One day, someone suddenly gives you a wallet address private key worth 1 million US dollars. Would you want to transfer the money immediately?
Introduction
OKX Web3 has specially planned the "Security Special Issue" column to address different types of on-chain security issues. Through real-life cases happening around users and joint sharing and answers from security experts or institutions, different perspectives are used to comprehensively summarize and summarize security trading rules, aiming to strengthen user security education and help users learn to protect private keys and wallet assets from themselves.
One day, someone suddenly gives you a wallet address private key worth 1 million US dollars. Would you want to transfer the money immediately?
If so, then this article is tailored for you.
This article is the 1st issue of OKX Web3's "Security Special Issue," and it has invited the well-known security organization in the encryption industry, SlowMist Security Team, to share from the most real cases encountered by users, full of practical content!
SlowMist Security Team: Thank you very much for the invitation from OKX Web3. SlowMist, as a leading blockchain security company, mainly provides services such as security audits and anti-money laundering tracking and tracing to a wide range of customers, and has built a solid threat intelligence cooperation network. In 2023, SlowMist assisted customers, partners, and publicly frozen funds involved in hacking incidents, totaling more than 12.5 million US dollars. We hope to continue to output valuable things with awe for the industry and security.
OKX Web3 Security Team: Hello, everyone. We are very happy to share this time. The OKX Web3 security team is mainly responsible for the security capability building of OKX Web3 wallet, providing multiple protection services such as product security, user security, and transaction security, guarding the security of user wallets 24/7, and contributing to the maintenance of the entire blockchain security ecosystem.
Q1: Can you share some real theft cases?
SlowMist Security Team: First, most cases are due to users storing private keys or mnemonic phrases online. For example, users often use cloud storage services such as Google Docs, Tencent Docs, Baidu Cloud, WeChat Favorites, and Notes to store private keys or mnemonic phrases. Once these platform accounts are collected and "cracked" by hackers, private keys are easily stolen.
Second, users downloading fake apps have led to private key leaks. For example, one of the most typical cases is the multi-signature scam, where fraudsters induce users to download fake wallets and steal wallet mnemonic phrases, then immediately modify the account permissions of the user's wallet: changing the wallet account permissions from the user alone to jointly held by the user and the fraudster, thereby seizing control of the wallet account. These fraudsters often remain patient, waiting for the user's account to accumulate a certain amount of encrypted assets before transferring them all at once.
OKX Web3 Security Team: SlowMist has outlined the two main situations in which private keys are stolen. In the second case, the essence of fraudsters using fake apps to steal user private keys is a Trojan program. This type of Trojan program steals user private keys by obtaining access to user input methods, photos, and other permissions. Compared to iOS users, Android users encounter more Trojan virus attacks. Here are two simple cases:
Case one: A user reported that their wallet assets were stolen. After our team communicated and investigated with the user, we found that it was because the user had previously searched, downloaded, and installed a disguised software of a certain data platform through Google search, which turned out to be a Trojan program. However, because the link to this platform software appeared in the top 5 of Google search results, the user mistakenly thought it was the official software. In fact, many users do not discern the links provided by Google, so it is very easy to encounter Trojan attacks in this way. We recommend that users enhance daily security protection through firewalls, antivirus software, and Hosts configuration.
