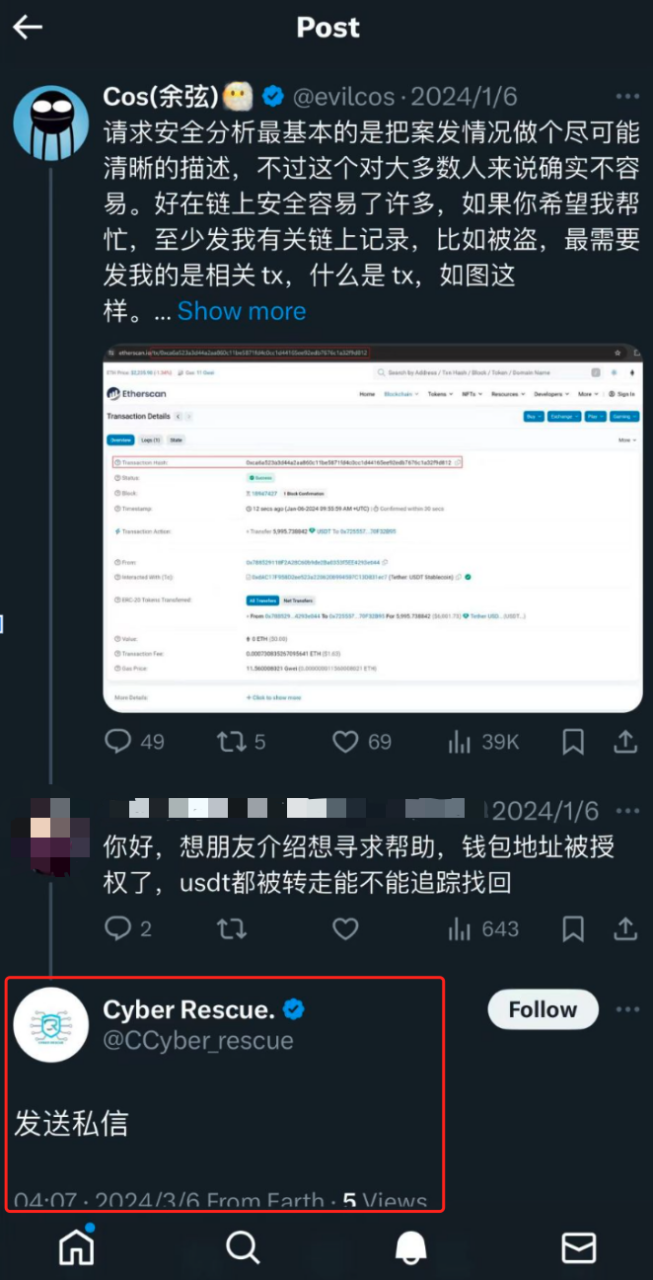
Background
Recently, a scammer (CYBER RESCUE) has been phishing victims under the guise of "helping to recover/restore stolen funds" in response to the security alert tweet from Cos, the founder of SlowMist. In response to this situation, the SlowMist security team conducted a reverse phishing operation against the scammer and exposed their fraudulent process, hoping to raise awareness among users and prevent falling victim to such scams.
Fraudulent Process
We contacted CYBER RESCUE, who claimed to be able to recover stolen funds 100% on behalf of the victim. The following is the scammer's fraudulent process:
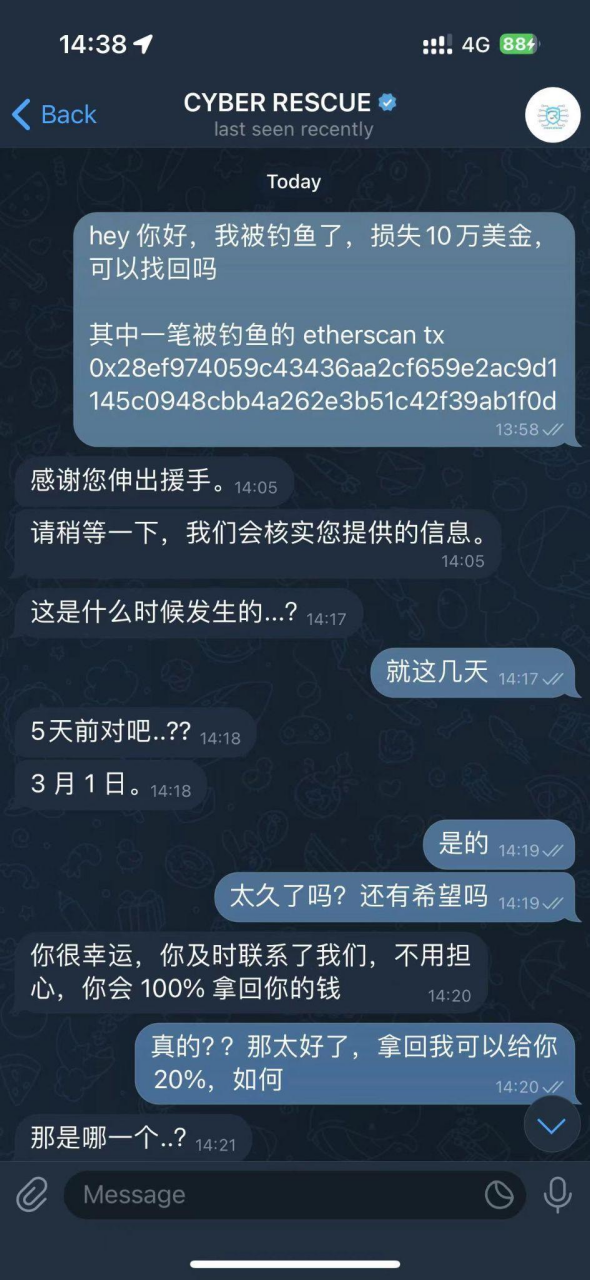
- CYBER RESCUE first inquired about the time of the theft, the wallet used, and the reason for the theft, and then claimed to be able to 100% recover the stolen funds. The method is to process the transaction through USDT on the BNB Smart Chain network and redirect the stolen funds to the victim's wallet. The victim needs to download MathWallet, and the scammer explained that this is to guide the victim in setting up the transfer and redirecting the funds to the victim's wallet.
