导语
关于反女巫的讨论,从最早的Uniswap到近期的Celestia空投几乎随处可见,在可预见的未来也将持续作为一个长期叙事存在,也许会被链上信誉相关的DIDs、DeFi、SocialFi、GameFi和其他叙事反复提及。然而,在Web3发展历史上,不同文本语境所指代的反女巫(Anti Sybil)概念似乎有些模糊、比较零散、令人困惑。这篇文章尝试将“反女巫”当做参照点,对其发展阶段及生长出来的新叙事、应用场景及涌现的各类解决方案进行概述和梳理。希望本文的视角对关注前述相关议题的朋友也能有所启示或帮助。
相较于一周一FOMO的热点变化,在Web3,女巫攻击(Sybil Attack)其实并不是多么新潮的概念;同时也非常新手友好,基本上是入圈1周左右的小白就有机会碰到、然后主动查询资料去了解和掌握的术语。写这篇研报有三方面的驱动因素:一是前段时间在看DIDs和社交图谱赛道,觉得“站在当下看未来”的方式可能对一些项目共性、核心及差异的把握有点困难,但往前追溯一个历史阶段来观察思考当前的叙事走向,反而会觉得更加清晰和有趣;二是相比之前几轮的空投项目方,Celestia的反女巫规则显然又升级了;三是不久前被一位朋友的灵魂拷问问倒了:“为什么Web2没有解决的女巫问题,到Web3还没解决?”
一、当我们谈论女巫攻击时,到底指的是什么?
1. 经典概念回顾
○反女巫(Anti Sybil)、又叫猎巫、反女巫攻击。女巫攻击一般指的是一个真人控制多个虚假身份以便重复领取生态建设者所提供激励收益的违规行为,是Web2“反作弊”、“反欺诈”概念在Web3的延伸和拓展。简单来说就是一个人伪装成若干个用户,瞒过项目方多次“薅羊毛”。更容易被我们察觉到的关联现象是层出不穷的“撸毛工作室”。
○据坊间流传,女巫攻击之所以叫女巫攻击,是有一部女主角拥有十几种人格的电影叫《女巫》,觉得用来代指一个人控制多个虚假身份非常形象。
○Web2时代的女巫攻击:滴滴曾经被司机跑空单骗过补贴、让你看广告赚佣金的视频平台其实在花着品牌方的广告预算做虚假的用户点击数据、明星粉丝为了危机公关而控评的水军,这些都是Web2时代的女巫攻击。
2. 用户需求还是反用户需求?
•代入用户或社区生态参与者视角,首先要想清楚的一个前提是:社区生态对反女巫的诉求是否真的足够坚固?需要承认,在当前阶段,反女巫并非用户的直接需求,更多是应用场景项目方的需求。甚至可以说,羊毛党们可能贡献了早期大量的TVL。以空投场景为例,用户其实有很强的动机成为女巫,只是在与项目方设置的奖惩规则斗智斗勇的过程中进行了利弊权衡,大多数具有女巫潜在风险的用户最终退一步成为了空投猎人。
•对于项目方来说,未发放代币给真实用户有两个不难想象的后果:营销拉新成本翻倍&巨大的抛压。
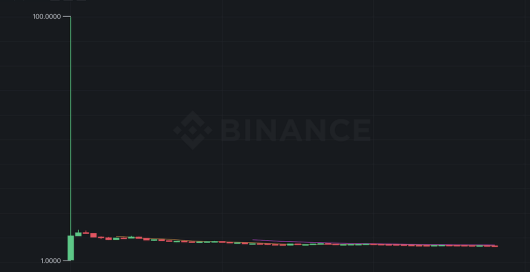
○举个例子:Aptos并未制定反女巫措施,空投消息一出,推特和社区中都有羊毛党晒几百个账户去申请测试网的截图,所以平均而言,项目方实际花费了几十倍的单位成本来获得一个真实的新用户。二是,从币安的交易走势来看,Aptos社区并未能承接住巨大的抛压,上线后一根针瞬间拉到 100 美元,随后就直接回到 10 美元附近,然后又一路下跌到 6 美元左右。有研究发现,流入交易所的代币中约有40%来自女巫地址。所以,提前获悉女巫地址比例对项目代币价格波动的预测也很有帮助。