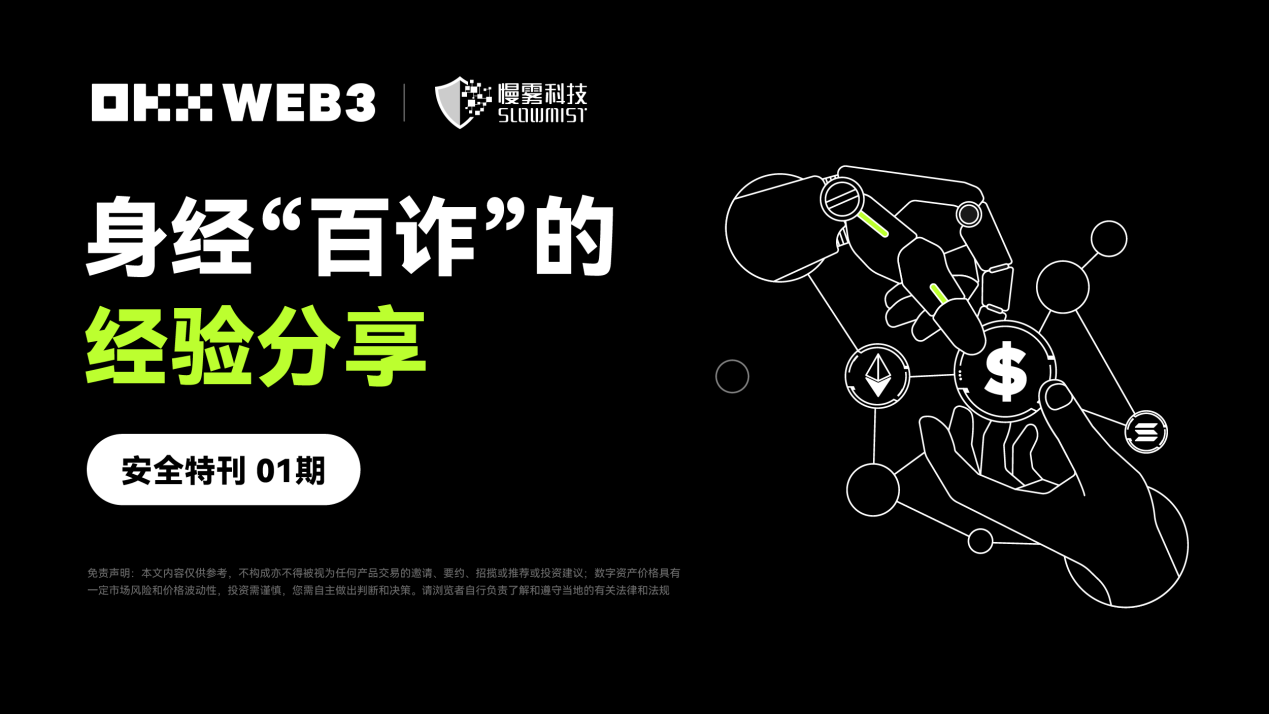
Case two: A user reported that their wallet assets were stolen when investing in a certain DeFi project. However, through our analysis and investigation, we found that the DeFi project itself was not the issue. User B's wallet assets were stolen because when they commented on the project on Twitter, they were impersonated by the official customer service of the DeFi project. Under the guidance of this fake customer service, they clicked on and entered a fake link and entered the mnemonic phrase, resulting in the theft of wallet assets.
It can be seen that the methods of scammers are not sophisticated, but users need to increase their discernment. Under no circumstances should they easily disclose their private keys. In addition, our wallet has provided security risk alerts for this malicious domain.
Q2: Are there the best methods for private key storage? What alternative solutions are currently available to reduce reliance on private keys?
SlowMist Security Team: Private keys or mnemonic phrases are actually a single point of failure. Once stolen or lost, it is difficult to recover. Currently, new technologies such as secure multi-party computation (MPC), social authentication technology, Seedless/Keyless, pre-execution, and zero-knowledge proof technology are helping users reduce their reliance on private keys.
Taking MPC as an example, first, MPC technology refers to all participants executing complex joint calculations to complete a task, while keeping their data private and secure, not shared with other participants. Second, in layman's terms, an MPC wallet uses MPC technology to securely break a private key into multiple pieces, managed by multiple parties; or simply, multiple parties jointly generate a virtual key, and the latter situation may be more common because at this point, no one has ever seen the complete private key. In short, the core idea of MPC is to decentralize control to disperse risk or enhance disaster recovery, effectively avoiding security issues such as single points of failure.
Note that MPC involves a term called Keyless, which can be understood as "without a mnemonic phrase" or "without a private key." However, this "without" does not mean the actual absence of a key, but rather that the user does not need to back up a mnemonic phrase or private key and is not aware of their existence. Therefore, regarding Keyless wallets, it is important to understand these three points:
During the creation of a Keyless wallet, the private key is not created or stored at any time or place.
