The application of network gambling, gray and black industries, and money laundering activities to encryption technology has become very mature. The encrypted funds that serve the upstream and downstream of such ecosystems flow around through open and anonymous encrypted networks, inevitably intersecting with compliant encrypted financial fields in the process of fund exchange and realization. This not only brings legal risks to ordinary investors but also contaminates the business addresses of encrypted enterprises.
To help web3 enterprises better reduce anti-money laundering compliance risks and ensure the legitimacy of user fund sources and overall fund risk control, Bitrace, based on on-chain address profiling analysis, introduces a method for assessing the fund risk of addresses based on Tron's "attractive" addresses, by illustrating the illegal use of risk activities on the encrypted infrastructure.
What are "attractive" Tron addresses
"attractive" addresses refer to blockchain addresses with obvious regular numbers or letters in the public key string, with neatly arranged numbers, aesthetic appearance, or special meanings, similar to personalized phone numbers, obtained by screening addresses generated from a large number of randomly generated private keys.
Compared to other ordinary blockchain addresses, "attractive" addresses have more distinct features and are easier to remember. In the practice of analyzing the threat of encrypted address funds, it is not difficult to find that these addresses are often used for network gray and black industries, online gambling, and other businesses, to facilitate functions such as fund receipt and payment, storage, circulation, accepting bets, and fund settlement.
For encrypted enterprises that primarily serve C-end users, these "attractive" addresses and their associated fund addresses pose a more significant fund threat. Therefore, it is necessary to take this risk into consideration when understanding your user address transactions (KYT) related activities.
Example of online gambling exploitation
Using cryptocurrency to participate in online gambling or acting as a casino agent to accept bets outside licensed areas is considered illegal in some countries or regions. For web3 enterprises that provide services such as fund custody, token exchange, and acceptance guarantee of encrypted assets for such users, it will bring certain legal risks to the platform itself.
Our research found that hash-based online gambling platforms commonly use "attractive" addresses to facilitate functions including accepting bets, fund transfer, and fund settlement. For example, the address TGV…ds888, which was highly active between May and October 2022, received a total of 551 bettors' bets amounting to 26,586,162 USDT, as identified by Bitrace's encrypted analysts through address profiling analysis and big data technology mining.
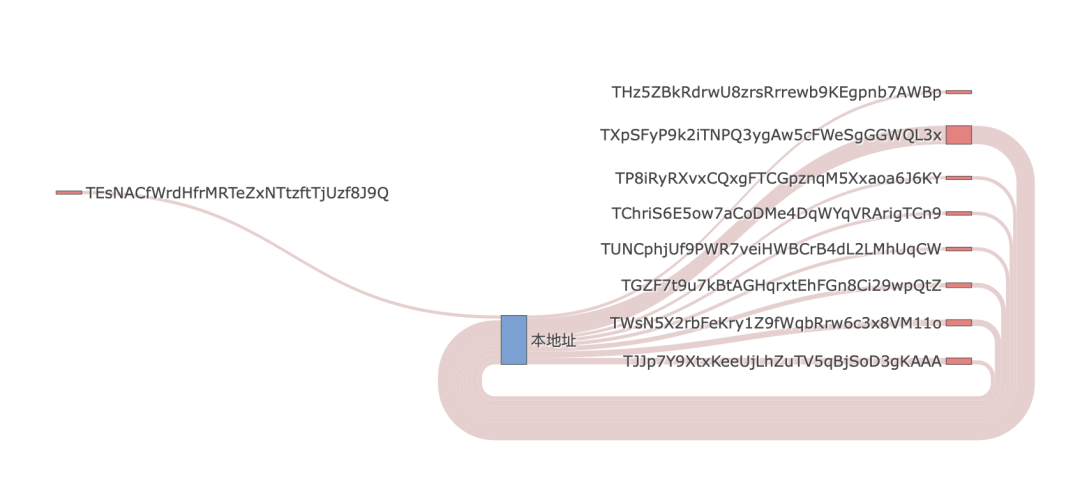
Image from DeTrust "Audit Report"
Based on the interaction pattern with its main counterparties, it was determined that this address is a betting address for a certain hash gambling platform and is also used for fund settlement. Therefore, on-chain transactions show high-frequency, fixed-amount fund flows between multiple addresses, including both bettors and other business addresses.
