North Korean APT organization Lazarus Group's main attack purpose is to steal funds, making it the biggest threat to global financial institutions. In recent years, they have been responsible for multiple attacks and fund theft cases in the cryptocurrency field.
Author: SharkTeam
National-level APT (Advanced Persistent Threat) organizations are top hacker groups with state support, specializing in long-term, persistent network attacks against specific targets. North Korean APT organization Lazarus Group is a very active APT group, with its main attack purpose being to steal funds, making it the biggest threat to global financial institutions. In recent years, they have been responsible for multiple attacks and fund theft cases in the cryptocurrency field.
I. Lazarus Group
According to Wikipedia, Lazarus Group was established in 2007 and is affiliated with the Reconnaissance General Bureau, Third Bureau of the North Korean People's Army General Staff Department, specializing in cyber warfare. The organization is divided into two departments: one is BlueNorOff (also known as APT38) with approximately 1700 members, responsible for illegal fund transfers through forged SWIFT orders, focusing on exploiting network vulnerabilities for economic gain or controlling systems to commit financial cybercrimes, targeting financial institutions and cryptocurrency exchanges. The other is AndAriel with approximately 1600 members, targeting South Korea.
The earliest known attack activity of Lazarus Group was in 2009 when they used DDoS technology to attack the South Korean government in the "Operation Troy." One of their most famous attacks was in 2014 against Sony Pictures, due to the release of a comedy about the assassination of North Korean leader Kim Jong-un.
A notable attack by the BlueNorOff organization under Lazarus Group was the 2016 Bangladesh Bank heist, where they attempted to illegally transfer nearly $1 billion from the New York Federal Reserve Bank account belonging to the Bangladesh Central Bank using the SWIFT network. After completing several transactions (tracing $20 million to Sri Lanka and $81 million to the Philippines), the New York Federal Reserve Bank stopped the remaining transactions due to suspicion caused by a spelling error.
Since 2017, the organization has started targeting the cryptocurrency industry and has profited at least $10 billion.
II. Technical Analysis
2.1 Analysis of Common Attack Techniques
In the early days, Lazarus mainly used botnets for DDoS attacks against targets; currently, their main attack methods have shifted to spear phishing, watering hole attacks, and supply chain attacks, as well as targeted social engineering attacks on different individuals.
Tactical characteristics:
(1) Use of spear phishing and watering hole attacks
(2) During the attack, they use system disruption or ransomware applications to interfere with event analysis
(3) Exploiting SMB protocol vulnerabilities or related worm tools for lateral movement and payload delivery
(4) Attacking the SWIFT system of banks to steal funds
Technical characteristics:
(1) Use of various encryption algorithms, including RC4, AES, Spritz, and standard algorithms, as well as XOR and custom character transformation algorithms
(2) Mainly use falsely constructed TLS protocols, bypassing IDS by writing white domain names in the SNI record. Also use IRC and HTTP protocols
(3) System disruption by damaging MBR, partition tables, or writing garbage data to sectors
(4) Use of self-deleting scripts
Attack methods:
(1) Spear phishing: A computer virus term, it is one of the hacker attack methods. It involves attaching a Trojan program as an email attachment with a highly enticing name, commonly in DOCX format, and later adding BMP format. The intrusion method mainly utilizes malicious macros, common Office vulnerabilities, 0day vulnerabilities, and RAT implantation.
(2) Watering hole attacks: As the name suggests, it sets a "watering hole (trap)" on the path that the victim must pass through. Lazarus usually uses watering hole attacks against small-scale banks and financial institutions in poor or underdeveloped areas, allowing them to steal funds on a large scale in a short period. In 2017, Lazarus launched a watering hole attack against the Polish financial regulatory authority, implanting malicious JavaScript vulnerabilities on the official website, infecting 104 organizations in 31 countries, with most targets located in Poland, Chile, the United States, Mexico, and Brazil.
(3) Social engineering attacks: It is a network attack behavior that uses "social engineering" to implement. In computer science, social engineering refers to influencing others through legitimate communication to make them take certain actions or disclose confidential information. This is usually considered a way to collect information, commit fraud, and invade computer systems. Lazarus excels at applying social engineering techniques throughout the attack cycle, whether in delivering bait or identity deception, making it difficult for victims to discern and fall into its trap. In 2020, Lazarus disguised as a recruitment of cryptocurrency personnel on LinkedIn and sent malicious documents, aiming to steal target cryptocurrency by obtaining credentials. In 2021, Lazarus lurked on Twitter as a cybersecurity personnel, sending engineering files with embedded malicious code to attack peers.
