This report provides a detailed analysis of the various security vulnerabilities and attack surfaces currently present.
Although blockchain technology demonstrates immense potential in decentralization, security, and trust mechanisms, its ecosystem still harbors a variety of security risks. From various vulnerabilities in L1/L2 cross-chain communication (such as not considering block rollbacks, improper handling of transaction failures, and light client validation flaws) to the hidden dangers in Cosmos application chains regarding module order, random number usage, and transaction rollbacks, as well as risks arising from script construction, UTXO handling, and rollbacks in the Bitcoin expansion ecosystem, all pose severe challenges to blockchain applications. Meanwhile, common errors in smart contracts or general programming languages, such as integer overflow, infinite loops, race conditions, and abnormal crashes, also significantly threaten the system's availability and security.
Additionally, the vulnerabilities of P2P network architecture (such as Sybil attacks and Eclipse attacks) and DoS attacks can also hinder the efficiency and reliability of blockchain systems, while cryptographic vulnerabilities (insecure hash algorithms, weak signature algorithms, insecure random number generation, etc.) further threaten data confidentiality and integrity. Improper handling of transaction memory pools, orphan blocks, and Merkle trees at the ledger level can lead to inconsistencies in on-chain data or asset risks. Finally, if the design of economic models and governance mechanisms is lacking, it may lead to imbalances or even fragmentation in network incentives, allowing attackers to exploit this imbalance to affect system stability.
In light of the aforementioned risks, only by deeply understanding and taking rigorous preventive measures can we ensure the security and sustainable development of the ever-evolving blockchain ecosystem. At the end of 2024, ScaleBit's parent brand BitsLab released the "2024 Emerging Ecological Public Chain Panorama Observation and Security Research Report." This report provides a detailed analysis of the various security vulnerabilities and attack surfaces currently present, with rich and practical content. This article extracts some content from the report, aiming to focus on presenting key types of security vulnerabilities in the blockchain ecosystem, helping readers prepare in advance and jointly promote the safe and healthy development of the industry.
Read the original report: https://bitslab.xyz/reports-page

1) List of Security Vulnerability Types
1.1 L2/L1 Cross-Chain Communication Vulnerabilities
Cross-chain communication is an important means to enhance the interoperability of the blockchain ecosystem, but there are many security risks in its implementation. The following are the main points of concern:
L2 does not consider L1 block rollbacks
When sending L1 transactions or retrieving data on the L1 chain, if this situation is not considered, it may lead to asset loss.
L2 does not check whether transactions sent to L1 are successful
Due to issues such as network problems and gas fees, the sent transaction may fail. If this situation is not considered, it may lead to asset loss for projects or users.
On-chain event forgery
When cross-chain bridges listen to on-chain events, they do not verify whether the events come from the specified contract address, allowing other contracts to forge events.
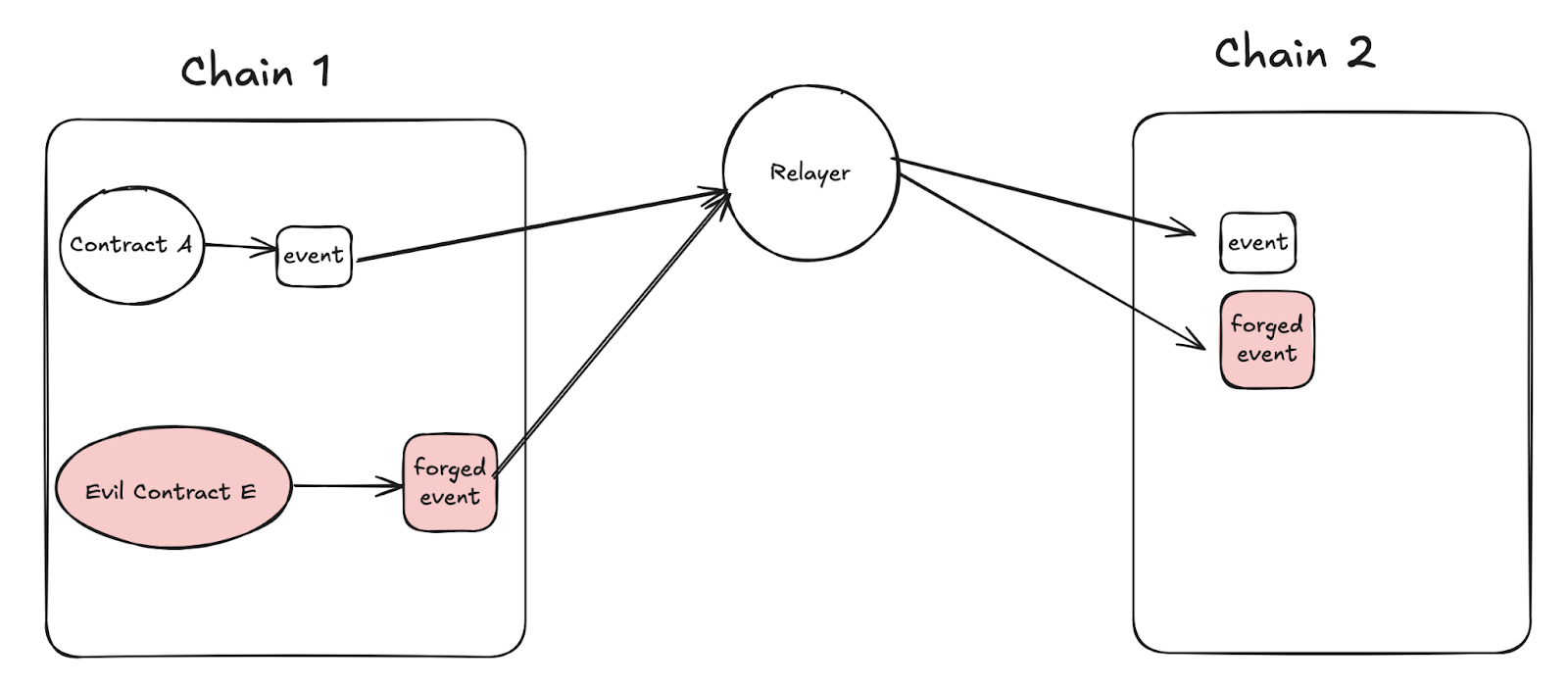
The same transaction contains multiple on-chain events
A single transaction can contain multiple events; if this situation is not considered, it may lead to asset loss for projects or users.
Light client validation vulnerabilities
PoW chains do not consider private mining attacks
Do not use the officially recommended algorithms
Man-in-the-middle hijacking
In L2/L1 cross-chain communication, the message transmission mechanism is crucial, and it is necessary to ensure the integrity and confidentiality of messages during transmission. Messages transmitted between different chains may face risks of being tampered with or monitored, so encryption methods must be used to protect the security of information. Additionally, ensuring the non-repudiation of messages during inter-chain forwarding is also key to prevent malicious tampering of information.
Delay and finality issues
Cross-chain communication often faces issues of delay and finality. Due to different consensus mechanisms and confirmation times of different chains, the confirmation time of cross-chain transactions may be inconsistent, leading to delays in state updates and increasing potential security risks. When designing cross-chain protocols, the definition of finality must be clear to ensure the consistency of transaction states and prevent double-spending attacks or state inconsistency issues caused by confirmation delays.
1.2 Cosmos Application Chain Vulnerabilities
As an ecosystem centered on blockchain interoperability, Cosmos allows different blockchains to connect through IBC (Inter-Blockchain Communication protocol). However, there may also be some vulnerabilities and security risks in the implementation of Cosmos application chains. The following are the main points of concern:
BeginBlocker and EndBlocker crash vulnerabilities
BeginBlocker and EndBlocker are optional methods that module developers can implement in their modules. They are triggered at the beginning and end of each block, respectively. Using crashes to handle errors in BeginBlock and EndBlock methods may cause the chain to stop running when an error occurs.
Incorrect use of local time
Due to differences in local time among different nodes, if this is not considered during consensus generation, it may lead to consensus issues.
Refer to the content:
Image source
https://forum.cosmos.network/t/cosmos-sdk-security-advisory-jackfruit/5319
Incorrect use of random numbers
Due to different random numbers generated by different nodes, if this is not considered during consensus generation, it may lead to consensus issues.
Incorrect use of map iteration functions
The iteration of maps in Go language is non-deterministic; if this is not considered during consensus generation, it may lead to consensus issues. Example code is as follows:
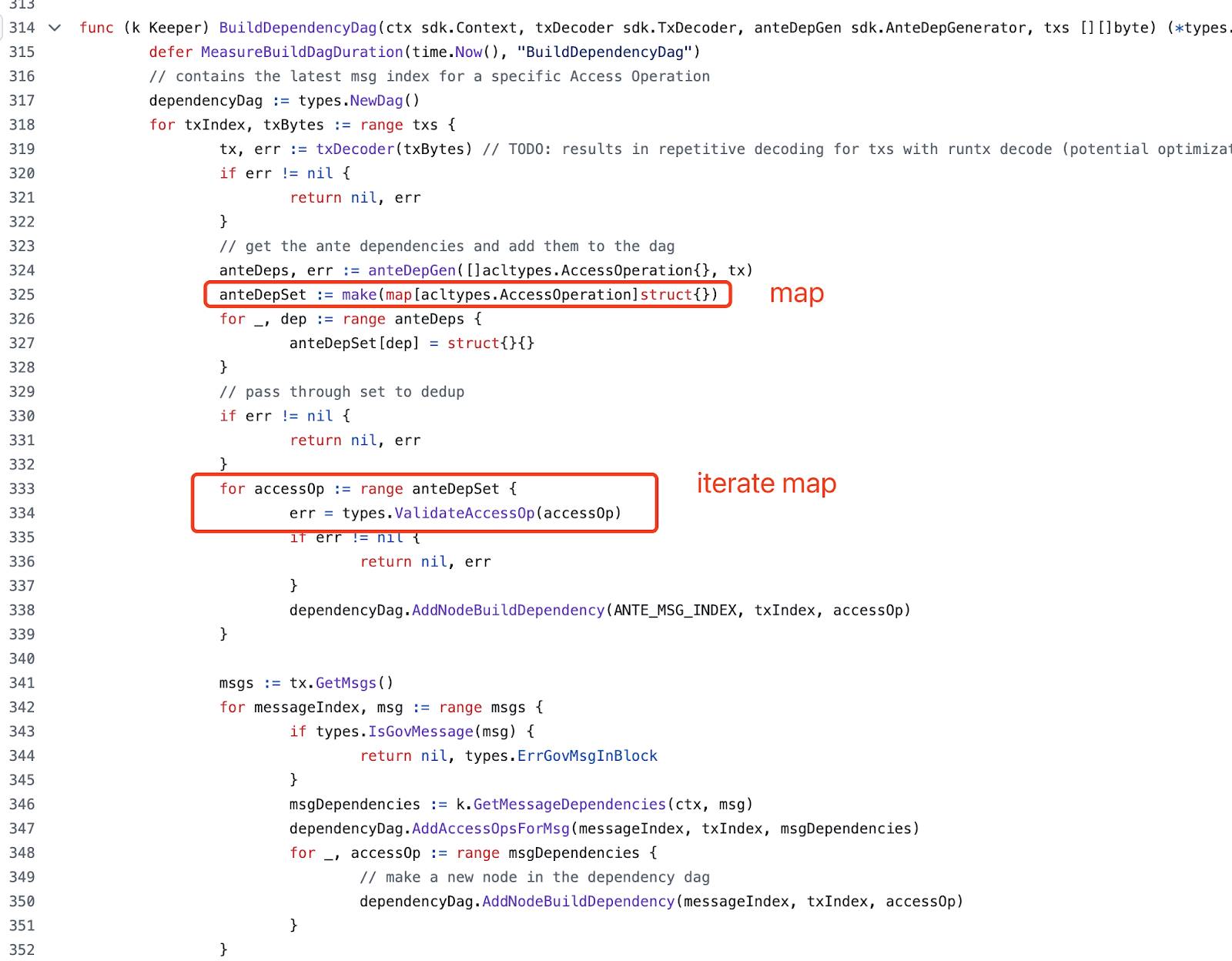
Issues caused by unreasonable module order
Cosmos application chains consist of multiple modules, and in certain event handling, the modules are ordered. If the order is set unreasonably, it may lead to security issues.