○我们可以做一个简单的博弈分析理解项目方的反女巫举措对真实用户可能产生的连带影响:假设Alice是一个真实用户,只有一个用于做交互的钱包地址;Bob是一个女巫,控制了N个虚假账户,额外投入单位成本为F。空投前需要用户做任务、刷积分、付gas费等时间、精力、金钱投入,设为X, 项目方设定的空投标准为Y,单个账户的空投收益为Z,女巫攻击净收益简记为N*(aZ-bX-cY-dF)。通常来说,项目方会选择提高X、Y或降低Z来减少女巫攻击的ROI。不过,当项目方针对Bob的反女巫措施不够精准或者过于严苛时,可能连带着真实用户Alice的空投收益(aZ-bX-cY)也大幅下降甚至是负值。这也能解释为什么有的空投收到了很多社区赞誉,有的却导致了大量不满。
○目前“反女巫”和“薅羊毛”双方博弈通常有两种平衡状态,有机会实现正和博弈而非通常认为的零和博弈:
▪(1)默认轻微程度的撸毛行为。即默许只使用1-3个精品钱包获取空投的空投猎人。但是会严厉打击女巫行为,即拥有上百个钱包,大多数使用脚本或指纹浏览器,偶尔手动操作的用户。
▪(2)共同缔造“虚假”的繁荣。一方面,从项目方的角度来说,撸毛行为是项目链上活跃数据的重要组成部分,并且可以在早期阶段找出项目的各种 Bug,推进产品体验上的优化,相当于帮着做了压力测试,而绝大多数项目方也需要羊毛党贡献数据来提高估值或上线 CEX。从羊毛党的立场来看,也可以在未来收到代币空投,因此是双赢局面。
二、我们距离成熟的反女巫解决方案,进度条推到哪了?
要充分理解这个问题,先要意识到反女巫其实有三层叙事结构。然后我们会发现早在空投和羊毛党盛行之前,女巫攻击的场景和解决方案就已经存在了,后来出现的一些新叙事和讨论其实也是反女巫的延续。
1. 反女巫的三层叙事结构:应用场景层、协议共识层和验证检测层
反女巫相关的赛道主要分为应用场景、协议共识与识别检测三层。应用场景层决定反女巫的价值目标,协议共识层决定反女巫的制度规则,验证检测层决定反女巫的技术效率。
1.1 应用场景层:女巫在哪出没?
挖矿
这里的「挖矿」取PoW共识机制下的狭义。
•价值目标:维持成比例的验证算力供给与主链控制权。工作量证明(Proof of Work, PoW)共识机制下,掌握了多数算力的攻击者可以在区块链网络中进行欺诈性操作。女巫的目标可能是发起51%攻击来创建新主链,然后通过撤销、逆转或者不确认旧主链的交易记录,在新主链上实现双花(双重支付)套利。
•相关解决方案:通常是靠堆高区块链网络规模来做自然防御,女巫攻击一般发生在小链,大链所需要消耗的算力、硬件资源太高,女巫攻击的投入产出效益(ROI)十分低下,无利可图自然会降低女巫攻击的发生频率和安全威胁。从这层意义上来说,头部公链(例如BTC)自然已经比其他基于PoW的小链更具备低成本防御女巫攻击的基础优势;其他相关概念:去中心化分布式算力。
投票
•价值目标:维持成比例的质押率与投票权。权益证明(Proof of Stake, PoS)共识机制下,女巫的表现形式是通过购买治理代币来干预投票。投票权或决策权通常与用户持有的代币数量相关,因此通过女巫攻击获得大量代币的攻击者可能不成比例地投票给某个不合理的提案,继而操纵投票结果。这可能导致对特定提案的“贿赂效率”被人为地提高或降低,项目中的资源分配向某一特定群体的利益倾斜。简单来说,巨鲸通过购买大量的治理代币,分别存入看上去毫无关联的多个钱包中,就有机会获得超过51%的投票权从而主导投票结果。
•相关解决方案:首先,与PoW共识机制类似,女巫攻击者不能仅通过注册新钱包地址来发起攻击,而是需要投入成本购买大量治理代币,因此大链比小链更容易抵御低成本的女巫攻击。其二,人格证明(PoP)共识机制可以解决这个问题。核心理念是确保每个参与者在网络中只拥有一个身份或投票权。与传统的区块链共识机制如权益证明或工作证明不同,PoP着重于个人身份的独一性,而不是基于经济资源(如币龄、代币持有量或计算能力)的权重。
空投
