Author: Chainalysis
Translated by: Felix, PANews
In response to the attacks by North Korean hackers on the cryptocurrency industry over the years, Chainalysis focused on analyzing the attack patterns of North Korean hackers in its 2025 hacking report. Below are the details.
Key Points:
- North Korean hackers stole $2.02 billion worth of cryptocurrency in 2025, a 51% increase year-on-year. Although the number of attacks decreased, the total amount stolen has reached $6.75 billion.
- North Korean hackers stole more cryptocurrency with fewer attacks, often by inserting IT personnel into crypto services or using complex impersonation strategies targeting executives.
- North Korean hackers show a clear preference for Chinese money laundering services, cross-chain bridge services, and mixing protocols, with a laundering cycle of about 45 days following significant theft incidents.
- In 2025, incidents of personal wallet theft surged to 158,000, affecting 80,000 users, although the total value stolen ($713 million) decreased compared to 2024.
- Despite an increase in the total value locked (TVL) in DeFi, losses from hacking attacks remained low from 2024 to 2025, indicating that improvements in security measures are having a significant effect.
In 2025, the crypto ecosystem faced severe challenges again, with stolen funds continuing to rise. Analysis indicates that the patterns of crypto theft exhibit four key characteristics: North Korean hackers remain the primary source of threats; individual attacks on centralized services are becoming increasingly severe; incidents of personal wallet theft have surged; and there is an unexpected divergence in the trend of DeFi hacking attacks.
Overall Situation: Stolen Amount Exceeds $3.4 Billion in 2025
From January to early December 2025, the amount stolen in the crypto industry exceeded $3.4 billion, with the attack on Bybit in February alone accounting for $1.5 billion.
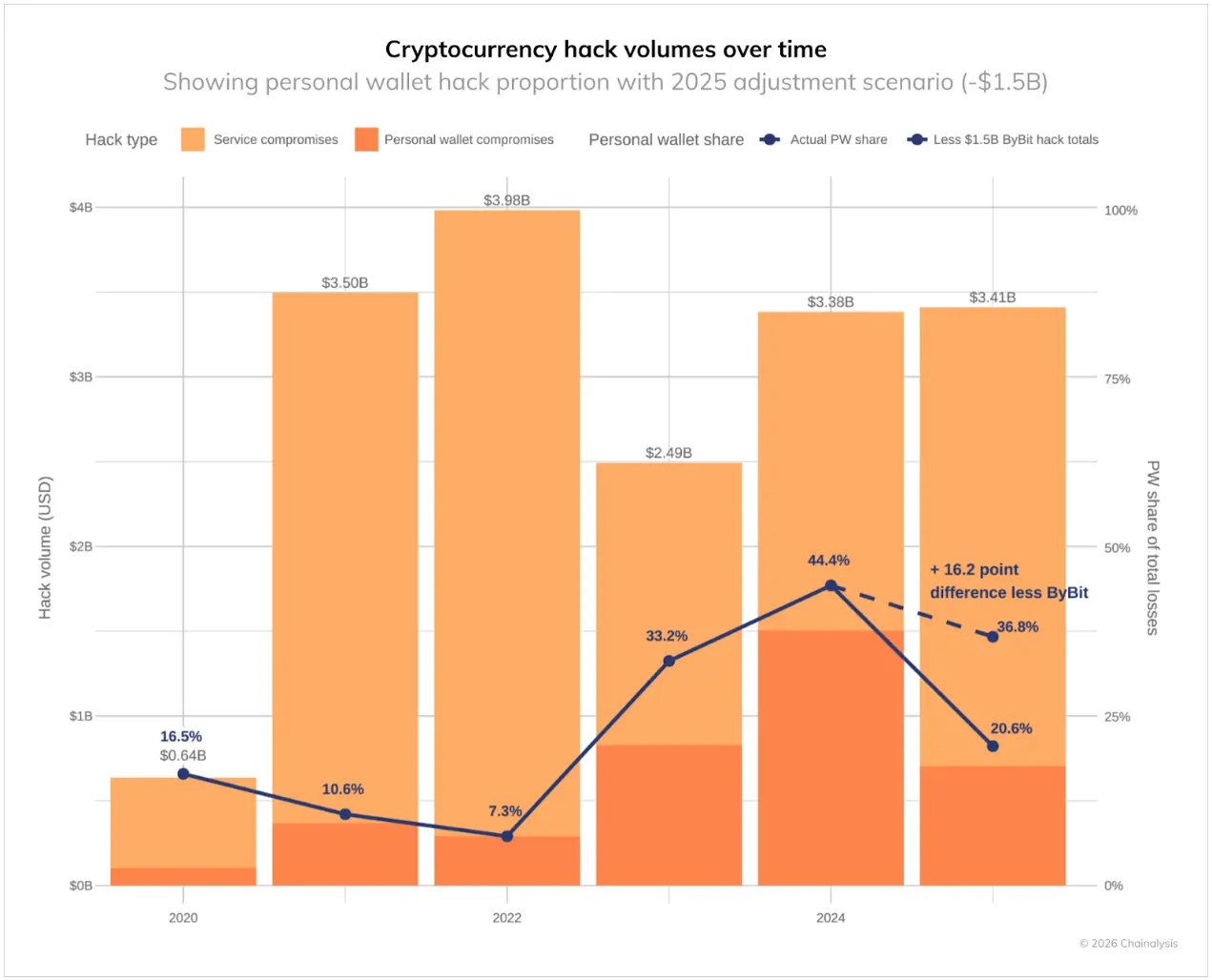
Data also reveals significant changes in these theft incidents. Incidents of personal wallet theft increased dramatically, rising from 7.3% of the total stolen value in 2022 to 44% in 2024. If not for the significant impact of the Bybit attack, this ratio in 2025 might have reached 37%.
Meanwhile, centralized services are suffering increasingly large losses due to complex attacks targeting private key infrastructure and signature processes. Despite these platforms having institutional resources and professional security teams, they remain vulnerable to threats that can bypass cold wallet controls. Although such intrusions are infrequent (as shown in the chart below), when they do occur, they result in massive amounts of stolen funds, with losses from such incidents accounting for 88% of total losses in the first quarter of 2025. Many attackers have developed methods to exploit third-party wallet integrations, luring signers into authorizing malicious transactions.
