Caution for 5 seconds, freedom for a lifetime.
Written by: Daii
TL;DR (Key Points)
Blue checkmark "CoinDesk Deputy Editor" invited me to record a podcast → Almost fell for a phishing app → 5 seconds of hesitation saved my wallet.
The real 0-Day lies in human nature: authority worship + time pressure = infinitely reusable vulnerabilities; over 40% of global crypto losses rely on scripted phishing.
The minimum defense = "5-4-3-2-1" countdown: pause for 5 seconds, raise 1 question, check 1 source—no matter how advanced the technology, it relies on this moment of clarity.
Originally, I was going to talk to you about the third part of "The Decentralization Trilogy" today, but I'm sorry, it has to be postponed for a while. Because in the past few days, I encountered something that almost changed my fate—
I almost got scammed, and it was almost without my awareness.
Last Friday morning, I opened my computer as usual. X (formerly Twitter) notified me that I had received a private message. Upon opening it, the identity of the sender immediately attracted me:
A legitimate profile, blue checkmark verified, ID: Dionysios Markou, claiming to be the Deputy Editor of CoinDesk.
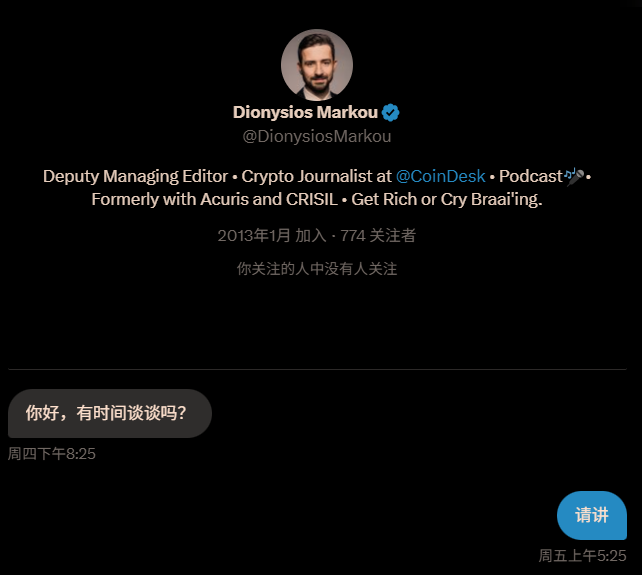
In our conversation, he told me:
I work at @CoinDesk, and we want to conduct a series of interviews with different members of the web3 community about the Asian crypto community. If you don't mind, we would like to invite you as our interview guest.
We plan to record a podcast and publish it on our website, Spotify, and other platforms.
This episode will delve into topics such as the future markets of Bitcoin/Ethereum/Solana, the MEME market, DeFi, and web3 projects in Asia.
Could you please let us know if you have time?
The content was concise and professional, and the format completely matched the common outreach invitations in the crypto media circle. I was intrigued: CoinDesk? A well-established media outlet in the industry, I'm very familiar with it.
I almost immediately agreed. Being an interview guest to discuss Bitcoin, Ethereum, Web3, and MEME projects is the ideal scenario for my content creation, right?
We scheduled to connect on Monday (May 12) at 10 PM.
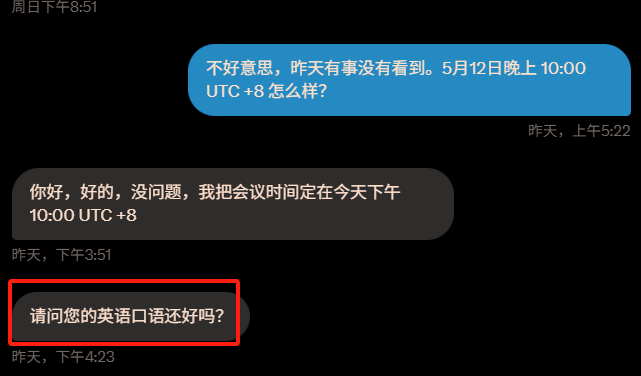
Please note the image above. The other party sent a message: "Is your spoken English okay?" This question would become an important premise for my potential scam.
On Monday night at 9:42, the other party greeted me on X, preparing to start the video.

