This article is jointly published by Aquarius Capital and Klein Labs, with special thanks to ecological projects such as NAVI Protocol and Bucket Protocol for their technical guidance and support during the research process, as well as Comma3 Ventures.
TL;DR
1. The Cetus vulnerability originates from contract implementation, not from SUI or the Move language itself.
The root of this attack lies in the lack of boundary checks in the arithmetic functions of the Cetus protocol—logical vulnerabilities caused by overly broad masking and bit shift overflow, unrelated to the resource security model of the SUI chain or the Move language. The vulnerability can be fixed with "a single line of boundary check" and does not affect the core security of the entire ecosystem.
2. The value of "reasonable centralization" in the SUI mechanism is revealed in times of crisis.
Although SUI exhibits slight centralization tendencies with features like DPoS validator rounds and blacklist freezing, this proved useful in the response to the CETUS incident: validators quickly synchronized malicious addresses to the Deny List and refused to package related transactions, resulting in the immediate freezing of over $160 million in funds. This is essentially a positive form of "on-chain Keynesianism," where effective macro-control plays a beneficial role in the economic system.
3. Reflections and suggestions on technical security.
Mathematics and boundary checks: Introduce upper and lower limit assertions for all critical arithmetic operations (such as shifts, multiplications, and divisions), and conduct extreme value fuzzing and formal verification. Additionally, enhance auditing and monitoring: beyond general code audits, include specialized mathematical audit teams and real-time on-chain transaction behavior detection to capture abnormal splits or large flash loans early.
4. Summary and suggestions for funding security mechanisms.
In the Cetus incident, SUI and the project team efficiently collaborated to successfully freeze over $160 million in funds and promote a 100% compensation plan, demonstrating strong on-chain resilience and ecological responsibility. The SUI Foundation also added $10 million in audit funding to strengthen security defenses. In the future, further advancements could be made in on-chain tracking systems, community-built security tools, and decentralized insurance mechanisms to improve the funding security system.
5. The diverse expansion of the SUI ecosystem.
In less than two years, SUI has rapidly transitioned from a "new chain" to a "strong ecosystem," building a diversified ecological landscape that includes stablecoins, DEX, infrastructure, DePIN, games, and more. The total scale of stablecoins has surpassed $1 billion, providing a solid liquidity foundation for DeFi modules; TVL ranks 8th globally, with trading activity ranking 5th globally and 3rd among non-EVM networks (only behind Bitcoin and Solana), demonstrating strong user participation and asset retention capabilities.
1. A chain reaction triggered by a single attack
On May 22, 2025, the leading AMM protocol Cetus deployed on the SUI network was attacked by hackers who exploited a logical vulnerability related to the "integer overflow issue," initiating precise manipulation that resulted in losses exceeding $200 million in assets. This incident is not only one of the largest security incidents in the DeFi space this year but also the most destructive hacker attack since the launch of the SUI mainnet.
According to DefiLlama data, the total TVL across the SUI chain plummeted by over $330 million on the day of the attack, with the locked amount in the Cetus protocol evaporating by 84% in an instant, dropping to $38 million. As a result, several popular tokens on SUI (including Lofi, Sudeng, Squirtle, etc.) plummeted by 76% to 97% within just one hour, raising widespread concerns about the security and stability of the SUI ecosystem.
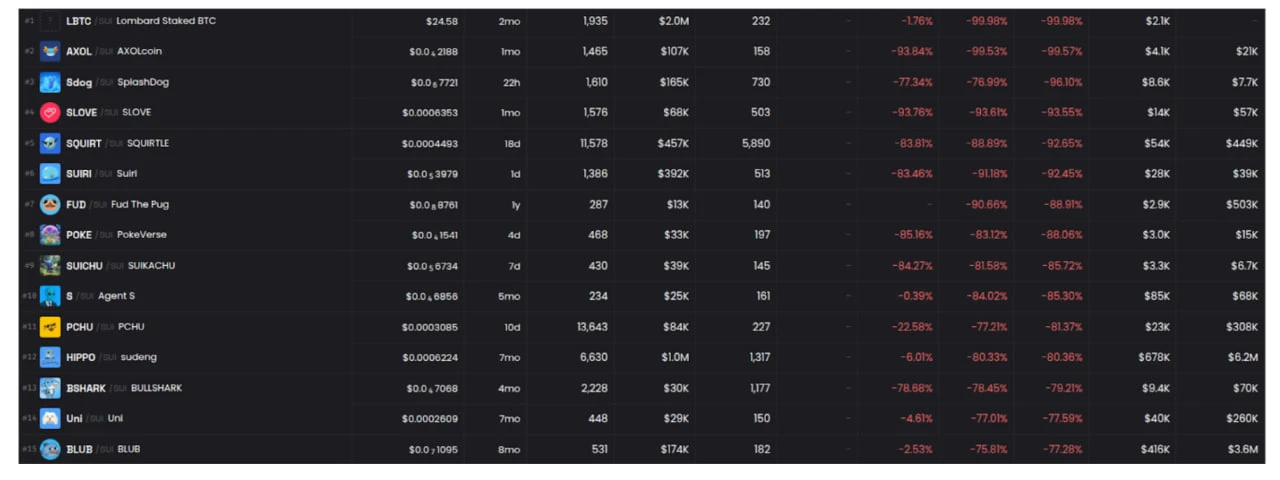
However, in the aftermath of this shockwave, the SUI ecosystem demonstrated strong resilience and recovery capabilities. Despite the short-term confidence fluctuations caused by the Cetus incident, on-chain funds and user activity did not experience sustained decline; instead, it significantly heightened the entire ecosystem's focus on security, infrastructure development, and project quality.
