Attackers can exploit the moment when the child virtual machine exhausts gas to pollute the libraries of the parent virtual machine and induce subsequent call failures, ultimately leading to abnormal behavior in contracts that depend on library integrity.
Author: BitsLab
TonBit, a subsidiary of BitsLab, has once again unearthed an "invisible bomb" in the deep code of the TON Virtual Machine (TVM) — the RUNVM instruction non-atomic state migration vulnerability. Attackers can exploit the moment when the child virtual machine exhausts gas to pollute the libraries of the parent virtual machine and induce subsequent call failures, ultimately leading to abnormal behavior in contracts that depend on library integrity.
Below, we retain the original technical details to present the complete process of vulnerability discovery and verification to developers, helping the community gain a deeper understanding of the issue and enhancing awareness of similar risks.

The following is a detailed description of the vulnerability:
The RUNVM instruction in TVM may pollute the caller's state and render libraries unavailable. A new vulnerability has been discovered in the 'RUNVM' instruction code. This vulnerability allows for the pollution of the caller's state. The relevant code snippet is as follows:
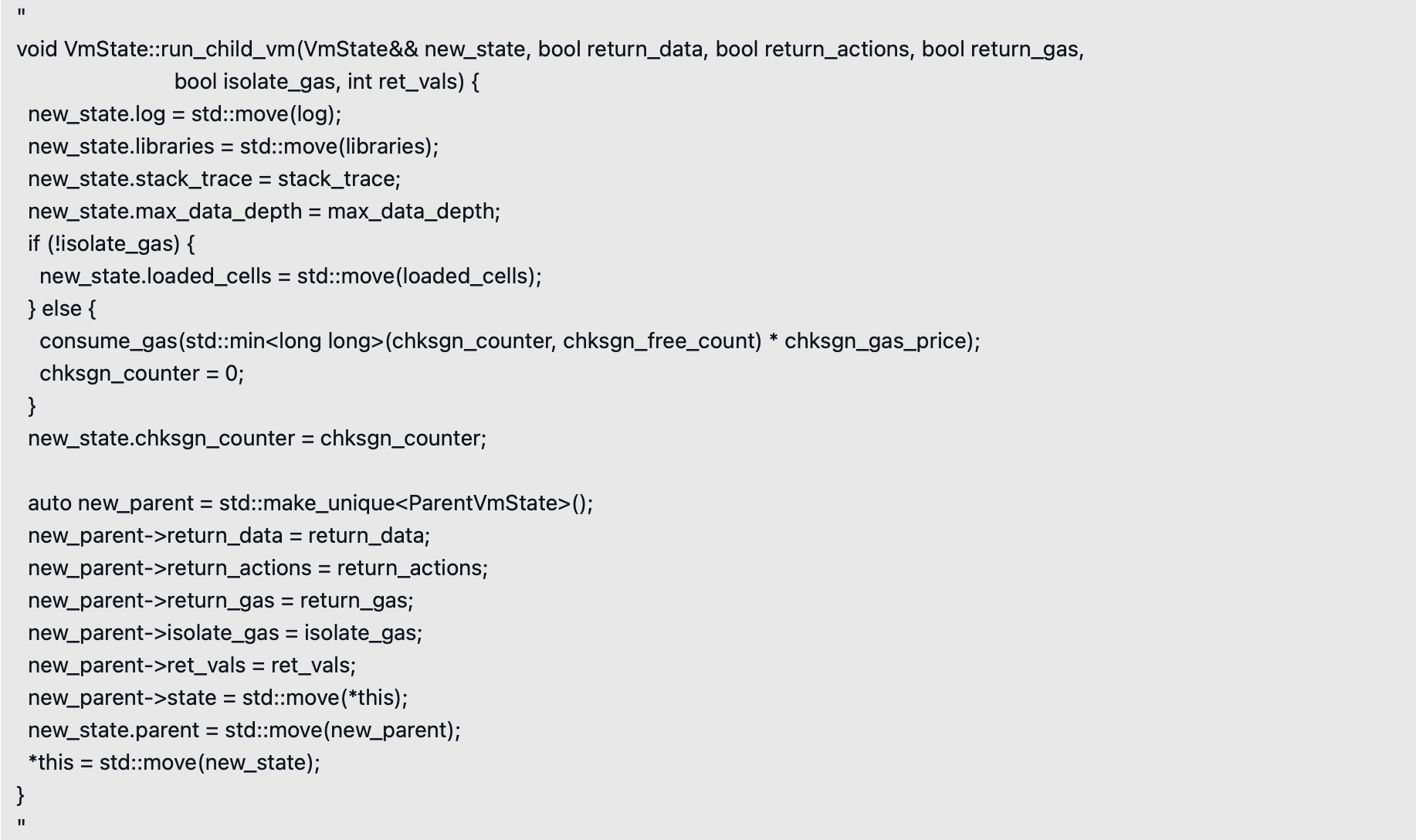
The above code is responsible for launching the child virtual machine. Its function is to move the 'log' and 'libraries' from the current VmState to a new VmState object 'newstate', and then replace the current VmState with 'newstate'.
The problem is that this operation is not truly atomic. Before executing the '*this = std::move(newstate);' statement, the virtual machine may abort the process due to gas exhaustion, causing 'newstate' to fail to successfully replace the current state. At this point, 'libraries' may have already been moved out, leaving the libraries of the child virtual machine in a cleared (moved) state.
Since the RUNVM instruction achieves gas consumption isolation between the child and parent virtual machines through the isolate_gas parameter, the following scenario may arise:
Even if the child virtual machine triggers a gas exhaustion exception, the parent virtual machine still retains enough gas to continue execution. However, due to the failed state transition, the child virtual machine has already moved/cleared the 'libraries', causing subsequent operations that depend on 'libraries' to fail. This situation can lead to unexpected behavior in contracts that assume library integrity.
Vulnerability Verification (PoC Verification)
We successfully reproduced the vulnerability through the following test cases:



