We have successfully identified a large, long-standing, and still active transnational fraud syndicate.
Authors: Bitrace, ChainArgos
This paper was completed by Bitrace, a blockchain data analysis company from China, and ChainArgos, a blockchain intelligence company from Singapore. Based on the addresses disclosed in a cryptocurrency scam case judgment in the Florida state court in the United States, we conducted in-depth mining and successfully identified a large, long-standing, and still active transnational fraud syndicate. This paper aims to disclose this research result and attempts to raise awareness among industry and government departments - we need to pay more attention to anti-fraud in the cryptocurrency field.
1 Introduction
Cyber fraud is ravaging the world like a massive epidemic, causing losses of hundreds of billions of dollars in at least dozens of countries (4). A cryptocurrency scam called "pig slaughtering" is rapidly growing, which typically uses cryptocurrency to defraud victims and then launder the funds on the chain (6). In this paper, we will explore the use of cryptocurrency in the "pig slaughtering" scam based on the situations of victims in the People's Republic of China and the United States of America, and prove that seemingly unrelated cases have significant similarities.
* The "pig slaughtering" scam is a type of trust fraud and investment fraud, where victims are gradually induced to invest more and more funds in seemingly reasonable cryptocurrencies before the party they are dealing with disappears and runs away.
This paper will infer that they are likely the same syndicate by listing the cryptocurrency addresses shared by scammers from these two countries, using the same address for money laundering services, and other facts; tracking the fraudulent funds through cryptocurrency chain tracking systems based on the victim sources and scam wallet addresses mentioned in the case reports to prove their connection; and finally, by combining on-chain and literature research, identifying a series of exchanges and other service providers to demonstrate the current situation of illegal elements using cryptocurrency for cross-border crimes, and emphasizing the challenges faced by global law enforcement agencies in dealing with such scams.
1.1 Explanation of the Report and Literature
For the sake of discussion and providing valuable figures, the appendix lists detailed information of all wallet addresses. We encourage knowledgeable parties to check and replicate this work, although we understand that the vast majority of readers are not interested in these details.
This is not an attempt to confuse or make it difficult for readers to verify our conclusions in any other way. On the contrary, it ensures that all flowcharts are readable and that all long strings required to check them can be easily copied from the document. The appendix contains the data needed to verify the conclusions of this paper.
In addition, for the conclusions of this paper, we have conducted a superficial assessment of all submitted documents, giving them equal weight and considering the information they contain to be reliable. It is worth noting that this analysis is not intended to compare the legal systems or police procedures of the two countries, but to demonstrate the significant overlap and similarity between active scams in China and the United States.
2 Victims
Here, we discuss four different types of victims:
- A case in Florida: Florida Case
- A case involving victims from California and Florida: California Case
- Two cases from China: China Cases
* This case was handled by a court in Florida for jurisdictional reasons, even though victims in California lost more money. The name was chosen to reduce confusion.
The case in Florida is much larger than the other cases, with one victim being defrauded of over $2 million. In this case, the criminals used various money laundering techniques to launder the funds involved. The other cases have smaller case values and fewer funds laundering methods used.
2.1 Florida Case Victims
In the Florida case, the victims fell into a more common "pig slaughtering" scam, as described in court documents:
On April 15, 2022, Plaintiff and Defendant communicated through Facebook, an online social media and social networking service. Id. ¶ 10. Defendant represented that she was successfully engaged in investing in cryptocurrency and that her aunt was a prosperous cryptocurrency trading expert who managed an analyst group at Grayscale Investments, a legitimate third-party digital currency asset management company. Id. ¶¶ 11, 12. Defendant represented that, if Plaintiff were to join a margin trading platform called foundrypro.net (“Foundrypro”), Defendant would use sophisticated algorithms designed and implemented by Defendant’s aunt to execute cryptocurrency trades in order to earn Plaintiff a profit. Id. ¶ 13. Neither Defendant nor Defendant’s aunt had a relationship with Grayscale Investments. Id. ¶ 15.
