Babylon uses a remote staking protocol to apply the security and liquidity of Bitcoin to PoS chains, addressing the challenges faced by Bitcoin holders and PoS chains, and providing strong security for various blockchain networks.
Author: Jaehyun Ha
Translation: Plain Blockchain

Abstract
Currently, Bitcoin holders and PoS chains each face their own problems. Bitcoin holders are striving to effectively utilize their assets (i.e., generate income), while PoS chains face security-related issues such as bootstrapping, low liveness elasticity, and long staking unlock periods.
As a bilateral market, Babylon acts as a bridge by collateralizing Bitcoin to help protect the security of PoS chains. Babylon's remote staking protocol, through its innovative implementation, combines timestamp protocols, finality gadgets, and bond contracts to provide strong security for consumer chains (PoS chains) and Bitcoin holders.
Due to its modular design, Babylon's Bitcoin staking protocol can be applied in various consensus protocols used by consumer chains. Any blockchain network that wishes to leverage the security and liquidity of Bitcoin on its protocol can benefit from Babylon. Some promising use cases include DeFi, non-forking Layer 2 Rollup upgrades, and oracle.
1. Introduction
Bitcoin assets are idle, while PoS chains need capital. Why not unleash their combined potential?
Bitcoin is often referred to as "digital gold" and is the most valuable and secure cryptocurrency globally. Its strength lies in its core goal as a decentralized peer-to-peer digital currency, prioritizing simplicity and security. Bitcoin's script language is intentionally designed to be limited, unable to perform complex calculations or create loops, greatly reducing the risk of vulnerabilities and attacks. The legitimacy of the Bitcoin ledger is safeguarded by the Proof of Work (PoW) protocol, requiring miners to invest significant computing power, making it difficult for attackers to easily disrupt the chain. This steadfast pursuit of simplicity and security is why Bitcoin is revered as digital gold.
However, these advantages of Bitcoin come with limitations in programmability and usability. Unlike the new generation of Proof of Stake (PoS) blockchains, Bitcoin is difficult to use for income-generating activities such as staking. Therefore, Bitcoin holders (HODLers in the crypto community) have little operational space beyond relying on the appreciation of their spot value. In today's financial landscape, simply holding assets often provides additional opportunities to generate more income through reinvestment. Therefore, this significantly underutilized digital asset in terms of market value is regrettable in this regard.
At this point, we also have to mention PoS chains. The PoS mechanism is adopted by newer blockchains such as Ethereum 2.0 and Solana, requiring validators to lock up their cryptocurrencies (i.e., staking), which may be slashed if malicious behavior is detected. The more tokens staked, the higher the security of the chain's cryptographic economy. Unlike Bitcoin, PoS offers more opportunities for income-generating activities. Individuals only need to stake tokens on the chain as validators to benefit, and can also increase asset value through providing liquidity (LP) or DeFi lending, among other methods. In addition, PoS is energy-efficient as it does not require validators to maintain consensus security through mining. Given these advantages, the mainstream has shifted from PoW to PoS in recent years.
However, despite its advantages, the fundamental limitations of PoS protocols lead to some security and user experience drawbacks. One of the most obvious problems is the bootstrapping issue. Emerging PoS blockchains (such as Cosmos Zones) find it difficult to attract sufficient capital for staking due to the low valuation of their tokens, resulting in weak security and difficulty attracting high-value decentralized application projects. In addition, due to the inherent limitations of PoS protocols, there are additional security issues, such as insufficient resistance to non-slashing long-range attacks without external sources of trust and lower liveness elasticity.
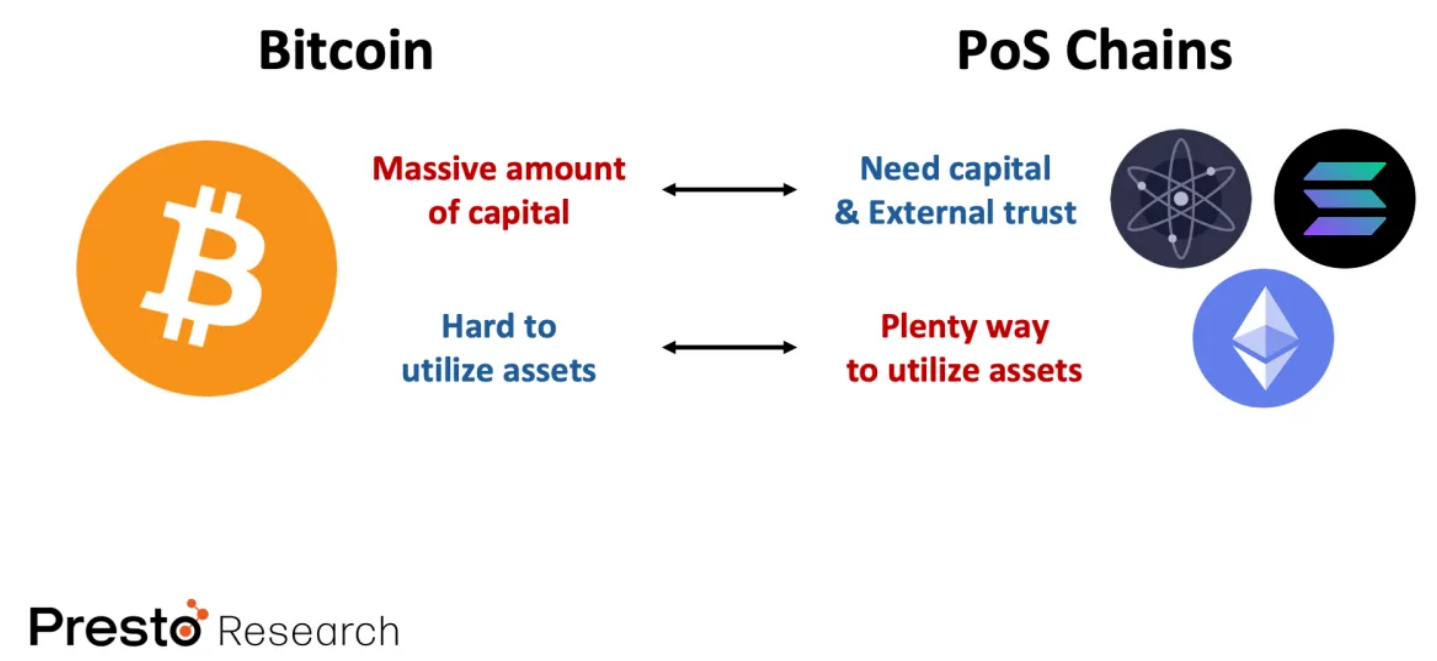
In short, while Bitcoin has a huge capital but lacks ways to utilize these assets, PoS chains provide various ways to utilize assets but require sufficient capital and external sources of trust to ensure security. Combining these insights, Bitcoin and PoS chains can complement each other perfectly. So, why not create a protocol to unleash their combined potential?
