Written by: Luke, Mars Finance

This week, two seemingly unrelated but closely connected news items from the tech and crypto circles have garnered widespread attention:
- Google claims that its latest "Willow" quantum chip has achieved "verifiable quantum advantage," being 13,000 times faster than top supercomputers on specific algorithms.
- Political dynamics: According to The Wall Street Journal, the Trump administration is negotiating to directly "invest" in a quantum computing company, aiming to "nationalize" this technology.
One technological breakthrough, one political move, both point to a chilling question for the crypto world: Is the "sword of Damocles" hanging over Bitcoin—the quantum threat—getting closer?
Why is "control" more critical than "speed"?
Every time there is quantum news, someone in the community (like the founder of Mysten Labs) comes out to "maintain stability," claiming that a substantial threat is "at least 10 years away." This viewpoint is based on a simple "linear extrapolation"—the assumption that technology will progress at a steady pace like cars.
However, this judgment may have misread Google's "trump card."
In this announcement, what is truly alarming is not the 13,000 times speed but a shift in terminology: from "quantum supremacy" to "verifiable quantum advantage."
If the "supremacy" of 2019 was a show of computational muscle, today's "verifiable advantage" is a precise declaration of control.
Google has successfully simulated "quantum chaos"—a state of a system in physics that is so complex and chaotic that even classical supercomputers cannot simulate it. This proves that Google's ability to manage noise is making significant leaps.
To understand this, we need to clarify two concepts:
What is a "qubit"? Classical computers use "bits" (0 or 1) for computation. Quantum computers use "qubits," which are microscopic particles that can exist in a superposition of 0 and 1 simultaneously. This property gives them the potential to surpass classical computers.
What is "noise"? "Qubits" are extremely fragile. Any slight external interference (like temperature or vibration) can cause them to "err" or "forget" information, which is referred to as "noise." "Noise" is the greatest enemy of quantum computing.
Therefore, Google's achievement means that humanity has made a breakthrough in the core challenge of "controlling noise." This is precisely the only path to building a quantum computer capable of breaking codes and possessing error correction capabilities.
So, this is no longer a distant cry of "the wolf is coming." It is a starting gun that has already been fired, announcing the official commencement of a global "cryptographic migration."
The real "nuclear weapon": Shor's algorithm and the historical burden of HNDL
The urgency of this migration stems from the unique nature of the quantum threat. What exactly is it?
It primarily comes from two algorithms. The first is Grover's algorithm, a "super search engine" that can accelerate the cracking of hash algorithms (like SHA-256). However, this is not a fatal blow; the computational power increase it brings remains within controllable limits.
The real "nuclear weapon" is Shor's algorithm.
The sole purpose of Shor's algorithm is to break the cryptographic foundation of the current internet. For cryptocurrencies, it can do something extremely dangerous: deduce your "private key" from your "public key."
What does this mean? We must first explain two fundamental terms:
Public Key: Like your bank account number or home address. You can give it to anyone, allowing others to transfer money to you or send you mail.
Private Key: Like your bank card password or house key. It is the only proof you have to access your assets, and you must never tell anyone.
Currently, all cryptocurrencies are based on an ironclad rule: a public key cannot be used to deduce a private key. Shor's algorithm is the "master key" that can break this rule.
So, how difficult is it to create this "master key"?
We must distinguish between "physical qubits" and "logical qubits":
Physical Qubits: The "Willow" chip released by Google has 105 physical qubits. You can think of them as 105 inexperienced "musicians" who are prone to hitting the wrong notes. They are very fragile and easily affected by "noise."
Logical Qubits: These are what Shor's algorithm truly needs; they are nearly perfect "musicians."
How do you obtain "logical qubits"? The answer is "massive numbers." Through a technique called quantum error correction (QEC), hundreds or thousands of unreliable "musicians" (physical qubits) form a "band" that corrects each other's errors to simulate a perfect "musician" (logical qubit).
The commonly accepted estimate in the community is that cracking a Bitcoin signature requires about 2,300 "logical qubits."
This corresponds to an astonishing number of "physical qubits": to crack it within 24 hours, approximately 13 million "physical qubits" (musicians) are needed.
This enormous gap is the source of the confidence behind the "10-year theory."
However, this calculation overlooks a more insidious and urgent threat model: "Harvest Now, Decrypt Later" (HNDL).
The logic of HNDL is extremely simple: an attacker with sufficient storage capacity can start today by downloading and storing the entire public ledger of Bitcoin (and other chains). They do not need to crack it immediately; they just need to wait.
