As the TON ecosystem grows, while looking for quality project investments, don't forget to protect your asset security.
Author: Keystone Chinese
This year, TON (The Open Network) has garnered a lot of attention. As a public chain deeply integrated with Telegram, with a large user base, the wealth effect of new projects has led users to want to enter the TON ecosystem and find their own Alpha.
As the saying goes: where there are people, there is a community, and where there is traffic on the public chain, hackers will swarm like sharks smelling blood. As a public chain with technical features different from EVM, when interacting on TON, we cannot rely on the security habits of EVM.
As a hardware wallet manufacturer actively promoting integration with the TON ecosystem, we have compiled some security suggestions to help everyone safely embrace the TON ecosystem. 🤗
I. Correctly choose a wallet
Due to different technical implementations, commonly used EVM wallets such as Metamask and Rabby currently do not support TON, so we need to install a wallet that supports TON.
At this time, a wallet with high security is crucial for us. We can evaluate which wallet is more suitable for us based on whether the wallet is open source, supports hardware wallets, and especially whether the wallet's parsing of transaction information is comprehensive.
For example, when facing phishing websites on TON, when hackers try to transfer some assets from my wallet, the transaction parsing results of wallet software OpenMask and TonKeeper @tonkeeper are quite different, as shown in the following image:
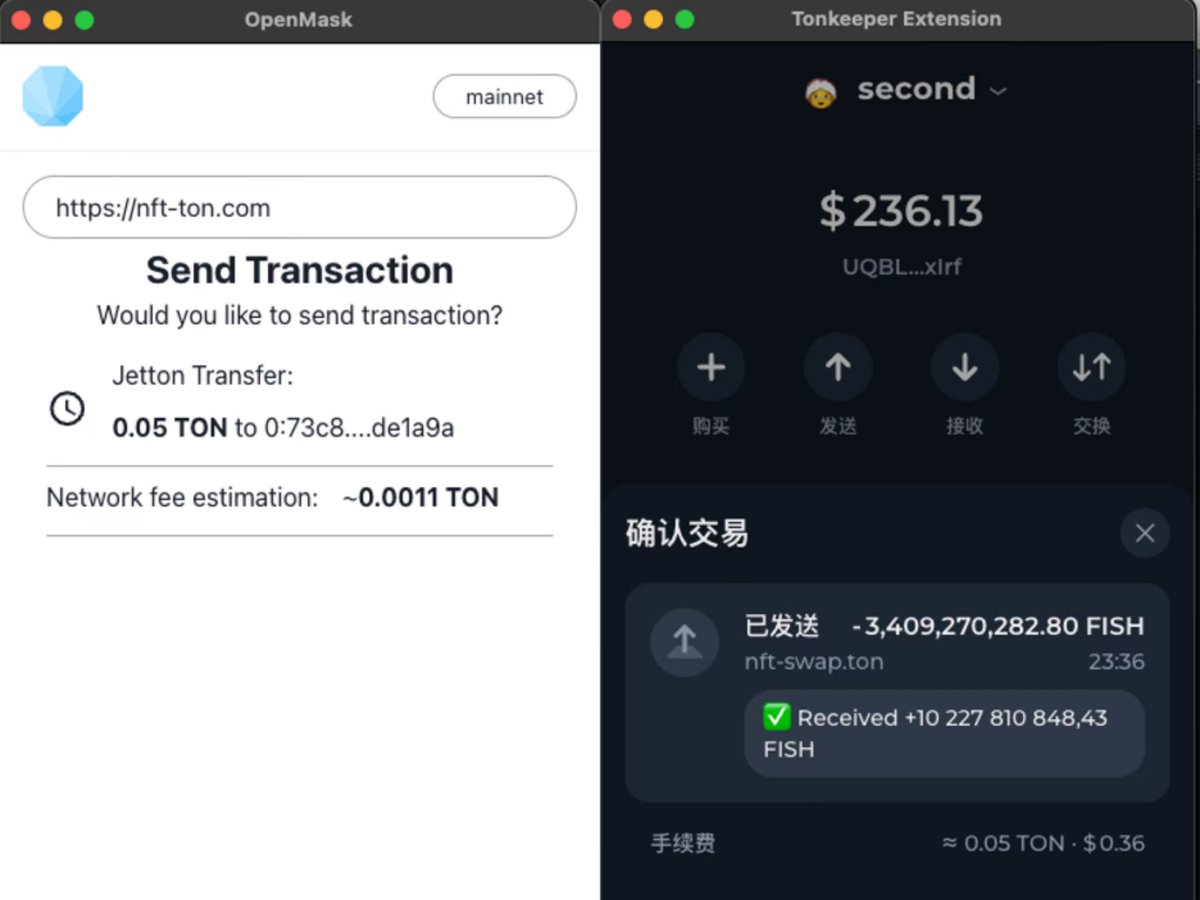
In OpenMask, this appears to be a normal "claim airdrop" transaction, but is this really the case?