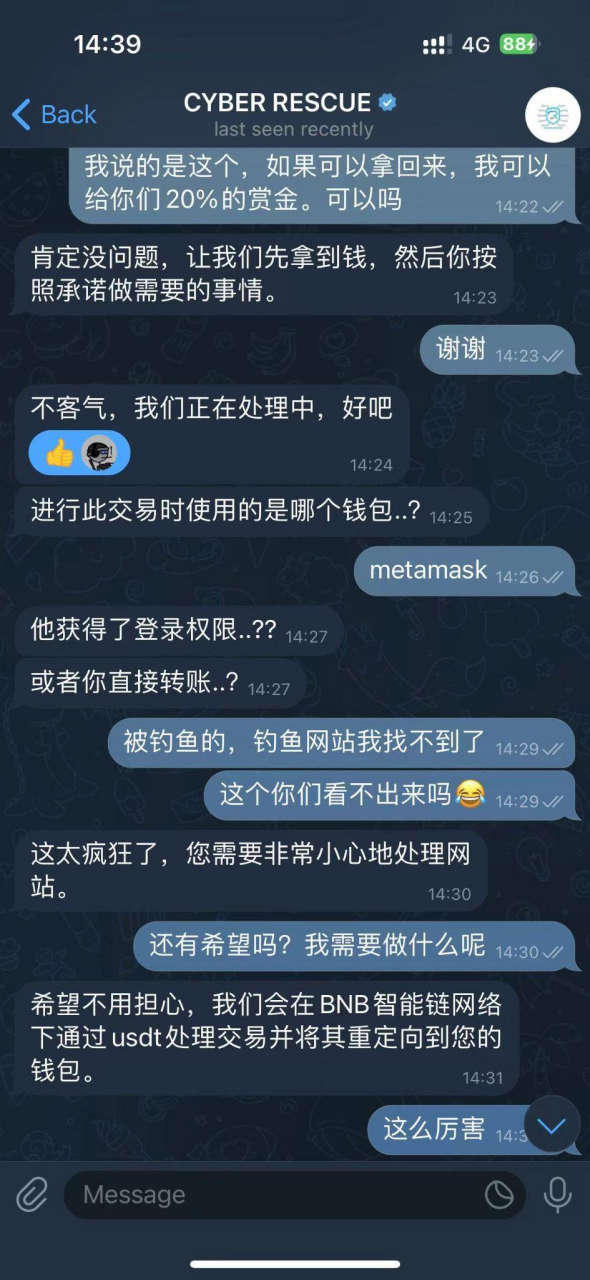
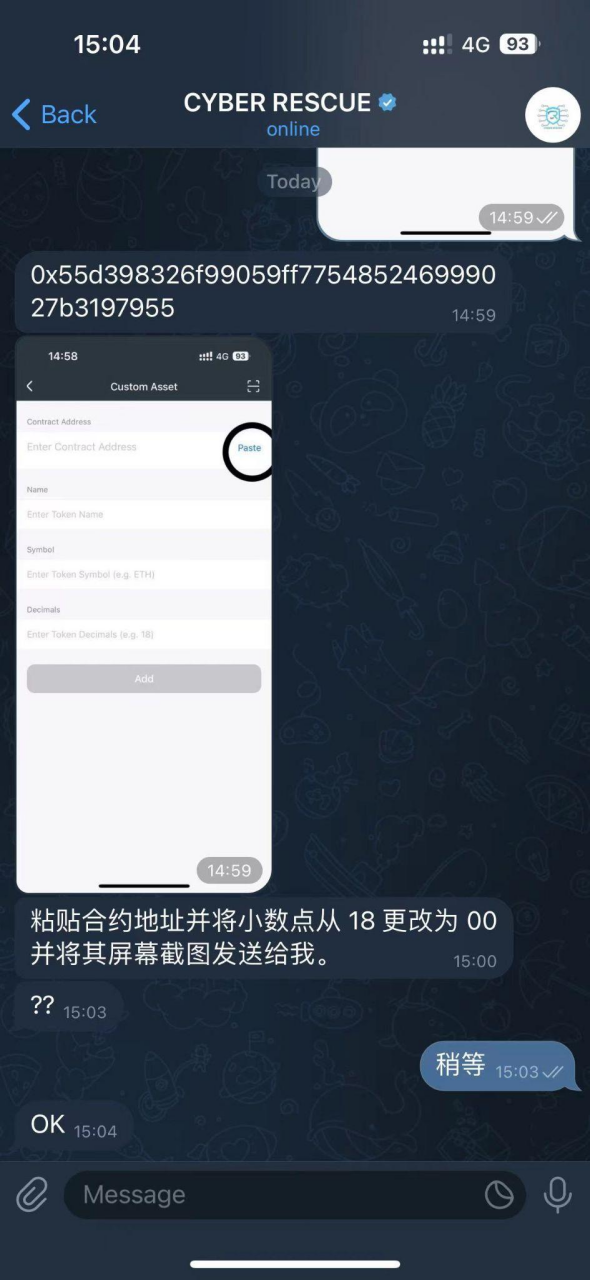
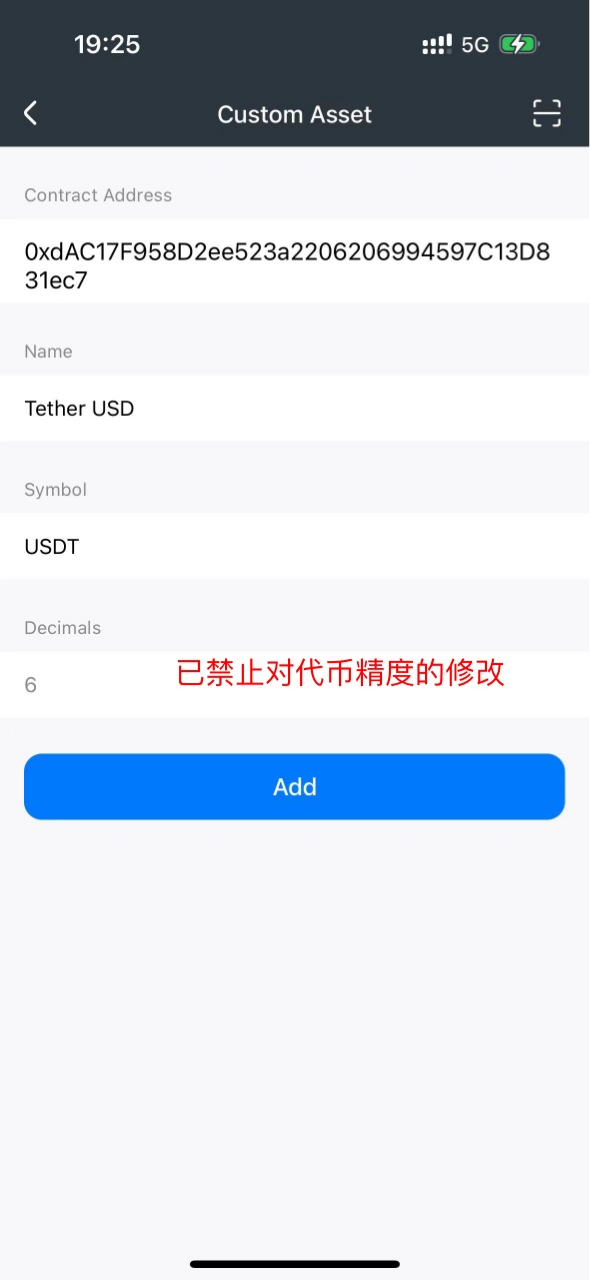
- The scammer then instructed the victim to click "Add Custom Asset" on the homepage, guiding the user to enter the USDT contract 0x55d398326f99059ff775485246999027b3197955 (this contract address is correct), at which point MathWallet will automatically recognize the token precision as 18.
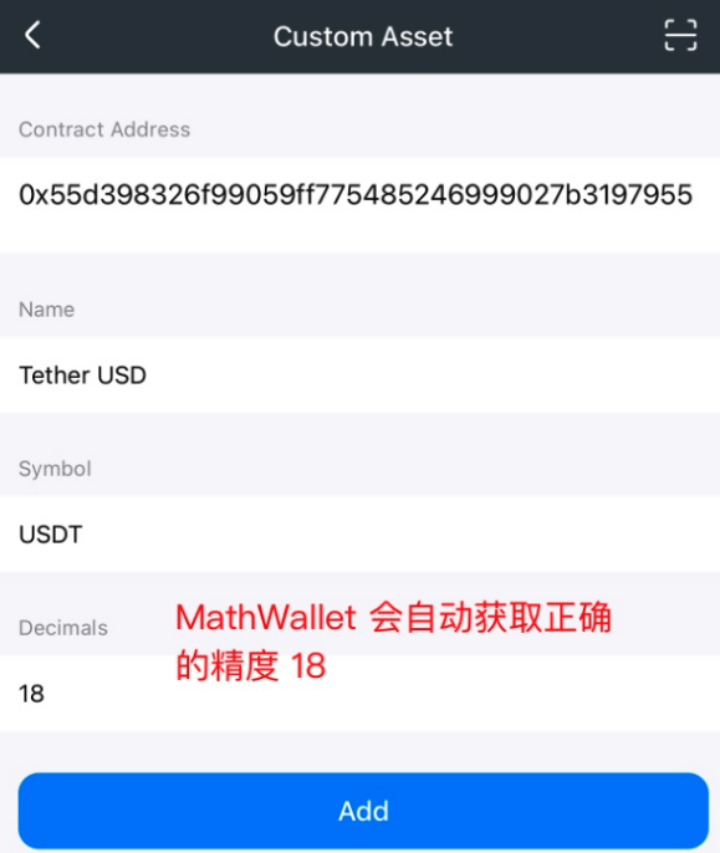
At this point, the scammer emphasized: when pasting the contract address, change the Decimals from 18 to 0. As a result, the victim added a USDT token with the correct contract but incorrect precision. Here's an explanation of what Decimals (decimal places) are: in tokens, Decimals represent the quantity of the smallest divisible unit of the token, determining the precision of the token in transactions and calculations. The higher the value of Decimals, the higher the precision of the token.
