How does TEE help us build better cryptocurrency applications?
Written by: Oliver Jaros, CMT Digital Analyst; Shlok Khemani, decentralised.co
Translated by: Yangz, Techub News
Uber's San Francisco headquarters, like most tech companies, has an open floor plan where employees can freely move around and share their ideas. However, in the center of the main floor, there is a room that few employees venture into. With its metal and glass exterior walls, a switch that can make transparent glass opaque, and frequent security personnel, this room appears very mysterious.
This is Uber's "war room," a space that operates around the clock and is primarily used for top executives to brainstorm and solve the company's biggest problems. To maintain confidentiality, this room is strictly operated on a "need to know" basis. This level of secrecy is crucial, as Uber needs to fiercely compete globally to maintain its dominant position in the ride-hailing market, and its competitors will not miss any opportunity to leak its strategies. Everything that happens in the war room stays in that room.

Inside Uber's war room; Source: Andrew Chen, a16z
This practice of setting up private spaces within originally accessible areas is quite common. When Apple is working on secret projects, it places designated teams in separate buildings from its headquarters. The U.S. Capitol and other government buildings have Sensitive Compartmented Information Facilities (SCIFs) that provide soundproofing and electromagnetic shielding for sensitive discussions. Even our own homes or hotel rooms have safes.
Secure Enclaves have extended beyond the physical world. Today, we primarily store data and process information using computers. As our reliance on silicon-based machines continues to grow, so do the risks of attacks and leaks. Just like Uber's war room, computers need a separate space to store the most sensitive data and perform critical computations. This space is known as a Trusted Execution Environment (TEE).
Although TEE has become a popular term in the cryptocurrency industry, its purpose and function are often misunderstood. We hope to change this situation with this article. Here, we will explain everything you need to know about TEE, including what they are, why they are important, how we use them every day, and how they help build better Web3 applications.
TEE is Everywhere
First, let's understand the definition of TEE.
TEE is a dedicated secure area within the main processor of a device that ensures the confidentiality of the data and code being processed. TEE provides an isolated execution environment independent of the main operating system, which is crucial for maintaining the security of applications handling sensitive information.
TEE primarily provides two guarantees.
- Isolated Execution: TEE runs code in an isolated environment. This means that even if the main operating system is compromised, the code and data in TEE remain secure.
- Memory Encryption: Data processed within TEE is encrypted. This ensures that even if an attacker gains access to physical memory, they cannot decipher the sensitive information stored in TEE.
To understand the importance of TEE, the device you are likely using to read this article, the iPhone, is a great example. Face ID has become the primary method for users to access their devices. In a matter of milliseconds, the device undergoes the following process:
- First, a dot projector projects over 30,000 invisible infrared dots onto the user's face. An infrared camera captures this pattern and the infrared image of the face. In low-light conditions, a flood illuminator enhances visibility.
- Next, the processor receives this raw data and creates a mathematical model of the face, including depth data, contours, and unique features.
- Finally, the mathematical model is compared to the stored model from when Face ID was initially set up. If the model is accurate enough, a "success" signal is sent to the iOS system, and the device unlocks. If the comparison fails, the device remains locked.

Unlocking the phone with 30,000 projected infrared dots on the face; Source: YouTube
Face ID is not only used to unlock the device but also to verify other operations, such as app logins and payments. Therefore, any security vulnerability would have serious consequences. If the model creation and comparison process were compromised, a non-owner of the device could unlock it, access the owner's personal data, and conduct fraudulent financial transactions. If an attacker managed to extract the stored user facial mathematical model, it would result in the theft of biometric data and a severe invasion of privacy.
Of course, Apple has taken great care in implementing Face ID. All processing and storage are done through The Secure Enclave, which is a dedicated processor built into iPhones and other Apple devices, functioning independently of other memory and processes. Its design purpose is to prevent access even if other parts of the device are compromised. In addition to biometric technology, it can also store and protect user payment information, passwords, keychains, and health data.
Apple's The Secure Enclave is just one example of TEE. Since most computers handle sensitive data and computations, almost all processor manufacturers now provide some form of TEE. Intel offers Software Guard Extensions (SGX), AMD has AMD Secure Processor, ARM has TrustZone, Qualcomm provides Secure Foundation, and Nvidia's latest GPUs come with secure computing capabilities.
TEE also has software variants. For example, AWS Nitro Enclaves allow users to create isolated computing environments to protect and process highly sensitive data within regular Amazon EC2 instances. Similarly, Google Cloud and Microsoft Azure also offer confidential computing.