Klein Labs will analyze the causes of this attack, the SUI node consensus mechanism, the security of the MOVE language, and the ecological development of SUI, outlining the current ecological landscape of this public chain still in its early development stage and exploring its future development potential.
2. Analysis of the causes of the Cetus incident attack
2.1 Attack Implementation Process
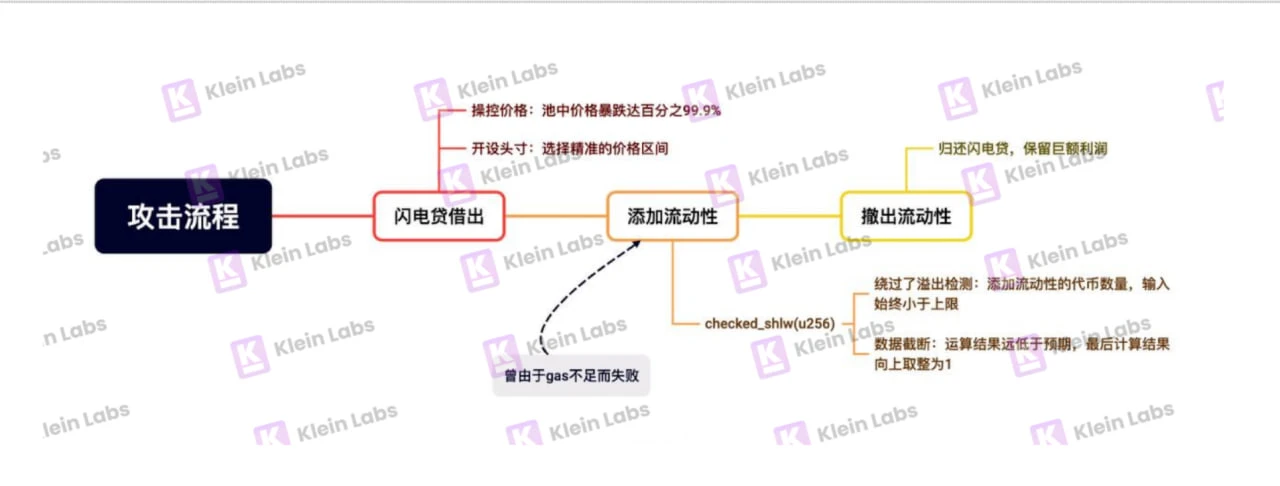
According to the technical analysis of the Cetus attack by the Slow Mist team, the hacker successfully exploited a critical arithmetic overflow vulnerability in the protocol, using flash loans, precise price manipulation, and contract defects to steal over $200 million in digital assets in a short period. The attack path can be roughly divided into the following three stages:
- Initiate a flash loan and manipulate prices.
The hacker first utilized a maximum slippage flash loan of 10 billion haSUI, borrowing a large amount of funds to manipulate prices.
Flash loans allow users to borrow and repay funds within the same transaction, requiring only a fee, characterized by high leverage, low risk, and low cost. The hacker used this mechanism to lower the market price in a short time and precisely control it within a very narrow range.
Subsequently, the attacker prepared to create an extremely narrow liquidity position, setting the price range precisely between the lowest quote of 300,000 and the highest price of 300,200, with a price width of only 1.00496621%.
Through this method, the hacker successfully manipulated the haSUI price using a sufficiently large number of tokens and massive liquidity. They then targeted several tokens with no actual value for manipulation.
- Add liquidity.
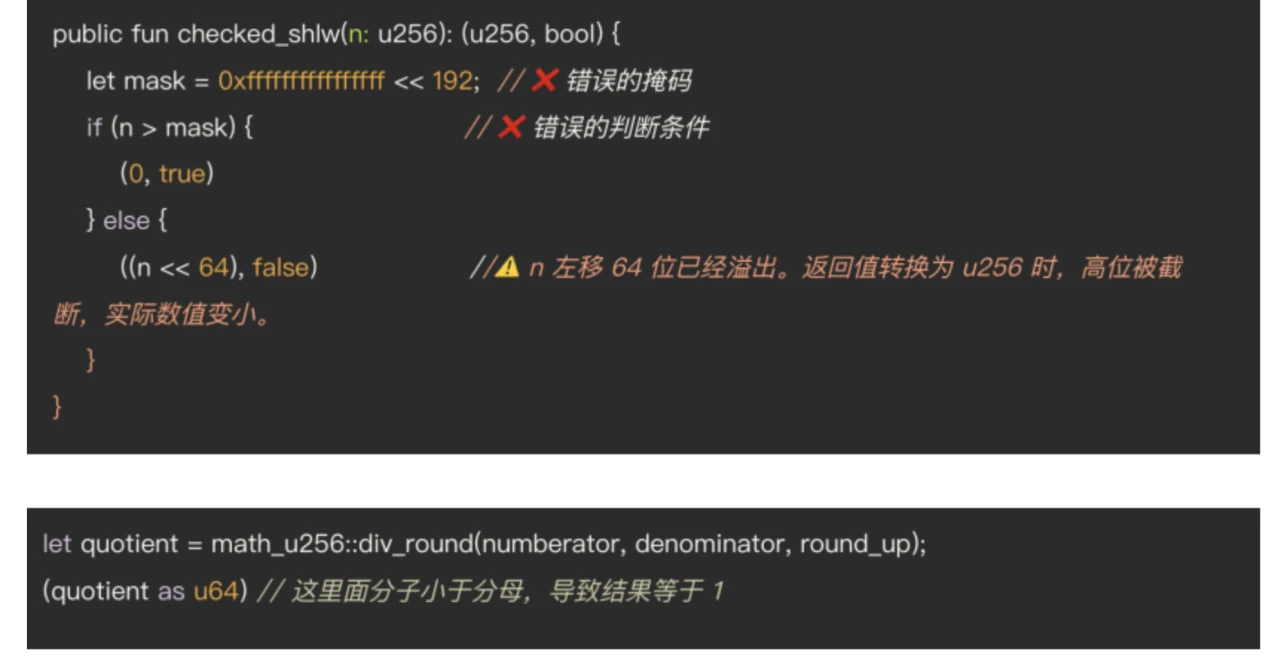
The attacker created a narrow liquidity position, declared adding liquidity, but due to a vulnerability in the checked_shlw function, ultimately only received 1 token.