I suggested using Teams, but the other party suggested using LapeAI instead, claiming that Teams did not have AI translation, which would allow for seamless Chinese and English conversation. They also sent me a screenshot indicating they were ready, along with the room number and invitation link, as shown in the image.
Although I had never used LapeAI, the other party's reasoning seemed reasonable. For safety, I did not click the link they provided but instead went to Google to search for LapeAI and found the following website.
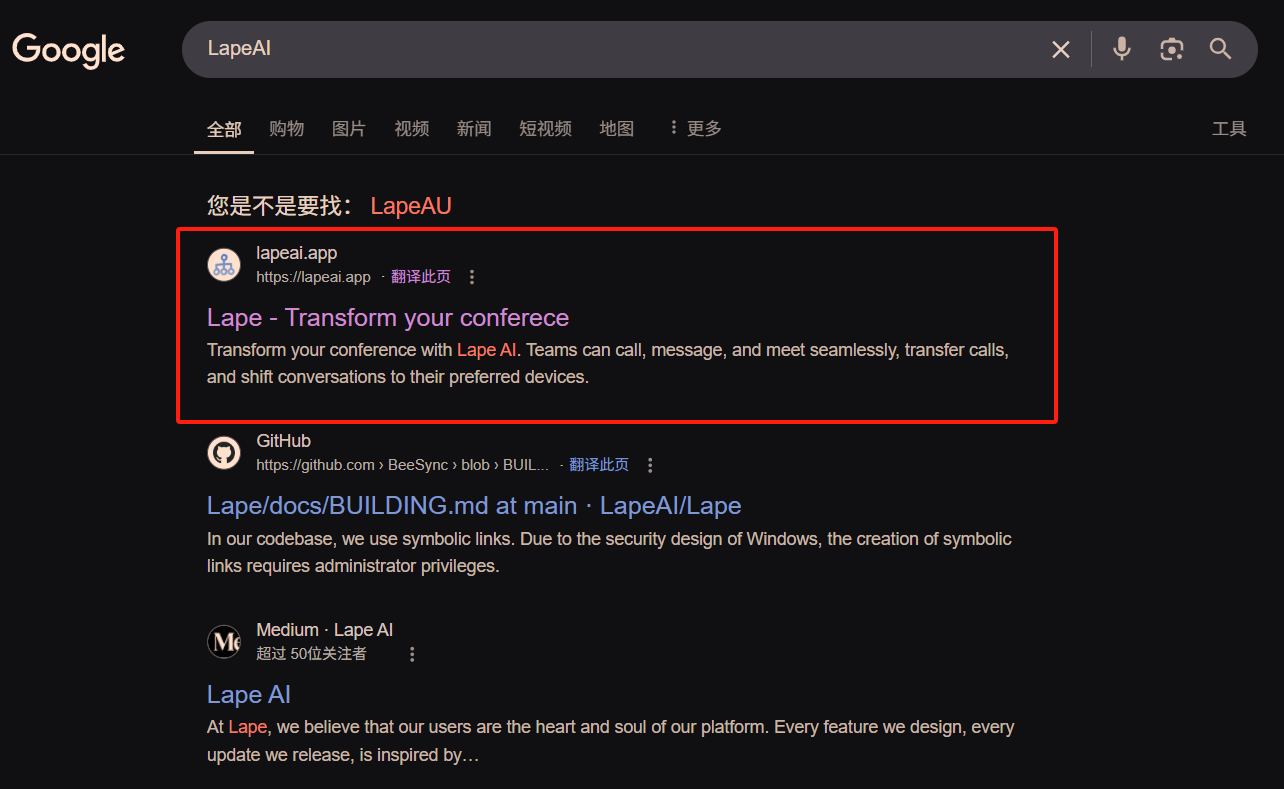
Upon opening it, I was startled; Chrome immediately warned me that this was a phishing site.
However, upon closer inspection of the domain name, the one they provided was LapeAI.io, while the Google search returned Lapeai.app, which had a different suffix, indicating they were two different websites. I directly typed Lapeai.io into the address bar, and indeed, there was no warning, as shown below.

Everything seemed normal, so I registered an account and entered the invitation code from the other party. Note that LapeAI.app and LapeAI.io were originally the same website. The .app version was discovered and subsequently, a new .io version was registered; you will understand as you read on.

After clicking the Synchronize button in the image above, what appeared was not a chat window, but the following page.

