Author: Tuo Luo Finance
Hackers are a constant presence every year, and this year is no exception. Since the inception of cryptocurrency, network attacks targeting it have emerged, evolving into more complex attack methods, sophisticated attack logic, and more deceptive technical means as technology matures. However, it must be acknowledged that no matter how tight the defenses are, they cannot withstand the weaknesses of human nature. Recently, the Web3 star social project UXLINK fell victim to such an attack.
Stolen in the early morning, contract issuance increased, and token prices plummeted. In less than half a day, UXLINK experienced one of its most catastrophic moments in history, even showcasing a dramatic "black eats black" scene.
The security of crypto projects seems to ultimately be a muddled account.
Unlike other projects, UXLINK may not be unfamiliar to users outside the circle. UXLINK is a social project built on Telegram, which differs from previous generalized social models by focusing on "acquaintance socializing." It allows one-click login through Telegram, WhatsApp, TikTok, and EOA wallets, providing deep social scenarios and token incentives to retain users and drive growth, emphasizing community-driven group functions and asset issuance.
From a technical and traffic acquisition perspective, UXLINK undoubtedly stands on the shoulders of giants. Telegram, the parent company, not only provides support in terms of technology and components but also offers preferential treatment in traffic acquisition. From onboarding to graphic formation, group tools to social trading, everything is seamlessly integrated within Telegram.
As a result, since its launch in April 2023, UXLINK has performed exceptionally well. It has garnered the favor of crypto-native capital such as OKX Ventures, Matrixport Ventures, SevenX Ventures, HashKey Capital, and Animoca Brands on the funding side, and its application direction has completed a cold start ahead of ordinary social DApps. By April 2024, UXLINK had 5.3 million registered users and built nearly 90,000 group chats. As of August 2025, data released on its official website shows that UXLINK's registered users have reached 54 million, with daily active wallets surpassing 24 million, propelling it to become a leading platform in Web3 social networking due to its massive user base.
In terms of assets, UXLINK adopted a dual-token model, consisting of a native utility token based on UXUY and a governance-focused UXLINK token. The former is primarily used for community and ecosystem development, allowing users to earn UXUY through invitations or other community activities, while the latter emphasizes governance functions, with a total supply of 1 billion tokens, of which 65% is allocated to the community, 40% to users, and 25% to developers and partners. In April of last year, UXLINK launched its first airdrop event, where users could claim airdrops with airdrop voucher NFTs, resulting in over 1.4 million NFTs being minted, with 15% of users receiving the airdrop. However, it is worth noting that the token's performance can only be described as mediocre. After UXLINK was listed on exchanges on July 18, it soared from $0.0998 to a peak of $3.85, but subsequently continued to decline, stabilizing around $0.32-$0.35 before this incident occurred.
Despite the poor performance of the token, UXLINK's operations have remained active compared to other social projects. It has strategically launched a social growth chain, entered the PayFi space, and subsequently initiated staking and airdrop activities to capture user attention. In terms of ecosystem building, it has also performed remarkably, establishing partnerships with over 500 industry projects and continuously expanding its market from Japan and South Korea to North America. In short, within the realm of social projects, UXLINK has maintained a strong presence and can be considered a standout.
Building a project is difficult, but destroying one only requires a single theft.
At 00:43 on September 23, security company Cyvers issued a warning, stating that its system detected suspicious transactions involving UXLINK, amounting to $11.3 million. The cause stemmed from within the project; due to a private key leak, an attacker executed a delegateCall operation on the UXLINK multi-signature wallet at 22:53 on September 22, removing the original multi-signature administrator and setting themselves as the sole controller of the project. Subsequently, this address called addOwnerWithThreshold, transferring out $4 million in USDT, $500,000 in USDC, 3.7 WBTC, 25 ETH, and approximately 3 million UXLINK tokens, with some being cross-chain bridged to the mainnet.
