Monero遭51%攻击后,Qubic社区把压力转向Dogecoin?
近期,AI公链Qubic在“有用工作证明(uPoW)”机制的驱动下,短时间内重组了Monero区块,导致60个区块被孤立。尽管此次攻击是否构成严格意义上的51%攻击仍存有争议,但其对市场的冲击已超越技术层面。网络完整性的不确定性迫使交易所采取风控措施,门罗币价格亦随之承压。此次攻击事件揭示了 PoW 机制下的安全预算在外部激励作用下可能被穿透,从而暴露出算力集中与安全边界的结构性脆弱。
更值得关注的是,Qubic 社区的后续投票将市值超350 亿美元的Dogecoin列为潜在攻击目标。这种动向不仅加深了市场的担忧,也使外部对激励算力分布与网络完整性之间关系的讨论再度升温。算力的可迁移性与安全预算的边界正在被重新检验,在此背景下,下文CoinW研究院将对此事件进行更深层次的剖析。
一.Qubic 的“51% 攻击”,是营销叙事还是技术威胁
1.1.uPoW 机制如何突破传统安全预算
在标准 PoW 架构中,算力稳定性的基石是链内安全预算,即区块奖励与手续费形成的激励闭环。以 Monero为例,目前网络已进入尾部排放模式,每区块奖励固定为 0.6 XMR,平均每两分钟出块一次,全网每日出块约 720 个,总安全预算(约等于矿工区块补贴*XMR市价)约 110,367美元/天,这也是攻击者持续控制多数算力所必须负担的经济下限。
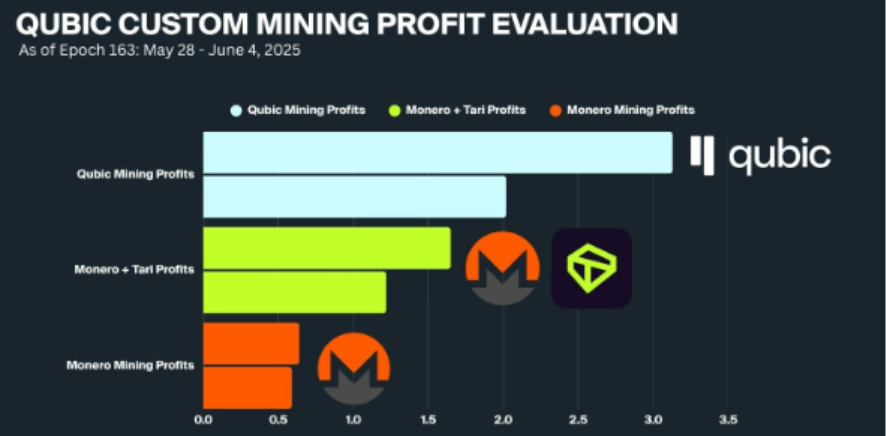
Qubic 引入有用工作证明(uPoW)突破了这一传统限制。不同于单纯依赖区块奖励的模式,Qubic 在给予矿工 QUBIC 出块奖励的同时,还将算力导向 Monero 挖矿,并把这部分奖励兑换成 USDT,用于在公开市场回购并销毁 QUBIC。这种情况下,矿工不仅能直接获得 QUBIC 区块补贴,还能通过回购销毁所带来的通缩效应获得间接收益,从而形成比单独挖 XMR 更高的综合回报。这使Qubic在短期内迅速调动了大量算力,并导致六个区块重组与近 60个孤块的异常现象。实际上,早在今年6月份,Qubic就开始对Monero和Tari进行挖矿,并把奖励都会兑换成 USDT,用于回购QUBIC代币,然后销毁。据Qubic官方披露,此种挖矿机制,比单独挖XMR和Tari的利润高出50%以上。
Source:qubic.org
1.2.Qubic 51% 攻击可信度存疑
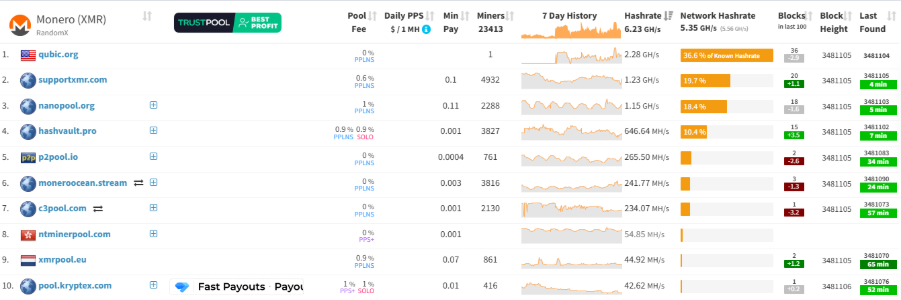
尽管Qubic称已对Monero实现了“51% 攻击”,但这一表述遭到社区质疑。根据研究机构 RIAT的公开数据,其峰值算力仅约 2.6 GH/s,而同期 Monero 全网算力在 6.25 GH/s 左右。换言之,Qubic 的算力占比不到 42%,与真正意义上的51%攻击存在显著差距。进一步的数据也佐证了这一判断,CoinWarz数据显示,事发当天,Monero 全网曾达到 6.77 GH/s 的峰值;而MiningPoolStats当日监测值为约 5.21 GH/s。这进一步说明Qubic 的算力峰值属瞬时波动,并非稳态控制。据MiningPoolStats数据,目前Qubic 矿池的算力约为每秒2.16GH/s,算力占比为35.3%。数据差异表明其控制能力存在不稳定性,且缺乏持续性认定。
