.
1) Provided Components
• Incentivized Data Availability: A mechanism to incentivize nodes in the intent propagation layer to provide data availability, incentivizing the generation of data required for future transactions.
• Programmable Solver: Functionality that allows users to outsource the calculation task of finding atomic state transitions (transactions) involving multiple parties simultaneously satisfying all their preferences to intent propagation nodes running solver algorithms, i.e., outsourcing complex multi-party transaction calculations to solver nodes.
• Programmable Threshold Decryption: A technology that uses Ferveo (a distributed key generation (DKG) cryptographic scheme) to encrypt and decrypt intents submitted by users, enabling on-demand batch processing and ensuring fairness.
• Programmable Privacy: A scheme that uses ZKP (zero-knowledge proof) systems and FHE (fully homomorphic encryption) to separate data attribute verification from the knowledge of the data itself, allowing users to build applications that handle transparent, shielded, and private states within the same application.
These components enable Anoma to build complex user-friendly applications that require specific game, privacy, and latency attributes.
2) Improvement for Existing Decentralized Applications Using Anoma Architecture
① Decentralized Exchanges (DEX)
The current mainstream DEX models use order books or AMM to match transactions. In the order book model, users submit orders off-chain, and then specific parties are responsible for submitting matched orders for settlement on-chain (e.g., 0x, Wyvern, Seaport, CoWSwap), or based on the chain itself, establish a trading pool for users to trade directly on-chain (e.g., Uniswap). The former leads to trust dependence on specific parties and potential unfair ordering, while the latter results in high fees and inefficient execution. Using the Anoma architecture, a decentralized approach can be adopted to replace these two models:
• Transaction participants use Anoma's distributed intent propagation network to broadcast their trade orders in the form of intents.
• Anoma's programmable solver can collect any number of complementary intents and match them through algorithms to find balanced trades that maximize meeting the conditions of all parties.
• The matched trades are submitted to Anoma fractal instances holding the relevant assets for centralized settlement, and provide threshold decryption to ensure fairness.
• This pattern generalizes arbitrary complex transactions, does not limit specific tokens, and removes reliance on a single platform or mechanism.
In other words, using the Anoma architecture can achieve privacy, batch transactions, and order books without the need for single-point trust.
② Rollups
For existing Rollup architectures, a major limitation is that they use a single sorting/solver node to sort transactions and calculate states, which raises some trust issues, such as unfair sorting or ignoring transactions. Some Rollup projects express a desire to achieve decentralized transaction sorting. If Anoma's technical solution is used, it can achieve decentralized Rollup sorting:
• Anoma can simulate the execution environment of Rollup by initiating a fractal instance, where Anoma's decentralized consensus algorithm Typhon can be used to achieve consensus on transaction sorting within the fractal instance, allowing multiple nodes to collaborate on sorting transactions, removing single-point dependence.
• At the same time, the fractal instance can submit execution results to the root chain based on ZK-Rollup or OP-Rollup rules, similar to existing Rollups.
③ Public Goods Donations
For public goods funding (such as Gitcoin), using Anoma has the following advantages:
• Sponsors, project parties, and donors can express funding commitment amounts, project execution requirements, and donation intentions, among other conditions. Anoma's distributed solver can match these complementary intentions, reflecting the priorities and threshold requirements of different participants.
• The solver may generate a single centralized transaction that meets all conditions, advancing settlement at the end of the QF. For donation amounts, Anoma's private computing capabilities can protect the privacy of individual donations.
• Expressive intent design can capture variables that cannot be expressed in a simplified QF model, such as the minimum funding threshold required for a project. Compared to the traditional model that only considers simple round matching, the Anoma version achieves a more expressive game theory capability. Additionally, it maintains fairness through decentralized decision-making, providing a convenient and unbiased experience for all participants.
Overall, the Anoma architecture can inject new vitality into public goods funding, balancing privacy protection, fairness, and user experience optimization.
3) Anoma Enables Innovative Applications
1) DAO 2.0
Anoma provides infrastructure for implementing private DAOs, with features that retain decision rules and data privacy, while selectively allowing the necessary proofs to be made public. With this system, a framework similar to a multi-currency system can be built, where communities can create exclusive private DAOs controlled by members, with independent internal currencies and assets, and impose restrictions or taxation on external transactions.
Anoma's design can help users easily establish secure, highly private, and transparent DAOs, fully protecting the privacy of participants while ensuring the healthy operation of the entire system. This is conducive to forming a diverse currency ecosystem and achieving common governance and collaboration among different communities.