•价值目标:将代币发放给真实的早期贡献用户,以维持成比例的新增用户与营销成本。空投是项目方营销拉新常用的用户增长工具,是目前反女巫行动的主阵地。如前文所述,未发放代币给真实用户,对于项目方来说有两个不难想象的后果:营销拉新成本翻倍以及巨大的抛压。
•主要存在两种空投类型:(1)Push 空投:一般指代币或 NFT 通过全额投放出现在用户钱包;(2)Pull 空投:用户主动领取奖励,包括 Uniswap、ENS、1INCH 和 Cow Swap等等。Push 空投容易被用作诈骗手段,所以绝大多数项目方的空投采取Pull模式。
•相关解决方案:声誉评分或身份证明(Gitcoin Passport、DegenScore、Otterspace 、Trusta Labs);生物信息验证(Humanode、Worldcoin);KYC、SBT、Poap、Proof of human等DIDs方案。
捐赠
•价值目标:维持成比例的公共物品评分和捐赠金额。例如,公共物品的二次方筹款(Quadratic Funding)是一种平衡捐赠激励以及去中心化之间矛盾的配捐机制,虽然二次方筹款降低了单笔大额捐赠对配捐匹配池中公共物品评分的影响,初步地提供了平衡捐赠激励和去中心化之间矛盾的算法设计,但非常容易遭遇女巫攻击。原因是,相比于一个账户,注册多个账户可以总量更少的资金投入影响配捐款的分配。并且,即便项目审核、捐赠者认证和数据回溯会降低女巫攻击的成功率,但仍然存在「女巫投毒」的可能性:
○女巫投毒:攻击者使用女巫账户为竞争对手或排行榜前列的项目进行小额捐赠,以使该项目被数据分析团队判定为「女巫」,从而让该项目无法获得配捐。这一方面打击了竞争对手,另一方面被取消的配捐将回到匹配池,从而使攻击者自己的项目获得更多的配捐金额。一旦这样的攻击手法成立,女巫账户针对项目的勒索行为也会出现。
•相关解决方案:GitCoin Passport等声誉评分或身份证明方案。
全民基本收入(UBI)
•价值目标:将全民基本收入资金发放给组织中的真人成员,以维持成比例的组织成员福利领取和基金支出。全民基本收入(Universal Basic Income)又叫无条件基本收入(Unconditional Basic Income)。UBI并不是一个Web3原生议案,在挪威、美国、德国等欧美高福利国家,曾多次出现在有关国家治理与国民福利的议案中。通常是指没有条件、没有资格限制,不做资格审查、无需拥有工作,每个国民或社区成员皆可定期领取一定金额的货币。简单来说,UBI就是面向组织成员发放的无差别低保。
•解决方案:主要是基于生物信息识别技术的人格证明(Proof of Person, PoP)。例如,Worldcoin需要到线下站点进行Orb虹膜检测才能领取补助金(Worldcoin Grant),也是出于防止一个真人控制多个账号以免重复投放Grant。Worldcoin声称只存储虹膜信息不可逆的哈希值而非虹膜照片本身来鉴别用户身份(World ID)的唯一性,从而克服传统KYC的隐私安全问题。
•相关解决方案:Worldcoin的虹膜验证
小结
•虽然在不同应用场景的具体表现形式有所出入,但不难看出,反女巫的价值目标可归结为“项目方价值目标的维护成本和组织成员的个人收益成比例”的一项网络安全机制,它在表现层主要与阻止用户大量申请虚假账户相关。
•如果项目方在对抗女巫攻击方面不能向社区成员提供可信承诺和技术证明,长期存在的女巫攻击就会损害项目的安全性和公信力。老用户和潜在新用户可能会减少参与或完全避免投资该项目,从而可能爆发矿工流失、质押率下降、真实用户数高估、捐赠激励不足、全民基本收入滥发等一系列应用层的连锁问题。
1.2 协议共识层:为什么有的反女巫收到了很多社区赞誉,有的却导致了大量不满?