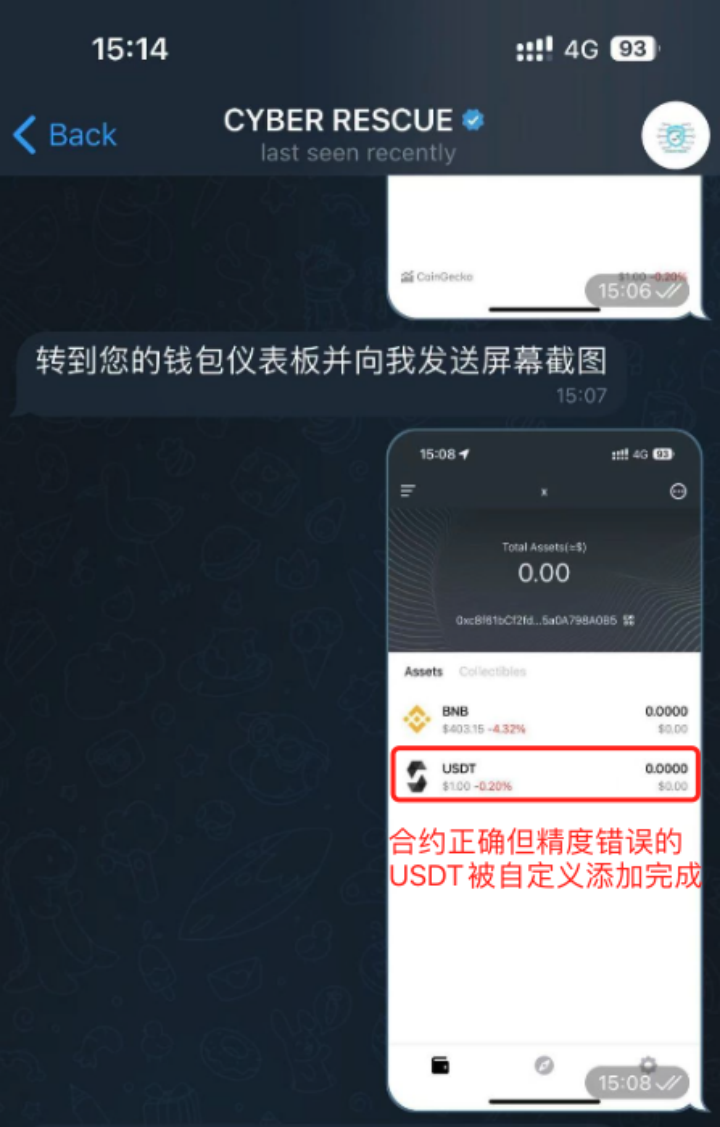
After following these steps, the scammer stated that everything was now in place, and that they needed to freeze the stolen funds and then return them to the victim's account. The victim now needed to provide a MetaMask wallet. Due to a translation error, the victim was confused by the term "元掩码钱包" (MetaMask wallet), which surprised the scammer, who asked, "You don't have a MetaMask wallet?"