Based on these representations, Plaintiff joined Foundrypro on May 17, 2022 and began executing margin trades on that platform on Defendant’s advice. Id. ¶ 17, 19. Over the course of Plaintiff and Defendant’s relationship, Plaintiff invested 2,215,118 units of “Tether” (USDT), a form of cryptocurrency known as stablecoin that is pegged to the value of the U.S. Dollar. Id. ¶¶ 23, 24. From April 15, 2022 through the end of October, 2022, Defendant communicated with Plaintiff via SMS, WhatsApp, telephone calls, and email. Id. ¶ 16. Foundrypro featured a dashboard that displayed illusory investment gains which, together with Defendant’s representations, encouraged Plaintiff to continue “investing” in Foundrypro. (1)
After a series of legal proceedings, the victim obtained a default judgment.
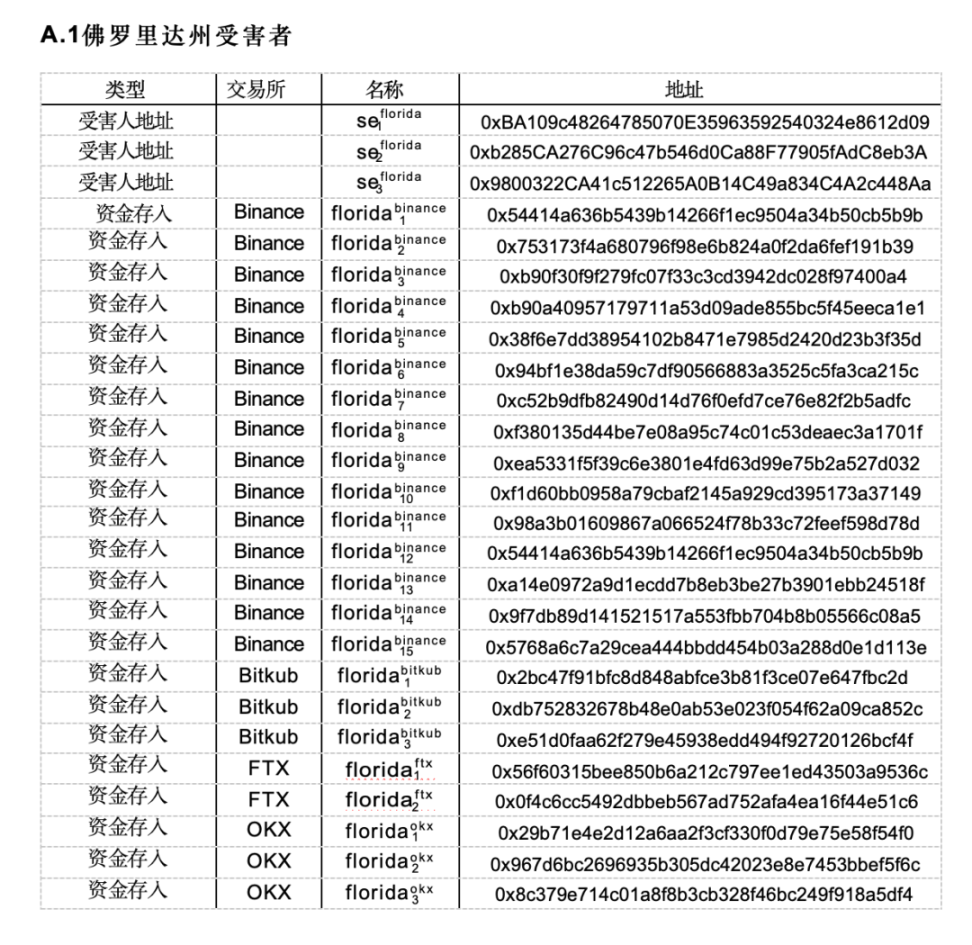
The case documents provide two types of cryptocurrency addresses. Firstly, the documents list the addresses to which the victims initially transferred funds, which we refer to as victim addresses. Secondly, the documents provide a list of cryptocurrency exchange deposit addresses to which the victims' funds were sent. See Appendix A.1.
* Cryptocurrency exchanges provide "deposit addresses" to simplify the process for customers to deposit funds. When customers intend to deposit funds, the exchange creates a dedicated address for them to send funds. In this way, the exchange can automatically allocate all transfers to that address to the specific customer account. Consider the "deposit address" as a tool to ensure that funds are sent to the correct internal account by using different external accounts.
