This article aims to evaluate and analyze the basic security risks of DeFi projects on the DefiLlama leaderboard.
Authors: Shange, Mr.A, SlowMist Security Team
Background
In recent years, DeFi projects have grown rapidly, leading a revolution in financial innovation. DeFi projects use blockchain technology to provide decentralized financial services such as lending, trading, asset management, etc., allowing users to interact directly without traditional financial intermediaries.
However, due to the significant funds and user base of DeFi projects, they have become potential targets for hackers. Many project teams believe that DeFi security is only about contract security, which is a misconception because DeFi also includes domain names, servers, and other information.
As a result, various phishing and scam groups have emerged, notably using social engineering attacks like Angel Drainer. This year, this phishing group has attacked DeFi projects such as Balancer, Galxe, Frax Finance, VelodromeFi, and Aerodrome.Finance by hijacking the project's DNS to inject malicious JavaScript code on the front end, tricking users into signing, and ultimately stealing assets.
In this context, this article aims to evaluate and analyze the basic security risks of DeFi projects on the DefiLlama leaderboard. DefiLlama, as a platform providing data and rankings of DeFi projects, represents the most widely used and widely used DeFi services in the market.
Test projects and methods
First, we divided the projects into different ranges based on DefiLlama's ranking, including the top 50, top 100, top 200, top 500, and top 3000, to conduct statistics. We mainly collected and analyzed the DNSSEC-related information of each project's corresponding domain name, domain whois information, CDN information, and source IP exposure.
DNSSEC Security Issues
DNSSEC (Domain Name System Security Extensions) is a technology extension used to enhance the security of the Domain Name System (DNS). Its main function is to provide a mechanism to ensure the integrity, authenticity, and authentication of DNS queries. The following are the main functions of DNSSEC:
1. Data integrity: DNSSEC signs DNS data using digital signature technology to ensure that the data is not tampered with during transmission. This can prevent malicious attackers from tampering with DNS responses, redirecting users to malicious websites, or hijacking network traffic.
2. Data authenticity and authentication: DNSSEC can verify the authenticity of DNS responses, ensuring that the data comes from authoritative DNS servers, not malicious DNS servers. This helps prevent DNS fraud attacks, where attackers attempt to forge DNS responses to deceive users.
3. Defending against cache poisoning attacks: DNSSEC can prevent cache poisoning attacks, which prevent attackers from inserting false DNS records into DNS caches, leading users to malicious websites. Through digital signature verification, DNSSEC can detect and reject false DNS records.
4. Enhancing DNS security: DNS is one of the critical infrastructures of the Internet, and many network activities rely on DNS. The use of DNSSEC can improve the overall security of the Internet, reduce the success rate of malicious attacks, and enhance the security of users and organizations.
In summary, the role of DNSSEC is to enhance the security of DNS by using digital signatures and verification mechanisms to ensure the integrity and authenticity of DNS queries. In particular, when DNSSEC is enabled, it allows the verification of the authenticity of authoritative DNS servers, reducing the risk of domain hijacking and DNS fraud, and helping to improve the overall security and trustworthiness of the Internet.
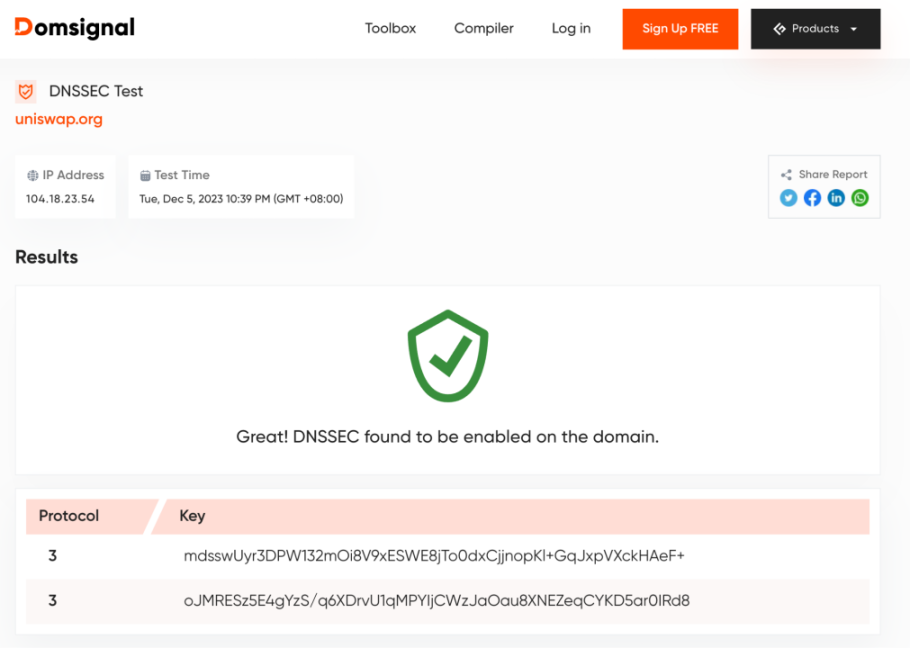
In this test, we conducted a security analysis of DNSSEC through scripts and third-party detection websites such as https://domsignal.com/, checking whether the DNSKEY of the project's domain name is correctly configured and whether RRSIG is valid, as shown below:
Domain Registrar Security Issues
Domain registrars are responsible for registering and managing domain names. Their security measures include protecting user accounts from unauthorized access, preventing domain names from being maliciously transferred or changed, and ensuring the security of domain registration data. A secure domain registrar typically provides two-factor authentication, regular security audits, and strong privacy protection features.