This is the core idea of Babylon's Bitcoin staking protocol: using Bitcoin assets to provide security for PoS chains while creating income for Bitcoin holders. This sounds very cool, but at the same time, creating an "excellent Bitcoin staking protocol" with strong security also faces many challenges. In this report, we will explore the elements of building an "excellent Bitcoin staking protocol," the challenges in its implementation, and how Babylon addresses these issues through technological advancements.
Figure 1: Complementarity of Bitcoin and PoS chains
2. Problem Statement for PoS Chains
In this section, we will delve into the problems related to PoS chains and Bitcoin, and clearly state the problem statements. We will first address the three inherent security limitations of PoS protocols and then discuss the difficulties of incorporating Bitcoin into income-generating activities.
1) Problem Statement 1: Bootstrapping Issue
The bootstrapping issue of PoS chains refers to the difficulty in attracting capital and validators due to inherent security issues when a new chain is launched. When a PoS chain is newly launched, its native tokens are usually of low value and low market capitalization, making the network vulnerable to various attacks, thereby compromising the integrity of the PoS protocol.
The low value of tokens allows individuals or groups to relatively cheaply acquire large amounts of tokens, potentially leading to centralization of staking. This centralization increases the possibility of security attacks, such as censoring transactions or rolling back the chain. In addition, since the maximum penalty faced by attackers is limited to the tokens they have staked (with low token value in a newly launched network), attackers may consider the potential loss acceptable, even if their staked tokens are slashed for protocol violations.
These risks, coupled with the lack of verified security and reliable records, often deter potential validators from investing. They may be concerned about potential losses from network failure or attacks. To mitigate this issue, PoS chains often adopt strategies such as offering high initial staking rewards or establishing partnerships with reputable entities to encourage validator participation. However, these methods may lead to high inflation rates and centralization of staking power, which, while significantly boosting chain usage in the short term, may have negative long-term effects.
2) Problem Statement 2: Low Liveness Elasticity Issue
The low liveness elasticity issue faced by PoS protocols refers to the protocol's ability to continue confirming transactions in the face of malicious validators. Different PoS protocols exhibit varying degrees of elasticity when facing malicious behavior. For example, protocols like Snow White and Ouroboros have high liveness elasticity, tolerating up to 1/2 of malicious validators.
However, protocols like Tendermint and Gasper, even with accountable security, cannot guarantee liveness when the proportion of malicious validators exceeds 1/3. Accountable security means that the protocol can not only maintain consistency of the chain's state but also identify and punish validators for improper behavior through a slashing mechanism (see subsequent sections). This 1/3 limit stems from the Byzantine Fault Tolerance (BFT) model, which is the basis of security for these protocols. According to BFT theory, the prerequisite for maintaining security and liveness is having more than two-thirds of honest validators. When more than one-third of validators are malicious, they can effectively delay the progress of the protocol by voting for conflicting blocks or refusing to vote, preventing the formation of this supermajority, and causing the protocol to stall.
3) Problem Statement 3: Long Staking Unlock Period
Even in PoS chains with accountable security, the most critical issue is still the long staking unlock period. Contrary to the advantage of PoS chains, where blocks can be confirmed within seconds or minutes, staking unlock typically takes several days to weeks. This extended unlock period reduces user experience because stakers cannot participate in the PoS protocol during this period, their staked assets are locked, and they cannot receive staking rewards. This not only leads to potential loss of income for stakers but also reduces overall liquidity in the PoS system.
Figure 2: Staking Unlock Period for PoS Chains
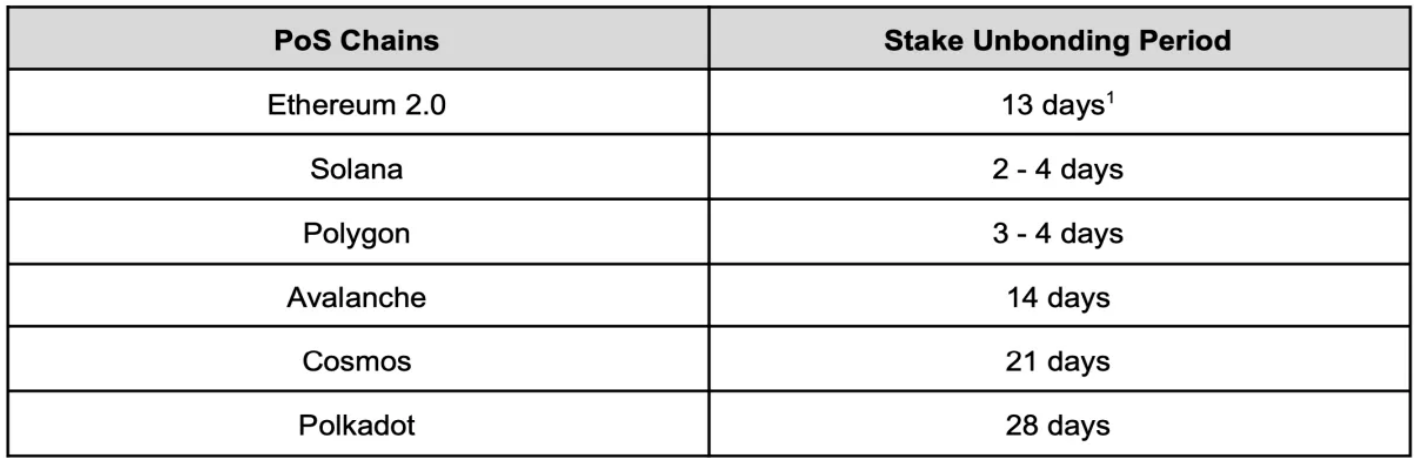
(1. According to the authors of the paper "Bitcoin-Enhanced Proof-of-Stake Security: Possibilities and Impossibilities (Oakland '23)," using the weak subjectivity analysis model proposed by D. Park and A. Asgaonkar, the average number of validators holding 32 ETH was calculated for PoS Ethereum.)
Given these inconveniences caused by the staking unlock period, why do most PoS chains still maintain a long unlock period? The answer lies in the need for PoS chains to guard against long-range attacks. To fully understand this, some terms need to be understood, such as fork choice rule and weak subjectivity. Let's delve into these concepts in more detail.
