The diversity of hacking methods that occurred in October included not only common contract vulnerability exploits and account theft but also supply chain attacks and price manipulation.
Written by: Zero Time Technology
The monthly security event highlights from Zero Time Technology have begun! According to statistics from various blockchain security risk monitoring platforms, the total losses from various security incidents in October 2024 increased compared to September. In October, there were over 28 typical security incidents, with total losses due to hacking, phishing scams, and Rug Pulls amounting to $147 million, an increase of about 22.5% from September, with $19.3 million returned. Additionally, according to the Web3 anti-fraud platform Scam Sniffer, there were 12,058 victims of phishing incidents this month, with losses totaling $18.04 million.
Hacking Incidents
Typical Security Incidents: 5
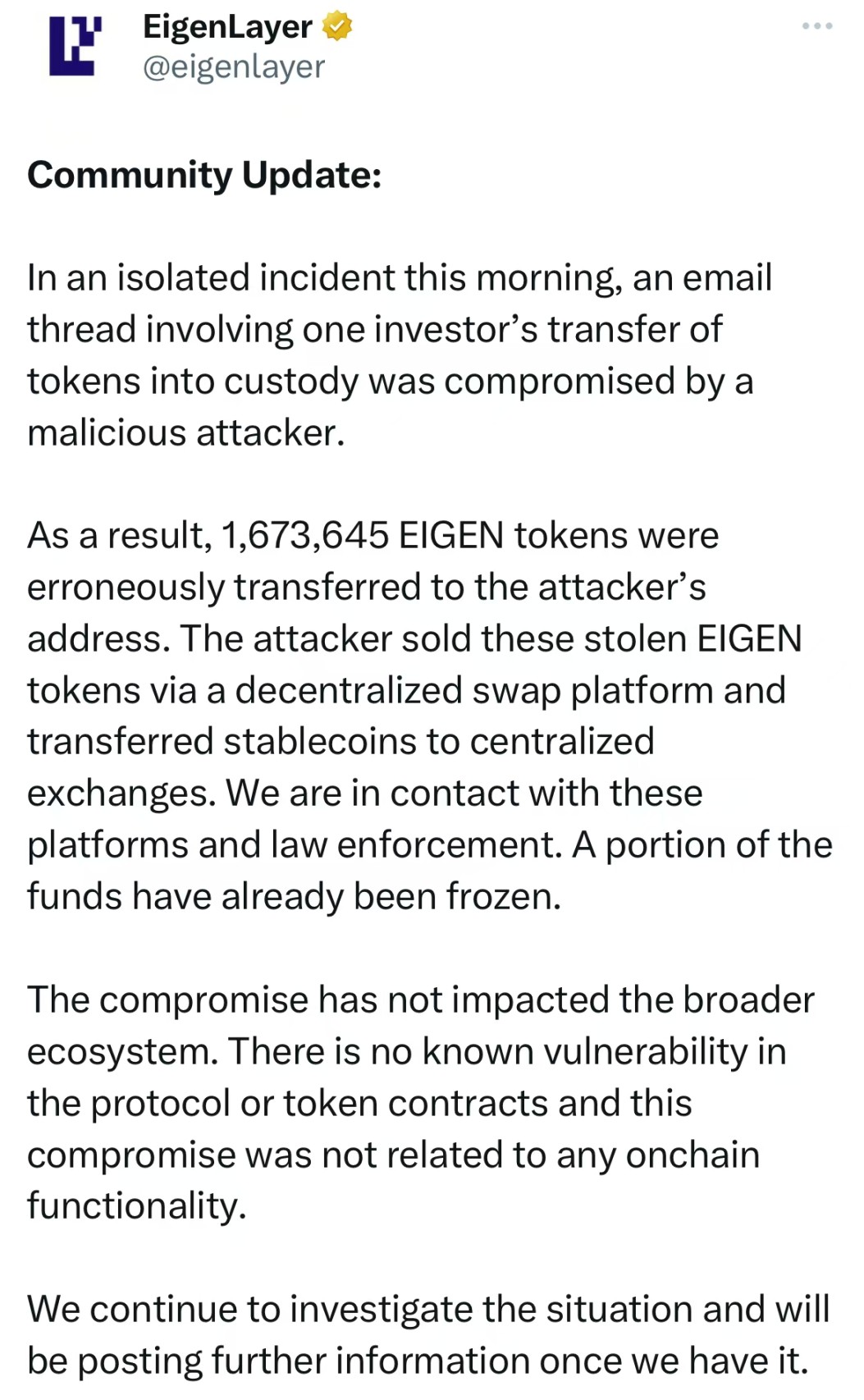
(1) On October 5, EigenLayer posted on X stating: This morning, an independent attack occurred, where an investor's token transfer to a custodial email thread was compromised by a malicious attacker. As a result, 1,673,645 EIGEN tokens were incorrectly transferred to the attacker's address. The attacker sold these stolen EIGEN tokens through a decentralized exchange platform and transferred stablecoins to a centralized exchange. We are in contact with these platforms and law enforcement. Some funds have already been frozen.
