TL;DR
- Crypto airdrops have evolved from simple free token distributions into complex marketing strategies, yet they still face numerous challenges in areas such as witch attacks and scalability.
- Sign Protocol serves as the "notary" of the digital world, enabling users to create verifiable cross-chain digital certificates and on-chain labels, thereby accurately identifying genuine community members.
- As part of the Sign Protocol ecosystem, TokenTable offers customized token management and distribution across multiple chains, implementing various token distribution access mechanisms (KYC, NFT, token/certificate proof) and flexible representative release mechanisms.
- Sign Protocol and TokenTable are committed to achieving more effective token airdrops, maximizing the number of genuine token holders at the launch of tokens and fostering long-term community loyalty and adoption.
- In the future, more airdrops will emerge to guide community building, converting millions of outsiders into token holders. Sign Protocol and TokenTable are key catalysts driving this transformation.
- Beyond airdrops, Sign Protocol has broader applications in digital identity, reputation systems, and decentralized communities, likely becoming a bridge between Web3 and Web2 ecosystems.

Airdrop Development Trajectory
1. Background
Since the inception of cryptocurrency, airdrops have come a long way. Initially, airdrops were merely simple free token distributions aimed at creating awareness and widely dispersing tokens. As cryptocurrencies gained mainstream attention, airdrops became the preferred marketing strategy for new projects to quickly build user communities. Especially since the successful Uniswap airdrop, the popularity of airdrops has exploded. Token airdrops from various projects such as dYdX, ENS, Jito, and Arbitrum have significantly rewarded early participants and generated substantial wealth effects, thus attracting widespread attention and discussion within the crypto community.
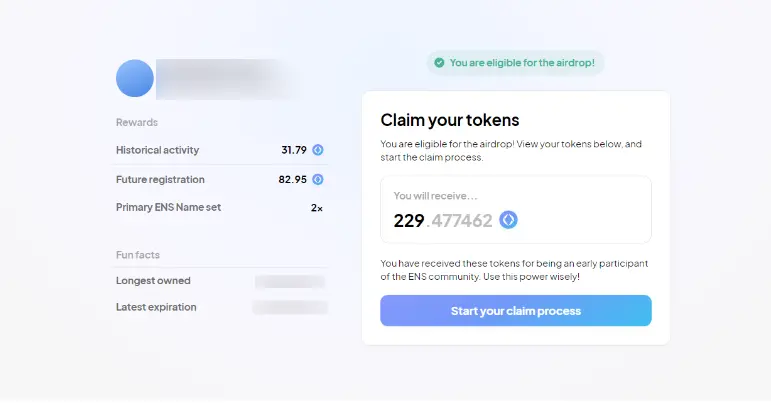
In recent years, the user base for airdrops has greatly expanded, far beyond the confines of the crypto community. Once a niche social practice among blockchain enthusiasts, airdrops have now evolved into a hot event that global users can participate in, capturing the attention of millions of potential participants. Airdrops from projects like $GRASS and $DOGS allow users to earn rewards by renting out idle bandwidth or attention, successfully engaging millions of users. To date, airdrops are driving the mass adoption of cryptocurrencies through widespread token distribution, becoming an important bridge between the crypto ecosystem and mainstream audiences.
2. Current Status and Future Challenges
As airdrops become increasingly popular, the practice of airdrop farming has emerged. Some project teams have begun implementing more complex airdrop strategies, including retroactive airdrops, participation-based airdrops, and multi-stage airdrops to combat opportunistic behavior and filter out airdrop witches.
However, current airdrop strategies seem insufficient. There are several unresolved challenges in the airdrop mechanism that hinder its development and popularity:
3. Witch Attacks
"Airdrop farming" exploits system vulnerabilities for speculative gains from airdrop expectations. Airdrop witches dilute the airdrop shares of genuine communities, and worse, they create significant sell pressure during the token generation event (TGE).
4. Scalability Issues
Some project airdrops attract hundreds of thousands or even millions of participants. However, due to the lack of a one-stop airdrop management tool, project teams find it difficult to conduct efficient and low-cost token distribution.
5. Community Quality Issues
Many airdrop participants are short-term speculators rather than genuine community members. They prioritize quick profits over true community engagement.
6. Regulatory Issues
As airdrops gain more attention, they face increasing regulatory compliance challenges. Projects may need to implement effective Know Your Customer (KYC) processes to mitigate potential regulatory risks.