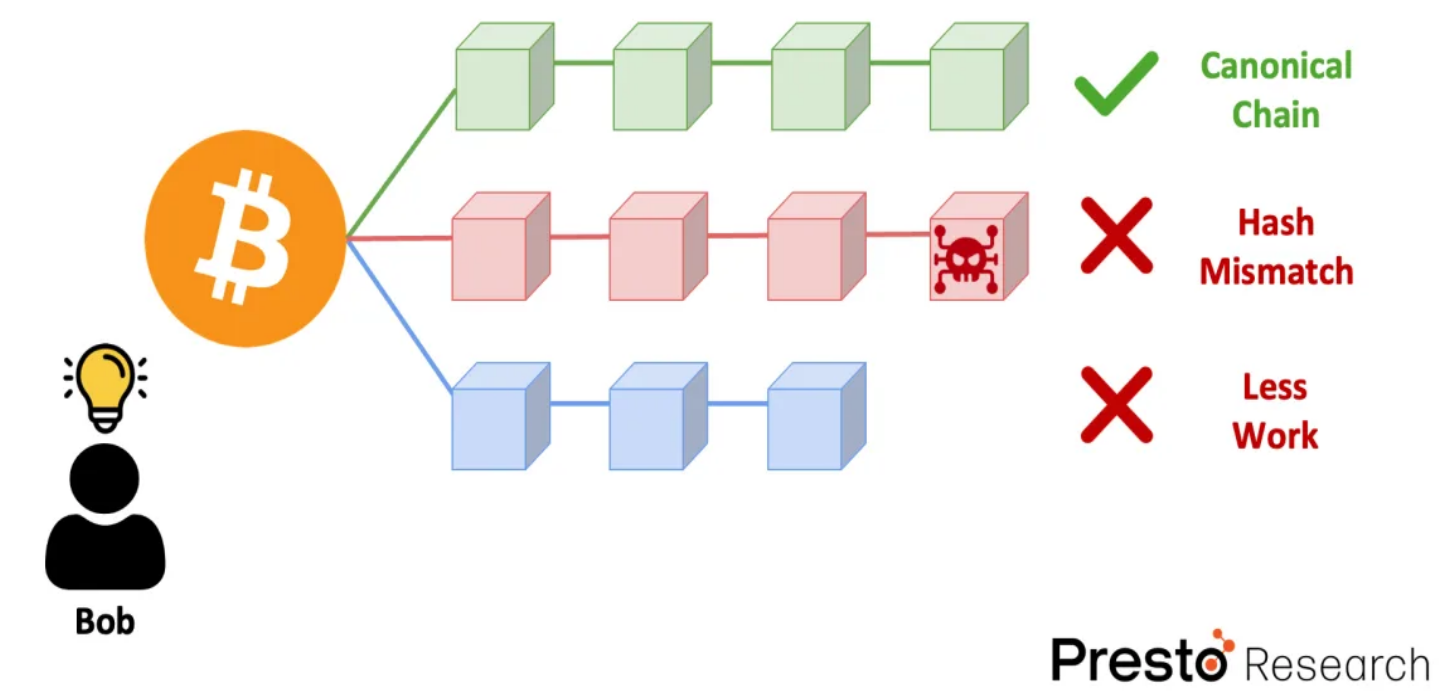
Suppose Bob wants to join and participate as a node in a decentralized blockchain protocol that has been running for a long time. In this type of blockchain, there is no central server distributing legitimate chain versions to each client. Instead, each node propagates its version of the chain to other nodes, and each client decides which chain to follow based on consensus rules. So how does Bob know which chain to follow? The answer is simple—he just needs to choose the chain with the most accumulated computational work, often referred to as the "Nakamoto consensus" or "longest chain rule."
Even if Bob receives 100 different conflicting chains, he doesn't need to worry. He can independently verify the legitimacy of these chains by recalculating the hash values on these chains (as the hash values and random numbers for each block are recorded on the chain) and then choose the chain to follow based on their computational work.
Figure 3: Can Bob (a new joining node) distinguish which chain is the canonical chain?—Bitcoin
However, if Bob wants to join a Proof of Stake (PoS) chain, the situation becomes more complex. Similar to the previous scenario, if Bob receives multiple conflicting chains, how does he choose the correct chain?
In a PoS chain, consensus is reached differently from a Proof of Work (PoW) chain. In PoS chains, consensus is achieved through validators, who are selected based on the amount of cryptocurrency they hold (staked assets) and are willing to use as collateral. Validators propose and vote on blocks, and the validity of the chain is determined by the collective agreement of these validators.
For example, in Ethereum 2.0, validators follow and vote for the chain with the highest recent voting weight to earn rewards (i.e., choose the canonical chain). If validators cast conflicting votes, they face penalties (slashing), and a portion of their staked assets will be confiscated. In this mechanism, validators are encouraged to follow the canonical chain and remain consistent with the network. In theory, these rules should prevent serious forks from the outset—if someone attempts a security attack, they would only harm their own interests.
In practice, when we look at Ethereum's reorg depth data, we find that cases of depth exceeding 1 are very rare (i.e., serious forks almost never occur).
Despite these rules, PoS chains still face a significant threat, which is the long-range attack. In this attack, the attacker gains the private keys of historical validators who have participated in consensus. By doing so, the attacker can potentially rewrite the entire history of the blockchain from the genesis block by forking, causing serious disruption to the network. As mentioned earlier, this attack should be invalid because the PoS system has a slashing mechanism. So how is this possible?
This attack is possible because the attacker cannot be penalized through the slashing mechanism, as the validators' staked assets have already been unlocked. In this scenario, the attacker can easily create a false chain (Figure 4) by purchasing or, worse, obtaining the private keys of those validators whose staking has been unlocked through hacking. Using these private keys, they can easily create a false chain because the PoS system does not require a large amount of computational work to generate a blockchain. Additionally, since the canonical chain's block timestamps are public, the attacker can simply replicate these timestamps on their chain, making it appear more legitimate.
