Authors: Liz, Zero, Keywolf, SlowMist Technology
Background
On May 3, according to the monitoring of Web3 anti-fraud platform Scam Sniffer, a whale encountered a phishing attack with the same first and last address digits, resulting in the loss of 1155 WBTC, worth about 70 million US dollars. Although this phishing method has been around for a long time, the magnitude of the loss in this incident is still shocking. This article will analyze the key points of the phishing attack with the same first and last address digits, the destination of the funds, hacker characteristics, and provide suggestions for preventing such phishing attacks.

(https://twitter.com/realScamSniffer/status/1786374327740543464)
Key Points of the Attack
Victim's address:
0x1E227979f0b5BC691a70DEAed2e0F39a6F538FD5
Victim's target transfer address:
0xd9A1b0B1e1aE382DbDc898Ea68012FfcB2853a91
Phishing address:
0xd9A1C3788D81257612E2581A6ea0aDa244853a91
1. Collision to generate phishing address: Hackers will pre-generate a large number of phishing addresses and deploy batch programs in a distributed manner. Based on the dynamic of users on the chain, they initiate phishing attacks with the same first and last address digits to the target transfer address. In this incident, the hacker used an address with the same first 4 digits and last 6 digits as the target transfer address, after removing the "0x".
2. Trailing transactions: After the user makes a transfer, the hacker immediately follows up with a transaction (approximately 3 minutes later) using the generated phishing address (transferring 0 ETH to the user's address), so that the phishing address appears in the user's transaction records.
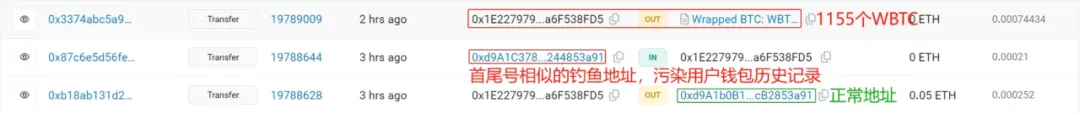
(https://etherscan.io/txs?a=0x1E227979f0b5BC691a70DEAed2e0F39a6F538FD5&p=2)
3. Willing victim: Due to the habit of users to copy the most recent transfer information from the wallet's transaction history, they did not carefully check whether the address they copied was correct after seeing the trailing phishing transaction, resulting in the accidental transfer of 1155 WBTC to the phishing address!
MistTrack Analysis
Using the on-chain tracking tool MistTrack, it was found that the hacker had exchanged 1155 WBTC for 22955 ETH and transferred it to the following 10 addresses.

On May 7, the hacker began transferring the ETH on these 10 addresses. The pattern of fund transfer shows that there is not more than 100 ETH left in the current address, and then the remaining funds are roughly evenly split and transferred to the next layer of addresses. Currently, these funds have not been exchanged for other currencies or transferred to platforms. The image below shows the fund transfer situation on address 0x32ea020a7bb80c5892df94c6e491e8914cce2641. Click the link to view the high-resolution image in the browser:

(https://misttrack.io/s/1cJlL)
Continuing to use MistTrack to query the initial phishing address 0xd9A1C3788D81257612E2581A6ea0aDa244853a91 in this incident, it was found that the source of the transaction fee for this address is 0xdcddc9287e59b5df08d17148a078bd181313eacc.

