Modern fraud is shifting from technical vulnerabilities to a dual attack on trust and psychological weaknesses.

Bitget Anti-Fraud Monthly Research Report (2025) Summary
Cryptocurrency fraud has entered a new era driven by AI deepfakes, social engineering, and the packaging of fake projects. This report, co-authored by Bitget, SlowMist, and Elliptic, analyzes common fraud methods from 2024 to early 2025 and proposes joint defense strategies for users and platforms.
The current three high-risk fraud types are:
Deepfake impersonation — using synthetic videos to promote false investments;
Social engineering fraud — including job scam Trojans, phishing bots, and fake staking schemes;
Modern Ponzi schemes — disguised as DeFi, NFT, or GameFi projects.
Modern fraud is transitioning from technical vulnerabilities to a dual attack on trust and psychological weaknesses. From wallet hijacking to multi-million dollar fraud, attacks are showing trends of high personalization, high deception, and concealment.
In response, Bitget has launched the "Anti-Scam Hub," upgraded the platform's protection system, and collaborated with SlowMist and Elliptic to achieve on-chain tracking of illicit funds, dismantling phishing networks, and marking cross-chain fraudulent activities.
The report includes real case analyses, a fraud red flag list, and protection guidelines for users and institutions.
Core conclusion: When AI can perfectly replicate anyone, security defenses must start with skepticism and end with collective defense.
Table of Contents
1. Core Summary
The current status of AI-assisted cryptocurrency fraud threats and the joint countermeasures by Bitget, SlowMist, and Elliptic.
2. Introduction: Threat Evolution Trends
How the development of DeFi, the popularity of AI, and cross-border convenience have created a new breeding ground for fraud, along with the risks involved.
3. Dissection of Modern Cryptocurrency Fraud
Analysis of the most dangerous frauds today:
3.1 Deepfake impersonation
3.2 Social engineering strategies
■ AI arbitrage bots
■ Job scam traps
■ Social media phishing
■ Address poisoning attacks
■ Pixiu token scams
■ Fake staking rebate platforms
■ Airdrop traps
3.3 Ponzi schemes in the Web3 era
4. Reinforcing Digital Defenses: Bitget's Multi-Layer Security Architecture
Detailed explanation of Bitget's real-time threat detection, token due diligence, dual audit mechanisms, and $300 million protection fund.
5. On-Chain Fraud Tracking and Fund Forensics (Written by Elliptic)
How transaction monitoring, cross-chain bridge tracking, and behavioral analysis can identify and block the flow of illicit funds.
6. Protection Recommendations and Best Practices (Written by SlowMist)
Practical guide for users and enterprises: from phishing identification to developing anti-fraud habits and enterprise-level response frameworks.
7. Conclusion: Future Path Planning
How cryptocurrency security is shifting from isolated defenses to network immunity, and how Bitget is staying one step ahead in the face of evolving threats.
Cutting-Edge Insights: Unveiling New Trends in Cryptocurrency Fraud
1. Core Summary
In January 2025, Hong Kong police dismantled a deepfake fraud group and arrested 31 individuals, who impersonated cryptocurrency executives to steal $34 million — this was just one of 87 similar cases uncovered in Asia during the first quarter (SlowMist, "2025 Cryptocurrency Crime Report"). These are indisputable facts. From AI-generated videos of the Prime Minister of Singapore to "false endorsements" by Musk, deepfake trust attacks have become a daily threat.
This report, completed by three parties, reveals how cryptocurrency fraud has evolved from crude phishing scams to AI-enhanced psychological manipulation: nearly 40% of high-value fraud cases in 2024 involved deepfake technology. Whether it’s job scam traps or Ponzi "staking platforms," the underlying theme is the precise exploitation of trust, fear, and greed through social engineering.
Cryptocurrency fraud is not just about stealing money — it is eroding the foundational trust of the industry.
Bitget's security system intercepts a large number of trust abuse behaviors daily: abnormal logins, phishing attacks, and malicious software downloads. To address this, we launched the Anti-Scam Center, developed proactive protection tools, and collaborated with global leaders like SlowMist and Elliptic to dismantle fraud networks and track illicit funds.
This report maps the evolution of threats, reveals current high-risk methods, and provides practical defense strategies for users and institutions. When AI can replicate anyone's face, security mechanisms must fundamentally possess a spirit of skepticism.
2. Introduction: Threat Evolution Trends
The borderless nature of cryptocurrency is both its greatest advantage and its greatest risk. As decentralized protocols lock in total value exceeding $98 billion, institutional participation continues to rise, and the same technology driving innovation is also fueling a new wave of cryptocurrency fraud.
This is no longer the primitive phishing attacks of the past. The scale and sophistication of fraud from 2023 to 2025 have increased dramatically: in 2024, global users lost over $4.6 billion to fraud, a year-on-year increase of 24% (Chainalysis, "2025 Cryptocurrency Crime Report"). From deepfake impersonation to Ponzi schemes disguised as "staking returns," fraudsters are using AI, psychological manipulation, and social platforms to deceive seasoned users.
The three main attack methods are:
● Deepfakes, impersonating public figures to endorse fake platforms.
● Social engineering scams, including job scam tests and phishing tweets.
● Variants of Ponzi schemes, such as scams packaged as DeFi/GameFi/NFT.
What is most alarming is the upgrade in psychological manipulation: victims are not merely deceived but gradually persuaded. Scammers not only steal passwords but also design traps targeting behavioral blind spots.
Of course, defense systems are also evolving in tandem: collaborative innovation within the ecosystem is accelerating.
Bitget's behavioral analysis system marks suspicious patterns in real-time; Elliptic tracks multi-chain assets for forensic evidence; SlowMist's threat intelligence helps eliminate phishing gangs in Asia.
This report integrates practical case studies, field research, and operational data from three parties, analyzing the main causes of current asset losses and providing counter-strategies for users, regulators, and platforms.
Fraud methods continue to evolve, but defense mechanisms are also upgrading simultaneously. This report elaborates on specific solutions.
3. Dissection of Modern Cryptocurrency Fraud: Top Ten Scams of 2024 - 2025
As blockchain technology becomes more widespread and cryptocurrency assets appreciate, scams are becoming increasingly complex, concealed, and sophisticated, exhibiting new characteristics of "high-tech disguise + psychological manipulation + on-chain inducement." Over the past two years, scammers have integrated AI, social engineering, and traditional fraud models to construct a more deceptive and destructive fraud ecosystem. Among these, deepfakes, social engineering, and Ponzi variants are the most rampant.
3.1 Deepfakes: The Collapse of Trust Systems
From 2024 to 2025, generative AI has spawned new types of trust fraud: a form of fraud based on trust using deepfake technology. Attackers use AI synthesis tools to impersonate well-known project founders, exchange executives, or community KOLs in audio and video to mislead users. The forged materials can often be indistinguishable from the real thing — mimicking the target's facial expressions and voice, even generating videos with "official logos" in the background, making it difficult for ordinary users to discern authenticity. Typical scenarios include:
(1) Celebrity deepfake promotion of investments
Scammers easily "invite celebrities to endorse" using deepfake technology. Example: Deepfake videos of Singapore's Prime Minister Lee Hsien Loong and Deputy Prime Minister Lawrence Wong were created to promote a "government-backed cryptocurrency platform."
