A mature "hunting chain" has quietly taken shape, and the improvement of verification mechanisms by manufacturers and the security awareness of users urgently need to be closed-loop.
Written by: Web3 Farmer Frank
Imagine you are a patient Holder who has endured a long bear market and finally transferred the BTC you painstakingly accumulated from a CEX to a newly purchased hardware wallet, feeling the peace of mind that your assets are firmly in your own hands.
Two hours later, you open the app, and the wallet is empty.
This is not a hypothetical scenario but a real event that just occurred: an investor bought a hardware wallet on JD.com and deposited 4.35 BTC, unaware that the device had already been pre-initialized by scammers, generating a mnemonic phrase and inserting a fake manual to guide users through a trap process linking to a mobile app.
In other words, the moment the user activates the wallet, it already belongs to the hacker.

Unfortunately, this is not an isolated case. Recently, there have been multiple incidents of users purchasing hardware wallets on platforms like Douyin, JD.com, and Amazon, leading to scams and even total asset loss. If we carefully analyze recent similar security incidents, we will find a maturely operating "hunting chain" surrounding the sales of hardware wallets quietly taking shape.
1. The "second-hand" gray chain targeting novices
As devices that generate private keys in a "completely offline environment," hardware wallets theoretically offer a nearly top-level security level as long as the mnemonic phrase is properly backed up. This is the common knowledge most Web3 players encounter daily.
However, the risks in reality often do not lie in the device itself but in the purchasing and activation stages.
Under long-term promotion, many investors easily form a simple cognitive formula: "hardware wallet = absolute security." This psychological suggestion leads many to overlook several key preconditions once they receive the device:
Is the device packaging intact? Is the seal abnormal? Must the mnemonic phrase be generated by oneself? Is the activation information verified as "first use"? As a result, many users, upon receiving the hardware wallet, eagerly transfer their assets, unknowingly giving scammers an opportunity.
Whether it was the previous incident where 50 million in crypto assets were drained after purchasing a hardware wallet on Douyin or the latest case of BTC being wiped out after buying an imKey hardware wallet on JD.com, without exception, all issues arose during the purchasing and activation stages.
The sale of hardware wallets on domestic e-commerce platforms has revealed a mature gray industrial chain.
Logically, since the domestic stance on cryptocurrencies has always been strict, e-commerce platforms banned the direct sale of cryptocurrencies as early as 2014. Furthermore, the announcement issued by the People's Bank of China and seven ministries on September 4, 2017, explicitly required domestic platforms not to provide services related to cryptocurrency trading, exchange, pricing, or intermediaries.
From a literal perspective, "intermediary services" is broad enough, and tools like hardware wallets that store private keys theoretically fall into a gray area of prohibition. Therefore, platforms like Taobao, JD.com, and Pinduoduo have never supported searches for any "currency-related" keywords.
But the reality is quite the opposite.
As of July 29, I conducted direct keyword searches for five hardware wallet products: Ledger, Trezor, SafePal, OneKey, and imKey (imToken) on Taobao, JD.com, Pinduoduo, and Douyin, and found that buying and selling channels are quite smooth.
Among them, Douyin has the most comprehensive offerings, with stores selling Ledger, Trezor, SafePal, OneKey, and imKey.