虽然创建一个新的钱包地址不需要任何成本,看上去女巫攻击很容易发生,但在协议共识层面上,已经存在了抵抗低成本女巫攻击的某些特征。例如PoW 机制要求每个节点为网络贡献算力以参与共识;PoS 机制则根据验证者投入的代币数量分配投票权。因此,用户没有办法仅通过创建新地址来增加影响力。然而,基本的共识机制只是增加了女巫攻击的成本,当女巫攻击收益远高于成本时,恶意行为者依然会选择发起攻击。因此,有很多共识机制层面的创新,例如人格证明机制(PoP)、委托权益证明(Delegated Proof of Stake, DPoS)、权益授权证明(Proof of Authority, PoA)等。也有开发具有内在防女巫攻击保护的分布式协议,如SumUp和DSybil等算法,这里不做具体展开。
此外,项目方通过影响女巫攻击ROI的规则措施也可能改变反女巫的效率。一般来说,不管在哪个应用场景,社区对反女巫举措的评价通常与该项目的资金池规模、代币分配公式和资格认定条件有关。
1.2.1 资金池规模
资金池规模,即项目可用于奖励和激励的资金量。因为资金池大小直接影响到每个参与者可能获得的回报。资金池较大时,社区成员可能普遍更加乐观,但与此同时被女巫攻击的潜在风险更大。
例如,OP的二次空投资金池仅占总代币供应量的 0.27%,相比于第一次空投的5%来说杯水车薪。因为资金池较小引发了社区的广泛争议。
1.2.2 代币分配公式
代币分配公式决定了参与者如何获得代币奖励。这包括如何计算每个参与者的贡献,以及基于这些贡献分配代币的规则。透明、公平的分配公式通常会受到社区的好评,因为它们确保了每个人的努力都得到了公正的回报。然而,如果分配公式复杂、不透明或有针对倾向性,可能会导致社区成员之间的不满和争议。
例如,OP的第二次空投分配注重治理,与此同时兼顾不参与治理的活跃用户。使用返还 GasFee 的方法使得不参与 Optimism 治理的“空投农民”在这次空投中无利可图。大部分的用户在这轮空投中都没有获得太好的利润,这也是导致这一轮空投没有产生财富效应的主要原因。大多数地址仅仅收到了小于50个$OP的空投激励,只有少部分地址拿到了上百个 $OP的空投激励。
1.2.3 资格认定条件
资格认定条件是确定谁有资格参与的标准。这些条件可能包括完成特定任务、与项目的多次互动,甚至是身份验证过程(如KYC)。如果资格条件太严格或过于繁琐,可能会阻止一些社区成员参与,从而导致不满。另一方面,如果条件过于宽松,可能无法有效防止滥用,从而削弱反女巫措施的效果。
例如,为了获得SEI的空投资格,用户不仅需要多次交互,做完五大任务,还需要多次填表,领取还需要 KYC ,复杂的流程和存在隐私信息暴露风险的做法引发了社区不满。
1.3 验证检测层:解决方案的技术路径异同和优劣对比
通过协议共识层来降低女巫攻击的投入产出比固然是一种“釜底抽薪”的好思路,但反女巫效果并不能保证“斩草除根”,而且项目方很难在这一层进行准确性的判定核验。因此,我们还需要一些验证检测女巫账户的激励机制或技术方案,例如社区侦探、身份凭证&人格证明(PoP)以及链上行为活动分析。值得注意的是,每一次识别出的历史女巫地址名单也会被新的项目方继承性采纳。
1.3.1 社区侦探
•Safe、HOP、CONNEXT、Optimism鼓励社区侦探进行女巫举报,将抗女巫的责任转移给整个社区。尽管初衷是好的,Report to earn也是一种很新颖的用户激励方式,但这种做法引发了社区争议。例如,CONNEXT被报告的女巫账户甚至威胁要对其他钱包进行投毒,一旦这可能会将社区的抗女巫努力付之一炬。
•优点:一般来说,社区侦探情报具有及时性、民间高手各显神通。
•缺点:准确性欠佳、举报成功率低、容易遗漏女巫账户,或者引发女巫的报复式投毒。