Within just five minutes of the news breaking, the market reacted strongly, with UXLINK's spot price rapidly dropping from around $0.3 to below $0.18, continuing a downward trend. An hour later, UXLINK officially acknowledged the attack, and nine hours later, UXLINK tweeted that it was working around the clock with internal and external security experts to identify the root cause and control the situation. They contacted major CEXs and DEXs to urgently freeze suspicious UXLINK deposits and later stated that most of the stolen assets had been frozen, emphasizing that there were no signs indicating that individual user wallets had been attacked.
According to standard procedures, acknowledging the theft, conducting emergency public relations, and beginning post-disaster reconstruction would typically mark the end of the incident. However, the hacker clearly had other plans. At 9:54 AM on the 23rd, the most destructive step began, as the attack address, wielding management power, used the contract minting function without permission to issue an additional 1 billion UXLINK tokens. The stability of a monetary system relies on the stability of its currency value, and the primary condition for currency value stability is controlling the circulation of the currency. The large-scale issuance undoubtedly brought the entire ecosystem to the brink of collapse. UXLINK continued to plummet, with the lowest price approaching zero, and the market cap on-chain dropped to a minimum of $80, while before the incident, UXLINK's market cap was $150 million. Current CEX data shows that the market cap has only recovered to $65 million.
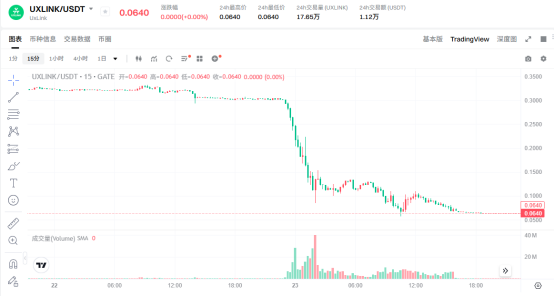
Even more despicable, after the additional issuance, the hacker continued to sell off on major exchanges, exchanging the newly minted UXLINK through different wallets, accumulating 6,732 ETH and profiting $28.1 million. It is worth mentioning that during this period, some users, following empirical practices, attempted to bottom-fish after UXLINK's announcement, but due to the hacker's additional issuance route, their losses further expanded, with one address even spending $900,000, ultimately nearing zero.
At this point, it seemed that the situation was coming to an end, but a dramatic twist occurred again. The hacker who stole UXLINK's assets fell victim to "black eats black," as they were attacked by a phishing team due to having authorized a phishing address. Upon verification, approximately 542 million $UXLINK tokens that were illegally obtained were stolen using "authorized phishing" techniques. After working hard to steal, they ended up making someone else a profit; it can only be described as unexpected.
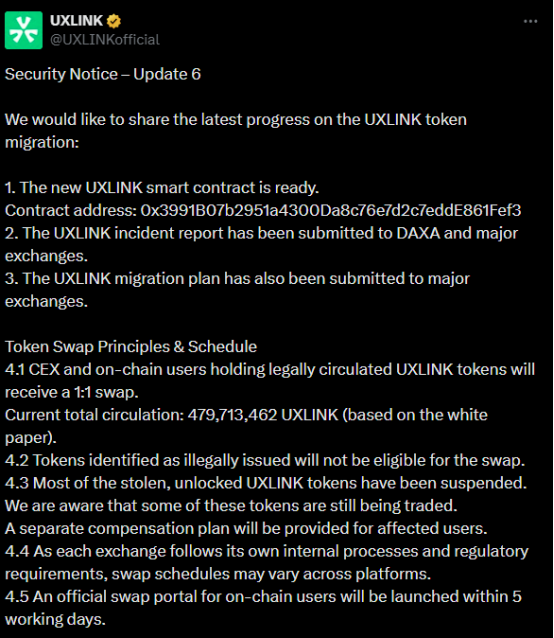
According to the latest developments, UXLINK has initiated a token contract migration plan. The new UXLINK smart contract has successfully passed a security audit and will be deployed on the Ethereum mainnet, canceling the minting and burning functions while maintaining its cross-chain capabilities through cross-chain partners. The new UXLINK smart contract is ready, with the contract address being 0x3991B07b2951a4300Da8c76e7d2c7eddE861Fef3. CEX and on-chain users holding legally circulating UXLINK tokens will receive a 1:1 exchange, while tokens deemed illegally issued will not qualify for exchange. For some tokens still being traded, the team will provide a separate compensation plan for affected users.
