Author: Frank, PANews
On September 22, the cryptocurrency market experienced a chilling drop during the day, and the night brought new frost.
On the evening of September 22, the highly anticipated SocialFi project UXLINK fell victim to a hacker attack. The attacker exploited a contract vulnerability to steal $4 million worth of assets from the project’s treasury and minted up to 100 trillion new tokens out of thin air, subsequently dumping them on-chain to extract funds from the liquidity pool, ultimately profiting over $11 million. As the news broke, market confidence collapsed instantly, with the UXLINK token price plummeting over 80% in just a few hours, and its market cap evaporating from a high of approximately $140 million to $16.8 million. However, the hacker storm was not yet over; just 24 hours later, on the night of September 23, the native token SFUND of the established Launchpad platform Seedify.fund also fell victim. Its cross-chain bridge treasury was drained by hackers, with assets worth over $1.7 million looted, causing the SFUND price to crash to a historic low, with its market cap again evaporating by over $10 million.
In two days, two seemingly unrelated projects lost over $100 million in market cap under the precise strikes of hackers. This inevitably led every practitioner and investor to once again ask themselves: beyond the volatile market cycles, are the security vulnerabilities lurking deep within the code the sharpest sword of Damocles hanging over the crypto world?
UXLINK's "Daytime Thunder," a Fatal Game of Permissions
The collapse of UXLINK was a typical "internal explosion" triggered by a smart contract permission vulnerability. The entire incident unfolded like a meticulously choreographed tech crime movie, swift and deadly.
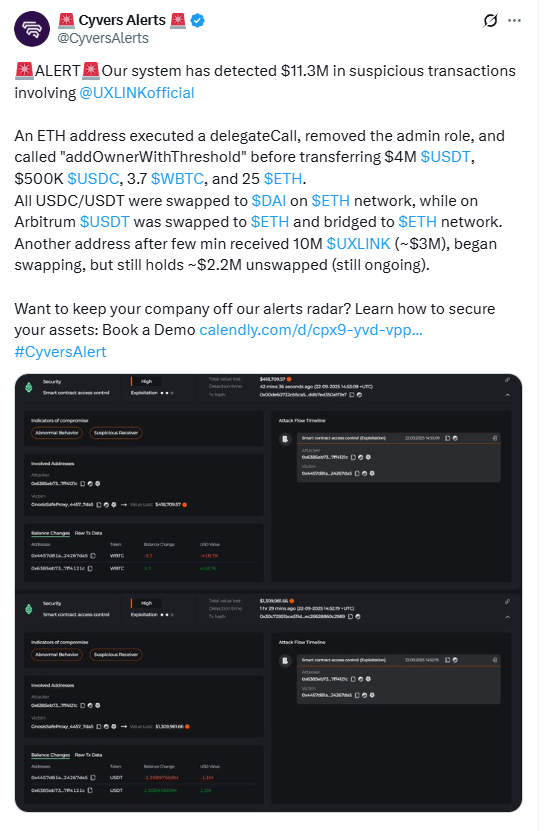
The main cause of the incident stemmed from a neglected "master key." Analysis showed that the attacker’s first step was to execute a delegateCall function. This transaction removed the legitimate admin role from the UXLINK contract and added a new multi-signature owner controlled by the hacker.
According to revelations from Cyvers Alerts, after gaining complete management control, the hacker immediately began transferring assets from UXLINK's treasury wallet. The initially stolen assets included approximately $4 million in USDT, $500,000 in USDC, 3.7 WBTC, and 25 ETH. This step secured direct and guaranteed profits for the attacker.
Subsequently, the attacker entered the most destructive phase: unauthorized token minting. On-chain data showed that the attacker created up to 100 trillion new UXLINK tokens. This activity completely destroyed market confidence, even though UXLINK quickly responded by communicating with several major CEXs to suspend trading. However, the on-chain price collapsed alongside the massive minting, with the lowest price even reaching six decimal places, nearly zero. A scene reminiscent of LUNA's infinite minting played out once again.
As of September 23, according to on-chain prices, UXLINK's market cap was around $80.
With almost unlimited supply of UXLINK tokens in hand, the attacker began systematically dumping them on major decentralized exchanges. To confuse observers, they used at least six different wallets to operate, exchanging the newly minted UXLINK tokens for high-value assets. On-chain analysis firm Lookonchain reported that the attacker obtained at least 6,732 ETH through these sales, valued at approximately $28.1 million at the time. However, there are currently two differing opinions on this profit asset on social media, with several security firms (including the loss amount cited by UXLINK officials being $11.3 million).
Regardless of the calculation method, it pales in comparison to the severe losses suffered by the community. Before the collapse, UXLINK's market cap was about $150 million, and after reaching the lowest price, the market cap displayed on centralized exchanges dropped to $16 million, with the community evaporating approximately $100 million in market cap.
During this process, many users mistakenly believed that the hacker would stop after stealing the treasury assets, so they planned to buy the dip. On social media, many users shared that they intended to gamble on a rebound by buying spot or opening long contracts, only to suffer losses exceeding 99%. One address invested over $900,000 in assets, ultimately losing 99.8%.
The "Darkest Hour" of a Star Project, Where Does UXLINK Go from Here?
The day before the attack, UXLINK's official account tweeted, "Something big is about to happen," but little did they know it would become a self-fulfilling prophecy.
