Written by: Bitcoin Magazine Pro
Translated by: Blockchain in Plain Language
Bitcoin is facing its first real survival threat, not from government bans or market crashes, but from quantum computing. The 1.1 million bitcoins (worth about $100 billion) stored in Satoshi's wallet, along with approximately 25% of the total circulating supply of Bitcoin, are currently exposed to old cryptographic keys that are highly susceptible to quantum attacks. When quantum computers mature—whether in 5 years or 25 years—these bitcoins will be compromised.
The Threat
The security of Bitcoin relies on the Elliptic Curve Digital Signature Algorithm (ECDSA). These algorithms make it extremely difficult to forge Bitcoin signatures without knowing the private key. For traditional computers, breaking such signatures would take millions of years. However, quantum computers operate in a completely different way, potentially solving the discrete logarithm problem behind ECDSA in minutes or hours.
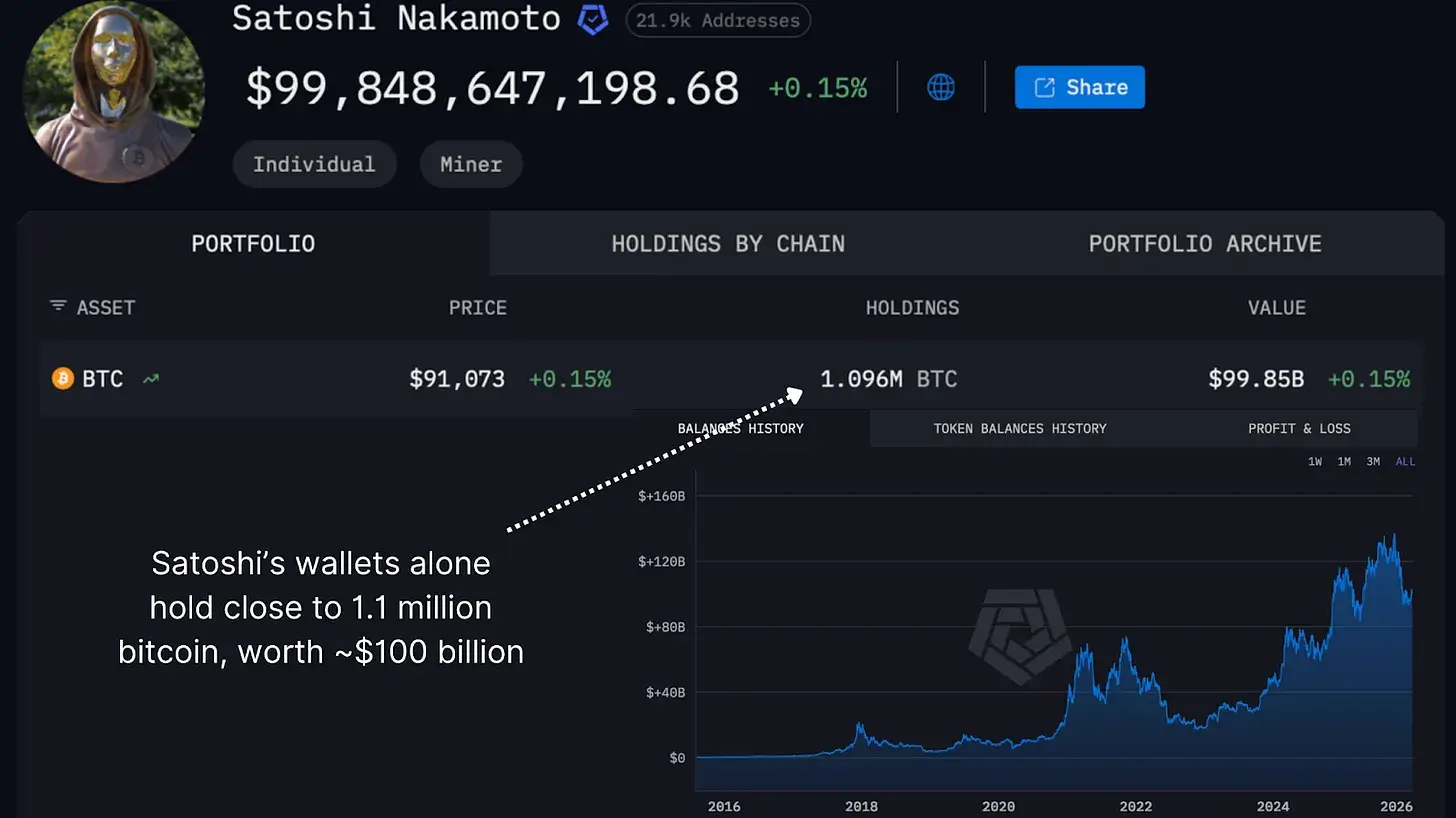 Figure 1: Satoshi's wallet holds nearly 1.1 million bitcoins.