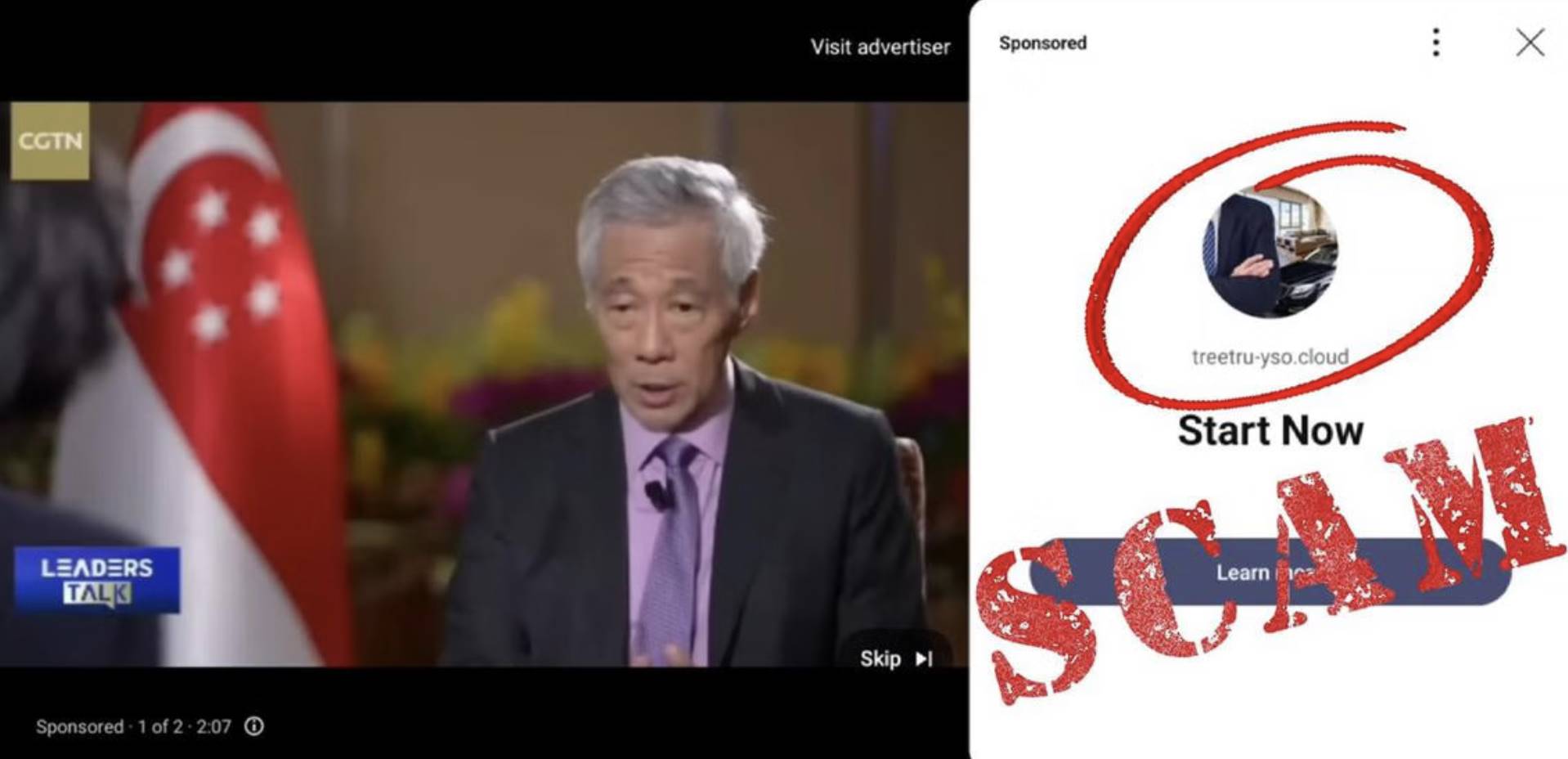
https://www.zaobao.com.sg/realtime/singapore/story20231229-1458809
Tesla CEO Elon Musk frequently appears in fake investment reward scams.
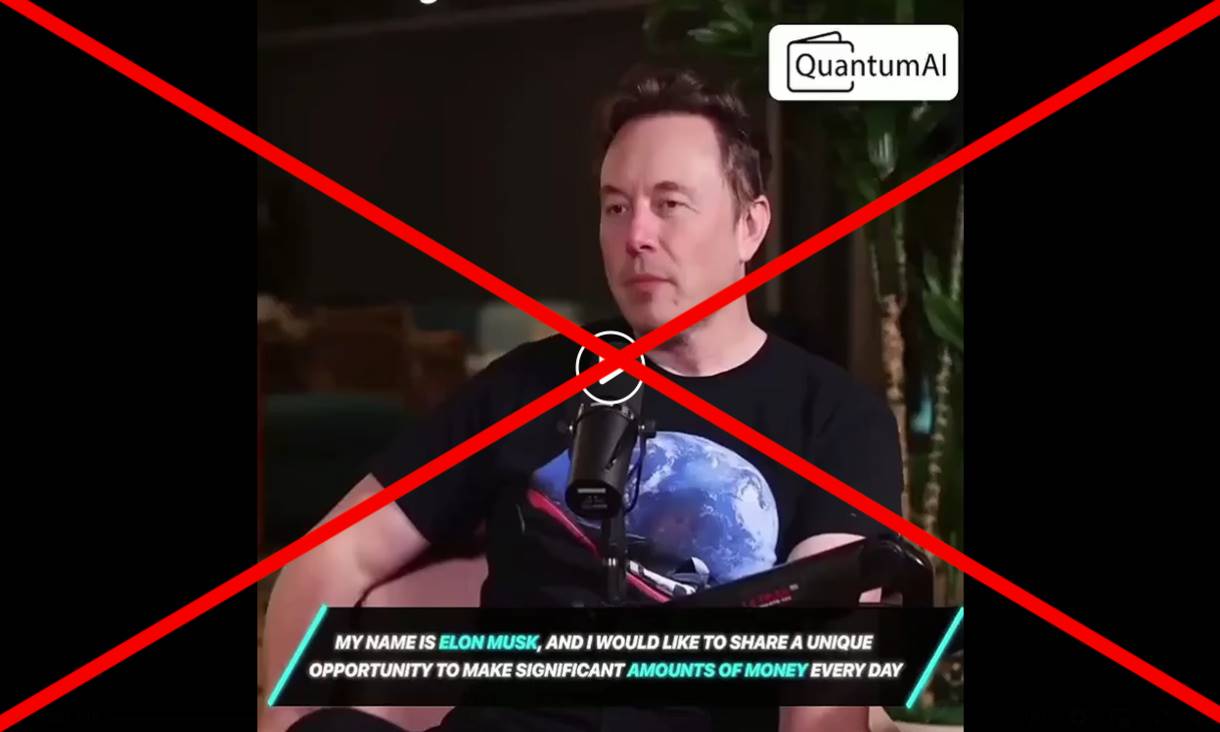
https://www.rmit.edu.au/news/factlab-meta/elon-musk-used-in-fake-ai-videos-to-promote-financial-scam
Such videos are widely disseminated through social media platforms like X/Facebook/Telegram, and scammers often disable comments to create a false impression of "official authority," enticing users to click on malicious links or invest in specific tokens. This attack method exploits users' inherent trust in "authoritative figures" or "official channels," making it highly deceptive.