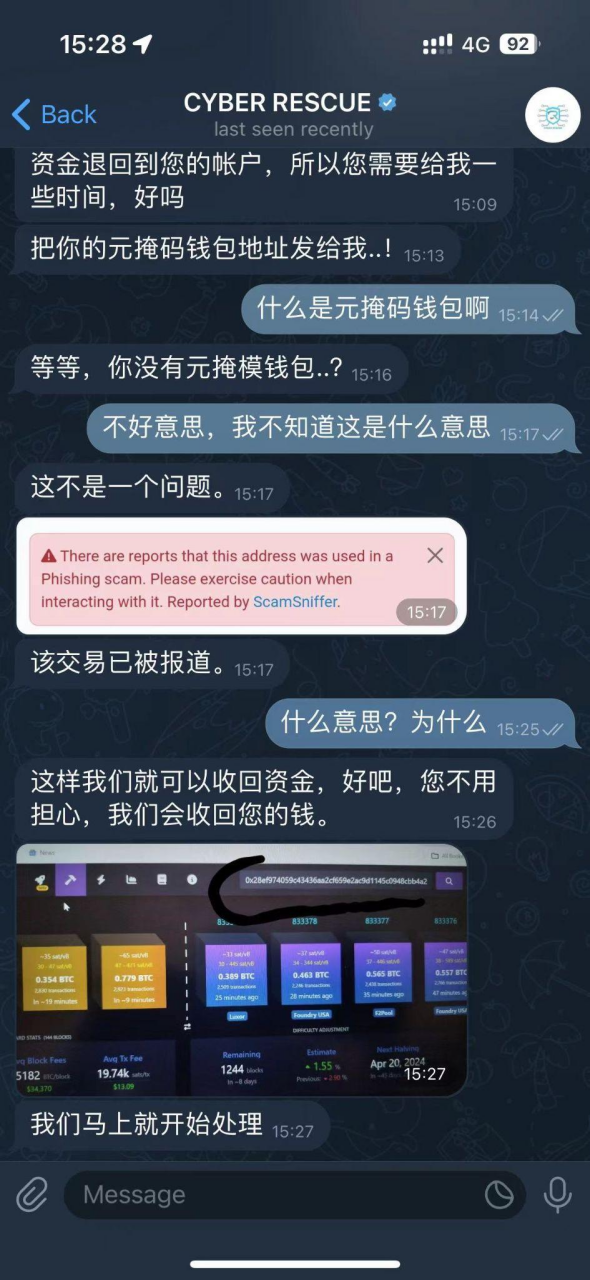
- At this point, the scammer began their "recovery" of the stolen funds:
After checking the stolen transaction provided by us, the scammer stated that they could only recover $89,589 of the stolen funds, claiming that the remaining funds had entered the foreign exchange market and been converted into local currency.
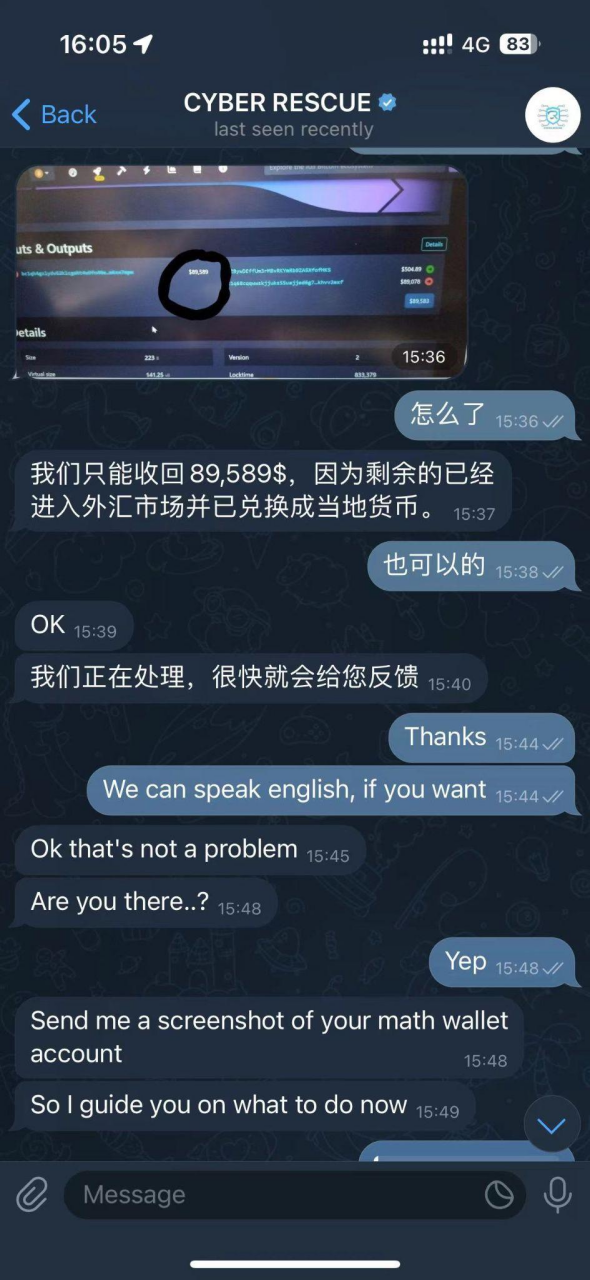
The scammer then asked the victim to send a screenshot of the MathWallet Account and reminded the victim: "Please stay online, success or failure hinges on this moment." This statement somewhat played with the victim's mindset. Having already lost money, the scammer's urgency at this point would make the victim single-mindedly focused on seizing the opportunity to recover the money, without realizing they were about to fall into another trap.