Transaction failure but data not rolled back
In Cosmos application chains, if a transaction execution fails but, due to design flaws, the data state fails to roll back to the state before the transaction execution, it may lead to inconsistencies in on-chain data. This situation not only affects user trust but may also result in financial losses. Therefore, it is essential to ensure that smart contracts can properly handle failed transactions, ensuring state consistency and reliability, and implement automatic rollback mechanisms when necessary.
Incorrect state validation
The state validation logic in Cosmos application chains needs to be very rigorous. If state validation is inaccurate, it may lead to illegal transactions being confirmed, thereby affecting the security of the chain. Developers need to carefully design state transition logic and conduct comprehensive testing to prevent vulnerabilities caused by incorrect state validation.
Cross-chain message passing security
Cosmos's IBC mechanism allows messages to be passed between different application chains, but this also introduces potential security risks. For example, if cross-chain messages are tampered with during transmission, it may lead to incorrect state updates or attackers exploiting the message for malicious operations. Encryption and signing mechanisms should be adopted to ensure the integrity and authenticity of messages, preventing tampering during transmission.
Contract upgrade and version management issues
Contracts in Cosmos application chains may need to be upgraded during use, but improper contract upgrades may lead to incompatibility of old contract states or security vulnerabilities. Developers need to establish clear contract upgrade strategies, including version management and migration plans, to ensure that the normal operation of the chain is not affected during upgrades.
Economic model and incentive mechanism
The design of the economic model in the Cosmos ecosystem directly affects the security and stability of the chain. If the incentive mechanism is set unreasonably, it may lead to imbalanced participant behavior, resulting in malicious behavior or economic attacks. A comprehensive assessment of the economic model is needed to ensure that the incentive mechanism effectively maintains the security and health of the network.
Governance mechanism vulnerabilities
The governance mechanism of Cosmos application chains allows token holders to participate in chain decision-making, but if the governance mechanism is poorly designed, it may lead to governance attacks or centralization issues. It is essential to ensure the fairness and transparency of the governance mechanism to prevent a minority from manipulating the chain's decision-making process.
1.3 Bitcoin Expansion Ecosystem Vulnerabilities
Bitcoin script construction vulnerabilities
Bitcoin scripts are often generated and deployed in real-time on Bitcoin, and the content of the scripts includes data provided by users. If the script construction is insecure, it may lead to asset loss.
Vulnerabilities due to unconsidered derivative assets
Common Bitcoin derivative assets include inscriptions and runes. If L2 only considers the native BTC when operating user assets without considering derivative assets, it may lead to user asset loss.
UTXO amount calculation errors
Mistakes in calculating transaction fees
Mistakes in calculating change amounts
For example, in the following code, the change output calculation includes a condition: change output will only be added if the change amount is greater than or equal to 546 satoshis. This value corresponds to the dust limit for traditional P2PKH transactions. However, the dust limit varies for different address types. Specifically, for Taproot addresses, the dust limit is 330 satoshis.
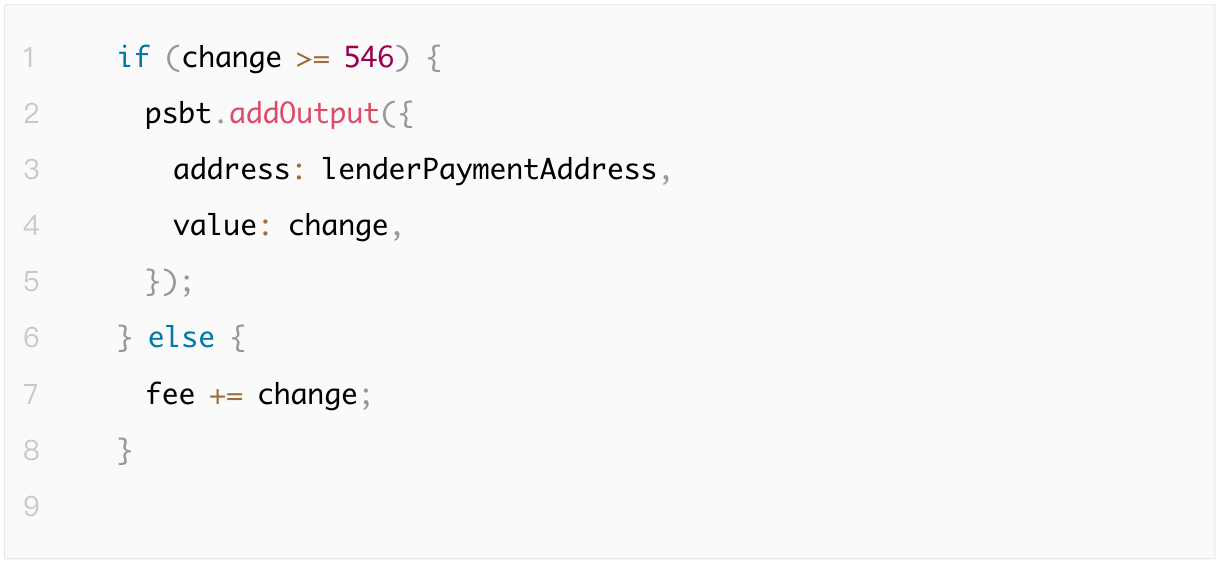
This hardcoded value does not consider the lower dust limit for Taproot addresses, which may lead to the loss of small assets in transactions involving Taproot addresses. Detailed information about the dust limits for various address types can be found in the Bitcoin Core source code and discussions on the BitcoinTalk forum.
https://bitcointalk.org/index.php?topic=5453107.msg62262343#msg62262343
UTXO not checked for "op_return"
UTXOs with "op_return" are unspendable.
SPV validation vulnerabilities
No verification of block header timestamp
No verification of block header proof of work
Not considering rollback situations
Since Bitcoin is based on PoW, block reorganization occurs frequently. When sending Bitcoin transactions or retrieving data on the Bitcoin chain, if this situation is not considered, it may lead to asset loss.
Not considering whether Bitcoin transactions are successfully sent
Bitcoin transactions may not necessarily be packaged by miners after being sent, so it is necessary to check whether the transaction has been successfully included in the blockchain. At the same time, third parties can construct transactions with higher fees to keep the transactions sent by L2 in the transaction memory pool for a longer time instead of being packaged.
Confusion between absolute time locks and relative time locks
When constructing Bitcoin scripts, confusing these two types of time can lead to severe asset loss.
Improper time settings for Hash Time Locked Contracts (HTLC)
Common situations include the following three:
Time set too large
Time set too small
L1 and L2 time not synchronized
1.4 Common Vulnerability Types in Programming Languages
1.4.1 Integer Overflow
Integer overflow occurs when a value exceeds the range that the type can represent, leading to value wrapping or logical errors, affecting the accuracy of program data. Rust automatically detects overflow in debug mode, while Go requires manual boundary checks.
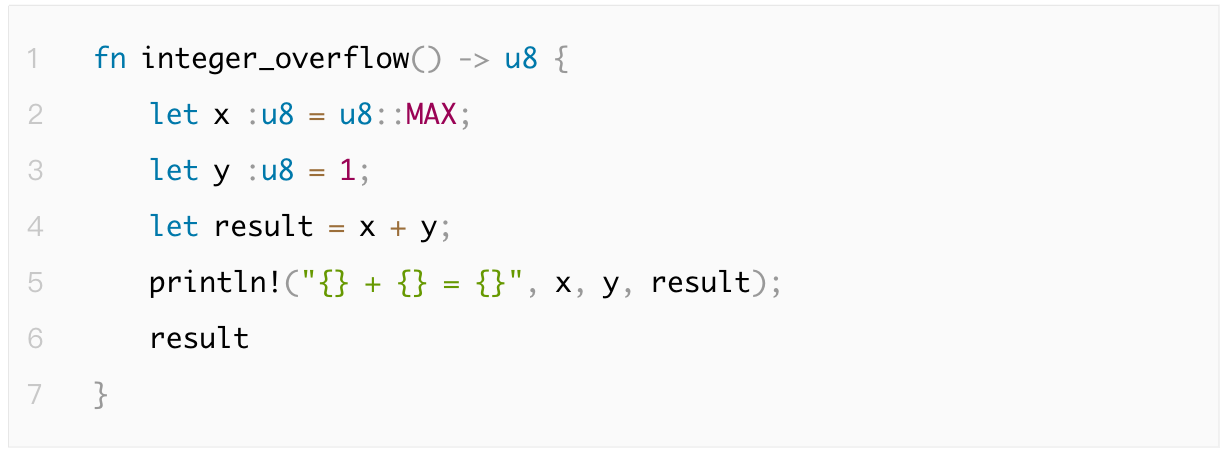
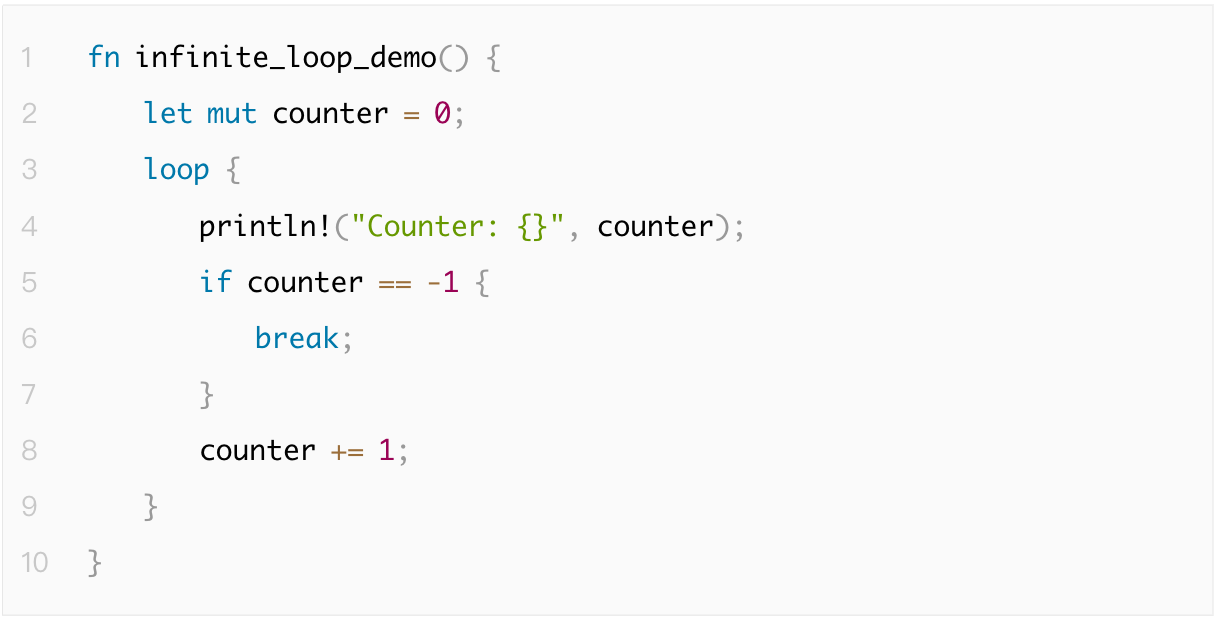
1.4.2 Infinite Loop
An infinite loop occurs when a program enters a loop indefinitely under certain conditions, consuming system resources and causing the program to freeze or become unresponsive. The key to avoiding this issue is to set reasonable loop exit conditions and use Rust's timeout mechanism or Go's context package to control long-running loops.
