Author: Zhang Feng
As the anonymity, global circulation, and decentralization characteristics of cryptocurrencies become widely recognized, they have become the "new favorite" for money laundering crimes. From the early "Silk Road" dark web market to the current complex on-chain transfers using decentralized financial protocols, money laundering methods are constantly evolving, posing a severe challenge to global financial security.
In this context, regulatory agencies in various countries are demanding unprecedented compliance from cryptocurrency trading platforms, custodians, and other virtual asset service providers to fulfill strict anti-money laundering obligations.
I. Legal Framework and Regulatory Requirements
Globally, the "FATF Recommendations" issued by the Financial Action Task Force (FATF) are the authoritative standards for international anti-money laundering and counter-terrorist financing. It explicitly includes virtual asset service providers under regulation, requiring them to implement the "travel rule," which mandates the collection and transmission of information about the sender and receiver for virtual asset transfers exceeding a certain amount (usually $1,000/€1,000).
In China, the law takes a harsh stance against money laundering activities involving cryptocurrencies. Article 191 of the Criminal Law defines money laundering crimes, clearly categorizing behaviors such as "transferring funds through transfers or other payment settlement methods" and "cross-border asset transfers" as money laundering methods, fully encompassing operations related to cryptocurrencies. Although cryptocurrency trading platforms are banned from operating within China, law enforcement agencies still exercise long-arm jurisdiction and impose strict crackdowns on platforms operating overseas that serve Chinese users, as well as "underground banks" providing services for outbound funds.
The EU's "Markets in Crypto-Assets Regulation" (MiCA) and the US's "Bank Secrecy Act" also impose clear registration, licensing, and anti-money laundering obligations on VASPs. Therefore, regardless of where the platform is located, fulfilling anti-money laundering obligations is no longer optional but a necessary requirement for survival and development.
II. Analysis of Ten Typical Cases at Home and Abroad and Reflection on Platform Obligations
Case 1: PlusToken Ponzi Scheme Money Laundering Case
Case Summary: This is a typical case combining a "funding scheme" with money laundering. PlusToken lured over 2 million participants with high returns, involving a total value of over 40 billion yuan in digital currency. After the incident, the criminal group converted massive assets between different addresses and currencies through intensive on-chain transactions, ultimately cashing out through domestic and foreign exchanges.
Money Laundering Techniques: "Breaking down into smaller amounts," "on-chain obfuscation," "cross-exchange withdrawals." They dispersed large sums of money to tens of thousands of addresses, utilizing the anonymity of Bitcoin, Ethereum, etc., for multiple transfers, and finally sold in batches at exchanges with looser regulations, converting to fiat currency.
Reflection and Suggestions on Platform Obligations: First, strengthen the identification and monitoring of high-risk activities. Platforms must establish effective transaction monitoring systems to automatically alert on frequent, small-value deposit and withdrawal activities from the same source or related addresses within a short time (characteristic of "structured transactions"); second, strictly implement the "travel rule." Although this case mainly occurred before the widespread implementation of the FATF Recommendations, it highlights the importance of information traceability. Platforms must collect and verify user identity information such as name and address for transactions exceeding the threshold, ensuring that the flow of funds is traceable.
Case 2: Money Laundering Using "Score Running Platforms" and USDT
Case Summary: Criminal groups involved in telecom fraud and online gambling extensively recruited "code merchants," instructing them to receive payments using their bank accounts or Alipay, then directing the "code merchants" to purchase equivalent USDT on cryptocurrency platforms and transfer it to designated wallet addresses of the criminal group. This way, criminal funds seamlessly transitioned from the traditional banking system to the cryptocurrency system.
Money Laundering Techniques: "Fiat currency-stablecoin" conversion, utilizing the stable price of USDT as a medium of value to "clean" the illicit funds.
Reflection and Suggestions on Platform Obligations: First, deepen customer due diligence for fiat currency channels. When providing fiat-to-cryptocurrency exchange services, platforms should not be satisfied with online KYC alone. Users frequently engaging in "small, multiple transactions with many counterparties" should be considered high-risk customers, requiring enhanced due diligence to verify the legality of their fund sources; second, establish abnormal behavior models. The system should be able to identify transaction patterns that are significantly inconsistent with the user's declared occupation and income level, such as an ordinary office worker conducting dozens of fiat transactions daily with different individuals.
