Written by: CertiK
Event Overview
MangoFarmSOL positions itself as a staking protocol on the Solana network, encouraging users to deposit SOL and receive rewards. The project had promised an airdrop on January 10th, which garnered attention from the Solana community.
However, the promised airdrop on January 10th never materialized. On January 6, 2024, MangoFarmSOL executed an exit scam, transferring 13,512 SOL (approximately $1.26 million at the time) deposited by users from the project's contract. They also deployed a malicious frontend, misleading users to authorize an "emergency migration" and stealing an additional $60,000. This is the largest exit scam we have discovered so far in 2024.
Subsequently, MangoFarmSOL closed its social accounts and website.
Similar to the previously reported xKingdom incident, this event once again highlights the inherent risks of exit scams in the DeFi space, emphasizing the importance of user vigilance and team KYC.
Scam Timeline
Step 1: Setting the Trap
① On January 3, the project used social media KOL promotion to enhance its credibility and attract more users.
② On January 5, the team announced that they would airdrop MANGO tokens on January 10, and staking SOL and referring other users would result in additional rewards.
③ From January 3 to January 7, users began depositing SOL into MangoFarmSOL's contract. Influenced by the promise of the MANGO token airdrop and online marketing, the protocol's TVL exceeded $1.3 million.
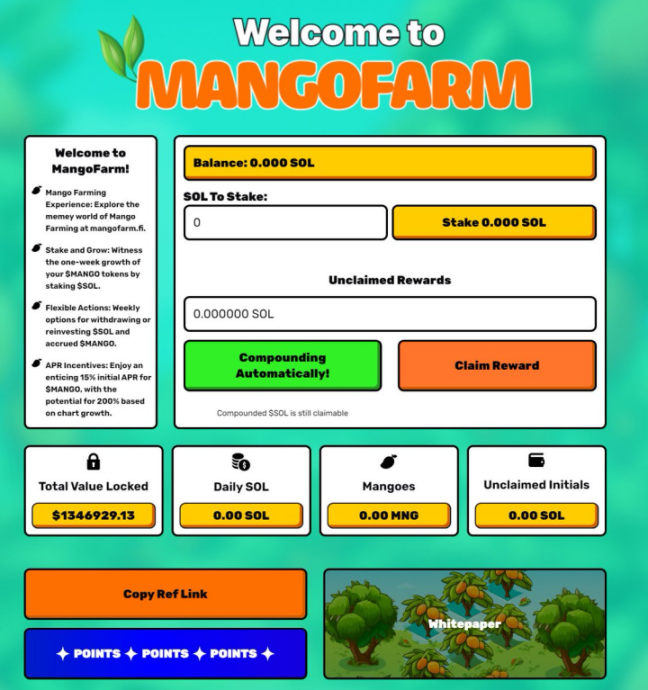
Step 2: Executing the Scam
① Stealing contract funds: The MangoFarmSOL team initiated the scam, transferring 13,514 SOL (about $1.26 million) deposited by users into the Mango contract to wallet 8ggvi.

First transaction: 135 SOL transferred from Mango contract (Bfg5SM) to wallet 8ggvi.
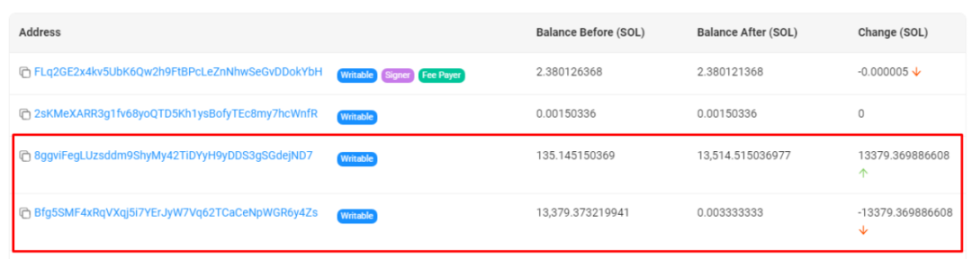
Second transaction: 13,379 SOL transferred from Mango contract (Bfg5SM) to wallet 8ggvi.
② Deploying malicious frontend for further scam: Subsequently, the team, leveraging the previous theft, deployed a frontend containing malicious code under the guise of an "emergency migration." The project's official social media accounts also promoted this malicious frontend, leading to an additional $60,000 being stolen.