When signing a transaction, the private key is not involved, and the private key is never reconstructed at any time.
A Keyless wallet does not generate or store complete private keys and seed phrases at any time.
OKX Web3 Security Team: There is currently no perfect way to store private keys. However, our security team recommends using hardware wallets, manually copying and saving private keys, setting up multi-signature, and dispersing storage of mnemonic phrases to manage private keys. For example, dispersing storage of mnemonic phrases means that users can divide the mnemonic phrase into 2 or more groups for storage, reducing the risk of the mnemonic phrase being stolen. For example, setting up multi-signature means that users can select trusted individuals to jointly sign to determine the security of transactions.
Of course, to ensure the security of user wallet private keys, the entire underlying system of the OKX Web3 wallet is not connected to the internet. User mnemonic phrases and private key-related information are all encrypted and stored locally on the user's device, and the related SDK is also open source, extensively verified by the technical community, and more transparent. In addition, the OKX Web3 wallet has undergone strict security audits through cooperation with well-known security organizations such as SlowMist.
Furthermore, to better protect our users, the OKX Web3 security team is providing and planning more powerful security capabilities for private key management, and is continuously iterating and upgrading. Here is a brief sharing:
Two-factor encryption. Currently, most wallets usually encrypt mnemonic phrases with a password and store the encrypted content locally. However, if a user is infected with a Trojan virus, the Trojan will scan the encrypted content and monitor the password entered by the user. If the fraudster listens in, they can decrypt the encrypted content and obtain the user's mnemonic phrase. In the future, the OKX Web3 wallet will encrypt mnemonic phrases using a two-factor method, so even if fraudsters obtain the user's password through a Trojan, they cannot unlock the encrypted content.
Private key copy security. Most trojans steal information from the user's clipboard when copying the private key, leading to the leakage of the user's private key. We plan to increase the security of the user's private key copying process, such as copying partial private keys, timely clearing clipboard information, and other methods or features to help users reduce the risk of private key information being stolen, and so on.
Q3: From the perspective of private key theft, what are the common phishing methods currently?
SlowMist Security Team: According to our observations, phishing activities are gradually increasing every month.
First, wallet drainers constitute the main threat of phishing activities, continuously attacking ordinary users in various forms.
Wallet drainers are a type of malicious software related to cryptocurrencies, deployed on phishing websites to deceive users into signing malicious transactions, thereby stealing the user's wallet assets. For example, currently active wallet drainers include:
Pink Drainer, which uses social engineering to obtain Discord Tokens and conduct phishing. Social engineering is commonly understood as obtaining a user's private information through communication.
Angel Drainer, which conducts social engineering attacks on domain name service providers. After obtaining domain account permissions, Angel Drainer modifies DNS resolution and redirects users to fake websites, and so on.
Second, the most common is blind signature phishing, where users interact with a project without knowing the content they are authorizing, leading to the loss of funds. Regarding blind signature phishing, we have a few examples:
Example 1: For example, eth_sign. eth_sign is an open signature method that allows signing any hash, meaning it can be used to sign transactions or any data. It is difficult for users without technical knowledge to understand the content of the signature, posing a phishing risk. Fortunately, more and more wallets have started to provide security reminders for this type of signature, which can to some extent avoid some risks of asset loss.
Example 2: Permit signature phishing. In ERC20 token transactions, users can call the approve function to authorize, but the permit function allows users to generate a signature off-chain and authorize a specified user to use a certain amount of tokens. Attackers use the permit method for phishing. When the victim visits the phishing website, the attacker prompts the user to sign the permit authorization. After the user signs, the attacker can obtain the signed data, call the token contract's permit function with the signature data, and then broadcast it to the chain to obtain authorization for the tokens, thereby stealing the user's tokens.