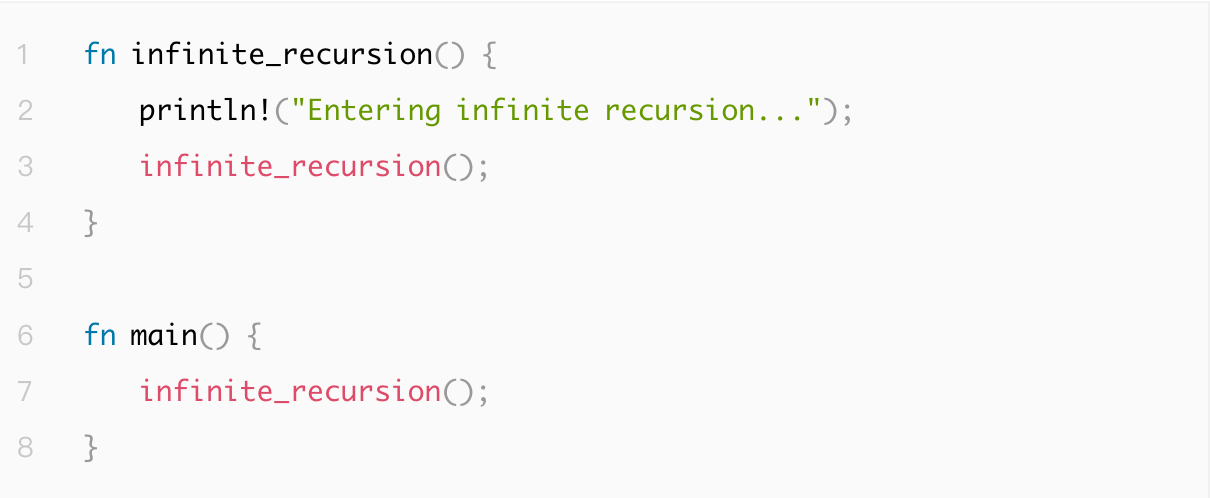
1.4.3 Infinite Recursive Calls
Infinite recursive calls refer to a recursive function lacking a termination condition, leading to stack overflow and crashes. Ensuring that recursion has clear base conditions and limiting recursion depth as needed can effectively prevent this issue.
Rust will display stack overflow errors in debug information, similar to the following output:

1.4.4 Race Conditions
Data races occur when multiple threads access shared resources unsynchronized, leading to data inconsistency. Rust avoids race conditions through ownership mechanisms and thread-safe libraries, while Go provides concurrency support through channels and the sync package.
The following Unsafe Rust example demonstrates two threads simultaneously accessing and modifying the same shared variable, leading to undefined behavior. This code causes a data race because no synchronization mechanism is used to protect the shared resource:
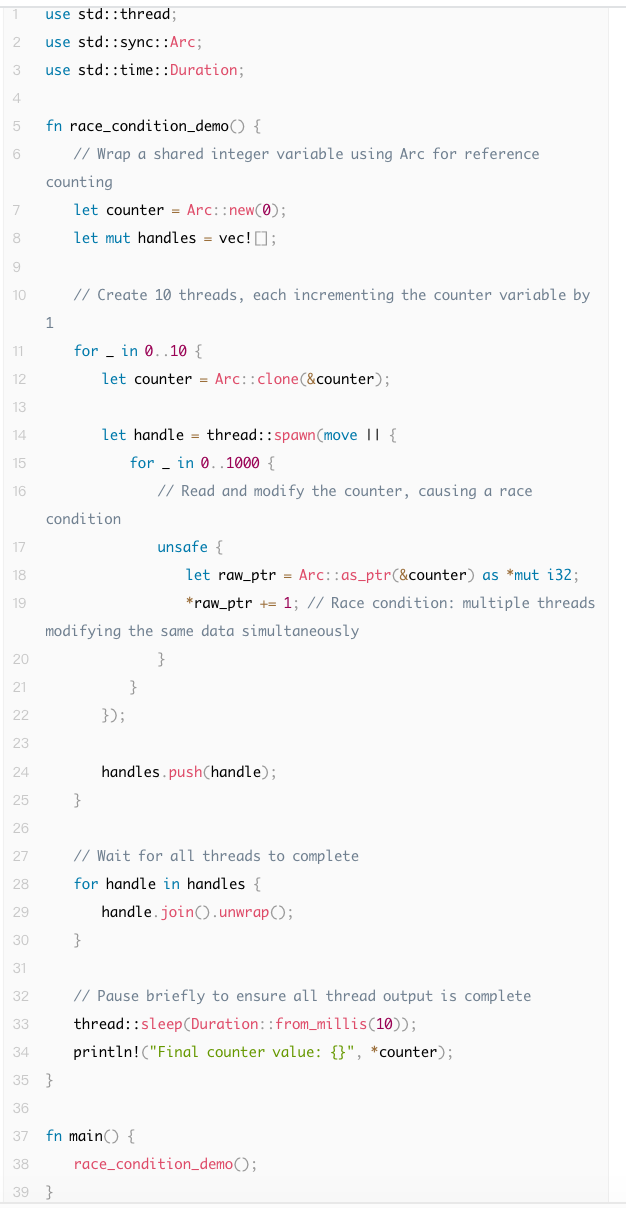
Although Safe Rust prevents data races, logical races may still occur. A logical race condition refers to a situation where code may produce unexpected behavior under a specific execution order. For example, in the following scenarios:
- Time-sensitive operations: The order of operations between two threads may affect the final logical result. For example:
a. One thread checks whether a certain condition is met, while another thread modifies that condition during this time. This can be coordinated in Rust using synchronization mechanisms like ArcMutexT>>, but it cannot prevent logical race conditions.
Double-Checked Locking: If multiple threads attempt to initialize a shared resource and all believe the resource is uninitialized, it may lead to logical errors. In this case, although data races do not occur, unexpected logical errors may arise.
Incorrect lock order: If multiple locks are used, threads may acquire locks in inconsistent orders, potentially causing deadlocks. Rust's type system cannot prevent this type of deadlock race condition.
The following demonstrates a race condition vulnerability in Safe Rust. In this example:
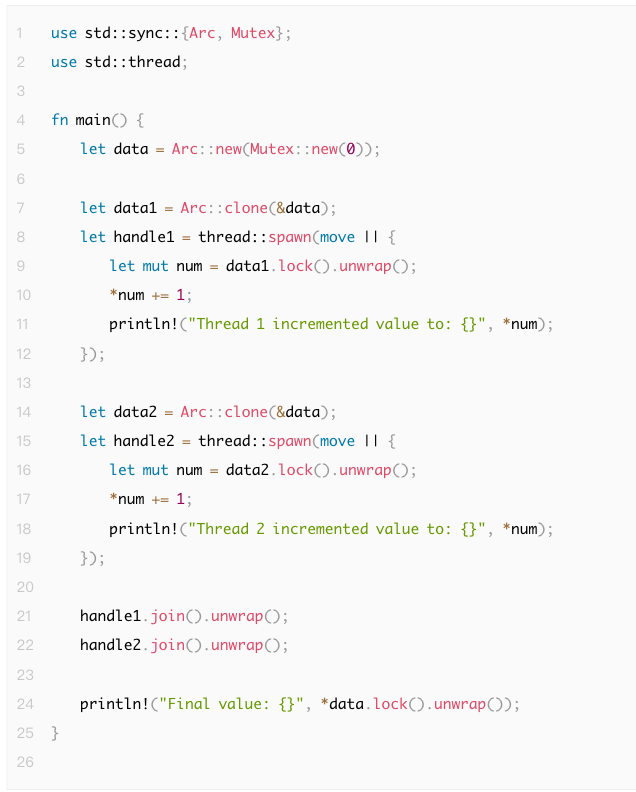
● Two threads each add 1 to the shared variable data. Each thread locks data and then increments its value.
● Because the operation is completed in steps, even though the data is protected by Mutex, the execution order of thread 1 and thread 2 will affect the final printed result. Theoretically, the final value should be 2, but the specific thread print output order may not be fixed.
1.4.5 Exception Crashes
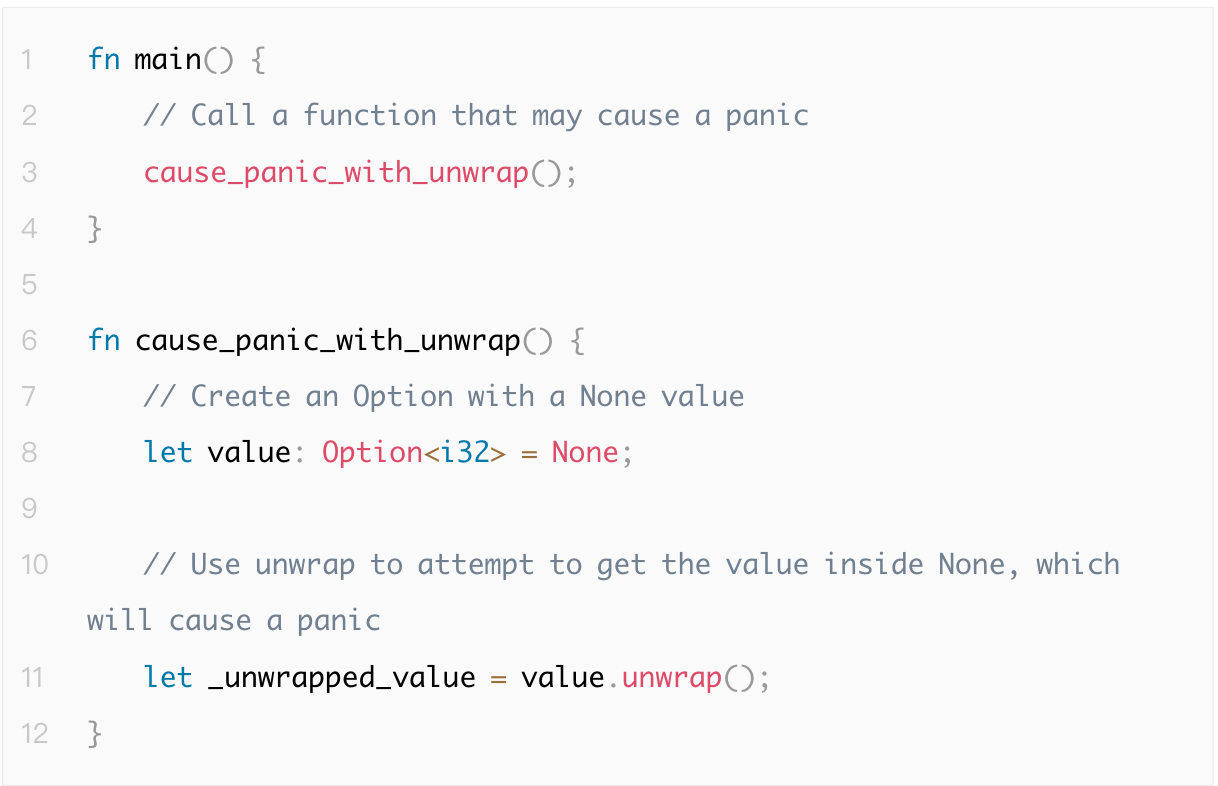
Exception crashes are usually caused by unhandled errors, leading to unexpected program termination. Go uses defer/panic/recover to catch exceptions, while Rust uses the Result and Option type systems to provide more robust error handling.