Figure 4: Can Bob (a new joining node) distinguish which chain is the canonical chain?—PoS chain
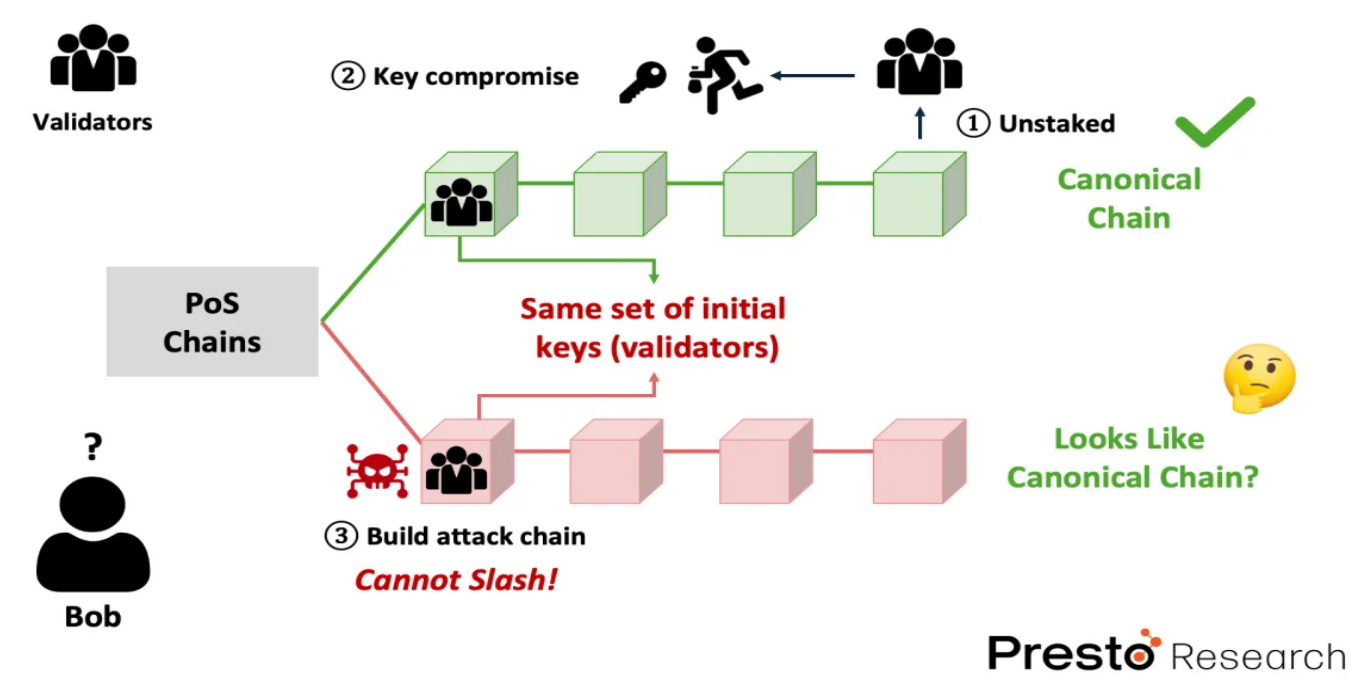
When Bob joins this PoS chain, he faces a significant challenge: how to distinguish which chain is the canonical chain. From his perspective, both chains seem legitimate because they are signed by legitimate validators, have consistent timestamps, and show regular validator rotation. In this scenario, Bob can only rely on external sources of trust (such as block explorers, node operator groups) to identify the correct chain. By consulting these external sources to find a reliable checkpoint, the so-called weak subjectivity point, Bob can synchronize the chain from that point and connect with other nodes.
Weak subjectivity is the key reason why PoS chains typically set a long staking unlock period. Since the weak subjectivity point ultimately relies on social consensus from external sources of trust, which usually takes time to form and may be communicated through channels such as Discord or Telegram, PoS chains have to enforce these extended unlock periods.** The authors of the paper "Bitcoin-Enhanced Proof-of-Stake Security: Possibilities and Impossibilities" (the foundational paper of Babylon) claim that without the help of external sources of trust, PoS chains are theoretically unable to fully prevent long-range attacks (i.e., the security of the slashing mechanism).
4) Problem Statement for Bitcoin Holders
Bitcoin's market value ranks first among all existing cryptocurrency assets (approximately $1.2 trillion as of August 2024) and holds over 56% of the entire crypto market, making it a leading blockchain in the industry. As a blockchain, Bitcoin excels in decentralization and security, although its scalability is somewhat lacking. In terms of decentralization, unlike emerging PoS chains, Bitcoin's tokens are not heavily distributed to early investors or foundation members but are held by globally distributed miners through its long-running history (although this also presents centralization issues among miners, it is still better than new PoS chains). In terms of security, due to its proof-of-work nature, chain reorganization is economically almost infeasible. Multiple studies have shown that segmenting its network using Bitcoin's overlay network and network layer incurs extremely high costs, making Bitcoin significantly more secure than other chains.
Despite Bitcoin's strong performance as a blockchain, Bitcoin holders face some dissatisfaction. Unlike other mainstream PoS-based blockchains (such as Ethereum and Solana), opportunities to participate in yield-generating activities are very limited, resulting in most assets being idle. To participate in yield-generating activities such as DeFi lending, Bitcoin holders typically need to bridge their Bitcoin to other chains, converting it into wrapped Bitcoin (wBTC). However, wBTC is primarily used as collateral, and due to the low volatility of collateral assets, the returns from holding or lending are often lower than other assets. In fact, on DeFi platforms such as Aave, Compound, and Blockchain.com, the annual percentage yield (APY) for wBTC is usually below 1%, making it difficult to achieve significant returns. Nevertheless, as of August 2024, the market value of wBTC still remains at around $9 billion, accounting for approximately 0.77% of Bitcoin's market value, indicating that the majority of Bitcoin assets remain idle.
5) Summary
The problems faced by PoS chains and Bitcoin holders can be summarized as follows:
Three major issues with PoS chains:
A. Bootstrapping problem of PoS chains: When a new chain is launched, the low token value and market value may lead to a concentration of staking power, lacking sufficient deterrence to prevent malicious activities, making the network vulnerable to attacks and hindering validator participation.
B. Low liveness resilience problem: PoS protocols with accountable security can only guarantee protocol liveness when less than one-third of validators are malicious.
C. Long staking unlock period problem: PoS chains rely on external sources of trust to prevent long-range attacks, and the formation of this trust consensus takes time, resulting in a long unlock period.
Problem faced by Bitcoin holders: Limited opportunities for Bitcoin holders to participate in yield-generating activities, typically requiring involvement in DeFi activities through wBTC, with low returns—usually an annual percentage yield of less than 1%, resulting in the majority of Bitcoin assets being idle.
3. Achieving "A High-Quality Bitcoin Staking Protocol"
Reviewing the previously discussed problem statements, it can be said that PoS chains require capital and external security guarantees, while Bitcoin needs a conducive environment for generating returns. The simplest way to address these two issues is to create a Bitcoin staking protocol.
1) How to define "A High-Quality Bitcoin Staking Protocol"?
So, how can we implement such a Bitcoin staking protocol? A simple method is to use cross-chain bridging: Bitcoin holders send their Bitcoin to the address of a trusted third-party bridging operator for locking, and then use the issued wBTC as staking assets in the PoS chain.
However, this method does not constitute "A High-Quality Bitcoin Staking Protocol." One significant drawback is that when Bitcoin holders want to convert their wrapped Bitcoin back to real Bitcoin, they have to rely on a third party for the transfer. The recent surge in cross-chain bridging vulnerabilities further exacerbates this concern ("Cross-Chain Bridging Vulnerabilities: More Risks You Don't Know," Jaehyun Ha, June 3, 2024), leaving Bitcoin holders skeptical of this protocol.
The same applies to PoS chains. The fundamental security issues of PoS chains mentioned in the previous problem statements remain unresolved. For example, this simple method cannot defend against long-range attacks, nor can it address the problem of long staking unlock periods (as the staking unlock process still relies on external trust assumptions).
Based on these considerations, a Bitcoin staking protocol relying solely on bridging cannot be considered a high-quality Bitcoin staking protocol. A high-quality Bitcoin staking protocol must be able to provide strong security for Bitcoin holders and PoS chains. So, what are the key security features required to build such a high-quality Bitcoin staking protocol?
2) Security Features of a High-Quality Bitcoin Staking Protocol:
The first is slashable security. To defend against security attacks such as long-range attacks, Bitcoin stakers who violate the protocol must face slashing penalties before unlocking their staking.
