These two tools collectively embody our mission—protecting the order and security of decentralized financial systems.
0. Introduction
Stablecoins have developed rapidly in recent years. With their widespread application, regulators have increasingly emphasized the establishment of mechanisms to freeze illegal funds. We have observed that mainstream stablecoins such as USDT and USDC already possess this capability technically. In practice, there have been multiple cases indicating that these mechanisms have indeed played a role in combating money laundering and other illegal financial activities.
Furthermore, our research shows that stablecoins are not only used for money laundering but also frequently appear in the financing processes of terrorist organizations. Therefore, this article analyzes from two perspectives:
- A systematic review of the freezing actions of USDT blacklisted addresses;
- Exploring the connection between frozen funds and terrorist financing.
This report is based on publicly available on-chain data and may contain inaccuracies or omissions. If you have suggestions or corrections, please feel free to contact us: contact@blocksec.com.
1. Analysis of USDT Blacklisted Addresses
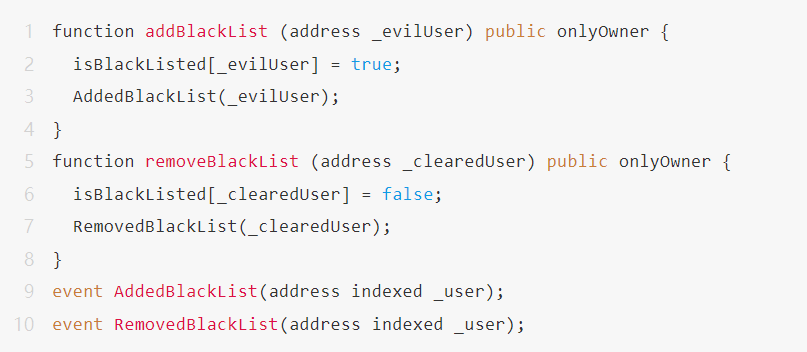
We identified and tracked Tether blacklisted addresses through on-chain event monitoring. The analysis method has been validated through the Tether smart contract source code. The core logic is as follows:
Event Identification:
The Tether contract maintains the blacklist status through two events:
- AddedBlackList: New blacklisted address
- RemovedBlackList: Removed blacklisted address
Dataset Construction:
We record the following fields for each blacklisted address:
- The address itself
- The time the address was blacklisted (blacklisted_at)
- If the address is removed from the blacklist, the time of removal (unblacklisted_at)
Below is the implementation of the relevant functions in the contract:
1.1 Core Findings
Based on Tether data on the Ethereum and Tron chains, we found the following trends:
Since January 1, 2016, a total of 5,188 addresses have been blacklisted, involving frozen funds exceeding $2.9 billion.
During the period from June 13 to June 30, 2025, 151 addresses were blacklisted, of which 90.07% came from the Tron chain (the address list can be found in the appendix), with frozen amounts reaching $86.34 million. The time distribution of blacklist events: June 15, 20, and 25 were peak days for blacklisting, with June 20 alone seeing as many as 63 addresses blacklisted in one day.
- Distribution of Frozen Amounts: The top ten addresses by amount froze a total of $53.45 million, accounting for 61.91% of the total frozen amount. The average frozen amount is $571,800, but the median is only $40,000, indicating that a small number of large addresses inflated the overall average, while the vast majority of addresses had smaller frozen amounts.
- Lifecycle Fund Distribution: These addresses cumulatively received $808 million, of which $721 million was transferred out before being blacklisted, leaving only $86.34 million actually frozen. This indicates that most funds were successfully transferred before regulatory intervention. Additionally, 17% of the addresses had no outgoing transaction records, possibly serving as temporary storage or fund aggregation points, warranting further attention.
- Newly Created Addresses More Likely to be Blacklisted: 41% of blacklisted addresses were created less than 30 days ago, 27% had existed for 91–365 days, and only 3% had been in use for over 2 years, indicating that new addresses are more likely to be used for illegal activities.