2.2 California Victims
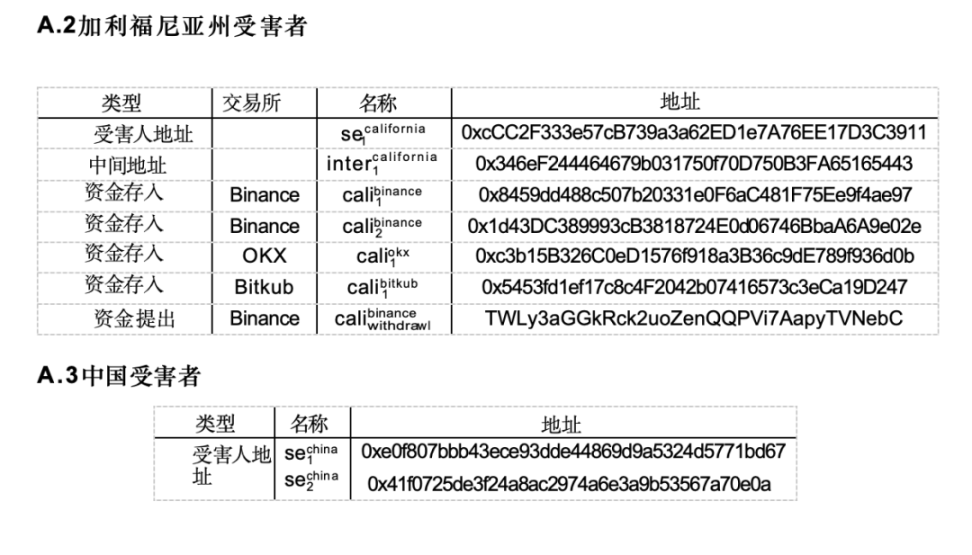
In the case in California, two different individuals became victims of the "pig slaughtering" scam, sending cryptocurrency to the same scam wallet provided in Appendix A.2.
The first scam involved approximately $177,502.29, as described in court documents:
[Victim] met an individual known to him as “Bunny” through social media (Facebook) and started a romantic relationship with her. During the relationship, Bunny offered [Victim] a way to make money through cryptocurrency so they could afford to buy a farm and live together one day.
During the relationship, Bunny convinced [Victim] to invest in cryptocurrency through “Pearcoin,” a fake cryptocurrency trading application, unknown to [Victim] at the time.
Ultimately, [Victim] attempted to withdrawal his funds from Pearcoin and was told he must pay the taxes up front or he would risk a 3 per cent penalty fee for each day he did not pay. At this point, [Victim] realized he was involved in a scam and subsequently contacted the Brevard County Sheriff’s Office to report the incident. [Victim] was unable to transfer, withdraw, or access any of his funds through the investment platform. (3)
The second scam was similar, involving approximately $300,000:
The victim … reported she had been romantically involved with an individual through social media. During the relationship, she was convinced to invest in cryptocurrency. (3)
2.3 Chinese Victims
Bitrace provided information and data on the Chinese cases. A victim from Tianjin reported being induced to establish an account on the cryptocurrency exchange OKX and withdraw USDT to the trading applications WBF and Pionex. After several smaller investments, the Tianjin victim received a return of $4,860, then made more investments and ultimately lost approximately $40,000. There were no reports of emotional fraud in this scam, resembling the "pig slaughtering" scam in the Florida case. The source of funds for the Tianjin victim is se.china in Appendix A.3, which is a wallet associated with a known scam, as we will detail later.
Another victim active in the OTC market reported a phishing scam involving se.china. A phishing scam involves convincing victims to download malicious "Trojan horse" software that empties their wallets and sends the funds to the scammers (7;5;9). Although two cryptocurrency acceptance merchant customers encountered this scam in cases reported to Bitrace, this scam appears to be associated with a smaller syndicate than the one involving the Tianjin victim.