Using an insecure domain registrar may lead to various DNS security issues, including:
1. DNS hijacking: Insecure domain registrars may be susceptible to DNS hijacking attacks, where attackers can tamper with DNS responses to redirect users to malicious websites, exposing them to phishing, malware, or other malicious activities.
2. DNS cache poisoning: Attackers can conduct cache poisoning attacks by providing false DNS records to insecure domain registrars. This can cause insecure DNS servers to cache false data, affecting a wide range of users and leading them to malicious websites.
3. Data tampering: Insecure domain registrars may be vulnerable to man-in-the-middle attacks, where attackers can tamper with data during DNS queries, leading users to receive false DNS responses. This can result in users connecting to the wrong servers or being exposed to the risk of malicious websites.
4. Service unavailability: If an insecure domain registrar is subjected to distributed denial-of-service (DDoS) attacks or other network attacks, its DNS servers may become unavailable, rendering websites and online services inaccessible.
5. Lack of DNSSEC support: Insecure domain registrars may not provide DNSSEC support, increasing the insecurity of DNS queries and making users more susceptible to DNS fraud and other attacks.
In conclusion, using an insecure domain registrar may lead to DNS security issues, exposing users and organizations to various network threats. Therefore, choosing a trusted domain registrar that provides strong security measures, such as DNSSEC support, is crucial for protecting domain and network security. DeFi project teams should carefully evaluate and select domain registrars to ensure that the services they provide are secure and reliable.
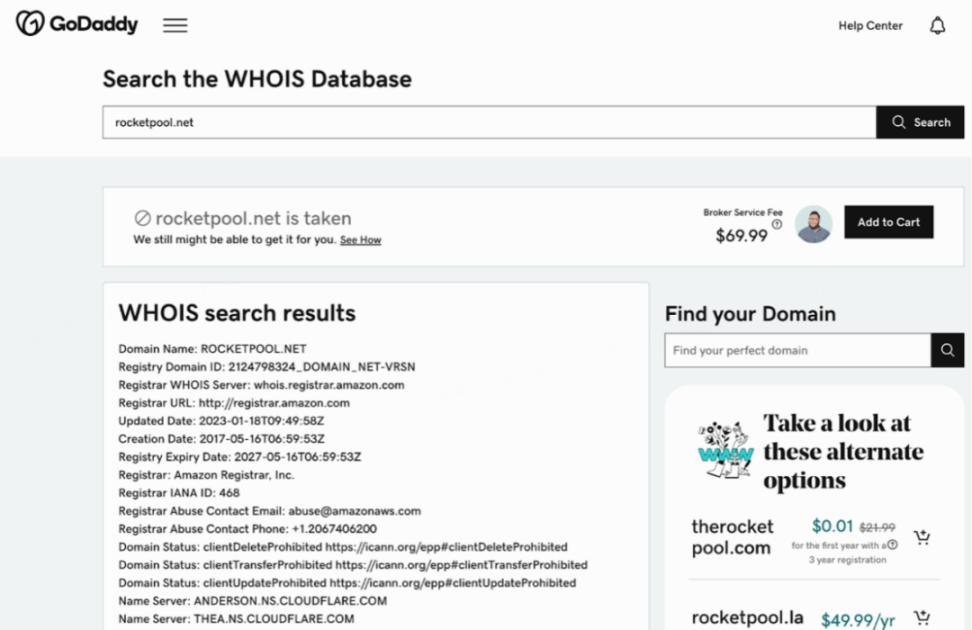
In this test, we conducted domain name queries using services such as https://www.godaddy.com/whois to collect the Register and current Name Server corresponding to the project's domain name, as shown below:
CDN and Traffic Protection Security Issues
Content Delivery Network (CDN) is a service that optimizes website performance and security by distributing website content across multiple nodes globally, reducing latency and improving access speed. CDN security measures include combating Distributed Denial of Service (DDoS) attacks, website application firewall protection, and HTTPS support to ensure secure and encrypted data transmission.