7. Focus on Witch Attacks
Among the many challenges mentioned, witch attacks have become the biggest threat in the airdrop space. When witch attacks occur, malicious actors create numerous fake accounts or bots to capture a higher proportion of airdrop tokens. These attackers not only manipulate the token distribution system but also significantly dilute the airdrop value for real users, undermining the fairness and broad purpose of token airdrops.
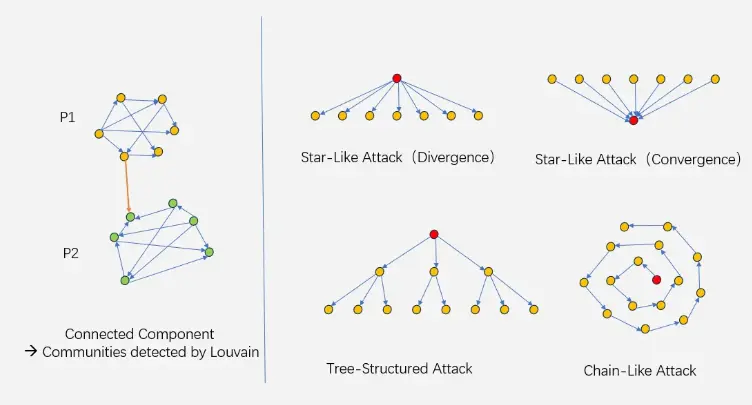
The prevalence of witch attacks has reached a concerning level, leading to significant losses.
Two recent notable airdrop cases illustrate this well:
- Celestia Airdrop
Celestia's $TIA airdrop became a victim of large-scale witch attacks. Malicious actors stole over 55% of the airdrop tokens. These attackers used at least 106,491 proxy wallets to transfer an astonishing 28.92 million $TIA tokens. At the peak price of $TIA, these airdrop tokens were worth over $500 million.
- Arbitrum Airdrop
The Arbitrum airdrop faced a similar fate. Approximately 150,000 witch addresses and groups harvested over 253 million $ARB tokens - accounting for 21.8% of the total airdrop volume.
These cases highlight the urgent need for improvements in airdrop mechanisms. As the crypto ecosystem evolves, preventing such attacks is not only a technical challenge but also a key factor in maintaining trust, fairness, and long-term development between cryptocurrencies and their communities.
Vitalik's Insights: How to Plan Better Airdrops
In a recent Twitter post, Vitalik Buterin outlined the challenges of designing more effective airdrops. As Vitalik observed, an ideal airdrop should reward genuine community members, recognize substantial community contributions, maintain a degree of fairness, and resist witch exploitation. These airdrop goals align perfectly with the vision of "blockchain-based identity, credential, and attestation frameworks."
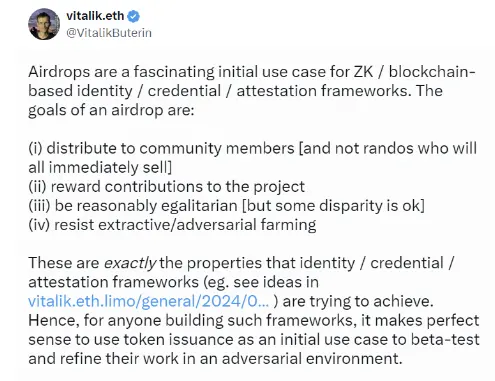
"Blockchain-based identity, credential, and attestation frameworks" represent a new approach to managing digital identities and verifying claims in the digital world. Among them, attestation frameworks play a crucial role in digital verification systems. Attestation frameworks allow third parties to verify specific claims of an identity, thereby establishing a vast trust network. For example, universities can verify students' degrees, employers can verify workers' skills, or governments can verify citizens' residency status. The immutability and transparency of blockchain ensure that blockchain-based attestations are tamper-proof and easily verifiable.
More importantly, attestation frameworks give users fine control over their information, allowing them to selectively disclose verified information without revealing unnecessary personal data. This feature is particularly valuable in scenarios like token airdrops, where project teams can use attestations to verify users' airdrop eligibility without infringing on user privacy. Attestation frameworks work in conjunction with identity and credential systems to build trust and reputation in a decentralized and secure manner. This combination brings enhanced privacy protection, improved security, and streamlined verification processes to the digital realm.
The Emergence of Sign Protocol and TokenTable
So the question arises: how can we leverage blockchain attestation frameworks to design better airdrops? Let's take a look at Sign Protocol, an attestation protocol that implements standardized interoperable credentials and on-chain labels.