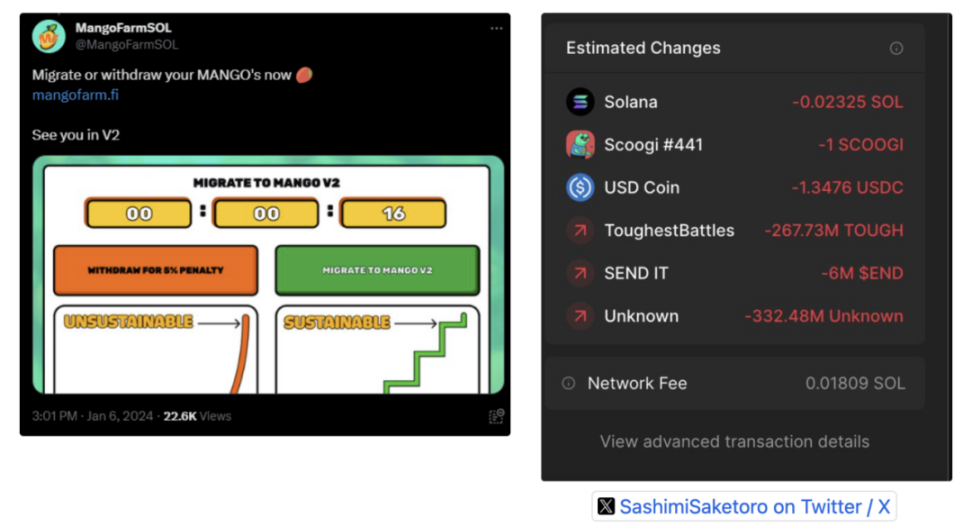
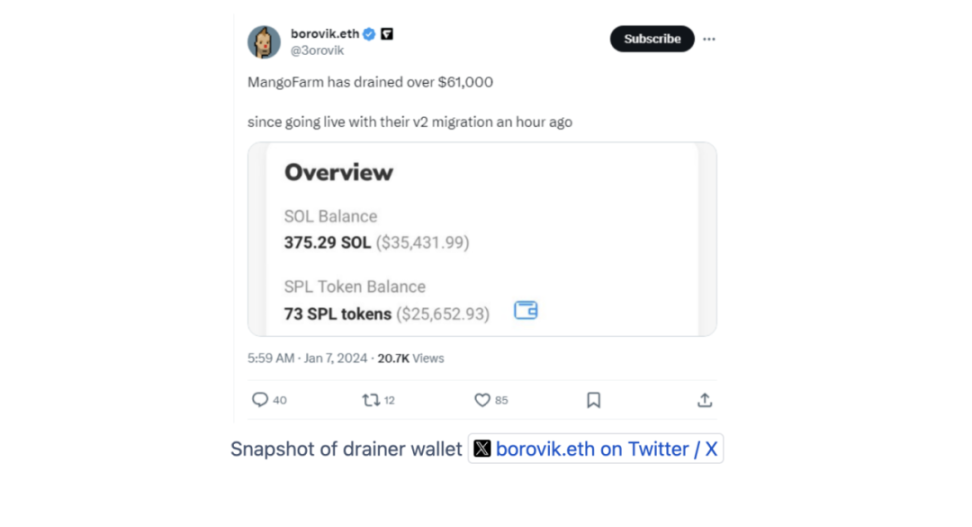 ③ Disappearing act: MangoFarmSOL then deactivated its social media accounts, closed its official website, and began transferring funds.
③ Disappearing act: MangoFarmSOL then deactivated its social media accounts, closed its official website, and began transferring funds.
Step 3: Fund Transfer
Flow of stolen funds from Mango contract
① Initial transfer: A total of 13.5K SOL, valued at approximately $1.26 million, was stolen from the Mango contract and sent to address 8ggvi…..ejND7.
② Mixing & conversion: Subsequently, 9,458 SOL was sent to 4nBETJ to obfuscate the fund's trail; all SOL in 8ggvi and 4nBE was then converted to USDC.
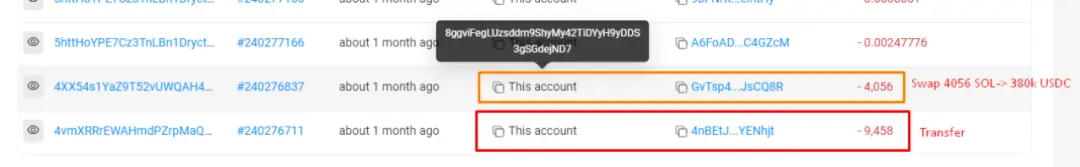
③ Cross-chain to Ethereum: These USDC were cross-chained from the Solana network to Ethereum via Wormhole, and through multiple transactions, these USDC were sent to 4 different ETH addresses.