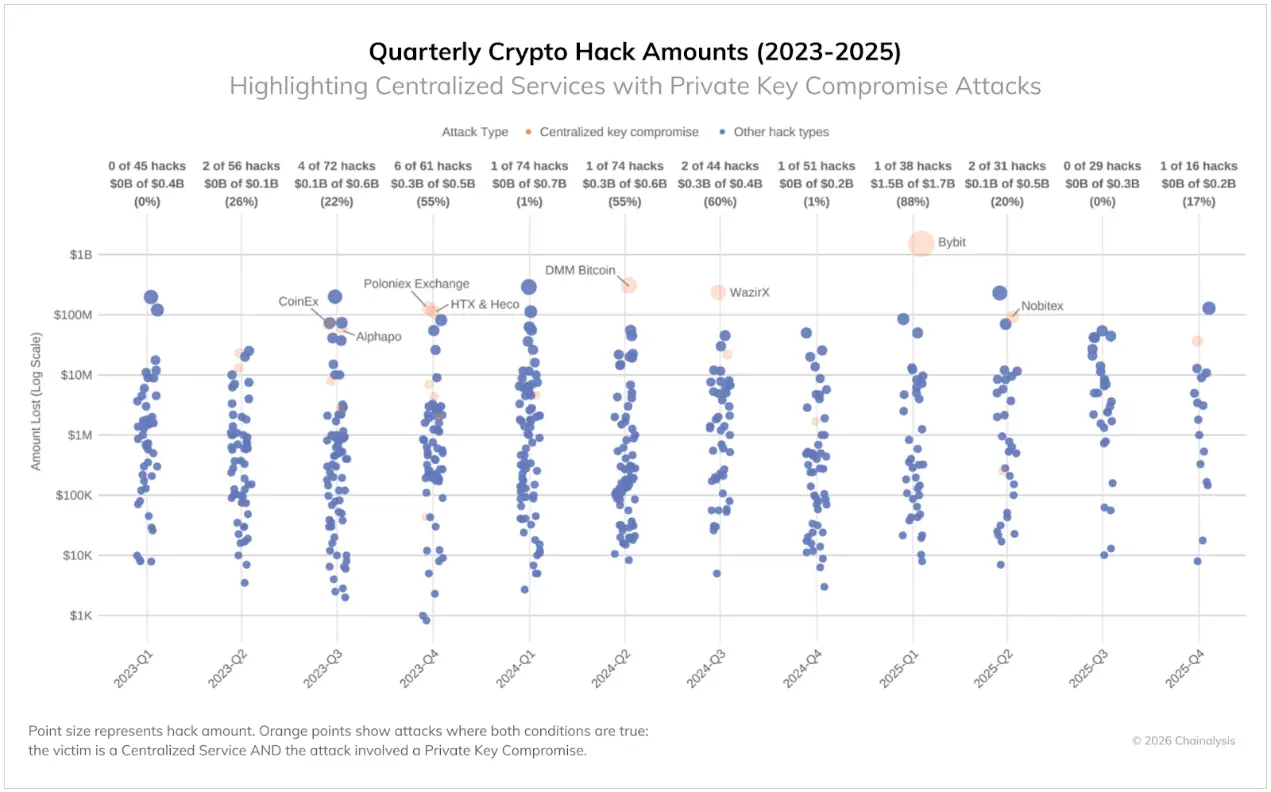
Although crypto security may have improved in certain areas, the high amount of stolen funds indicates that attackers are still able to succeed through various means.
The Top Three Hacking Attacks Account for 69% of Total Losses, with Extremes Reaching 1000 Times the Median
The incidents of stolen funds have historically been driven by extreme events, with most hacking attacks being relatively small in scale, but a few are massive. However, the situation in 2025 worsened: the ratio between the largest hacking attacks and the median of all events broke the 1000 times threshold for the first time. Now, the funds stolen in the largest attacks are 1000 times those stolen in ordinary events, even surpassing the peak of the 2021 bull market. These calculations are based on the dollar value of stolen funds at the time of theft.
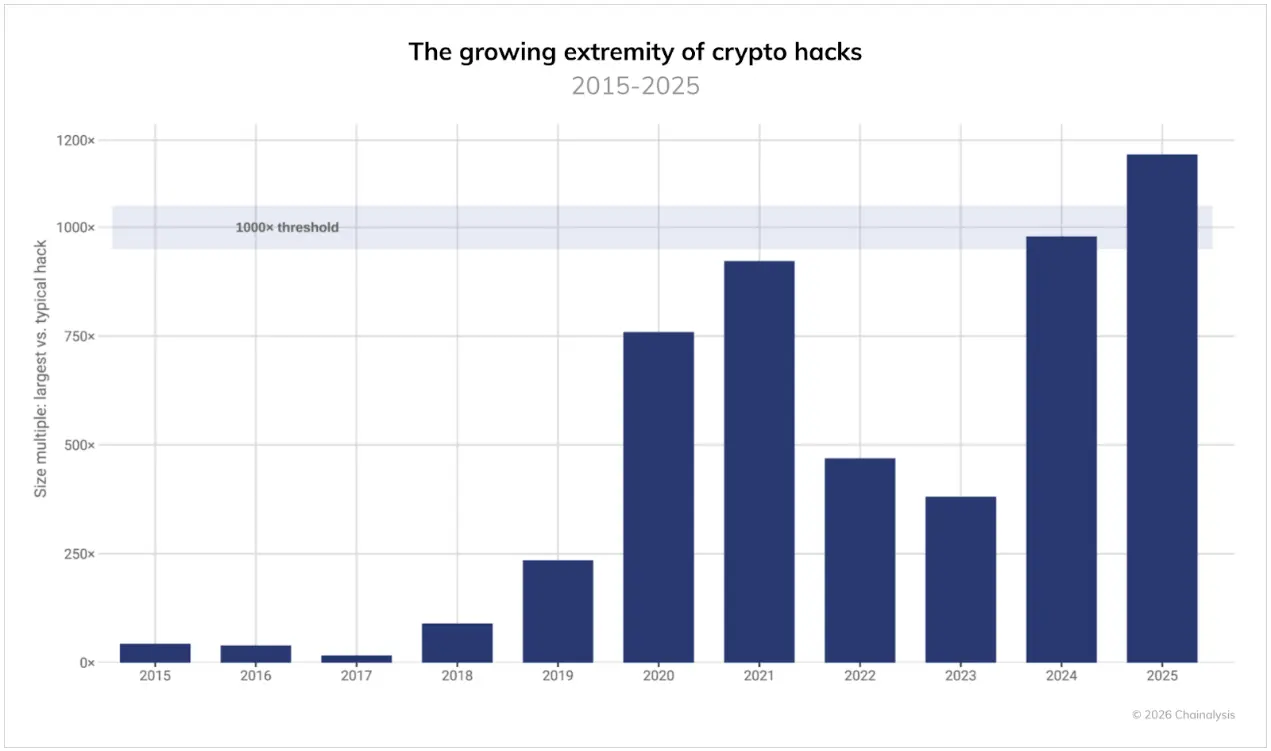
This widening gap leads to a high concentration of losses. The top three hacking attacks in 2025 accounted for 69% of all losses, with individual events having an exceptionally significant impact on the annual total losses. Although the frequency of attacks may fluctuate, and the median loss may increase with rising asset prices, the potential losses from individual major vulnerabilities are still rising at a faster pace.