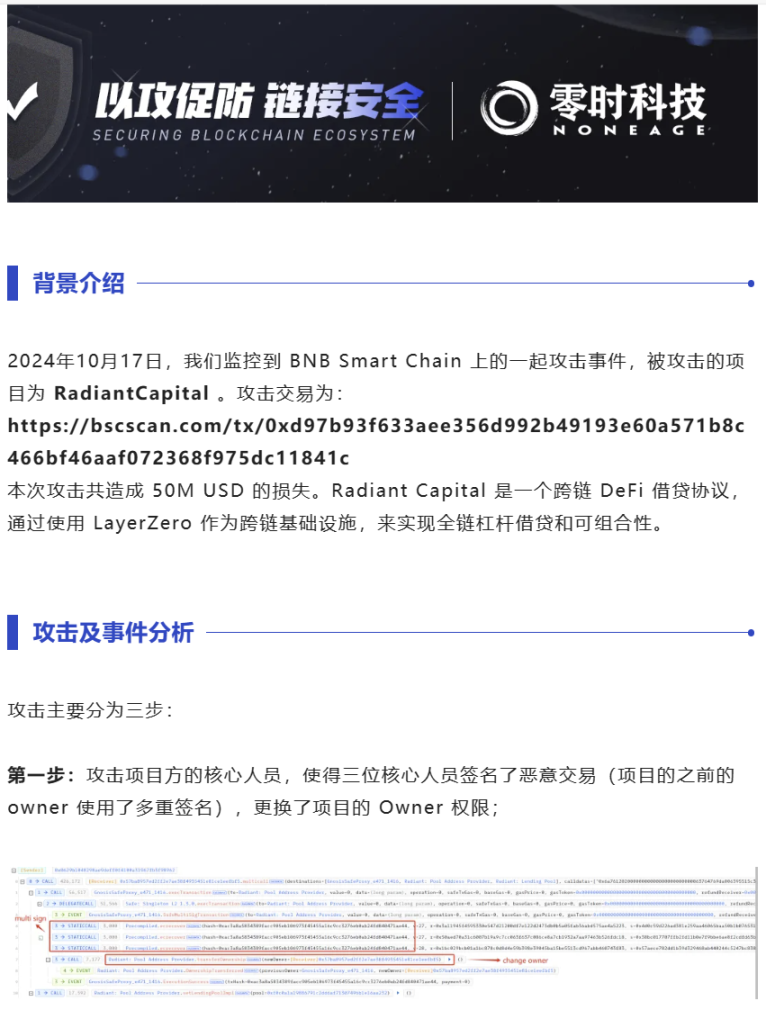
(2) On October 17, the lending protocol Radiant Capital tweeted that its lending markets on the BNB Chain and Arbitrum networks were attacked, and markets on the Base network and Ethereum mainnet have also been suspended. The Zero Time Technology security team analyzed that the root cause of this attack was the hardware wallets of three core developers being hacked, where the front end of the hardware wallet displayed a normal compliant signature, but the actual operation was signing an attack transaction constructed by the hacker. Once the three core developers signed, the attack was completed. This attack resulted in losses of $58 million.