Source:miningpoolstats
尽管多数控制存疑, Monero的网络安全也并未受到实际性的影响,但Qubic的算力扰动在短期内冲击了市场。Kraken因网络完整性风险暂停 XMR入金,在恢复后将确认门槛提高至 720 区块,并保留再次暂停的权利。这表明即便非真正的 51% 攻击,只要计算操控存在可能,交易安全链条就会提前承压,流动性与信心同步受到挑战。
二. Dogecoin成为下一个潜在攻击目标
2.1 Dogecoin成为下一个潜在的攻击对象
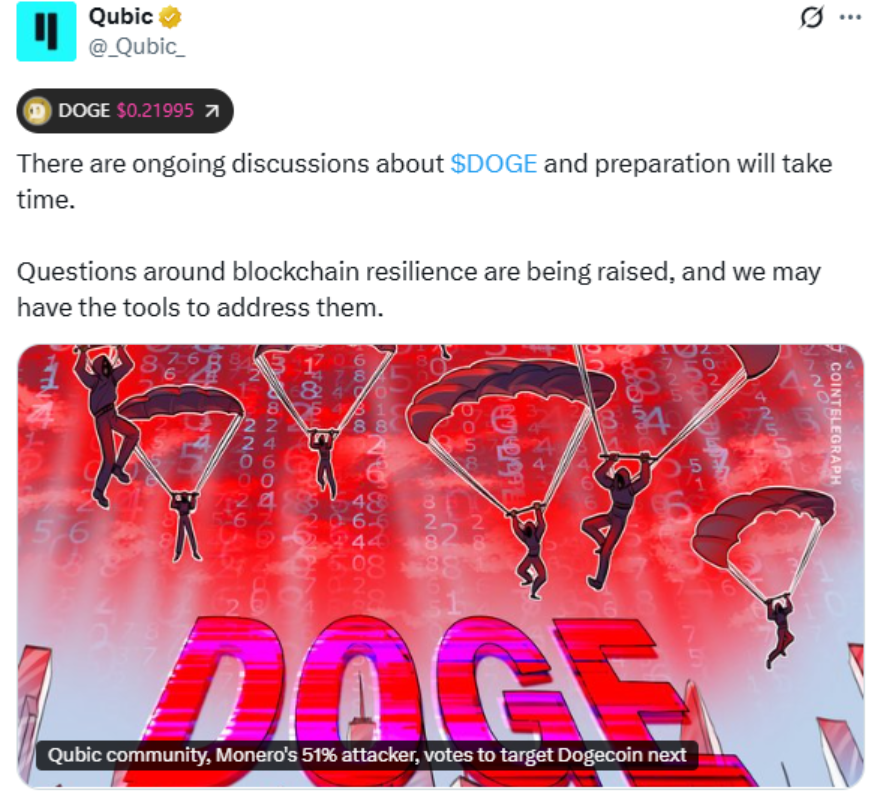
Monero之后,Qubic又将Dogecoin作为下一个潜在的攻击目标。近日,Qubic 的社区发起了一次新的投票,决定下一步可能发动 51% 攻击的目标。最终结果显示,Dogecoin获得超过300张投票,明显高于 Kaspa 与 Zcash 等候选对象。此次投票引发了市场的关注,它意味着Qubic的攻击焦点已经从隐私币 Monero,转移到了一个市值更高、用户基础更广的主流 Meme币。
Qubic之所以受到市场关注,在于它在 Monero 攻击中展示了新型经济激励模型。这并非传统意义上黑客行为,而是借助经济诱因来“租用”算力,从而重塑 PoW 的安全假设。目前这一模式有可能被投射到 Dogecoin,也放大了市场的不安。比较有趣的是,Qubic社区在投票后又称对 Dogecoin是进行挖矿而非“攻击”。从目前 Qubic 官方的表态来看,社区普遍将此次事件解读为带有营销意味的操作,而非单纯的技术性攻击。
Source:@_Qubic_
2.2.Qubic攻击Dogecoin 能否实现
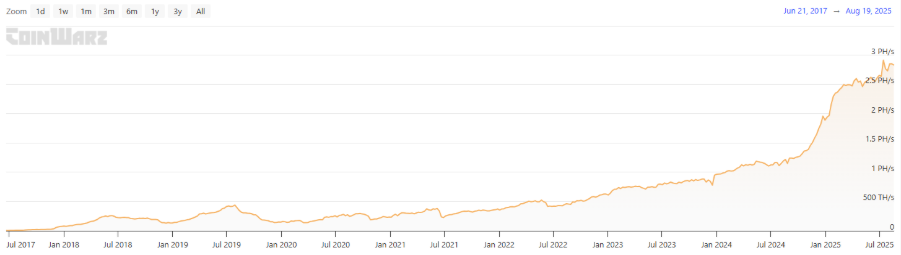
需要注意的是,Qubic对Monero也是采用先挖矿,后“攻击”的方式。因此,社区猜测Qubic或许未来也会对Dogecoin进行“攻击”。它能否实现呢?要理解风险,需要先审视 Dogecoin 的算力规模。据CoinWarz 数据,目前Dogecoin全网算力约为 2.69 PH/s,历史高点曾达 7.68 PH/s,这显示出矿工在硬件与电力方面的投入规模。按照网络机制,Dogecoin 平均每分钟出块一次,每块固定奖励 10,000 DOGE,因此全网每天新增供给约1,440万枚 DOGE;以当前价格约 0.21 美元计算,Dogecoin每日安全预算约为 300 万美元。相比之下,Monero 在尾部排放阶段每日新增仅 432 枚 XMR,对应的安全预算约11万美元,远低于 Dogecoin。这一差距表明,在相同条件下,若Qubic企图对Dogecoin发起 51% 攻击,攻击 Dogecoin 在资金与技术门槛上要远高于 Monero。
Source:coinwarz