The following is an example where the program crashes due to an uncaught panic:
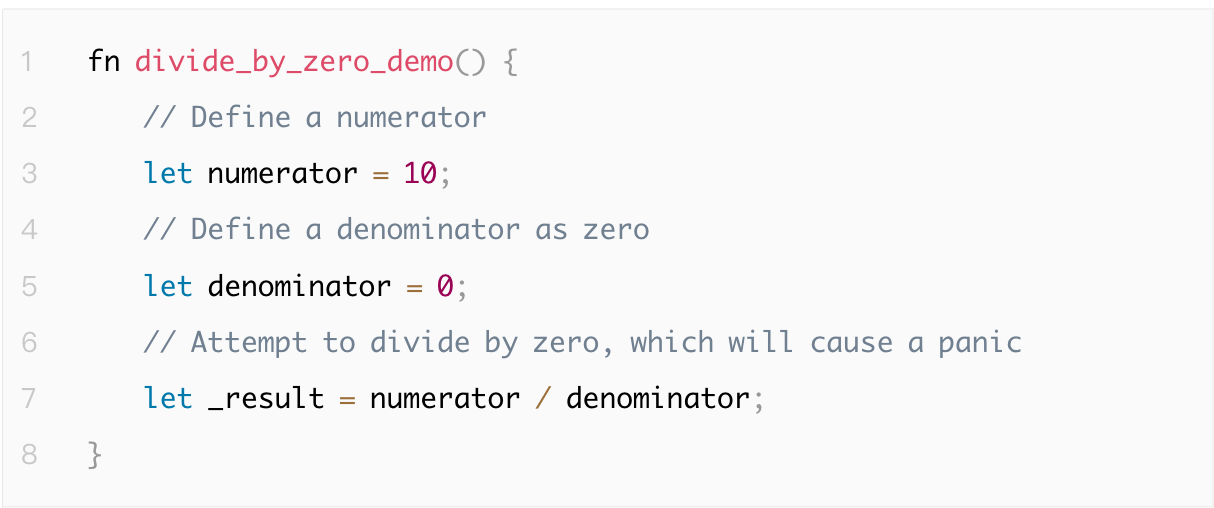
1.4.6 Division by Zero Vulnerability
The division by zero vulnerability refers to a situation where the program attempts to perform a division operation with a denominator of zero, which may trigger exceptions or crashes. It is recommended to check the denominator value before performing division to prevent zero-value operations and ensure program stability.
1.4.7 Type Conversion
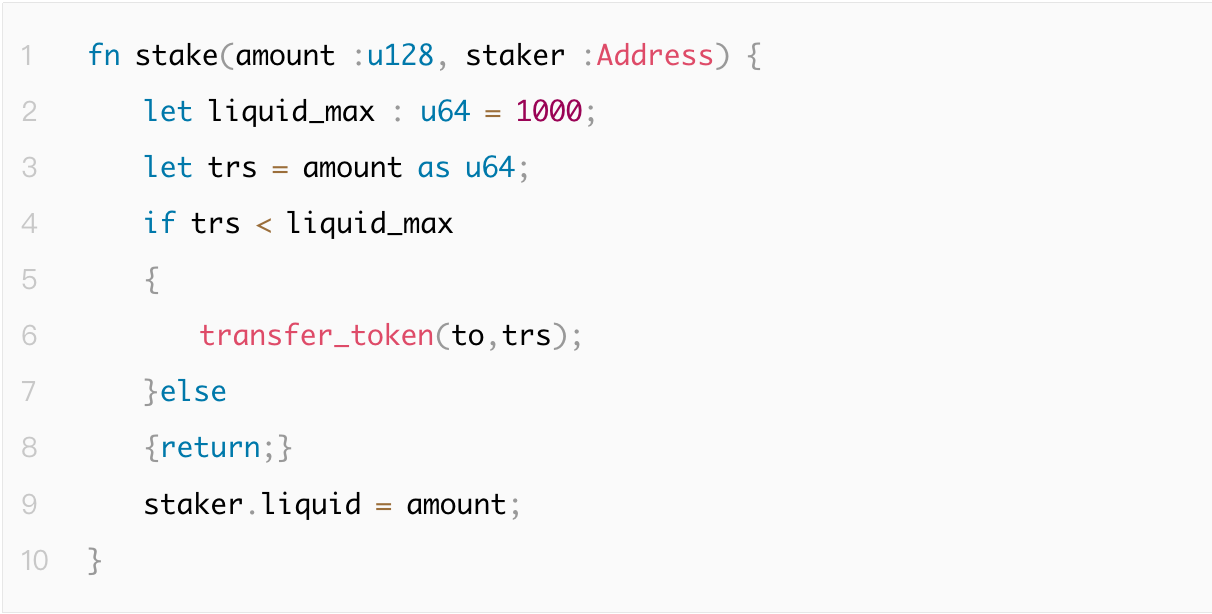
Type conversion errors are usually caused by unsafe or incompatible conversions, which may lead to unpredictable behavior. Go and Rust will prompt type incompatibility during conversion, with Rust being stricter in conversions, requiring the use of the "as" operator for explicit conversion.
In the following example code, the user adds liquidity for a certain amount of tokens, and then the system records the amount of liquidity. If amount = (u128::MAX 64) | 1, then only 1 token is actually paid, but the liquidity balance is recorded as 340282366920938463444927863358058659841.
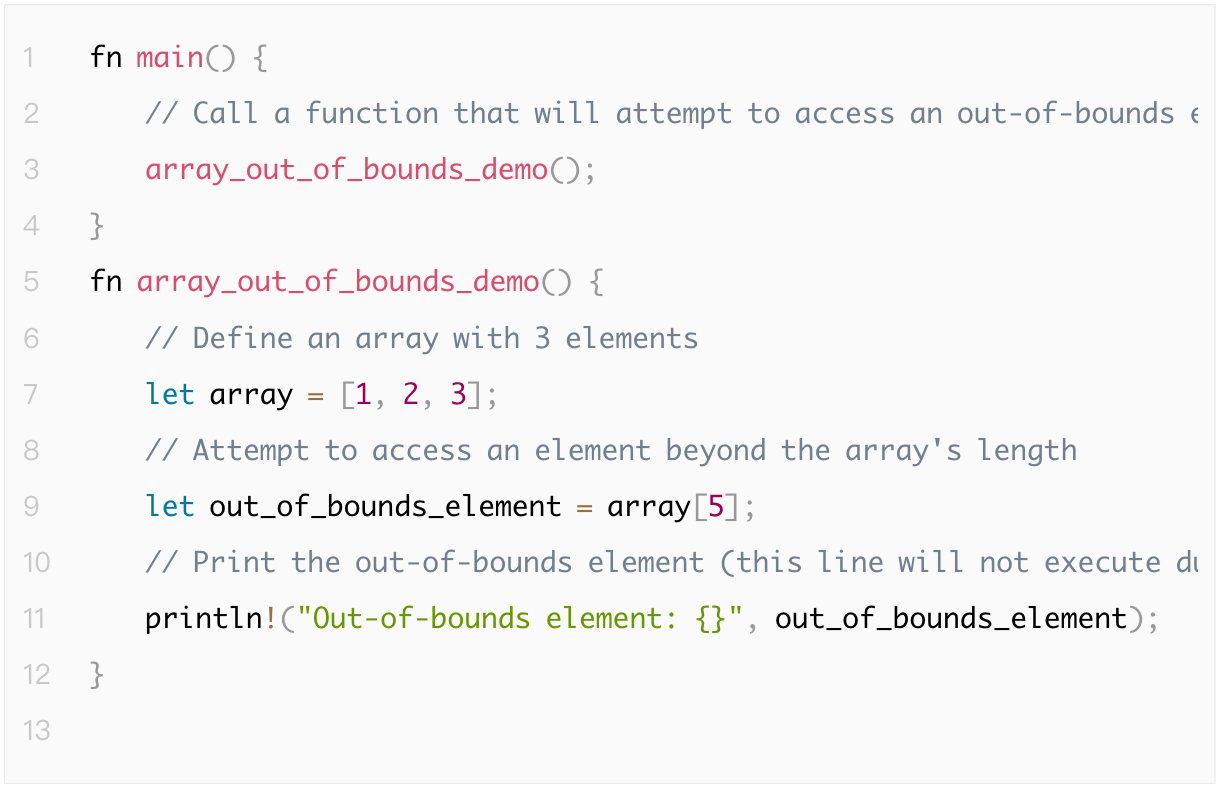
1.4.8 Array Out of Bounds
Array out of bounds refers to accessing invalid index positions in an array, leading to memory access errors or program crashes.
The following example code demonstrates a program crash due to array out of bounds:
1.5 P2P Network Vulnerabilities
P2P (peer-to-peer) networks are used for direct connections and communication between distributed nodes in blockchain systems. Although P2P networks provide the network foundation for decentralized systems, they also face a series of security vulnerabilities and attack risks.
From a security perspective, P2P network types can be divided into two categories: one is permissionless, which is more commonly used on L1. The other is permissioned, which is more common on L2.
In permissionless P2P networks, many attack vulnerabilities are based on Sybil attacks. In permissioned networks, we cannot assume that all nodes are trustworthy; from a security perspective, we must assume that there is at least one malicious node.
Common vulnerability types in P2P networks are as follows:
- Anomalous Attack Vulnerability:
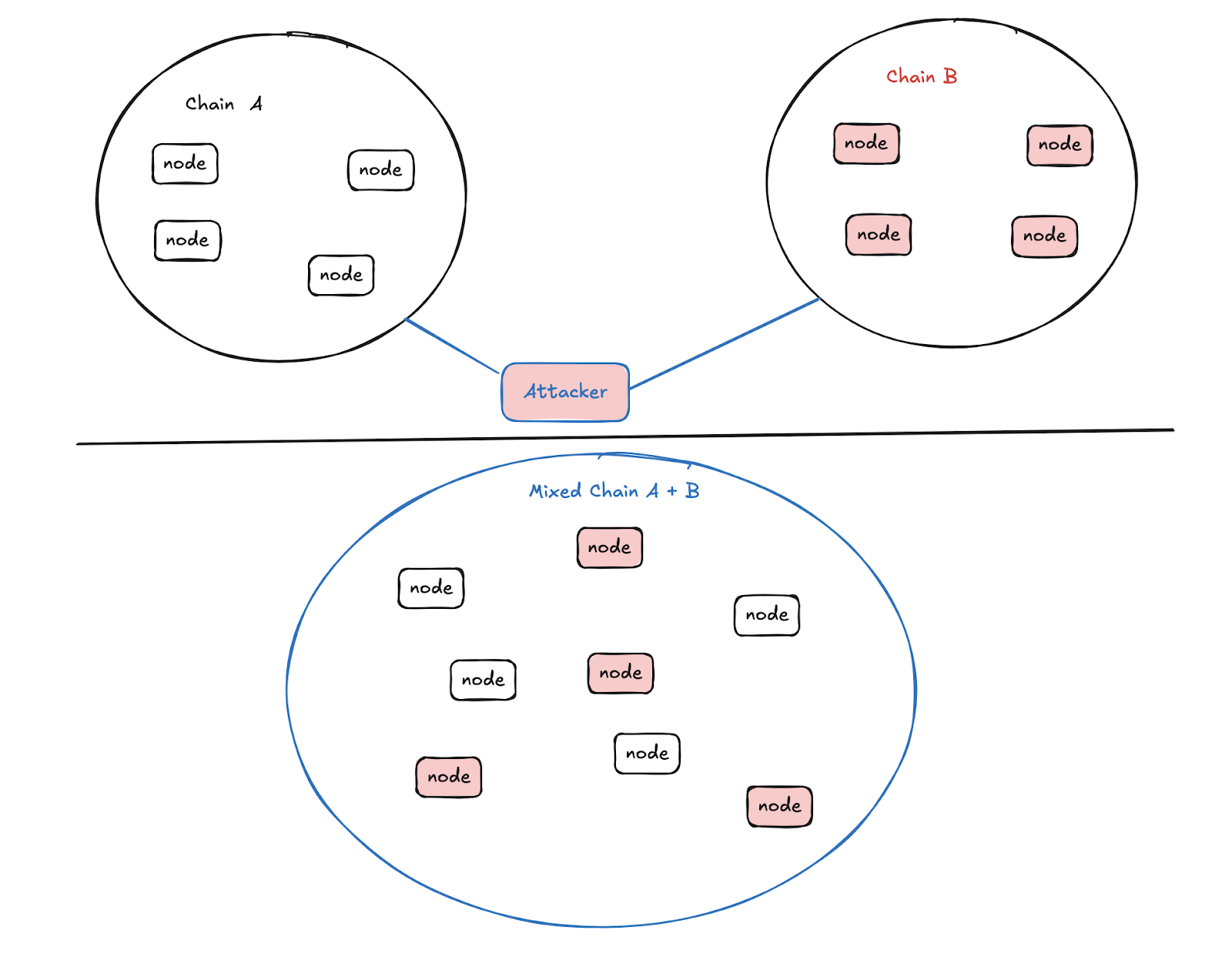
Anomalous attacks, also known as address pool pollution, refer to a type of attack that induces nodes of the same type of chain to invade and pollute each other. The main reason for the vulnerability is that the communication protocol of the same type of chain system does not identify non-similar nodes.