Apple recently announced the launch of Private Cloud Compute, a cloud intelligence system designed to privately handle artificial intelligence requests that devices cannot provide locally. Similarly, OpenAI is also developing secure infrastructure for artificial intelligence cloud computing.
One reason TEE is exciting is that they are ubiquitous in personal computers and cloud service providers. They enable developers to create applications that benefit from user-sensitive data without worrying about data leaks and security vulnerabilities. They can also directly improve user experience through innovative technologies such as biometric authentication and passwords.
So, what does this have to do with cryptocurrency?
Remote Attestation
TEE provides the possibility for computations that cannot be tampered with externally, and blockchain technology can also provide similar computational guarantees. Smart contracts are essentially computer code that, once deployed, automatically execute and cannot be altered by external participants.
However, there are some limitations to running computations on a blockchain:
- Compared to regular computers, blockchains have limited processing power. For example, a block on Ethereum is generated every 12 seconds and can only accommodate up to 2 MB of data. This is smaller than the capacity of a floppy disk, which is already an outdated technology. Although blockchains are becoming faster and more powerful, they still cannot execute complex algorithms, such as the algorithm behind Face ID.
- Blockchains lack native privacy. All ledger data is visible to everyone, making them unsuitable for applications relying on private information such as personal identities, bank balances, credit scores, and medical histories.
TEE does not have these limitations. While TEE's speed is slower than regular processors, they are still orders of magnitude faster than blockchains. Additionally, TEE inherently provides privacy protection by default, encrypting all processed data.
Of course, blockchain applications that require privacy and greater computational power can benefit from the complementary functions of TEE. However, while blockchain provides a highly trusted computing environment where every data point on the ledger should be traceable to its source and replicated across numerous independent computers, the TEE process occurs in a local physical or cloud environment.
So, we need a way to combine these two technologies, and this is where remote attestation comes into play. But what is remote attestation? Let's take a detour back to the Middle Ages to understand the background.
Before the invention of technologies like telephones, telegrams, and the internet, handwritten letters delivered by human messengers were the only way to send information over long distances. But how could the recipient ensure that the information truly came from the intended sender and had not been tampered with? For centuries, sealing wax provided the solution to this problem.
The envelope containing the letter would be sealed with hot wax imprinted with a unique and intricate pattern, often the coat of arms or symbol of a king, noble, or religious figure. Because each pattern was unique to the sender and nearly impossible to replicate without the original seal, the recipient could be assured of the authenticity of the letter. Additionally, as long as the seal remained intact, the recipient could be confident that the information had not been tampered with.

The Great Seal of the Realm: Used to symbolize the monarch's approval of state documents
Remote attestation is akin to a modern-day seal, i.e., an encrypted proof generated by TEE that allows the holder to verify the integrity and authenticity of the code running within it and confirm that the TEE has not been tampered with. Here's how it works:
TEE generates a report containing information about its state and the internal running code.
The report is encrypted and signed using a key that only genuine TEE hardware can use.
The signed report is then sent to a remote verifier.
The verifier checks the signature to ensure the report comes from genuine TEE hardware. It then examines the report's contents to confirm that the expected code is running and has not been modified.
If the verification is successful, the remote party can trust the TEE and the code running within it.
To integrate blockchain with TEE, these reports can be published on the chain and verified by designated smart contracts.
So, how does TEE help us build better cryptocurrency applications?
Practical Use Cases of TEE in Blockchain
As a "leader" in the Ethereum MEV infrastructure, Flashbots' solution MEV-boost separates block proposers from block producers and introduces a trusted intermediary entity called a "relayer" between the two. The relayer verifies the validity of the block, conducts auctions to select the winning block, and prevents validators from exploiting MEV opportunities discovered by the producer.
