Written by: Beosin
On September 23, UXLINK was attacked due to the leakage of the multi-signature wallet private key. The attacker minted UXLINK tokens and sold them, profiting over $11.3 million. The Beosin security team conducted a vulnerability analysis and fund tracking of this attack incident, and the results are shared as follows:
Incident Review
The UXLINK project contract was compromised due to the private key leak, leading to the attacker's address being added as a multi-signature account for the contract while removing the original multi-signature accounts. The contract's signature threshold was reset to 1, allowing the attacker’s address to execute contract operations with a single signature, thus achieving complete control over the contract. Subsequently, the attacker began to mint additional UXLINK tokens and sell them for profit.
The attacker minted tokens 5 times, and three addresses receiving the tokens—0xeff9cefdedb2a34b9e9e371bda0bf8db8b7eb9a7, 0x2ef43c1d0c88c071d242b6c2d0430e1751607b87, 0x78786a967ee948aea1ccd3150f973cf07d9864f3—exchanged UXLINK tokens for ETH and DAI through swaps, transfers, and cross-chain transactions, storing them on ETH chain addresses.
Tracking of Stolen Funds
Below is the analysis by the Beosin security team regarding the main flow of funds in this security incident:
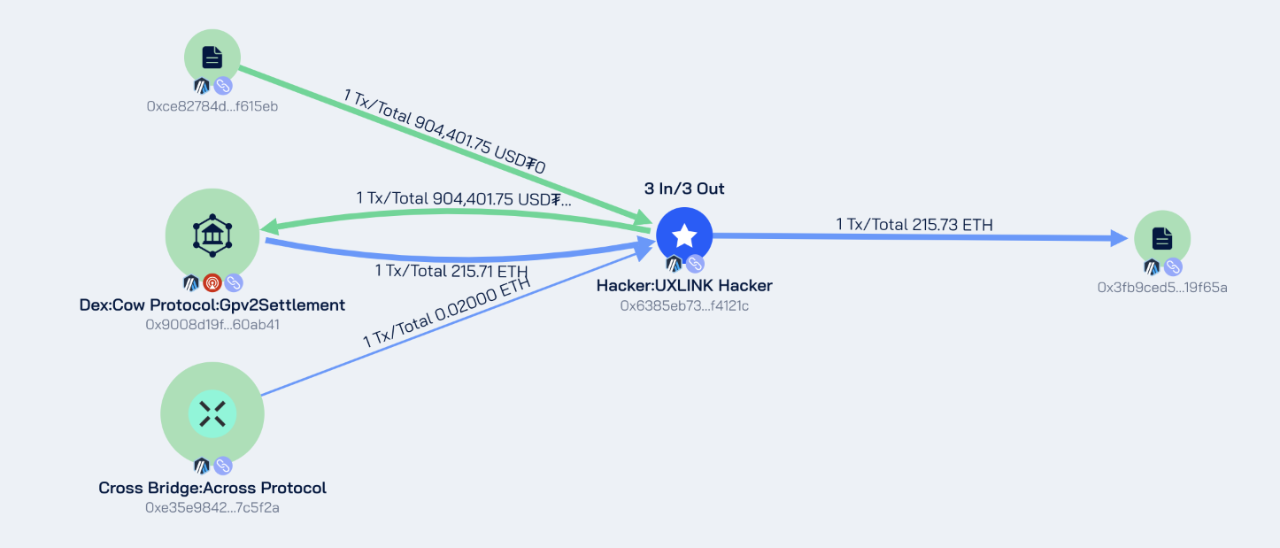
ARBITRUM Chain
Hacker Address: 0x6385eb73fae34bf90ed4c3d4c8afbc957ff4121c
Stolen Address: 0xCe82784d2E6C838c9b390A14a79B70d644F615EB
Amount Stolen: Approximately 904,401 USDT
After stealing the funds, the hacker exchanged 904,401 USDT for 215.71 ETH and transferred the ETH to the Ethereum address 0x6385eb73fae34bf90ed4c3d4c8afbc957ff4121c via cross-chain.