Arsenal:
Lazarus uses a large number of custom tools in its network arsenal, and the code used has many similarities. It is certain that these software come from the same developers, indicating that Lazarus has a development team of a certain scale. Lazarus's attack capabilities and toolkits include DDoS botnets, keyloggers, RATs, wiper malware, and malicious code such as Destover, Duuzer, and Hangman.
2.2 Analysis of Typical Attack Events
Below is an analysis of a typical spear phishing attack by Lazarus targeting the cryptocurrency industry. Lazarus induces target employees to download malicious compressed files through email attachments or links and execute the malicious files in the compressed package.
(7) Use a script execution program copied to the %public% directory to execute RgdASRgrsF.js
RgdASRgrsF.js is a typical two-stage script of Lazarus, with a very simple function: it generates a random UID, communicates with the server, and then loops to receive commands from the server and execute them. The commands executed are usually for collecting system information:
With this, the attack is complete, and the hacker can obtain the files or sensitive information they need on the user's computer. Through analysis of Lazarus, it can be found that its current attack targets include government, military, finance, nuclear industry, chemical industry, medical, aerospace, entertainment media, and cryptocurrency, with a significant increase in the proportion of attacks on the cryptocurrency industry since 2017.
III. Money Laundering Analysis
The security events and losses from Lazarus's attacks in the cryptocurrency field are as follows:
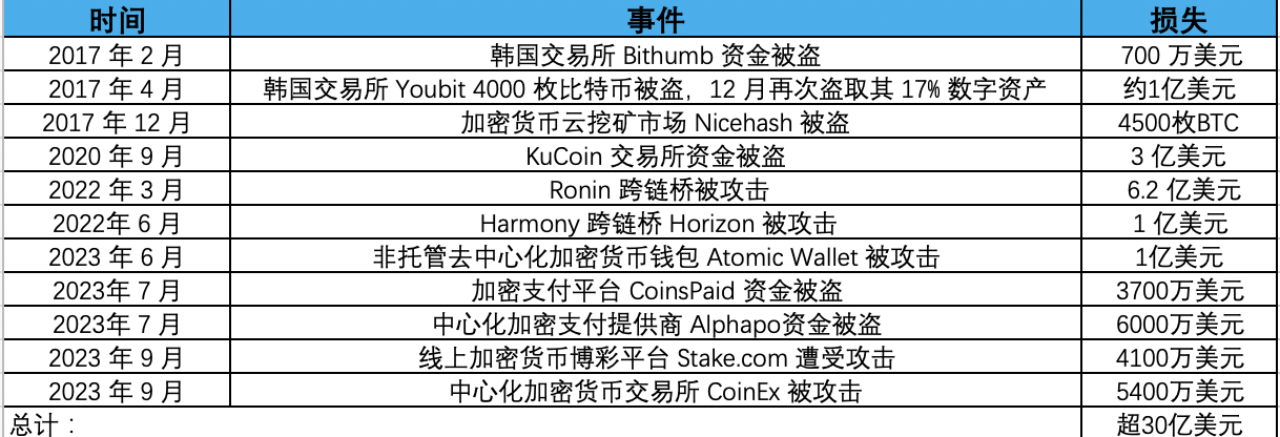
Over $3 billion in funds have been stolen by Lazarus in cyber attacks. It is reported that the Lazarus hacker organization is supported by North Korean strategic interests, providing funds for North Korea's nuclear and ballistic missile programs. In response, the United States has announced a $5 million reward for sanctions against the Lazarus hacker organization. The U.S. Department of the Treasury has also added related addresses to the Office of Foreign Assets Control (OFAC) Specially Designated Nationals (SDN) List, prohibiting individuals, entities, and related addresses in the United States from conducting transactions to ensure that state-sponsored groups cannot cash in on these funds, thus imposing sanctions. Ethereum developer Virgil Griffith was sentenced to five years and three months in prison for helping North Korea evade sanctions using virtual currency. This year, OFAC also sanctioned three individuals associated with the Lazarus Group, including two sanctioned individuals, Cheng Hung Man and Wu Huihui, who are over-the-counter (OTC) traders providing cryptocurrency trading convenience for Lazarus, and the third individual, Sim Hyon Sop, provided other financial support.