- Most Addresses Achieved "Escape Before Freezing": About 54% of addresses had transferred out over 90% of their funds before being blacklisted, and another 10% had a balance of 0 at the time of freezing, indicating that law enforcement actions mostly only freeze the residual value of funds.
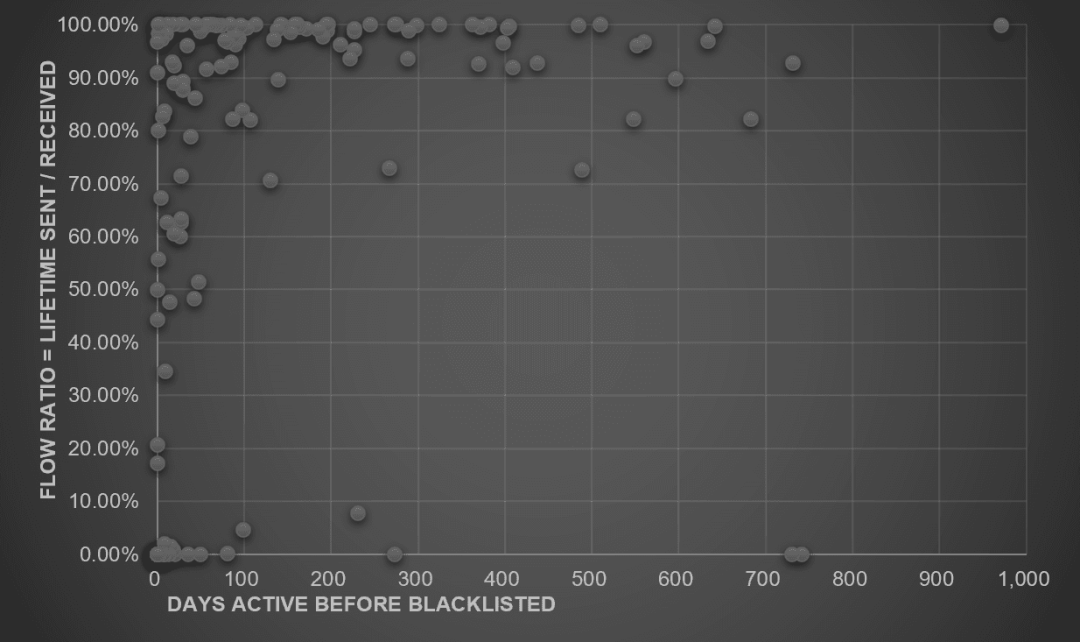
- New Addresses Have Higher Money Laundering Efficiency: Through the FlowRatio vs. DaysActive scatter plot, we found that new addresses excelled in terms of quantity, blacklisting frequency, and transfer efficiency, achieving the highest success rate in money laundering.