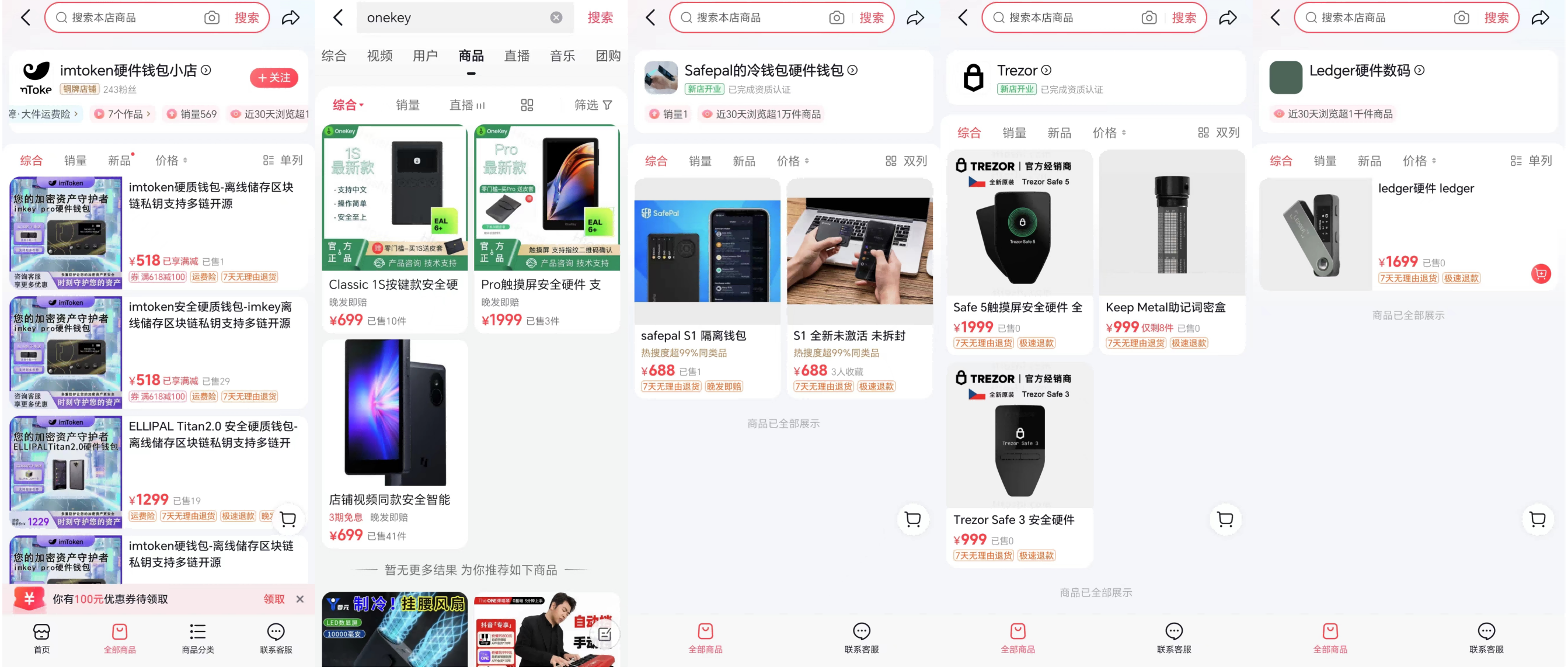
Next is JD.com, where hardware wallet products for Ledger, Trezor, SafePal, and OneKey can be found, while imKey-related stores have likely been taken down due to security incidents.