Key test modification notes:
To facilitate local observation of library status, we modified the NOP instruction to force the registration of a library entry:

Reproduction Steps:
1) Add this test case to the crypto/test/vm.cpp file
2) Run the test-vm executable
3) Observe the exception thrown due to an empty library when executing the XLOAD instruction
Expected Behavior:
After executing the NOP instruction: the library contains 1 entry
After executing the RUNVMX instruction: although the parent virtual machine continues to run, the library becomes empty
The execution of the XLOAD instruction fails and throws an exception
This fully demonstrates that the combination of non-atomic state transitions and gas isolation mechanisms can produce inconsistent states that violate execution context integrity.
This discovery once again reflects the profound strength of TonBit, a subsidiary of BitsLab, in security research within the TON ecosystem. We have promptly submitted the technical details and mitigation solutions to the TON Foundation and assisted in completing the fix. We recommend that all developers update their dependent libraries in a timely manner after the official patch is released; at the same time, incorporate more rigorous library integrity verification and gas management logic in self-developed contracts to prevent similar issues from being maliciously exploited. BitsLab will continue to uphold the principle of "responsible disclosure" and work with the community to strengthen the security defenses of Web3.
About BitsLab
BitsLab is a security organization dedicated to safeguarding and building the emerging Web3 ecosystem, with a vision to become a respected Web3 security institution in the industry and among users. It has three sub-brands: MoveBit, ScaleBit, and TonBit.
BitsLab focuses on infrastructure development and security auditing for emerging ecosystems, covering but not limited to Sui, Aptos, TON, Linea, BNB Chain, Soneium, Starknet, Movement, Monad, Internet Computer, and Solana. Additionally, BitsLab has demonstrated profound expertise in auditing various programming languages, including Circom, Halo2, Move, Cairo, Tact, FunC, Vyper, and Solidity.
The BitsLab team comprises several top vulnerability research experts who have won international CTF awards multiple times and discovered critical vulnerabilities in well-known projects such as TON, Aptos, Sui, Nervos, OKX, and Cosmos.
About TonBit
TonBit, as the core sub-brand of BitsLab, is a security expert and early builder within the TON ecosystem. As the main security assurance provider for the TON blockchain, TonBit focuses on comprehensive security audits, including audits of Tact and FunC languages, ensuring that TON-based projects possess integrity and resilience. To date, TonBit has successfully audited several well-known projects, including Catizen, Algebra, and UTonic, and has discovered multiple critical vulnerabilities, showcasing our excellence in the field of blockchain security. Furthermore, TonBit has successfully hosted the TON CTF competition, attracting numerous participants and gaining widespread attention, further solidifying its position as a security expert in the TON ecosystem. In the future, TonBit will continue to safeguard blockchain security and promote the continuous development of technology and ecosystems.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