(2) Bypassing identity verification
Scammers use AI to forge dynamic facial videos (which can respond to voice commands) combined with victims' photos to bypass identity verification systems of exchanges/wallet platforms, hijacking accounts to steal assets.
(3) Virtual identity investment scams
From 2024 to 2025, police in Hong Kong and Singapore have continuously dismantled multiple deepfake fraud groups. For instance, in early 2025, Hong Kong police arrested 31 suspects in a case involving HKD 34 million, with victims spread across Singapore, Japan, Malaysia, and other Asian countries and regions. Characteristics of the criminal organization include:
● Recruiting media professionals to build rich virtual identities and backgrounds;
● Creating numerous phishing groups on Telegram to approach targets with "high education, gentle, friendly personas";
● Inducing users to invest in fake platforms through "friendship → guiding investment → withdrawal obstacles" narratives;
● Forging chat records/customer service dialogues/profit screenshots to create a sense of reality and a trustworthy illusion;
● Inducing continuous recharges under the guise of "activating computing power" and "withdrawal review" (Ponzi structure).

https://user.guancha.cn/main/content?id=1367957
(4) Deepfake + Zoom phishing
Scammers impersonate Zoom to send fake meeting invitation links, tricking users into downloading "meeting software" that contains Trojans. During the meeting, "participants" use deepfake videos to impersonate executives or technical experts, manipulating victims to click further, authorize, or transfer funds. Once the device is controlled, scammers begin to remotely control the device, stealing cloud data or private keys.
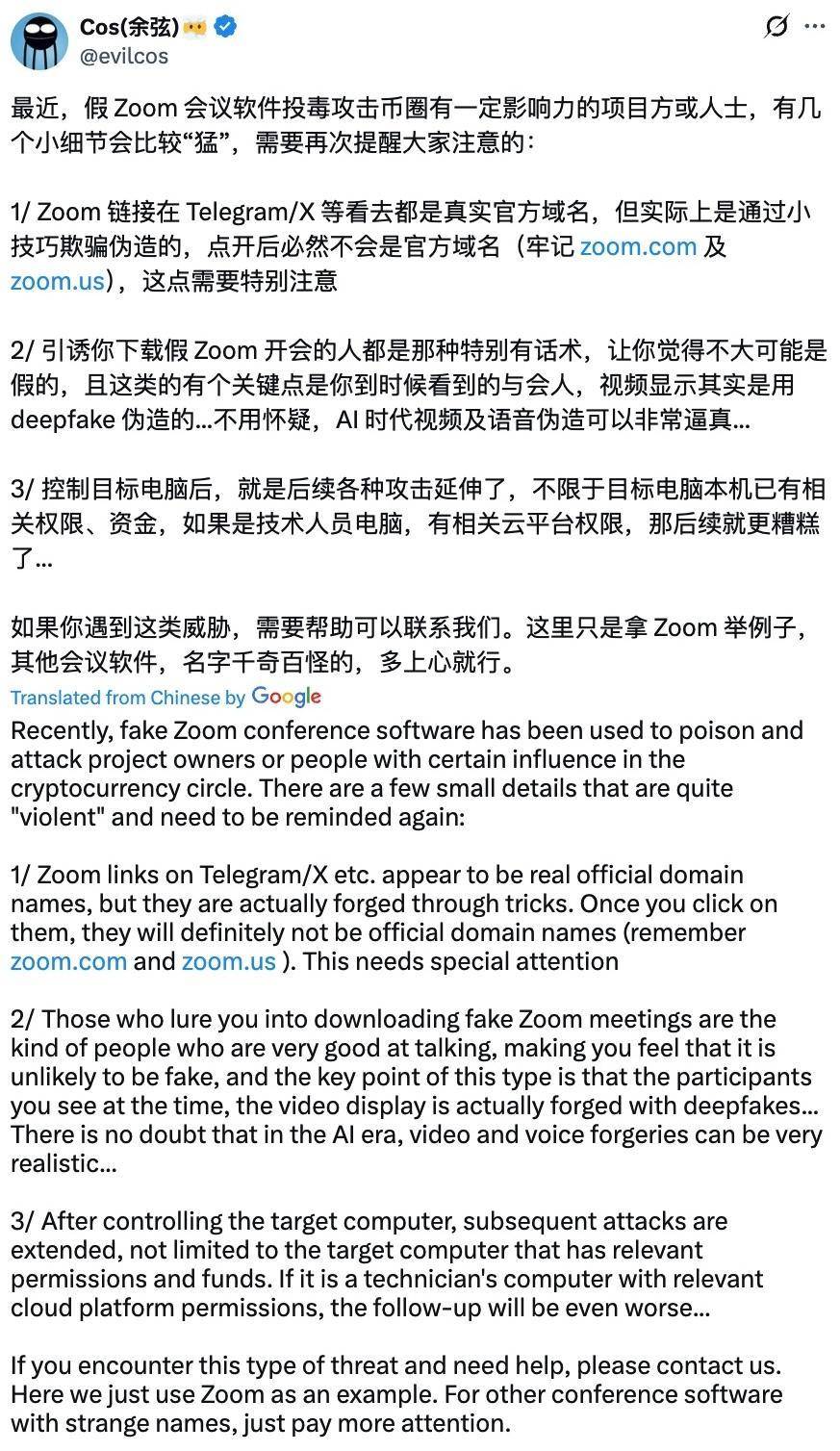
https://x.com/evilcos/status/1920008072568963213
From a technical perspective, scammers use AI synthesis tools like Synthesia, ElevenLabs, and HeyGen to generate high-definition audio and video in minutes, spreading them through platforms like X/Telegram/YouTube Shorts.
Deepfake technology has become a core component of AI-driven scams. The credibility of visual and auditory content has sharply declined in the AI era. Users must verify asset operation-related "authoritative information" through multiple channels to avoid blindly trusting "familiar faces or voices." At the same time, project teams should recognize the brand risks posed by AI forgery, establish a single trusted information dissemination channel, or use on-chain signature broadcasting for identity verification, thereby structurally resisting forgery attacks.
3.2 Social Engineering Strategies: Exploiting Psychological Vulnerabilities
Complementing high-tech means are low-tech but highly effective social engineering attacks. Human nature is the weakest and most easily overlooked link, leading many users to underestimate the threats posed by social engineering. Scammers often manipulate user behavior through disguise, guidance, and intimidation, gradually achieving their fraudulent goals by exploiting users' psychological weaknesses.
(1) AI Arbitrage Bot Scam
AI has become a hallmark technology for enhancing productivity, and scammers quickly seized this trend, packaging scams with the label "ChatGPT generated" (a phrase that sounds cutting-edge and credible) to lower user defenses.