2) Private Auctions
Anoma can also be applied to "private auctions." Through private data and threshold cryptography, Anoma can ensure that bidders' identities and bids are anonymous, and reveal the winner and price at the end of the auction, avoiding information leakage during the bidding process. This allows auctions to avoid some problems in game theory, such as bidders overbidding or undervaluing their true worth.
3) Local Private Games
Applications that interact directly with mobile devices can deploy dedicated fractal instances for small-scale users within a local area network, achieving low-latency private gaming experiences. Anoma can be used to implement applications similar to poker games, where players can sort and transition states on a temporary consensus instance and submit the results to a long-running fractal instance at the end of the game. This allows players to enjoy low-latency and cost-free gaming experiences while maintaining the privacy of their hands and randomness.
In summary, Anoma not only supports innovative application types but also helps improve the performance of existing applications, making its application prospects broad.
4. Track Space and Potential
4.1. Track Overview
4.1.1. Project Classification
Anoma belongs to the blockchain infrastructure field, specifically in the intent-driven architecture track.
4.1.2. Track Scale
Intent-driven applications are currently in the early stages but have broad development prospects. As a new and cutting-edge field, there are currently no clear market size data for intent-driven applications. However, considering the continuous expansion of the overall blockchain market size and the wide application prospects in scenarios such as DEFI, cross-chain transactions, and privacy protection, it can be foreseen that it has long-term application prospects and market potential.
4.1.3. Track Landscape
The initial framework provided by CV Labs for intent-driven application classification provides a preliminary framework for potential application types in this field. However, it should be noted that there is some overlap between application classifications, and the current framework is overly simplistic. Additionally, as this field is developing rapidly, the classification framework needs continuous revision and improvement. Several months from now, the framework may already need to be updated. Typical intent-driven applications that have garnered widespread attention in the market include decentralized trading platforms such as 1inch Fusion and UniswapX, which have integrated user intent expression and matching, as well as cross-platform trading experiences. Other types of applications existing in the market may not be fully covered in this preliminary classification, and continuous summarization and refinement of classification criteria are needed based on industry practices. As the concept of intent-driven applications deepens in the blockchain field, the classification framework is expected to evolve from a single surface feature to a multi-level system considering both functionality and implementation mechanisms.
In conclusion, this classification attempts to summarize potential application types in this new field, but as the field is still in its early stages, the classification criteria need further improvement and enrichment through practical research to truly explore the direction of industry development.
Source: CV Labs
Let's first understand the architectural elements required to build intent and then provide a simple interpretation of the track classification.
1) Key Elements Required for Intent Architecture
① Account Abstraction (AA): Separating wallet addresses from user accounts through smart contract wallets to simplify transaction processes and enhance security.
② Minimizing the Impact of Maximum Extractable Value (MEV): MEV can lead to unfair transaction sorting, so achieving intent requires minimizing MEV's adverse effects on decentralization.
③ Cross-Chain Technology: Supporting cross-chain asset transfers, connecting blockchain networks, and achieving cross-chain intent.
④ Oracle: Obtaining reliable off-chain data to avoid reliance on failures and ensure smooth intent execution.
⑤ Various Aggregators: Assisting solvers in finding the optimal execution path to improve intent matching efficiency.
⑥ Gas Optimization: Lowering gas costs through products, protocols, etc., to improve intent execution efficiency.
⑦ Simplified Wallet Authorization Process: Achieving secure and convenient wallet authorization through account abstraction and other methods.
Intent architecture requires various technical elements to work together to reduce execution complexity, improve efficiency, and achieve a simple, secure, and convenient intent interaction experience.
2) General Purpose Solutions
A general-purpose solution refers to a solution that can be applied to any domain and any state of intent, without being limited by a single domain or user account. This solution needs to provide a flexible and general language or tool support at the underlying level, allowing users to easily express their intent and support diverse and complex intent types. This solution also needs to effectively address user intent and provide the optimal or near-optimal solution. Additionally, it needs to ensure the correctness, completeness, and privacy of user intent, and support cross-chain and cross-domain intent interaction. Intent projects based on domain-specific languages (DSL) are a typical classification of general-purpose solution intents. Current intent general-purpose solution projects include Anoma, Essential, SUAVE, and CoW Protocol.