Note the content in the red box in the image above; although the other party did not ask me to click to download the app, the text above clearly stated that I needed to click the Sync button on both the website and the app simultaneously.
Why download the app? Isn't there a web version available?
Although I hesitated a bit, I still downloaded it. However, just as I entered the installation page below, I hesitated.
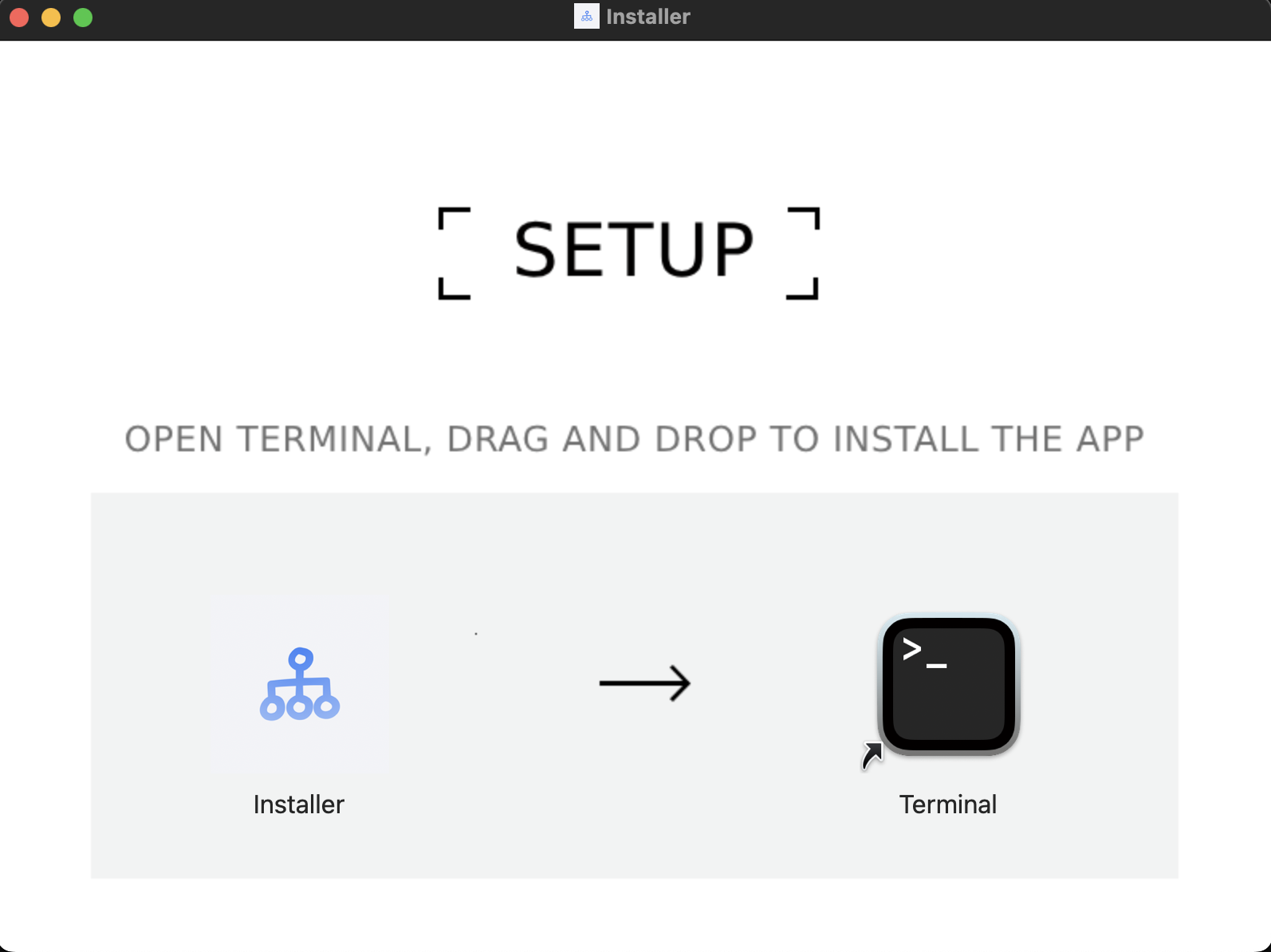
The reason for my hesitation was that this app was not installed directly but was to be run through the terminal, which I had never encountered before. So, I paused and thought about asking ChatGPT o3 to help me identify it. The result was shocking; see the image below.
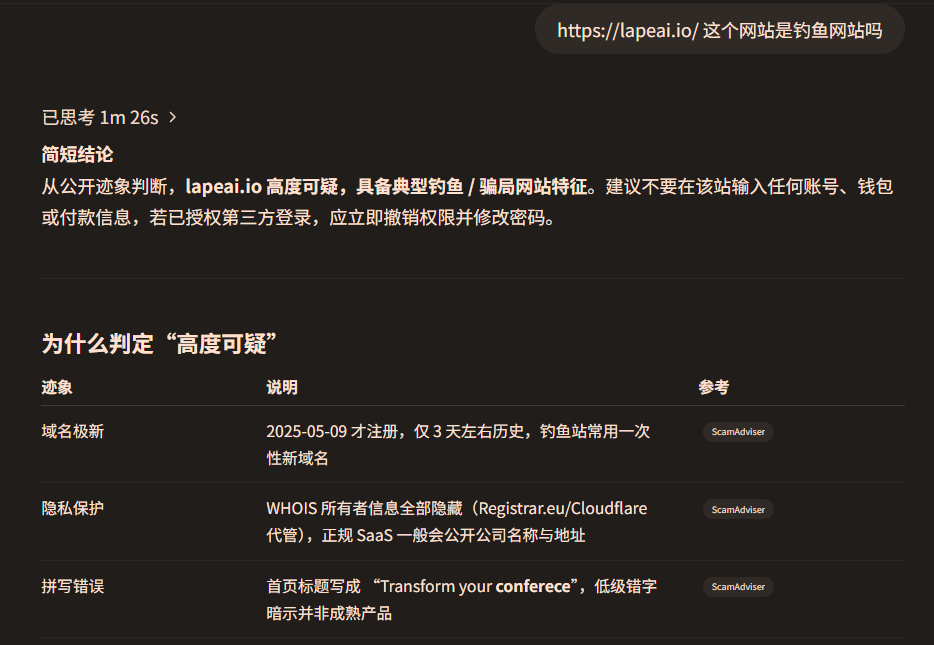
This investigation truly made me realize how close I had come to danger.
The domain registration date for lapeAI.io was May 9, 2025, just three days ago;
The owner information for this domain was hidden;
The page title even contained a clear spelling error: "Transform your conferece" (it should be "conference"). Note that this title is the same as that of the already marked phishing site LapeAI.app.
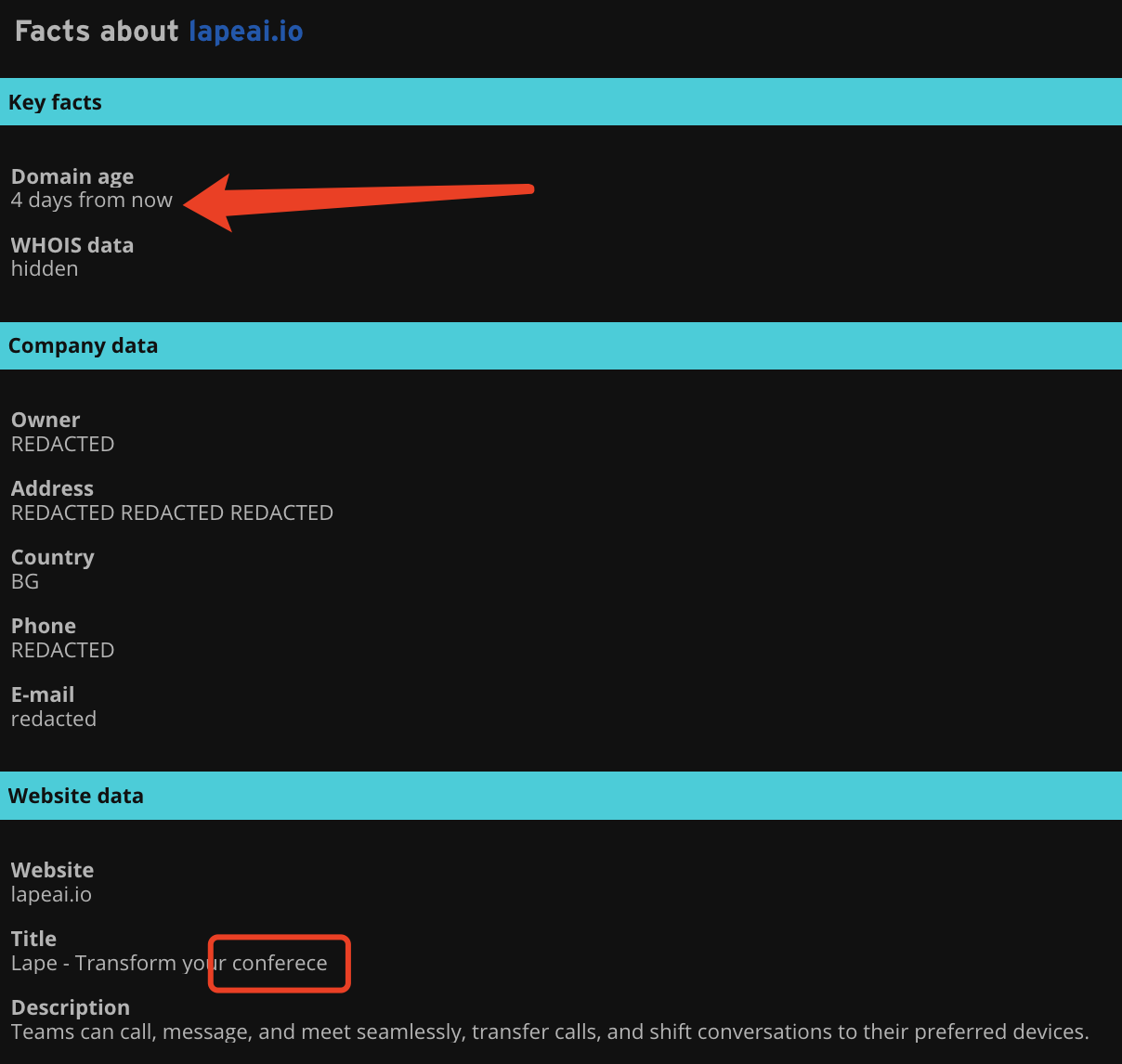
Any one of the three points above was enough to make me stop installing that suspicious program.
1. I Confirmed I Encountered a Scammer
I realized that this was not an interview invitation from CoinDesk; it was a meticulously packaged social engineering attack.