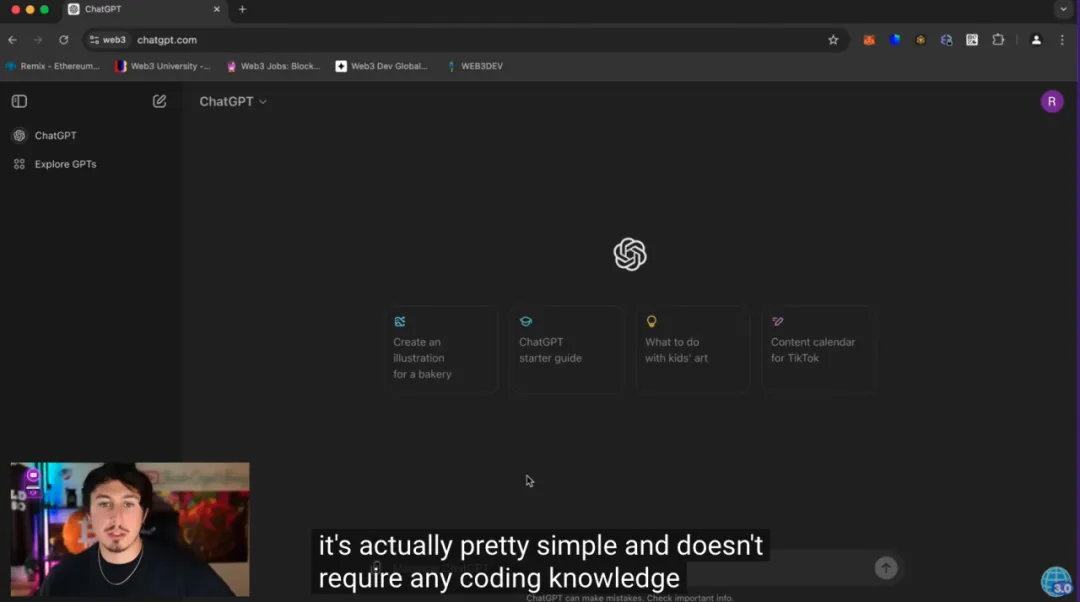
The scam typically begins with a detailed video tutorial. In the video, scammers claim that the code for the arbitrage bot is generated by ChatGPT, which can be deployed on blockchains like Ethereum to monitor the release of new tokens and price fluctuations, conducting arbitrage through flash loans or price differences. They emphasize that "the bot will automatically complete all logical operations for you; you just need to wait for the profits to generate." This statement aligns perfectly with many users' preconceived notion that "AI = easy money," further lowering their vigilance.
Scammers guide users to access a highly realistic Remix IDE interface (which is actually a fake page) by using language that lowers the technical barrier. At first glance, the interface is indistinguishable from the real one. Users are asked to paste the so-called "contract code written by ChatGPT." After deployment, users are told to inject startup funds into the contract address as initial arbitrage capital, while scammers imply that "the more you invest, the higher the returns." After completing these steps and clicking the "Start" button, what awaits them is not a continuous stream of arbitrage profits but a total loss of funds. This is because the code that users copied and pasted already contains the scam logic: once the contract is activated, the deposited ETH is immediately transferred to the scammer's preset wallet address. In other words, the entire "arbitrage system" is essentially a beautifully packaged money-making tool.
SlowMist's analysis indicates that such scams employ a "wide net, small bait" strategy, resulting in individual user losses ranging from dozens to hundreds of dollars. Although the amount scammed from each user is relatively small, scammers can still obtain stable and considerable illegal profits by widely disseminating tutorials and enticing numerous users to fall for the trap. Since the amount lost by each victim is not large and the operation appears to be "self-completed" rather than a direct fraudulent transfer, most victims choose to remain silent and do not investigate further. Even more concerning is that these scams can easily rebrand and relaunch: scammers only need to change the bot's name or swap a few page templates to continue their fraudulent activities.
Other social engineering tactics include: Trojan job traps, fake interview programming tasks, phishing links in tweets/Telegram direct messages, similar address poisoning attacks, blocking the sale of "Pixiu" tokens, and fake staking platform rebate scams. These attacks continuously change their packaging forms through trust (private chat contact), greed (high return promises), or confusion (forged interfaces and chat records), leading to user fund losses in a covert manner that encourages user cooperation.
3.3 Ponzi Schemes: Old Wine in New Bottles
The rapid development of the crypto ecosystem has not eliminated traditional Ponzi schemes; rather, they have evolved alongside it. They utilize on-chain tools, social viral growth, and AI-driven deepfakes to undergo a "digital evolution." These scams typically disguise themselves as DeFi/NFT/GameFi projects to raise funds, engage in liquidity mining, or stake platform tokens. The essence remains the Ponzi structure of "new money paying old debts," collapsing when cash flow breaks or operators abscond with the funds.
