How to Upgrade from "Protecting Assets" to "Protecting People": Institutional Design to Reduce the Feasibility of Coercive Behavior May Become a Key Proposition for Future Industry Development
Written by: CertiK
On February 2, Web3 security company CertiK released the "Skynet Ransom Attack Report," indicating that physical violence against cryptocurrency holders has evolved from extreme cases into a structural risk. As the security of crypto assets continues to strengthen, this method of bypassing technical defenses and directly targeting "people" is rapidly spreading.

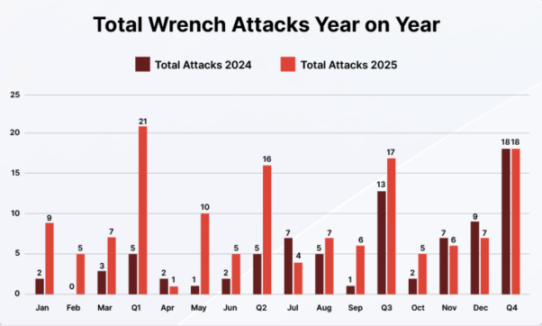
The report shows that in 2025, there were a total of 72 verified ransom attack incidents recorded globally, a 75% increase from 2024. The so-called "ransom attack" refers to attackers using physical means such as violence, intimidation, or kidnapping to force victims to hand over their private keys or passwords. These attacks do not rely on technical vulnerabilities but instead directly target the individuals behind the crypto assets.
Significant Increase in Violence, Europe Becomes a High-Risk Area
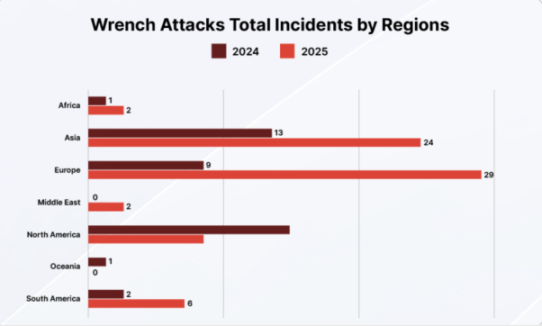
In terms of attack patterns, ransom attacks in 2025 show a clear trend of escalating violence. The report notes that kidnapping remains the primary attack method, with 25 incidents occurring throughout the year; direct personal attacks increased by 250% year-on-year, becoming one of the most concerning changes.
Geographically, Europe has become the highest-risk region globally for the first time. In 2025, Europe accounted for over 40% of known incidents worldwide, with France recording the highest number of attacks, surpassing the United States. CertiK pointed out in the report that this change does not mean that risks in North America have disappeared, but rather reflects that such crimes are spreading to regions with more complex legal environments and higher costs for cross-border cooperation.
Losses Exceed $40 Million, True Scale May Be Severely Underestimated
From a financial impact perspective, confirmed losses related to ransom attacks in 2025 exceeded $40.9 million, a 44% year-on-year increase. However, the report warns that due to victims' low willingness to report incidents, fear of retaliation, and the involvement of some assets in tax evasion or gray areas, this figure is only "the tip of the iceberg."
By comparing attack patterns, the report finds that ransom attacks in 2025 have completely moved away from the early speculative and fragmented characteristics, entering a stage of professional and industrialized operation. Attackers often exist in the form of transnational criminal groups, typically preparing for weeks before an attack, analyzing target digital footprints using open-source intelligence (OSINT), identifying weak defense periods, and even deploying specialized equipment such as signal jammers and Faraday bags to cut off victims' contact with the outside world.
It is noteworthy that the targets of attackers are becoming more generalized. While industry executives and project founders remain high-value targets, attackers are now also beginning to target individuals with smaller holdings. Additionally, attackers are increasingly using "associated targets," applying psychological pressure by threatening the victims' spouses, children, or parents.
How to Respond to Personal Threats? Security Recommendations for Individuals and Institutions
As technical security standards continue to improve, "breaking systems" is becoming increasingly difficult, while "coercing individuals" is cheaper and more efficient. This paradox makes personal safety the weakest and most easily overlooked link in the current crypto ecosystem.
The report proposes a series of security recommendations for individuals and institutions: at the individual level, it is suggested to reduce coercion losses through "decoy wallets," geographically isolate the storage of mnemonic phrases, and remove encryption applications from daily devices to mitigate risks; at the institutional level, it emphasizes the adoption of multi-signature mechanisms, time-lock contracts, transaction friction mechanisms, and other technical measures, while also extending security training to family members and employees.
In the conclusion of the report, CertiK emphasizes that the situation in 2025 indicates that ransom attacks have become an independent crime type within the crypto ecosystem, and relying solely on the security of mnemonic phrases is no longer sufficient to address the risks. How to upgrade from "protecting assets" to "protecting people" and reduce the feasibility of coercive behavior through institutional design may become a key proposition for the future development of the industry.
Report link: https://indd.adobe.com/view/6399f4eb-e37c-485d-a225-a7a1fc68914f
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