Some similar chains in Ethereum have experienced similar vulnerabilities. Ethereum similar chains (specifically, public chains using the Ethereum P2P discv4 node discovery protocol, including Ethereum and Ethereum Classic) cannot distinguish whether nodes belong to the same chain due to the use of compatible handshake protocols, leading to address pool pollution, decreased node communication performance, and ultimately causing node blockage.
The attack process is shown in the figure below:
- Lack of Trust Model Mechanism
Establish a reputation score for each node, adjusting trust levels based on the node's historical behavior. For example, if a node frequently sends invalid data, its reputation should be lowered. High-reputation nodes are more trusted, while low-reputation nodes need to be restricted.
- Lack of Node Quantity Limitation Mechanism
Limit the speed of new node creation or the number of connections per IP to prevent the rapid creation of a large number of fake nodes.
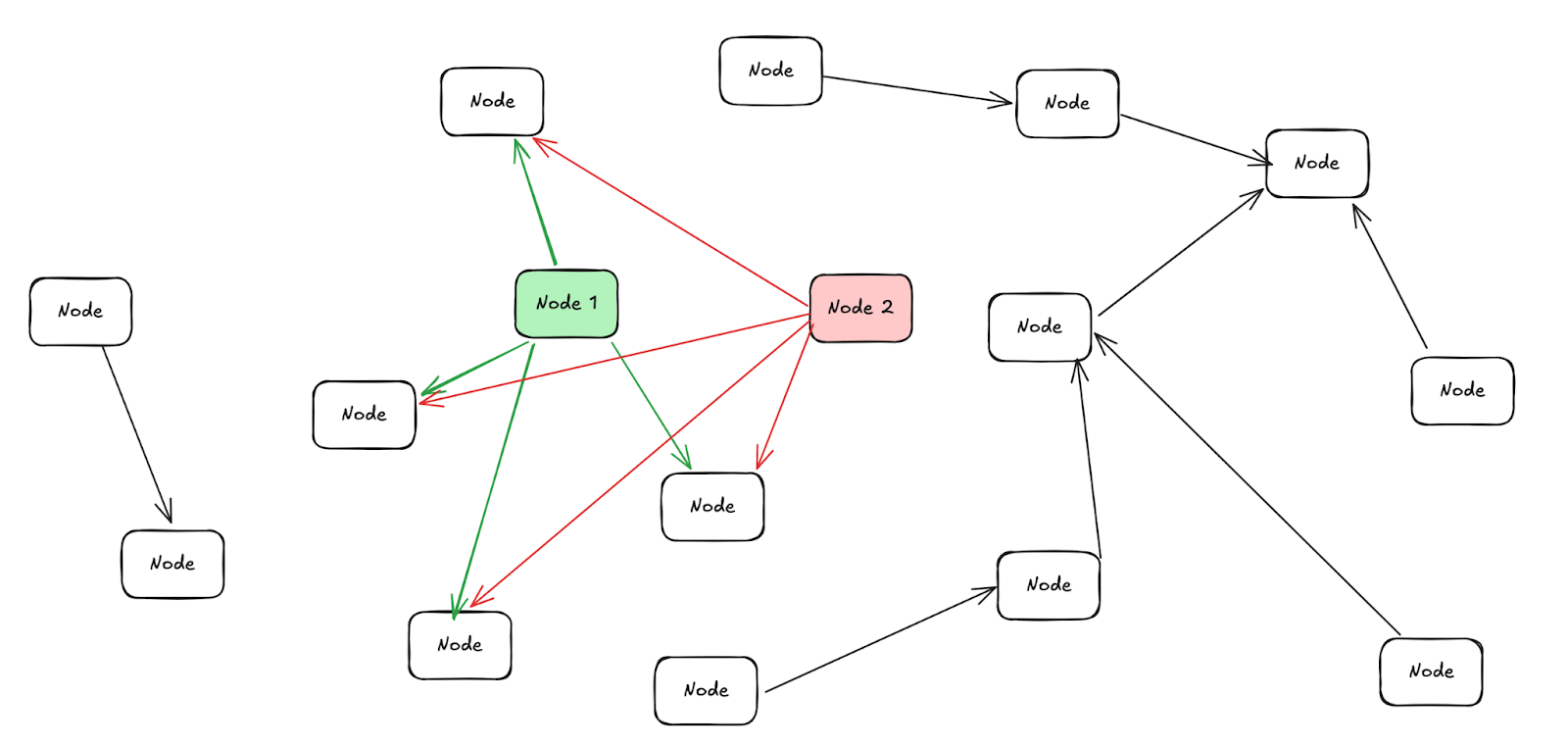
- Node Discovery Algorithm Issues
Node discovery and selection algorithms are responsible for locating new nodes and establishing connections in the P2P network. If the algorithm design is unreasonable, such as an unbalanced distance algorithm, it can easily lead to network topology imbalance and overload certain nodes. It is necessary to ensure the algorithm's balance and unpredictability to enhance the security of node distribution and the network's resistance to attacks.
The following image shows an extreme case of network topology imbalance:
- Vulnerable Node Selection Mechanism
If nodes use a vulnerable node selection mechanism, it is possible that all other nodes they connect to are malicious, leading to an Eclipse Attack. Below are common secure node selection mechanisms:
Random node selection: Randomizes the target connections of nodes, making it difficult for attackers to control the connection structure of nodes.
Local connection strategy: Allows nodes to prioritize connections with physically or topologically closer nodes, making it harder for attackers to infiltrate the entire network.
- Lack of Authentication
In permissioned P2P networks, it is necessary to verify the identity of nodes.
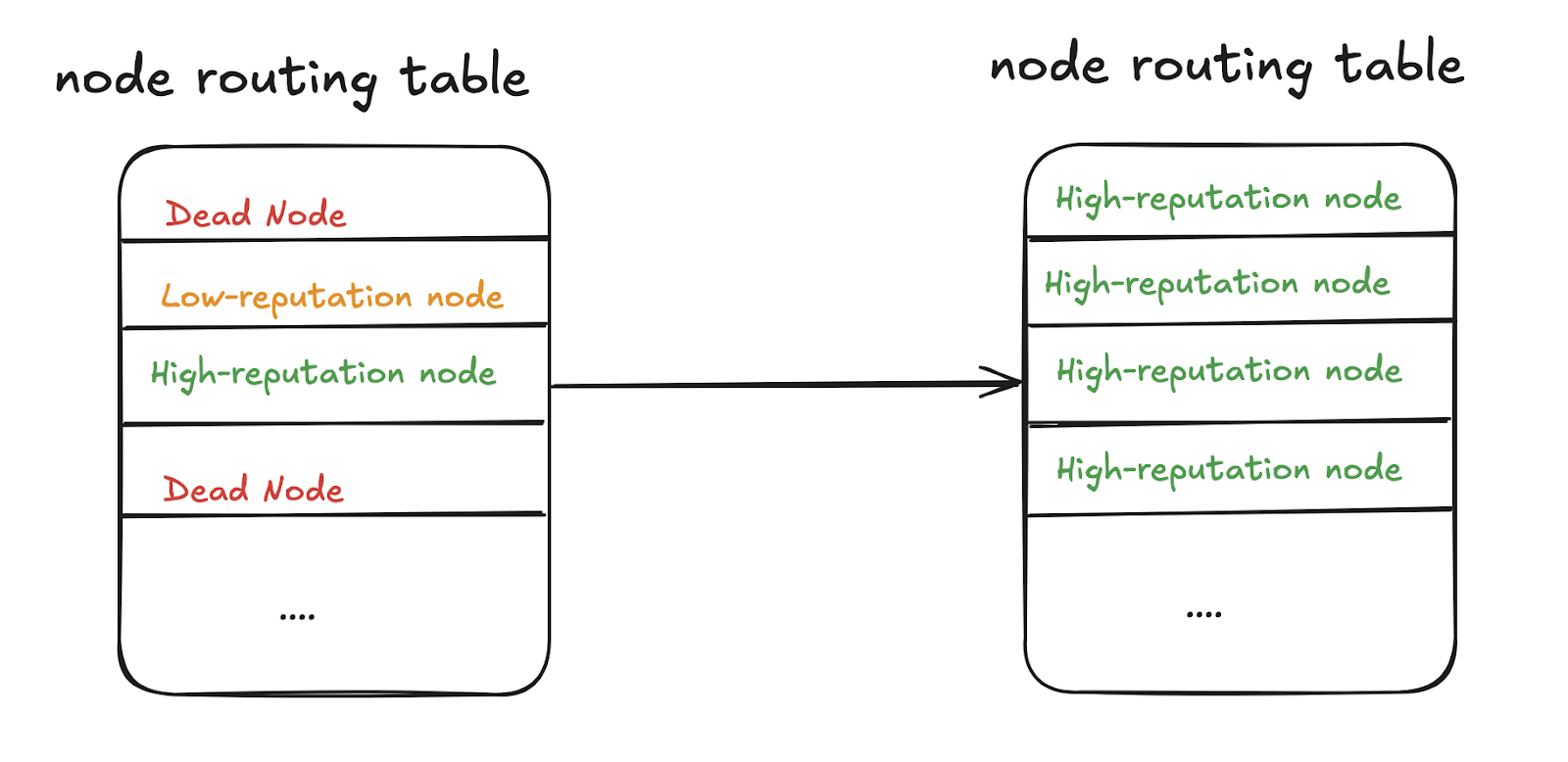
- Lack of Regular Routing Table Update Mechanism
If a node is found to return illegal data, consideration should be given to whether to delete its record in the routing table.
Nodes should regularly remove long-inactive nodes from the routing table and replace them with new nodes to avoid network isolation caused by routing table failures.
- Man-in-the-Middle Hijacking Vulnerability
P2P data must maintain data integrity during transmission. If the encryption algorithm used is incorrect or has vulnerabilities, it may allow data to be tampered with.