This was essentially due to two reasons:
Overly broad masking: equivalent to a very large liquidity addition limit, rendering the contract's user input validation ineffective. The hacker bypassed the overflow detection by setting abnormal parameters, constructing inputs that were always less than this limit.
Data overflow was truncated: when performing a shift operation on the value n by n 64, the shift exceeded the effective bit width of the uint256 data type (256 bits), resulting in data truncation. The high-order overflow part was automatically discarded, causing the computation result to be far lower than expected, leading the system to underestimate the amount of haSUI required for the exchange. The final calculation result was approximately less than 1, but due to rounding up, it ended up equaling 1, meaning the hacker only needed to add 1 token to exchange for massive liquidity.
Withdraw liquidity.
Repay the flash loan while retaining massive profits. Ultimately, the hacker withdrew token assets worth hundreds of millions of dollars from multiple liquidity pools.
The funding loss was severe, with the attack resulting in the following stolen assets:
- 12.9 million SUI (approximately $54 million)
- $60 million USDC
- $4.9 million Haedal Staked SUI
- $19.5 million TOILET
- Other tokens like HIPPO and LOFI dropped 75-80%, leading to liquidity exhaustion.
2.2 Causes and Characteristics of the Vulnerability
The vulnerability in Cetus has three characteristics:
- Extremely low repair cost.
On one hand, the root cause of the Cetus incident is a flaw in the Cetus math library, not an error in the protocol's pricing mechanism or underlying architecture. On the other hand, the vulnerability is limited to Cetus itself and is unrelated to SUI's code. The root of the vulnerability lies in a boundary condition check, and only two lines of code need to be modified to completely eliminate the risk; once repaired, it can be immediately deployed to the mainnet to ensure the subsequent contract logic is complete and eliminate this vulnerability.
- High concealment.
The contract has been running smoothly for two years without any faults, and the Cetus Protocol has undergone multiple audits, but the vulnerability was not discovered, mainly because the Integer_Mate library used for mathematical calculations was not included in the audit scope.
The hacker precisely constructed the trading range using extreme values, creating a rare scenario of submitting extremely high liquidity, which triggered the abnormal logic, indicating that such issues are difficult to detect through ordinary testing. These types of problems often lie in blind spots in people's vision, which is why they remain hidden for a long time before being discovered.
- Not unique to Move.
Move excels over many smart contract languages in resource security and type checking, with built-in native detection for integer overflow issues in common scenarios. This overflow occurred because, when adding liquidity, the wrong value was first used for the upper limit check when calculating the required number of tokens, and a shift operation was used instead of conventional multiplication. If conventional addition, subtraction, multiplication, or division were used in Move, overflow checks would be performed automatically, preventing such high-order truncation issues.
Similar vulnerabilities have also appeared in other languages (such as Solidity and Rust), and they are even more easily exploited due to their lack of integer overflow protection; before updates to Solidity, overflow checks were very weak. Historically, there have been addition overflows, subtraction overflows, multiplication overflows, etc., with the direct cause being that the computation result exceeded the range. For example, vulnerabilities in Solidity language's BEC and SMT smart contracts were exploited by carefully constructed parameters that bypassed detection statements in the contract, resulting in excessive transfers.
3. SUI's Consensus Mechanism
3.1 Introduction to SUI's Consensus Mechanism
SUI Official Medium
Overview:
SUI adopts a Delegated Proof of Stake (DPoS) framework. While the DPoS mechanism can improve transaction throughput, it cannot provide the high level of decentralization that Proof of Work (PoW) offers. Therefore, SUI's level of decentralization is relatively low, and the governance threshold is relatively high, making it difficult for ordinary users to directly influence network governance.
- Average number of validators: 106
- Average Epoch cycle: 24 hours
Mechanism Process:
- Stake Delegation: Ordinary users do not need to run nodes themselves; they can participate in network security assurance and reward distribution by staking SUI and delegating it to candidate validators. This mechanism lowers the participation threshold for ordinary users, allowing them to engage in network consensus by "hiring" trusted validators. This is a significant advantage of DPoS compared to traditional PoS.
- Representative Block Production: A small number of selected validators produce blocks in a fixed or random order, enhancing confirmation speed and increasing TPS.
- Dynamic Election: At the end of each voting cycle, a dynamic rotation occurs based on voting weight, re-electing the Validator set to ensure node vitality, interest consistency, and decentralization.
Advantages of DPoS:
- High Efficiency: With a controllable number of block-producing nodes, the network can achieve confirmation in milliseconds, meeting high TPS demands.
- Low Cost: Fewer nodes participating in consensus significantly reduce the network bandwidth and computational resources required for information synchronization and signature aggregation. This leads to lower hardware and operational costs, reducing the requirements for computing power and ultimately resulting in lower user transaction fees.
- High Security: The staking and delegation mechanism amplifies the cost and risk of attacks; combined with on-chain penalty mechanisms, it effectively suppresses malicious behavior.