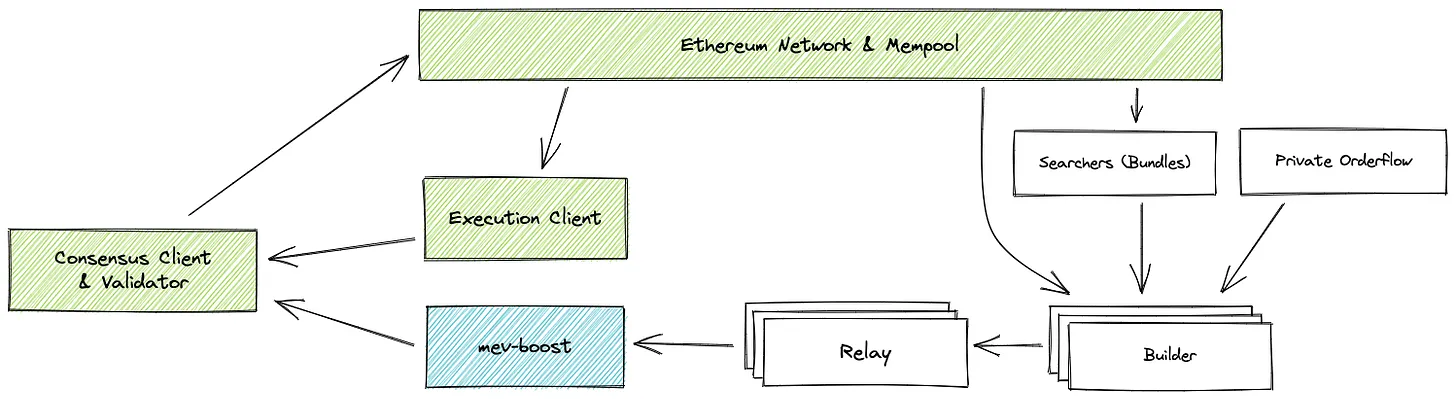
MEV-Boost Architecture
However, if the relayers are centralized, such as if three relayers handle over 80% of the blocks, issues can still arise. As outlined in this blog post, this centralization poses risks such as relayer censorship of transactions, collusion with producers to prioritize certain transactions over others, and the risk of relayers themselves stealing MEV.
So, why not implement the relayer function directly in smart contracts? Firstly, relayer software is very complex and cannot run directly on the chain. Additionally, using relayers is to maintain the privacy of inputs (blocks created by producers) to prevent MEV theft.
TEE can effectively address this issue. By running the relayer software in TEE, the relayer can not only maintain the privacy of input blocks but also prove that the winning block was fairly selected without collusion. Currently, Flashbots is developing SUAVE (in testing), a TEE-driven infrastructure for this purpose.
Recently, this publication and CMT Digital discussed how the Solver network and Intent can help abstract the chain and improve the user experience of cryptocurrency applications. We both mentioned a solution called order flow auctions, a generalized version of auctions conducted in MEV boost, and TEE can enhance the fairness and efficiency of these order flow auctions.
Additionally, TEE is of great help in DePIN applications. DePIN is a device network that rewards contributors (e.g., bandwidth, computing power, energy, mobile data, or GPU) with tokens, and suppliers have a strong incentive to deceive the system by altering the DePIN software, such as displaying duplicate contributions from the same device to earn more rewards.
However, as we have seen, most modern devices have some form of built-in TEE. The DePIN project can request proof of a device's unique identifier generated through TEE, ensuring the device is genuine and running the expected secure software, thus allowing remote verification of contributions' legitimacy and security. Bagel is an example of a DePIN project exploring the use of TEE for data.
Furthermore, TEE plays a crucial role in Joel's recent discussion of Passkey technology. Passkey is an identity authentication mechanism that stores private keys in local devices or cloud solutions' TEE, eliminating the need for users to manage mnemonic phrases, supporting cross-platform wallets, allowing social and biometric authentication, and simplifying key recovery processes.
Clave and Capsule apply this technology to embedded consumer wallets, while hardware wallet company Ledger uses TEE to generate and store private keys. Lit Protocol, in which CMT Digital has invested, provides infrastructure for decentralized signing, encryption, and computation for application, wallet, protocol, and AI agent developers. The protocol uses TEE as part of its key management and computation network.
TEE also has other variants. As the development of generative AI progresses, distinguishing between AI-generated images and real images is becoming increasingly difficult. To address this, major camera manufacturers such as Sony, Nikon, and Canon are integrating technology that assigns digital signatures to captured images in real-time. They also provide infrastructure for third parties to verify the origin of images through verified proofs. While this infrastructure is currently centralized, we hope these proofs will be validated on the chain in the future.
Last week, I wrote an article about how zkTLS brings Web2 information into Web3 in a verifiable manner. We discussed two approaches using zkTLS, including multi-party computation (MPC) and proxies. TEE provides a third approach, handling server connections in a device's secure enclave and publishing computational proofs on the chain. Clique is a project implementing zkTLS based on TEE.