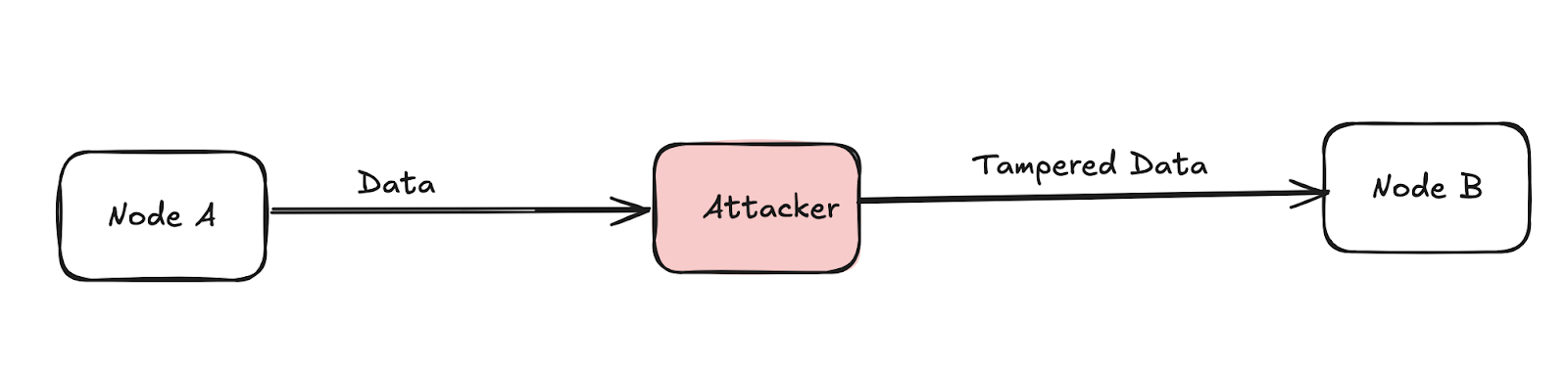
1.6 DoS Vulnerabilities
DoS (Denial of Service) vulnerabilities can lead to resource exhaustion, hindering normal access for legitimate users. The following are key types:
- Memory Exhaustion Attack
Utilizing a large memory demand to crash the system; it is recommended to set resource limits to prevent this.
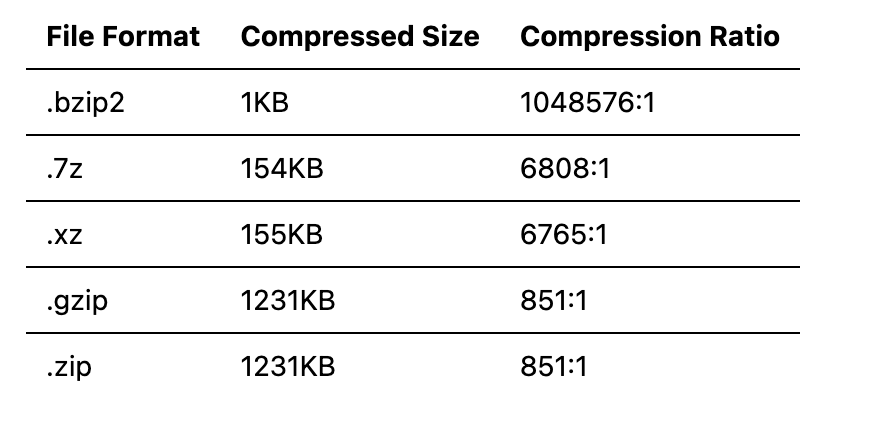
A common memory exhaustion attack is the "zip bomb." The basic principle of a zip bomb is to generate a very large file filled entirely with 0s (or other values) and then compress it into a zip file. Due to the high compression ratio of files with identical content, the resulting zip file is very small. When the target of the attack decompresses the zip file, it requires a significant amount of memory to store the decompressed files, quickly exhausting memory and causing the target to crash due to OOM (Out of Memory).
Other compression algorithms can also exhibit the same problem. Below is a list of compression ratios for compressing a 1GB file filled entirely with 0s using common algorithms:
- Disk Exhaustion Attack: Writing useless data to fill storage space, preventing resource shortages through disk quota management.
Common scenarios for disk exhaustion attacks include the following two cases:
Zip bomb. The attack method is the same as the "memory exhaustion attack" above, except that the target program decompresses the zip file to disk rather than directly to memory.
Writing a large amount of data to disk at no or low cost can exhaust disk data.
Kernel Handle Exhaustion Attack: A large number of resource requests exhaust handles; it is recommended to control handle allocation and monitor for anomalies.
The general principle of this attack is: the attacker exploits a vulnerability to exhaust or nearly exhaust the target node's kernel handles, preventing it from responding to normal business requests.
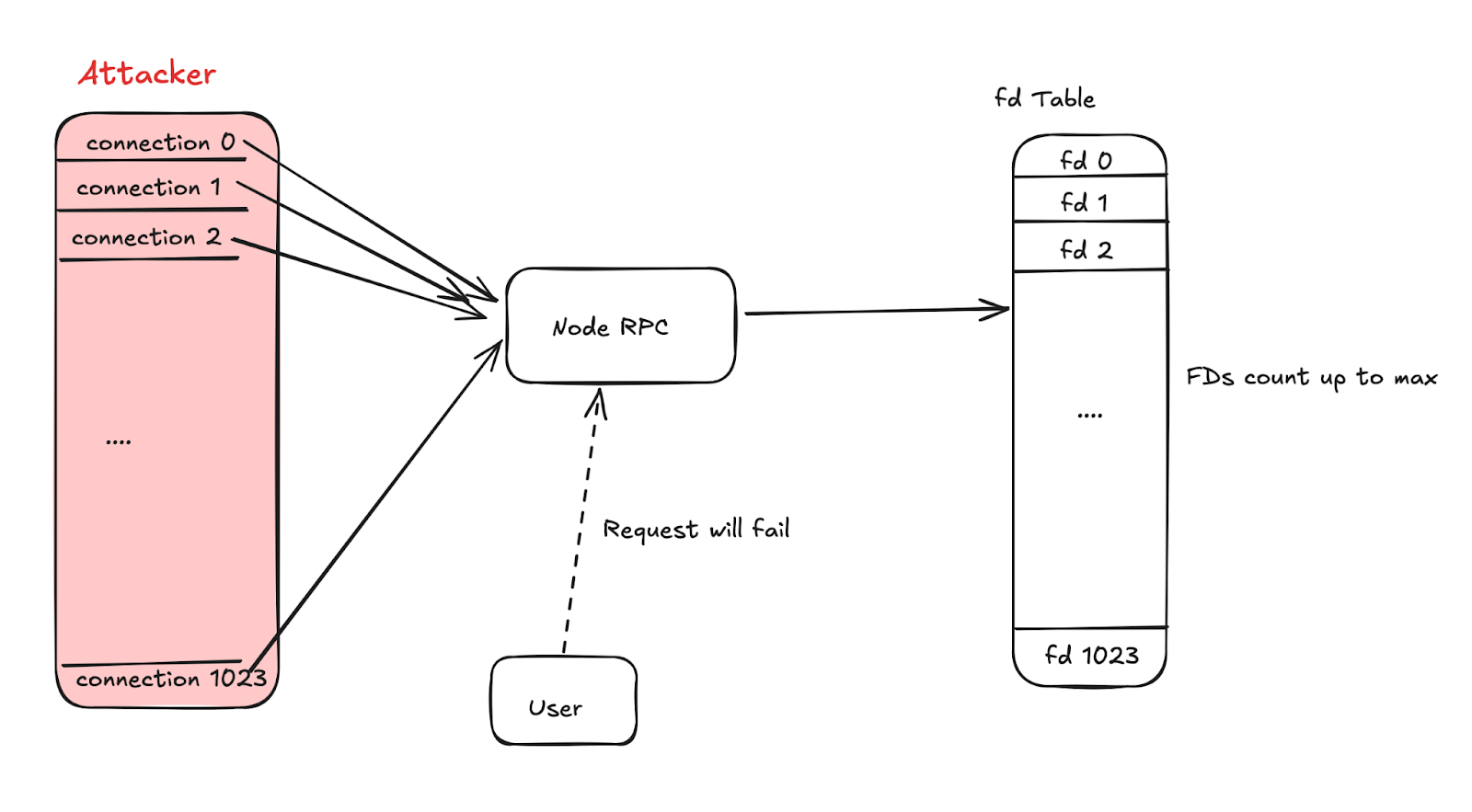
A common attack is the "Socket Stress Attack." If the target node does not limit the number of connections and concurrency, the attacker can send and maintain a large number of connection requests, exhausting the system's socket resources.
- Persistent Memory Leak: Memory that cannot be released normally leads to resource exhaustion; regular memory usage checks are needed to prevent the problem from worsening.
Memory leaks are generally not considered security vulnerabilities. However, if an attacker can actively trigger a memory leak in the target node and repeat this operation, over time, the target node's program may crash due to insufficient memory.
1.7 Cryptographic Vulnerabilities
Cryptographic vulnerabilities can compromise the confidentiality and integrity of data, posing potential security threats to the system. The following are the main types of cryptographic vulnerabilities:
Using hash algorithms that have been proven to be insecure
Hash algorithms are used to generate unique identifiers for data, ensuring that integrity is not tampered with. Common hash algorithms like MD5 and SHA-1 have been proven to have collision risks, which may be exploited by malicious attackers. Therefore, it is recommended to use more secure modern hash algorithms such as SHA-256 or SHA-3 and to keep the algorithms updated to avoid data integrity risks posed by easily cracked old algorithms.
Using insecure custom hash algorithms
Some projects use their own defined hash algorithms, which generally do not have the security of publicly known algorithms.