Additionally, SUI's consensus mechanism employs a Byzantine Fault Tolerance (BFT)-based algorithm, requiring more than two-thirds of validators to reach consensus to confirm transactions. This mechanism ensures that even if a minority of nodes act maliciously, the network can maintain secure and efficient operation. Any upgrades or major decisions also require more than two-thirds of the votes to be implemented.
Essentially, DPoS is a compromise of the impossible triangle, balancing decentralization and efficiency. In the security-decentralization-scalability "impossible triangle," DPoS chooses to reduce the number of active block-producing nodes in exchange for higher performance, sacrificing a certain degree of complete decentralization compared to pure PoS or PoW, but significantly enhancing network throughput and transaction speed.
3.2 SUI's Performance in This Attack
3.2.1 Operation of the Freezing Mechanism
In this incident, SUI quickly froze the addresses related to the attacker.
From a code perspective, this prevents transfer transactions from being packaged on-chain. Validator nodes are the core components of the SUI blockchain, responsible for validating transactions and executing protocol rules. By collectively ignoring transactions related to the attacker, these validators effectively implemented a mechanism similar to "account freezing" in traditional finance at the consensus level.
SUI itself has a built-in deny list mechanism, which is a blacklist feature that can block any transactions involving listed addresses. Since this feature exists in the client, SUI was able to immediately freeze the hacker's address when the attack occurred. Without this feature, even with only 113 validators, it would be difficult for Cetus to coordinate all validators to respond individually in a short time.
3.2.2 Who Has the Authority to Change the Blacklist?
TransactionDenyConfig is a YAML/TOML configuration file loaded locally by each validator. Anyone running a node can edit this file, hot reload, or restart the node to update the list. On the surface, it seems that each validator is freely expressing their values.
In reality, for the consistency and effectiveness of security policies, updates to this critical configuration are usually coordinated. Since this is an "emergency update driven by the SUI team," it is essentially the SUI Foundation (or its authorized developers) that sets and updates this deny list.
SUI publishes the blacklist; theoretically, validators can choose whether to adopt it—but in practice, most people default to automatically adopting it. Therefore, while this feature protects user funds, it does indeed have a certain degree of centralization.
3.2.3 The Nature of the Blacklist Function
The blacklist function is not actually a part of the underlying protocol logic; it serves more as an additional layer of security to respond to emergencies and ensure the safety of user funds.
Essentially, it is a security assurance mechanism. Similar to a "security chain" tied to a door, it is activated only against those who wish to intrude, i.e., those who would act maliciously against the protocol. For users:
- For large holders, the main providers of liquidity, the protocol aims to ensure the safety of funds, as the on-chain data TVL is primarily contributed by major holders. For the protocol to develop sustainably, it must prioritize safety.
- For retail investors, contributors to ecological activity and strong supporters of technology and community co-construction, the project team also hopes to attract retail investors to co-build, which is essential for gradually improving the ecosystem and enhancing retention. In the DeFi space, the primary concern remains the safety of funds.
The key to judging "whether it is centralized" should be whether users have control over their assets. In this regard, SUI, through the Move programming language, reflects a natural ownership of user assets:
SUI is built on the Move language, and the core concept of Move can be summarized as "funds follow addresses":
Unlike Solidity, which centers interactions around smart contracts, in Move, user assets are always directly stored under personal addresses, and transaction logic revolves around the transfer of resource ownership. This means that the control of assets naturally belongs to the user, not to contract custody, reducing the risk of losing funds due to contract vulnerabilities or improper permission design, and fundamentally enhancing decentralization attributes.
SUI is also currently working to strengthen decentralization. It is gradually lowering the entry threshold for validators by implementing the SIP-39 proposal. The new proposal adjusts the entry threshold for validators from merely the amount of staked tokens to voting power, thereby increasing ordinary users' participation.
3.3 The Boundaries and Realities of Decentralization: Governance Controversies Triggered by SUI
In the emergency response to this incident, the joint actions of the community and validators sparked intense discussions about the degree of "decentralization":
Some crypto practitioners believe SUI is relatively decentralized:
- SUI community members responded, "Decentralization is not about watching people suffer; it is about allowing everyone to take action without needing anyone's permission."— With huge funds stolen, it is impossible to sit idly by.
- "This is true decentralization in the real world; it is not 'powerless,' but rather 'in alignment with the community and responding.' The core of decentralization is not standing by while people are attacked, but the ability of the community to act collaboratively without permission."
- This is not unique to SUI— from Ethereum to BSC, most PoS chains face similar risks of validator centralization. The SUI case merely highlights the issue further.
Others believe SUI is too centralized:
- For example, Cyber Capital founder Justin Bons bluntly stated, "Are SUI validators colluding to review the hacker's transactions? Does this mean SUI is centralized? The short answer is: yes. But more importantly, why? Because the 'founder' holds most of the supply, and there are only 114 validators!" In contrast, Ethereum has over 1 million validators, while Solana has 1,157.
However, we believe this theory is somewhat one-sided:
- All SUI validators essentially perform the same functions, and dynamic rotation updates the validators, achieving a metabolism that prevents the concentration of power and unequal distribution.
From a macroeconomic theory perspective, due to information asymmetry and the market's incomplete development, moderate and slight centralization is somewhat necessary at the current stage.
Traditional economic theory also recognizes the advantages of centralized models:
- Reducing the risk of information asymmetry: Centralized entities often possess more information, enabling them to assess transaction risks more accurately and effectively avoid adverse selection and moral hazard.
- Responding to market fluctuations: In the face of external shocks or systemic risks, centralized mechanisms can quickly unify decision-making and allocate resources, enhancing market resilience and adaptability.
- Facilitating coordination and cooperation: Centralized institutions help achieve more efficient coordination in multi-party interest games, promoting rational resource allocation and overall efficiency improvement.