1. Sign Protocol
Sign Protocol is a full-chain attestation system designed to create and verify digital claims across multiple blockchain networks. At its core, Sign Protocol achieves the verifiability and accessibility of blockchain attestations.
To understand Sign Protocol, you can think of it as the digital notary of the internet age. Just as notaries in the real world verify and stamp important documents, Sign Protocol does something similar in the digital world, but it is applicable to notarizing various digital claims and information. Essentially, Sign Protocol uses cryptography (which can be seen as unbreakable digital codes) to create super-secure digital signatures: these are not just images of signatures - they are mathematical proofs that are nearly impossible to forge.
Through these digital signatures, Sign Protocol can turn claims into facts. Suppose you want to prove that you are a five-year loyal customer of a particular coffee shop. Instead of just making a verbal statement, Sign Protocol allows the coffee shop to "prove" your loyalty in a digital form. Now, you have a verifiable "Coffee Expert" digital badge!

One of the coolest features of Sign Protocol is that it is designed to work across different blockchains and even off-chain. It's like having a universal passport that can prove your digital identity and achievements. This versatility unlocks a variety of application scenarios. For example, users can earn an ENS badge on Ethereum as proof of being early adopters of ENS domains. At the same time, they can receive an on-chain summer badge on Base as proof of active participation. Additionally, participants attending TON Society offline gatherings can also receive a soulbound token (SBT) as a digital record of their actual interaction with the community. These diverse badges and SBTs can serve as ideal digital proofs for generating various on-chain labels, thereby building a comprehensive digital identity and user profile.
2. TokenTable
Based on digital proofs, Sign Protocol has developed a complete ecosystem of applications. Among them, TokenTable is one of the most popular tools in the Sign Protocol suite.
In short, TokenTable is like a Swiss Army knife for token management, providing a range of tools to manage and distribute tokens efficiently and transparently. Through a customizable claiming interface, TokenTable can achieve precise, transparent, and automated token distribution across multiple chains. The platform also empowers project teams with the ability to customize airdrops precisely by integrating specific parameters such as lock-up periods and vesting schedules.
Notably, with the support of Sign Protocol, TokenTable allows for various access mechanisms, including:
- KYC Access: Ensuring that only KYC-verified users can claim tokens, similar to showing an ID at an exclusive club.
- NFT Access: Allowing specific NFT holders to claim tokens, akin to a VIP pass for token access.
- Token/Proof Access: Controlling access based on holding certain tokens or possessing specific credentials.
To date, TokenTable has supported over 15 blockchains, covering everything from EVM-compatible blockchains to Solana and TON networks. TokenTable has distributed tokens worth over $807 million to more than 33.5 million addresses. This user base is 50 times and 25 times the total number of $ARB and $STRK airdrop addresses, respectively. In a recent milestone token airdrop, TokenTable facilitated the distribution of $DOGS tokens to over 42 million eligible Telegram users, setting a record for the largest airdrop in cryptocurrency history.

Airdrop Reimagined: The Practice of Sign Protocol + TokenTable
The powerful collaboration between Sign Protocol and TokenTable is poised to revolutionize traditional airdrop methods. This innovative combination builds a comprehensive solution that directly addresses the core pain points long faced by token airdrops.
Sign Protocol acts like a digital notary for verifying user identities and achievements. It mitigates witch attacks by creating tamper-proof on-chain labels—such as certified digital badges for KYC verification, community participation proof, and validation of specific skills or contributions—while identifying genuine community members and implementing KYC for identity verification and regulatory compliance when necessary. Meanwhile, TokenTable uses proofs to determine who can receive what in the airdrop. It functions like a vending machine, dispensing tokens only to those with the correct "digital key."
By combining the powerful verification capabilities of Sign Protocol with the flexible distribution features of TokenTable, project teams can create airdrops that are safer, more efficient, more attractive, and fairer. This synergy encourages genuine community building and rewards true supporters, creating a more valuable and sustainable token ecosystem.
Imagine a scenario where a decentralized finance (DeFi) platform on the TON network wants to use an airdrop to reward early adopters and guide community building. By leveraging Sign Protocol and TokenTable, they can:
- Verify users' past interactions with their smart contracts, community projects, and offline gatherings.
- Employ KYC/NFT/token access mechanisms to filter out witches and verify users' authenticity or loyalty.
- Allocate and distribute tokens on Telegram based on engagement or account age, setting up custom vesting plans.