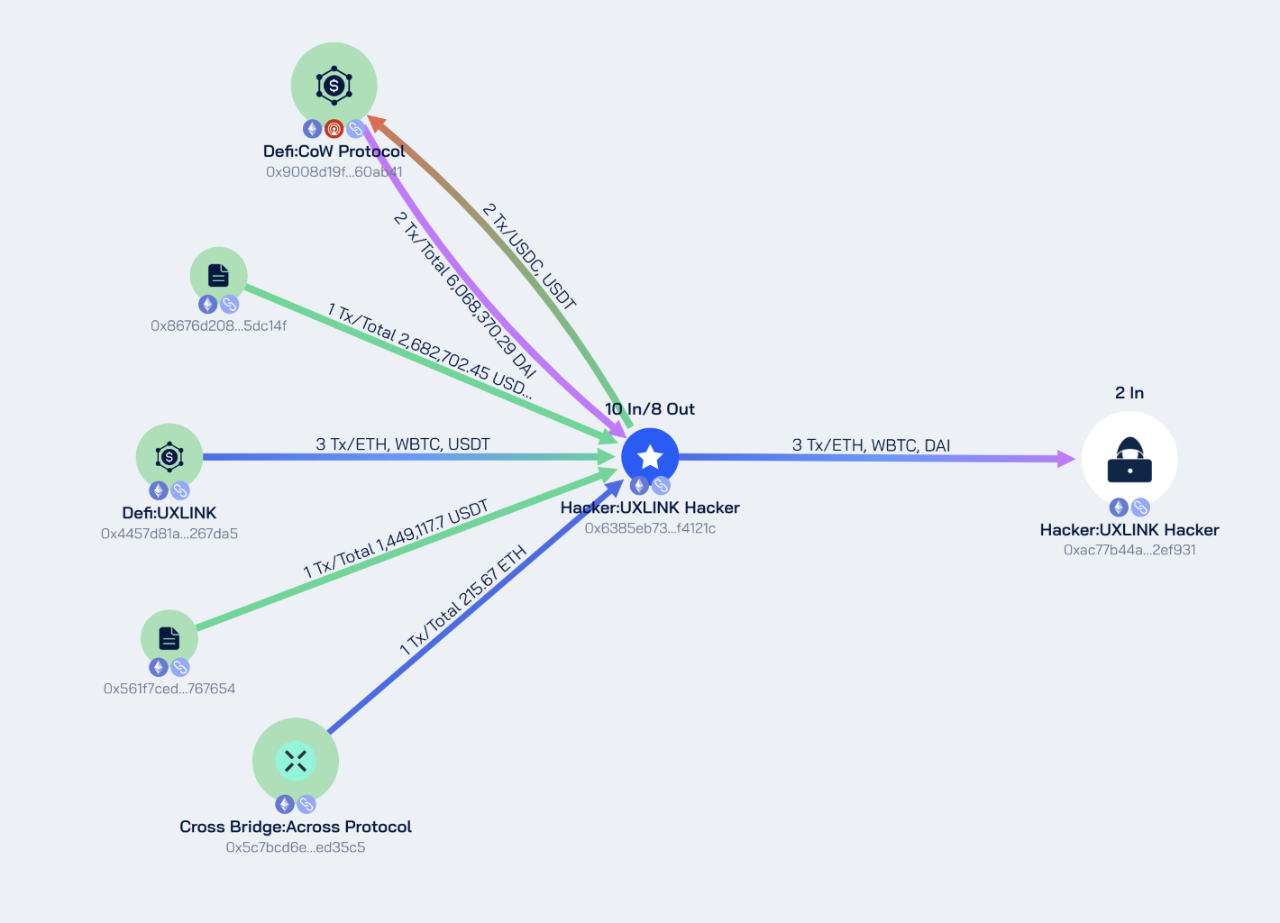
Ethereum Chain
Hacker Address: 0x6385eb73fae34bf90ed4c3d4c8afbc957ff4121c
Stolen Addresses: 0x4457d81a97ab6074468da95f4c0c452924267da5, 0x8676d208484899f5448ad6e8b19792d21e5dc14f, 0x561f7ced7e85c597ad712db4d73e796a4f767654
Amount Stolen: Approximately 25.27 ETH, 5,564,402.99 USDT, 3.7 WBTC, 500,000 USDC
After stealing the funds, the hacker exchanged 5,564,402.99 USDT and 500,000 USDC for 6,068,370.29 DAI, ultimately consolidating the funds to the address 0xac77b44a5f3acc54e3844a609fffd64f182ef931, which currently has a balance of: 240.99 ETH, 6,068,370.29 DAI, 3.7 WBTC.