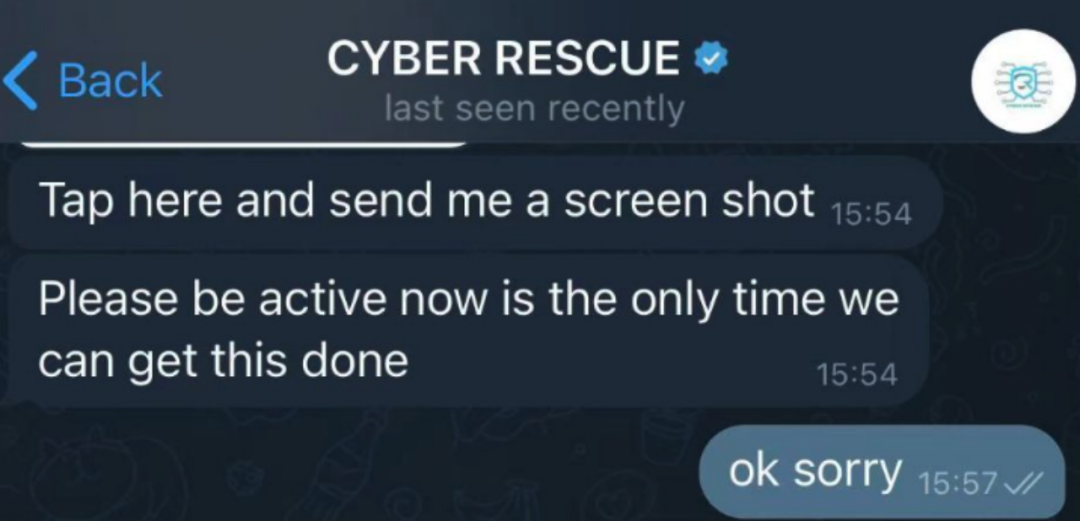
The scammer requested the victim to click "Export Private Key" in the Manage Wallet section, guiding the victim to copy the private key to them. If the victim wasn't already suspicious from the previous actions, the scammer asking for the private key should have been a red flag – run!
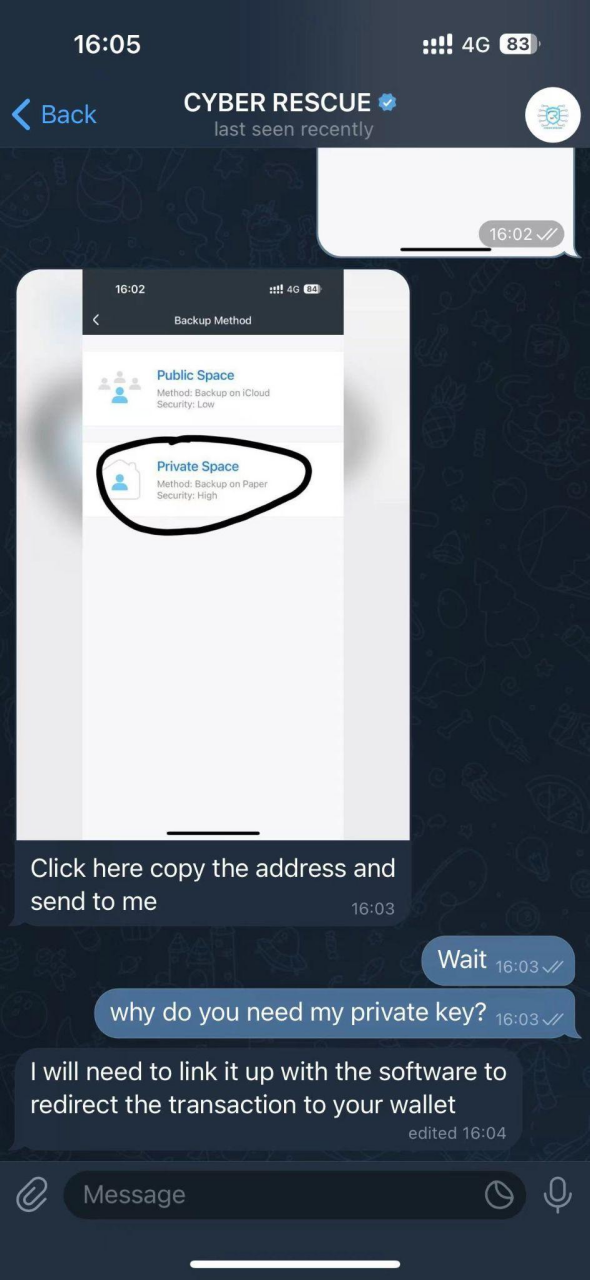
The victim sent the private key to the scammer. Soon after, the scammer claimed that the operation was successful and asked the victim to check their wallet. The victim found that the quantity of USDT had indeed changed to the 89589 that the scammer had promised to recover. How could this be?