https://mp.weixin.qq.com/s/7v2i8piOMBO2gs6f6lY53g
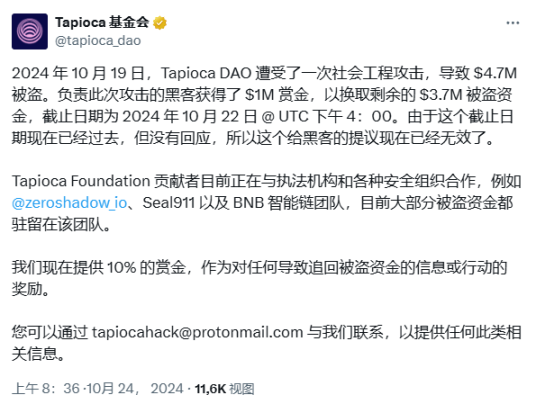
(3) On October 18, Tapioca DAO encountered a significant security vulnerability, where the attacker obtained relevant private keys through social engineering attacks, stealing approximately $4.7 million in cryptocurrency. On October 25, Tapioca DAO released an incident analysis report stating that the security vulnerability occurred because the attacker successfully hacked the private key of a core contributor responsible for smart contract development. SEAL911 confirmed that the attacker was a North Korean hacker organization that used an infectious interview attack method to inject malware into the contributor's computer, thereby obtaining the private key of their address to carry out the theft.
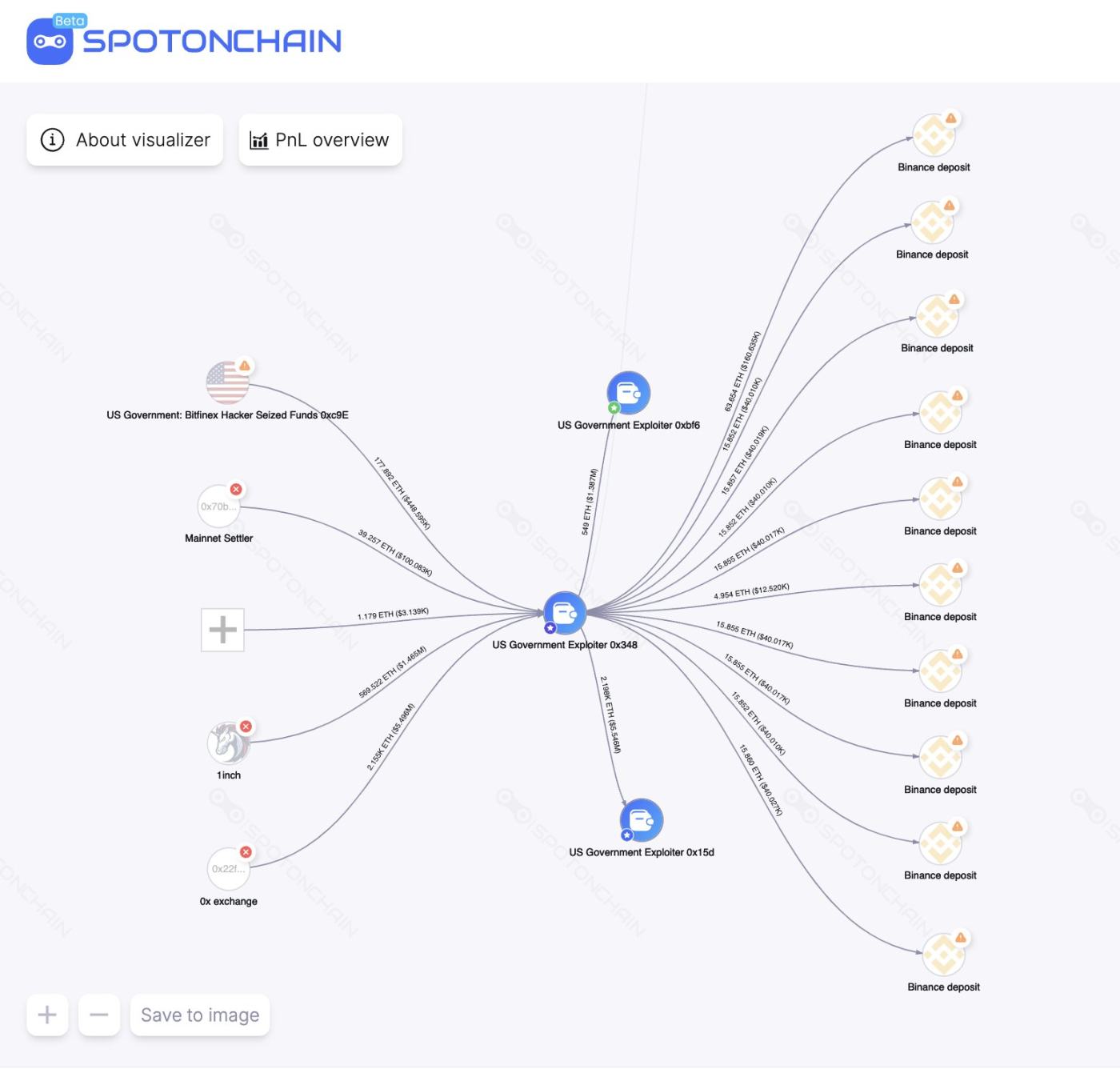
(4) On October 25, the address managing the Bitfinex hacker's seized funds was hacked, resulting in the theft of $20.71 million worth of USDC / USDT / aUSDC / ETH. The stolen funds were transferred to address 0x348…40A9f, where some stablecoins were exchanged for 2,709 ETH, worth $6.8 million.