Overall, slight and bounded centralization is not a monstrous flood, but rather an effective supplement to the ideal of "decentralization" under real economic conditions. This is a transitional arrangement, and the crypto world will ultimately evolve toward decentralization, which is the consensus of the industry and the ultimate goal of technological and conceptual development. In the context of this incident, such centralization achieved a form of Keynesian macro-control. In economic systems, a completely decentralized market economy can also lead to economic crises; moderate macro-control can guide the economic system toward favorable development.
4. The Technical Moat of the Move Language
In a crypto world where security incidents in smart contracts are frequent, the Move language, with its resource model, type system, and security mechanisms, is gradually becoming an important infrastructure for the next generation of public chains:
1. Clear ownership of funds, natural isolation of permissions
- Move: Assets are "resources," each resource is independent, can only belong to one account, and it must be clear who the "owner" is. Assets strictly belong to the money in the user's wallet, and only the user can manage them, with clear permissions.
- Solidity: User assets are actually controlled by contracts, and developers must write additional control logic to restrict access. If permissions are written incorrectly, it can lead to smart contract failures and arbitrary manipulation of assets.
2. Language-level prevention of reentrancy attacks
- Move: Based on resource ownership and a linear type system, each time a resource is used, it is "emptied" and cannot be called again, naturally shielding against the risk of reentrancy attacks.
- Solidity: "Reentrancy attacks" are one of the most famous attack methods on Ethereum, such as the notorious DAO vulnerability. Solidity has reentrancy attack vulnerabilities, requiring developers to manually defend against them using the "check-effects-interactions" pattern; any oversight can lead to high risks.
3. Automatic memory management and resource ownership tracking
- Move: Based on Rust's linear type and ownership model, all resources can be tracked for their lifecycle at compile time, with the system automatically reclaiming unused variables and prohibiting implicit copying or discarding, eliminating the risks of dangling and double-freeing.
- Solidity: Uses a manually managed stack model for memory, requiring developers to maintain variable lifecycles themselves, which can easily lead to memory leaks, invalid references, or permission abuse, increasing the potential for vulnerabilities and attack surfaces.
4. Structure derived from Rust, stronger security and readability
- More rigorous syntax: Strong type checking at compile time, memory safety, no uninitialized variables, and logical errors can be caught before runtime, reducing online incidents.
- Improved error reporting mechanism: The compiler clearly indicates error locations and types, facilitating development and debugging, and reducing unpredictable behavior.
5. Lower gas costs, higher execution efficiency
The Move language features a streamlined structure and shorter execution paths, with an optimized virtual machine that consumes less Gas per unit of computation. This enhances execution efficiency and reduces user operation costs, making it suitable for high-frequency trading applications such as DeFi and NFT minting.
Overall, the Move language not only significantly outperforms traditional smart contract languages in terms of security and controllability but also fundamentally avoids common attack vectors and logical vulnerabilities through its resource model and type system. The Move language represents a shift in smart contract development from "it just needs to run" to "inherently secure." It provides a solid infrastructure for new public chains like SUI and opens up new possibilities for the technological evolution of the entire crypto industry.
5. Reflections and Suggestions Based on the SUI Attack Incident
Technical advantages do not guarantee infallibility. Even on chains designed with security as a core principle, complex contract interactions and improper handling of boundary conditions can still become vulnerabilities exploited by attackers. The recent security incident on SUI serves as a reminder that, beyond security design, auditing and mathematical verification are equally indispensable. Below, we present targeted suggestions and reflections from the perspectives of development and risk control.
5.1 Hacker Attacks
1. Mathematical boundary conditions must be strictly analyzed
The hacker incident revealed vulnerabilities due to imprecise mathematical boundary conditions. The attacker manipulated liquidity positions within the contract, exploiting erroneous boundary conditions and numerical overflows to bypass the contract's security checks. Therefore, all critical mathematical functions must undergo rigorous analysis to ensure they work correctly under various input conditions.
2. Complex vulnerabilities require professional mathematical auditing
The data overflow and boundary check errors in this incident involved complex mathematical calculations and bitwise operations, which are difficult for conventional audits to capture. Traditional code audits primarily focus on the functionality and security of contracts, while reviewing complex mathematical issues typically requires a more specialized mathematical background. Thus, it is advisable to engage professional mathematical auditing teams to identify and rectify such risks.
3. Raise review standards for previously attacked projects
The hacker's use of flash loan mechanisms for market manipulation underscores that even projects that have previously experienced attacks still face potential risks. If a project has been attacked, its code and contracts need to undergo stricter and more detailed reviews to ensure similar vulnerabilities do not recur. Reviews, especially concerning mathematical processing, data overflow, and logical vulnerabilities, should be more comprehensive.
4. Strict boundary checks for cross-type numerical conversions
The hacker exploited issues such as overly broad mask settings and data overflow truncation, ultimately leading to contract calculation errors and successful price manipulation. All cross-type numerical conversions, such as between integers and floating-point numbers, must undergo strict boundary checks to ensure there is no risk of overflow or loss of precision. Particularly when dealing with large values, stricter handling methods should be adopted.
5. The significant damage caused by "dust attacks"
The hacker manipulated low-value tokens ("dust") for price manipulation, taking advantage of these tokens' low liquidity characteristics, especially during AMM exchanges in the DeFi space, making them easy to manipulate in the market. This operation is not limited to high-value tokens; low-value tokens can also become points of attack. Therefore, project teams need to be aware of the potential threats posed by "dust attacks" and take measures to mitigate such risks.