Insecure Content Delivery Network (CDN) providers may bring various security risks, including:
1. Data leakage: Insecure CDN providers may not adequately protect data hosted on their servers. This could lead to the leakage of sensitive information, such as customer data, login credentials, or sensitive documents. Attackers could exploit weaknesses in the CDN to access or steal this data.
2. Man-in-the-middle attacks: Attackers may attempt to conduct man-in-the-middle attacks between the CDN and end users. This means attackers could tamper with or monitor data traffic transmitted through the CDN to obtain sensitive information or distribute malicious content.
3. Service unavailability: If CDN providers are subjected to DDoS attacks or other network attacks, CDN services may be disrupted, rendering websites or applications inaccessible. This can have a severe impact on business availability and performance.
4. Spread of malicious content: If CDN providers do not take sufficient security measures to verify and review the content hosted on their network, malicious users may abuse the CDN to distribute malware, malicious scripts, or other harmful content.
5. Lack of encryption support: Insecure CDN providers may not provide sufficient encryption support, making data transmission susceptible to eavesdropping. This could lead to data leakage and privacy issues.
6. Exploitation of security vulnerabilities: Attackers can exploit security vulnerabilities in insecure CDNs to infiltrate the CDN network and access sensitive data or control network resources.
7. Legal and compliance issues: Some CDN providers may be located in different countries or jurisdictions, potentially involving legal and compliance issues. This could lead to concerns regarding data privacy and compliance.
To mitigate these risks, DeFi project teams should carefully evaluate the security measures, privacy policies, and compliance of CDN providers when choosing a CDN provider. Selecting a trusted CDN provider with a good security record and a dedicated security team is an important step in ensuring data and network security.
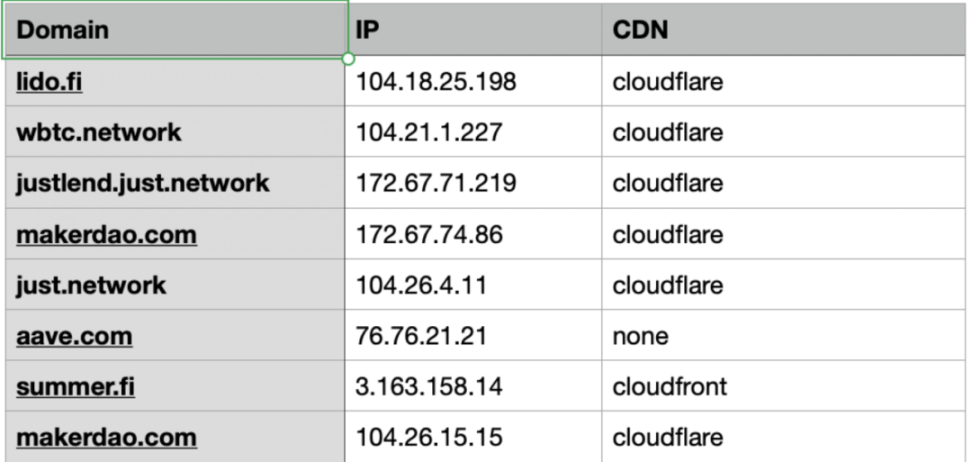
In this test, we obtained the IP corresponding to the project's domain name to analyze the usage of mainstream CDNs such as Akamai, Azure CDN, Cloudflare, Cloudfront, Fastly, Google Cloud CDN, and MaxCDN. An example is shown below:
Source IP Exposure Security Issues
Source IP exposure refers to attackers being able to identify the real IP address of the website's backend server, bypassing the CDN or other security measures to directly attack the server, bypass firewall restriction policies, and other issues. Source IP exposure of web servers may lead to the following security issues:
1. Direct attacks: The exposed IP address becomes a direct target for hackers, including Distributed Denial of Service (DDoS) attacks, which could render the website inaccessible.
2. Exploitation of security vulnerabilities: If the server software has known vulnerabilities, hackers can exploit these vulnerabilities to infiltrate the server.
3. Data leakage risk: Hackers may access sensitive data through the exposed IP, leading to data leakage.
4. Phishing and fraud: Hackers may impersonate the server to conduct phishing or fraudulent activities.
Therefore, protecting the source IP address of web servers is an important measure for maintaining network security. To protect the source IP from exposure, measures are typically taken to hide the real IP address, such as using reverse proxy servers, configuring secure DNS records, and ensuring that all entry points of the server have appropriate security protection, reducing the risk of direct attacks on the source server.