When that "13 million qubit" machine is developed in the future, it can be used to decrypt the "historical data" that has already been stored on hard drives.
The early protocol design of Bitcoin (like P2PKH, an early address format) is particularly vulnerable to this attack vector. Its mechanism stipulates that a "public key" (your "home address") for an address is only broadcast to the entire network and permanently recorded in an immutable ledger when that address first sends a transaction.
This means that any Bitcoin address that has ever spent money has its "public key" permanently exposed.
It is estimated that at least 25% of BTC is stored in addresses where the public key has been exposed. For Ethereum (which uses an account model, meaning your public key is always public), this proportion may even exceed 65%.
Most critically, HNDL is a historical burden. Even if Bitcoin successfully upgrades to quantum-resistant algorithms through a hard fork in the future, it cannot retroactively protect these already recorded and exposed public keys in historical blocks.
This "ghost" has already lurked in the system, targeting not the future but the "past."
The expensive "new continent": The real cost of PQC migration
In the face of this clear and present threat, the global cryptographic community has not remained idle. A defensive "great migration" has already begun, aiming to sail toward a new "safe continent"—post-quantum cryptography (PQC).
The "map" for this migration has been drawn by NIST (the National Institute of Standards and Technology, the U.S. government's technology standards-setting body). NIST has initiated a global open competition to select a new generation of cryptographic standards that can withstand quantum computer attacks. The first batch of "winners" has already been determined:
- ML-KEM (Kyber): for public key encryption and key exchange.
- ML-DSA (Dilithium): for digital signatures (to replace Bitcoin's signature algorithm).
- SLH-DSA (SPHINCS+): as a backup standard, based on lattice cryptography (a new type of mathematical problem considered difficult for both classical and quantum computers) and hash algorithms to diversify risk.
However, while the map of the "new continent" has been drawn, the cost of navigation may be prohibitively high.
We have previously discussed the challenges of "governance" and "consensus" too much, but the reality is that PQC algorithms themselves (especially hash-based SPHINCS+) are extremely costly in terms of performance.
According to the latest Ethereum testnet data (such as the Poqeth 2025 study):
- Gas cost: Current ECDSA signature verification costs about 21,000 Gas. In contrast, SPHINCS+ verification costs as much as 1,200,000 - 2,500,000 Gas—an increase of over 100 times. In a network with a block gas limit of only 30M, a single signature consumes nearly 10% of the capacity, which is completely unscalable.
- Signature size: ECDSA signatures are about ~70 bytes. In contrast, SPHINCS+ signature size skyrockets to ~41,000 bytes (about 41KB)—an increase of nearly 600 times.
As pointed out sharply in the community: "In a block, gas is far from enough; it can't run, let alone that old-fashioned Bitcoin network."
This "inability to run" reality makes the word "upgrade" feel incredibly heavy. It is no longer a simple governance choice between "soft/hard fork," but a fundamental technical feasibility issue.
Different blockchains are preparing their own "ships":
- Bitcoin's "Dreadnought": The community is discussing an extremely radical "hard fork" proposal. A hard fork is a mandatory, non-backward-compatible network upgrade, akin to an entire traffic system suddenly switching from "driving on the right" to "driving on the left." This proposal may even "freeze" funds in old addresses that have not migrated. Such a "cutting off the arm" strategy faces significant consensus resistance.
- Ethereum's "Exploration Fleet": Vitalik Buterin's roadmap is much more flexible. He suggests using L2s (layer 2 networks, like Arbitrum or Optimism, designed to speed up and reduce costs for Ethereum) as a "testing ground" for PQC, gradually infiltrating through AA (account abstraction, a new feature that makes Ethereum wallets smarter and more flexible) to ultimately complete the replacement "from the outside in."
- Solana and BNB Chain: As representatives of high-performance public chains, they are currently more in the research and exploration phase and have not proposed a clear official roadmap like Ethereum. Performance overhead is their biggest concern in migrating to PQC.
Comparison of mainstream blockchain PQC migration strategies.
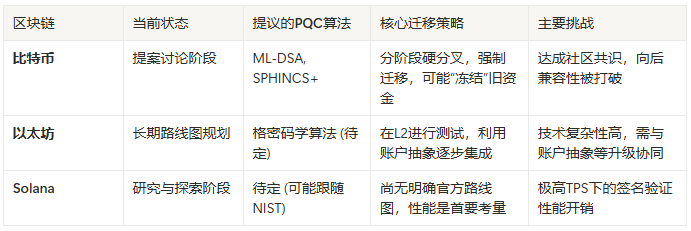
This comparison table clearly reveals that this is not just a choice of technical routes, but a survival of the fittest in governance models across various projects.