6. Strengthen real-time monitoring and response capabilities for hacker behavior
Before successfully attacking the protocol, the hacker attempted a similar attack but failed due to potential insufficient Gas. Such large liquidity transactions, even if they fail, should be detected promptly and raise alerts. The platform's monitoring system should be able to trigger risk control mechanisms immediately when such abnormal transactions occur, allowing for early identification of potential threats. By enhancing real-time monitoring of on-chain transaction behavior and combining advanced analytical tools and techniques, the platform can intervene promptly at the onset of issues, preventing further losses.
5.2 On-chain Fund Security Assurance and Emergency Response
5.2.1 SUI's Response Mechanism in Crisis Management
- Interconnected validator nodes promptly block hacker addresses
SUI enhanced the interconnectivity among validator nodes, quickly blocking hacker addresses and minimizing losses.
First, it is essential to understand the basic principles of on-chain fund transfers: every transfer must be signed by a private key to prove ownership of the funds, confirmed for legitimacy by network validators (such as nodes or sorters), and then packaged and broadcasted on-chain by a block, ultimately completing an immutable settlement process.
SUI's blocking of funds is effectively realized at the step of validator confirmation: by adding the hacker's address to a blacklist and synchronously distributing it to all validator nodes, they refuse to package and confirm transactions related to that address, thereby preventing funds from being recorded on-chain and achieving a freezing effect.
Audit subsidies and enhancement of on-chain security
SUI consistently prioritizes on-chain security, providing free auditing services for on-chain projects. It has also provided strong support for the security assurance of the ecosystem. Following the Cetus hacker attack incident, the SUI Foundation announced an additional $10 million in audit funding to strengthen auditing and vulnerability protection, further enhancing on-chain security.Collaborative response between Cetus and SUI
In this security incident, SUI and Cetus demonstrated strong collaborative adaptability and ecological linkage mechanisms. After the anomaly occurred, the Cetus team quickly communicated with SUI validator nodes and, with the support of most validators, successfully froze two wallet addresses belonging to the attacker, locking in a total of over $160 million, which created a critical time window for subsequent asset recovery and compensation.
More importantly, Cetus has officially announced that, in conjunction with its cash and token reserves, and with key support from the SUI Foundation, it will be able to achieve 100% compensation for affected users.
This series of collaborative actions not only reflects SUI's infrastructure flexibility and execution capability in the face of extreme risks but also demonstrates the trust foundation and responsibility consensus among projects within the ecosystem, laying a solid foundation for building a more resilient security ecosystem for SUI DeFi.
5.2.2 Reflections on User Fund Security from the Cetus Hacker Attack Incident
- From a technical perspective, directly recovering on-chain funds is not entirely impossible. Common response methods mainly include two:
Rolling back on-chain operations: essentially "reversing" certain on-chain transactions to restore the state to a point before the attack occurred;
Utilizing multi-signature authority: through multi-party authorization, controlling key wallets to forcibly recover funds from hacker addresses.
However, these practices are generally only activated when the fund volume is very large and the risk is extremely high. While effective, they do have a certain impact on the principle of decentralization and can easily lead to controversy. Therefore, many project teams tend to avoid adopting them unless absolutely necessary, unable to negotiate, or funds cannot be recovered.
In the recent handling case by Cetus and SUI, they did not choose to directly "cut" on-chain data but instead handled it in a more gentle manner—such as freezing transaction requests from malicious addresses at the validator level. This approach, compared to traditional violent methods, respects the spirit of decentralization and reflects a more nuanced security governance capability under the Move ecosystem.
Community co-construction to improve security tracking mechanisms
To enhance the security of the Move ecosystem, community co-construction is key. Currently, the technical foundation of Move is solid, but the number of participants is relatively small, especially in on-chain tracking and security auditing, which remains immature. In contrast, Ethereum has developed a comprehensive on-chain monitoring tool (such as Etherscan) through years of community building. Therefore, more developers and security institutions need to participate in jointly building similar tracking systems to improve the overall transparency and risk resistance of the ecosystem.Introduce insurance compensation to safeguard fund security
Some decentralized projects collaborate with insurance protocols like Nexus Mutual to provide security guarantees for user-staked funds, reducing the risk of losses due to vulnerabilities or attacks.
6. The Continuously Thriving SUI Ecosystem: Growth Beyond DeFi
SUI is undoubtedly in a unique period; although facing some challenges, it still maintains a leading position in terms of TVL, developer activity, and ecosystem development, firmly establishing itself as a leader among Move series public chains. However, some community members still harbor FUD and lack a rational understanding of SUI's technical advantages and ecological potential.
As of now, the TVL of the SUI network is approximately $1.6 billion, with an average daily trading volume of around $300 million on DEX, demonstrating strong capital activity and enthusiasm among on-chain users. Although SUI is still relatively young among mainstream public chains, it ranks among the top in developer activity, with rapid progress in ecosystem construction. Starting from early NFT collections, it now encompasses multiple verticals, including DEX, infrastructure, gaming, and DePIN, with an increasing number of projects choosing to build on SUI, gradually forming a diversified application matrix.