The JPEX incident that shook Hong Kong in 2023 is a typical case. The platform claimed to be a "global exchange," promoting its platform token JPC through offline advertisements and celebrity endorsements while promising "high stable returns," attracting a large number of users without regulatory approval and lacking information disclosure. In September 2023, the Hong Kong Securities and Futures Commission marked the platform as "highly suspicious," and police arrested multiple individuals during "Operation Iron Gate." By the end of 2023, the case involved HKD 1.6 billion and over 2,600 victims, potentially becoming one of the largest financial fraud cases in Hong Kong's history.
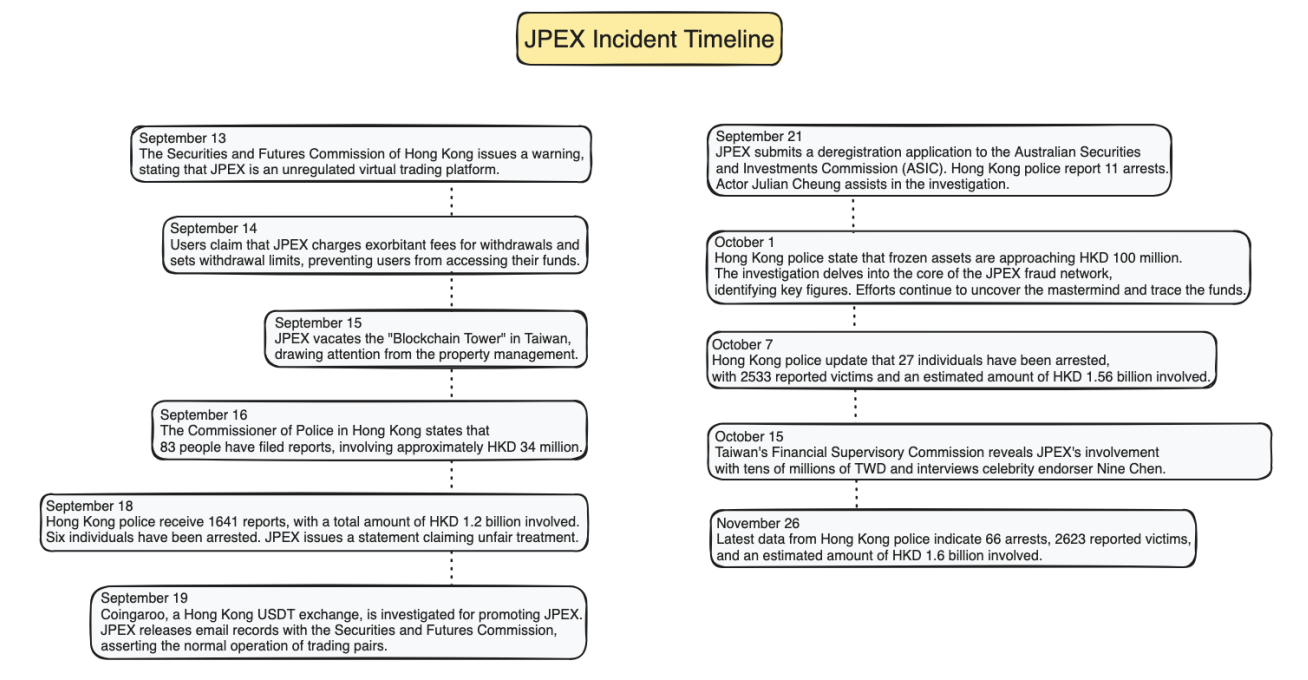
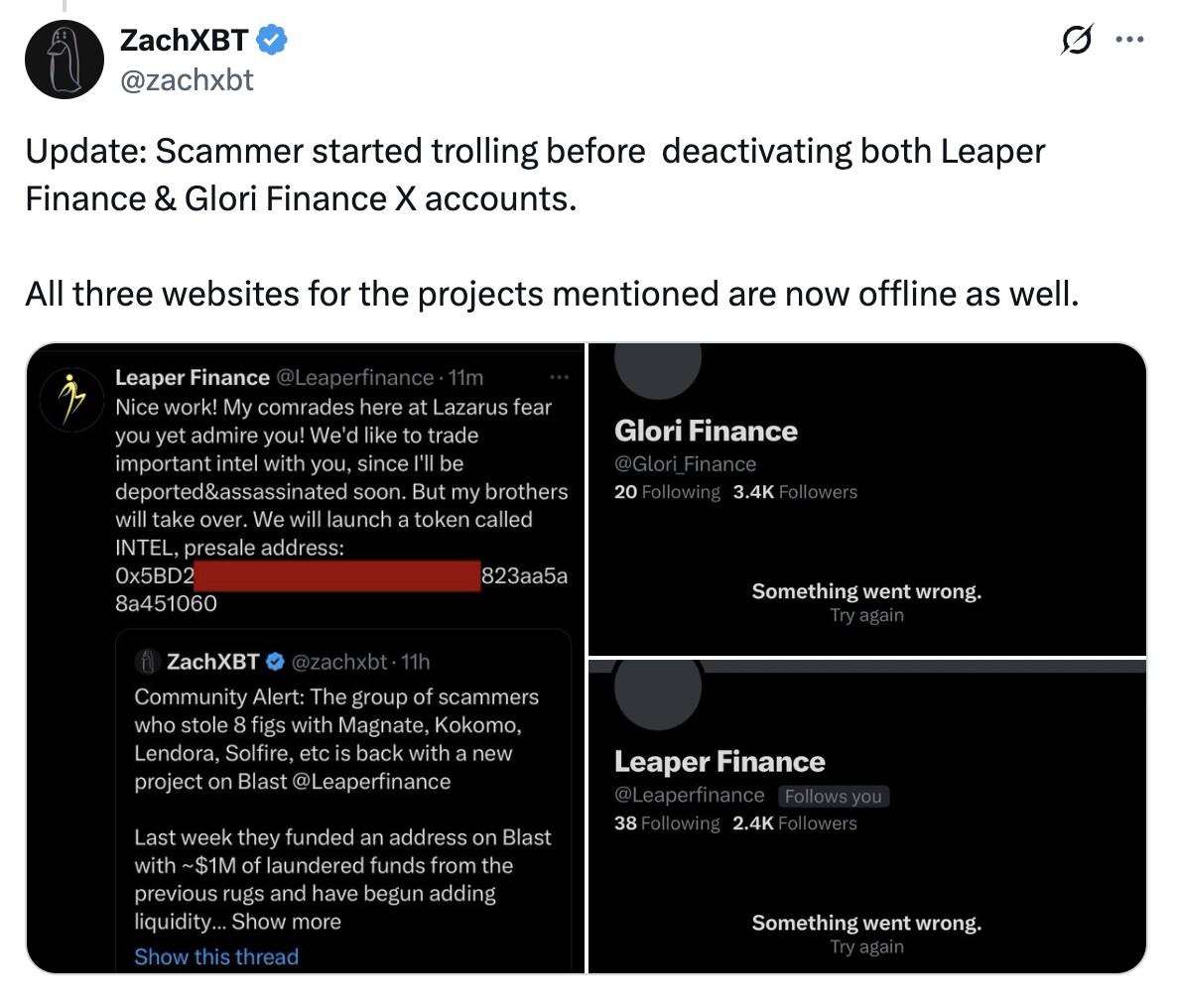
Additionally, the typical model of on-chain Ponzi projects is continuously evolving. In 2024, blockchain analyst ZachXBT exposed a scam group that deployed the Leaper Finance project on the Blast chain. This group had previously operated projects like Magnate, Kokomo, Solfire, and Lendora, stealing tens of millions of dollars. They forged identity verification documents and audit reports, pre-washed funds, and artificially inflated on-chain data to lure users into investing, quickly withdrawing liquidity after the TVL reached millions of dollars and absconding with the funds.
Even more shocking is that this group has repeatedly targeted multiple mainstream chains, including Base, Solana, Scroll, Optimism, Avalanche, and Ethereum, using a rapid "skin change and rebranding" rotation scam method.
For example, their Zebra lending project deployed on the Base chain once had a TVL exceeding $310,000; on Arbitrum, their Glori Finance project peaked at a TVL of $1.4 million. Both projects are forks of Compound V2. These projects used funds extracted from other scams like Crolend, HashDAO, and HellHoundFi as seed capital, forming a scam closed loop.
Compared to traditional Ponzi schemes, digital scams have the following new characteristics:
● More covert technical disguises: Using open-source contracts/NFT packaging/on-chain data accumulation to create a false impression of "technological innovation," misleading users into believing these are legitimate and compliant DeFi products.
● Complex rebate structures: Concealing cash flow under the guise of "liquidity mining," "staking rewards," and "node dividends," while actually extracting funds through multiple layers and manipulating both internal and external markets.
● Social viral propagation: Relying on WeChat groups/Telegram channels/KOL live broadcasts to drive user referrals, forming a typical multi-level marketing propagation model.
● Gamified interfaces and identity forgery: Many projects adopt game UIs and NFT project IPs to create a "youthful" and "legitimate" image. Some projects even combine AI face-swapping and deepfake technology to forge images or videos of project founders or endorsers, thereby increasing credibility.
For instance, in February 2025, hackers hijacked the X account of Tanzanian billionaire Mohammed Dewji, using deepfake videos to promote the fake token $Tanzania, raising $1.48 million within hours. Similar forgery techniques have been widely used to fabricate founder videos, create fake meeting screenshots, and forge team photos, making it increasingly difficult for victims to discern authenticity.
The following fraud red flag comparison table summarizes core warning signs and simple preventive measures for user reference.