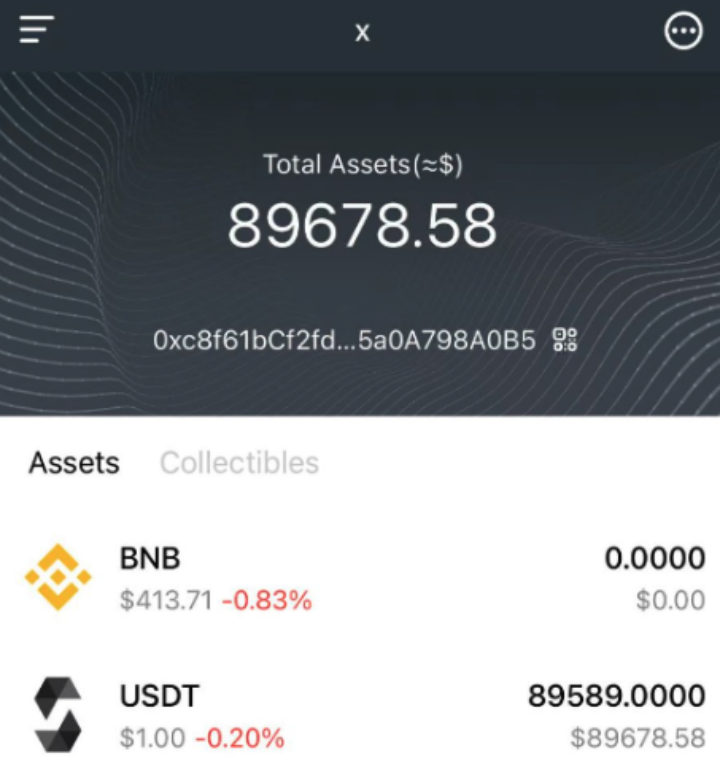
Upon checking the blockchain explorer, it was discovered that the actual amount transferred by the scammer to the victim was 0.000000000000089589 USDT. This was because, under the scammer's guidance, the victim manually changed the Decimals of the custom token in the wallet from 18 to 0. Therefore, although the scammer transferred 0.000000000000089589 USDT to the victim, the victim's wallet displayed receiving 89589 USDT.
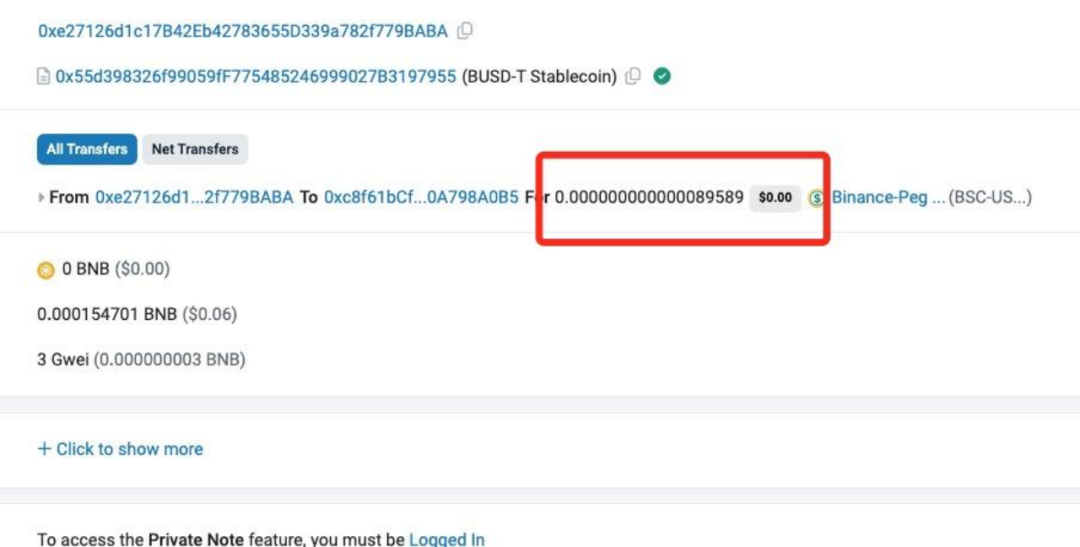
(https://bscscan.com/tx/0x00901c40073dc1ec64041a3aee689874406fdb1bf7b112a6c380ec3839d6a8e5)
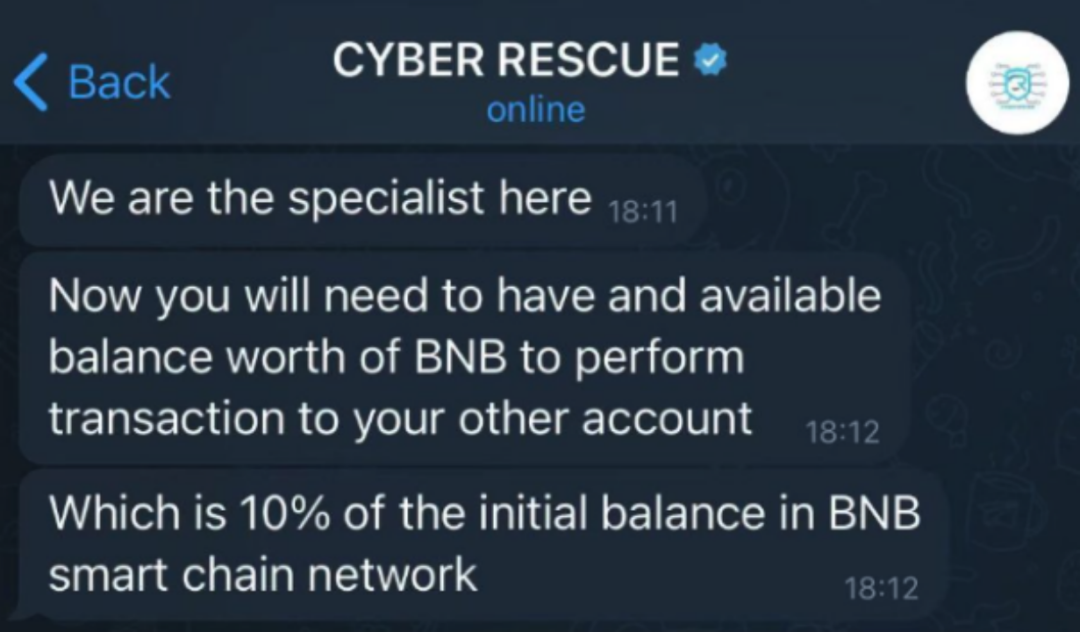
The scammer had obtained the private key, so how did they profit from this? They informed the victim that they needed to have a sufficient available balance of BNB in order to execute transactions to other accounts, which should be 10% of the initial balance in the BNB Smart Chain network. If the victim believed this and transferred approximately $8968 worth of BNB into the wallet as requested, the scammer would have stolen it.