Looking back at that X (Twitter) account, although it had a blue verification, upon closer inspection, I found that this account had initially used Indonesian (see the image above) and had only recently changed to a Swedish crypto media editor identity. Moreover, its follower count was suspiciously low, only 774—far from the tens of thousands of followers that real CoinDesk editors typically have.
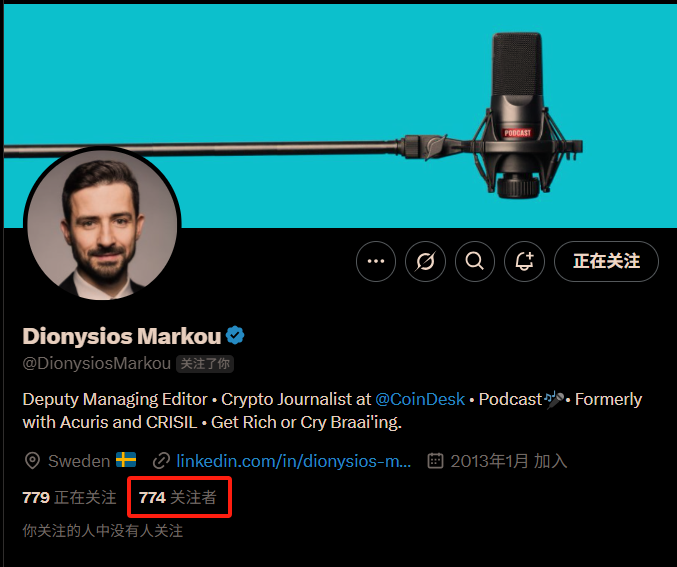
I realized that the other party was not a journalist but a scammer. Reflecting on the communication process, it was chilling.
From the initial private message response, confirming the time, registering the account, to almost clicking to run the installation package, I was just one step away from being scammed.
The other party knew I used Chinese and proactively mentioned AI translation; they knew I wrote about Web3 and specifically emphasized that this podcast episode would discuss Bitcoin, MEME, and Asian projects; they certainly knew CoinDesk's influence in this circle—using it as bait.
I was deceived in a tailored manner.
I began to realize that this was not a "random net scam," but a precise social engineering attack.
It did not use any hacking techniques, did not write a line of code, and did not send a virus link. It attacked my trust, my professional identity, and my "content creator's desire to be interviewed."
At that moment, I thought of a term—zero-day vulnerability (0-day vulnerability).