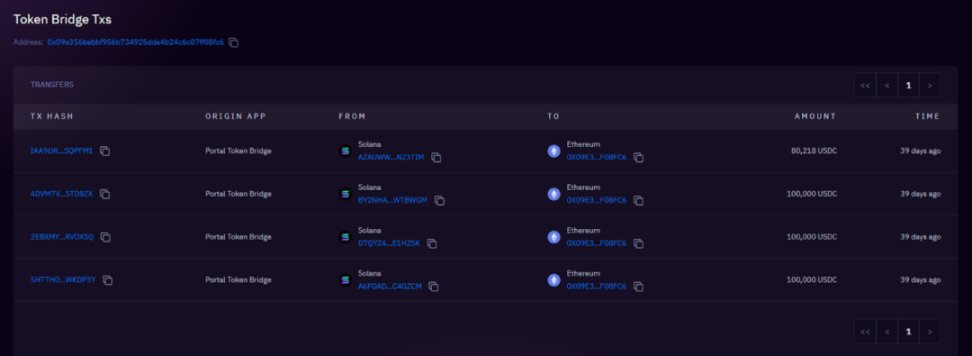 380k USDC cross-chained to 0x09e3
380k USDC cross-chained to 0x09e3
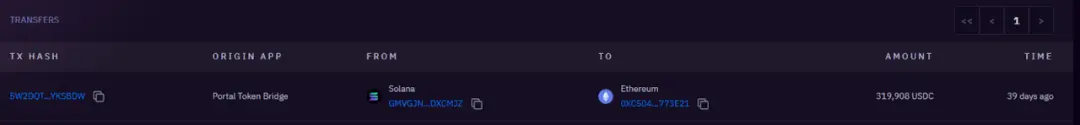 319k USDC cross-chained to 0xc504
319k USDC cross-chained to 0xc504
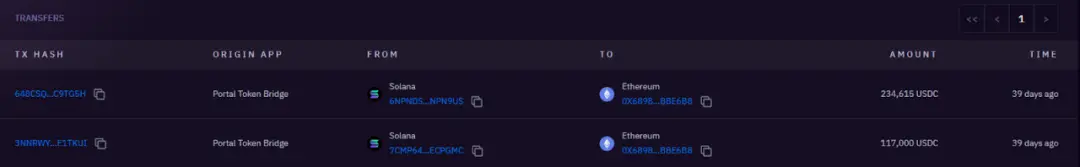 351k USDC cross-chained to 0x6898
351k USDC cross-chained to 0x6898
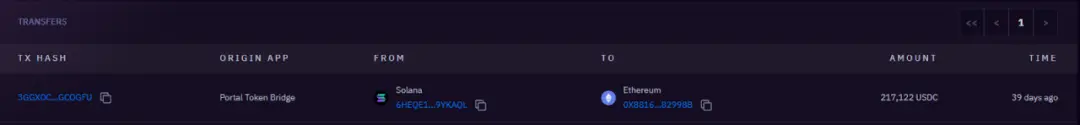 217k USDC cross-chained to 0x8816
217k USDC cross-chained to 0x8816
④ Final laundering: Upon entering the Ethereum network, USDC was exchanged for ETH. Subsequently, the stolen funds were laundered through Railgun (a privacy mixer) and exchanged through eXch (instant exchange) to further obfuscate the funds.
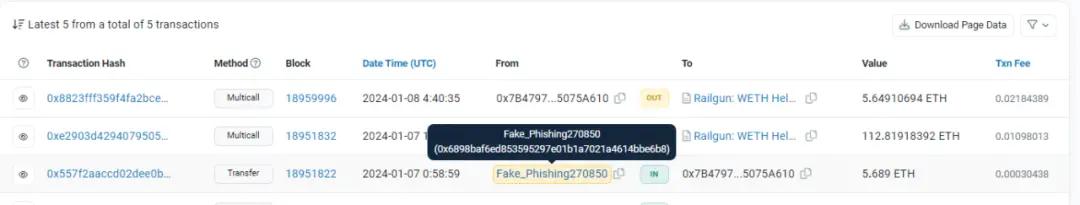 Example of transaction to Railgun
Example of transaction to Railgun
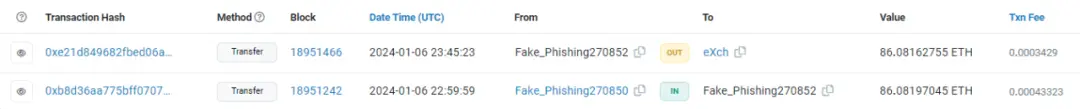
Example of transaction to eXch
Flow of stolen funds from malicious frontend
① Consolidation & conversion: User assets stolen through the malicious frontend were consolidated into SOL, then exchanged for approximately $5.86 thousand USDC.