3) Specific Intent Solutions
Intent-Specific Solutions
Intent-specific solutions refer to solutions that are only applicable to specific domains or intent related to user accounts, subject to limitations related to a single domain or user account. These solutions use smart contract wallets (SCW) as the entry point for intent, allowing users to specify and implement simplified intent while simplifying gas payments and verification processes. These solutions are mainly suitable for common and simple intents, such as limit orders, gas sponsorship, delegation, and transaction batching. The current types of domain-specific solutions include:
① Aggregation & Limit Orders
Aggregation and Limit orders are two methods to improve transaction efficiency and reduce costs.
• Aggregation reduces the number of transactions and gas fees by aggregating multiple on-chain transactions into one transaction. It can be achieved through cross-chain protocols, aggregators, etc. It utilizes all available on-chain liquidity to provide the best price but may increase third-party risks and costs, affecting decentralization.
• Limit orders allow traders to specify buy and sell prices instead of trading at market prices. It can be implemented through smart contract wallets, relayers, etc. It gives traders more pricing control and strategy implementation space, avoiding slippage, but may result in unfulfilled trades or missed opportunities due to market prices not meeting the criteria.
② Gas Sponsorship, TX Batching & Delegation
Gas sponsorship and TX Batching & Delegation are two methods for executing transactions on-chain, allowing users to avoid paying gas fees or holding native tokens, thereby reducing barriers to use and costs. Gas sponsorship involves a third party paying gas fees on behalf of the user, while TX Batching & Delegation involves a third party executing transactions on behalf of the user. The advantages of these methods include improving user experience and efficiency, attracting more users to use blockchain applications. However, the disadvantages include potentially increasing third-party risks and costs, as well as affecting the security and decentralization of the chain.
③ Bundlers
Bundlers are a special role on-chain responsible for packaging user intent into regular transactions and submitting them to specific contracts. Bundlers can receive gas fees or other incentives from users or contracts to execute user intent. They can improve chain efficiency and user experience by optimizing transaction execution paths and results without requiring users to be concerned about technical details and complexity. An example of bundlers is proposed in ERC-4337, which is a method for implementing account abstraction (i.e., allowing users to use smart contract wallets instead of externally owned accounts as the primary account).
4.2. Competitive Analysis
4.2.1. Competitive Analysis
According to the track landscape classification, Anoma, as a general-purpose solution, competes mainly with intent infrastructure projects such as SUAVE, Essential, and CoW Protocol.
1) SUAVE
SUAVE is a unified auction protocol for value expression, separating the mempool and block generation from existing blockchains and providing highly specialized plug-and-play alternatives. SUAVE promotes decentralization collaboration by sharing the same sorting layer and uses preference as a core concept to address MEV-related challenges.
While SUAVE is a new blockchain, it is not a general smart contract platform that can compete with Ethereum or any other participating chains. If Anoma is compared to building an intent-centric blockchain, then SUAVE is building intent-centric infrastructure.
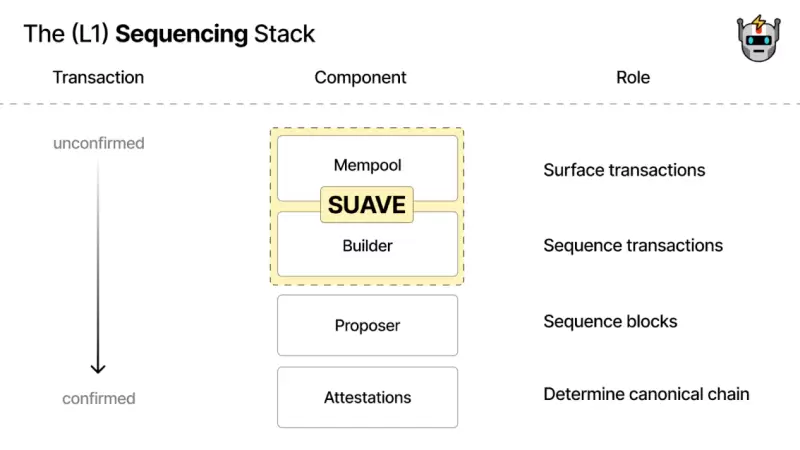
Image Source: SUAVE in the blockchain stack
The main innovations of SUAVE include:
• Illuminating the Dark Forest: SUAVE aims to expose and quantify unfair events in the MEV ecosystem, breaking down information barriers between participants, and increasing transparency and fairness.
• Democratic Mining: SUAVE aims to integrate miners and retrievers in a maximal way to promote competition among all parties and is open to all miners to prevent MEV integration and centralization.