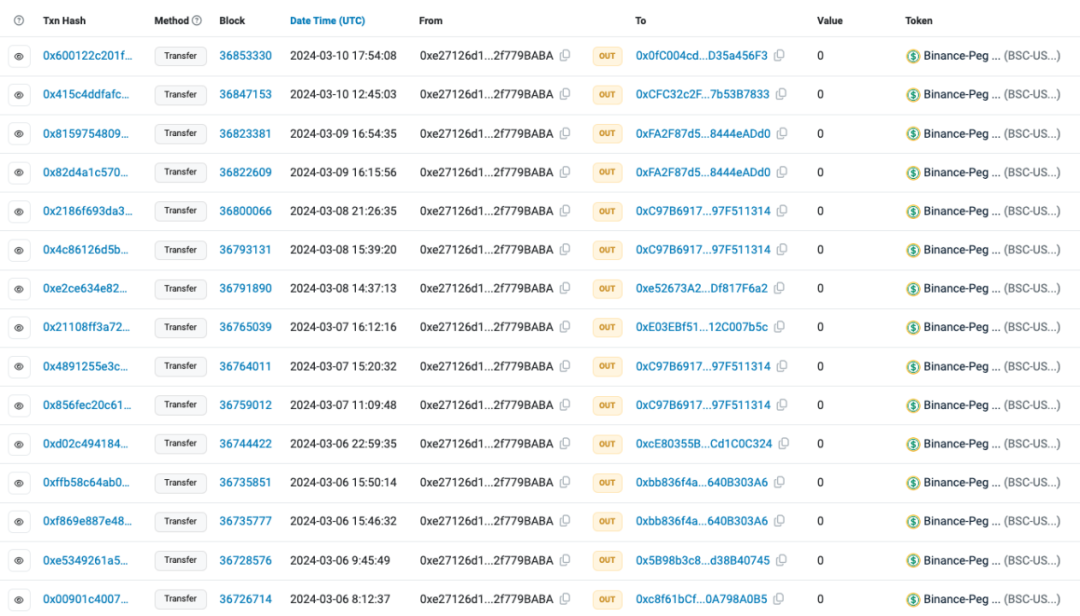
We used a blockchain explorer to view the scammer's address (0xe27126d1c17B42Eb42783655D339a782f779BABA) and found that this address frequently made small transfers to other addresses, indicating that the scammer continues to use this scam technique.
(https://bscscan.com/txs?a=0xe27126d1c17B42Eb42783655D339a782f779BABA&p=1)
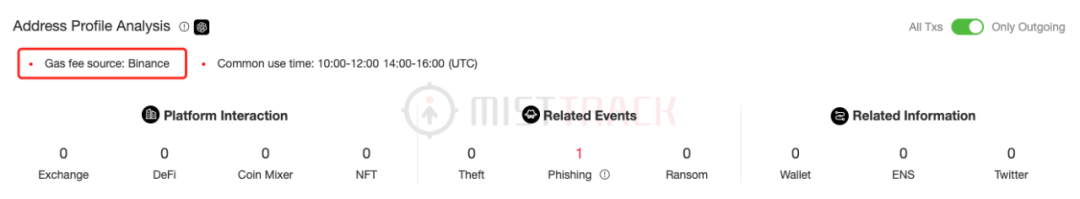
Using MistTrack (https://misttrack.io/) to query this address, it can be seen that the source of the transaction fees for this address is Binance. MistTrack has blacklisted the relevant address and will continue to monitor fund movements.
MathWallet Update
After receiving feedback on this case, MathWallet immediately fixed and released a new version, disabling the manual modification of precision by users. Users who have already installed MathWallet should upgrade in the App Store or Google Play.
Conclusion
Scams in the dark forest of blockchain are endless. The scammer in this article even impersonated an on-chain tracking expert to phish the stolen victims, practically guiding the victims on how to give away their private keys. The SlowMist security team reminds all users to remain vigilant. No matter what identity the other party claims, never give out your private keys to prevent theft. If your cryptocurrency is unfortunately stolen, we will provide free community assistance for case assessment. You only need to submit the form according to the classification guidelines (funds stolen/scammed/extorted). At the same time, the hacker addresses you submit will also be synchronized to the InMist threat intelligence cooperation network for risk control. (Note: Chinese forms can be submitted at https://aml.slowmist.com/cn/recovery-funds.html, and English forms can be submitted at https://aml.slowmist.com/recovery-funds.html)
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