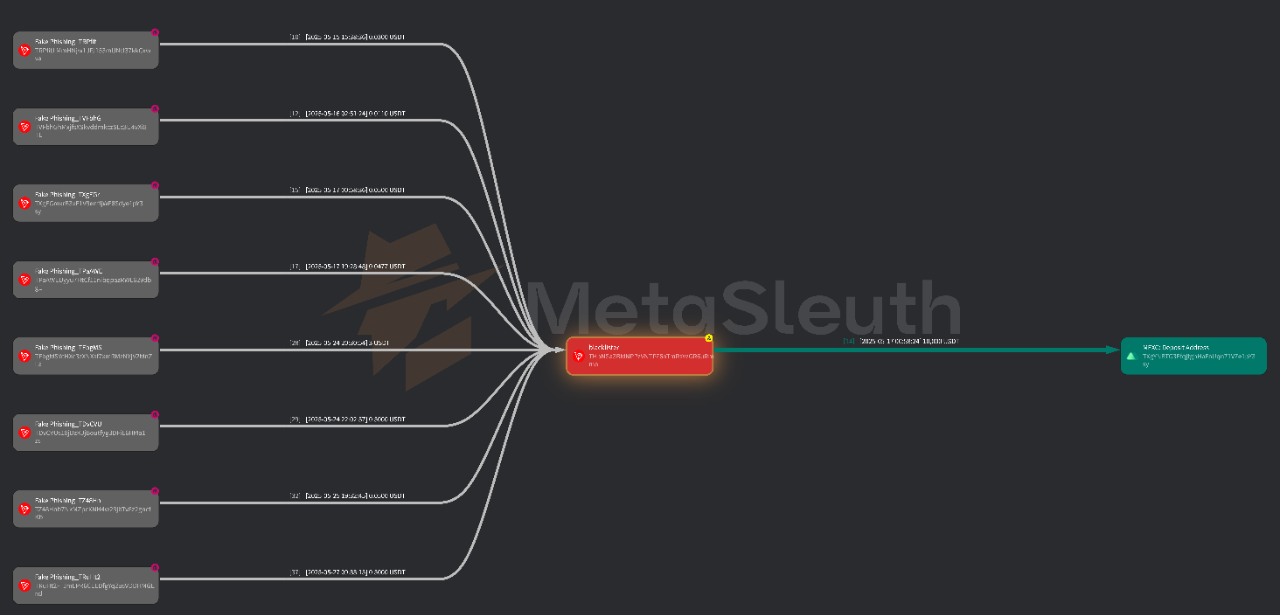
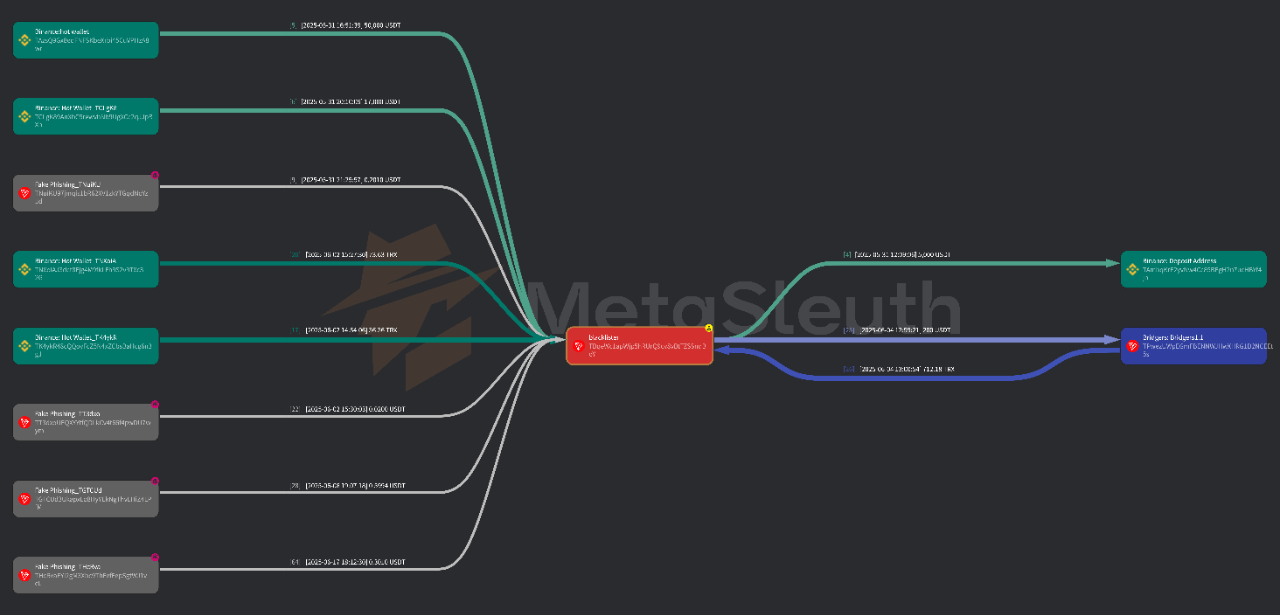
1.2 Fund Flow Tracking
Using BlockSec's on-chain tracking tool MetaSleuth (https://metasleuth.io), we further analyzed the fund movements of the 151 USDT addresses blacklisted between June 13 and June 30, identifying the main sources and destinations of the funds.