For example, during our audit process, we encountered the following custom hash algorithm:
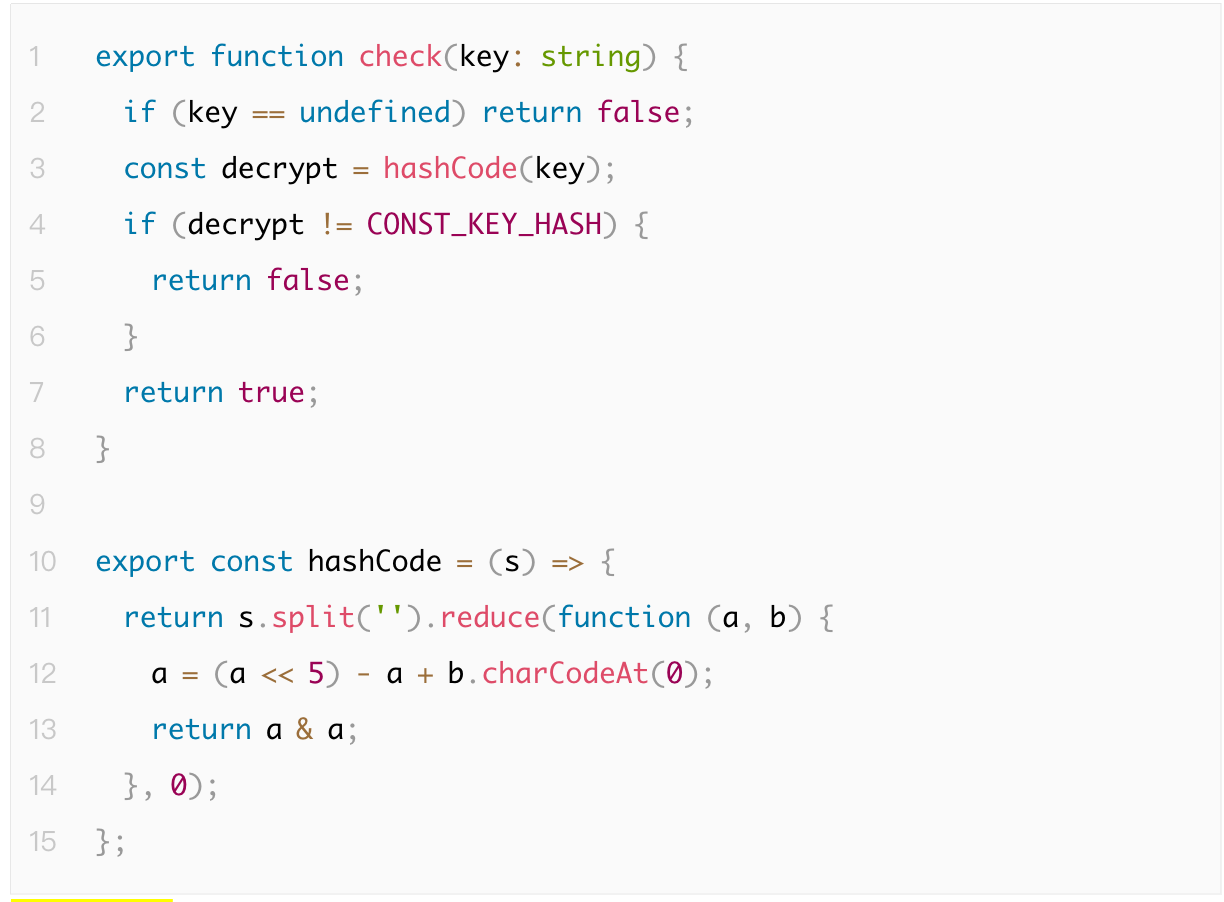
The hashCode function is not a cryptographic hash function and is prone to collisions. It only performs very simple bitwise and addition operations. Additionally, the input length and output length of this function follow a clear and predictable pattern, making it easy to reverse-engineer and crack. Due to this weak hash mechanism, attackers can easily generate keys that lead to the same CONST_KEY_HASH value, thereby jeopardizing the security of the API authorization process.
The following is proof of concept (PoC) code demonstrating how to exploit this weak hash vulnerability:
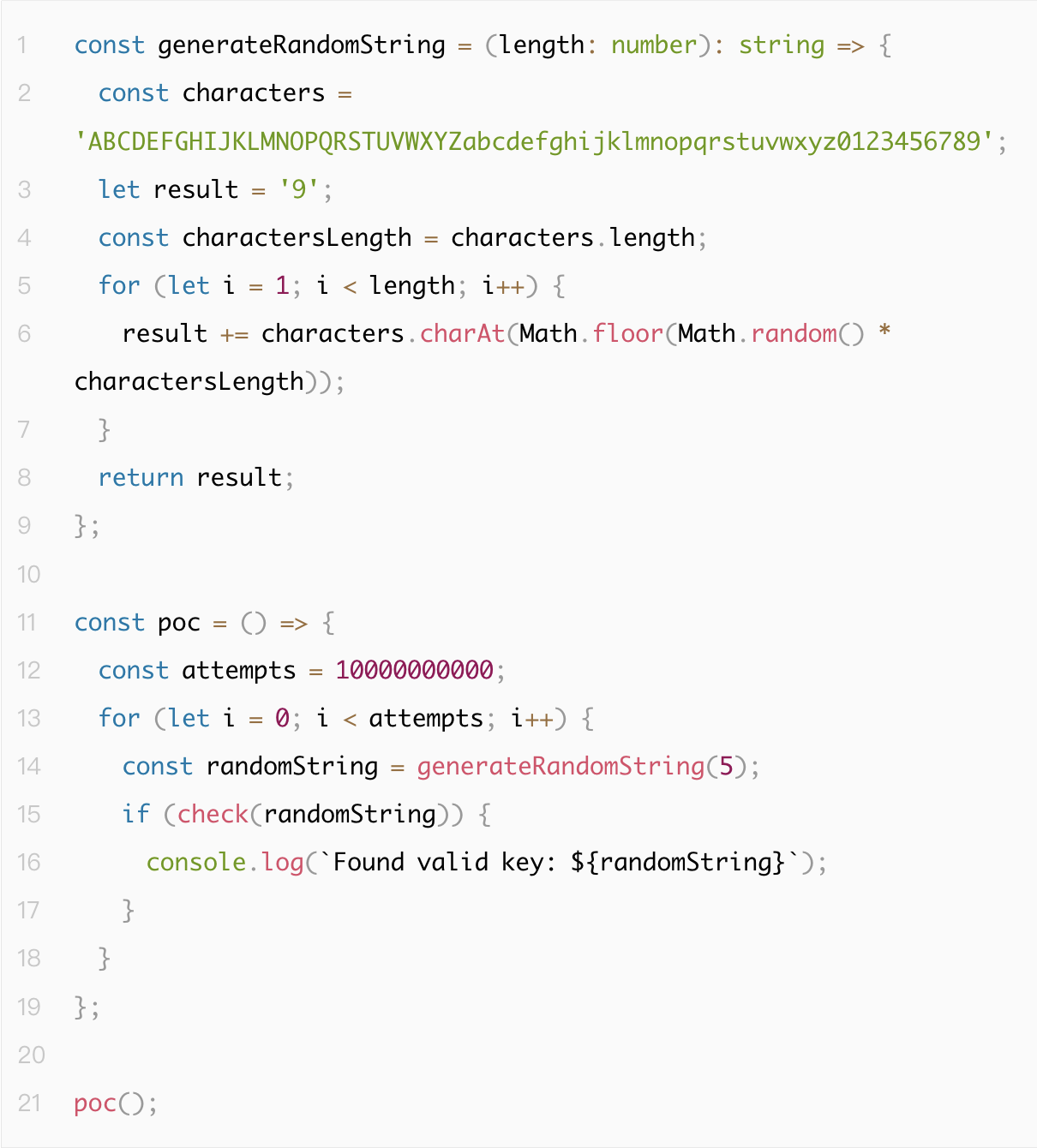
Insecure usage leading to hash collisions
A common situation is that HASH(A+B+C)=HASH(D+E), where this occurs because A+B+C=D+E. Although 'A+B+C' and 'D+E' are identical, the individual components A, B, C, D, and E are different.
Using insecure digital signature algorithms
Digital signature algorithms are used to verify the authenticity and origin of data, preventing data from being tampered with. Early signature algorithms like DSA and RSA may fail under quantum computing threats. Using modern signature algorithms like ECDSA or EdDSA can provide stronger security, protecting the legitimacy of data and anti-counterfeiting capabilities. This is particularly crucial in distributed systems and smart contracts, where ensuring the reliability of signature algorithms is essential.
Using insecure encryption algorithms
The strength of encryption algorithms directly affects the confidentiality of data; weak encryption algorithms (like DES) can be easily cracked by attackers. It is recommended to use higher-bit symmetric encryption algorithms like AES-256 and to implement end-to-end encryption (such as TLS) during communication to ensure the security of data transmission and prevent eavesdropping or tampering. Additionally, ensure proper key management to prevent key leakage.
Using insecure random number generation algorithms
Random number generators are the foundation of many cryptographic operations, especially when generating keys, IVs (initialization vectors), and important parameters in asymmetric encryption, ensuring their unpredictability is crucial. Common security issues include:
Insecure random number generation algorithms lead to predictable or even manipulable random numbers;
Random number algorithms on public chains generally have risks of random number prediction, as all information is publicly transparent, making random numbers predictable.
Insecure random number generation algorithms lead to poor randomness of random numbers, increasing the probability of certain vulnerabilities or issues (such as miner block production).
Using insecure random number seeds
Leaking random number seeds or being vulnerable to brute force attacks can lead to predictable random numbers.
Cryptographic side-channel attacks
Side-channel attacks obtain sensitive information by monitoring the physical characteristics of the system (such as power consumption, execution time, cache, etc.). This type of attack bypasses the security of the algorithm itself and is particularly common in hardware devices and embedded systems. Defense measures include optimizing algorithm implementations to keep execution time and power consumption constant, reducing leakable characteristics. Additionally, techniques such as masking and obfuscation can reduce the likelihood of side-channel information leakage.
Signature malleability
Signature malleability refers to the ability to derive another different valid signature from a known valid signature without changing the signed content. A significant risk posed by this characteristic is transaction malleability, which allows malicious users to exploit different signature variants for transaction replay. The replayed transactions have different hash values due to differing signatures, confusing users' judgment of the transaction status during the transaction confirmation process, thereby enabling double spending.
1.8 Ledger Security Vulnerabilities
Transaction memory pool vulnerabilities
Transactions can be replayed
Failed transactions do not incur fees
Block hash collision vulnerabilities
If there are issues with the construction of blocks, collisions may occur.
Orphan block handling logic vulnerabilities
Orphan blocks can be directly discarded, but if caching is chosen, restrictions such as height and time must be added.
Merkle tree hash collision vulnerabilities
If the construction method of Merkle tree leaf nodes has issues, collisions may occur.
Transaction amount processing issues
Issues such as upper and lower bound overflows, type inconsistencies, precision errors, negative values, and unexpected values caused by external condition changes can occur during transaction amount processing.
Transaction fee processing issues
Issues such as upper and lower bound overflows, type inconsistencies, precision errors, negative values, and unexpected values caused by external condition changes can occur during transaction fee processing.
Block and transaction verification time sensitivity
Due to time discrepancies between different nodes, time verification cannot be overly sensitive, as it may easily lead to block forks.
Issues with transaction authorization logic
This mainly includes the following two aspects:
Identity forgery bypass
Permission check errors
1.9 Economic Model Vulnerabilities
Economic models play a crucial role in blockchain and distributed systems, influencing the network's incentive mechanisms, governance structures, and overall sustainability. The following are the main points of concern:
Economic model of Cosmos application chains (taking UniChain as an example)
The economic model of Cosmos application chains focuses on blockchain interoperability and scalability. Taking UniChain as an example, its economic model design considers not only the circulation and use of on-chain tokens but also the needs of different application scenarios. By utilizing the Cosmos SDK, UniChain can create application-specific blockchains and achieve cross-chain communication, promoting resource sharing and value flow between different chains. The economic model should focus on token issuance, inflation rates, transaction fee structures, and on-chain governance mechanisms to ensure the stability and prosperity of the ecosystem.
Reasonableness of the incentive mechanism
The incentive mechanism is a core part of the economic model, directly affecting the participation of users and nodes. A reasonable incentive mechanism should ensure that all participants (such as miners, validators, developers, and users) receive fair returns. It is necessary to assess the sustainability of the incentive structure to ensure it effectively prevents malicious behavior and centralization trends. Additionally, the incentive mechanism should adapt to market changes and adjust with the maturation of the network and the evolution of user demands. For example, whether there are appropriate reward and punishment mechanisms, how to balance short-term and long-term incentives, etc., are all issues that require in-depth analysis.
Sustainability of network economics
The economic model also needs to focus on the long-term sustainability of the network, including the management of economic incentives, value creation, and distribution among various parties within the ecosystem. It is necessary to assess whether there are economic imbalances or resource wastage, ensuring that all participants can obtain reasonable value within the network. Additionally, it is essential to analyze external factors that may affect network stability, such as market fluctuations and changes in user behavior.
Market Feedback Mechanism
Establishing an effective market feedback mechanism allows the economic model to adjust according to user demands and market dynamics. Through regular data analysis and user feedback, potential issues can be identified and corrected in a timely manner, ensuring the flexibility and adaptability of the economic model.
Impact of Governance Structure
The design of the economic model should be integrated with the governance structure, ensuring that users can participate in economic decision-making during the governance process, thereby enhancing the sense of community participation and belonging. A reasonable governance mechanism can promote the self-repair and continuous optimization of the economic model, improving the overall health of the network.