Qubic的策略并非直接投入庞大资金,而是通过补贴模式吸引算力临时迁移。如果短期内足够多的矿工被 QUBIC 激励离开其他链而转向 Dogecoin,仍可能对出块稳定性造成冲击。即便无法真正实现“双花”,也可能导致区块延迟增加、孤块率上升,从而干扰网络正常运行。也可以理解为,Qubic的攻击不一定要“成功”,只要制造混乱就足以打击市场信心。
三.从Qubic事件看AI 算力下PoW的新博弈
3.1.矿工的流动性与忠诚困境
传统的 PoW 共识依赖于算力即安全的逻辑,即算力越高,攻击网络的成本越大,形成稳固的护城河。然而,Qubic 事件暴露了新的现实,算力并非长期锁定在某一条链上,而是一种可以快速转移、租用甚至投机的资源。当算力具备高度流动性时,它的属性更像资本市场中的流动资金,随时会涌向收益更高的领域。
这种算力流动性直接改变了矿工与网络之间的关系。过去矿工的激励主要来自区块奖励和手续费,与链之间形成了长期绑定。而在 Qubic模式下,矿工的收益来源被重新定义。这让矿工逐渐转变为算力套利者,而不是某条链的长期守护者。
更深远的影响在于 PoW 网络的安全性将不再取决于算力规模本身,而是取决于算力的稳定性。一旦算力能够随时被更高出价者买走,网络的攻击成本就不再是静态的绝对数,而是与外部市场的波动高度相关。结果是,PoW 不再是牢固的安全基石,而变成了受制于外部市场动态的临时防御,安全边界可能随时被突破。
3.2.AI 算力时代下PoW的新博弈
在 AI 算力需求持续高涨的背景下,PoW 网络的安全性被重新定义。传统模式下,算力只在链内循环,安全预算完全依赖区块奖励与手续费。而Qubic模式下,证明了算力也可以被引导到链外。对矿工而言,算力会自然流向汇报最高的市场。这意味着 PoW 的安全预算不再是链内的静态成本,而是与全球算力市场挂钩,甚至可能在 AI 算力价格飙升时出现安全闪崩。
这种环境下,PoW 很可能只是 AI 公链短期的过渡方案。单纯依靠 PoW 维系安全的模式,在长期算力外流的背景下难以维持。未来或有更多类似项目转向 PoS 或混合共识机制。是否能够平稳完成共识机制的迁移,或将成为判断 AI+PoW 公链长期竞争力的重要因素。
与此同时,外部安全绑定正成为 PoW 与 AI 结合公链更具可行性的路径。比如通过安全租赁市场,类似 EigenLayer 的再质押机制,将以太坊的质押资本外包给 AI 公链使用,为其提供更稳定、抗攻击的安全预算。这种方式下,它不再依赖自有算力规模,而是通过绑定成熟网络的长期安全来对冲算力流动性风险,这可能成为 AI 公链突破 PoW 局限的重要方向。
参考链接:
3.https://www.coinwarz.com/mining/dogecoin/hashrate-daily-chart
3.https://riat.at/qubic-attack-on-xmr-monero-no-51-attack-proven
4.https://qubic.org/pr/qubic-mines-monero
5. https://rfc.tari.com/RFCD-0130_Mining
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