1.2.1 Fund Source Analysis
- Internal Contamination (91 addresses): The funds of these addresses came from other already blacklisted addresses, indicating a highly interconnected money laundering network.
- Phishing Labels (37 addresses): Many upstream addresses were labeled as "Fake Phishing" in MetaSleuth, possibly deceptive labels to obscure illegal sources.
- Exchange Hot Wallets (34 addresses): Fund sources include hot wallets from exchanges like Binance (20), OKX (7), and MEXC (7), possibly related to stolen accounts or "mule accounts."
- Single Major Distributors (35 addresses): The same blacklisted address acted multiple times as an upstream, possibly serving as an aggregator or mixer for fund distribution.
- Cross-Chain Bridge Entry (2 addresses): Some funds originated from cross-chain bridges, indicating cross-chain money laundering operations.
1.2.2 Fund Destination Analysis
- Flowing to Other Blacklisted Addresses (54): There is an "internal loop chain" structure among blacklisted addresses.
- Flowing to Centralized Exchanges (41): These addresses transferred funds to recharge addresses of CEXs like Binance (30), Bybit (7), achieving an "exit."
- Flowing to Cross-Chain Bridges (12): This indicates that some funds attempted to escape the Tron ecosystem, continuing cross-chain money laundering.
It is noteworthy that Binance and OKX appear on both the inflow (hot wallets) and outflow (recharge addresses) sides, further highlighting their core position in the funding chain. The current inadequacy of exchanges in executing AML/CFT measures and the lag in asset freezing may allow criminals to complete asset transfers before regulatory intervention.
We recommend that major cryptocurrency trading platforms, as core channels for funds, strengthen real-time monitoring and risk interception mechanisms to prevent issues before they arise.
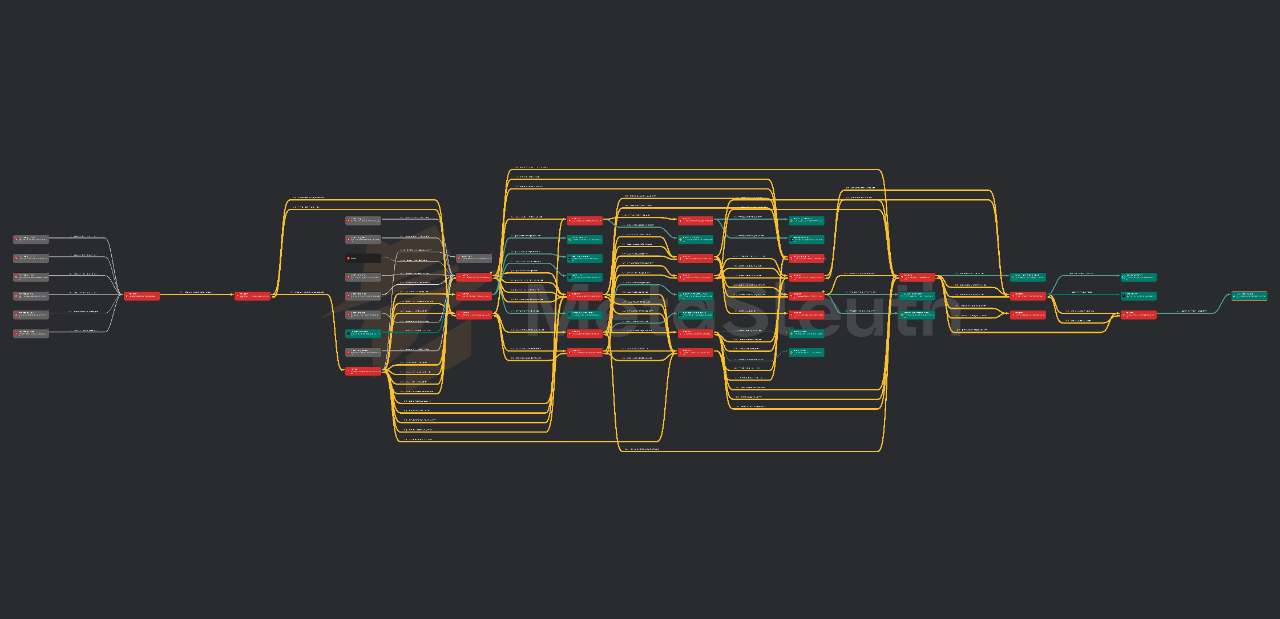
2. Terrorist Financing Analysis
To further understand the use of USDT in terrorist financing, we analyzed the Administrative Seizure Orders issued by Israel's National Bureau for Counter Terror Financing (NBCTF). Although the single data source we used makes it difficult to restore the full picture, it serves as a representative sample for a conservative analysis and estimation of USDT's involvement in terrorist transactions.