2. Human Nature 0-Day: An Everlasting Vulnerability, Always Online Attack
You may have heard of the term "0-Day vulnerability"—it represents the highest level of threat in the field of cybersecurity.
"0-Day" was originally a purely technical term. It first appeared in the underground BBS of the 1980s and 1990s: hackers used "zero-day software" to refer to programs that had been released for 0 days, were not publicly known, and had no patches available.
Because developers were unaware of the vulnerability, hackers could exploit it on "Day 0" to invade first; later, the term evolved into "zero-day vulnerability" itself, as well as "zero-day attack" targeting it. Common collocations with 0-day include:
Zero-day vulnerability (0-day vulnerability): The vendor is completely unaware, and no patch exists.
Zero-day exploit (0-day exploit): Attack code written for that vulnerability.
Zero-day attack (0-day attack): Invasion actions carried out using that vulnerability.
Due to the lack of patches and rules to intercept, zero-day attacks have always been regarded as the "highest level threat."
But you may have never thought that there exists a "0-Day vulnerability" within human nature itself.
It is not hidden in a segment of code on a server, but deeply embedded in the instinctive responses that humans have evolved over thousands of years. You think you are browsing the internet, working, or gathering information, but in reality, you are already exposed to countless psychological vulnerabilities that are set to default.
For example:
Do you automatically assume that a blue checkmark account is "official"?
Do you immediately feel anxious when you hear "limited spots" or "the event is about to end"?
Do you feel compelled to click and check when you encounter "abnormal login to your account" or "assets frozen"?
This is not stupidity or negligence; it is a survival mechanism evolved by humans. More accurately, it is the human nature 0-Day that has been weaponized after being repeatedly validated and refined by scammers and hackers.
2.1 What is Human Nature 0-Day?
We can understand this concept as follows:
Human nature 0-Day refers to those psychological vulnerabilities that can be repeatedly exploited by social engineering attacks but cannot be completely fixed by technical means.
Technical 0-Day vulnerabilities can be patched with a single fix. However, human nature's 0-Day is nearly impossible to eradicate. It is written in our desire for security, in our innate trust in authority, and in our instinctive impulses to "take advantage" and "not fall behind."
It does not require complex technology or code; it only needs a phrase, a familiar icon, or an email that "looks real." It does not need to invade your device; it only needs to bypass your brain—specifically, bypass the time you take to think.
Moreover, it has no "update" mechanism, and no antivirus software can block it. Every online person is automatically exposed to the attack range.

2.2 Three Characteristics of Human Nature 0-Day
The reason why "human nature 0-Day" is frightening is that it possesses three core characteristics that surpass technical vulnerabilities.
First, it transcends time. These psychological response mechanisms are almost written into the evolutionary genes of humanity. In the era of raw survival, our instinctive reactions to fear (such as seeing fire or snakes) were essential for survival; showing absolute obedience to the "leader" in a group was the foundation of group cohesion. Thousands of years later, these mechanisms still reside in the decision-making circuits of you and me.
Second, it transcends culture. Your nationality, educational background, or technical expertise does not matter. The famous North Korean Lazarus hacking group can phish Bybit employees in English, deceive defectors in Korean, and fool crypto KOLs on Telegram in Chinese. Language can be translated, but human nature needs no translation.
Finally, it can be reused in bulk. You might still be wondering if you are "being targeted." In fact, attackers no longer need to "target" anyone. A script, a set of phrases, can be copied and pasted to thousands of people. In scam parks in Cambodia and northern Myanmar, scammers can "go to work" after just 8 hours of "script training," generating millions of dollars each month—with almost no cost and a success rate far exceeding traditional phishing emails.
This is not a vulnerability; this is an industry.
2.3 Your Brain is Running a Default Open "Social Interface"
If we compare the human brain to an operating system, many of our thought responses are essentially a set of APIs that are always running—psychological interface functions.

These APIs have no code and cannot be turned off. As long as you are human, they are automatically open. For example:
Sending a private message from a blue checkmark account can trigger your trust mechanism in "authority";
Starting with "your account may have abnormal operations" can ignite your fear response regarding asset risk;
Adding "300,000 people have already participated" makes you feel "I can't miss out";
Then telling you "limited time to process, only 20 minutes left" compresses your rational judgment to the minimum.
Throughout the process, they do not need to hold you down, scare you, or even lie to you. They only need to present a script that aligns well with your expectations, allowing you to click the link, register on the platform, and download the app yourself—just like every step I took in my scam experience was voluntary and proactive.
So, what is truly frightening is:
You think you are "operating software," but in fact, you are the object being "called" by the "program."