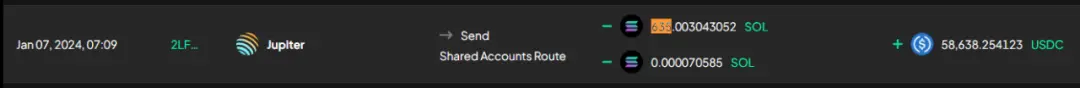
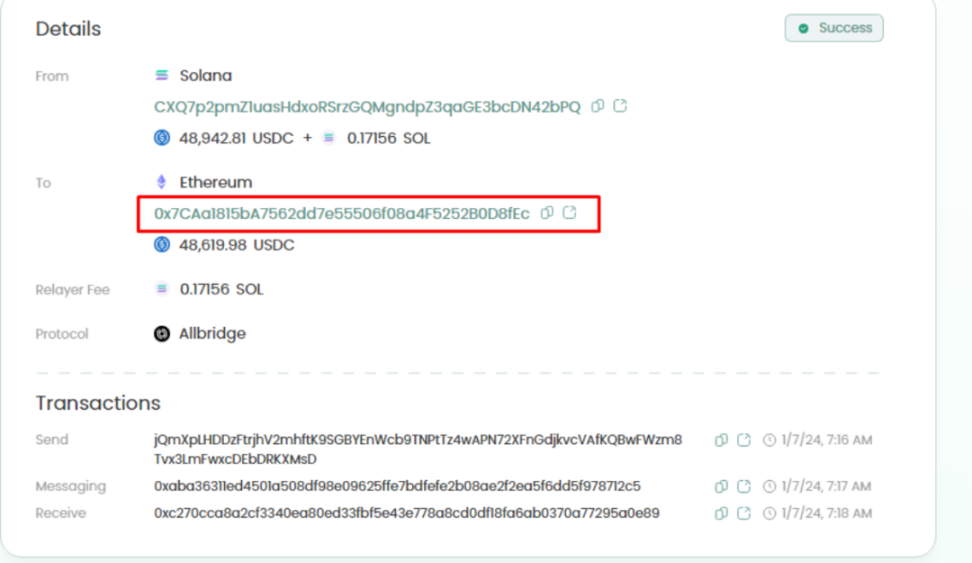
② Cross-chain to Ethereum via Allbridge: These USDC were cross-chained to the Ethereum network through Allbridge in 2 transactions to address 0x7ca…..d8fec.
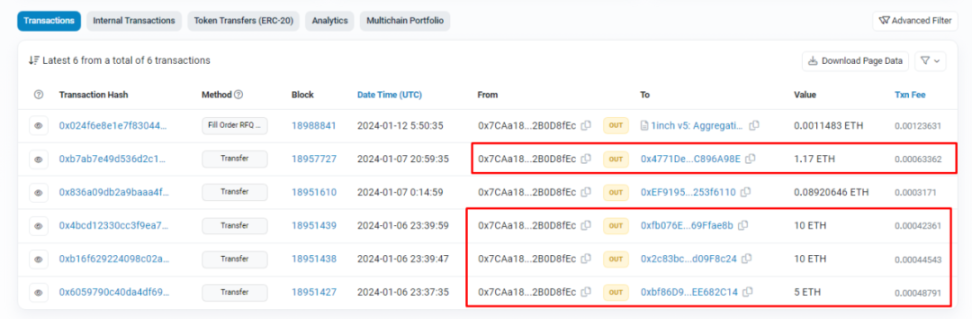
③ Final laundering: The USDC bridged to Ethereum was exchanged for 26 ETH. Subsequently, these funds were deposited multiple times into FixedFloat.
Final Distribution of Stolen Funds
The stolen funds cross-chained to the Ethereum network were primarily concentrated in three locations:
- eXch: Approximately 292 ETH
- Railgun: Approximately 263 ETH
- FixedFloat: Approximately 26 ETH
Lessons Learned
The MangoFarmSOL scam is the largest exit scam to date in 2024. The tactics of this scam bear similarities to the 2023 Harvest Keeper incident. Both projects, after the initial theft, deployed a malicious frontend to further steal user funds.
The MangoFarmSOL exit scam is estimated to have caused a loss of $1.32 million, highlighting the urgent need for decentralized project reviews.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