1.3.2 身份凭证&人格证明(Proof of Personhood)
身份凭证&人格证明方向的解决方案有很多,通常涉及去中心化身份(DIDs)的若干概念,例如灵魂绑定代币(SBT)、可验证证书(VC)和POAP(Proof of Attendance Protocol)等。
1.灵魂绑定代币(Soulbound Tokens, SBT):
•SBT 是一种特殊类型的非同质化代币(NFT),它代表个人身份、属性或成就。与普通的 NFT 不同,SBT 不能被交易或转让,因为它们与持有者的“灵魂”(即个人身份)绑定。它们用于在数字世界中表达不可转移的属性,如教育资格、工作经历或社区信誉。
•优点:
○个人化与不可转移性:SBT 是与个人身份紧密绑定的,不能转移或交易,这增加了其在代表个人身份和资质时的准确性。
○灵活性与扩展性:可以根据需要创建各种类型的 SBT,用于不同的验证目的。
•缺点:
○隐私问题:与个人紧密相关的 SBT 可能暴露过多个人信息。
○撤销与更改的困难:一旦发出,SBT 可能难以撤销或修改,这在信息需要更新时可能成问题。
2.可验证凭证(Verifiable Credentials, VC)
•VCs 是一种数字证书,用于证明持有者的某些属性或资格。这些证书可以由各种机构或个人发出,并可以用来验证身份、资格、会员资格或其他任何可证实的信息。VCs 的关键特点是它们可以在去中心化的环境中使用,而无需依赖于单一的发行机构。
•优点:
○更好的隐私控制:VC 允许持有者选择他们想要分享的信息,增强了隐私保护。
○广泛的适用性:VC 可以用于多种场景,从身份验证到资格证明等。
○易于管理和更新:与 SBT 相比,VC 更容易被更新或撤销。
•缺点:
○中心化:VC 的可信赖程度高度依赖于发行方的声誉和可靠性。
3.POAP(Proof of Attendance Protocol)
•POAP是一种数字收藏品系统,用于验证个人参与或出席某个特定事件或活动的记录。这一概念在加密货币和区块链社区中越来越受欢迎,特别是作为对参与各类虚拟和现实世界活动的确认。
•优点:
○唯一性和不可篡改性:POAP作为基于区块链的NFT,具有唯一性和不可篡改性。这有助于确保每个POAP代表一个真实的参与事件,降低了伪造或重复身份的可能性。
○验证参与度:POAP可以用作验证用户参与某项活动的凭证。这种方法在投票或其他需要验证真实参与者的场景中特别有用。
○增加攻击成本:要成功执行女巫攻击,攻击者需要获取大量POAP,这可能涉及实际参与多个事件或找到其他方法来获取这些POAP。这增加了执行攻击的成本和复杂性。
○透明性和可追踪性:由于POAP记录在区块链上,因此它们的发行和转移是透明和可追踪的,这有助于识别和防止恶意行为。
•缺点:
○成本高:在某些区块链上,如ETH,创建和转移NFT可能需要支付昂贵的交易费用。
其他身份凭证类解决方案:KYC、生物信息识别、OP的链上证明AttestationStation等等。
1.3.3 链上行为活动分析
AI-ML算法可以通过监测链上行为活动模式来抵抗女巫攻击,然而这类技术对于女巫检测的困难性源于真实女巫账户的标签缺失,从而无法通过构建一个合适的训练集进行监督学习,并外推至测试集以检查算法判定的准确性。例如,算法不仅可能会遗漏一部分女巫账户,也可能会误将一个真人账户判别为女巫账户,导致空投名单有偏,引发社区成员的不满。因此,目前而言的反女巫AI-ML算法主要是基于链上数据做时间序列分析和图挖掘,如分析批量转移和交互、行为序列模式挖掘以及资产转移图,再通过人工核实的方式逐步积累真实的女巫标签。
•批量转移和交互:通过分析不同地址之间的交易行为来检测女巫账户。包括识别可能表明女巫行为的批量转账和交互模式。