Example 3: Covert create2 technique. create2 allows developers to predict the address of a contract before deploying it to the Ethereum network. Based on create2, attackers can generate temporary new addresses for each malicious signature. After deceiving the user into signing the authorization, the attacker can create a contract at this address and transfer the user's assets. Because these addresses are blank, they can bypass some phishing plugins and security company monitoring alerts, making them highly covert and easy for users to fall victim.
In summary, users can authenticate the official website of a project before interacting and be vigilant for any malicious signature requests during the interaction. They should also be cautious about submitting mnemonic phrases or private keys, and never disclose them anywhere.
OKX Web3 Security Team: We have researched common phishing methods and provided multidimensional security protection on the product side. Here are the main types of phishing methods users currently encounter:
The first type is fake airdrops. Hackers typically generate addresses similar to the victim's address and conduct small transfers, 0U transfers, or fake token transfers as airdrops, which will be displayed in the user's transaction history. If the user accidentally copies and pastes the wrong address, it can result in asset loss. OKX Web3 Wallet can identify these historical transactions and mark them as risky, and provide security risk prompts when users transfer to these addresses.
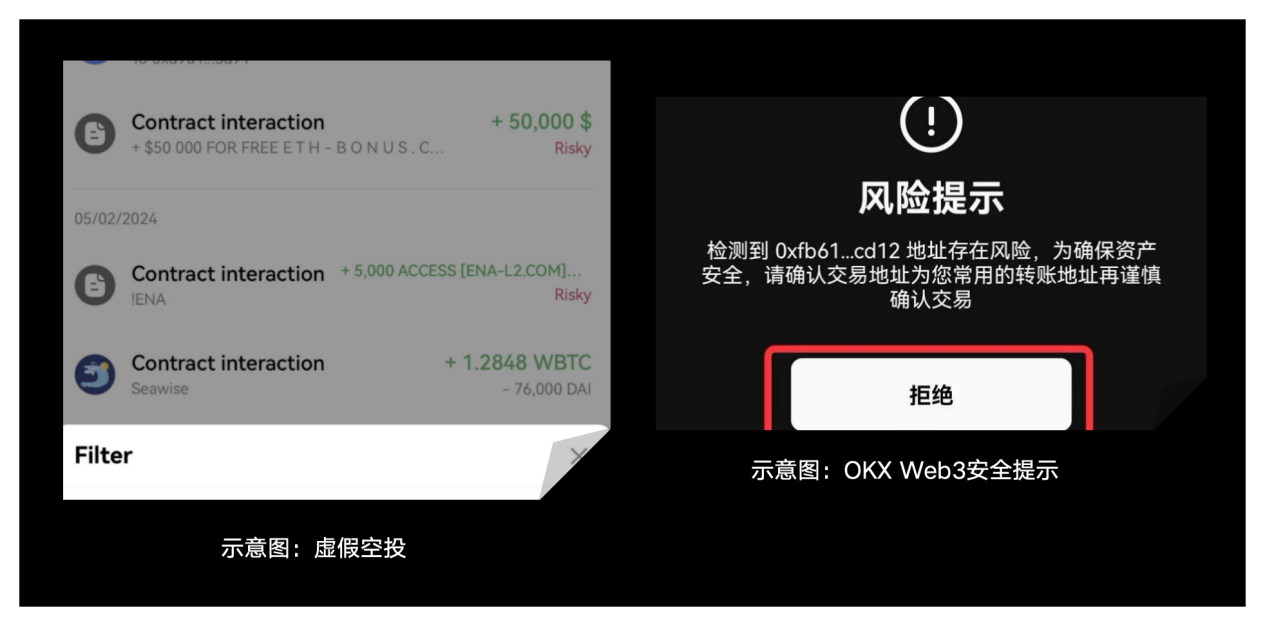
The second type is induced signature. Typically, hackers comment on well-known projects on Twitter, Discord, TG, and publish fake DeFi project URLs or URLs for claiming airdrops, inducing users to click and steal their assets. In addition to the signature phishing mentioned by SlowMist, there are also:
Method 1: Direct transfer to steal mainnet tokens. Hackers often name malicious contract functions as Claim, SeurityUpdate, and other suggestive names, with empty actual function logic, only transferring the user's mainnet tokens. The OKX Web3 Wallet has launched the pre-execution function, which can display on-chain asset changes and authorization changes, providing security risk prompts to users.