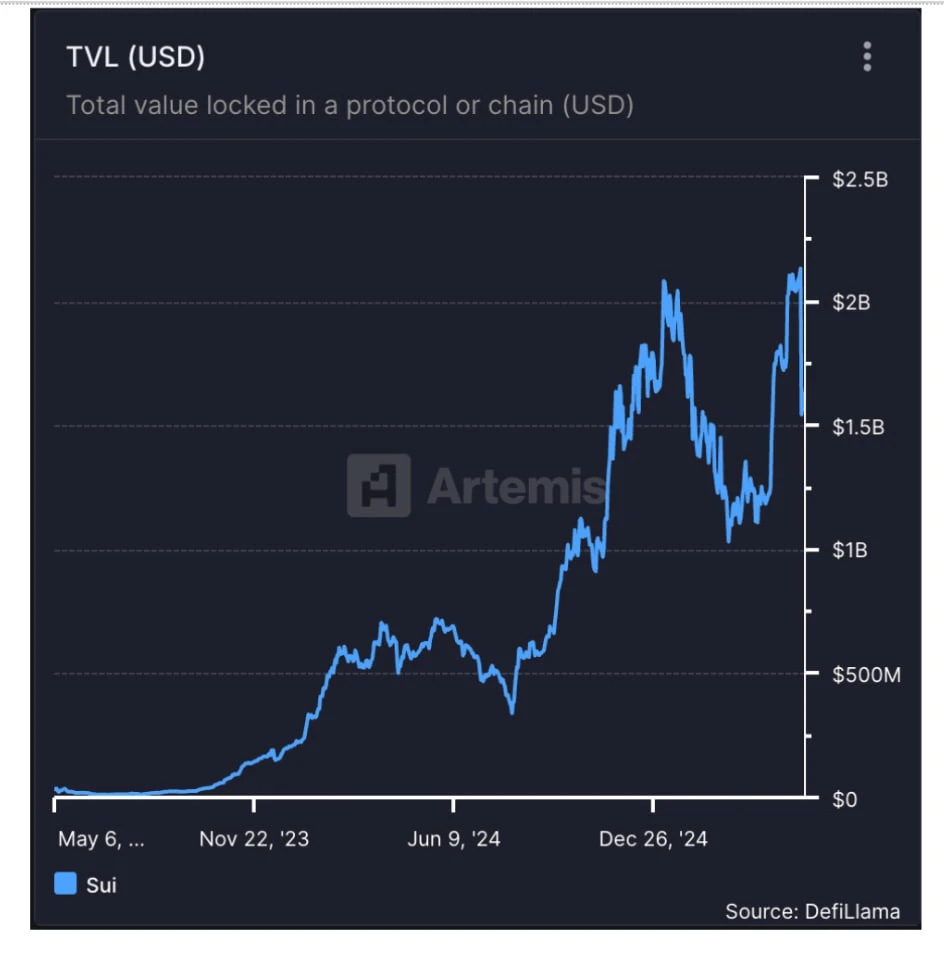
TVL of the SUI ecosystem, DefiLlama
Among them, the rapid development of the stablecoin ecosystem has laid a crucial foundation for SUI's DeFi. According to DefiLlama, the total scale of stablecoins deployed on the SUI chain has surpassed $1 billion, occupying an important proportion of the TVL and becoming a significant source of on-chain liquidity.
This trend is also reflected in the DefiLlama public chain rankings: SUI currently ranks 8th in total TVL across all chains and 3rd among non-EVM chains (only behind Solana and Bitcoin); in terms of on-chain trading activity, SUI ranks 5th globally and 3rd among non-EVM networks. Remarkably, SUI achieved this within less than two years of its mainnet launch, which cannot solely be attributed to the resources invested by Mysten Labs or the foundation, but is also a result of the collective participation of developers, users, and infrastructure partners.
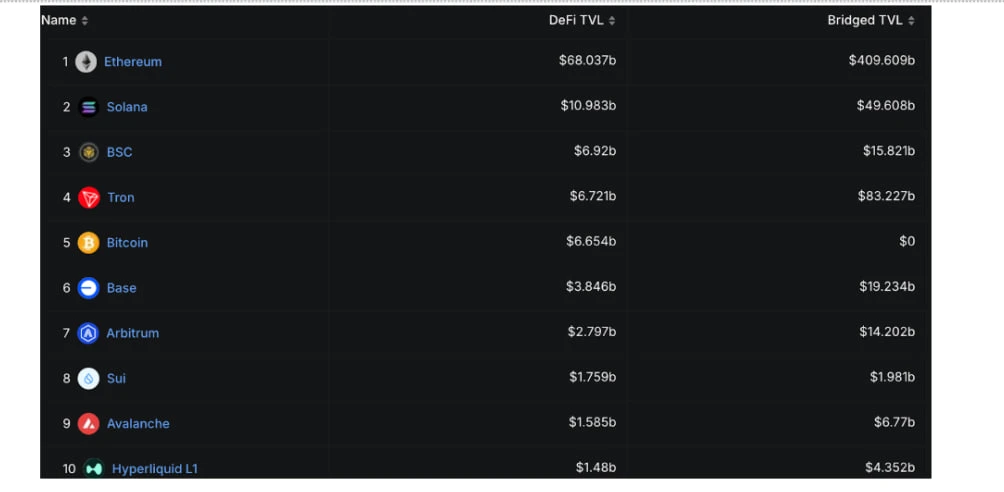
Ranking of SUI ecosystem TVL among all public chains, DefiLlama
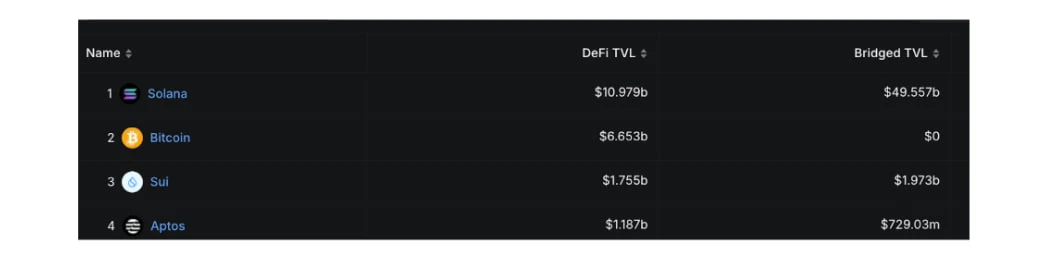
Ranking of SUI ecosystem TVL among non-EVM public chains, DefiLlama
Binance's attention to the SUI ecosystem has also significantly increased recently. Its Alpha project zone has successively launched several representative projects, including NAVI, SCA, BLUE, HIPPO, and NS, further amplifying the exposure and trading liquidity of ecosystem projects, and highlighting the strategic position of the SUI ecosystem in the CEX landscape.