Figure 1: Satoshi's wallet holds nearly 1.1 million bitcoins.
Not all bitcoins face the same risk. Early peer-to-peer K (public key payment) addresses (including Satoshi's address) have their public keys directly displayed on the ledger. For these bitcoins, a quantum computer is akin to a "master key" that can directly access the wallet. In contrast, later address types (like peer-to-peer KH) hide the public key behind an encrypted hash, revealing the public key only when a transaction is initiated. This creates a brief window of vulnerability: during the time it takes to reveal the public key for a transfer until the transaction is confirmed by miners, a sufficiently powerful quantum computer could intercept it.
Uncertainty of the Timeline
The timeline for quantum computing is highly uncertain. It could arrive within a year, or it may never materialize. But uncertainty is the enemy, as Bitcoin needs proactive migration, not passive adaptation. If quantum computers emerge before Bitcoin has migrated to post-quantum cryptography (PQC), Bitcoin will be doomed. Hundreds of billions of dollars in public keys will be exposed, allowing attackers to start stealing bitcoins and dumping them on the market, leading to a devastating price crash.
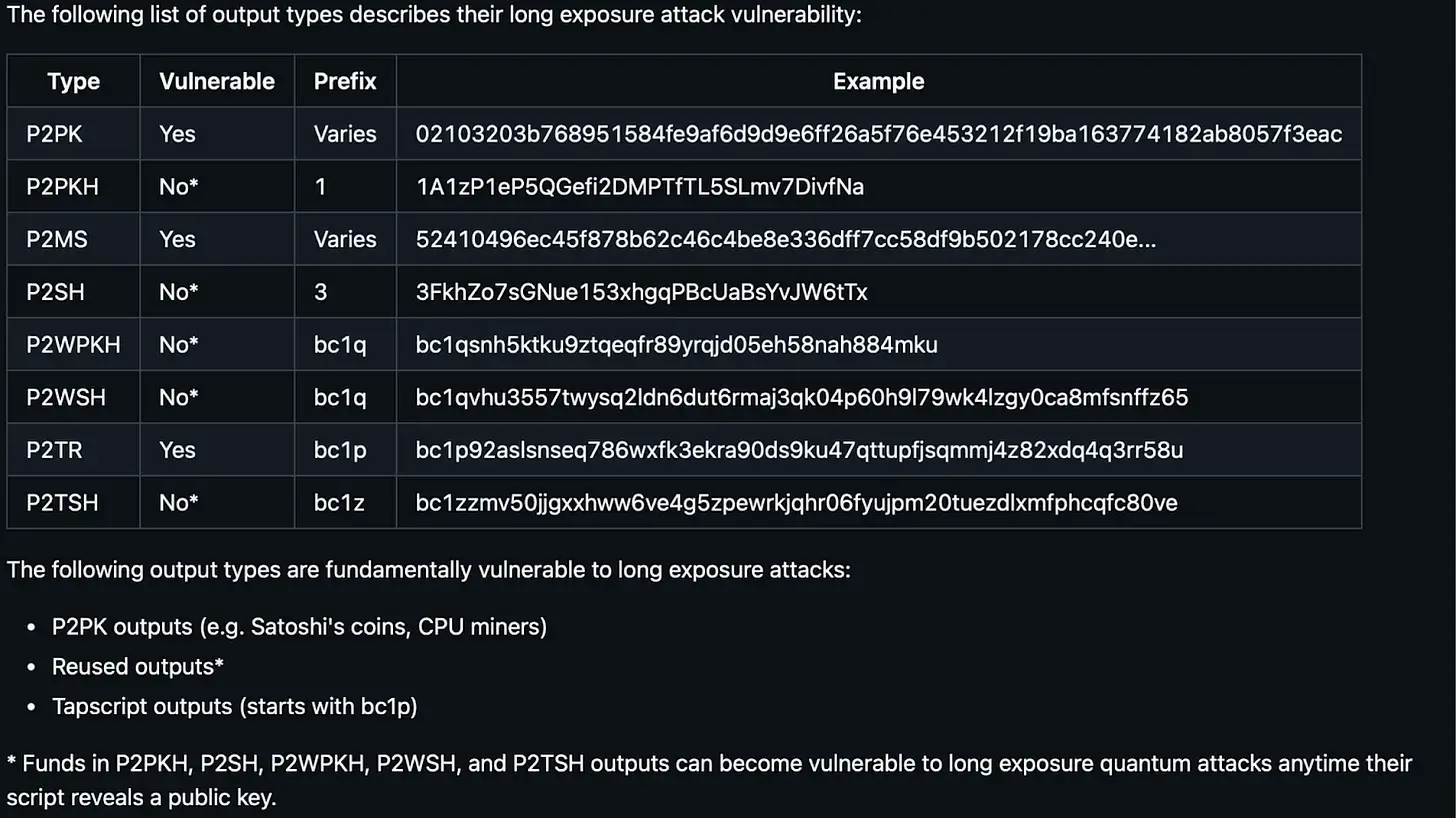 Figure 2: Comparison of long-term exposure attack vulnerabilities of different Bitcoin address types.
Figure 2: Comparison of long-term exposure attack vulnerabilities of different Bitcoin address types.
The timeline for implementing PQC solutions, in the best-case scenario, requires 6 to 12 months just to finalize the code and reach consensus; depending on the level of signature optimization, the migration process may take an additional 6 months to 2 years.
Token Burning
The question is whether a deadline should be set to "burn" those bitcoins that have not migrated to quantum-resistant addresses before the cutoff date. If about 20-30% of the supply is unlocked (compromised) at the same time, Bitcoin will face a massive crisis of trust, and its argument for being "hard money" will collapse. A sell-off of this scale would create bear market conditions and could jeopardize the entire philosophy of Bitcoin.