China does not have court documents like the United States, but we can extract local reports on similar cases to further emphasize these scams. Local authorities in Ningbo (2) and Wenzhou (8) reported similar fraudulent cases. For example, a press release from law enforcement in Wenzhou described a scam involving "Trojan horse" software, similar to a scam reported by one of Bitrace's clients:
Upon investigation, since February 2022, the gang has posted advertisements for discounted fuel cards on multiple overseas social software, using the pretext of testing the authenticity of virtual currency wallets and virtual currency, luring victims to click on the Trojan program link, and secretly controlling their wallets. When the time is right, they illegally obtain virtual currency from the wallets, committing more than 30 cases in just over a month, involving more than 1 million yuan. (8)
This sounds both similar to scams reported around the world and similar to the coin theft scams reported by Chinese victims active in the OTC market.
In the Chinese cases, due to differences in the legal systems of the two countries, it is not possible to provide documents similar to those in the Florida and California cases for comparative analysis, but this does not diminish the similarity in the way the two countries operate. As we have seen, all the funds involved in the analysis were laundered through wallets and intersected with addresses of service providers, demonstrating a connection between the two cases and indicating that the fraudsters in both cases belong to the same criminal entity.
3 Service Providers
The court documents for the Florida victims mention four cryptocurrency exchanges: Binance, Bitkub, FTX, and OKX, all of which are well-known large service providers. Binance has long been the world's largest cryptocurrency exchange, FTX was founded by Sam Bankman Fried and is currently awaiting the outcome of a highly publicized fraud trial. OKX is a large cryptocurrency exchange, and although not as well-known as Binance and FTX, it sponsors several high-profile sports teams and events worldwide. Bitkub is the smallest of the four listed companies and is the largest cryptocurrency exchange in Thailand, also engaging in high-profile sponsorships in its market.
Further analysis reveals that Coinbase, Huobi, Maicoin, Maskex, Paribu, and Peatio are similar well-known exchanges. Coinbase is listed on Nasdaq, with annual revenue in the billions of dollars and a current market value in the hundreds of billions of dollars. Huobi is a large exchange with several subsidiaries listed on the Hong Kong Stock Exchange, and like many other Asian exchanges, it sponsors sports projects including the Spanish national men's football team. Maicoin describes itself as Taiwan's leading cryptocurrency exchange. Maskex is a cryptocurrency exchange based in the UAE and holds a VASP license. Paribu is a Turkish exchange with partnerships with several Turkish football clubs. Peatio is a Chinese cryptocurrency exchange that closed a few years ago and opened its trading software, and although the exchange may have closed, its wallet addresses are still active.
Here, we only want to establish that these service providers are large, well-known, and visible entities, and do not need to further analyze their existence or involvement in cryptocurrency trading or provide any form of written evidence.
Further discussion will involve the smaller parties operating between the entry points of the scams and the exchanges. While these may not be as prominent in the news and sports world, it is clear that the exchanges are involved in managing the proceeds of the scams.
4 Downstream Fund Tracking
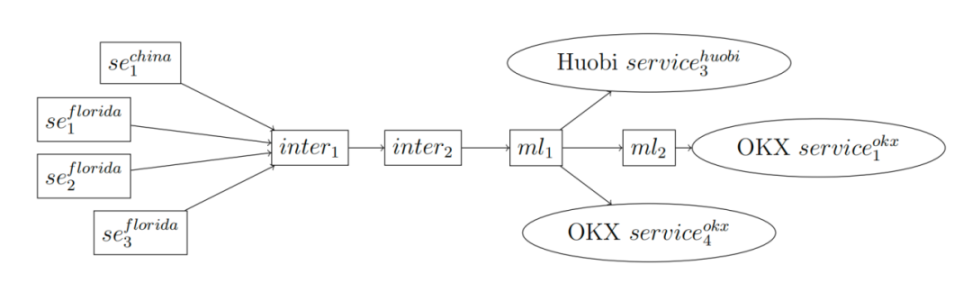
This section analyzes the downstream addresses of the Chinese and Florida cases, revealing the final destination of the fraudulently obtained funds. In Figure 1, we plot the movements from three addresses in Florida and one address in China through the same intermediary address to two wallets we label as ml1 and ml2. "ml" represents "money launderers," who profit from a series of scams and deposit the money into exchanges, acting as fund collection addresses.
It is important to note that fraudulent proceeds do not transfer in a point-to-point single-line sequence through the laundering addresses, and not every unit of fraudulent proceeds passes through this exact wallet sequence simultaneously. Instead, we only establish that these types of fraud events and their subsequent money laundering activities occur in a similar manner and at similar times. Therefore, these syndicates are likely part of the same overall group. This is particularly convincing as these funds ultimately flow to the same group of money laundering addresses leading to the exits.