In this test, third-party services were used to attempt to bypass the domain names using CDNs to detect whether the source IP of the project's domain name is exposed, as shown below:
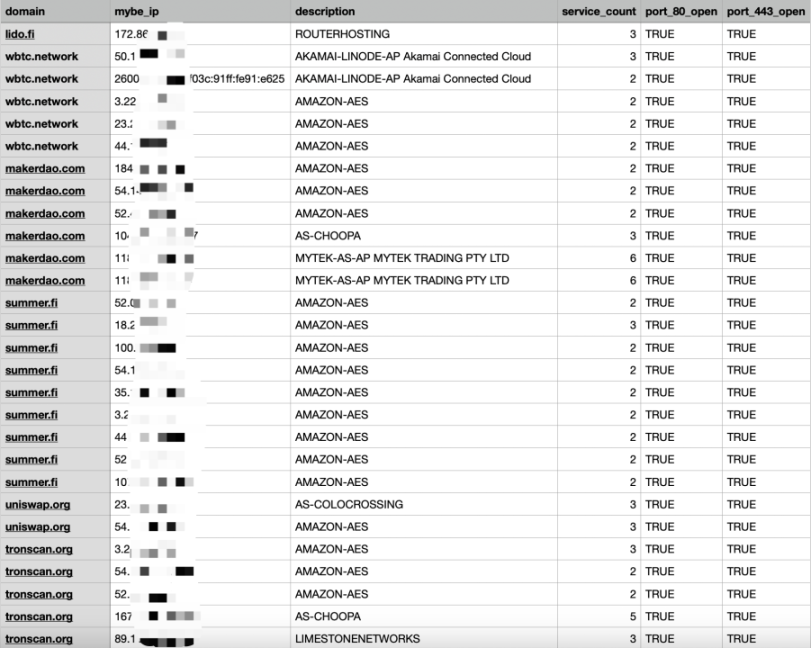
Based on the above tests, let's proceed to analyze the results.
Results Analysis