This is no longer a scammer "phishing"; this is a phishing-as-a-service network composed of an entire script factory, customer service system, and money laundering process.
These types of attacks have no "fixable" vulnerabilities, only "eternally exploitable" human nature.
3. This is not just your crisis; it is a global cognitive war
After understanding the concept of "human nature 0-Day," I deeply realized that I am not an isolated case or an exception.
I am merely a pawn in this precisely targeted global psychological attack—just like millions of ordinary people, being manipulated in bulk by the same "social engineering script."
Hackers' weapons are no longer keyboards and code, but "context design, authority disguise, and trust scripts"; and the entire attack ecology has long evolved from "individual crimes" to an industrialized model of "content factories + script assembly lines."
3.1 The "Black Hole" of Crypto Assets: 43% of Losses Are Not Hacked, But Scammed
According to Chainalysis's "Crypto Crime Report 2025": In 2024, the direct losses caused by stolen crypto assets globally reached $2.2 billion, with private key leaks (often triggered by phishing, social engineering, etc.) accounting for 43.8%, approximately $960 million.
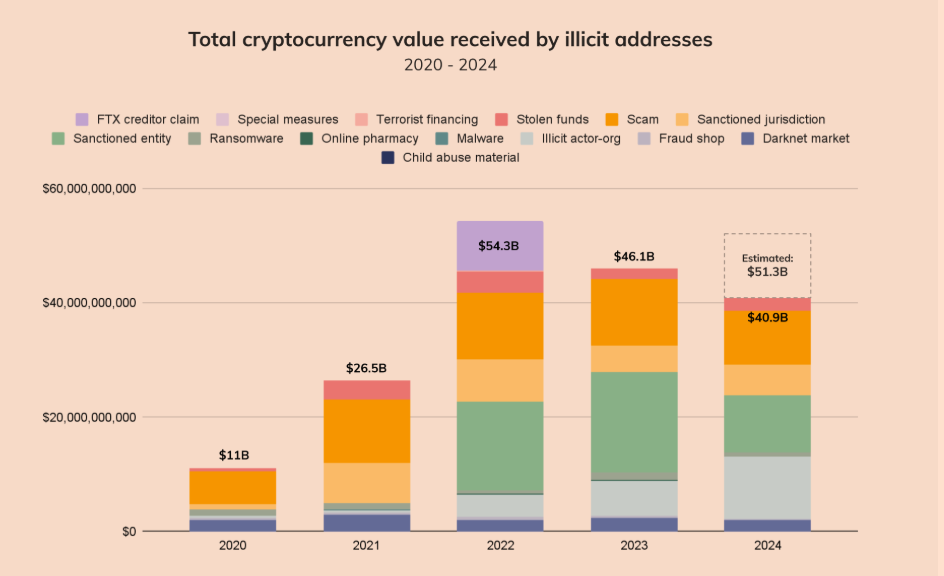
This means that nearly $2 out of every $5 lost is not due to technical vulnerabilities or attack scripts, but because human nature was precisely manipulated, and users voluntarily "handed over the keys."
These attacks do not invade wallets, crack contracts, or hijack nodes. They only need to send an email, a private message, a fake identity, or a "tailored inducement script."
Losses often occur at the moment of clicking the link or entering the mnemonic phrase.
This is not a system crash; it is each of us, under the cognitive model of "default trust," repeatedly opening the backdoor ourselves.
3.2 Hacker Script Factory: Lazarus Group's $1.3 Billion Cognitive Plunder
If you think these attacks are sporadic and unorganized, you need to get to know the world's "most professional" social engineering team—the Lazarus Group, backed by the North Korean state, operating globally.
According to tracking data from multiple security companies:
In 2024, Lazarus launched over 20 major social engineering attack incidents;
Targets included mainstream crypto platforms like Bybit, Stake.com, and Atomic Wallet;
Methods of operation included fake recruitment (resume + interview software), vendor disguise, collaboration emails, podcast invitations, etc.;
Annual asset theft exceeded $1.34 billion, accounting for nearly 61% of global crypto attack totals.
Even more astonishing is that these attacks utilized almost no system-level vulnerabilities, relying entirely on "scripts + packaging + psychological phishing."
You are not their technical target; you are their cognitive interface.
They study your language, habits, and identity information; they mimic the companies, friends, and platforms you are familiar with; they are not hackers but more like a psychological manipulation content team.

3.3 Hackers Do Not Attack Wallets, But Take Over Your Brain's "Trust System"
Let’s restore the essence of the entire situation:
Ultimately, this is not a disaster at the system level, but a collapse of default trust at the user level.
Attackers did not crack your wallet password, but they broke through those few seconds of hesitation in your cognitive system.
It was not a virus that took you down; it was you, step by step, walking towards the wrong "confirm" button within a well-packaged script.
You might think: "I am not an exchange employee, not a KOL, and I don't have many coins in my wallet, so no one should be targeting me, right?"
But the reality is:
Attacks are no longer "specially designed for you," but rather "as long as you fit the template, a script will be precisely thrown at you."
Have you publicly shared an address? They will come to "recommend tools";
Have you submitted a resume? They will come to "send interview links";
Have you written articles? They will come to "invite collaboration";
Did you mention a wallet error in a group? They will immediately come to "assist in fixing it."
They are not looking at whether you have money; they are looking at whether you meet the script-triggering conditions.
You are not an exception; you just happened to "trigger the automatic delivery system."
You are not naive; you just have not realized yet: human nature is the core battlefield of this era.
Next, I will break down the most critical tactical weapon in this war—the attack scripts themselves. You will see how they are meticulously refined step by step, with each move targeting the "default operating system" deep within you.

4. Scripted Attacks: Step by Step Calling Your "Human Nature API"
99% of social engineering attacks are not because you accidentally clicked the wrong thing, but because you were "guided step by step to click the right thing."
This may sound like a tall tale, but the fact is—
In the process where you think you are "just replying to a message" or "just registering on a platform," you have already fallen into the carefully orchestrated psychological script of the other party. Each step is not about violent control, but clever design, leading you willingly to the endpoint of the attack.
4.1 The Attack Process is a Chain of Cognitive Manipulation
Don't think that being "scammed" is just about clicking a certain link or downloading a certain app. The real social engineering attack is never about a single action; it is about a psychological process.
Every click, every input, every confirmation is actually the other party invoking the "behavior shortcuts" that are already written in your brain.
Let's break down the five most common attack scripts used by hackers:
【Step 1】Context Priming
Hackers first design a scenario that you are "willing to believe."
Are you a media person? They will claim to be a CoinDesk editor inviting you for an interview;
Do you work in a company? They say you have been selected to participate in a "high-level test";
Are you a Web3 developer? They pose as project partners inviting collaboration;
Are you an ordinary user? They scare you with "account anomalies" or "transaction freezes."
These scenarios are not rigid; they are highly aligned with your identity, role, and daily needs. They allow you to naturally immerse yourself without a second thought. This is the hook and the anchor.
▶ A classic case I analyzed involved a journalist who was scammed. He simply sought help from Ledger customer service on Twitter, and that "reasonable" message became the entry point for hackers' precise targeting.