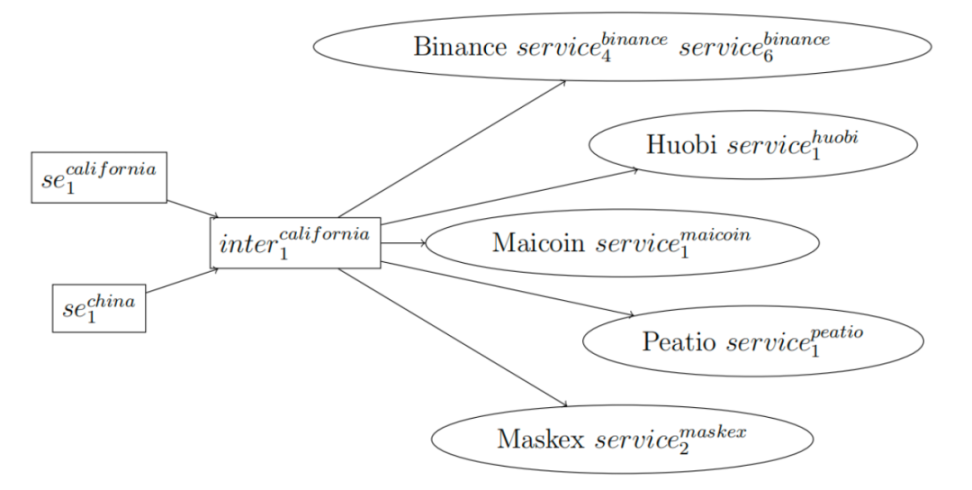
Now let's connect the cases from China and California. In Figure 2, we see the overlap of funds flowing from different addresses in both cases - the same wallet appears in the downstream of two different cases.
It is also worth noting that the intermediary address inter.california is related to many deposit addresses given in the civil forfeiture order (3) of the California case. Additionally, one of the Binance deposit addresses in Figure 4 was disclosed by Reuters reporters several months ago and caught the attention of ChainArgos, as it is related to many scams related to (6).
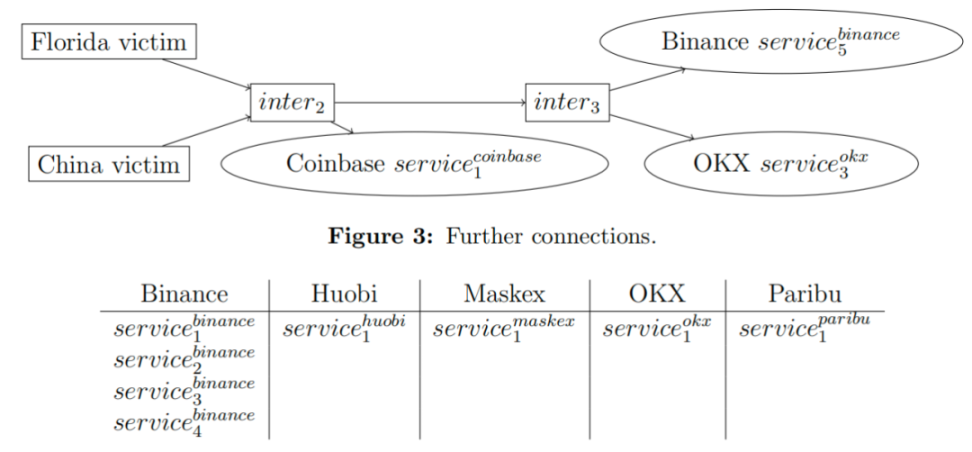
Next, we will show the connection between the intermediary addresses and the exchanges in Figure 3. The scam entry address in the Chinese case also has a direct connection to the exchange deposit addresses in Figure 4.
A similar structure can also be seen downstream at se2.china, where the funds are deposited into service5.okx after passing through two intermediary wallets.
While this is not a complete display of all addresses, it still indicates the interconnectedness of these scams and their involvement with many exchanges.