Despite a Decrease in Confirmed Attack Incidents, North Korea Remains a Major Threat
Despite a significant decrease in attack frequency, North Korea remains the country posing the most serious threat to crypto security, with the cryptocurrency funds stolen in 2025 reaching a new high of at least $2.02 billion (an increase of $681 million from 2024), representing a 51% year-on-year growth. In terms of stolen amounts, this is the worst year on record for North Korean cryptocurrency thefts, with attacks initiated by North Korea accounting for 76% of all intrusion incidents, setting a historical high. Overall, the cumulative total of cryptocurrency stolen by North Korea is conservatively estimated to be $6.75 billion.
North Korean hackers are increasingly inserting IT personnel (one of their main attack methods) into crypto services to gain privileged access and carry out significant attacks. This year's record-breaking attack incidents may reflect North Korea's greater reliance on IT personnel infiltrating exchanges, custodians, and Web3 companies, which can expedite initial access and lateral movement, thereby creating conditions for large-scale theft.
However, recent hacker groups associated with North Korea have completely subverted this IT worker model. They no longer simply apply for positions and infiltrate as employees; instead, they increasingly impersonate recruiters from well-known Web3 and AI companies, meticulously orchestrating fake recruitment processes to ultimately obtain victims' login credentials, source code, and VPN or single sign-on (SSO) access from their current employers. At the executive level, similar social engineering tactics appear in the form of contact from fake strategic investors or acquirers, who use pitch meetings and pseudo-due diligence to probe sensitive system information and potential high-value infrastructure—this evolution is directly built on the foundation of North Korean IT worker fraud actions and focuses on strategically important AI and blockchain companies.
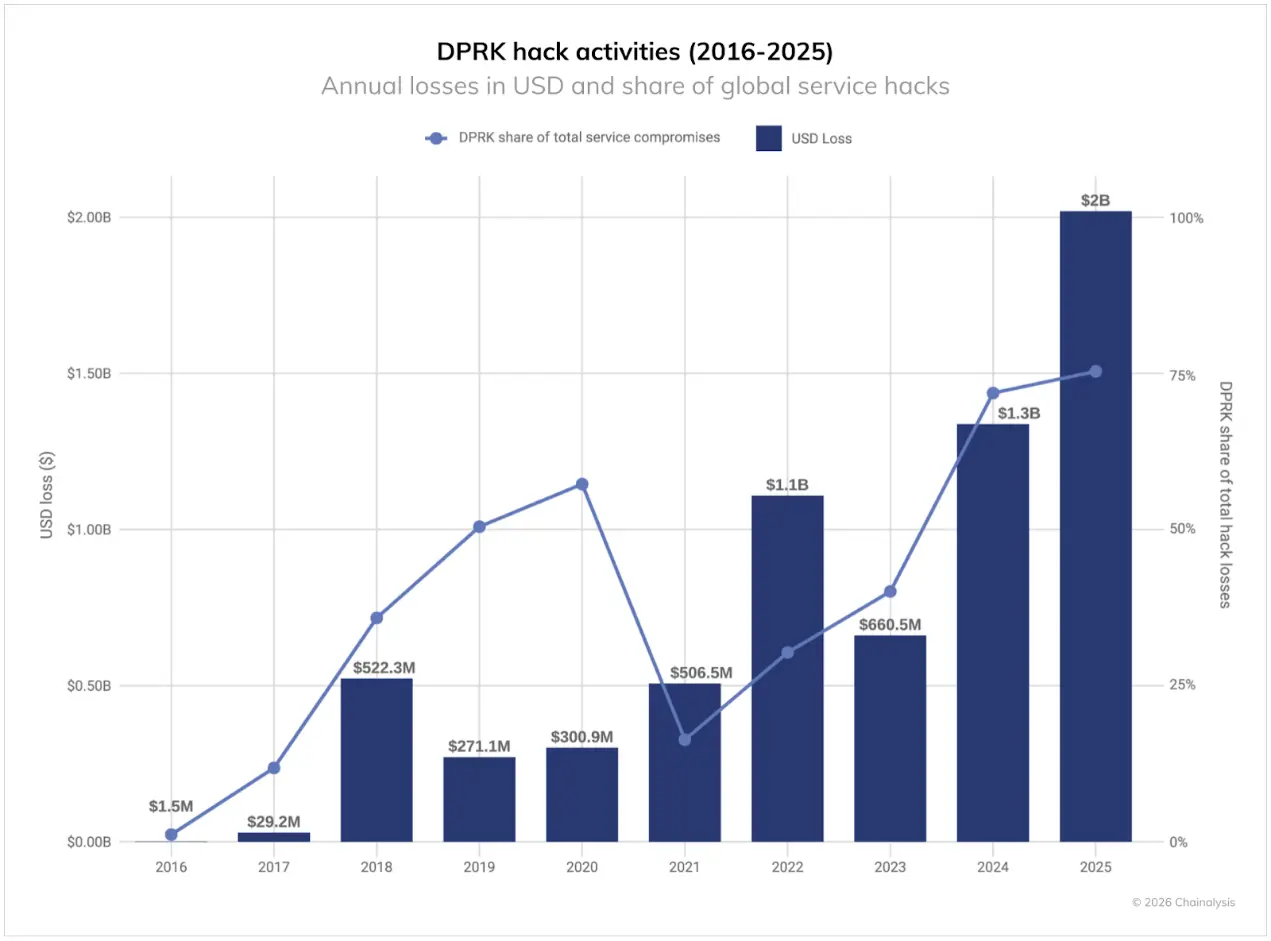
As seen in recent years, the value of cyberattacks continuously carried out by North Korea far exceeds that of other hackers. As shown in the chart below, from 2022 to 2025, North Korean hacking attacks occupy the highest value range, while non-North Korean hacking attacks are distributed more normally across all theft scales. This pattern further indicates that when North Korean hackers launch attacks, they target large services, aiming to create the maximum impact.