The second is staker security. If Bitcoin stakers honestly follow the PoS protocol, they should be able to withdraw funds or unlock staking at any time. This requires the system to resist withdrawal censorship and support trustless staking unlock.
Lastly, staker liquidity. Given the current long staking unlock periods in PoS protocols, necessitated by the need for social consensus, a fast and secure unlock process is necessary, without going through this lengthy procedure.
3) How does Babylon achieve such a high-quality Bitcoin staking protocol?
Babylon achieves "A High-Quality Bitcoin Staking Protocol" through remote staking. Remote staking refers to the use of assets on one blockchain (the provider chain) to secure another blockchain (the consumer chain) without the need for these assets to leave the provider chain. In Babylon's framework, Bitcoin serves as the provider chain to enhance the security of the PoS consumer chain. The core of Babylon's creation of a high-quality Bitcoin remote staking protocol lies in the integration of three key components: timestamp protocol, finality gadget, and staking contract.
Figure 5: Babylon's Remote Staking Protocol
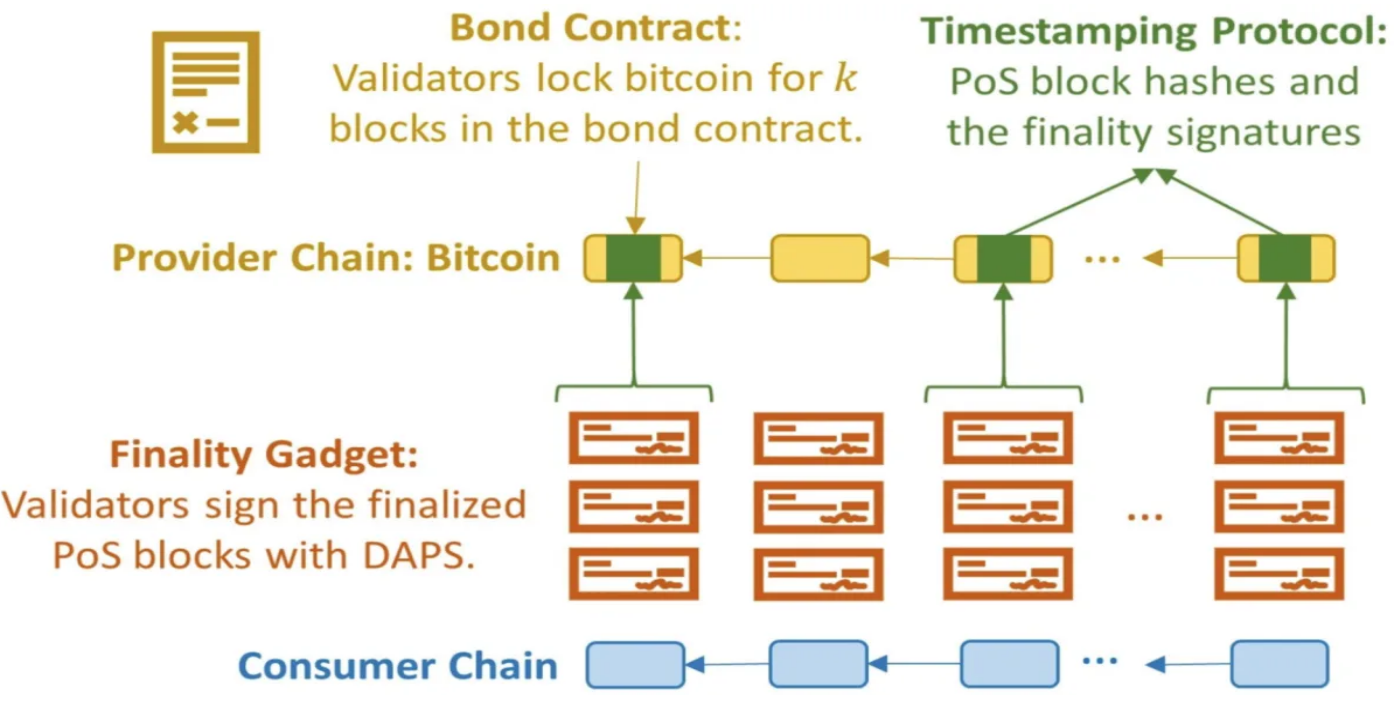
The timestamp protocol (Figure 6) is crucial for ensuring data consistency between the Bitcoin blockchain and the PoS chain during the Bitcoin staking process. It is a process that uses the Bitcoin network as a timestamp server (i.e., an external source of trust) to mark checkpoints for updates to the PoS chain. This includes recording the hash values of PoS consumer chain blocks on the Bitcoin blockchain and attaching confirmation signatures from validators.
The primary purpose of this timestamp protocol is to enhance slashable security and staker liquidity. As mentioned in the previous section, every PoS chain must rely on external sources of trust to mitigate the risk of long-range attacks (i.e., penalizing attackers before they unlock their staking). Here, Babylon has chosen the most secure blockchain—Bitcoin—as its external source of trust. Once the checkpoint of the PoS chain is deeply embedded in the Bitcoin blockchain (i.e., 6 block depth), it becomes probabilistically irreversible. This ensures that an attack chain checkpoint recorded late on Bitcoin will be considered fraudulent and easily ignored, effectively mitigating long-range attacks. In other words, if attackers attempt an attack before unlocking their staking, they will be penalized. If they have already unlocked their staking, there is still no issue, as their attack attempt will be easily identified and prevented through the Bitcoin timestamp protocol.