•行为序列模式挖掘:挖掘数据以找到可能表明女巫攻击的连续行为模式。
•资产转移图(ATG):使用资产转移图挖掘来分析实体间的资产流动,帮助识别潜在的女巫攻击。
譬如,Celestia空投采用了Trusta Labs的反女巫方案,分两阶段的链上行为分析锁定女巫账户。
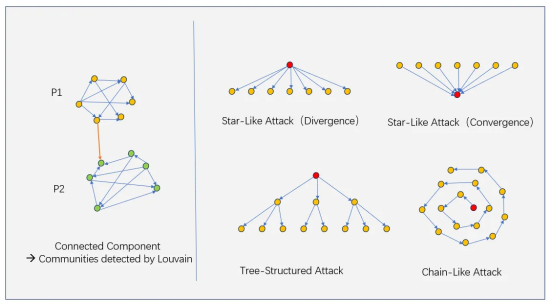
•第 1 阶段:ATG上的社区检测。使用 Louvain 和 K-Core 等社区检测算法分析资产转移图 (ATG),以检测密集连接和可疑的女巫群组。
○星状发散攻击:群组内地址从相同源地址接收转账;
○星状汇聚攻击:群组内地址向相同目标地址发送资金;
○树状攻击:群组内的资金转账关系形成树状拓扑;
○链式攻击:地址之间序列化转账,形成一个链式结构;
•第 2 阶段:基于行为相似性的K-Means优化。计算每个地址的用户配置文件和活动。K-means 通过筛选不同的地址来优化聚类,以减少第 1 阶段的误报。
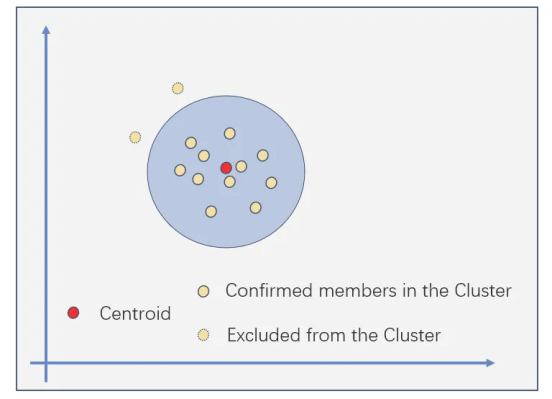
图源:Trusta空投抗女巫框架介绍:一种基于AI和机器学习的可靠性方案
•优点:
1.AI-ML保护用户隐私。用户不需要提供个人生物信息和他在Web2中的一系列身份认证。人格证明则要求身份确认,牺牲了用户匿名性。
2.AI-ML全面分析大量的链上数据以减少脆弱性,让方案更加可靠。而身份验证是可以被以被利用和伪造的,这使得人格证明的方案容易收到攻击。
3.AI-ML的方案本质上无需任何人的许可,任何人都可以分析相同的公开数据。
4.由于AI-ML分析的透明性,女巫判别可以被公开以获得多方校验。
•缺点:
1.真实女巫标签的缺失使得可采用的AI-ML算法在复杂度、准确性和召回率受限。在2022年,没有任何已经标记为女巫的基准数据集可用于训练监督模型。在静态的女巫/非女巫数据上进行训练,模型的精确度和召回率可能是脆弱的。由于单一数据集不能涵盖所有的女巫模式,召回率是有上限的。此外,被误分类的用户无法提供反馈,这阻碍了精度的进一步提升。
2.大部分女巫的行为与普通用户并没有显著差异、识别困难,目前来说最合适的检测手段是聚类算法。随着真实女巫标签的积累确认,未来可以采取更成熟的深度学习算法框架来优化检测手段。
2. 从反女巫延伸出了哪些新叙事?
虽然当下的反女巫叙事听上去更像是由项目方的需求驱动,"反用户"的特性使其在哲学价值层面的合理性存疑。但我们完全有理由相信它在未来的叙事上扩展出更坚固的生态价值。
2.1 DeFi:信用评分&信用评级
延伸叙事方向之一是DeFi与信用借贷。此前,区块链信用借贷几乎是空白,因为缺乏一个链上信用评估体系,导致现在绝大部分的借贷只能使用超额抵押机制,劝退了大量不愿意超额借贷的资金流动性,可吸纳的新增质押率空间还很大,而信用评估体系的构建需要建立在排除大量虚假账户的工作基础之上。
•相关项目:Gitcoin Passport、TrustaGo的MEDIA分数等
2.2 SocialFi :社交图谱
另一个生长出来的叙事方向是SocialFi与社交图谱。在基于社交图谱和链上信誉的内容创作生态中(例如SocialFi和GameFi)。一旦社交影响力能被合理定价,女巫可能通过创建大量假账户来操纵声誉分数、评论或社交影响力来盈利,这很类似于Web2社交媒体上刷评的水军和机器人。
•相关项目:基于智能合约的社交图谱Lens Protocol和CyberConnect、基于网络的社交图谱Farcaster和Deso、社交交易协议Friend.tech和内容创作者经济相关的Bodhi。
三、展望:“反女巫”和“薅羊毛”博弈的终局形态可能是什么?