The combination of Sign Protocol and TokenTable opens up a wealth of innovative strategies for effective airdrops. The fine control over airdrop eligibility standards sets a new benchmark for project teams on how to align token distribution with long-term ecosystem growth. Crucially, it maximizes the number of genuine token holders at the token launch, transforming individuals from diverse backgrounds into active stakeholders in the community.
This large-scale airdrop distribution method could become a powerful catalyst for the mass adoption of cryptocurrencies. By maximizing token allocation to community users, project teams can quickly establish a diverse and highly engaged community, where every user has a vested interest in the project's success. As more project teams adopt this forward-thinking airdrop strategy in the future, we anticipate the emergence of a new narrative characterized by large-scale participation, value-driven engagement, and community-centered development in the token economy.
Beyond Airdrops: New Application Scenarios
The applications of Sign Protocol and TokenTable are not limited to airdrops. Looking at a broader digital future, these two innovations are expected to unlock more vibrant real-world use cases.
This "web3 magic" combination aims to break down the walled gardens of traditional Web2 markets, paving the way for free movement and universal reputation across digital ecosystems. By capturing on-chain and off-chain information, Sign Protocol seeks to put as much data on-chain as possible, thereby democratizing access to user reputation and identity. Crypto projects can easily utilize this data to explore various new use cases, such as:
- Real World Asset (RWA) Verification: Bridging the physical and digital worlds through verifiable labels.
- Decentralized Reputation Systems: Personal crypto resumes that include real-world and on-chain experiences and achievements.
- Governance 2.0: Weighted governance voting rights based on verifiable on-chain credentials.
- Cross-Chain Interoperability: A universal crypto identity applicable wherever you go.
Conversely, Web2 projects can also leverage Sign Protocol to find specific marked audiences and incentivize their offline participation, thereby building organic online communities. This enables traditional platforms to utilize blockchain-based tools to enhance user acquisition and retention strategies.
TokenTable is not just an airdrop tool. It also achieves a balance of complex control and flexibility in token distribution, particularly adept at handling large-scale distributions at the million-user level. Whether through strategic lock-ups or programmatic releases, TokenTable provides project teams with a one-stop solution, enabling them to automatically distribute crypto assets to eligible users in a user-friendly and cost-effective manner. Imagine a scenario where completing ten coffee purchases (verified on-chain) automatically triggers a smart contract to distribute loyalty badge tokens to the user's account. This is the innovative potential of Web3 magic, creating frictionless, trustless reward systems that enhance user engagement and loyalty.
In summary, the innovations embodied by Sign Protocol and TokenTable have the potential to drive paradigm shifts far beyond the realm of crypto airdrops themselves. As these technologies mature and find broader applications beyond cryptocurrencies, we may witness a paradigm shift in how digital reputation is established and maintained, and how it impacts both on-chain and real-world activities.
Conclusion and Outlook
The evolution of airdrops is an important milestone in the maturation of the crypto ecosystem. However, as airdrops become increasingly popular and involve a wider audience, traditional airdrop models face severe challenges. Issues such as witch attacks and scalability remain unresolved.
As Vitalik pointed out, the answer to these challenges may lie in attestation frameworks. As an emerging solution based on attestation frameworks, Sign Protocol and its ecosystem project TokenTable represent a powerful "web3 magic" combination that will redefine existing concepts of airdrops. Project teams can leverage the robust verification capabilities of Sign Protocol and the flexible distribution mechanisms of TokenTable to create secure, efficient, and truly community-value-aligned airdrop strategies from scratch.
Cryptocurrencies are poised to surpass traditional stocks in promoting community engagement. Token-based models enable more direct and seamless community participation, making them particularly effective in building and maintaining active user bases. As one of the simplest and most effective ways to distribute tokens, airdrops remain the preferred setup for most project teams to establish large-scale, highly engaged communities at TGE. It is foreseeable that more airdrops will emerge in the future, attempting to transform millions of ordinary people into new token holders. In this new paradigm, Sign Protocol and TokenTable act as the Trojan horse of this round of transformation, aiming to accelerate the establishment of broader, fairer, and more attractive decentralized digital communities.
Looking ahead, the impact of these emerging technologies, Sign Protocol and TokenTable, extends far beyond the airdrop activities themselves. They have the potential to break down the walled gardens of the Web2 world, creating a new universal digital identity and reputation paradigm across various ecosystems. From verifying real-world assets and implementing Governance 2.0 models to creating cross-chain identity interoperability, these use cases are laying a solid foundation for a more interconnected and trusted Web3 vision.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