Case 3: Underground Bank Using Bitcoin for Cross-Border Matching
Case Summary: Domestic clients transferred RMB to the underground bank's domestic account, which instructed its overseas partners to pay equivalent foreign currency (or cryptocurrency) to the client's designated overseas account. In this process, Bitcoin served as a bookkeeping unit balancing the domestic and foreign funds, with no physical cross-border fund movement, but achieving actual cross-border fund transfer.
Money Laundering Techniques: "Matching," using cryptocurrency as a measure of value and settlement tool to evade foreign exchange controls.
Reflection and Suggestions on Platform Obligations: First, strengthen regional risk monitoring. Platforms should identify and monitor transactions involving countries on the jurisdiction's sanctions list and high-risk areas. Accounts frequently engaging in "buying entirely on one side and selling entirely on the other" between specific jurisdictions, especially when the user's IP address does not match the trading behavior, should be subject to close scrutiny; second, global perspective risk assessment. Platforms should not view transactions on a single platform in isolation. They should actively participate in industry information sharing (within legal limits) to identify matching transaction patterns from a global perspective.
Case 4: Money Laundering Using Cross-Border E-Commerce
Case Summary: Criminal groups set up fake cross-border e-commerce companies, forged import and export trade contracts, purchased Bitcoin through domestic OTC merchants, and transferred it to overseas affiliated companies. After selling Bitcoin, the overseas company paid foreign exchange to the domestic company under the guise of "export payment," thus cloaking illegal funds in a legitimate foreign trade disguise.
Money Laundering Techniques: Trade-based money laundering, fabricating real transactions, utilizing the cross-border convenience of cryptocurrencies to forge fund flows.
Reflection and Suggestions on Platform Obligations: First, conduct in-depth reviews of corporate users. For corporate users claiming to engage in international trade, platforms should not only verify their business registration information but also examine their actual trade background, such as logistics documents and customs records, being wary of transactions that are severely inconsistent with the company's scale; second, pay attention to OTC market risks. OTC merchants are key nodes connecting fiat and cryptocurrency. Platforms must conduct strict entry reviews and ongoing monitoring of OTC merchants, treating them as a focal point for anti-money laundering efforts.
Case 5: Online Gambling "Salary" Converted to USDT
Case Summary: Online gambling platforms converted all deposits, withdrawals, and payments of "salaries" and "commissions" to agents and employees into USDT. Gamblers purchased USDT with fiat currency and deposited it into the gambling platform, and after winning or receiving commissions, the platform returned USDT to the users' wallets, who then sold it themselves.
Money Laundering Techniques: Full-process cryptocurrency conversion, isolating the entire illegal business system from the traditional financial system, significantly increasing the difficulty of investigation.
Reflection and Suggestions on Platform Obligations: First, identify addresses associated with illegal activities. Platforms should utilize on-chain analysis tools to mark known gambling platforms, dark web markets, and related deposit addresses. Any users associated with these addresses should be immediately flagged and restricted; second, behavior analysis and association mapping. Establish user behavior profiles to automatically identify and alert on patterns where a large number of users regularly deposit USDT into a centralized address and receive "salaries" in USDT from that address.
Case 6: Bitfinex 2016 Hacker Attack Money Laundering Case (USA)
Case Summary: Hackers stole nearly 120,000 Bitcoins from the Bitfinex exchange. In the following years, they laundered the funds through mixers, decentralized exchanges, converting them into other tokens, and creating thousands of new wallet addresses. It wasn't until 2022 that the U.S. Department of Justice arrested two suspects and recovered some assets.
Money Laundering Techniques: Utilizing mixers and DeFi protocols for on-chain obfuscation, severing the flow of funds.
Reflection and Suggestions on Platform Obligations: First, block addresses associated with mixers. Platforms should blacklist known mixing services (such as ChipMixer, Wasabi Wallet, etc.) and prohibit users from depositing from these addresses, while reviewing withdrawal activities to these addresses. Second, integrate on-chain analysis tools. Platforms must procure or develop on-chain tracking capabilities, using tools like Chainalysis, Elliptic, etc., to score the "purity" of deposited funds and refuse services or freeze funds associated with high-risk addresses or linked to illegal activities.