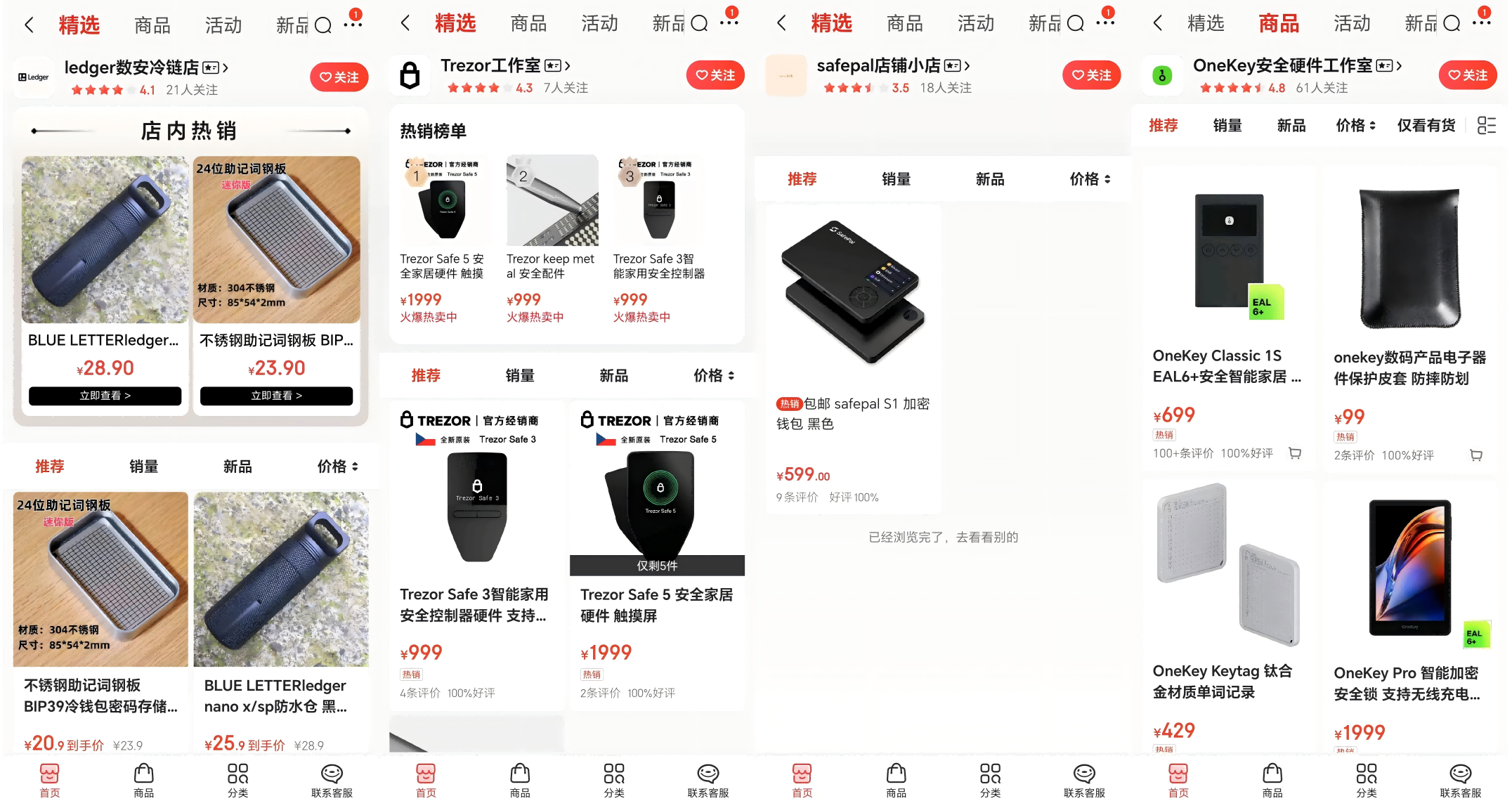
Taobao is relatively stricter, with only one store selling imKey found, while Xiaohongshu does not have direct store searches, but second-hand sales and purchasing posts are everywhere.
Undoubtedly, except for a very few agents, most stores are small retailers from unofficial channels, lacking brand authorization and unable to guarantee the safety of the device circulation process.
Objectively speaking, the agency/distribution system for hardware wallets exists globally, including brands like SafePal, OneKey, and imKey, which are relatively popular in the Chinese-speaking region, with a similar sales system:
Official direct purchase: Orders can be placed on the official website for various models of hardware wallets;
E-commerce channels: Typically paired with WeChat stores like Youzan in China, and relying on official platforms like Amazon overseas;
Regional distributors: Authorized agents in various countries/regions provide localized purchasing channels and can verify authenticity on the official website, such as SafePal providing a global agent query page on its website;
However, in the domestic e-commerce ecosystem, the vast majority of users still purchase through unofficial, unverifiable channels, providing a natural breeding ground for the gray industry's "pre-set mnemonic phrase trap."