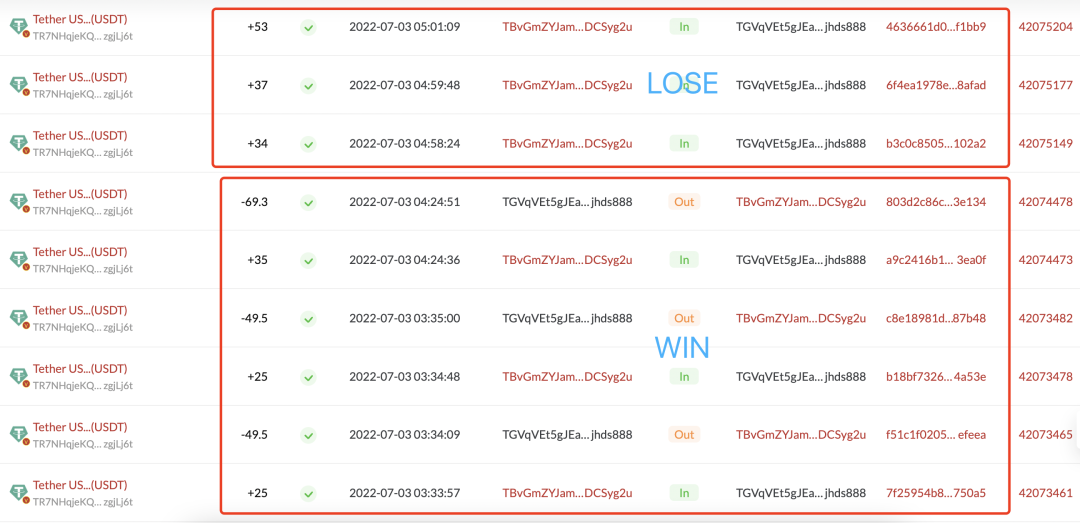
The gameplay is a typical "guess the last digit," where bettors initiate transfers to the betting address. If the hash value of the transfer ends with a specific number or letter, the bettor wins, and the platform returns double the chips after deducting some points. If the last digit does not match, the bettor loses, and the chips are not returned.
Different from traditional gambling websites that only use stable-value USDT as "chips," this type of gameplay also accepts bets in TRX because it is short and quick. From initiating the transfer to completing the fund settlement, it often takes less than a minute, allowing the platform to avoid profit losses caused by fluctuations in the value of encrypted funds in fiat currency.
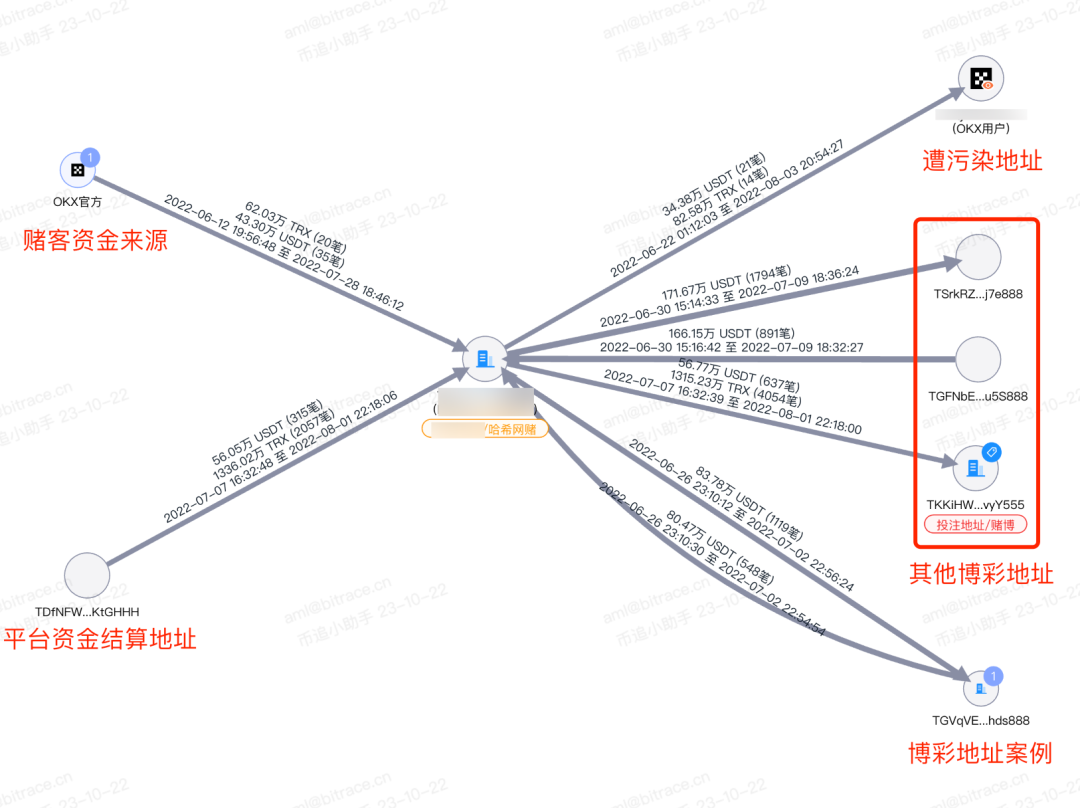
Image from DeTrust "Canvas"
Analyzing the fund activities of platform bettors revealed that typical bettor addresses are only used for gambling and do not have much other activity. The sources and destinations of their funds are mainly from encrypted trading platforms, causing fund contamination to the business addresses of related centralized platforms.