 Figure 3: Circulating supply of Bitcoin.
Figure 3: Circulating supply of Bitcoin.
However, burning tokens faces significant philosophical obstacles. This effectively means that Bitcoin could become seized property. If the network decides it can redeem itself by burning tokens, what would stop governments or controllers from deciding which addresses (such as those belonging to terrorists or dissidents) can be destroyed and censored? This would set a precedent that destroys sovereign individuals' ownership of assets.
Primary Target
Bitcoin is the world's largest "honey pot." It is the only financial network where you can directly steal value and have 24/7 liquidity to cash out. The dollar cannot do this—stealing large sums would lead to transfers being blocked, and even if hacked, institutions would refund customers. Bitcoin does not have this luxury; it is purely built on trust in the code.
 Figure 4: The number of addresses with balances over 10,000 BTC is significant.
Figure 4: The number of addresses with balances over 10,000 BTC is significant.
If someone achieves the quantum computing capability to break encryption, Bitcoin wallets will become the primary target, as they are easier to liquidate and have a first-mover advantage. If the money has already been taken by the first breaker, the second breaker will gain nothing.
Conclusion
While this survival-level vulnerability has long been recognized in cryptographic literature, the window for preventive action is closing, requiring miners, trading platforms, wallet providers, and individual stakeholders to give immediate strategic attention. The real test is not whether the threat exists, but whether the network can coordinate and systematically migrate to quantum-resistant signature algorithms before sufficiently powerful quantum computers emerge.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。