Many of these devices may be "second-hand/third-hand" or even "counterfeit devices," and it cannot be ruled out that some devices are unsealed, initialized, and pre-set with mnemonic phrases during the resale process. Once users activate the device, their assets naturally go directly into the scammers' wallets.
Therefore, the key question is, outside of the sales end, can users verify and protect against risks for the hardware devices they purchase to ensure all related risks are eliminated?
2. User-side loopholes and "self-verification" mechanisms
In simple terms, the reason these hardware wallet traps are repeatedly successful is not due to technical flaws in the devices themselves, but rather the entire circulation and usage process exposes multiple exploitable vulnerabilities.
From the perspective of the domestic e-commerce and distributor circulation chain, the main risks are concentrated in two areas:
Second-hand or multi-hand circulation devices: The gray industry may unseal, initialize, and pre-set mnemonic phrases or accounts during the second-hand device or circulation process. Once users directly use that device, their assets will be directed into the scammers' wallets.
Counterfeit or tampered devices: Non-official channels may circulate counterfeit devices, or even directly embed backdoors, putting users at risk of losing their entire assets after transferring them;
For Degen users who are already familiar with hardware wallets, these traps are almost harmless because they naturally perform security verification during the purchasing, initialization, and binding processes. However, for first-time buyers or inexperienced hardware wallet novices, the probability of falling into traps skyrockets.
In the latest security incident, the scammers had pre-created the wallet and specifically set up a fake paper manual to guide purchasing users to unseal and activate this second-hand imKey using a fake process, thereby directly transferring the assets. According to my communication with relevant industry professionals, it has indeed been noted that cases of unsealed products being sold with fake manuals have started to appear more frequently.