For example, one bettor's address received all their gambling funds from a certain trading platform, initially participating in hash gambling through interaction with TGV…ds888, resulting in a loss of 33,400 USDT. They then engaged in larger-scale and more frequent gambling activities on three other platforms, showing interactions with four "attractive" addresses in USDT and TRX on-chain transactions. This ultimately resulted in a total loss exceeding 250,000 USD, with the remaining gambling funds returned to a certain trading platform.
Through this case, it is evident that "attractive" addresses used for online gambling and their associated fund addresses pose a fund threat to web3 enterprise addresses.
Establishing an address fund threat assessment model
"attractive" addresses are often used for risky activities, but not all "attractive" addresses have the ability to contaminate funds. Therefore, this cannot be the sole criterion for determining address threats. To assist Web3 institutions in better avoiding potential fund risks arising from user address activities and fulfilling encrypted financial anti-money laundering (AML) compliance obligations, Bitrace suggests conducting a comprehensive assessment of the fund threat level of "attractive" addresses and their associated addresses from the following dimensions:
Source of transaction fees. Determine whether the initial transaction fees of the address come from illegal entity addresses or anonymous channels. If "yes," it indicates a higher likelihood of malicious behavior for the address.
Proportion of risky funds. Observe the fund inflow situation of the address. If the proportion of funds from risky sources is high, it indicates a large number of transactions or long-term associations with high-risk addresses, resulting in a higher fund threat level.
Business type. Infer the platform's business type based on address transaction frequency, fund types, and fund flows. If "attractive" addresses have high transaction frequency, large fund flows, and lack public address labels, it suggests the possibility of operating illegal businesses.
Real user activities. Determine whether the address is a personal address based on smart contract interactions, public network exposure, interactions with centralized institutions, etc. More diverse address activities imply a more stable real individual behind the address. Conversely, if address activities are not associated with the user's social media or centralized platforms, these addresses have a lower cost of malicious behavior and a higher fund threat level.
In summary, the more rules a user address meets, the greater the potential fund threat. When formulating KYT rules, web3 enterprises need to consider this point.
Application scenarios
The address fund threat assessment model aims to help web3 enterprises identify potential user fund risks during operations and also provides a reference for individual investors:
- For wallet companies, the establishment of this model can effectively identify the risk types and levels of contract addresses. When users access risk pages or interact with risky contracts, timely reminders or front-end blocking can prevent users from suffering losses.
- For centralized trading platforms, as part of understanding their user address transactions (KYT), this model can provide a cautious evaluation of user address risks, helping platforms adopt different risk control measures for users of different risk levels in the scenario of hot wallet recharges, to prevent compliance risks due to the inflow of risky funds into business addresses.
- For individual users, in over-the-counter trading scenarios, this method can help investors make a simple assessment of the fund risks of their trading counterparts, preventing involvement in cases due to receiving risky encrypted funds.
Conclusion
Regulatory compliance, security protection, and reputation maintenance are crucial in the encrypted industry. All parties involved in the cryptocurrency market should take effective monitoring and compliance measures to ensure legal and transparent transactions and always maintain a distance from fund risk addresses.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