DNSSEC Security Issues
Partial results:
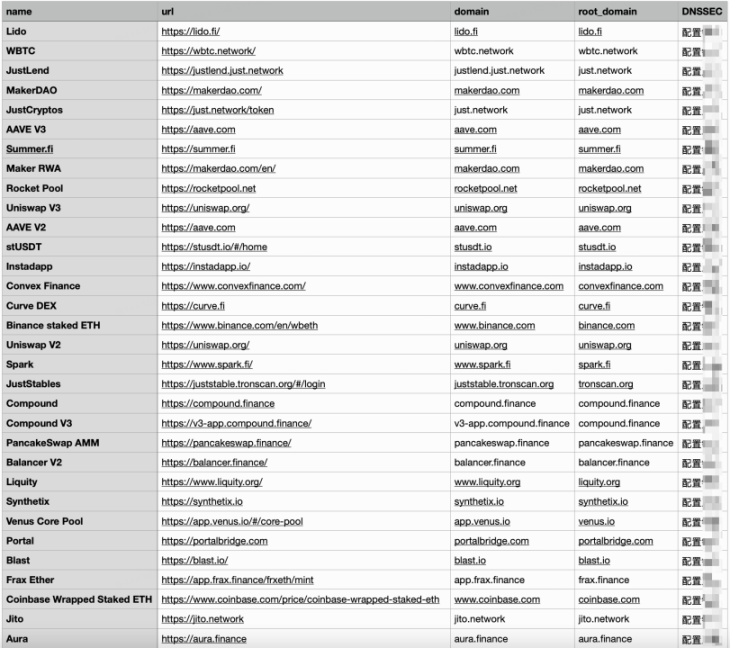
DNSSEC statistics:
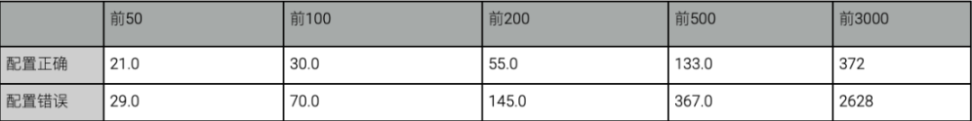
(Quantity distribution)
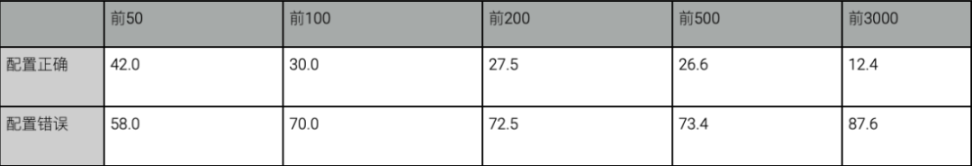
(Percentage distribution)
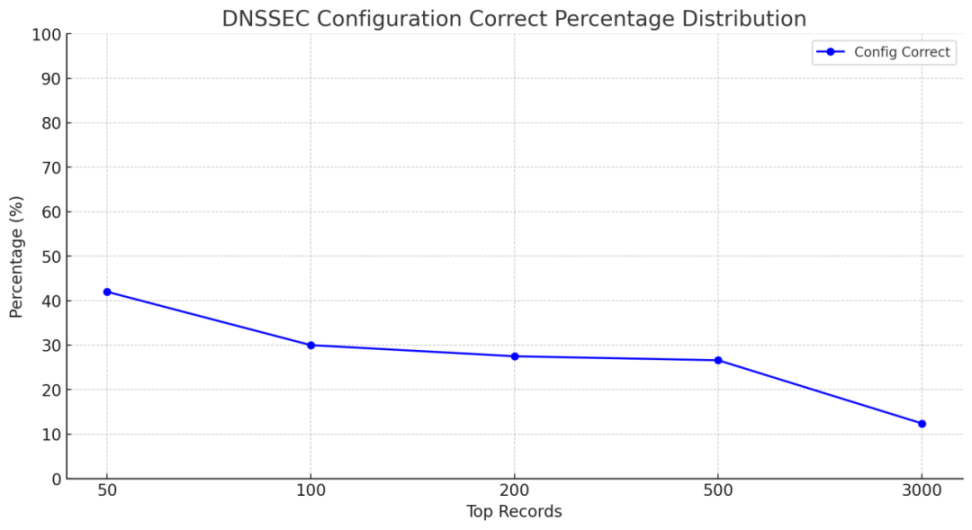
Domain Registrar Security Issues
Partial results:
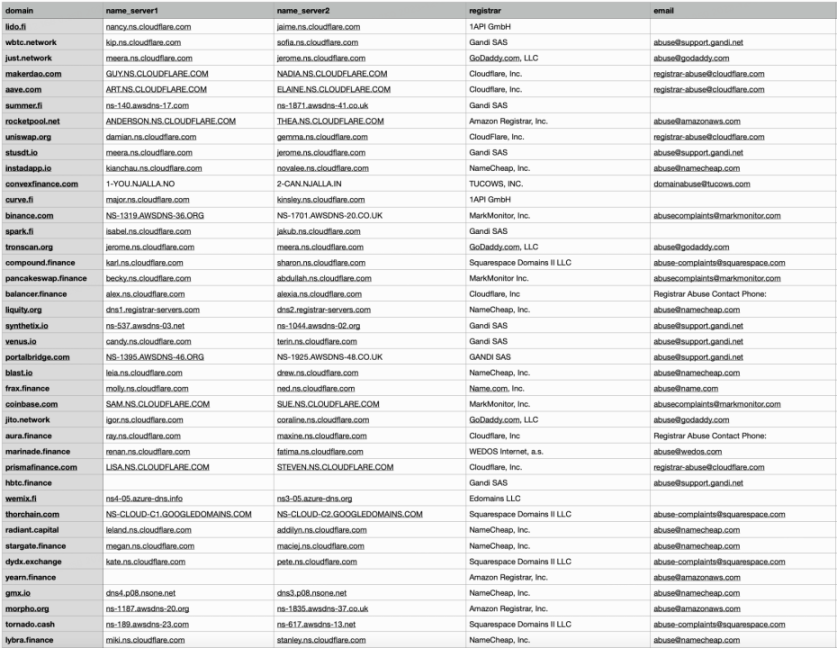
Domain registrar statistics:
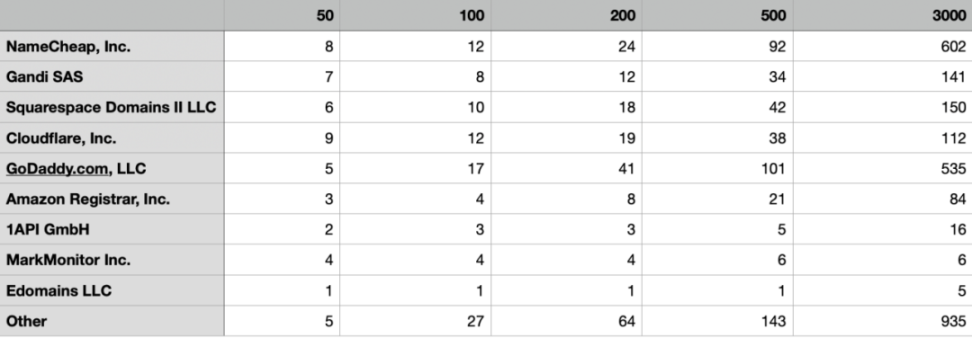
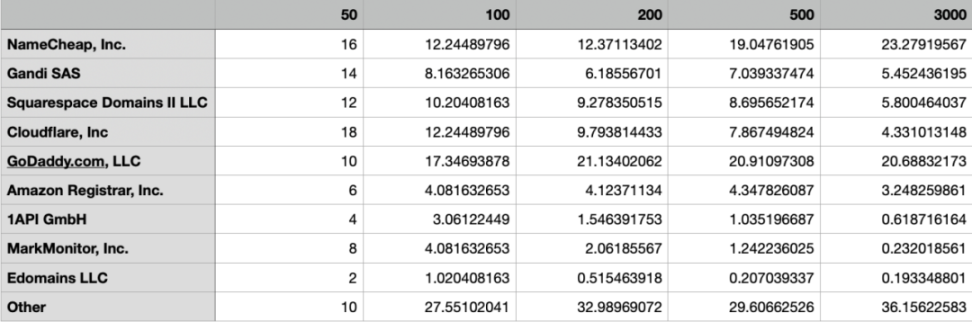
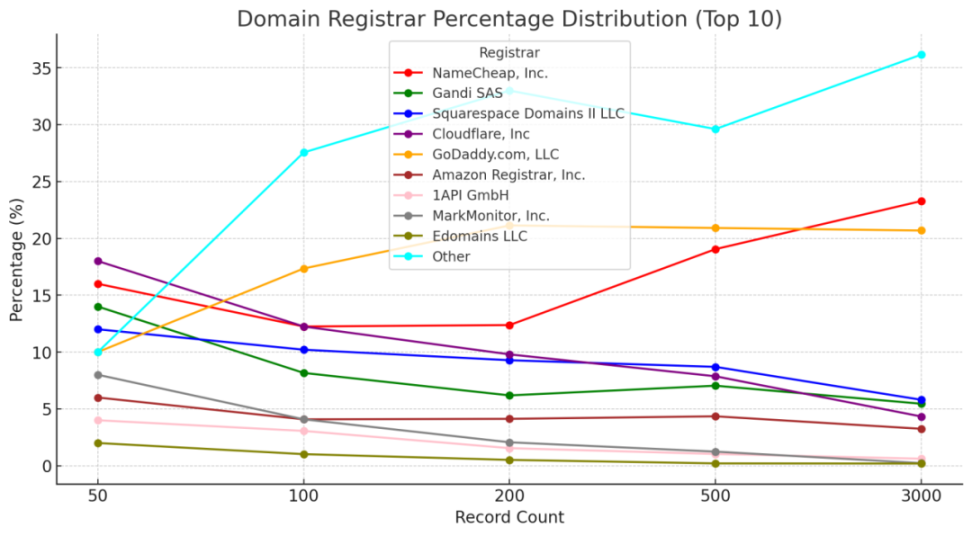
CDN and Traffic Protection Security Issues
Partial results:
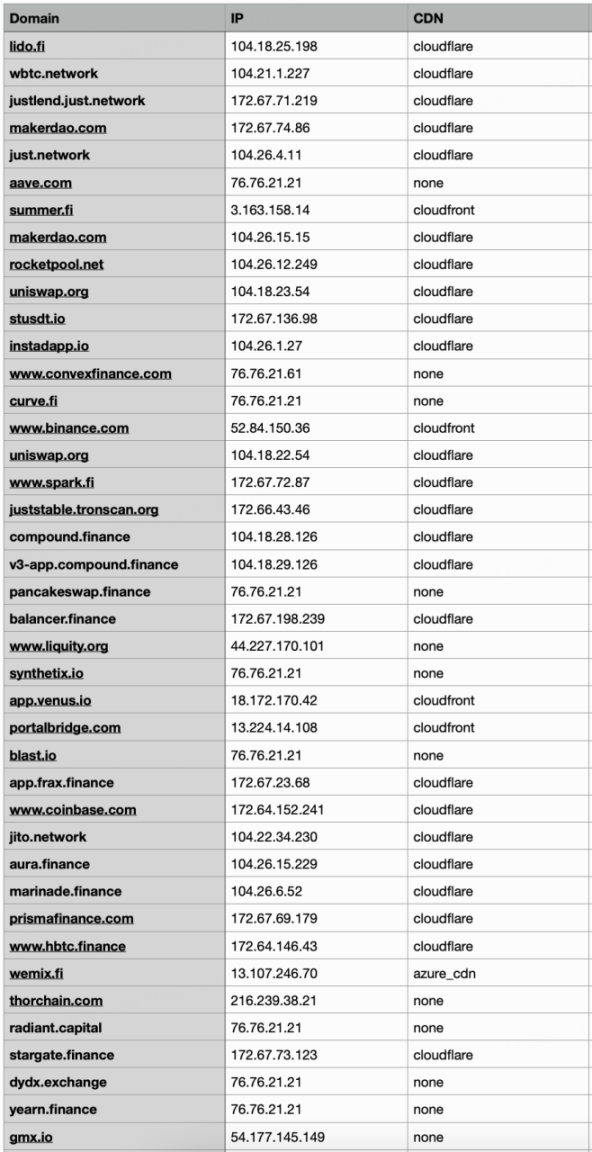