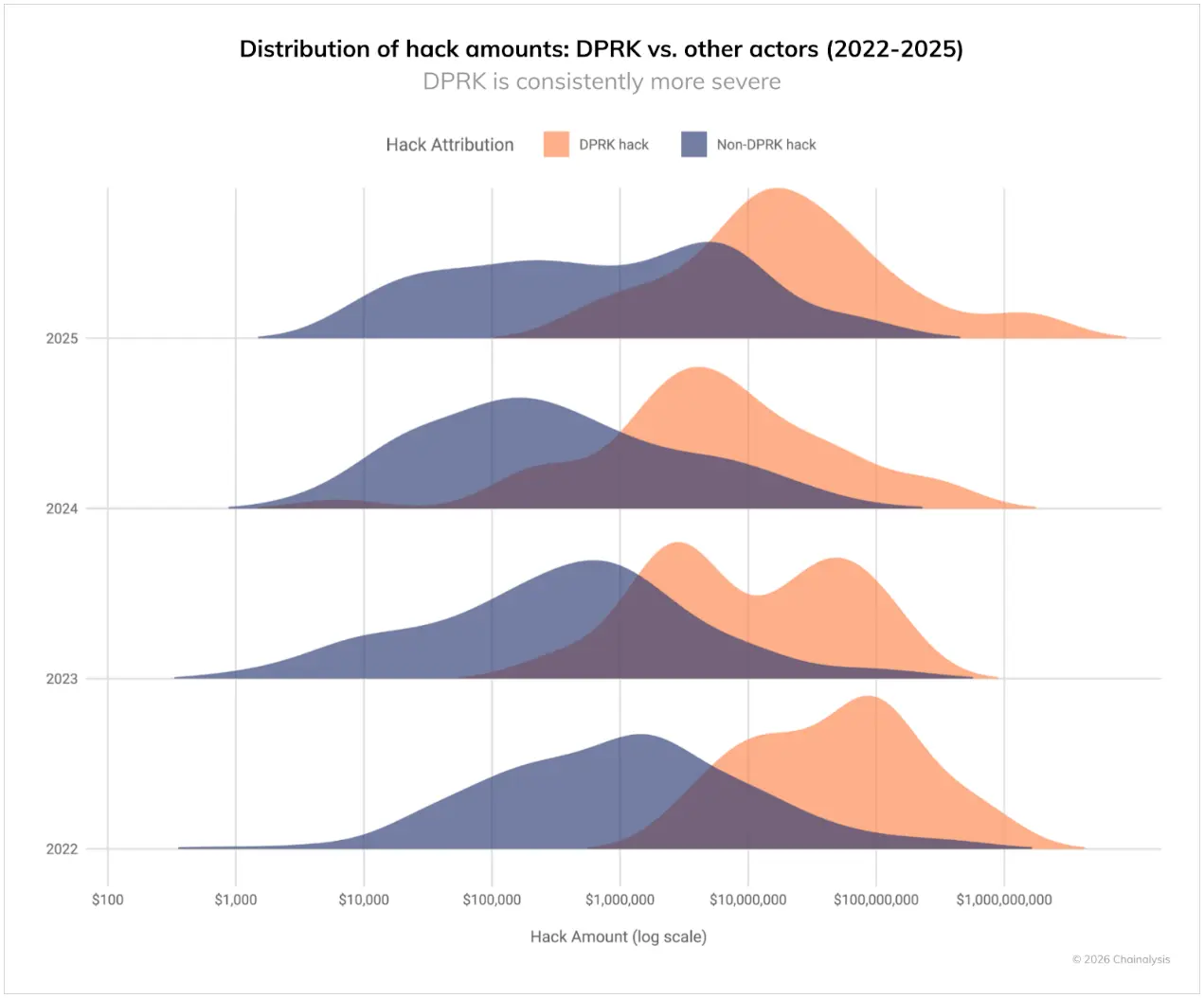
This year's record losses stem from a significant reduction in known incidents. This shift (fewer incidents but significantly increased losses) reflects the impact of the large-scale hacking attack on Bybit in February 2025.
North Korea's Unique Money Laundering Model
The influx of a large amount of stolen funds at the beginning of 2025 reveals how North Korean hackers launder cryptocurrency on a large scale. Their model is distinctly different from that of other cybercriminals and has evolved over time.
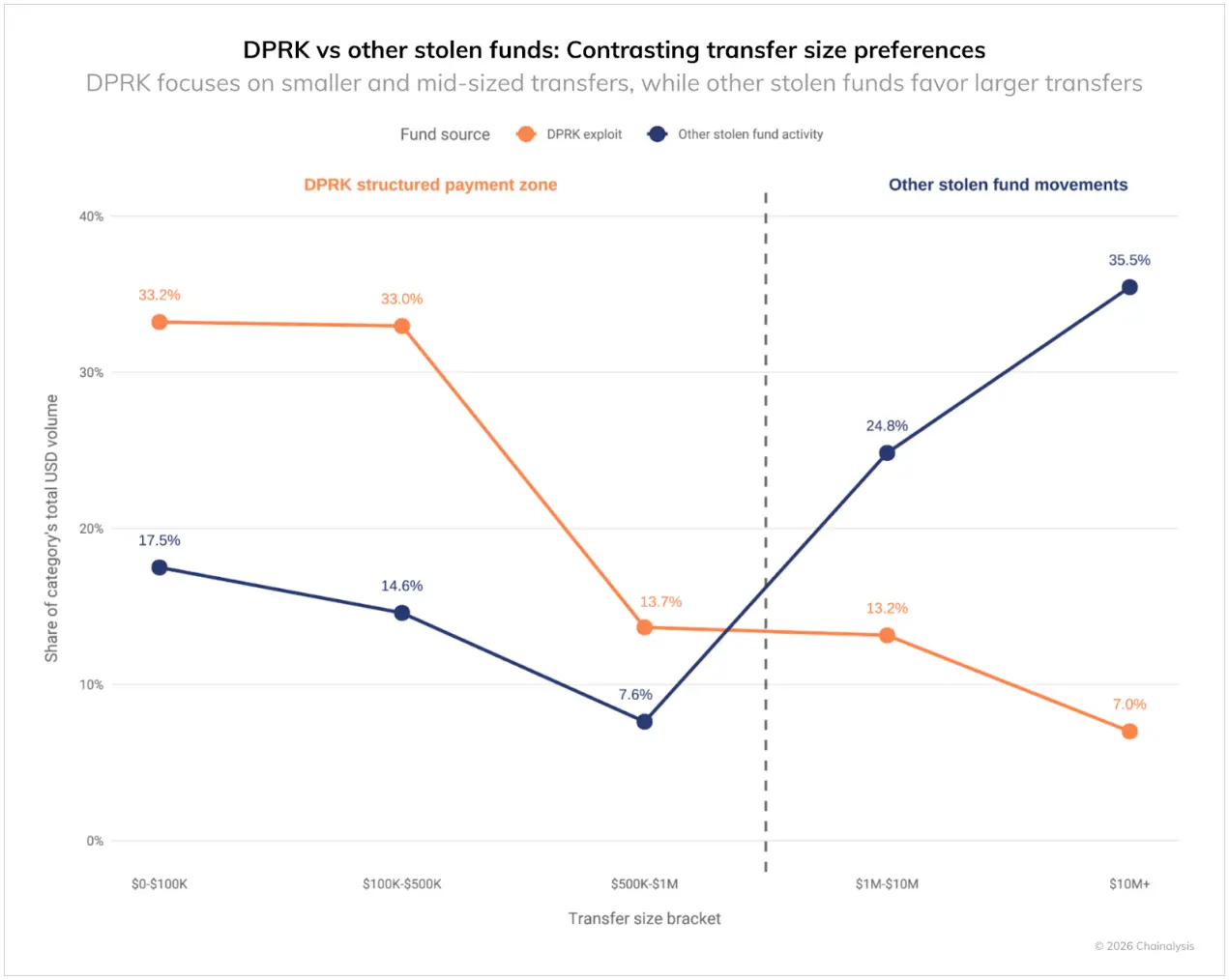
North Korea's money laundering activities exhibit a clear "tiered" pattern, with over 60% of transaction volume concentrated below $500,000. In contrast, over 60% of the funds transferred on-chain by other hackers are done in batches within the range of $1 million to $10 million. Although North Korea launders more money each time than other hackers, they break down on-chain transfers into smaller batches, highlighting the complexity of their laundering methods.
Compared to other hackers, North Korea shows clear preferences in certain laundering stages:
North Korean hackers tend to favor:
- Chinese fund transfer and guarantee services (+355% to over 1000%): This is the most distinctive feature, heavily relying on Chinese guarantee services and a network of money laundering operators that may have weaker compliance controls.