•应用场景的扩展:链上信用&社交图谱
“反用户”的项目方需求向用户直接需求过渡。虽然当下的反女巫叙事听上去更像是由项目方的需求驱动,"反用户"的特性使其在哲学价值层面的合理性存疑,但我们完全有理由相信它在未来的叙事上很可能扩展出更坚固的生态价值。延伸叙事方向之一是DeFi与信用借贷。此前,区块链信用借贷几乎是空白,因为我们缺乏一个链上信用评估体系,导致现在绝大部分的借贷只能使用超额抵押机制,而信用评估体系的构建需要建立在排除虚假账户的工作基础之上。另一个生长出来的叙事方向是SocialFi与社交图谱。在基于社交图谱和链上信誉的内容创作生态中(例如SocialFi和GameFi)。一旦社交影响力能被合理定价,女巫攻击可能通过创建大量假账户来操纵声誉分数、评论或社交影响力来实现可观的盈利,这很类似于Web2社交媒体上刷评的水军和机器人。因此,在DeFi、SocialFi和GameFi场景,我们都有可能看到从反女巫延伸出来的、用户需求驱动的应用场景。
•地址信用评分体系的多元化:集成多重检测方案
集成多重检测方案以权衡隐私性和准确性之间的关系。通过绑定身份凭证或提供生物信息固然能更有效地区分真人和虚假账户、可以借助许多较为成熟的Web2解决方案,但也伴随着更高的用户信息收集要求。反之,基于AI-ML算法的解决方案具有大规模检测、可多方验证、隐私保护等优势,但也面临无法事先或实时拦截的问题。因此,集成多重检测方案是更优解。
•用户拥有一个主地址和多个副地址,通过钱包管理
需要权衡声誉绑定和身份丢失之间的关系。未来也许每个真实用户都只有一个主地址能记忆、标识一个可持续积累信誉的身份(与DIDs的部分语义重合),并且用户只能通过主地址接受空投等项目方所提供的激励收益。但是,TA可以关联多个细分场景的局部地址用于和应用项目交互,防范因主地址丢失或被盗所承担的系统性风险。
结语
通过以上的梳理,我们已经基本可以回答本篇提出的一些疑问。首先,Web3的反女巫是Web2的反欺诈、反作弊的概念延伸,但是兼具一些Web3原生的特征,例如在空投叙事大范围推广之后,女巫攻击的收益激励才有了显著提升。因为具有“项目方-羊毛党”之间博弈的鲜明特征,猎巫行动的验证检测措施也从温和迅速转向了严厉和复杂,目前技术手段仍然在不断升级。其次,虽然当下的反女巫叙事听上去更像是由项目方的需求驱动,"反用户"的特性使其在哲学价值层面的合理性存疑,但我们完全有理由相信它在Web3未来的叙事上很可能扩展出更坚固的生态价值,继而完成用户需求驱动的价值证明,例如DeFi的信用借贷、SocialFi和GameFi的社交图谱等等。目前,反女巫的技术方案正在从萌芽期向成熟期过渡,终局形态可能是用户拥有一个主地址和多个副地址,通过钱包管理;主地址与一个集成多重检测方案的信用评分体系挂钩,多个副地址用于垂直应用场景的交互和账号找回验证。
最后,希望当读者以后再看到一个项目讲反女巫和链上信誉相关的叙事的时候,能清楚地知道他们所说的“女巫”具体是在试图使用虚假身份对哪一个价值场景发起攻击;项目方是在提出一种新的协议共识从源头降低女巫攻击的ROI,还是在讲攻击发生前的准入凭证或身份标识,抑或是在讲攻击发生后的检测工具和手段?当然,相关的项目很可能会做不止一层。反女巫和薅羊毛的博弈也会一直持续,但很可能是一个正和博弈而非通常认为的零和博弈。具体来说,一级投资逻辑大致是应用价值前景>验证检测技术>协议共识创新。
参考资料
[1] https://medium.com/@trustalabs.ai/trustas-ai-and-machine-learning-framework-for-robust-sybil-resistance-in-airdrops-ba17059ec5b7
[2] https://passport.gitcoin.co/
[3] https://docs.lens.xyz/docs
[4] https://cyberconnect.me/
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