【Step 2】Authority Framing
With an entry point established, trust must be built.
Attackers will use familiar visual symbols—blue checkmarks, brand logos, official tones.
They may even clone official website domains (for example, replacing coindesk.com with coindesk.press), adding realistic podcast topics, screenshots, or samples to make the entire narrative look "just like real."
▶ In my case, the other party wrote a CoinDesk position in their profile, covering topics like Web3, MEME, and the Asian market—perfectly hitting the psychological target for me as a content creator.
This tactic is designed to activate the "trust_authority()" function in your mind—you think you are judging information, but in reality, you are just defaulting to trusting authority.
【Step 3】Scarcity & Urgency
Before you have fully calmed down, the other party will immediately accelerate the pace.
"The meeting is about to start."
"The link is about to expire."
"If not processed within 24 hours, the account will be frozen."
—The purpose of such wording is singular: to make you unable to verify and just comply.
▶ In the classic case where Lazarus hacked Bybit, they deliberately chose to send "interview materials" via LinkedIn just before employees got off work, creating a dual psychological pressure of "time crunch + high temptation," precisely hitting the target's weak moment.
【Step 4】Action Step
This step is crucial. Hackers do not request all permissions at once; instead, they guide you to gradually complete each key action:
Click the link → Register an account → Install the client → Authorize access → Enter the mnemonic phrase.
Each step appears to be a "normal operation," but this is the rhythm design of the script itself.
▶ In my experience, the other party did not directly send a compressed file but instead used "invite code registration + synchronized installation" to disperse vigilance across multiple steps, creating the illusion that "it should be fine" at each stage.
【Step 5】Extraction
By the time you realize something is wrong, it is often too late.
At this stage, attackers either induce you to enter the mnemonic phrase or private key, or silently obtain your session, cookies, or wallet cache files through software backdoors.
Once the operation is complete, they will immediately transfer the assets and complete the mixing, withdrawal, and laundering processes in the shortest time possible.
▶ The $1.5 billion theft from Bybit was completed in a very short time, encompassing the entire process of permission acquisition, transfer splitting, and mixing, leaving almost no chance for recovery.

4.2 Why Does This Process Almost Never Fail?
The key lies in the fact that it does not defeat your technical system; rather, it leads you to "take down" your own defense system.
From the first step "who you are," to the second step "who you trust," then to the third step "you don't have time to think," and finally to "you pressed the execute button yourself"—this process is not violent but precisely layered, with each step targeting an "automatic reactor" in your psychology.
In psychology, this state is called Fast Thinking. It refers to when a person is anxious, excited, or under pressure, the brain skips logical analysis and makes decisions directly based on emotions and experiences. To understand the principles and mechanisms behind this, I recommend reading the book "Thinking, Fast and Slow."
What hackers excel at is creating an environment that puts you in a Fast Thinking mode.
So remember this crucial statement:
Social engineering attacks do not breach your defenses; they invite you to "open the door" step by step.
They do not break through your blockchain encryption algorithms but perfectly bypass the most critical "user-level firewall"—you yourself.
Now, if "human nature 0-Day" cannot be fixed by technology, is there a habit or a rule that can allow you to hit the pause button before the script is triggered?
The answer is: yes.
It is called the "5-Second Rule."

5. The 5-Second Rule: The Minimal Action Plan to Crack Human Nature 0-Day
By now, we can see very clearly:
The target of social engineering attacks is never your wallet or your phone—it is your brain's response system.
It is not a violent attack that breaks through defenses; it is a cognitive manipulation game of boiling a frog in warm water: a private message, a link, a seemingly professional conversation, guiding you step by step to "voluntarily" walk into the trap.
So, if the attacker is "programming you," how do you interrupt this automatic process?
The answer is actually very simple; you just need to do one thing:
Whenever someone asks you to enter a mnemonic phrase, click a link, download software, or claims to be an authority—force yourself to stop and count to 5 seconds.
This rule may sound trivial, but when executed, it becomes:
The lowest cost, highest return "human nature patch."
5.1 No Matter How Thick the Technical Defense, It Can't Stop Your Quick Hands
You might ask: "I'm not a novice; I use cold wallets, multi-signatures, and two-factor authentication. Why do I still need the '5-Second Rule'?"
Indeed, today's Web3 world has built a complete layered security tech stack:
Logging into accounts with Passkey;
Using Ledger or Trezor for offline transaction signing;
Opening suspicious links in a Chrome sandbox;
Validating every installation package with macOS Gatekeeper;
Monitoring device connection behavior with SIEM systems.
These tools are powerful, but the biggest problem is: you often do not have time to use them.
When you downloaded that app, did you check the signature?
Before entering the mnemonic phrase, did you compare the domain spelling?
When you clicked on a private message saying "system error, please fix," did you think to check the account history first?
Most people are not incapable of defense; they simply do not have time to activate their defenses.
That is why we need the "5-Second Rule." It is not anti-technology; it is about buying time for technology.
It does not fight the battle for you, but it can call you back before you "click too quickly."
It makes you think for a second: "Is this link reliable?"
It prompts you to check: "Who sent this?"
It gives you a pause: "Why am I in such a hurry to click?"
These brief 5 seconds are the time for your cognitive system to come online, and they are the prerequisite for all your technical defenses to take effect.
5.2 The Behavioral Science Logic Behind the "5-Second Rule"
Why is it specifically 5 seconds, rather than 3 seconds or 10 seconds?
This comes from the experimental evidence and neuroscientific explanations presented by behavioral writer Mel Robbins in her book "The 5 Second Rule" and TEDx talk.