- Cross-chain bridge services (+97%): Highly reliant on cross-chain bridges to transfer assets between different blockchains, attempting to increase tracking difficulty.
- Mixing services (+100%): More frequent use of mixing services to attempt to obscure the flow of funds.
- Professional services like Huione (+356%): Strategically using specific services to assist their laundering activities.
Other hackers involved in money laundering tend to favor:
- Lending protocols (-80%): North Korea avoids using these DeFi services, showing limited integration with the broader DeFi ecosystem.
- No KYC exchanges (-75%): Surprisingly, other hackers use no KYC exchanges more than North Korea.
- P2P exchanges (-64%): North Korea shows limited interest in P2P platforms.
- CEX (-25%): Other hackers have more direct interactions with traditional exchange platforms.
- DEX (-42%): Other hackers are more inclined to use DEXs due to their high liquidity and strong anonymity.
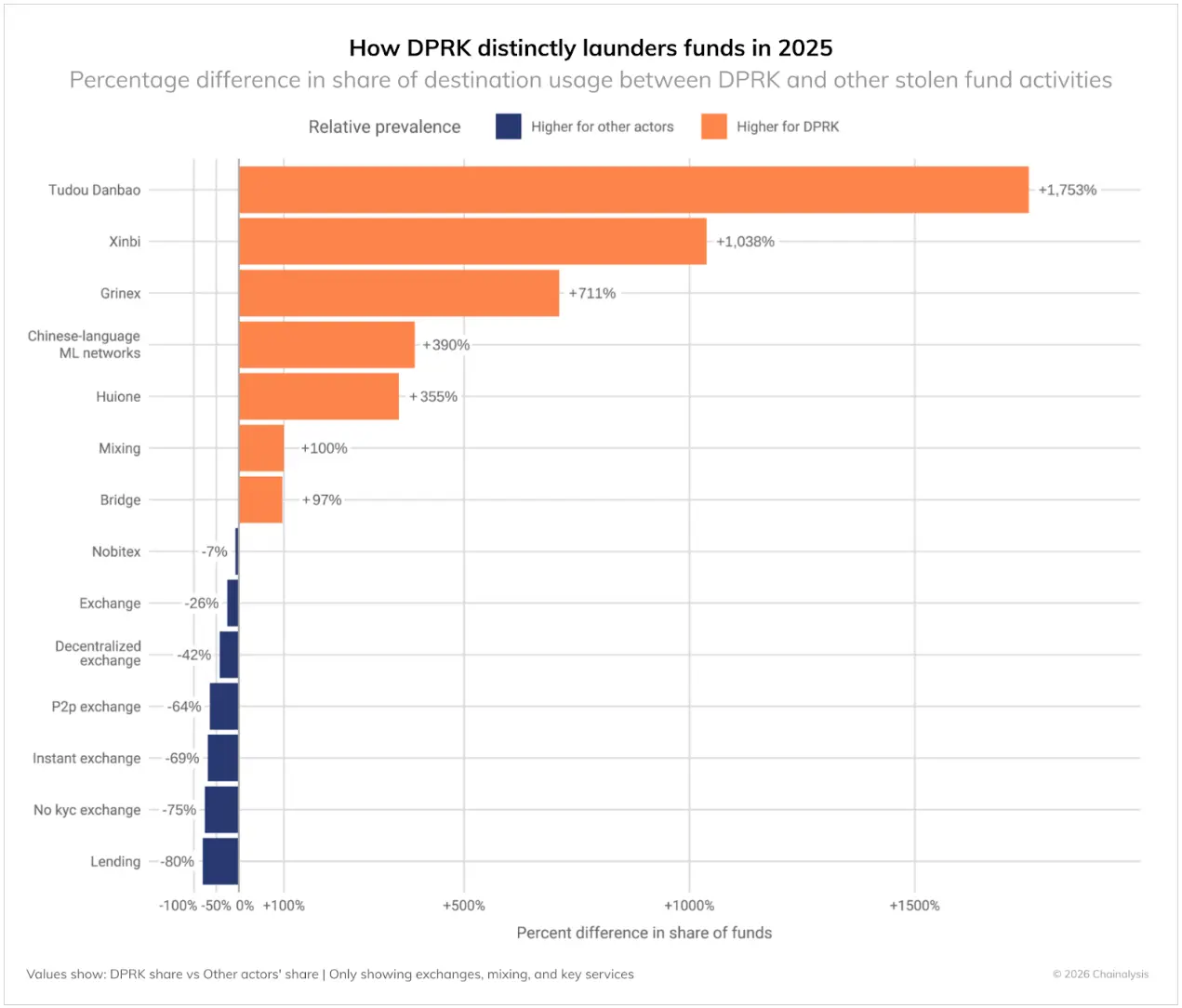
These patterns indicate that North Korea's operations are influenced by constraints and objectives different from those of non-state-sponsored cybercriminals. They heavily utilize specialized Chinese money laundering services and over-the-counter (OTC) traders, indicating a close connection between North Korean hackers and illegal actors in the Asia-Pacific region.