• Benefit Distribution: SUAVE aims to give MEV to those who create it—Ethereum users—by providing optimal execution, reducing slippage, and lowering gas fees.
2) Essential
Essential is a project driving the blockchain ecosystem from value extraction to intent fulfillment, developing a range of products including a domain-specific language (DSL) for expressing intent, an Ethereum standard for intent-based account abstraction, and a modular intent layer. Essential's mission is to empower users, eliminate exploitation, and promote a user-centric and fair blockchain future. The main innovations of Essential include:
• DSL: Essential provides a domain-specific language (DSL) for expressing intent, allowing users to express what they want to do without needing to understand the technical details and complexity of blockchain. DSL can achieve standardized intent expression and optimized solving, enhancing the composability and development of intent-based applications.
• Account Abstraction Standard: Essential provides an Ethereum standard for intent-based account abstraction (ERC-4337), empowering solvers to construct valid transactions based on user intent and introducing intent functionality into existing EVM chains. The account abstraction standard can enhance blockchain security and flexibility.
• Modular Intent Layer: Essential provides a modular intent layer to ensure the architecture of intent, aggregated order flow, MEV resistance, and the possibility of cross-chain intent execution. The modular intent layer can improve blockchain efficiency and user experience.
3) CoW Protocol
CoW Protocol builds a trustless and efficient peer-to-peer trading network for traders and solvers. Transactions can be settled directly through on-chain AMMs or through DEX aggregators, depending on which pool/path offers the best price. It achieves batch auctions through Coincidence of Wants (CoWs) to maximize liquidity and utilizes all available on-chain liquidity when needed. The main innovations of CoW Protocol include:
• Batch Auctions: CoW Protocol uses batch auctions as a matching system to optimize transaction execution paths and results, enabling intermediary-free or currency-agnostic transactions while improving liquidity and efficiency. CoW Protocol spreads user intent through the Gossip algorithm and finds the optimal CoWs combination through solvers to maximize transaction value.
• Coincidence of Wants (CoWs) as a matching mechanism for user intent and transaction results, enabling intermediary-free or currency-agnostic transactions while improving liquidity and efficiency.
• Utilization of On-Chain Liquidity: CoW Protocol can optimize transaction execution and results by utilizing all available on-chain liquidity, including AMMs, DEX aggregators, bridge protocols, etc.
• CoW Hooks: CoW Protocol provides CoW Hooks functionality, allowing users to perform custom operations such as staking, providing liquidity, bridging assets, selling or buying NFTs before and after transaction execution.
4) dappOS V2
dappOS V2
dappOS V2 is an intent protocol that references dappOS accounts and dappOS networks to simplify user interaction with dApps to achieve a user experience at the level of CeFi. It also eliminates the fragmentation barriers brought by multiple chains through "Chain Abstraction" technology (similar to account abstraction). The main innovations of dappOS V2 include:
• Chain Abstraction: dappOS V2 uses chain abstraction technology to eliminate the fragmentation barriers brought by multiple chains, allowing users to focus on the total amount of funds in their accounts without needing to be concerned about the differences and compatibility between different chains.
• dappOS Accounts: dappOS V2 provides a dappOS account that allows users to complete all actions with a single signature, without specifying execution paths and details. dappOS accounts can implement functions such as multi-signature, key recovery, gas-free transactions, multi-sign authorization, multiple transfers in a single transaction, and fee limits.
• dappOS Network: dappOS V2 offers a dappOS network that enables users to interact with dApps at the level of CeFi user experience. The dappOS network can facilitate fast, secure, and convenient transactions and contract execution, while also supporting cross-chain, privacy, MEV, and other functionalities.
4.2.2. Competitive Advantages
The core competitive factors between intent-oriented infrastructures mainly include: technological innovation capabilities (product architecture, performance, etc.), business model advantages (project economic model, etc.), user scale (acquiring users), and ecosystem application landing capabilities. Compared to other competitors in the same track, Anoma's competitive advantages are mainly reflected in:
① Providing a full-stack unified solution, supporting various applications.
② Using fractal technology to solve scalability issues.
③ Protecting user privacy with privacy payment technology.
④ High brand awareness and strong financial strength.
⑤ Strong technological research and development capabilities, fast product iteration.
⑥ Initial scale of ecosystem construction, continuous incubation of applications.