Robbins discovered:
When you count down from 5-4-3-2-1 within the first 5 seconds of feeling an impulse to act and immediately take the first step, the prefrontal cortex of the brain is forcibly activated, thereby "seizing" the emotional brain's procrastination and avoidance pathways, allowing rational thinking to temporarily take over decision-making.
The countdown is essentially a form of metacognition ("metacognitive trigger"):
Interrupting inertia—counting down for a few seconds is equivalent to pressing the "pause button" on the brain, interrupting automated procrastination or impulsive behavior;
Activating rationality—the countdown forces you to focus on the present, awakening the prefrontal cortex and putting you into "slow thinking" mode;
Triggering micro-actions—once the countdown ends, moving or speaking immediately makes the brain perceive this step as a fact, significantly reducing resistance to subsequent actions.
Psychological experiments show that this simple technique significantly increases the success rate of participants in self-control, overcoming procrastination, and social anxiety scenarios; Robbins herself and millions of readers' cases have repeatedly confirmed this.
The 5-second countdown does not make you wait; it allows your rationality to "cut in line."
In social engineering scams, these 5 seconds are enough to switch you from "automatically clicking" to "questioning and verifying," thereby dismantling the time pressure of the other party's script.
Therefore, the "5-Second Rule" is not metaphysical; it is a "cognitive emergency brake" supported by neuroscience and metacognitive research.
It costs almost nothing but can bring all subsequent technical measures (two-factor authentication, cold wallets, browser sandboxes…) to the forefront at the most critical behavioral entry point.
5.3 High-Risk Scenarios: Stop Immediately in These 3 Situations, Don't Hesitate
I have summarized over 80% of the scenarios in which social engineering attacks occur. If you encounter any of the following three situations in real life, please immediately implement the 5-Second Rule:

Scenario 1: "There’s a problem with your wallet; I’m here to help you fix it."
You seek help on a social platform, and a few minutes later, a blue checkmark account claiming to be "official customer service" messages you, conveniently providing a "repair link" or "synchronization tool."
Stop: Do not reply or click on anything.
Think: What is the history of this account? Has the profile picture changed?
Check: Go to the official website to verify customer service channels or Google this domain.
Many scams start with this "timely help." You think the other party is coming to your aid, but in reality, it is a pre-set script.
Scenario 2: "Congratulations! You’ve been selected for beta testing / an interview / an interview."
You receive a well-formatted invitation email that appears to be from a major industry player, with a formal tone and attached PDF or download links.
Stop: Don’t rush to click the file; first check the sender's domain.
Think: Would Coinbase really use a zip attachment? Why would CoinDesk need to use LapeAI?
Look: When was this website registered? Is there a misspelled letter?
▶ My case is a typical example of this script. The other party did not use low-quality scams but rather sophisticated disguises. They are not here to scam you out of a meal; they are here to take over your wallet.
Scenario 3: "Your account has unusual login activity; please verify your identity."
This type of scam is the most common, featuring an alarming "warning email" or text message with an urgent link, accompanied by a tone suggesting "if not addressed, your account will be frozen."
Stop: Do not click the link in the text; go directly to the official website to verify.
Think: Would an official notification be this urgent? Does the tone sound like a template?
Check: Is the sender's email ending in google.com or g00gle.co?
These scenarios target your fear and sense of responsibility; once you click, the consequences are immediate.
5.4 Why Is This Rule Suitable for Everyone?
You don’t need to be a hacker hunter, learn cold signing, use cold wallets, or install a bunch of interceptors and plugins. You just need to:
Count down 5 seconds
Ask yourself one question
Check the source (Google / domain / tweet history)
This is the "behavioral patch" you apply to the "human nature 0-Day."
This rule has no barriers, no costs, and does not rely on technological updates. It only depends on whether you are willing to stop and think at critical moments.
This is the simplest, most practical, and most universal "human firewall" to crack script attacks.

Conclusion: Be Cautious for 5 Seconds, Enjoy Freedom for a Lifetime
Initially, I just wanted to document an experience of "almost being scammed."
Seeing cloned scam websites, similarly misspelled webpage titles, and phishing domains registered just three days ago… I realized:
This is not an individual misjudgment but an entire script assembly line, harvesting trust globally in bulk.
It does not rely on technical attacks but on that one second of hesitation when you "click."
You think cold wallets are invincible, yet you hand over your mnemonic phrase; you think blue checkmarks are trustworthy, but that’s just an $8 disguise; you think you are unimportant, yet you just happened to walk into the script they wrote.
Social engineering attacks do not breach systems; they gradually hijack your cognition.
You do not need to master cold signing or study address authorization; you just need a small habit:
At critical moments, force yourself to stop for 5 seconds.
Look at this account, this link, this reason, and see if it is worth your trust.
These 5 seconds are not slow; they are clarity; they are not suspicion; they are dignity.
When cognition becomes a battlefield, every click you make is a vote.
Be cautious for 5 seconds, enjoy freedom for a lifetime.
May you not be the next victim, and may you share this message with the next person who might not have time to hesitate.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