Timeline of Money Laundering of Stolen Funds After North Korean Hacking Attacks
Analysis of on-chain activities attributed to North Korean hacking incidents from 2022 to 2025 shows a consistent pattern in the flow of stolen funds within the crypto ecosystem. Following significant theft incidents, stolen funds follow a structured, multi-stage laundering path that lasts approximately 45 days:
Phase One: Immediate Layering (Days 0-5)
In the initial days following a hacking attack, a series of activities are observed to be exceptionally active, focusing on immediately transferring funds away from the stolen source:
- The flow of stolen funds in DeFi protocols increased the most (+370%), becoming a major entry point.
- The transaction volume of mixing services also saw a significant increase (+135-150%), forming the first layer of obfuscation.
- This phase represents an urgent "first step" action aimed at distancing from the initial theft.
Phase Two: Initial Integration (Days 6-10)
Entering the second week, the money laundering strategy shifts to services that help integrate funds into a broader ecosystem:
- Exchanges with fewer KYC restrictions (+37%) and CEXs (+32%) begin to receive fund flows.
- Second-layer mixing services (+76%) continue laundering activities at a lower intensity.
- Cross-chain bridging (e.g., XMRt, +141%) helps to disperse and obscure the flow of funds between blockchains.
- This phase is a critical transition period where funds begin to flow toward potential exit channels.
Phase Three: Long-Tail Integration (Days 20-45)
The final phase clearly leans toward services that can ultimately be exchanged for fiat or other assets:
- The use of exchanges without KYC (+82%) and guarantee services (e.g., Potato Single Treasure, +87%) significantly increases.
- Instant exchanges (+61%) and Chinese platforms (e.g., Huiwang, +45%) become the final exchange points.
- CEXs (+50%) also receive funds, indicating complex attempts to mix funds with legitimate money.
- Jurisdictions with less regulation, such as Chinese money laundering networks (+33%) and platforms like Grinex (+39%), complete this model.
This typical 45-day money laundering operation window provides critical intelligence for law enforcement and compliance teams. This pattern has persisted for years, indicating that North Korean hackers face operational constraints, possibly due to limited access to financial infrastructure and the need to coordinate with specific intermediaries.
Although these hackers do not always follow this exact timeline—some stolen funds may lie dormant for months or years—this pattern represents their typical on-chain behavior when actively laundering money. Additionally, it must be recognized that there may be blind spots in this analysis, as certain activities (such as private key transfers or over-the-counter cryptocurrency exchanges for fiat) will not be visible on-chain without corroborating intelligence.
Personal Wallet Theft: Increasing Threat to Individual Users
By analyzing on-chain patterns and reports from victims and industry partners, the severity of personal wallet theft can be understood, although the actual number of thefts may be much higher. The minimum estimate indicates that in 2025, the value loss from personal wallet theft accounted for 20% of total losses, down from 44% in 2024, suggesting changes in both scale and pattern. The total number of theft incidents in 2025 surged to 158,000, nearly tripling the 54,000 recorded in 2022. The number of victims increased from 40,000 in 2022 to at least 80,000 in 2025. This significant growth is likely due to the broader adoption of cryptocurrency. For example, one of the blockchains with the most active personal wallets, Solana, had a theft incident count far ahead (approximately 26,500 victims).
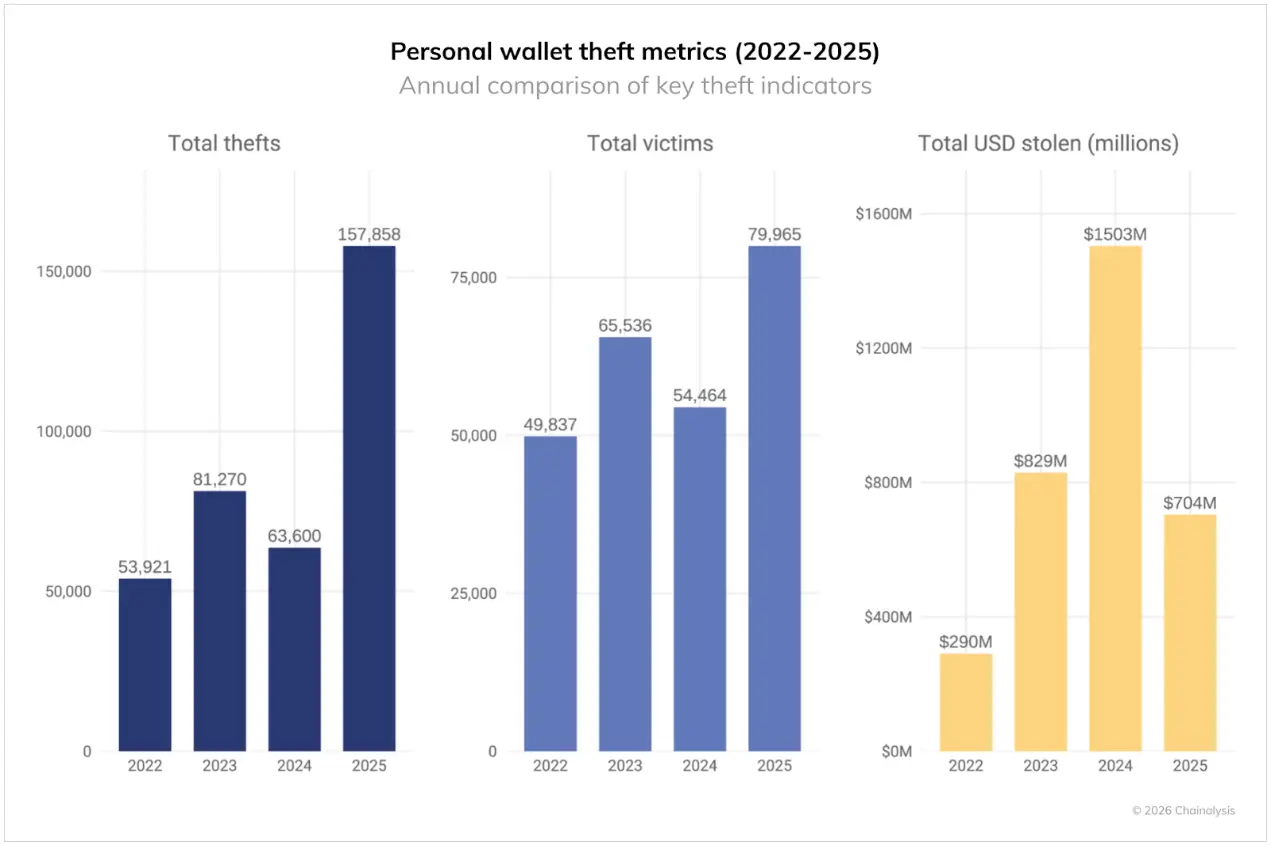
However, despite the increase in incidents and victims, the total dollar amount stolen from individual victims in 2025 decreased from a peak of $1.5 billion in 2024 to $713 million. This indicates that while the target user base has expanded, the amount stolen from each victim has decreased.