Figure 6: Timestamp Protocol
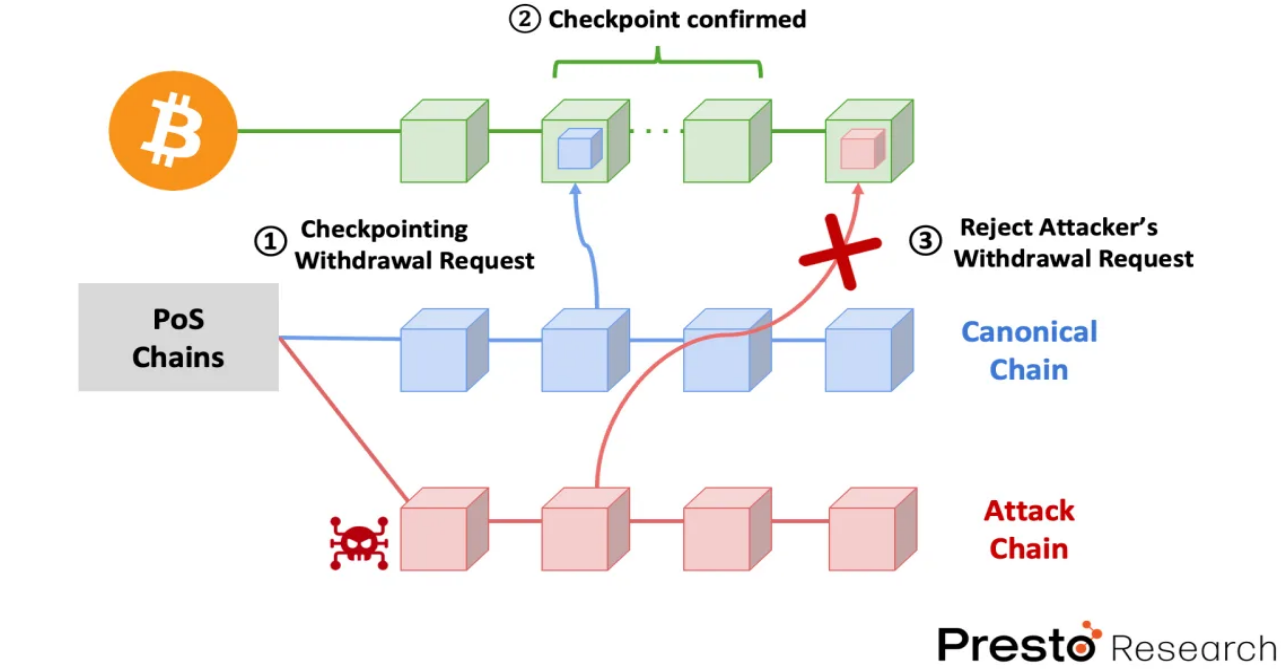
Not only does Babylon's protocol enhance defense against security attacks, but it also helps reduce the delay in staking unlock. Unlike existing solutions that rely on social consensus, Babylon's timestamp protocol only requires recording PoS blocks containing unlock requests to the Bitcoin blockchain before any conflicting checkpoint and obtaining sufficient confirmation in the Bitcoin chain (6 blocks) to approve the unlock request. This significantly reduces the unlock delay, taking only hours instead of weeks.
Furthermore, the timestamp protocol also requires recording timestamps of provider chain blocks in consumer chain blocks to help clients track changes in the validator set. As staking and unlocking activities lead to the continuous evolution of the validator set, timestamp data allows validators and clients to verify the current validity of the validator set.
The Finality Gadget is another key component in Babylon's design, introducing an additional finality layer to the consensus process of the consumer chain. In a standard PoS chain, a block is considered finalized after receiving sufficient validator votes, but this process may be vulnerable to attacks if a majority of validators act maliciously. The Finality Gadget addresses this vulnerability by requiring each validator to sign only one block at each height using a Double Authenticated Pre-Image Sampling (DAPS) signature.
If a validator attempts to sign multiple conflicting blocks, their private key will be extracted and exposed, leading to an automatic slashing of their staked assets. This mechanism ensures that once a block is finalized using the Finality Gadget, it cannot be revoked without severe consequences for the relevant validators. By ensuring that only one block at each height can be finalized, the Finality Gadget provides a strong deterrent against double-signing behavior during staking.
The Bond Contracts are the final key component for implementing Bitcoin staking, ensuring secure Bitcoin staking without relying on complex smart contracts. Babylon's design acknowledges that Bitcoin, as the provider chain, does not support Turing-complete smart contracts, limiting the complexity of operations that can be directly executed on the Bitcoin blockchain. To address this limitation, Babylon employs an innovative staking contract mechanism using Bitcoin's existing script functionalities, particularly multi-signature and time locks.
The staking contract first requires validators to lock a portion of their Bitcoin as a deposit in the staking contract on the Bitcoin blockchain, and the lockup period is determined by the number of Bitcoin blocks. During this period, validators must fulfill their responsibilities on the consumer chain, such as participating in the consensus mechanism or validating transactions. The locked Bitcoin serves as collateral, ensuring validators have economic incentives to act honestly and responsibly. This simple locking mechanism ensures that the Bitcoin cannot be spent until a certain number of Bitcoin blocks have passed, providing a secure exit option for stakers. Even if everything fails, as long as the Bitcoin network continues to operate, stakers can always retrieve their Bitcoin after the lockup period ends (i.e., staker security).
To enforce slashing penalties, the staking contract utilizes Bitcoin's covenants, which restrict when and how the locked funds can be spent. If a validator fails to fulfill their responsibilities or their key is compromised, a slashing transaction can be initiated. This slashing transaction will send the locked Bitcoin to an unspendable address, effectively destroying the funds. This is achieved through the use of covenants in the Bitcoin script, specifying an unspendable output address. This unspendable output is typically an OP_RETURN output, making it impossible for the validator or anyone else to reclaim the slashed funds.
The covenant mechanism is crucial for enforcing slashing, but before Bitcoin script natively supports covenants, a simulated approach is used. This simulation involves a covenant committee composed of multiple members. The staking contract is constructed as a multi-signature scheme, requiring signatures from both validators and the covenant committee to spend the deposit before the end of the validator's responsibilities. The committee pre-signs the slashing transaction when creating the staking contract, ensuring that anyone can execute the transaction if the validator's key is compromised. This simulated covenant relies on an existing trust assumption that at least one committee member remains honest and safeguards their signing key, ensuring the ability to execute the slashing transaction when needed.
In practice, the simulated covenant using a multi-signature scheme (such as MuSig2) ensures that the contract remains lightweight and space-efficient on the Bitcoin blockchain. The MuSig2 scheme allows the committee to generate a single aggregated signature composed of participating members, which can be used to authorize transactions. However, if someone in the committee fails to respond or refuses to participate, partial signatures can be published on the chain, allowing the community to identify and exclude uncooperative members. This approach ensures that even before full covenant support in the Bitcoin script, the slashing mechanism remains robust, providing a strong deterrent against dishonest behavior by validators.