Method 2: On-chain authorization. Hackers typically induce users to sign approve / increaseAllowance / decreaseAllowance / setApprovalForAll transactions, allowing the hacker's specified address to transfer the user's token assets. Once the user signs, the hacker monitors the user's account in real-time, immediately transferring any corresponding assets that come in. Protecting against phishing attackers is a process of confrontation and continuous upgrading.
Although most wallets perform security risk checks on the attacker's authorized addresses, attackers are also upgrading their attack methods. For example, using the features of create2, attackers can pre-calculate new addresses, which are not in the secure black address library, allowing them to easily bypass security checks. Attackers wait for a victim to take the bait, then deploy a contract at that address and transfer the user's funds. For example, we have also found many attackers who make users authorize the uniswap.multicall contract, which is a legitimate project contract and can also bypass security product checks.
Method 3: Permission changes: including tron permission changes and solana permission changes. In tron permission changes, multisig is a feature of the tron chain. In many phishing websites, attackers disguise account permission change transactions as transfer transactions. If the user accidentally signs this transaction, the user's account becomes a multisig account, and the user loses control of their account. In solana permission changes, attackers use SetAuthority to change the owner of the user's token ATA account. Once the user signs this transaction, the owner of the ata account becomes the attacker, allowing the attacker to obtain the user's assets.
Other methods: Additionally, due to protocol design mechanisms and other issues, they are also easily exploited by phishers. The EigenLayer middleware protocol on Ethereum allows the queueWithdrawal call to specify another address as the withdrawer. If the user signs this transaction, seven days later, the specified address can use completeQueuedWithdrawal to obtain the user's staked assets.
The third type is uploading mnemonic phrases. Attackers typically provide disguised airdrop projects or fake new tools, inducing users to upload private keys or mnemonic phrases. Specific cases are as mentioned above. Sometimes, attackers also disguise as plugin wallet pop-ups to induce users to upload mnemonic phrases.
Q4: Differentiated attack methods for hot wallets and cold wallets
OKX Web3 Security Team: The difference between hot wallets and cold wallets lies in the different ways private keys are stored. The private key of a cold wallet is generally stored offline, while the private key of a hot wallet is usually stored in an online environment. Therefore, the security risks for cold wallets and hot wallets will be different. The security risks of hot wallets have been comprehensively covered above and will not be further elaborated.
The main security risks of cold wallets include:
First, there are risks of social engineering and physical attacks, as well as transaction risks. Regarding the risks of social engineering and physical attacks, since cold wallets are usually stored offline, there may be attackers using social engineering to impersonate relatives or friends to gain access to the cold wallet.
As a physical device, it may be damaged or lost. Regarding transaction risks, cold wallets also encounter various types of attacks such as airdrops and induced signature scenarios mentioned earlier during transactions.
Q5: In addition to the "giving away high-value wallet private keys" mentioned at the beginning, what are some other alternative phishing traps?
SlowMist Security Team: Yes, "intentionally giving away high-value wallet private keys" is a very classic case that appeared many years ago, but people still fall for it today. In this scam, the fraudster intentionally leaks the private key or mnemonic phrase. Once you import the private key or mnemonic phrase into your wallet, the attacker monitors your wallet and immediately transfers the ETH as soon as you deposit it. This method takes advantage of users' greed. The more people who import the private key, the higher the transaction fees, resulting in greater losses.
Furthermore, some users may think "I have nothing worth attacking," which is a defensive mindset that makes users more susceptible to attacks. Any person's information (such as email, password, bank information, etc.) is valuable to attackers. Some users even believe that as long as they don't click on links in spam emails, they won't be threatened, but some phishing emails may implant malicious software through images or attachments.
Finally, we need to have an objective understanding of "security," which is that there is no absolute security. Moreover, phishing attacks evolve rapidly and in various ways, so everyone should continue to learn and improve their self-security awareness, which is the most reliable approach.