After gaining an in-depth understanding of the various types of security vulnerabilities present in the blockchain ecosystem, the next step is to explore the specific attack surfaces that these vulnerabilities may be exploited. An attack surface refers to the entry points and paths in the system that potential attackers can exploit. By identifying and analyzing these attack surfaces, risks can be more effectively assessed, and corresponding protective strategies can be formulated. Therefore, comprehensively understanding the relationship between vulnerability types and attack surfaces is crucial for building a robust blockchain security defense. The following will detail the common attack surfaces currently found in the blockchain ecosystem, helping readers better understand the specific implementation of threats.
2. Attack Surface List
The following is a list of common attack surfaces:
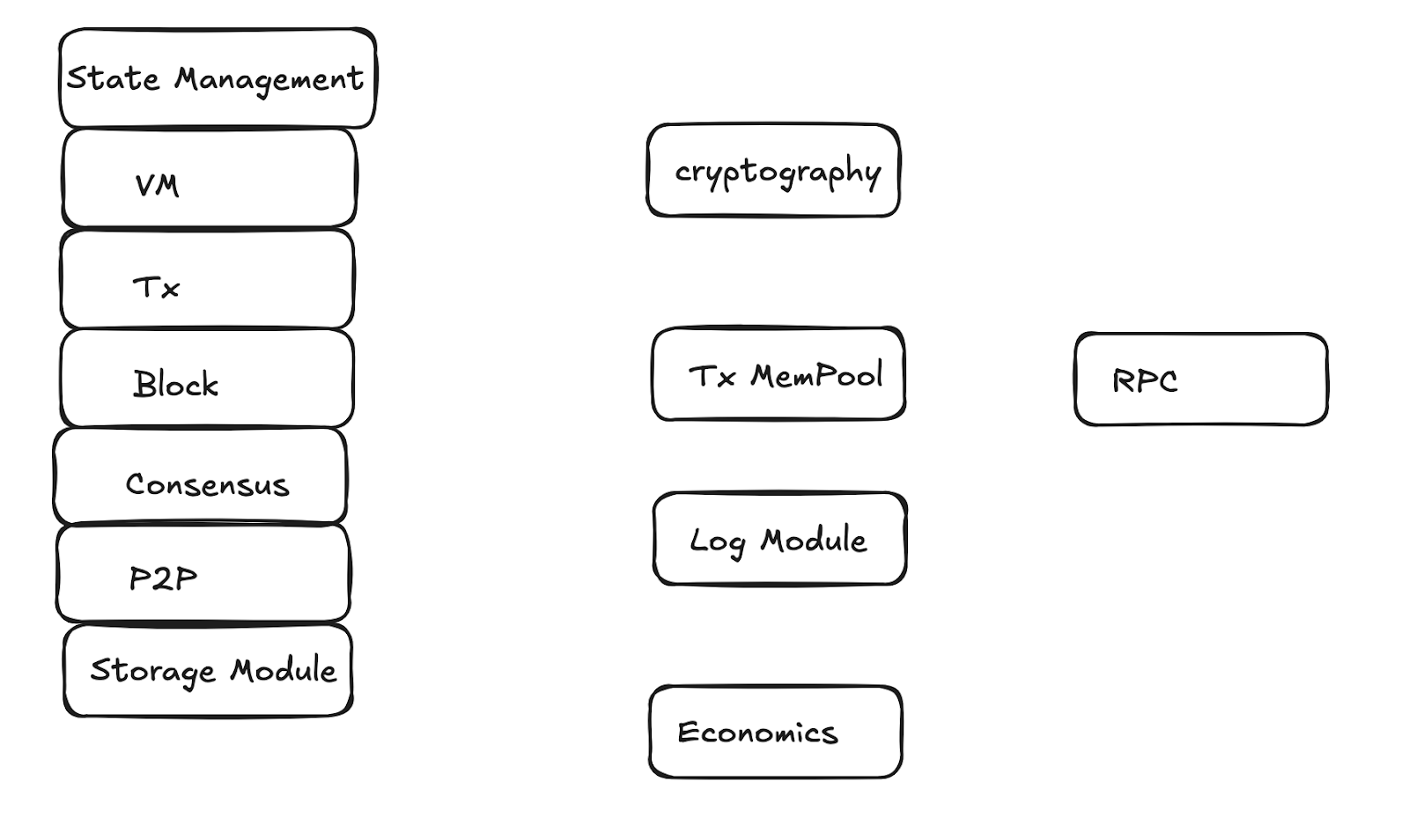
4.1 Virtual Machine
Attack Surface: The virtual machine is responsible for executing smart contracts and processing bytecode, often carrying a large amount of complex logic, which poses potential risks such as reentrancy attacks, integer overflow, and memory overflow. Additionally, smart contracts with high computational consumption may trigger DoS attacks, leading to resource exhaustion. Furthermore, if the bytecode of smart contracts contains unverified vulnerabilities, it can easily lead to arbitrary code execution and privilege escalation risks.
4.2 P2P Node Discovery and Data Synchronization Module
Attack Surface: If the discovery and synchronization functions of P2P nodes are poorly designed, they may be susceptible to Sybil attacks, where a large number of fake nodes are fabricated to control the network, resulting in degraded network performance or even failure. The routing table pollution during the node data synchronization process can affect the quality of connections between nodes, rendering some nodes unavailable. Additionally, there may be forged or malicious data in the data packets, leading to nodes receiving incorrect information, which in turn affects synchronization and consensus.
4.3 Block Parsing Module
Attack Surface: Block parsing involves a large amount of data processing. If there are overflows or error handling issues in the parsing code, it may be attacked by malicious blocks, leading to service crashes or denial of service (DoS). Moreover, incorrect block format validation may result in tampered blocks being transmitted across the network, making them unrecognizable and affecting overall network consistency.
4.4 Transaction Parsing Module
Attack Surface: Transaction parsing involves verifying transaction structures and signatures. If forged transaction formats, malicious data, or abnormal signatures are not handled properly, it may allow false transactions to pass through, consuming system resources. Additionally, if there are boundary overflow issues in transaction parsing, it may be exploited to execute memory injection attacks.
4.5 Transaction Memory Pool
Attack Surface: The memory pool is a temporary storage area for transactions before they are added to the blockchain. It may be abused to insert a large number of invalid or malicious transactions, leading to memory consumption attacks that prevent nodes from responding to normal requests. Furthermore, malicious attackers can use the transaction memory pool to insert duplicate or high-frequency transactions, further causing resource exhaustion and DoS risks.
4.6 Consensus Protocol Module
Attack Surface: When the consensus mechanism is poorly designed or manipulated, it may encounter issues such as double spending attacks, selfish mining, and 51% attacks. Attackers can execute malicious forks by controlling more than half of the computational power, affecting the legitimacy of transaction records. Additionally, certain consensus mechanisms may fail in the face of high latency or partitioned networks due to a lack of clear fault tolerance mechanisms.
4.7 RPC Interface
Attack Surface: The RPC interface is the means for external interaction with blockchain nodes. If access permissions are improperly configured, it may lead to unauthorized access and data leakage. If privileged RPC interfaces are not adequately protected, attackers can forge requests to execute high-privilege operations, further manipulating on-chain data. Additionally, RPC interfaces are vulnerable to request flood attacks, leading to node response overload.
4.8 Log Processing Module
Attack Surface: The log module is responsible for recording detailed information about system operations. If attackers can inject forged log content through log injection, it may lead to sensitive information leakage. Excessively recorded logs may also be maliciously exploited to cause log bloat, leading to storage resource consumption and even system unavailability.
4.9 Network Middleware
Attack Surface: If the communication middleware of the blockchain network lacks encryption transmission and identity authentication mechanisms, it may be susceptible to man-in-the-middle (MITM) attacks, leading to packet interception and tampering. Additionally, middleware is vulnerable to traffic attacks (such as DoS) and protocol abuse attacks, affecting normal communication across the entire network.
4.10 Cryptographic Algorithms
Attack Surface: The design and implementation of cryptographic algorithms directly relate to data security. If there are hash collision vulnerabilities, it may lead to the forgery of transaction content; if cryptographic algorithms do not adhere to strong randomness principles, it may result in key leakage. Other common attacks include side-channel attacks, such as obtaining sensitive information by observing energy consumption or electromagnetic leakage during cryptographic execution.
4.11 Economic Model
Attack Surface: The design of the blockchain's economic model must balance incentives for all parties; otherwise, attackers may influence system stability by manipulating token circulation or reducing miner rewards. An unreasonable incentive design in the economic model may lead miners (or validating nodes) to behave contrary to expectations, posing risks of economic attacks.
4.12 Data Storage Module
Attack Surface: On-chain and off-chain data storage face risks of unauthorized access, tampering, and data persistence. Attackers may attempt to exploit insufficient database permissions or insecure storage mechanisms to directly modify ledger data or smart contract states. Additionally, unreasonable data storage strategies may lead to data bloat, affecting system performance.
4.13 State Management Module
Attack Surface: The state management of the blockchain is used to record critical data such as account balances and contract storage. If the state management module is poorly designed, it may be exploited by attackers, resulting in incorrect account balances or tampered state information. Malicious attackers can also construct special transactions to cause state hijacking, leading to resource locking.
Conclusion
In summary, while the blockchain ecosystem is full of innovation and development potential, its security issues cannot be overlooked. This article has detailed various types of security vulnerabilities across multiple key areas, including cross-chain communication, Cosmos application chains, Bitcoin expansion ecosystems, programming language vulnerabilities, P2P network vulnerabilities, DoS attacks, cryptographic vulnerabilities, and ledger security. Through systematic analysis and summarization, the aim is to help developers and security practitioners identify potential risks, take effective preventive measures, and enhance overall security levels. In the face of increasingly complex and diverse security challenges, only by continuously strengthening technical defenses, improving security audit mechanisms, and promoting cooperation and communication within the industry can we ensure the healthy and sustainable development of blockchain technology. ScaleBit and its parent company BitsLab will continue to focus on blockchain security research, providing forward-looking security solutions to contribute to building a more robust and trustworthy blockchain ecosystem.
Read and download the "2024 Emerging Ecological Public Chain Panorama Observation and Security Research Report": https://bitslab.xyz/reports-page
About ScaleBit
ScaleBit, a sub-brand of BitsLab, is a blockchain security team providing security solutions for Web3 mass adoption. With expertise in blockchain cross-chain and zero-knowledge proof expansion technologies, we primarily offer detailed and cutting-edge security audits for ZKP, Bitcoin Layer 2, and cross-chain applications.
The ScaleBit team consists of security experts with extensive experience in both academia and industry, dedicated to providing security assurance for the large-scale application of scalable blockchain ecosystems.
About BitsLab
BitsLab is a security organization committed to safeguarding and building the emerging Web3 ecosystem, with a vision to become a respected Web3 security agency in the industry and among users. It has three sub-brands: MoveBit, ScaleBit, and TonBit.
BitsLab focuses on infrastructure development and security auditing for emerging ecosystems, covering but not limited to Sui, Aptos, TON, Linea, BNB Chain, Soneium, Starknet, Movement, Monad, Internet Computer, and Solana ecosystems. Additionally, BitsLab has demonstrated profound expertise in auditing various programming languages, including Circom, Halo2, Move, Cairo, Tact, FunC, Vyper, and Solidity.
The BitsLab team brings together several top vulnerability research experts who have won international CTF awards multiple times and have discovered critical vulnerabilities in well-known projects such as TON, Aptos, Sui, Nervos, OKX, and Cosmos.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