CDN usage statistics:
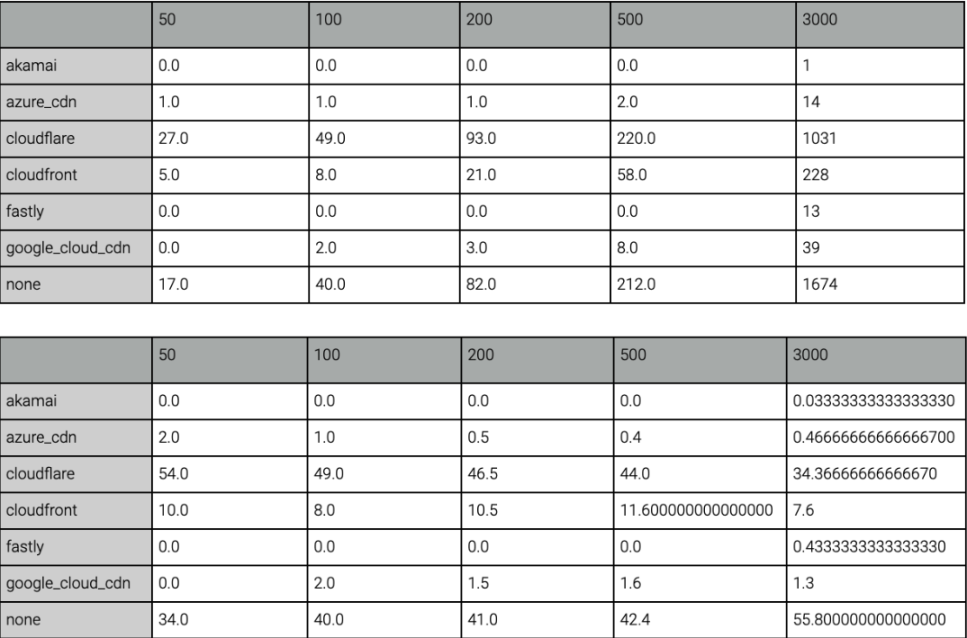
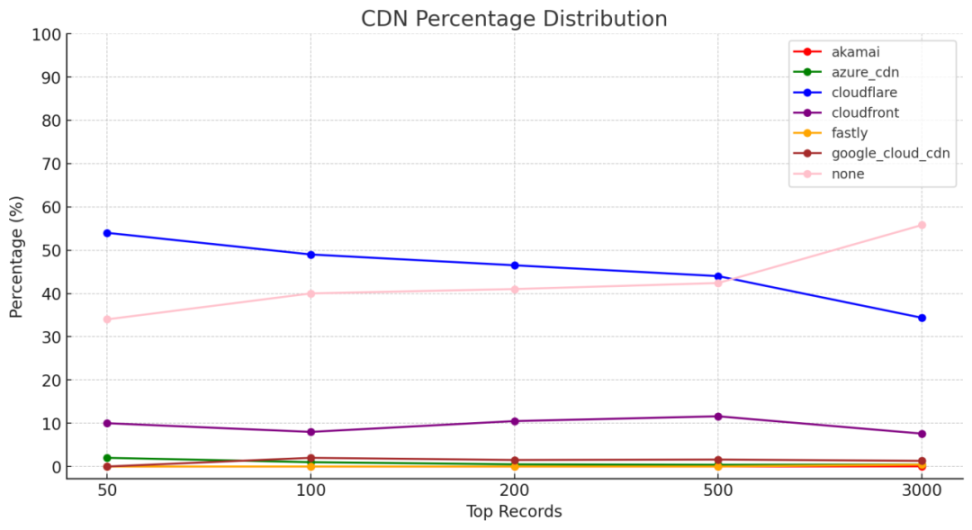
It can be seen that the usage rate of the world's top security CDN provider, Akamai, in the DeFi industry is basically 0, indicating a long way to go in improving the basic security and security awareness of DeFi.