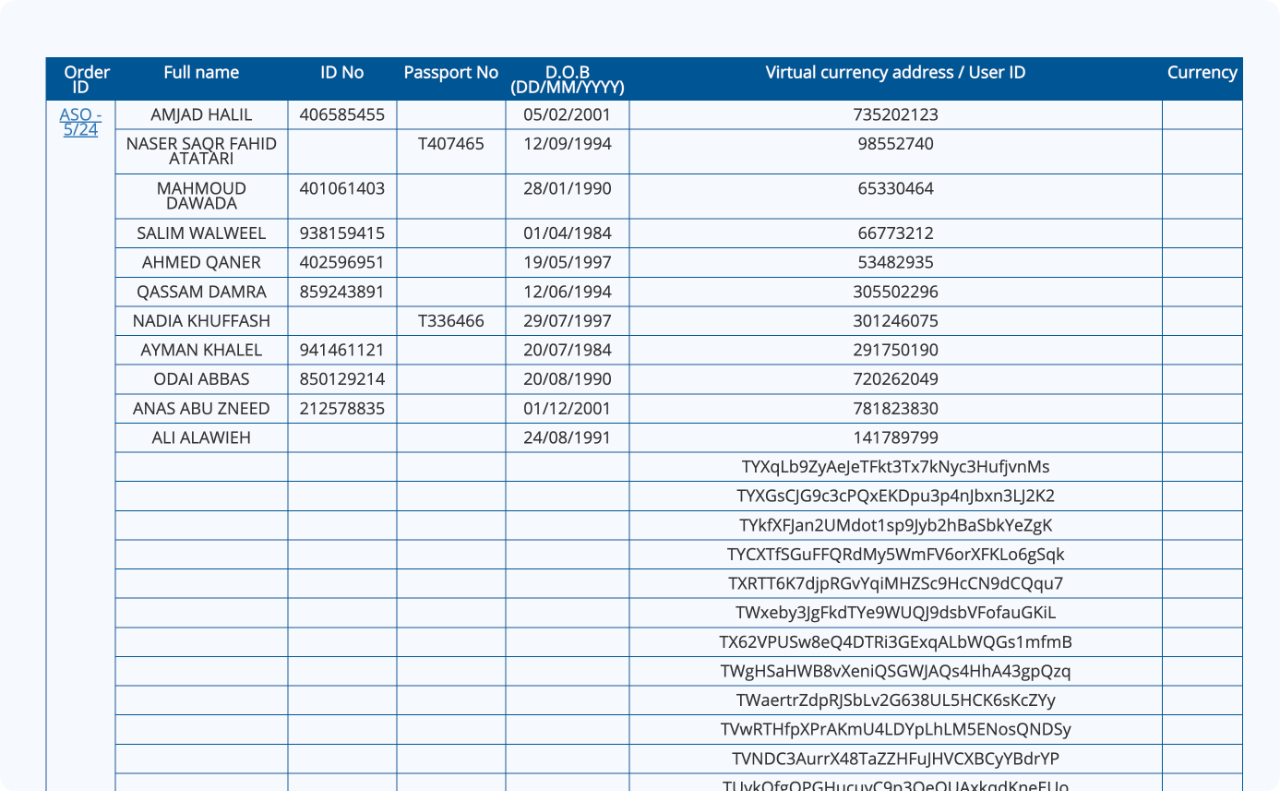
2.1 Core Findings
Release Timing: Since the escalation of the Israel-Iran conflict on June 13, 2025, only one new seizure order has been issued (June 26). The previous document was dated June 8, indicating a lag in law enforcement response during periods of geopolitical tension.