Despite this, Lazarus has completed the transfer and laundering of over $1 billion in assets. Their money laundering pattern analysis is as follows. Taking the Atomic Wallet incident as an example, after removing the technical interference factors set by the hackers (a large number of fake token transfer transactions + multiple address splitting), the hackers' fund transfer pattern can be obtained:
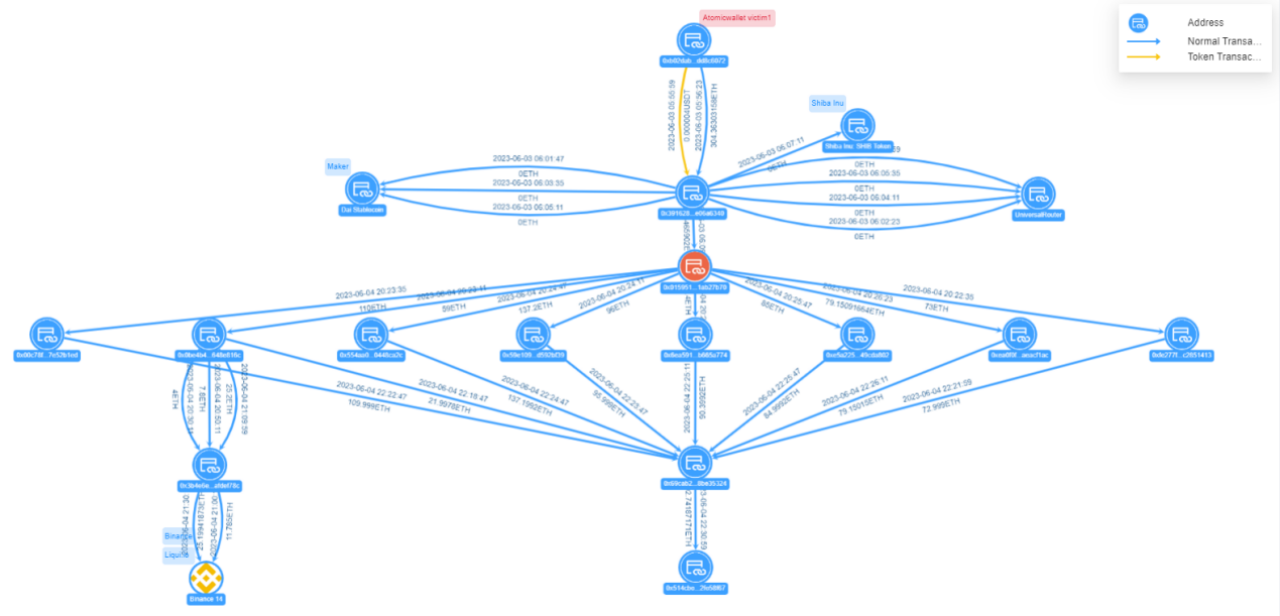
Figure: Victim 1 fund transfer view in the Atomic Wallet incident
Victim 1 address 0xb02d…c6072 transferred 304.36 ETH to the hacker address 0x3916…6340, which was split 8 times through the intermediary address 0x0159…7b70 before being aggregated to address 0x69ca…5324. The aggregated funds were then transferred to address 0x514c…58f67, and the funds are currently still in that address, with an ETH balance of 692.74 ETH (worth $1.27 million).