Data on specific networks provides more insight into which areas pose the greatest threat to crypto users. The following chart shows victim data adjusted for active personal wallets across various networks. Measured by the crime rate per 100,000 wallets in 2025, Ethereum and Tron had the highest theft rates. The large user base of Ethereum indicates a higher theft rate and number of victims, while Tron’s ranking shows that despite having fewer active wallets, its theft rate remains high. In contrast, although Base and Solana have large user bases, their victim rates are relatively low.
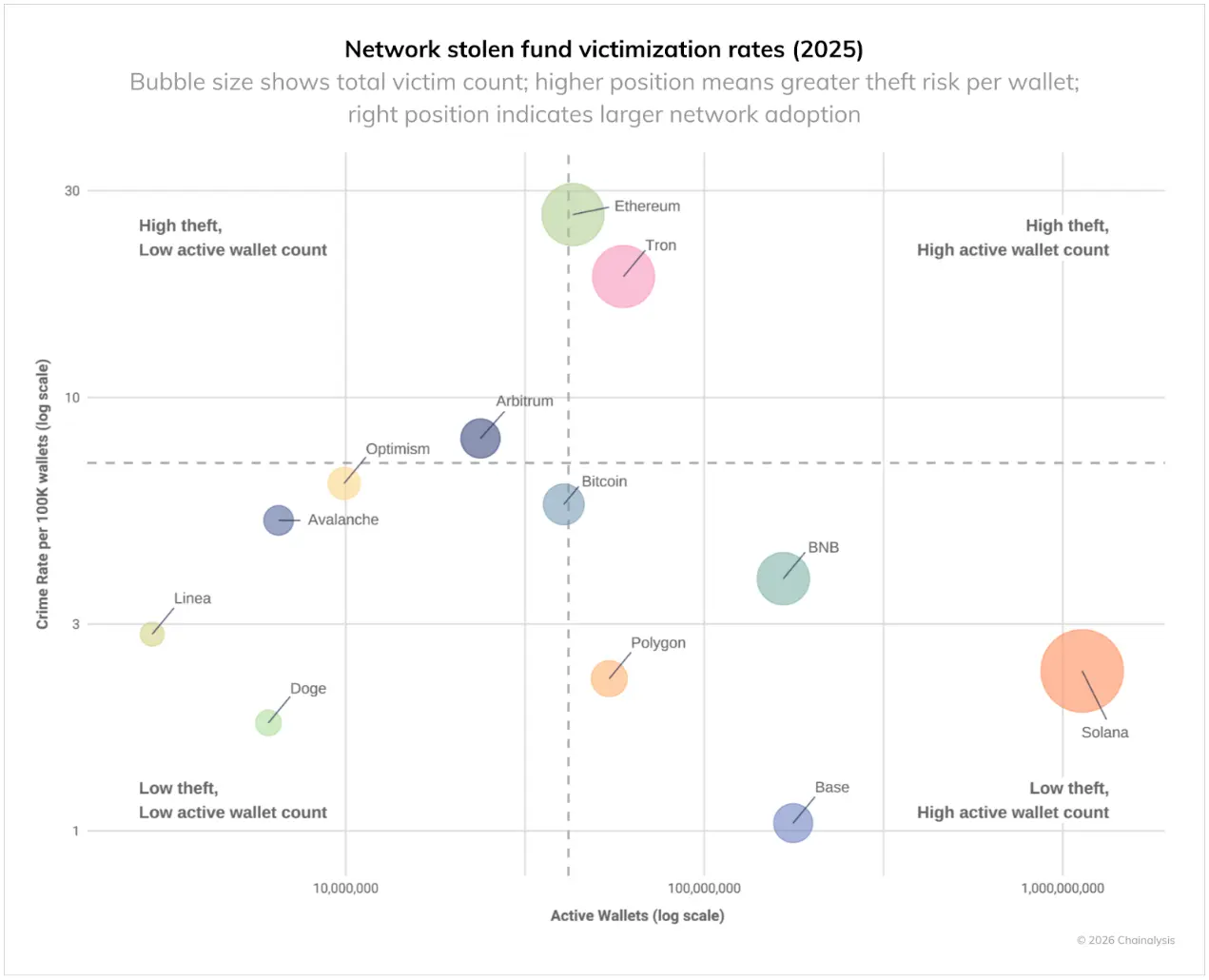
This indicates that the security risks of personal wallets in the crypto ecosystem are not equal. Even with similar technical architectures, different blockchains exhibit varying victim rates, suggesting that factors beyond technical aspects, such as user demographics, popular applications, and criminal infrastructure, play significant roles in determining theft rates.
DeFi Hacking Attacks: Diverging Patterns Indicate Market Shifts
The crime data in the DeFi sector for 2025 presents a unique pattern, significantly diverging from historical trends.
The data shows three distinctly different phases:
- Phase One (2020-2021): DeFi TVL and hacking attack losses grew in sync.
- Phase Two (2022-2023): Both metrics declined in tandem.
- Phase Three (2024-2025): TVL rebounded while hacking attack losses remained stable.