Additionally, Ethereum L2 solutions Scroll and Taiko are experimenting with multi-proof approaches aimed at integrating TEE with ZK proofs. TEE can generate proofs faster, more economically, and without increasing finality time. They complement ZK proofs by increasing the diversity of proof mechanisms and reducing errors and vulnerabilities.
At the infrastructure level, there are projects supporting the use of TEE remote attestation for an increasing number of applications. Automata is launching a modular verification chain, serving as Eigenlayer AVS, acting as a registration center for remote verification, making it publicly verifiable and easily accessible. Automata is compatible with various EVM chains, enabling composable TEE proofs across the entire EVM ecosystem.
Additionally, Flashbots is developing a TEE coprocessor called Sirrah to establish a secure channel between TEE nodes and the blockchain. Flashbots also provides code for developers to create Solidity applications that can easily verify TEE proofs. They are using the aforementioned Automata verification chain.
"The rose is thorny"
While TEE has wide-ranging applications and has been applied in various areas of cryptocurrency, adopting this technology is not without its challenges. It is hoped that builders looking to adopt TEE can keep in mind some key points.
First and foremost, the most significant consideration is that TEE requires a trusted setup. This means that developers and users must trust that the device manufacturer or cloud provider will uphold security guarantees and not have (or provide to external actors such as governments) backdoor access to the system.
Another potential issue is side-channel attacks (SCA). Imagine taking a multiple-choice test in a classroom where you can't see anyone's answer sheet, but you can observe how long it takes for the students next to you to choose different answers.
The principle of side-channel attacks is similar. Attackers use indirect information such as power consumption or timing variations to infer sensitive data processed within TEE. To mitigate these vulnerabilities, careful implementation of encryption operations and constant-time algorithms is needed to minimize observable changes during TEE code execution.
TEE such as Intel SGX has been proven to have vulnerabilities. The SGAxe attack in 2020 exploited vulnerabilities in Intel SGX to extract encryption keys from the secure enclave, potentially exposing sensitive data in cloud environments. In 2021, researchers demonstrated the "SmashEx" attack, which could cause SGX enclaves to crash and potentially leak confidential information. The "Prime+Probe" technique is also a form of side-channel attack that can extract encryption keys from SGX peripheral devices by observing cache access patterns. All these examples highlight the "cat and mouse game" between security researchers and potential attackers.
One of the reasons why most servers in the world use Linux is its robust security. This is due to its open-source nature and the continuous testing and patching of vulnerabilities by thousands of programmers. The same approach applies to hardware. OpenTitan is an open-source project aimed at making the silicon root of trust (RoT, another term for TEE) more transparent, trustworthy, and secure.
Future Outlook
In addition to TEE, there are several other privacy-preserving technologies available for builders to use, such as zero-knowledge proofs, multi-party computation, and fully homomorphic encryption. A comprehensive comparison of these technologies is beyond the scope of this article, but TEE has two prominent advantages.
First is its ubiquity. The infrastructure of other technologies is still in its infancy, while TEE has become mainstream and integrated into most modern computers, reducing the technological risk for founders looking to leverage privacy technologies. Secondly, TEE has much lower processing overhead compared to other technologies. While this feature involves security trade-offs, it is a practical solution for many use cases.