OKX Web3 Security Team: Preventing third-party phishing traps is indeed a complex issue because phishers often exploit people's psychological weaknesses and common security oversights. Many people are usually cautious, but when faced with a sudden "windfall," they often relax their vigilance and magnify their own greedy nature, leading to falling for scams. In this process, human weaknesses outweigh technology. Even with more security measures, users may temporarily overlook them. It is only after the fact that they realize they have been scammed. We need to be clear that "there is no such thing as a free lunch" and always be vigilant, especially in the dark forest of blockchain.
Q6: Suggestions for users to improve the security of their private keys
SlowMist Security Team: Before answering this question, let's first review how attackers steal users' assets. Attackers generally steal users' assets through the following two methods:
Method 1: Deceiving users to sign malicious transaction data to steal assets, such as deceiving users to authorize or transfer assets to the attacker.
Method 2: Deceiving users to enter the wallet's mnemonic phrase on a malicious website or app, such as deceiving and luring users to enter the wallet's mnemonic phrase on a fake wallet page.
Knowing how attackers steal wallet assets, we need to take precautions against potential risks:
Prevention 1: Strive for "see before sign." It is said that the wallet is the key to entering the Web3 world, and the most important thing for users is to refuse blind signatures. Before signing, users should identify the data to be signed and understand what the transaction they are signing is for, otherwise, they should refrain from signing.
Prevention 2: Don't put all your eggs in one basket. By managing wallets in layers based on different assets and usage frequency, users can control the risk of assets. Wallets used for activities such as airdrops, which have a higher usage frequency, are recommended for storing small amounts of assets. Large assets are generally not frequently used and should be stored in a cold wallet, ensuring the network and physical environment are secure when used. If possible, use a hardware wallet, as it generally cannot directly export mnemonic phrases or private keys, thus raising the threshold for theft.
Prevention 3: Various phishing methods and events are constantly emerging, and users need to learn to recognize various phishing methods, raise their security awareness, self-educate to avoid being deceived, and have the ability to help themselves.
Prevention 4: Don't be hasty or greedy, and use multiple verifications. Additionally, if users want to understand a more comprehensive asset management plan, they can refer to SlowMist's "Cryptocurrency Security Solution" for more security awareness and self-education, or refer to the "Blockchain Dark Forest Self-Rescue Manual."
OKX Web3 Security Team: The private key, as the sole credential for accessing and controlling encrypted assets in a wallet, is crucial to protect.
Prevention 1: Know your DApp. When investing in on-chain DeFi, it is essential to have a comprehensive understanding of the DApp being used to prevent accessing fake DApps and causing asset loss. Although OKX Web3 Wallet has implemented various risk detection and prompts for DApps, attackers continue to update their attack methods and bypass security risk detection. When investing, users must be vigilant.
Prevention 2: Know your signature. When signing on-chain transactions, users must confirm the details of the transaction and be cautious about signing transactions they do not understand. OKX Web3 Wallet parses and simulates on-chain transactions and offline signatures, showing the results of asset changes and authorization changes. Before making a transaction, users should pay close attention to these results to see if they match expectations.
Prevention 3: Know the software you download. When downloading auxiliary trading and investment software, ensure that it is downloaded from the official platform and promptly scan it with antivirus software. If malicious software is downloaded, trojans can obtain the user's mnemonic phrase or private key through methods such as screenshot monitoring, clipboard scanning, and uploading cache files.
Prevention 4: Raise security awareness and properly safeguard the private key. Avoid copying important information such as mnemonic phrases and private keys as much as possible, refrain from taking screenshots, and avoid saving such information to third-party cloud platforms.
Prevention 5: Strong passwords and multi-signature. In using passwords, users should increase the complexity of passwords as much as possible to prevent hackers from cracking encrypted files after obtaining the private key. If there is a multi-signature mechanism during transactions, it should be used to ensure that if one party's mnemonic phrase or private key is compromised, it will not affect the overall transaction.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