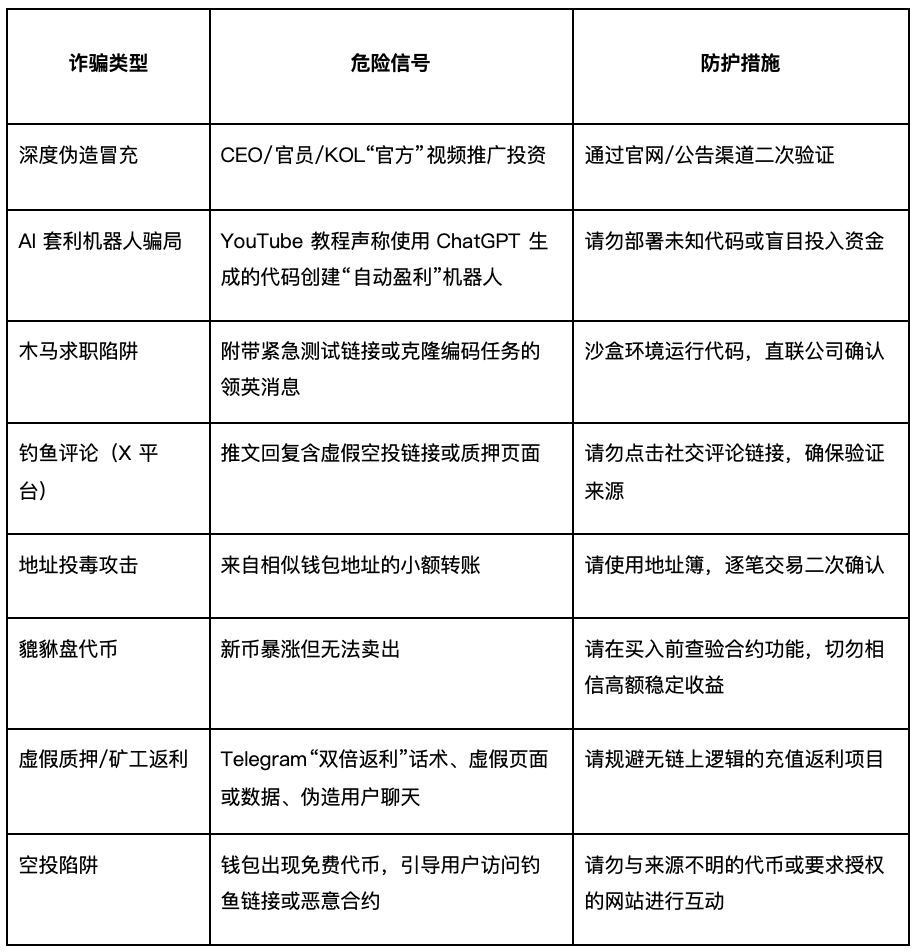
How to Ensure Safety: Remain vigilant against suspicious or unknown content — whether through LinkedIn, Telegram, or email; do not run unfamiliar code or install unknown files (especially under the pretext of work tests or application demonstrations); bookmark official websites; use browser plugins like Scam Sniffer; do not connect wallets to unknown links. Trust in the crypto world must be actively verified rather than passively given.
4. Reinforcing Digital Defenses: Bitget's Multi-Layer Security Architecture
In the face of increasingly complex digital asset threats, Bitget has built a comprehensive security framework aimed at protecting every platform user. This section introduces the strategic measures implemented in account protection, investment review, and asset protection.
1. Account Protection: Real-Time Blocking of Unauthorized Access
Bitget employs a complete set of real-time monitoring tools to detect and alert users to any unusual activity. When logging in from a new device, users receive detailed email notifications that include anti-phishing codes, verification codes, login locations, IP addresses, and device details. This instant feedback allows users to promptly identify and address unauthorized access.
To reduce impulsive actions that may arise from scams, Bitget has established a dynamic cooling-off period. This mechanism is triggered by indicators such as unusual login locations or suspicious transactions, temporarily disabling withdrawals for 1-24 hours, allowing users to reassess and confirm whether account activity is normal.
Additionally, Bitget provides an official verification channel that enables users to verify communication content and effectively prevent phishing attacks.
2. Investment Review: Strict Evaluation of Digital Assets
Bitget recognizes the surge of high-risk tokens in the crypto market, thus establishing a detailed due diligence process for asset listings, which includes comprehensive background checks on project teams, in-depth analysis of token economics, assessment of valuation and distribution models, and evaluation of community engagement levels.
To further ensure assessment accuracy, Bitget has implemented a dual-layer security audit system. Internal blockchain security engineers conduct thorough code reviews to identify vulnerabilities. At the same time, third-party authoritative organizations perform re-evaluations to ensure the review is thorough.
After assets are listed, Bitget's proprietary on-chain monitoring system continuously monitors transactions and contract interactions in real-time. This system is designed to adapt to new security threats, evolving and updating its threat model to quickly respond to emerging risks.
3. Asset Protection: Comprehensive Protection of User-held Assets
Bitget employs a dual wallet strategy, utilizing both hot and cold wallets to enhance security. Most digital assets are stored in offline, multi-signature cold wallets, significantly reducing the risk of cyber attacks.
Additionally, Bitget has established a substantial protection fund worth over $300 million to compensate users in the event of security incidents related to the platform.
For Bitget Wallet users, the platform additionally employs several security features, including phishing website alerts, built-in contract risk detection tools, and the innovative GetShield security engine. GetShield continuously scans decentralized applications, smart contracts, and websites to detect potential threats before user interactions.
Through this multi-layered security architecture, Bitget not only protects users' asset security but also enhances user trust in its platform, setting a benchmark for security standards in the cryptocurrency exchange industry.
5. On-chain Fraud Fund Tracking and Tagging
The previous sections of this report introduced how scammers deceive cryptocurrency users through various means, including the use of deepfake technology. Scammers typically attempt to transfer illicit funds and ultimately convert them into fiat currency. These fund flows can be tracked—blockchain analysis tools are crucial in this process. Such tools are mainly divided into three categories: transaction monitoring, address screening, and investigation tools. This section focuses on how transaction monitoring tools detect and tag fraud-related funds, increasing the difficulty of utilizing illicit funds.
Transaction monitoring tools have been widely adopted by cryptocurrency exchanges like Bitget. These tools identify and tag potential risks by scanning incoming and outgoing transactions. A typical application scenario includes checking all user deposits to identify potential risks. Most normal user deposits are not flagged as high risk, and funds are automatically processed and credited to user accounts in a timely manner; however, if the source of the deposit funds is from a known scam address, the funds will be marked as high risk.
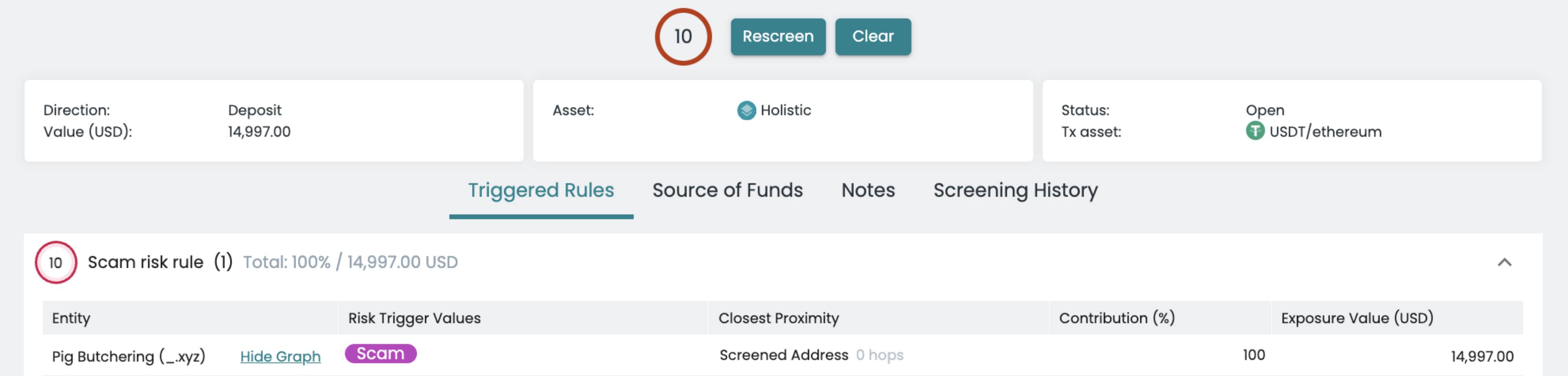
We can look at a practical example of transaction monitoring. The image below shows the analysis of user deposits at a cryptocurrency exchange by the transaction monitoring tool. As shown, a user's deposit was identified as a transfer associated with a "pig butchering" investment scam.