Some members of the SUI community are experiencing a reaction delay, providing us with time and opportunities to observe other potential projects on SUI. As a leading public chain in the Move ecosystem, projects on SUI still deserve our attention. In this process, we can discover more innovative projects worth investing in and supporting, while also accumulating experience for the future development of blockchain.
So, what representative projects currently make up the SUI ecosystem? To present the current ecological landscape of SUI more intuitively, we will briefly outline the most representative protocols.
Although many outstanding projects have emerged on SUI in consumer and gaming directions, given our identity as liquidity providers, this analysis will focus on the core protocols in the DeFi field.

SUI Ecosystem Map, Klein Labs, 23.5.28
DeFi Protocol
Navi Protocol
Navi is a one-stop DeFi protocol on SUI, covering multi-asset lending, leveraged vaults, LSTFi (VOLO LST), and the aggregator Astros. It supports blue-chip assets, LP Tokens, and long-tail assets, providing flash loan services to meet advanced strategy needs. Currently, its TVL exceeds $400 million, ranking second across the SUI network. The native token $NAVI has been listed on major exchanges such as OKX and Bybit, becoming one of the most representative lending platforms on SUI.
Website: https://www.naviprotocol.io/
X: https://twitter.com/navi_protocol
Bucket Protocol
Bucket Protocol is a liquidity platform deployed on the SUI network, allowing users to mint the $BUCK stablecoin by collateralizing various assets. It supports multiple assets, including $SUI and $BTC, providing flexible ways to acquire stablecoin liquidity. Currently, its TVL exceeds $110 million, playing a key role in enhancing liquidity in the SUI ecosystem and expanding DeFi application scenarios.
Website: https://www.bucketprotocol.io/
X: https://x.com/bucket_protocol
Momentum
Momentum Finance is a decentralized exchange built on Sui, utilizing ve(3,3) token economics, aiming to unify token issuance and liquidity management into a single DeFi infrastructure. The ve(3,3) model coordinates incentives among liquidity providers, traders, and the protocol. The protocol incentives promote liquidity and APR, with voters receiving 100% of fees and bribes, liquidity providers receiving 100% of MMT emissions, and traders enjoying low fees and low slippage. Momentum is also responsible for issuing key stablecoins on Sui, such as AusD, FDUSD, and USDY, further solidifying its role as critical infrastructure.
Website: https://app.mmt.finance/
X: https://x.com/MMTFinance
Bluefin
Bluefin is a decentralized perpetual contract trading platform on SUI, supporting over 10 contract markets collateralized by USDC, with a maximum leverage of 20 times. It employs an off-chain order book and on-chain settlement architecture, with confirmation delays of less than 30 milliseconds. Its cumulative trading volume has surpassed $50 billion, with a market share exceeding 80%. Bluefin is also expanding into spot trading and the sub-protocol AlphaLend, comprehensively laying out the DeFi lending market. Currently, its native token $BLUE has been listed on the major South Korean exchange Bithumb.
Website: https://bluefin.io/
X: https://x.com/bluefinapp
Haedal Protocol
Haedal is the native LSD protocol on SUI, allowing users to stake SUI in exchange for haSUI, achieving both yield and liquidity. It enhances validator yield through dynamic allocation and introduces the Hae3 module, which includes an anti-MEV market-making mechanism (HMM), a CEX simulation strategy vault (haeVault), and a governance system (haeDAO), collaboratively improving APR and capital efficiency. Currently, its TVL ranks fourth across the entire chain, becoming an important player in the LSD field. Its native token $HAEDAL has been listed on major exchanges such as Binance, Bybit, and Bithumb.
Website: https://www.haedal.xyz/
X: https://x.com/HaedalProtocol
Artinals
Artinals is an RWA protocol built on SUI, dedicated to transforming real-world assets such as artworks, real estate, and collectibles into tradable NFTs. Its self-developed ART20 standard supports the entire process of asset creation, trading, and management in a digital format, featuring dynamic metadata and royalty-sharing mechanisms. Artinals provides a no-code dashboard and low-code SDK to lower the barriers for asset onboarding, and enables real-time asset trading through ObjeX.world.
Website: https://artinals.com/
X: https://x.com/artinalslabs
DePIN & AI
Walrus Protocol
Developed by Mysten Labs, Walrus Protocol is a decentralized storage and data availability protocol for SUI, specifically designed to address the storage of large files on-chain. It combines erasure coding technology with DPoS consensus, distributing data slices across multiple nodes to ensure high fault tolerance and data recoverability. Additionally, leveraging Move smart contracts, Walrus achieves programmable storage, excelling in applications such as NFT media files. Currently, its native token $WAL has been listed on South Korean exchanges UPbit, Bithumb, and Bybit.
Website: https://www.walrus.xyz/
X: https://x.com/WalrusProtocol/
The SUI ecosystem is growing at an astonishing pace, attracting a large number of developers, users, and capital participation due to its unique technical architecture and rich application scenarios. Whether in infrastructure, DeFi, gaming, or DePIN and AI fields, SUI demonstrates strong competitiveness and innovation. As more mainstream exchanges like Binance increase their support for the SUI ecosystem, SUI is expected to further consolidate its industry position as a "gaming chain" and a diversified application platform, opening a new chapter in ecological development.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