4.3. Token Economic Model Analysis
4.3.1. Token Total Supply and Distribution
Anoma tokens have not been issued yet, and it is expected that governance tokens will be issued.
4.3.2. Core Demand for Tokens
The core demand for Anoma tokens may include network nodes, developers, and end-users:
• Network nodes need to hold and stake a certain amount of Anoma tokens to participate in the network's governance process. Nodes need to lock tokens for a long period to become validation nodes responsible for network security and transaction confirmation.
• Developers need to hold Anoma tokens to deploy on the Anoma network in a cost-effective manner. Anoma tokens can be used to pay for deploying smart contracts, creating accounts, and other gas-related operations.
• End-users need to hold a small amount of Anoma tokens to pay for transaction gas fees. As the Anoma ecosystem grows, various DApps will attract a large number of users to use the Anoma network, and users will need tokens to pay for transaction fees.
5. Preliminary Valuation Assessment
To conduct a preliminary assessment of Anoma's value, we can analyze based on the following questions:
5.1. Core Issues
What stage is the project in its business cycle? Is it in the mature stage or in the early to mid-stage of development?
Based on the current development status of the Anoma project:
• The project's technical system and product architecture are still undergoing continuous improvement and iteration, with key technologies such as fractal solutions and intent interaction frameworks in the exploration and validation stage.
• Ecosystem construction is also in its early stages, with the core blockchain infrastructure in place, but applications and ecosystem support need further refinement.
• The financial strength has reached a certain scale, but in terms of team expansion and business expansion, operational management scale still needs improvement.
• Market visibility is increasing rapidly, but user scale and application scenarios require long-term accumulation and mastery.
• The overall technological maturity and business ecosystem of the project still need time to be tested.
Considering that the key indicators are in the early stage of development, the Anoma project can be considered to be in the early to mid-stage of development. This provides sufficient room for future technological optimization, ecosystem layout, and user growth, with broad prospects. However, it also faces significant uncertainties.
What are the main variable factors in the project's operations? Are these factors easy to quantify and measure?
The main variable factors in the project's operations are the scale of developers and users, which are relatively easy to quantify:
• Number and activity of developers: Key indicators include the number of registered developers and active developers. Analysis can also be done through statistics on developer platform registrations and application submissions.
• User count: The key indicator is the number of active users (e.g., daily or monthly active users). User address count changes can also be tracked through blockchain explorers and various platforms.
• User activity: Metrics such as monthly transaction frequency/amount reflect user usage frequency. Transaction data can be used for statistical analysis to measure user stickiness.
What is the project's management and governance approach?
The project's current management and governance approach is primarily characterized by product development-oriented governance led by the core development team:
• The project is initiated by the Anoma Foundation, with the core development team responsible for daily operational management.
• Product design and development decisions are made by the technical team, primarily based on a technology-first approach.
• User feedback is channeled to the team through community communication channels, but direct decision-making influence is limited.
5.2. SWOT Analysis
5.2.1. Strengths
The strengths of the project are detailed in the Core Investment Logic section:
• Cutting-edge technological concepts and a strong team.
• Recognition by top institutions and support from multiple rounds of financing.
• Early layout of intent concepts, accumulating deep technological genes.
5.2.2. Weaknesses
Complexity and risk of technical implementation: Anoma's cutting-edge technological concepts require solving many technical challenges to achieve modules such as intent propagation, solving, and settlement, necessitating continuous investment in technical research and long-term exploration.
Challenges in ecosystem construction: As a new architecture for blockchain infrastructure, Anoma's value needs to be amplified through ecosystem effects. This requires the Anoma team to focus on developer community building, top-tier application incubation, and attract developers and users. If ecosystem development progresses slowly and applications are insufficient, it will be challenging to drive widespread adoption and application of Anoma.
Governance mechanism risk: The governance mechanism of Anoma requires observation. The core development team has significant influence in the project, and if the governance mechanism is not well designed, it may lead to excessive centralization of power, deviation from user needs, and hinder the long-term development of the ecosystem. Continuous observation of Anoma's governance approach is necessary.
Slow landing speed risk: Compared to many other projects in the intent track, Anoma's progress is relatively slow, and it will take some time before the mainnet goes live. If competitors iterate their products faster, Anoma may face the risk of being overtaken by competitors. The Anoma team needs to control the product pace and accelerate the landing progress.