Source IP Exposure Security Issues
Partial results:

Exposure statistics:
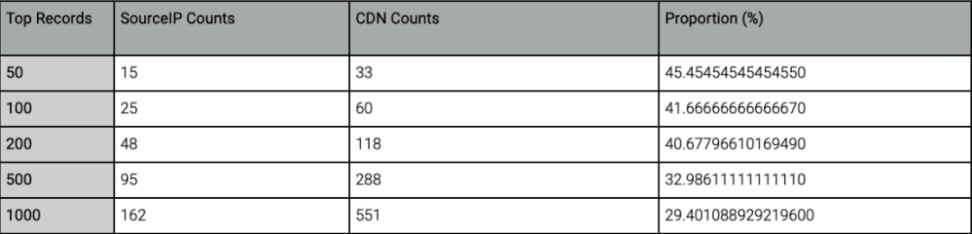
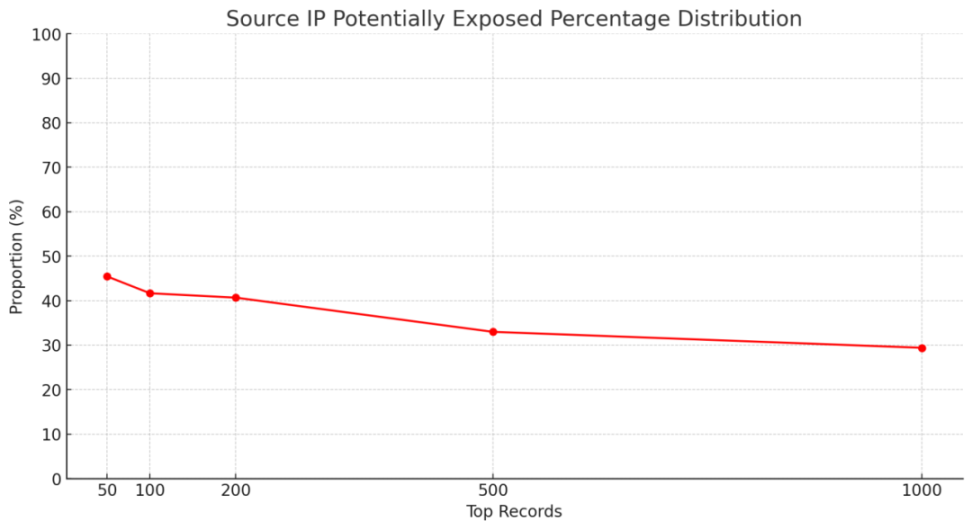
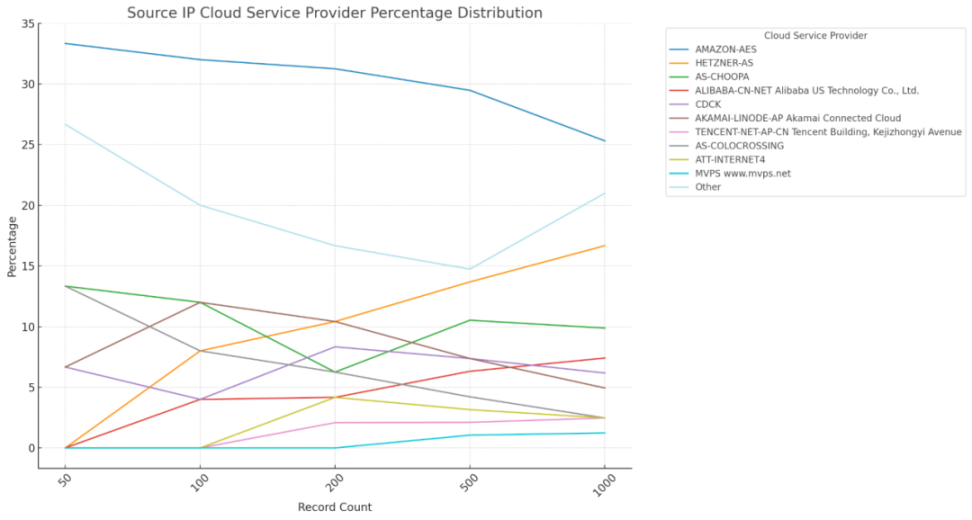
The security issues caused by source IP exposure cannot be ignored. Just on December 7th, the well-known gaming project @XAI_GAMES was hit by a DDoS attack, causing its official website to be unavailable. At the same time, attackers posted a fake official website in the project's Discord community, deceiving victims to visit the fraudulent website and conduct phishing attacks, resulting in a large number of victims being deceived, with losses of approximately over 400 ETH. Therefore, DeFi project teams should prioritize protecting the source IP address of web servers to reduce the risk of direct attacks on the source server.
Summary
From the comprehensive statistical information above, it is clear that the basic security risks of DeFi projects are severe, with a large number of DeFi projects being insecure and at risk of attack.
Through the analysis in this article, we understand that DeFi security is not only about contract security; security is a whole. The security team at SlowMist has released the Web3 Project Security Practice Requirements (https://github.com/slowmist/Web3-Project-Security-Practice-Requirements) and the Web3 Industry Supply Chain Security Guide, both aimed at guiding and reminding Web3 projects to pay attention to comprehensive security measures. The MistEye security monitoring system deployed by the SlowMist security team covers contract monitoring, front-end and back-end monitoring, vulnerability discovery and early warning, focusing on the end-to-end security of DeFi projects before, during, and after the process. Project teams are welcome to use the MistEye security monitoring system to control risks and improve project security.
Acknowledgments: @DefiLlama @censysio
Reference links:
https://www.akamai.com/blog/trends/dnssec-how-it-works-key-considerations
https://en.wikipedia.org/wiki/Domain_name
https://www.akamai.com/glossary/what-is-a-cdn
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