After all, many novice users often overlook product integrity (whether the packaging is unsealed, whether the anti-counterfeit sticker is damaged) and easily miss comparing the item list inside the packaging. They also may not know that "new/old" verification can be completed within the official app. If this information is correctly verified, most traps can be identified at the first moment.
It can be said that whether the product design of hardware wallets can comprehensively cover and actively support users in self-verification is the most critical gateway to breaking the gray industry's attack chain.
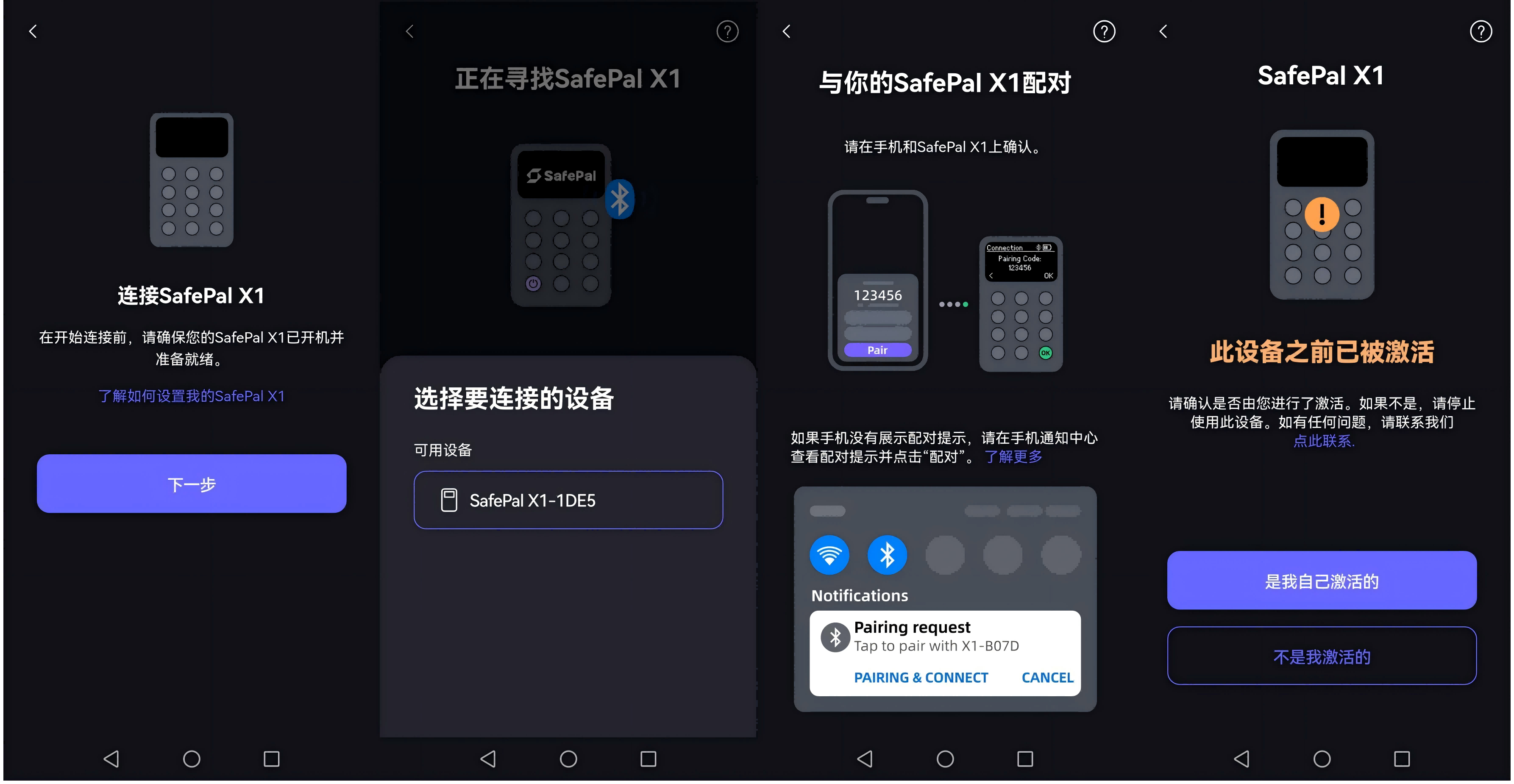
Taking SafePal's Bluetooth X1 hardware wallet as an example, it has a relatively complete self-verification path for users:
First binding reminder: When activating the hardware wallet and binding the app, it prompts, "This device has been activated, is this your operation?";
Display of historical activation information: Subsequently, the SafePal interface will also display the device's first activation time and whether it is the first binding with this phone, helping users quickly determine whether the device is new or has been initialized by someone else;
In addition, based on my actual usage experience, whether using the QR code interaction mechanism of SafePal S1, S1 Pro, or the Bluetooth information interaction of SafePal X1, they allow users to view the corresponding hardware wallet's SN code and historical activation time at any time after binding the SafePal app (as shown below) to further confirm the device's source and usage status.
This is thanks to SafePal's hardware wallets, which write an SN to each device at the factory and bind the hardware fingerprint information of this hardware device with this SN, saving it in the SafePal backend to further confirm the device's source and usage status.