Case 7: OneCoin Ponzi Scheme Case (Global)
Case Summary: OneCoin claimed to be the "Bitcoin killer," but was actually a Ponzi scheme without a blockchain and centralized bookkeeping, raising over 4 billion euros globally. It transferred funds through a complex network of global bank accounts and cash transport, but also partially utilized cryptocurrencies for layering.
Money Laundering Techniques: A combination of traditional and new methods, using cryptocurrencies as one of the layered tools.
Reflection and Suggestions on Platform Obligations: First, be wary of "pseudo-cryptocurrency" projects. Platforms should conduct thorough due diligence before listing any tokens, ensuring their technical authenticity, team transparency, and reasonable business logic. They should firmly resist centralized "Ponzi coins" that promise high returns; second, strengthen internal compliance culture. Prevent internal employees from being bribed or colluding with criminal groups. Regularly train employees on anti-money laundering practices and establish independent compliance reporting channels.
Case 8: Africrypt Investment Platform Scam Case (South Africa)
Case Summary: The founder of the cryptocurrency investment platform Africrypt went missing after claiming to be "hacked," absconding with approximately 69,000 Bitcoins. They quickly converted Bitcoin into other tokens through mixers and cross-chain bridges, cashing out using unregulated exchanges.
Money Laundering Techniques: Embezzlement, utilizing cross-chain technology to transfer assets.
Reflection and Suggestions on Platform Obligations: First, fulfill monitoring obligations for DeFi and cross-chain protocols. As cross-chain bridges become more prevalent, money laundering paths become more complex. Platforms need to update monitoring rules to track asset transfer paths across different blockchains; second, establish a rapid response mechanism with law enforcement agencies. Upon receiving reports of suspicious activities or requests for law enforcement cooperation, platforms should have a standardized internal process to quickly freeze assets and provide data, avoiding missed opportunities due to lengthy internal processes.
Case 9: Russian Drug Trafficking Group Using BTC for Money Laundering
Case Summary: A Russian drug trafficking group sold drugs on the dark web, receiving Bitcoin and hiring a professional money laundering team. This team laundered funds through exchanges like BTC-e, which had weak anti-money laundering measures at the time, ultimately funneling the money into the legitimate economy.
Money Laundering Techniques: Dark web-exchange-physical economy, a typical three-stage money laundering process.
Reflection and Suggestions on Platform Obligations: First, list addresses associated with the dark web as the highest risk. Any funds flowing in from known dark web market addresses should be considered extremely high risk. Platforms should automatically trigger investigations and consider directly freezing related accounts; second, implement a risk-based approach. Based on users' nationality, trading behavior, source of funds, occupation, and other multidimensional information, classify users into risk levels (low, medium, high) and apply stricter ongoing monitoring and transaction limits for high-risk users.
Case 10: Money Laundering Case of North Korean Hacker Group Lazarus Group (Global)
Case Summary: This organization stole large amounts of cryptocurrency through phishing, malware, and other methods (such as the $625 million theft from the Ronin Network cross-chain bridge), and then employed a complex strategy of "on-chain hopping," exchanging, staking, and transferring through multiple DeFi protocols, ultimately attempting to launder the money through mixers.
Money Laundering Techniques: National-level, highly complex on-chain money laundering, combining various methods such as hacking attacks, DeFi, and mixers.
Reflection and Suggestions on Platform Obligations: First, comply with sanctions regulations. Platforms must incorporate international sanctions lists such as OFAC into their systems, automatically intercepting transactions related to IP addresses, emails, and wallet addresses associated with sanctioned countries like North Korea and Iran; second, enhance defenses against advanced persistent threats. Platforms themselves may also become targets of hacking attacks. Significant investments must be made to strengthen cybersecurity to prevent becoming a source of money laundering crimes. Additionally, share threat intelligence with peers and law enforcement to jointly address threats from state-level hacker organizations.
III. Systematic Construction of Anti-Money Laundering Obligations by Platforms
Based on the above cases, a cryptocurrency business platform must build a multi-layered, full-process defense system to effectively fulfill its anti-money laundering obligations.
First, customer due diligence is the cornerstone. Identity verification should not be limited to names and ID cards but should incorporate biometric technologies such as facial recognition and live detection to ensure "real person, real name, real identity." Risk classification should establish a dynamic risk assessment model that adjusts risk levels in real-time based on user behavior, geography, transaction patterns, etc. Strengthen ongoing due diligence; for high-risk users, understand their sources of funds, wealth status, transaction purposes, and continuously monitor whether their transaction behavior aligns with initial declarations.