4) Babylon: Remote Staking with Economic Security
Figure 7: Overview of Babylon's Bitcoin Staking Protocol
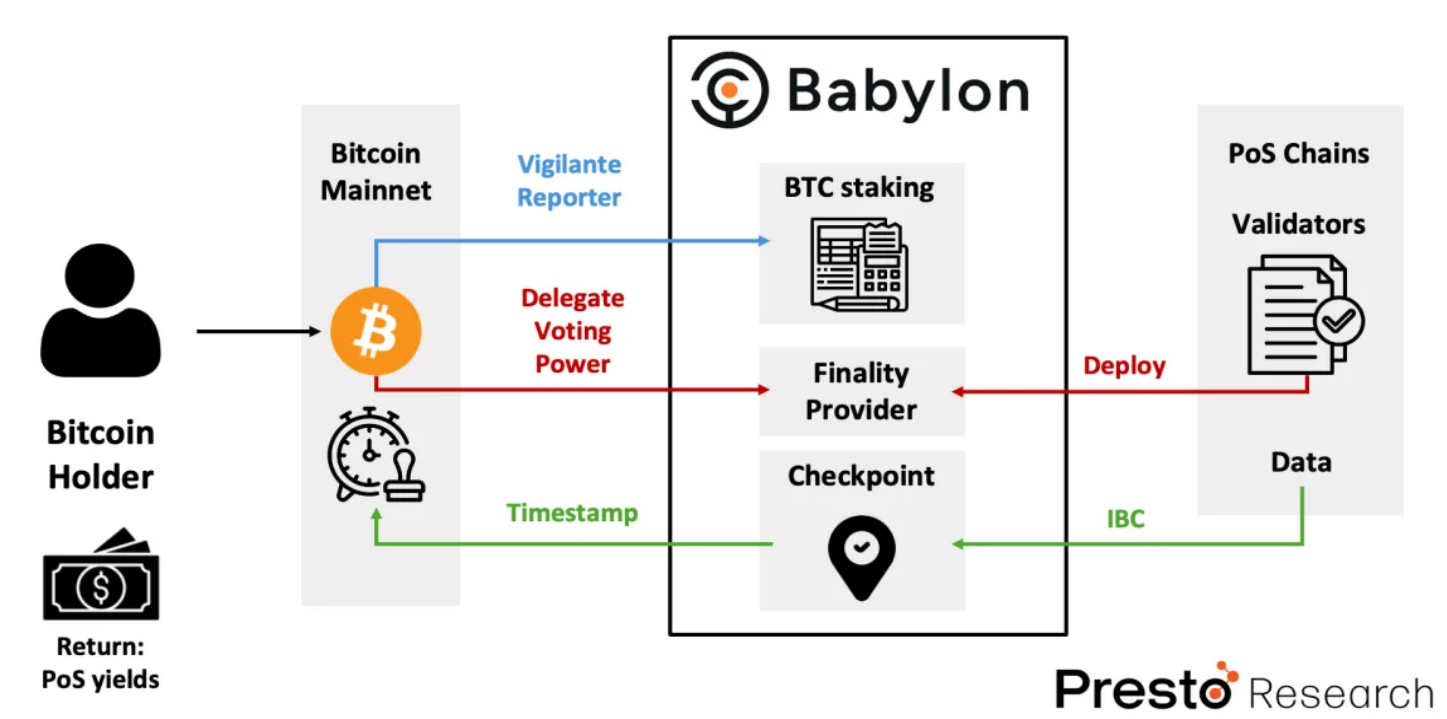
Next, let's explore how Babylon's Bitcoin staking protocol operates as a two-way market, based on the previously discussed technical foundation.
For Bitcoin holders, they can participate in yield-generating activities through the Babylon protocol. As explained earlier, each Bitcoin holder can lock their BTC in a self-custodied staking contract, which is then communicated to Babylon nodes by an independent program called the Vigilante reporter. Within the Babylon node, the BTC staking module acts as the ledger manager, responsible for verifying and activating BTC staking requests. Once this initial staking process is completed, the next step is for Bitcoin holders to select a finality provider and delegate their voting rights to that provider. Delegating voting rights means granting the right to participate in the finality component to an entity known as the finality provider. In return, Bitcoin holders receive additional rewards from staking in their chosen PoS chain and pay the finality provider a certain percentage of commission (in the first phase of the Babylon mainnet, this percentage ranges from 3% to 10% of the rewards).
On the other hand, each PoS chain can pay staking rewards to Bitcoin holders through participation in the Babylon protocol to obtain enhanced security guarantees. In addition to generating and validating blocks according to their own PoS protocol, they deploy a finality provider module and sign finality signatures on the finality component. By doing so, validators of the PoS chain publish their blockchain data to the BabylonChain via cross-chain communication protocol (IBC), and this data is recorded on the Bitcoin chain by the checkpoint module of Babylon nodes. Under Babylon's remote staking protocol, the entire process is economically secured: if a PoS chain experiences a security breach, at least one-third of the staked Bitcoin funds will be slashed (the audit system in the PoS chain cannot prevent this mechanism).
4. Babylon Ecosystem
Babylon's modular design allows it to adapt to various consensus protocols used by consumer chains. By integrating Babylon's Bitcoin staking protocol, these consumer chains can leverage the security and liquidity of Bitcoin to overcome the limitations of staking only with native tokens. Potential applications of this approach include DeFi, Layer 2 Rollups, and oracles.
1) DeFi
An important part of the Babylon ecosystem is the support for Liquid Staking Tokens (LSTs), which provides Bitcoin holders with the opportunity to maintain liquidity while staking BTC through the Babylon protocol. Projects like Bedrock, Nomic, and Solv have developed their own LSTs—uniBTC, stBTC, and SolvBTC—on the Babylon protocol. Users can stake BTC in Babylon through these services and earn additional rewards through staking.
The Babylon ecosystem also includes projects aimed at enhancing Bitcoin's role in the DeFi space. For example, the Lorenzo protocol integrates with Babylon to build a scalable Bitcoin application layer, facilitating the use of Bitcoin assets in data storage and network security. Another ecosystem participant, Persistence One, focuses on maximizing returns and security through liquid staking and re-staking, using Babylon to enhance their staking capital and security.
2) Layer 2 Rollups
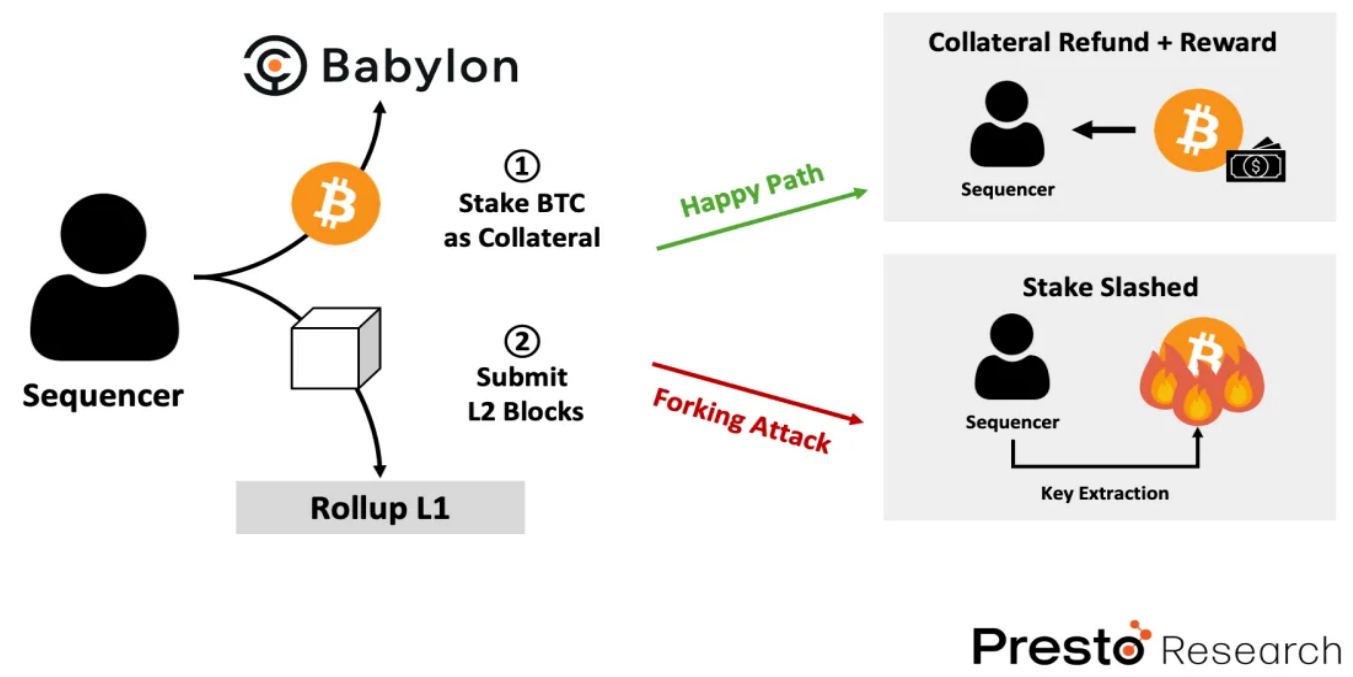
Another important aspect of the Babylon ecosystem is the support for non-forking Rollups. Currently, Rollups face the major bottleneck of the sequencer problem, where users have to rely on centralized sequencers to submit L2 blocks to L1. However, this reliance introduces significant security risks, especially the threat of fork attacks, where sequencers may submit different versions of blocks to users and L1, allowing for double spending and other malicious activities. Existing mechanisms such as ZK proofs and insufficient dispute periods are not enough to fully prevent these attacks, and users are forced to trust centralized sequencers for quick finality, reintroducing the risk of theft and censorship.