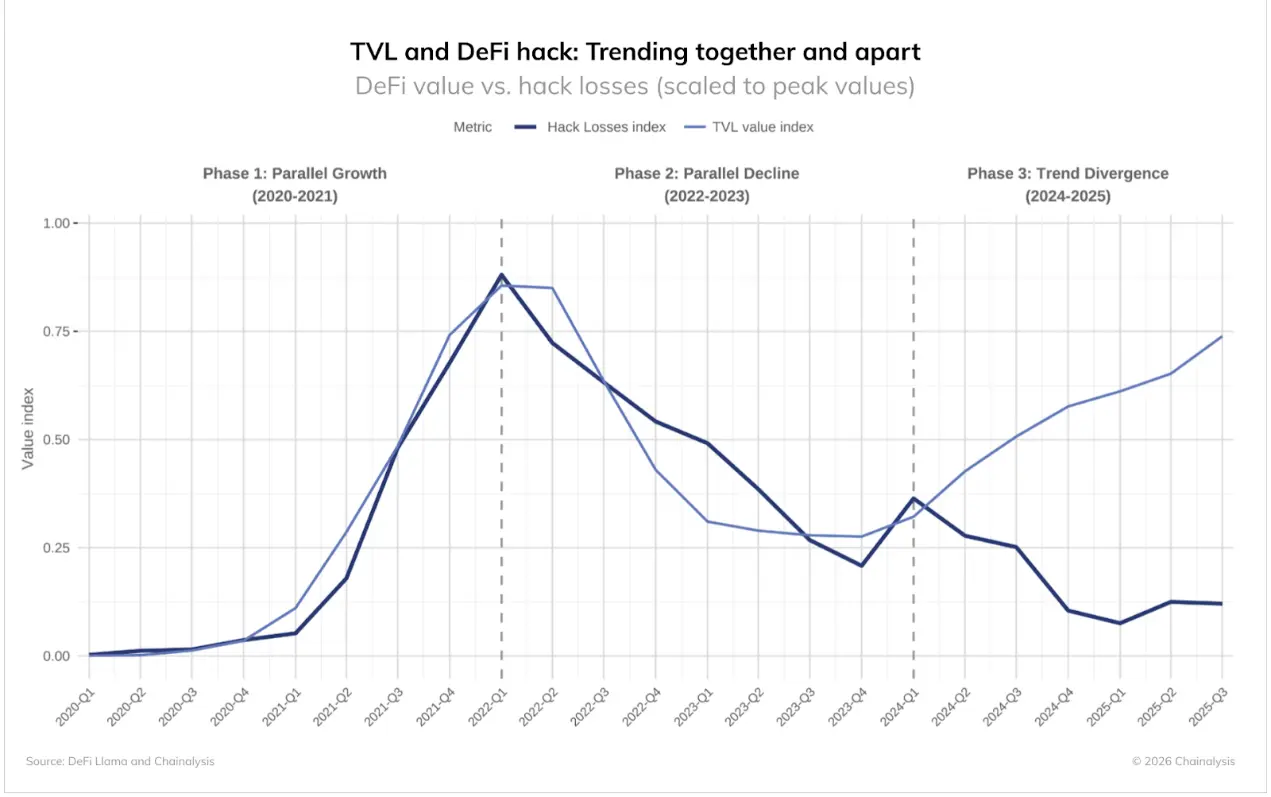
The first two phases follow an intuitive pattern: the greater the value at risk, the more value is available to steal, and the more intense the attacks on high-value protocols. As bank robber Willie Sutton famously said, "Because that's where the money is."
This makes the difference in the third phase even more pronounced. DeFi TVL has significantly rebounded from its low point in 2023, but the losses from hacking attacks have not increased accordingly. Despite billions flowing back into these protocols, DeFi hacking incidents have remained at low levels, representing a significant change.
Two factors may explain this difference:
- Enhanced Security: Despite the continuous growth of TVL, the hacking attack rate has continued to decline, indicating that DeFi protocols may be implementing more effective security measures than during the 2020-2021 period.
- Shift in Targets: The simultaneous increase in personal wallet theft and centralized service attack incidents suggests that attackers' attention may be shifting to other targets.
Case Study: Venus Protocol's Security Response
The Venus Protocol incident in September 2025 illustrates that improved security measures are yielding tangible results. At that time, attackers exploited a compromised Zoom client to gain system access and lured a user into granting them delegated access to an account worth $13 million, a situation that could have had catastrophic consequences. However, Venus had just enabled the Hexagate security monitoring platform a month prior.
The platform detected suspicious activity 18 hours before the attack occurred and immediately issued another alert as soon as the malicious transaction took place. Within 20 minutes, Venus paused its protocol, preventing any fund movement. This coordinated response demonstrates the evolution of DeFi security:
- Within 5 hours: Partial functionality restored after completing security checks.
- Within 7 hours: Forced liquidation of the attacker's wallet.
- Within 12 hours: All stolen funds recovered and services restored.
Notably, Venus passed a governance proposal to freeze $3 million in assets still controlled by the attacker; the attacker not only failed to profit but also incurred losses.
This incident indicates that DeFi security infrastructure has seen substantial improvements. The combination of proactive monitoring, rapid response capabilities, and decisive governance mechanisms has made the entire ecosystem more agile and resilient. Although attacks still occur, the ability to detect, respond to, and even reverse attacks represents a fundamental shift compared to the early DeFi era, where successful attacks often meant permanent losses.
Implications for 2026 and Beyond
The data from 2025 presents a complex picture of North Korea as the biggest threat to the cryptocurrency industry. The number of attacks launched by the country has decreased, but the destructiveness has significantly increased, indicating that their methods are becoming more sophisticated and patient. The impact of the Bybit incident on their annual activity pattern suggests that when North Korea successfully executes a major theft, it slows its operational tempo and focuses on laundering.
For the cryptocurrency industry, this evolution necessitates heightened vigilance toward high-value targets and improved recognition of North Korea's specific money laundering patterns. Their ongoing preference for certain types of services and transfer amounts provides opportunities for detection, distinguishing them from other criminals and aiding investigators in identifying their on-chain behavioral characteristics.
As North Korea continues to use cryptocurrency theft to fund national priorities and evade international sanctions, the crypto industry must recognize that North Korea's operational patterns differ fundamentally from those of typical cybercriminals. North Korea's record performance in 2025 (with known attacks decreasing by 74%) suggests that we may only be seeing the most apparent aspects of their activities. The challenge for 2026 will be how to detect and prevent these actions before North Korea launches another attack on the scale of Bybit.
Related Reading: Surge in Crypto Security Losses: Fewer Attacks, but Significantly Increased Destructiveness
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