Second, transaction monitoring is core. Smart rules engine: Establish monitoring rules based on case experience, such as "structured transactions," "rapid asset transfers," and "interactions with blacklisted addresses." Behavior analysis model: Introduce machine learning to analyze each user's "normal" behavior baseline, and immediately alert if significant deviations occur (e.g., sudden large transactions, changes in transaction counterparties). On-chain tracking capabilities: Must be equipped with professional on-chain analysis tools capable of tracing the source of funds and identifying mixing behaviors.
Third, record-keeping and reporting are key. Complete record retention: All KYC materials, transaction records, and internal communication records must be legally retained for at least five years. Timely submission of suspicious transaction reports: Establish an independent anti-money laundering compliance officer who should report any confirmed suspicious transactions to the financial intelligence center without hesitation.
Additionally, organization and systems are safeguards. Clear anti-money laundering policies: Develop clear, executable internal anti-money laundering policies and ensure that all employees are aware of and comply with them. Independent compliance functions: The anti-money laundering compliance department should have a high degree of independence and authority, reporting directly to the board of directors or senior management. Ongoing employee training: Ensure frontline employees, especially customer service and operations personnel, are familiar with the latest money laundering techniques and the platform's response strategies.
Moreover, technological investment and innovation are the future. Embrace regulatory technology: Actively explore the application of privacy protection technologies such as zero-knowledge proofs in compliance fields to achieve compliance verification while protecting user privacy. Industry collaboration: Promote the establishment of an industry-wide risk address sharing database (within legal and privacy frameworks) to form a joint defense and control effort.
For cryptocurrency business platforms, anti-money laundering is no longer just external regulatory pressure; it is an intrinsic requirement for their long-term healthy development, a "passport" for building market trust and winning legitimate users. From PlusToken to Lazarus Group, each case serves as a painful lesson and a clear mirror reflecting the vulnerabilities in the platform's anti-money laundering defenses. Only by integrating anti-money laundering obligations into the corporate culture, using technology as a shield and systems as a sword, can a solid, intelligent, and dynamic defense system be constructed. This will enable steady progress on the balance beam of innovation and compliance, truly becoming a responsible and trustworthy participant in the future financial ecosystem. The fight against money laundering crime is an ongoing battle.
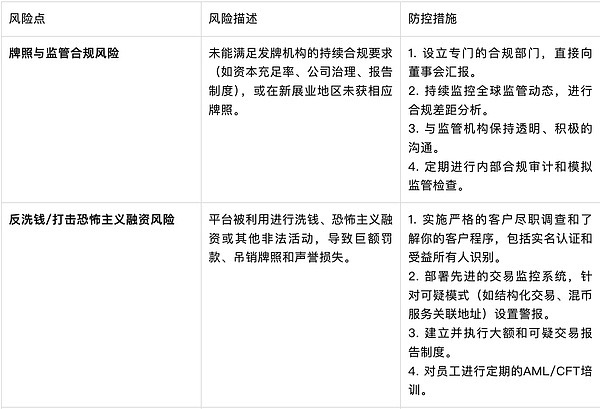
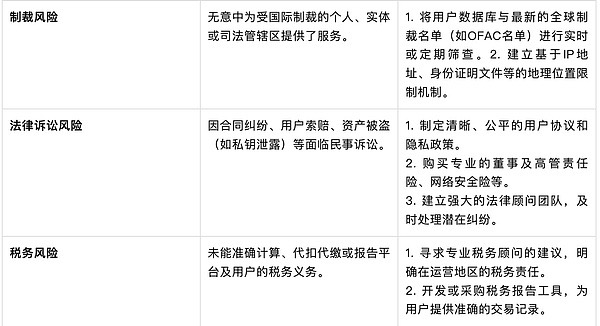
IV. Anti-Money Laundering Risk Management for Licensed Exchanges
As a licensed exchange, it faces various risks related to legal compliance, anti-money laundering regulatory requirements, technology and security, market and operations, asset management, strategy, and public relations. The key points of risk management regarding anti-money laundering discussed in this article lie in the continuous compliance with the ever-changing global and local regulatory requirements.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