The exchanged ETH has been distributed to Binance and two new addresses, and the hacker's wallet currently still holds $13.2 million worth of AUSDC. Subsequently, approximately $19.3 million worth of tokens were returned to the U.S. government address.
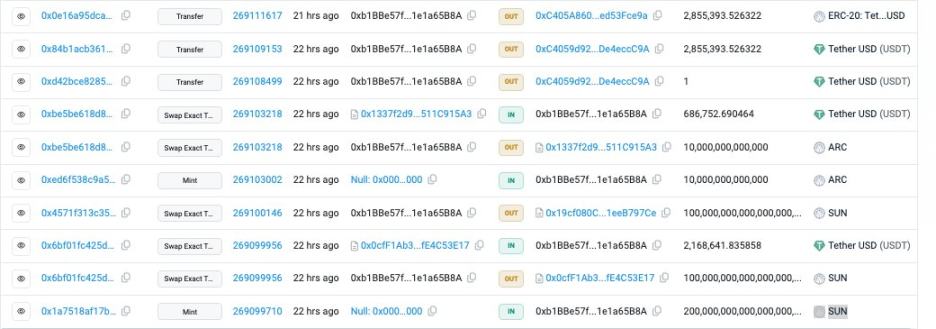
(5) On October 31, the private key of SUNRAY FINANCE was leaked; the attacker gained ownership of SUN and ARC tokens, minted a large number of tokens, and then sold them to deplete the trading pair. Currently, the attacker has stolen $2.855 million. Previously, SUNRAY FINANCE announced: "Regarding the transfer of SUN and ARC token treasury assets, we are working hard to recover. Don't worry, all user assets are available on-chain."
Rug Pull / Phishing Scams
Typical Security Incidents: 11
(1) On October 6, an address starting with 0x213b fell victim to phishing, losing $100,000 just 20 minutes after signing a "approve" phishing transaction to withdraw from MEXC.
(2) On October 7, an address starting with 0x5bfb was phished, resulting in a loss of $192,000 in steakLRT.
(3) On October 9, an address starting with 0x63e4 was phished, leading to a loss of $133,000 in VOW.
(4) On October 11, an address starting with 0xeab2 lost 15,079 fwDETH (worth $35 million) after signing a "permit" phishing signature.
(5) On October 14, an address starting with 0xb0b8 lost $1.39 million worth of PEPE, MSTR, and APU after signing a "permit2" phishing signature.
(6) On October 15, a holder who profited 20 times on MSTR lost $347,868 after signing a "transfer" phishing transaction.
(7) On October 18, an address starting with 0x84b7 was phished, resulting in a loss of $800,000 in mETH.
(8) On October 21, an address starting with 0x2Ff7 fell victim to a phishing scam, leading to a loss of $148,000 in BEAM.
(9) On October 25, an address starting with 0x05f5 lost $126,000 worth of HyPC after signing an "increase allowance" phishing transaction.
(10) On October 26, a victim lost approximately $40,000 after signing phishing signatures on SOL and Bonk.
(11) On October 31, an address starting with 0x3d00 was phished, resulting in a loss of 10 BTC ($723,436).
Summary
From the analysis of the above incidents, the hacking methods that occurred in October were diverse, including not only common contract vulnerability exploits and account theft but also supply chain attacks and price manipulation. Additionally, there were two incidents of exit scams this month that resulted in losses of millions of dollars.
The losses from phishing incidents this month decreased compared to last month, but the number of victims increased.
The Zero Time Technology security team advises project parties to remain vigilant at all times and reminds users to be cautious of phishing attacks. Users are encouraged to thoroughly understand the project's background and team before participating and to carefully choose investment projects. Furthermore, internal security training and permission management should be conducted, and professional security companies should be sought for audits and background investigations before the project goes live.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。