For the same transaction, Tonkeeper has revealed more information for us, indicating that the phishing website is trying to steal the FISH tokens from the wallet, and the hacker's behavior has been successfully exposed by Tonkeeper.
In comparison, which wallet do you think is more likely to deceive its users?
A more secure wallet, like a "demon-revealing mirror," can effectively reduce users' anxiety in identifying phishing scams. Recently, Keystone has successfully integrated with TonKeeper, and we believe that the addition of hardware wallets can significantly enhance user security on TON.
II. Guard against common phishing forms
Like other public chains, phishing is also the most common and widespread form of attack on TON. Let's take this opportunity to understand the phishing methods used by hackers on TON:
1. Zero-amount transfer phishing
Hackers send TON with a value of 0 to many addresses in batches, and then add transaction notes to the transfer transactions such as "claim 1000 TON airdrop, visit "http://xxxxx.com," etc. "Inexperienced" users may fall for this and visit the phishing website, and then engage in the so-called claiming interaction, only to have their valuable assets stolen by hackers.
2. NFT airdrop phishing
In addition to token transfers, hackers also attempt to airdrop NFT to user wallets for phishing. Besides attractive images, the NFT also contains the URL of a phishing website to deceive users.
For example, in the following case, the NFT airdropped to the user contains a fake fragment market link. When the user enters the fake market and tries to list the airdropped NFT for sale, they fall into the hacker's trap, not only failing to sell the NFT but also having other assets transferred away.
3. Be wary of TON's unique "transaction comments" feature
Transfer transactions on TON have an optional comment field, which we can understand as the transaction note in a bank transfer. This was originally a convenient feature for users, but it has also been exploited by malicious phishing websites.
As shown in the image below, the hacker attempts to trick the user into transferring out FISH tokens from the wallet and writes "Received +xxx,xxx,xxx FISH" in the transaction comment, misleading the user into thinking they will receive more FISH tokens than the current amount, thereby confirming the transaction.
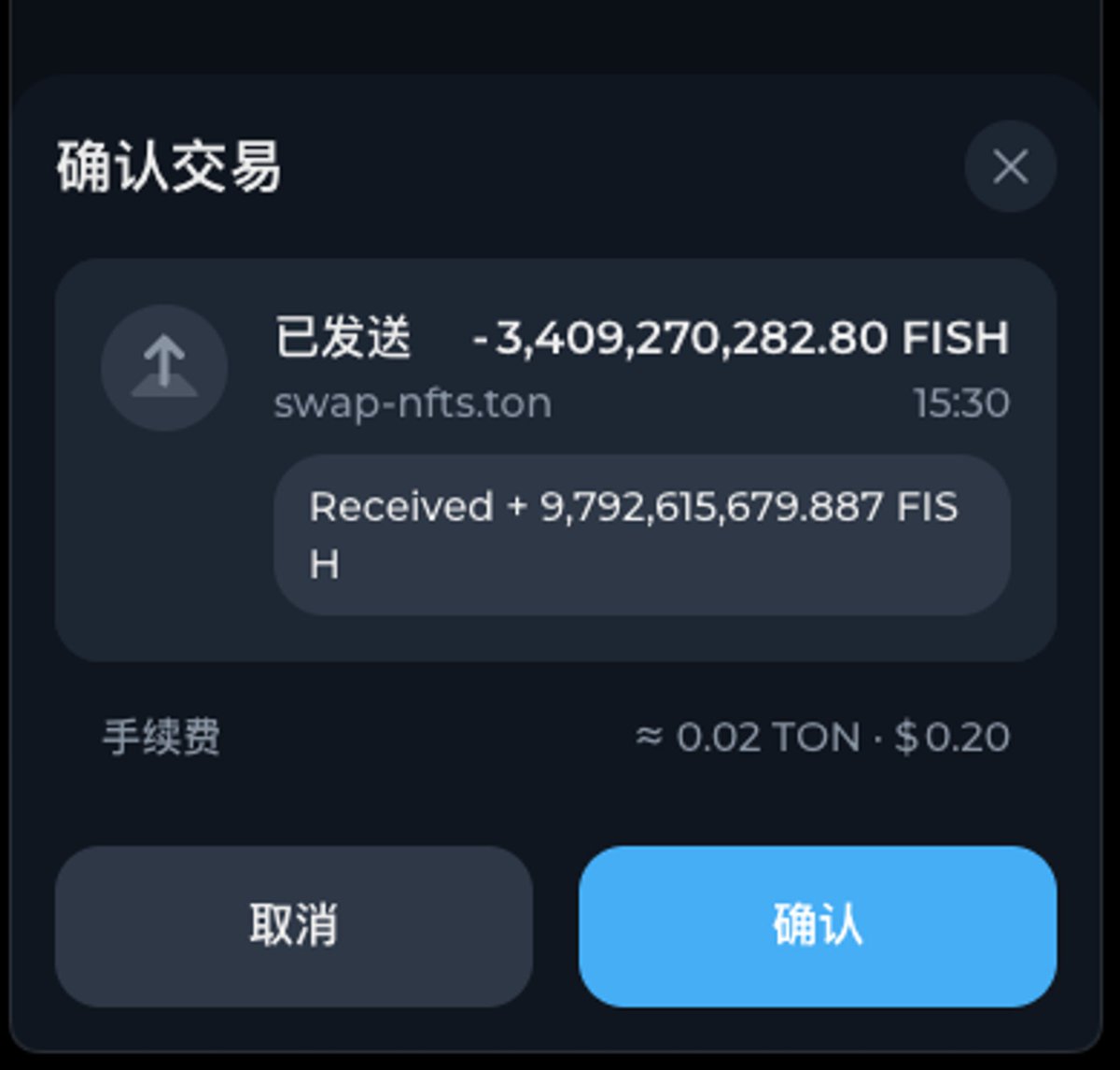
Here we remind everyone not to trust any content in the transaction comments, and we hope that in the future, various wallet software will provide clearer security prompts for transaction comments.