(https://dashboard.misttrack.io/address/WBTC-ERC20/0xd9A1C3788D81257612E2581A6ea0aDa244853a91)
Following this transaction fee address, it was found that between April 19 and May 3, this address initiated over twenty thousand small transactions, distributing small amounts of ETH to different addresses for phishing.
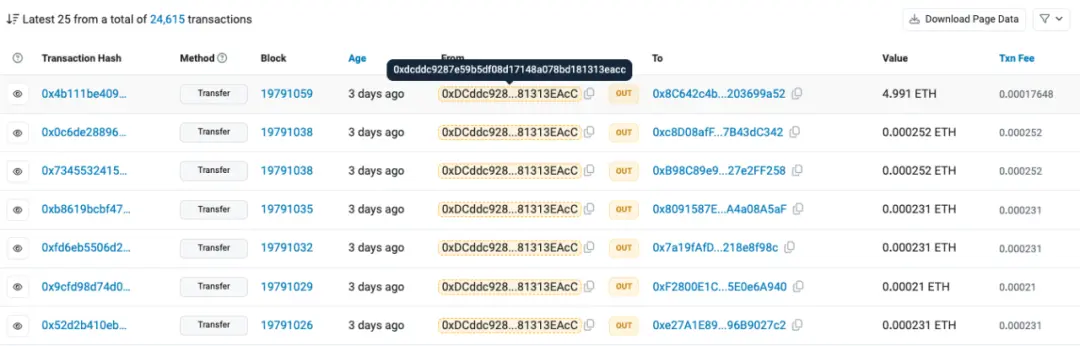
(https://etherscan.io/address/0xdcddc9287e59b5df08d17148a078bd181313eacc)
Based on the above image, it can be seen that the hacker adopted a wide net approach, indicating that there is definitely more than one victim. Through large-scale scanning, other related phishing events were also found, as shown in the following examples:

Taking the phishing address 0xbba8a3cc45c6b28d823ca6e6422fbae656d103a6 in the second event in the above image as an example, by continuously tracing back the transaction fee addresses, it was found that these addresses overlapped with the transaction fee source addresses of the 1155 WBTC phishing event, indicating that they belong to the same hacker.
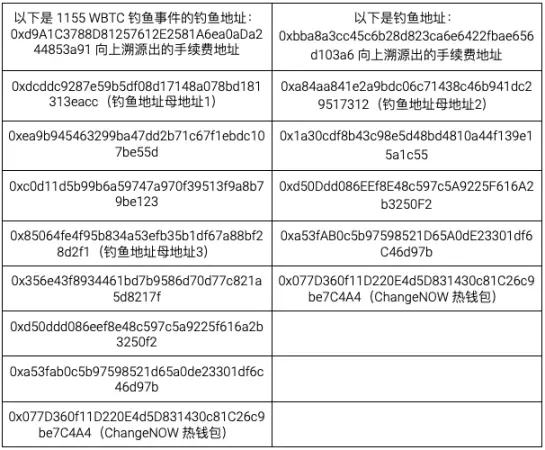
By analyzing the situation of the hacker transferring other profits (since the end of March), it was also concluded that another characteristic of the hacker's money laundering is to convert the funds on the ETH chain into Monero or cross-chain to Tron, and then transfer them to suspected OTC addresses. Therefore, there is a possibility that the hacker will use the same method to transfer the profits from the 1155 WBTC phishing event in the future.
Hacker Characteristics
According to SlowMist's threat intelligence network, it was found that the suspected hacker used mobile base station IPs located in Hong Kong (not ruling out the possibility of using VPN):
- 182.xxx.xxx.228
- 182.xxx.xx.18
- 182.xxx.xx.51
- 182.xxx.xxx.64
- 182.xxx.xx.154
- 182.xxx.xxx.199
- 182.xxx.xx.42
- 182.xxx.xx.68
- 182.xxx.xxx.66
- 182.xxx.xxx.207
It is worth noting that even after stealing 1155 WBTC, it seems that the hacker did not intend to retire.
Following the three phishing addresses (used to provide transaction fees to many phishing addresses) collected earlier, it was found that they share the common characteristic of the last transaction amount being significantly larger than the previous ones. This indicates that the hacker has stopped using the current address and transferred the funds to a new phishing address. Currently, the three newly activated addresses are still involved in high-frequency transfers.

(https://etherscan.io/address/0xa84aa841e2a9bdc06c71438c46b941dc29517312)
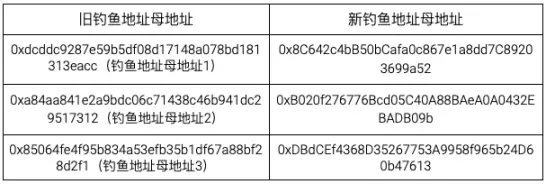
In subsequent large-scale scans, we found two deactivated phishing address master addresses, and after tracing them, we found their association with the hacker. We will not elaborate further on this here.
- 0xa5cef461646012abd0981a19d62661838e62cf27
- 0x2bb7848Cf4193a264EA134c66bEC99A157985Fb8
At this point, we have raised the question of where the hacker's funds on the ETH chain originated from. After tracking and analyzing by the SlowMist security team, we found that the hacker initially carried out the same first and last address digit phishing attack on Tron, and after profiting, targeted users on the ETH chain, transferring the profits from Tron to ETH to start phishing. The image below shows an example of the hacker's phishing on Tron:

(https://tronscan.org/#/address/TY3QQP24RCHgm5Qohcfu1nHJknVA1XF2zY/transfers)
On May 4, the victim conveyed the following message to the hacker on the chain: "You win, brother. You can keep 10%, then give back 90%, and we can pretend nothing happened. We all know that 7 million dollars is enough for you to live well, but 70 million dollars will make you sleepless."
On May 5, the victim continued to call out to the hacker on the chain, but has not received a response yet.
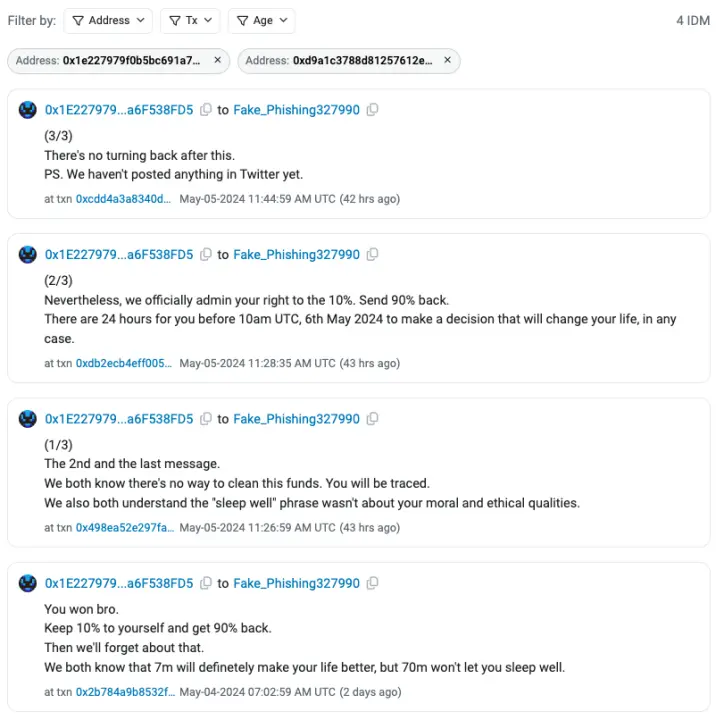
(https://etherscan.io/idm?addresses=0x1e227979f0b5bc691a70deaed2e0f39a6f538fd5,0xd9a1c3788d81257612e2581a6ea0ada244853a91&type=1)
How to Defend
- Whitelist Mechanism: It is recommended that users save the target address in the wallet's address book. The next time they make a transfer, they can find the target address in the wallet's address book.
- Enable Wallet Small Amount Filtering: It is recommended that users enable the wallet's small amount filtering function to block such zero transfers and reduce the risk of phishing. The SlowMist security team has analyzed this phishing method in 2022. Interested readers can click the links to view (SlowMist: Beware of TransferFrom Zero Transfer Scams, SlowMist: Beware of Same Last Digit Airdrop Scams).

- Carefully Verify the Address: It is recommended that users, when confirming an address, at least check whether the first 6 digits and last 8 digits (excluding the initial "0x") are correct, and ideally, check every digit.
- Small Amount Transfer Test: If the user's wallet defaults to displaying only the first 4 digits and last 4 digits of the address, and the user insists on using this wallet, they can consider conducting a small amount transfer test. If unfortunately phished, the damage will be minimal.
Conclusion
This article mainly introduces the phishing attack using the same first and last address digits, analyzes the characteristics of the hacker and the fund transfer pattern, and provides suggestions for preventing such phishing attacks. The SlowMist security team reminds users that due to the tamper-proof nature of blockchain technology and the irreversible nature of on-chain operations, users must carefully verify addresses before conducting any operations to avoid asset losses.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