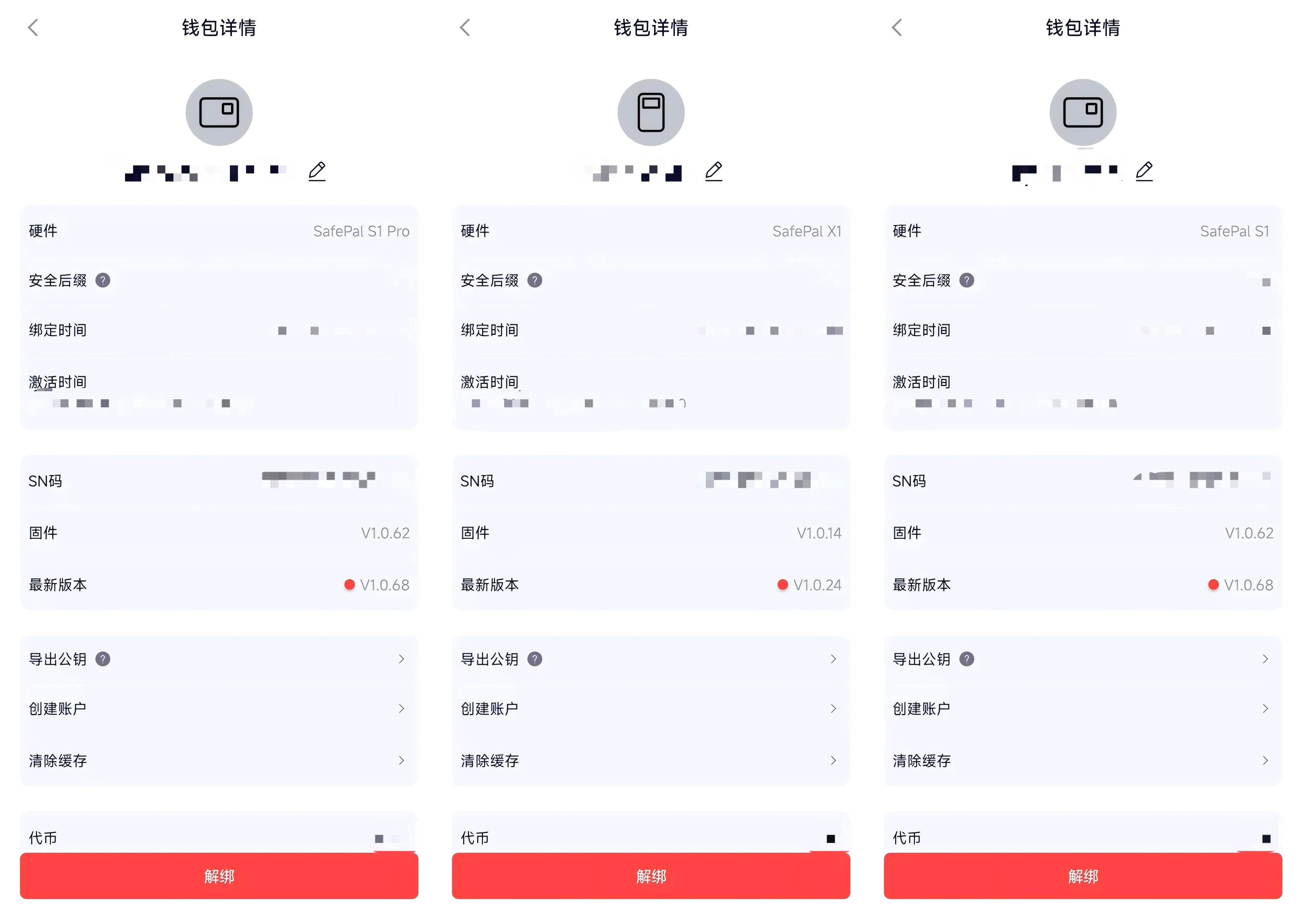
This means that when users first use this hardware wallet, they need to activate it to create a wallet. During activation, the mobile app will return the connected hardware wallet's SN and fingerprint information to the SafePal backend for verification. Only if both match will the user be prompted that the hardware wallet can continue to be used, and the activation time will be recorded.
When other mobile devices bind this hardware wallet again, it will also prompt the user that this hardware has already been activated and is not the first use, requiring the user to confirm again.
Through these verification steps, users can almost identify second-hand traps or counterfeit devices at the first contact with the device, thereby cutting off the common first step of the gray industry's attack chain.
For novice users using hardware wallets for the first time, SafePal's visual and traceable verification mechanism is easier to understand and execute than simple usage instructions or text warnings, and it better meets the actual needs for fraud prevention.