Trust and immaturity of intent concept in the intent execution process: Anoma's intent execution relies on specific executors (solvers), which may centralize power and pose a risk of monopolization, affecting the trust foundation of the entire system. Application developers of Anoma need to balance security, privacy, and convenience. Additionally, while the intent concept has mature applications in Web2, this relies on a mature Web2 infrastructure. To achieve mature intent applications on the developing Web3, continuous progress in blockchain technology is needed. Intent computation involves multiple aspects of blockchain and requires further development for mature application.
5.2.3. Opportunities
The pain points of blockchain applications are huge, and the solution is highly anticipated: There are widespread pain points in current blockchain applications, such as discovery, solving, and settlement, which have constrained the further development of blockchain applications. This presents a huge opportunity for projects like Anoma, which provide a completely new application architecture solution. By building an intent-oriented application architecture, Anoma is expected to fundamentally address the pain points in existing blockchain applications. This new technological path has attracted the attention of numerous capital and developers. Once Anoma successfully realizes its technical roadmap, its solution will be highly anticipated by blockchain applications, which will help Anoma quickly acquire customers and users, leading to rapid growth. Once these cutting-edge technological solutions mature, they are expected to trigger a new round of explosive growth in blockchain applications, ushering in the era of Blockchain 3.0. If Anoma can seize this opportunity, the project has broad prospects.
Empowering intent for intelligent on-chain interaction, Anoma returns control to users: With the development of intent-oriented protocols and infrastructure such as Anoma, SUAVE, and DappOS, Web3 is expected to achieve more intelligent, customizable, and fair on-chain interactions. Based on intent, users can interact with mainstream DApps as conveniently as using Uber. More importantly, the intent architecture will allow users to regain control of on-chain activities. Users can customize their needs through third-party solvers, no longer being passive participants or subject to unfair cycles. Ordinary users can also participate in MEV profits, no longer just being exploited by extractors. The emergence of projects like Anoma transforms users from passive recipients to active intent expressers, truly controlling blockchain activities. This significant progress brought about by intent interaction presents an important opportunity for Web3 products to surpass Web2 from a user experience perspective. Anoma is leading the advancement of intent technology, and if it can seize this opportunity to truly benefit ordinary users, it has broad prospects. Anoma is expected to lead blockchain into the era of user control, fairness, and efficiency in 3.0.
Deep integration of AI and blockchain, Anoma is expected to open a new window of opportunity for Web3: The intent-centric design concept is essentially the project's exploration and efforts to reduce user barriers. Previously, although the project has been striving to simplify user interactions, the core concept of "user intent" has not been fully emphasized. The recent new approach to intent-centricity promoted by Paradigm and EthCC has begun to introduce AI technology as a key productivity tool to understand and automatically execute user intent. This marks the deep integration of AI and blockchain, opening a new window of opportunity for Web3, no longer just staying at the conceptual level.
5.2.4. Project Threats
Competitors progressing too quickly, insufficient landing applications. In the field of intent-oriented blockchain applications, Anoma faces challenges from multiple competitors. On the other hand, Anoma's own product landing speed is relatively slow, and it will take some time before the mainnet launches. The critical lack of landing applications also hinders Anoma's progress in acquiring users and developers. If competitors continue to maintain a leading pace in product development, Anoma may face the threat of competitors seizing market opportunities, severely impacting Anoma's market share and growth potential. These collectively constitute the core threats that Anoma's development faces. The Anoma team needs to pay attention to the competitive landscape, control the product pace, and address this threat.
Difficulty in achieving intent privacy: Anoma's intent has an irreversible nature, making it difficult and costly to cancel once signed, which presents challenges in achieving intent privacy. Currently, EVM-based systems struggle to provide intent privacy protection. To achieve standardization and privacy in intent, new solutions such as Anomo are attempting to use customized privacy languages like Juvix. Juvix can be compiled into WASM or circuit languages for use by chains like Anoma. However, these customized languages and compilation technologies are still immature, and achieving privacy still faces many difficulties. This is a core risk point that Anoma faces in its technological research and development.
6. References
https://anoma.net/ Anoma Project Official Website
https://twitter.com/anoma Anoma Official Twitter
https://anoma.net/blog Anoma Official Blog
https://github.com/anoma/whitepaper/blob/main/whitepaper.pdf Anoma Whitepaper
https://www.techflowpost.com/article/detail_13964.html Exploring intent-oriented intelligent interaction
https://www.panewslab.com/zh/articledetails/z8zisjz3o8x6.html Focusing on results with "intent" at the center, an excellent path for the large-scale landing of Web3
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