After the incident, UXLINK's official team quickly responded, stating they had urgently contacted several CEXs to suspend UXLINK trading and would initiate a token swap plan. However, due to the inability to recover contract permissions, they could not prevent the hacker from minting trillions of tokens. This heavy blow will pose significant challenges to UXLINK's community confidence and ecological development.
Before the attack, UXLINK was one of the most watched star projects in this cycle, especially in the Korean market, where its influence was not to be underestimated. As a SocialFi platform, UXLINK rapidly accumulated a large user base through its unique "acquaintance social" and group fission model. According to public information, the project has completed over $9 million in financing, with notable institutional investors.
UXLINK viewed Korea as a core market, investing substantial resources in localized operations and marketing, accumulating a large number of real users. According to official data, UXLINK achieved a milestone of over 10 million registered users by 2024.
Subsequently, UXLINK successfully launched on Korea's largest compliant exchange, Upbit, and repeatedly topped the daily trading rankings on major Korean exchanges Upbit and Bithumb. Its perpetual contracts also successfully launched on Binance, further expanding its global influence.
After the attack, the UXLINK team stated they would formulate a new token swap plan to compensate affected users through snapshots and other methods. However, the road ahead remains fraught with challenges.
The biggest challenge comes from rebuilding trust and the attitude of exchanges. Especially for compliant exchanges like Upbit, the stability and security of the token economic model are core considerations for listing and maintaining trading pairs. Historically, there have been many precedents of being delisted due to similar incidents. For example, the former Pundi AI (PUNDIX) was delisted by compliant exchanges like Upbit due to a hacker attack that led to abnormal token minting, citing "untimely information disclosure" as the reason for terminating trading support.
The current situation faced by UXLINK is highly similar to this. If its new token plan cannot convince Upbit and other exchanges that it can completely fix the vulnerabilities and restore a healthy economic model, being "delisted" will be a high-probability event. Once liquidity in the core market is lost, UXLINK's path to recovery will become increasingly difficult.
Coincidence or Not, SFUND's Alarm and Industry Reflection
Just as the market was still digesting the impact of the UXLINK incident, on the evening of September 23, the theft of the governance token SFUND from the Web3 project incubation and launch platform Seedify.fund once again sounded the alarm for the entire industry.
The attack method on SFUND was similar to that of UXLINK. According to revelations from Specter, the hacker gained permissions through Baseshang and conducted minting, issuing up to 3 quattuordecillion (10 to the 24th power) tokens.
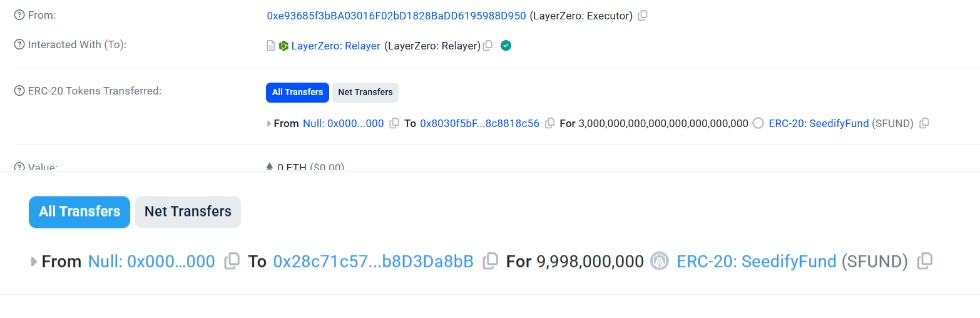
Subsequently, 10 billion tokens were minted on the BSC chain and sold for $1.2 million worth of ETH. Previous related information indicated that this hacker had a clear connection to the North Korean hacker group Serenity Shield.
Although the amount stolen this time was not large, the blow to market confidence was equally significant. Within 15 minutes, SFUND's price plummeted 73%, with its market cap dropping from $27 million to a low of $11 million. Its script was highly similar to UXLINK's; it remains unclear whether this was a coincidence or if both attacks originated from the same hacker group.
Although a complete security report on both incidents has yet to be released, we can still draw some reflections from them. The underlying causes of both incidents stemmed from contract permission issues and the minting switch.
The founder of SFUND emphasized in a warning message that its contract had been audited and had been running for three years. This indicates that audits are not a panacea; routine audits may not uncover all deep logical vulnerabilities, and ongoing security audits and code reviews are crucial.
However, for users, we do not possess the logic to review contracts and their operational logic. How to avoid pitfalls indeed becomes a profound subject. A simpler approach might be to set some necessary stop-loss orders even when hoarding coins, to prevent total loss in the event of a black swan event.
Additionally, during these two incidents, many users, driven by luck, attempted to buy the dip early, only to suffer significant losses. Such actions are akin to licking blood from a knife's edge and are inadvisable.
Furthermore, proposing a "snapshot swap" plan to the project parties typically involves recording all users' holdings at a certain point in time before the attack and issuing a new token to users in proportion. The essence of this plan is akin to closing the barn door after the horse has bolted and does not represent a means to compensate for all losses.
From UXLINK to SFUND, within two days, we witnessed how code vulnerabilities can topple a project's value and ecosystem like a row of dominoes. This once again proves that in the dark forest of crypto, security is always "1," while other brands, communities, and market caps are merely "0s" that follow. Without the "1" of security, everything else is meaningless. For project parties, every line of code must be treated with the utmost reverence. For investors, while pursuing high returns, potential security risks must be prioritized in decision-making. Otherwise, the next to zero out may not be far off.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