Here, Babylon proposes a non-forking Rollups solution by using Bitcoin staking as collateral to address the sequencer problem (Figure 7). The sequencer stakes Bitcoin and adds a finality signature to each L2 block. If the sequencer publishes conflicting blocks, the secret key can be extracted from the final signature, leading to a slashing of the sequencer's stake. This mechanism is executed by the Rollup smart contract on L1, which verifies the finality signature before accepting L2 blocks, economically deterring malicious behavior.
Additionally, the protocol decentralizes the role of sequencers by introducing a finality provider committee, which verifies each L2 block. If a finality provider signs on conflicting blocks, they will also be slashed, ensuring that at least one-third of honest finality providers can prevent forks and invalid blocks. This decentralized verification process provides strong security guarantees without significantly increasing latency, making it well-suited for high-risk applications requiring quick finality. Projects like AltLayer, Chakra, Merlin, and B² Network are currently integrating Babylon to secure their Rollups.
Figure 8: Non-Forking Rollups in Babylon
Furthermore, Babylon is expanding its ecosystem through more collaborations to enhance security, accessibility, and research capabilities. Projects like Glacier Network, Automata Network, Yala, and Hana Network have integrated Babylon to strengthen their security protocols, enhance validator networks, and seamlessly implement Bitcoin staking on various platforms.
In case you missed it: Phased release of Babylon Bitcoin staking mainnet
The launch of the Babylon mainnet is divided into three main phases, with the first phase update starting on August 22, 2024. In this initial phase, although the process of establishing Bitcoin staking is set up, it is not yet activated, meaning staking rewards are not available. This phase is primarily a preparatory stage, allowing Bitcoin holders or stakers to lock their Bitcoin and delegate their PoS voting rights to the selected finality provider by submitting staking transactions to the Bitcoin network.
Stakers can lock Bitcoin for up to 64,000 Bitcoin blocks (approximately 15 months) and have the flexibility to unlock their staking as needed, but they must go through a mandatory unlocking period of 1,008 Bitcoin blocks (approximately 7 days) before withdrawing. The initial total staking limit for the first phase is set at 1,000 Bitcoin, with a minimum staking amount of 0.005 BTC and a maximum staking amount of 0.05 BTC per staking transaction. Staking is accepted on a first-come, first-served (FCFS) basis, and once the limit is reached, there is no queuing system to process overflow staking.
It is important to note that there are no slashing mechanisms and staking rewards in the first phase. Stakers do not lose their staked Bitcoin due to network penalties, as there is no need to sign a consent form for PoS slashing. Instead of traditional staking rewards, a point system is implemented. Stakers earn points based on their active staking, with 3,125 points allocated per Bitcoin block, distributed proportionally to active staking during the initial staking limit period, benefiting both stakers and their finality providers. This point system serves as a measure of staking activity and may be adjusted as the first phase progresses, but these points have no monetary value and cannot be traded, sold, or exchanged for any form of currency or assets.
After the initial phase launch, two more updates are planned. The second phase marks the activation of Babylon PoS chains, where finality providers from the first phase start participating in the chain's consensus, determining block finality, and enabling cross-chain time synchronization using the Bitcoin timestamp protocol. In the third phase, the Babylon Bitcoin staking protocol will allow Bitcoin holders to stake the same Bitcoin in multiple PoS systems simultaneously, enabling multiple staking rewards.
5. Conclusion
BabylonChain, as a groundbreaking solution, addresses the challenges faced by Bitcoin holders and Proof of Stake (PoS) blockchains. By leveraging the security and liquidity of Bitcoin, BabylonChain has created a unique market, allowing idle Bitcoin capital to enhance the security of PoS networks. This collaboration not only unlocks earning opportunities for Bitcoin holders but also provides a strong security layer for PoS chains, especially in addressing issues such as bootstrapping, low activity resilience, and long staking unlock periods.
BabylonChain's approach to remote Bitcoin staking is unique in its innovative use of the timestamp protocol, finality gadget, and staking contract. These elements collectively ensure that the protocol maintains high security standards, providing slashing security, staker security, and staker liquidity. The timestamp protocol significantly reduces the risks associated with late corruption attacks and shortens the staking unlock period by anchoring PoS chain checkpoints on the Bitcoin blockchain. The finality gadget further strengthens the consensus process by enforcing only one block at each height to be finalized, preventing malicious behavior by validators. Meanwhile, the staking contract ensures the security and liquidity of staked assets without relying on complex smart contracts, leveraging Bitcoin's inherent capabilities.
In addition to securing PoS chains, BabylonChain's modular design paves the way for various applications in the blockchain ecosystem, including decentralized finance (DeFi), Layer 2 Rollups, and oracles. By integrating Bitcoin staking, these applications can benefit from enhanced security and liquidity, driving innovation and addressing some of the most pressing vulnerabilities in existing blockchain architectures.
In conclusion, BabylonChain represents the advancement of blockchain technology, bridging the gap between Bitcoin's unparalleled security and the dynamic earning opportunities of PoS networks. Its implementation not only enhances the utility of Bitcoin but also provides a security layer for the broader blockchain ecosystem, positioning BabylonChain as a crucial infrastructure for the future of decentralized finance and other fields.
Original article link: https://www.hellobtc.com/kp/du/09/5400.html
Source: https://www.prestolabs.io/research/babylonchain-two-birds-with-one-stone
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