From this incident, the project's response speed was quite rapid, not only stabilizing user emotions quickly but also providing a solution at the first opportunity. Their emergency management performance is commendable. However, it must be said that the essence of this attack lies in the lack of multi-signature management. Although a Safe multi-signature mechanism was adopted and multiple multi-signature accounts were configured, actual management was severely lacking, rendering the multi-signature system virtually ineffective, which led to the crisis.
It is worth noting that the method of additional issuance has recently become quite frequent. Similar to UXLINK, the Web3 project incubation and launch platform Seedify.fund was also hacked and had 3 trillion tokens issued, severely impacting the SFUND token, which dropped from $0.42 to $0.08 and is now stabilizing around $0.27.
Just today, the European Web3 project Griffin AI was attacked by hackers to maliciously issue 5 billion GAIN tokens just 12 hours after completing the Binance Alpha airdrop, causing its token price to plummet by 95% to nearly zero. According to official disclosures, the attack address initiated the attack by introducing an unauthorized LayerZero Peer, deploying a forged Ethereum contract to bypass the official contract, and then using the forged tokens to achieve on-chain issuance on the BNB Chain via LayerZero. The hacker GAIN then profited by dumping the abnormal issuance address, earning 2,955 BNB (approximately $3 million), which was exchanged for 720.81 ETH through the cross-chain bridge deBridge and then transferred entirely to Tornado Cash for mixing. As of now, Griffin AI has removed the official liquidity pool for GAIN on the BNB chain and formally requested all CEXs to suspend trading, deposits, and withdrawals of GAIN (BSC) tokens. However, it should be noted that the project has not proposed a solution for compensating the victims.
The only silver lining is that, unlike UXLINK and SFUND, some bottom-fishers of GAIN successfully reaped decent returns, with one address buying $20,000 worth of GAIN at an average price of $0.00625, realizing a floating profit of $107,000 within an hour.
Overall, compared to previous one-time attacks, the current attack methods are increasingly focusing on contract permissions and token issuance control. Although both are forms of attack, the latter is clearly much more malicious. For projects, malicious token issuance destroys the entire ecosystem centered around the token, significantly reducing user trust in the project and triggering a series of chain reactions. A typical example is that with the frequency of additional issuance events, voices have already emerged in the market suggesting that project parties are self-directed and self-acted through multi-signatures.
From a security perspective, the management of multi-signatures is also worth paying attention to. Nowadays, project parties generally adopt multi-signature systems for smart contracts, but management should keep pace. The primary step should be to enforce the use of hardware wallets for physical isolation, and secondly, to decentralize the signers as much as possible to mitigate centralized risks in terms of time, space, hardware, and backups. In addition to avoiding risks through hard technical means, the soft environment is also crucial. Multi-signature holders should maintain anonymity and establish cross-verification processes for effective secondary checks, building a human defense line. Furthermore, drills are essential; maintaining a sense of crisis and conducting regular drills with crisis response plans is vital, as in the industry, a fake drill can turn into a real battle in an instant.
Yuxian, the founder of Slow Mist, also suggested that multi-signature owners should match hardware wallets that only support complex signatures and large screens, covering the entire process from mnemonic phrase generation to usage, and should also include Passphrase or SSS backups to enhance security. In daily use, vigilance should be heightened, and signature requests should be approached with caution to minimize potential risks.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