Target Organizations: Since the outbreak of conflict on October 7, 2024, the NBCTF has issued a total of 8 seizure orders, 4 of which explicitly mention "Hamas," while the latest one mentions "Iran" for the first time.
Addresses and Assets Involved in the Seizure Orders:
- 76 USDT (Tron) addresses
- 16 BTC addresses
- 2 Ethereum addresses
- 641 Binance accounts
- 8 OKX accounts
Our on-chain tracking of 76 USDT (Tron) addresses reveals two behavioral patterns of Tether in responding to these official directives:
- Proactive Freezing: Tether had already blacklisted 17 Hamas-related addresses before the issuance of the seizure order, averaging 28 days in advance, with the earliest being 45 days ahead.
- Rapid Response: For the remaining addresses, Tether completed the freezing in an average of only 2.1 days after the announcement of the seizure order, demonstrating good law enforcement cooperation capabilities.
These signs indicate a close, even preemptive, cooperation mechanism between Tether and certain national law enforcement agencies.
3. Summary and Challenges Facing AML/CFT
Our research shows that while stablecoins like USDT provide technical means for transaction controllability, AML/CFT still faces the following challenges in practice:
3.1 Core Challenges
- Delayed Law Enforcement vs. Proactive Prevention: Most law enforcement actions currently rely on post-event processing, leaving room for criminals to transfer assets.
- Regulatory Blind Spots in Exchanges: Centralized exchanges, as hubs for capital inflow and outflow, often lack sufficient monitoring, making it difficult to timely identify abnormal behaviors.
- Increasing Complexity of Cross-Chain Money Laundering: The use of multi-chain ecosystems and cross-chain bridges makes fund transfers more covert, significantly increasing the difficulty of regulatory tracking.
3.2 Recommendations
We recommend that stablecoin issuers, exchanges, and regulatory agencies:
- Strengthen on-chain intelligence sharing;
- Invest in real-time behavioral analysis technology;
- Establish a cross-chain compliance framework.
Only under a timely, collaborative, and technologically mature AML/CFT system can the legitimacy and security of the stablecoin ecosystem be truly guaranteed.
4. BlockSec's Efforts
At BlockSec, we are committed to promoting the security and compliance of the cryptocurrency industry, focusing on providing actionable on-chain solutions for AML and CFT. We have launched two key products:
4.1 Phalcon Compliance
- Designed specifically for exchanges, regulatory agencies, payment projects, and DEXs, supporting:
- Multi-chain address risk scoring
- Real-time transaction monitoring
- Blacklist identification and alerts
Helping users meet increasingly stringent compliance requirements.
4.2 MetaSleuth
Our visual on-chain tracking platform has been adopted by over 20 regulatory and law enforcement agencies worldwide. It supports:
- Visual fund tracking
- Multi-chain address profiling
- Complex path reconstruction and analysis
These two tools collectively embody our mission—protecting the order and security of decentralized financial systems.
Addresses mentioned in the text:
https://docs.google.com/spreadsheets/d/1pz7SPTY2J4S7rGMiq6Dzi2Q5p0fXSGKzl9QF2PiV6Gw/edit?usp=sharing
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。