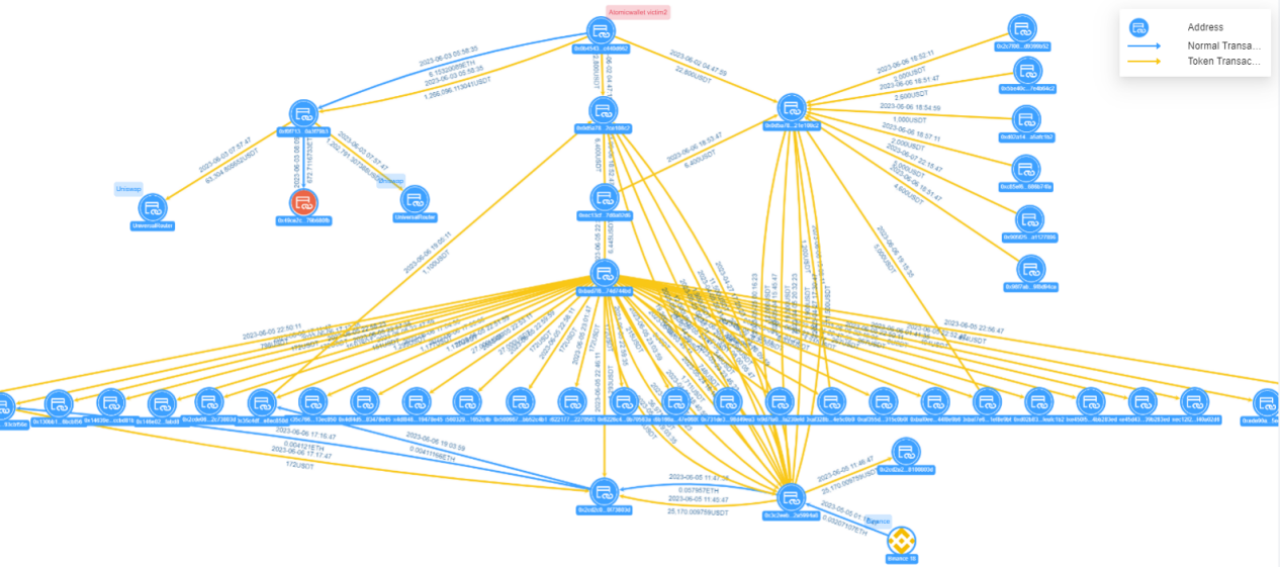
Figure: Victim 2 fund transfer view in the Atomic Wallet incident
Victim 2 address 0x0b45…d662 transferred 1.266 million USDT to the hacker address 0xf0f7…79b3, which was split into three transactions, with two transactions transferred to Uniswap, totaling 1.266 million USDT; the other was transferred to address 0x49ce…80fb, with a transfer amount of 672.71 ETH. Victim 2 transferred 22,000 USDT to the hacker address 0x0d5a…08c2, and the hacker aggregated the funds directly or indirectly to address 0x3c2e…94a8 through multiple splits using intermediary addresses such as 0xec13…02d6.
This money laundering pattern is highly consistent with the money laundering patterns in previous incidents such as the Ronin Network and Harmony attacks, all of which include three steps:
(1) Consolidation and exchange of stolen funds: After launching the attack, the original stolen tokens are consolidated and swapped into ETH through dex and other methods. This is a common way to avoid frozen funds.
(2) Aggregation of stolen funds: The consolidated ETH is aggregated into several one-time wallet addresses. In the Ronin incident, the hackers used a total of 9 such addresses, Harmony used 14, and the Atomic Wallet incident used nearly 30 addresses.
(3) Transfer of stolen funds: The aggregated addresses are used to wash the money out through Tornado.Cash. This completes the entire fund transfer process.
In addition to having the same money laundering steps, there is also a high degree of consistency in the details of the money laundering:
(1) The attackers are very patient, using a laundering process that lasts for up to a week, and all start the laundering process several days after the incident.
(2) Automated trading is used in the laundering process, with a large number of transactions and a uniform pattern in most fund aggregation actions.
Based on the analysis, we believe that Lazarus's money laundering pattern is usually as follows:
(1) Splitting funds across multiple accounts and making small, multiple transfers to increase tracking difficulty.
(2) Creating a large number of fake token transactions to increase tracking difficulty. In the Atomic Wallet incident, 23 out of 27 intermediary addresses were found to be fake token transfer addresses. A similar technique was also found in the recent analysis of the Stake.com incident, but this interference technique was not used in previous incidents such as the Ronin Network and Harmony, indicating an upgrade in Lazarus's money laundering technology.
(3) Increasing use of on-chain methods (such as Tornado Cash) for coin mixing. In earlier incidents, Lazarus often used centralized exchanges to obtain startup funds or conduct subsequent OTC transactions, but recently, there has been a decreasing use of centralized exchanges, and it can even be said that there is an effort to avoid using centralized exchanges as much as possible, which is likely related to recent sanction events.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