5 Total Amount
So far, this article has revealed individual scams, tracked their common sources of funds, and determined that these scams are part of a larger fraudulent organization. Currently, there is not enough information to support recording all the scams carried out by this group or related groups. Given the nature of the crimes and the victims, it is difficult for us to have a reliable and comprehensive list. Therefore, the next logical step is to look at the total amount of funds in the addresses of service providers used in these cases to determine the potential scale of this organization. The analysis of the scale of funds raises three independent but related questions:
- How much money flowed into the disclosed "fraud entry" addresses?
- How much money was transferred through the service providers?
- How much money flowed to fund exits such as exchanges?
5.1 Scale of Scams
We found that from the beginning of 2021 to the time of writing, a total of $20.7 million flowed through the addresses related to the Chinese Tianjin victim case. Since the victim lost about $40,000, we only focus on a small part of the activities of this group, and it is certain that there is more fraudulent funds concentrated in these addresses.
In the Florida case, the victims claimed to have lost about $2.2 million, but the total inflow of these three addresses is slightly less than $6.5 million, confirming that there are definitely more victims. In the six "fraud entry" addresses used to map this traffic, we found the total inflow to be:
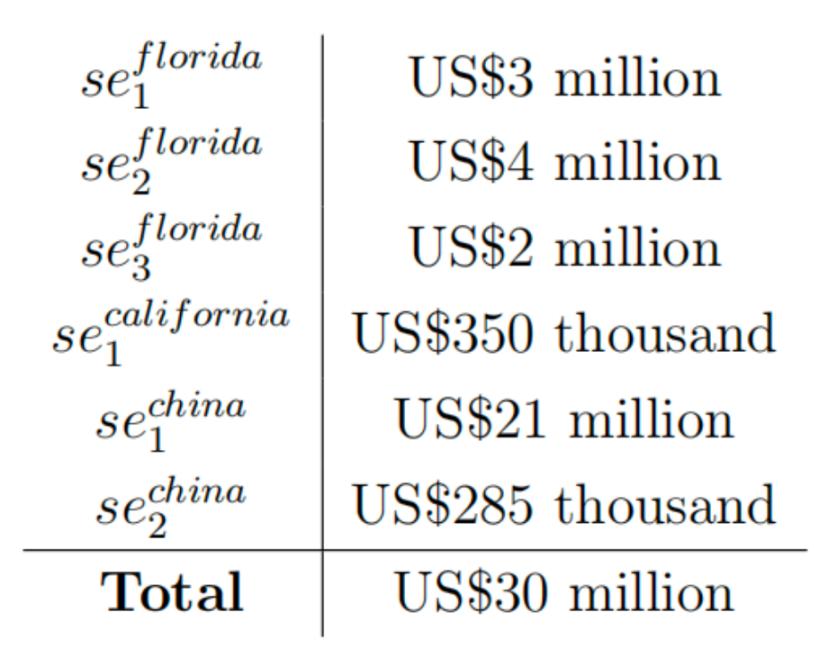
Of note, the most unique aspect is that most of the fraudulent funds flowing into se1.california are denominated in Ether, not the stablecoin USDT, with a total of 156.04 Ether received by se1.california. We have monetized Ether at a price of $2000, reflecting the average conversion price at the time of transfer.