3. A "full-process" security manual for hardware wallets
Overall, for users who are first encountering hardware wallets, it does not mean that simply buying a hardware wallet guarantees asset security.
On the contrary, the security of hardware wallets is not achieved through a one-time purchase but is built upon a defense line constructed by the security awareness in the three stages of purchasing, activating, and using. Any negligence in one of these stages can become an opportunity for attackers.
1. Purchasing Stage: Only Recognize Official Channels
The security chain of hardware wallets begins with the choice of purchasing channels, so it is recommended that everyone purchase directly from the official website.
Once you choose to place an order on e-commerce platforms or live streaming rooms, or purchase from second-hand platforms, such as through Taobao, JD.com, Douyin, and other unofficial channels, it means exposing yourself to extremely high risks—no cold wallet brand will sell products through Douyin live broadcasts or Kuaishou links; these channels are almost all the main battlegrounds of the gray industry.
The first step after receiving the product is to check the packaging and anti-counterfeiting labels. If the packaging is unsealed, the anti-counterfeiting sticker is damaged, or the inner packaging is abnormal, you should immediately raise your vigilance. It is best to verify the items in the packaging against the list published on the official website to quickly eliminate some risks.
The more carefully this stage is handled, the lower the subsequent security costs will be.
2. Activation Stage: Not Initializing is "Giving Away Money"
Activation is the core stage of hardware wallet security and is also the phase where the gray industry is most likely to set traps.
A common tactic is for the gray industry to unseal the device in advance, create a wallet, write in the mnemonic phrase, and then insert a forged manual to guide users to directly use this ready-made wallet, ultimately draining the assets transferred later. The recent JD.com imKey scam incident is an example of this.
Therefore, the primary principle of the activation stage is to self-initialize and generate a new mnemonic phrase. During this process, products that can perform self-checks on device status and verify historical activation can significantly reduce the risk of users being passively exposed. For example, as mentioned earlier, SafePal prompts whether the device has been activated during the first binding and displays historical activation time and binding information, allowing users to identify abnormal devices at the first moment, thereby cutting off the attack chain.
3. Usage Stage: Protect the Mnemonic Phrase and Maintain Physical Isolation
Once in daily use, the core of hardware wallet security is mnemonic phrase management and physical isolation.
The mnemonic phrase must be handwritten and saved; do not take photos, screenshots, or store it through WeChat, email, or cloud storage, as any online storage behavior is equivalent to actively exposing the attack surface.
When signing or transacting, Bluetooth or USB connections should be used briefly and as needed, prioritizing QR code signing or offline data transfer to avoid long-term physical contact with network environments.
It can be said that the security of hardware wallets has never been "foolproof just by buying," but is a defense line constructed by users in the three major stages of purchasing, activating, and using:
Eliminate second-hand and unofficial channels in the purchasing stage;
Self-initialize and verify device status in the activation stage;
Protect the mnemonic phrase and avoid long-term online exposure in the usage stage;
From this perspective, hardware wallet manufacturers urgently need to provide a verifiable "full-process" mechanism design for users, similar to SafePal, which offers prompts during the first activation, displays activation dates, and binding information. Only then will the hunting chain that the gray industry relies on truly become ineffective.
In Conclusion
Hardware wallets are a good tool, but they have never been an ultimate amulet that allows for complete peace of mind.
On one hand, major hardware wallet manufacturers need to timely perceive changes in the market environment, especially regarding the "hunting chain" that novice users are likely to encounter. They should build more intuitive and easy-to-operate verification mechanisms into product design and usage processes, allowing every user to easily determine the authenticity and security status of the device in their hands.
On the other hand, users themselves must also develop good security habits. From purchasing through official channels to initializing and activating, and then to daily management of the mnemonic phrase, every step is essential, fostering a security awareness that spans the entire usage cycle.
Only when the wallet's verification mechanism and the user's security awareness form a closed loop can hardware wallets move closer to the goal of "absolute security."
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