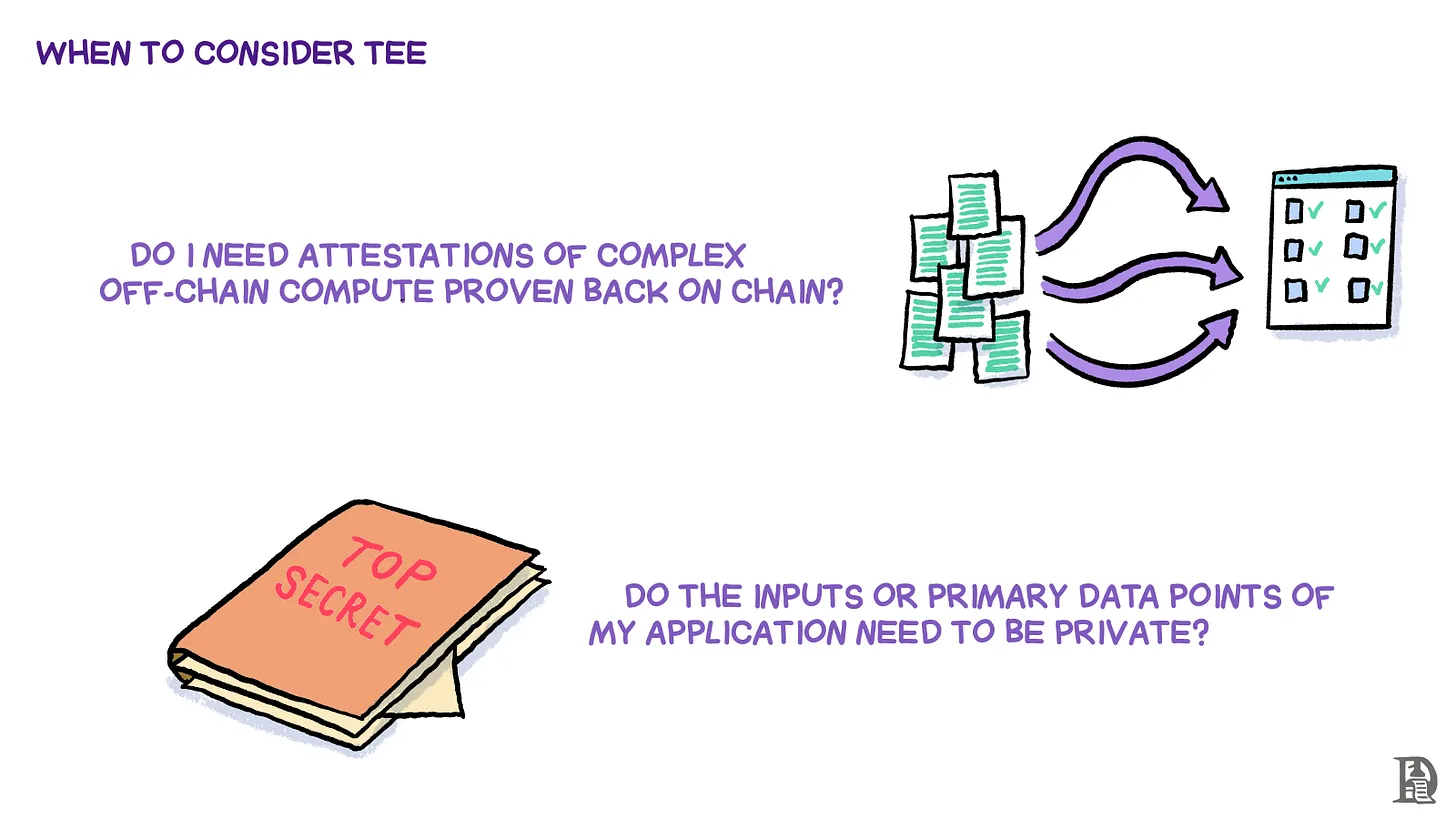
Finally, if you are considering whether TEE is suitable for your product, ask yourself the following questions:
- Does the product need to prove complex off-chain computations on-chain?
- Does the application's input or primary data points need to be privatized?
If the answer is yes to both questions, then TEE is worth a try.
However, considering the fact that TEE is still susceptible to attacks, it is important to remain vigilant. If the security value of the application is lower than the cost of an attack (which could be in the millions of dollars), you may consider using TEE alone. However, if you are building "security-first" applications such as wallets and Rollups, you should consider using decentralized TEE networks (such as Lit Protocol) or combining TEE with other technologies (such as ZK proofs).
Unlike builders, investors may be more concerned with the value proposition of TEE and whether it will give rise to billion-dollar companies.
In the short term, as many teams continue to experiment with TEE, we believe that value will be generated at the infrastructure level, including TEE-specific Rollups (such as Automata and Sirrah) and protocols providing critical components for other TEE-based applications (such as Lit). With the introduction of more TEE coprocessors, the cost of off-chain privacy computation will decrease.
In the long term, we expect the value of applications and products utilizing TEE to surpass the infrastructure level. However, it is important to note that users adopt these applications not because they use TEE, but because they are excellent products solving real problems. We have already seen this trend in wallets like Capsule, where the user experience has been greatly improved compared to browser wallets. Many DePIN projects may use TEE solely for identity verification rather than as a core part of their product, but they will also accumulate significant value.
Every week, our confidence in the assertion that "we are in a transition from fat protocols to fat applications" grows stronger. We hope that technologies like TEE will also follow this trend. The timeline on X won't tell you this, but with the maturation of technologies like TEE, the cryptocurrency space will experience unprecedented and exciting times.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