5.2 Scale of Service Providers
Next, let's take a look at the total amount of flow through some intermediary addresses. For the six intermediaries mentioned in the examples above, we found the inflow of USDC and USDT to be:
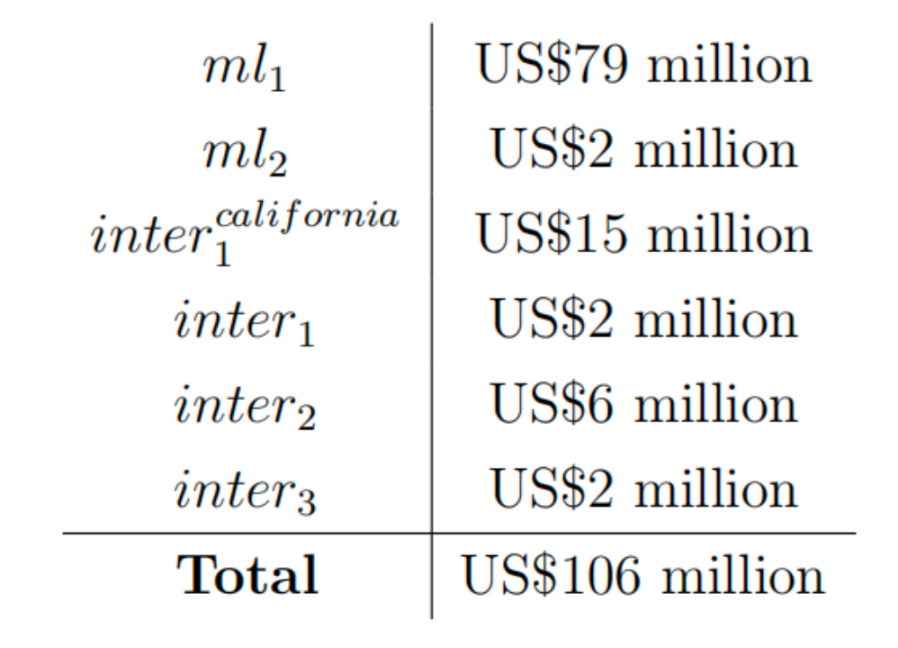
Some of the same tokens flow through multiple addresses, and the examples even show the flow from ml1 to ml2. Based on reasonable estimates of the flow, the processing amount of these intermediaries is between $80 million and $100 million.
So far, the largest amount of funds has flowed to exchanges. By examining the deposits at the exchanges' addresses specified in (1), we found the following totals:
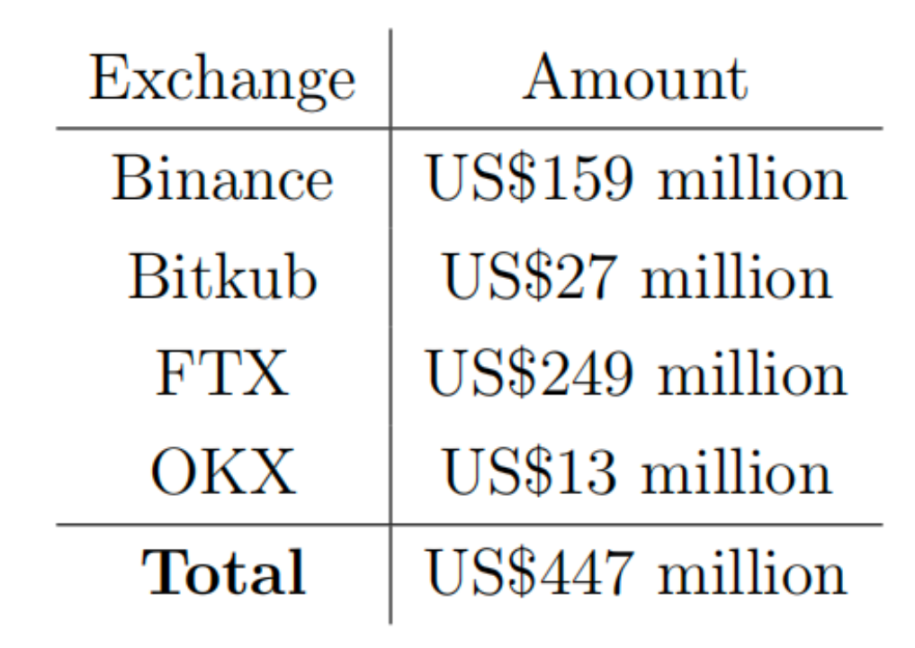
If we add the addresses connected through other cases, we get:
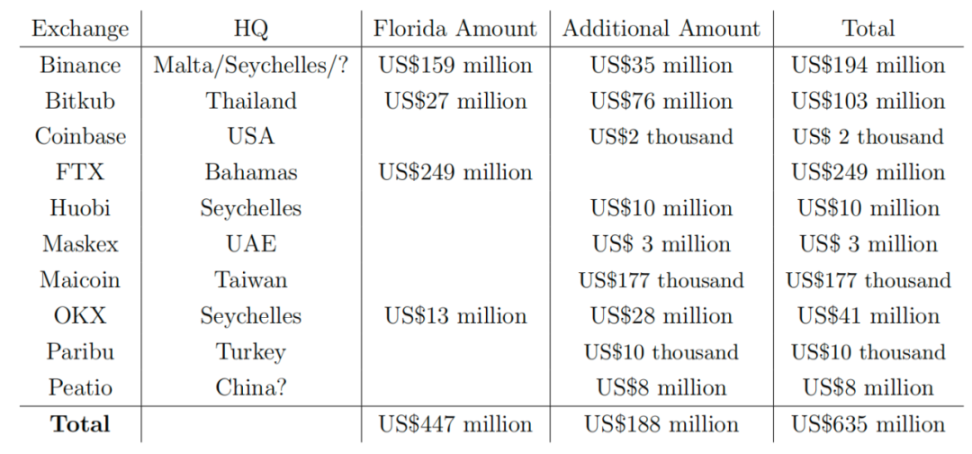
While this does not imply that this criminal organization is responsible for all of these assets, it provides strong evidence that there is still a significant amount of criminal flow of funds in the region waiting to be discovered.