First Acceleration: The Geopolitical Race for Nationalization
Don’t think this is just a matter for "code monkeys." The real force driving this "great migration" is the national teams.
Quantum computing has long been a "strategic high ground" in the great power game. The U.S. National Quantum Initiative Act in 2018 allocated $1.2 billion; China's "14th Five-Year Plan" lists it as the second major focus, with public investment estimated to exceed $15 billion.
But this is still just "money support."
The Wall Street Journal's report on the "Trump administration negotiating equity stakes" sends a completely different signal: this is no longer "government support," but nationalization. Quantum computing is transitioning from a "research project" to a "national strategic asset," comparable in nature to nuclear weapons or national oil companies. What the U.S. government wants is no longer influence, but absolute control.
This "national-level" arms race is a double-edged sword.
On one hand, the frenzied investment from the "national teams" is hastening the emergence of this quantum specter, significantly compressing our defense time.
On the other hand, it is precisely this fear of national security that is forcing NIST to desperately create PQC standards.
The biggest risk brought by the "national teams getting personally involved" is the fragmentation of standards.
NIST is working on "open-source" standards, hoping for global adoption. However, if the U.S. government controls core technologies through "equity," other major powers will inevitably develop their own "national standards" for national security reasons.
This could lead to a "Splinternet" at the cryptographic level.
This is fatal for systems like BTC and ETH, which rely on global unity and borderless consensus. A demand for "national sovereignty" could fundamentally undermine the "decentralized" global consensus.
Second Acceleration: The Bubble of Wall Street Capital
If the "national teams" are the first accelerator, then the second accelerator is Wall Street.
While the "10-year theory" was still popular, the capital markets had already gone "all in" with real money. Over the past year, quantum computing companies in the U.S. stock market have seen astonishing surges, such as $RGTI (Rigetti Computing), whose stock price soared from $0.8 to $40, a staggering increase of 50 times.
However, this enthusiasm is backed by a high valuation bubble. Companies like $IONQ and $QUBT have EV/sales (enterprise value/revenue) ratios as high as 400 times or even over 10,000 times. It’s important to note that these companies are currently all in a state of severe losses.
This poses a huge risk for investors chasing high stock prices. But for the entire crypto world, it sends a more dangerous signal: the market (private capital) is crazily "bleeding" for the quantum race alongside the "national teams."
Whenever this "quantum bubble" bursts, the massive funds injected have already significantly accelerated the R&D processes of these companies. This constitutes another layer of "accelerator," making the "10-year theory" seem even less reliable.
Survival Rules in the Era of "Great Filtering"
Google's "verifiable quantum advantage" is not a drill; it is a starting gun. It announces that humanity's control over quantum systems is crossing a threshold, moving from "theory" to "engineering."
Under the dual acceleration of the "national teams" and "Wall Street," participants in the circle should wake up:
- The threat is here. The "ghost" (HNDL) has entered the village; it is "peeking" at all your exposed historical public keys.
- The "new continent" (PQC standards) has been found; NIST has drawn the map.
- The great migration is the only way to survive. But the real challenge is first technical feasibility (cost and performance), and then "governance" and "consensus." If it "can't run," governance is out of the question.
In the face of this future, the survival rules for different roles are simple:
- For VCs and funds: Immediately incorporate "quantum readiness" into the "DD" (due diligence, i.e., in-depth research before investment) core framework. A project that has no plans for PQC migration or avoids discussing its high performance costs should be seen as a significant risk point.
- For developers and project teams: Start studying NIST standards immediately. New systems must adhere to the "crypto-agility" principle—this design concept means making cryptographic modules "pluggable," allowing for future replacements without starting from scratch.
- For ordinary token holders: Develop good "cryptographic hygiene" habits before PQC wallets become widespread. The core rule is simple: never reuse addresses! Use a new address for every payment. This simple habit can greatly reduce your public key exposure risk and prevent you from becoming a "historical legacy issue."
The quantum threat is not "doomsday"; it is a great filtering.
It will ruthlessly filter out those ecosystems that are chaotic in governance, slow to respond, and only focused on speculation. Ultimately, those who can successfully "land" will be the projects that truly have capability, vision, and execution power, and they will be the ones who can "create a safe and autonomous financial future."
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