The tool gives a maximum risk score of 10/10, triggering a manual review process—user funds will not be automatically credited, and the activity will be handed over to the compliance team for manual verification.
Advanced criminal organizations are well aware of transaction monitoring mechanisms and often employ specific on-chain operations to obfuscate (i.e., hide) the flow of funds. A typical method is "fund layering": transferring illicit funds through multiple intermediate addresses in an attempt to sever the connection to the source. Advanced transaction monitoring tools can penetrate infinite layers of intermediate addresses to accurately locate the source of the financial crime. Criminal organizations are also increasingly using cross-chain bridges, which will be analyzed in the next section.
5.1 Cross-Chain Bridges
In recent years, various blockchains have been launched in the market. Users may be attracted to a particular blockchain because it hosts specific cryptocurrencies, decentralized applications, or other services. Cross-chain bridges allow users to transfer value across chains almost in real-time. While ordinary blockchain users are the primary users of cross-chain bridges, scammers are increasingly exploiting them to transfer illicit funds. Scammers typically have the following motivations for using cross-chain bridges:
● Obfuscation Opportunities: Specific obfuscation tools only support certain blockchains (e.g., most coin mixers only handle Bitcoin). Criminal organizations often cross-chain to the target blockchain to use obfuscation services before transferring to other blockchains.
● Increased Tracking Difficulty: Cross-chain transfers significantly increase the complexity of tracking funds. Even if investigators can manually track a single cross-chain action, repeated cross-chain operations will greatly slow down the investigation process, and if the funds are split, the feasibility of investigators manually tracking all leads will also decrease (the following case shows that dedicated tools can achieve seamless cross-chain fund tracking).
Criminal organizations are aware that some automated transaction monitoring tools will stop tracking at cross-chain bridges. The upper part of the image below shows how such tools halt at cross-chain bridges when identifying illegal activities, resulting in exchanges only seeing funds from bridging addresses without being able to trace the preceding path. The lower part of the image shows the Elliptic transaction monitoring tool used by Bitget, which automatically penetrates cross-chain bridges to fully restore the fund path, exposing related illegal entities.
The following case study describes how illegal entities utilize a series of cross-chain bridges and blockchains to systematically and deliberately attempt to launder cryptocurrency, as well as how to identify this activity using certain tools.
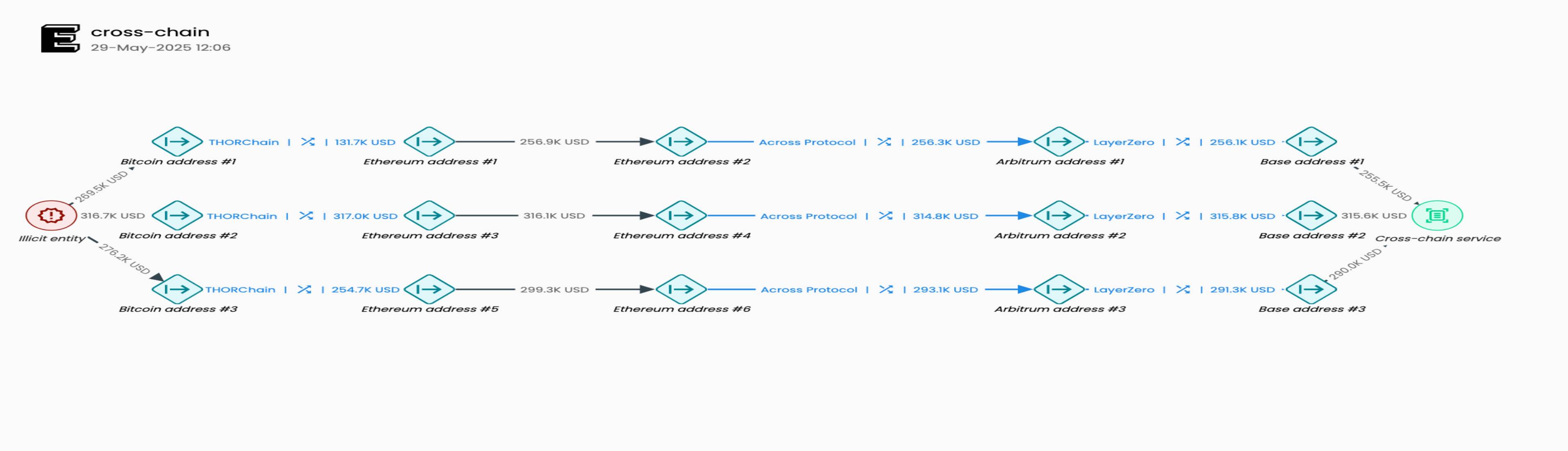
Case Study: The screenshot of the Elliptic investigation tool below shows how a criminal organization uses cross-chain bridges to transfer funds across multiple blockchains, ultimately depositing the funds into a cryptocurrency service platform.
Funds are initiated from the Bitcoin chain (left), cross-chain to Ethereum, internally transferred by switching addresses on Ethereum, cross-chain to Arbitrum, then cross-chain to the Base chain, and finally deposited into a cryptocurrency service platform. The image also highlights two other instances with the same pattern. Although not fully displayed, similar tactics appeared over a dozen times, reflecting the systematic nature of the money laundering behavior.
The purpose of this behavior is twofold: to delay the speed of investigators' tracking or to create interference; to prevent the receiving exchange from identifying the illegal source of the funds. However, blockchain investigation tools that support automated cross-chain bridge tracking can seamlessly restore the complete path. Transaction monitoring tools with cross-chain tracking capabilities (such as the Elliptic system used by Bitget) can automatically identify the original association of funds with criminal organizations.
5.2 How to Use Behavior and Patterns to Investigate Fraud Funds
The previous case relied on known illegal cryptocurrency address tags (such as pig butchering addresses), which typically come from multi-channel data collection such as victim reports and law enforcement collaboration. However, the scale of scams has expanded (along with low reporting rates from victims), making it impossible to cover all addresses.
Therefore, some advanced transaction monitoring tools have introduced behavior detection as a supplementary line of defense. By automatically analyzing behaviors and patterns, the system can infer whether a specific address is engaging in on-chain operations that match scam characteristics and mark related interactions for risk. Such behavior analysis is usually performed by specialized behavior detection models (some using machine learning techniques). As of now, Elliptic's behavior detection can identify over 15 types of scams (including pig butchering, address poisoning, ice fishing attacks, etc.), and its detection capabilities continue to expand.
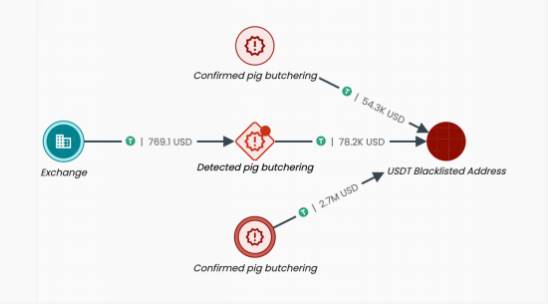
The example below demonstrates how behavior detection can prevent users from transferring funds to scam addresses: in this example, there are three addresses related to pig butchering. The top and bottom addresses have been identified and confirmed through victim reports. The middle address, although not reported, is marked as a potential pig butchering associated address by the behavior detection model.