Please note that these data include several smaller volume transactions. These are included for the completeness of the data and are not exhaustive. Even within the larger volume exchanges, we find individual deposit addresses at different orders of magnitude in the total flow.
Also note that almost all of the trading volume occurs on exchanges outside of China and the United States, with the vast majority being handled by companies headquartered in overseas jurisdictions.
5.3 Exchange Withdrawals
In the California case, the investigation also uncovered a withdrawal address on the Tron blockchain controlled by the fraud syndicate, with funds of approximately $1.1 million flowing through this TRX address, far exceeding the approximately $500,000 lost in the California case, indicating that further investigation into Tron and other blockchains may reveal more related clues.
6 Discussion
The analysis has demonstrated three key facts:
- Similar scams occurring simultaneously have victims in both China and the United States;
- Funds extracted from two jurisdictions flow through common intermediary addresses;
- The amounts involved range from tens of millions to billions of dollars.
It is important to understand the following limitations in the analysis:
- We are not claiming that the $30 million flowing into these "scam addresses" wallets are all proceeds from fraudulent activities, it is just what is currently traceable;
- Although $635 million in foreign exchange deposits has been discovered, we are not claiming that all of this can be attributed to scams;
- Considering the cyclical nature of trading, the above figures may not be entirely free of double counting.
* For example, some funds deposited at one exchange may be withdrawn and redeposited elsewhere.
Instead, the analysis should be understood in the context of the scope and scale of the scams being perpetrated. First, only four cases have been analyzed, where victims have come forward and initiated some form of formal legal proceedings. Second, we have demonstrated that these scams are related to those discussed in (6), indicating that the scale and scope of such scams may be more far-reaching and widespread than previously understood.
It appears that there are more clues to be discovered in the flow of funds, and the proceeds obtained through cryptocurrency ecosystems for fraudulent activities may be much larger than our current estimates. Additionally, it is worth noting that while the victims of these cases are in the world's two largest economies, only a small fraction of the exchanges handling these fraudulent proceeds are located in these countries. Addressing these issues will require extensive international cooperation.
References
[1] Bowen v. Xingzhao Li, 23-cv-20399-BLOOM/Otazo-Reyes (S.D. Fla. Jul. 26, 2023). [2] China Ningbo Net. A large amount of virtual currency was stolen from a ningbo citizen by a hacker., 7 2022.
[3] Florida Circuit Court. Eighteenth Judicial Circuit In And For Brevard County, Florida Case No: 05-2002-CA- Filing 162250539 Civil Forfeiture.
[4] Global Anti-Scam Alliance. The global state of scams - 2022 report, 2022.
[5] Ledger. Security incident report, 12 2023.
[6] P. McPherson and T. Wilson. Crypto scam: Inside the billion-dollar ‘‘pig-butchering‘‘ industry. 11 2023.
[7] ScamSniffer. From google to x ads: Tracing the crypto wallet drainer‘s $58 million trail, 12 2023.
[8] Wenzhou Public Security Bureau. 743 cases were solved and 2,093 people were arrested! the results of the wenzhou clean network 2022 operation are announced!, 11 2022.
[9] ZachXBT. Monkey drainer twitter thread, 10 2022.
Appendix: Addresses
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。