The main flow of funds between Ethereum and Arbitrum is shown in the diagram below:
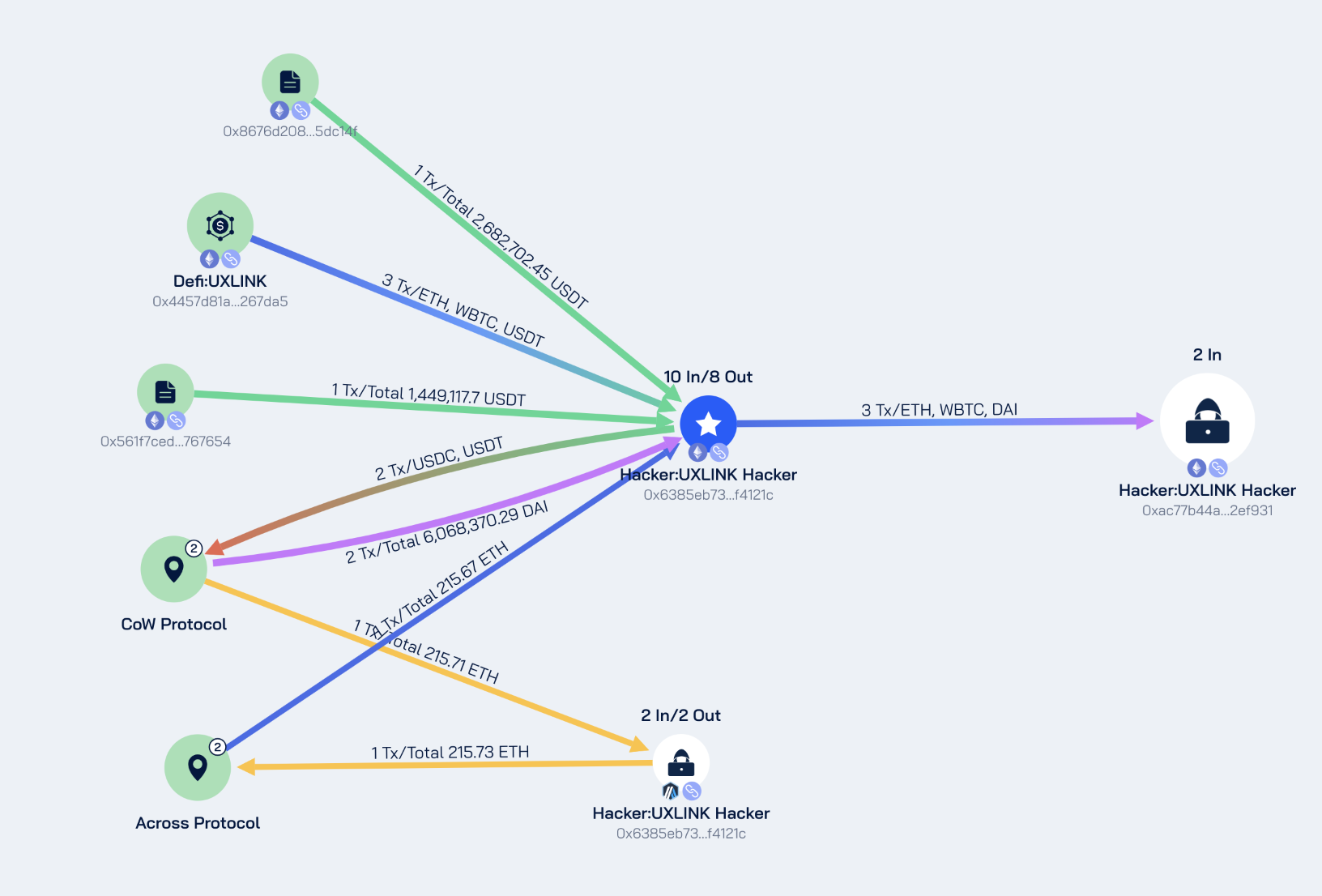
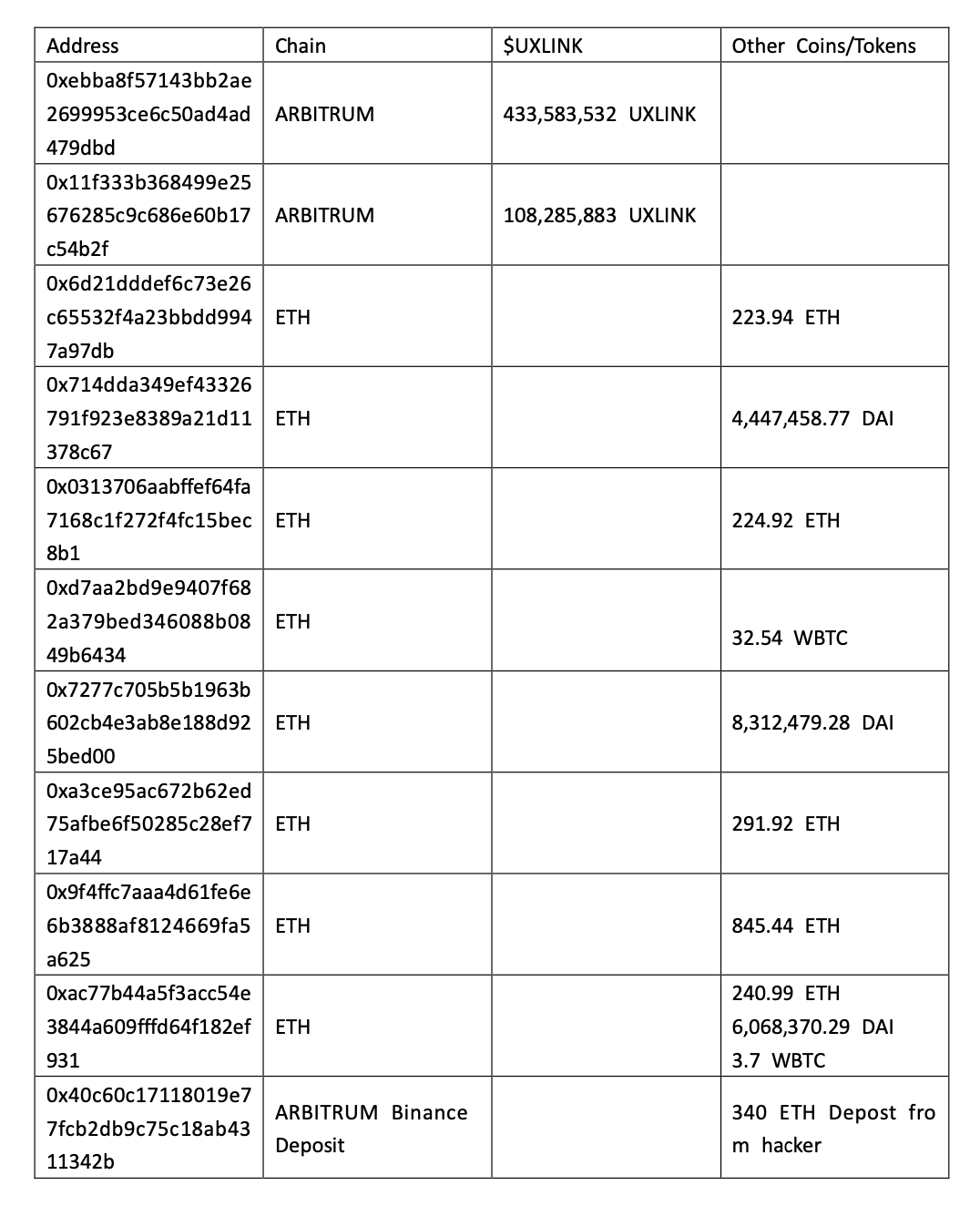
According to Beosin Trace analysis, all stolen funds are still held in multiple addresses of the attacker.
Beosin Trace has blacklisted all addresses related to the attacker and continues to track them. Below is the current balance situation of the addresses related to the attacker:
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