This address subsequently received a transfer from a certain exchange. If that exchange had enabled behavior detection alerts, the risk could have been identified before the transfer, thus preventing user fund losses. Ultimately, all three pig butchering addresses directed funds to the same address, which was later frozen by Tether officials and blacklisted. All USDT held by that address were frozen, further confirming the illegal nature of the funds involved.
Click here to learn how Bitget increased its risk interception rate by 99% after integrating the Elliptic blockchain analysis tool—this industry-leading tool supports over 50 blockchains and has automated cross-chain bridge tracking and behavior detection capabilities.
6. Protective Recommendations and Best Practices
In the face of continuously evolving scam technologies, users need to establish a clear self-protection awareness and technical identification ability. To this end, SlowMist offers the following core anti-fraud recommendations:
(1) Enhance the ability to verify social media content
Never click on any links in the comments section or group chats—even if they appear "official." When performing key actions such as wallet binding, claiming airdrops, or staking, always verify through the project's official website or trusted community channels. It is recommended to install security plugins like Scam Sniffer to detect and intercept phishing links in real-time, reducing the risk of accidental clicks.
(2) Be wary of new risks introduced by AI tools
With the rapid development of large language model (LLM) technology, various new AI tools have emerged. The Model Context Protocol (MCP) standard has become a key bridge connecting LLMs with external tools/data sources. However, the widespread adoption of MCP also brings new security challenges. SlowMist has published a series of MCP security research articles and recommends that relevant project teams conduct self-checks and strengthen defenses in advance.
(3) Effectively use on-chain tools to identify risky addresses and Ponzi characteristics
For suspected exit scams or fraudulent token projects, it is recommended to use anti-money laundering tracking tools like MistTrack to check the risk of project-related addresses or quickly assess using GoPlus token security detection tools. Combine with platforms like Etherscan/BscScan to view victim comment section warnings. Maintain a high level of vigilance towards high-yield projects—abnormally high returns are often accompanied by extremely high risks.
(4) Do not blindly trust "scale effects" and "success stories"
Scammers often create a profit atmosphere through large Telegram groups, fake KOL endorsements, and forged profit screenshots. Generally, the credibility of a project should be verified through transparent channels such as GitHub repositories, on-chain contract audits, and official announcements. Users need to cultivate the ability to independently verify information sources.
(5) Guard against social trust-based "file inducement" attacks
Increasingly, attackers are using platforms like Telegram, Discord, and LinkedIn to send malicious scripts disguised as job opportunities or technical test invitations, luring users to operate high-risk files.
User protection guidelines:
● Be wary of suspicious job or freelance invitations that require downloading/running code from platforms like GitHub. Always verify the sender's identity through the company's official website or email, and do not be easily swayed by "limited-time high-return tasks."
● Rigorously review the project source and author background when handling external code, and refuse to run unverified high-risk projects. It is recommended to execute suspicious code in a virtual machine or sandbox environment to isolate risks.
● Exercise caution when handling files received from platforms like Telegram/Discord: disable automatic download features, manually scan files, and be wary of script execution requests under the guise of "technical tests."
● Enable multi-factor authentication and regularly change high-strength passwords to avoid cross-platform password reuse.
● Do not click on meeting invitations or software download links from unknown sources; develop the habit of verifying the authenticity of domain names and confirming the source of official platforms.
● Use hardware wallets or cold wallets to manage large assets, reducing the exposure of sensitive information on connected devices.
● Regularly update operating systems and antivirus software to guard against new types of malware and viruses.
If you suspect your device is infected, immediately disconnect from the internet, transfer funds to a secure wallet, remove malware, and reinstall the system if necessary to minimize losses.
Corporate Protection Guidelines:
● Regularly organize phishing attack and defense drills to train employees to recognize forged domain names and suspicious requests.
● Deploy email security gateways to intercept malicious attachments and continuously monitor code repositories to prevent sensitive information leaks.
● Establish a phishing incident response mechanism that integrates technical defenses with employee awareness. This multi-layered strategy helps minimize the risk of data breaches and asset losses.
(6) Remember the "Basic Principles" of Investment Judgment
● High return promises = high risk: Any platform claiming "stable high returns" or "capital protection with profit" should be regarded as high risk.
● Viral growth based on recruitment is a typical red flag: Projects that set up recruitment rebate mechanisms or "team profit" tier structures can be preliminarily identified as pyramid schemes.
● Use on-chain analysis tools to identify abnormal fund flows: Platforms like MistTrack can track large abnormal fund movements and analyze team cash-out paths.
● Verify the transparency of auditing institutions and teams: Be wary of "fake audit reports" provided by some projects or the formal endorsements of small auditing firms; users should confirm whether smart contracts have been audited by trusted third parties and whether the reports are publicly available.
In summary, cryptocurrency scams in the AI era have evolved from simple "exploitation of technical vulnerabilities" to a dual manipulation of "technology + psychology." Users need to enhance their technical identification abilities and strengthen their psychological defenses:
● Verify more, act less impulsively: Do not lower your guard due to "familiar faces, authoritative videos, or official backgrounds."
● Question more, transfer less: When it comes to asset operations, be sure to delve into the underlying logic, verify the source, and confirm safety.
● Avoid greed, maintain skepticism: The more enticing a project's "capital protection with profit" promise, the more vigilant you need to be.
It is recommended to read the “Self-Rescue Manual for the Blockchain Dark Forest” authored by SlowMist founder Cos to master basic skills in on-chain anti-fraud and enhance self-protection. In case of theft, users can seek assistance from the SlowMist team at this link.
Only by thoroughly understanding the mechanisms of fraud, improving information discernment, strengthening awareness of security tools, and standardizing operational habits can we safeguard asset security in the wave of risks in the tempting and risky digital age. Security protection cannot be a one-time effort; it requires continuous attention. Building a complete cognitive system and basic defensive habits is the only beacon for steady progress and avoiding fraud traps in the digital age.
7. Conclusion: Future Path Planning
Five years ago, anti-fraud meant "do not click suspicious links"; today, it means "what you see is not necessarily real."
As AI-generated videos, fake recruitment processes, and tokenized Ponzi schemes turn trust into a means of harming users, the next phase of crypto security relies not only on intelligent technology but also on collective defense. Bitget, SlowMist, and Elliptic are building a joint defense network through shared threat intelligence, automated fund tracking, and cross-ecosystem risk tagging.
The conclusion is clear: security cannot rely on isolated measures; a networked, continuous, and user-centered system must be built.
To this end, Bitget will vigorously promote three major directions:
● AI Red Team Attack and Defense Drills: Simulate new scam techniques to test system vulnerabilities.
● Compliance Data Collaboration Network: Collaborate with regulatory agencies and compliance partners to build an intelligence-sharing ecosystem.
● Promote Security Education: Empower users with real-time threat awareness through the anti-fraud center.
Scammers continue to evolve, and we must also upgrade and iterate. In this industry, the most precious currency has never been Bitcoin, but trust.
To download the full report, please click here.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