III. Use blockchain explorers to identify fraudulent phishing
On Ethereum, we often use etherscan to view on-chain information, while on TON, the corresponding tools are tonscan and tonviewer.
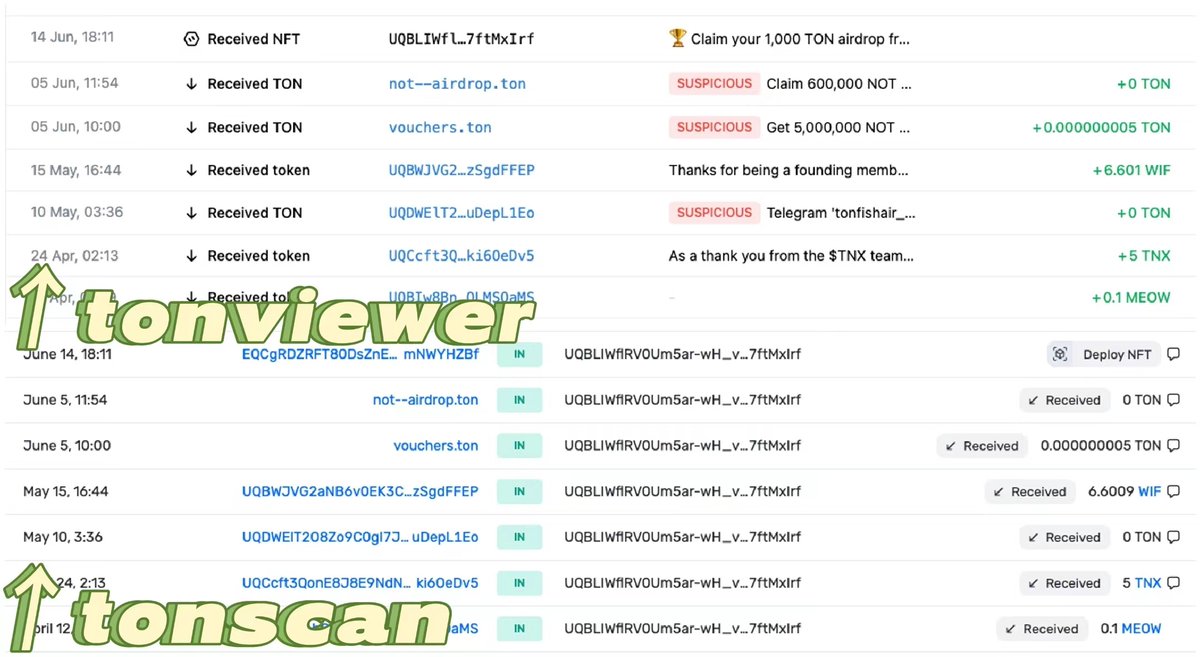
By comparing the security features of the two, we can see that tonviewer excels in identifying fraudulent phishing: not only does it provide a "SUSPICIOUS" suspicious prompt for transactions suspected of phishing, but it also adds the word "SCAM" for fraudulent NFT airdrops, preventing users from being deceived.

In contrast, tonscan only displays on-chain information and lacks some security-related prompts. We recommend that users who have just entered the TON ecosystem prioritize using tonviewer to view wallet address information.
IV. Further ensure security using a hardware wallet
On any public chain, using a hardware wallet to air-gap the mnemonic and perform secondary verification of transactions are effective means of protecting assets. Keystone's integration with the TonKeeper wallet allows TON ecosystem users to enjoy the security benefits of hardware wallets. For hardware wallet users, we have the following suggestions:
• Use a hardware wallet to store large assets
• Use Keystone's 3 sets of mnemonics to separate assets into multiple wallets to prevent single-point risks
• Carefully review the transaction information displayed by Keystone to avoid signing phishing transactions
In the blockchain world, opportunities often coexist with risks. As the TON ecosystem grows, while looking for quality project investments, don't forget to protect your asset security. Keystone is also willing to continue BUIDL with all parties in the TON ecosystem to build a secure interactive environment.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




