Author: SlowMist AML Team
With the rapid development of blockchain, security incidents such as coin theft, phishing, and fraud targeting users are increasing, and the attack methods are diverse. SlowMist receives a large number of requests for help from victims every day, hoping that we can provide assistance in tracking and rescuing funds, including many high-value victims who have lost millions of dollars. Based on this, this series statistically analyzes the stolen forms received each quarter and aims to dissect common or rare malicious methods with desensitized real cases, helping users learn how to better protect their assets.
According to statistics, MistTrack Team received a total of 467 stolen forms in the Q2 of 2024, including 146 overseas forms and 321 domestic forms. We provided free evaluation community services for these forms (Ps. This article only focuses on cases submitted through forms, not those contacted through email or other channels).
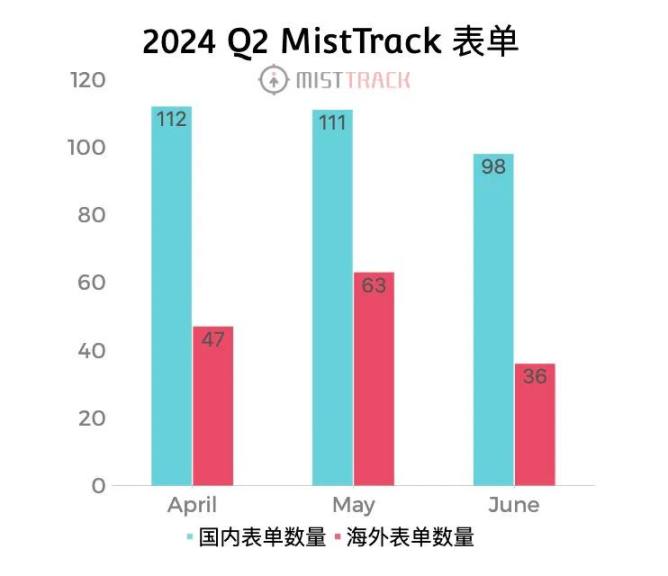
Among them, MistTrack Team assisted 18 stolen clients in freezing approximately 20.6641 million US dollars on 13 platforms.
Top 3 Reasons for Theft
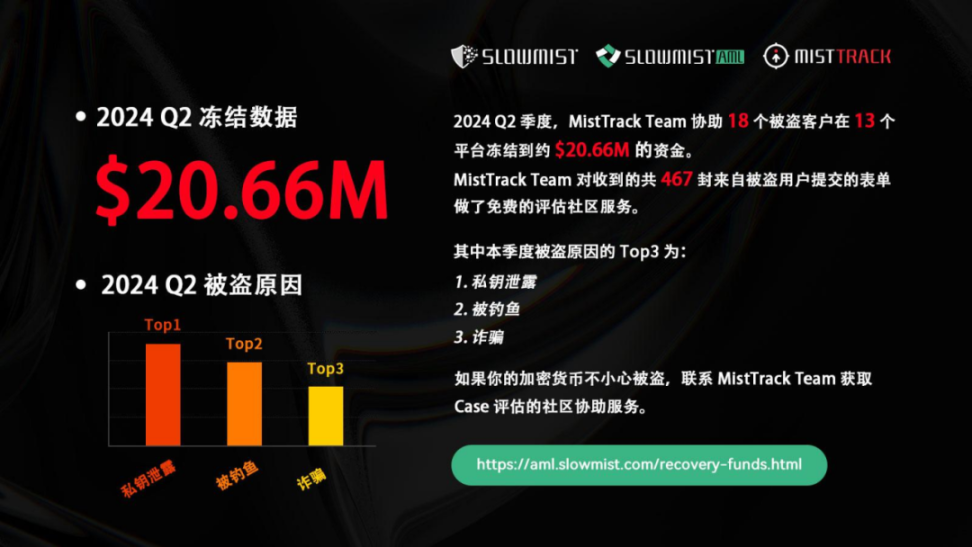
The most common malicious methods in the Q2 of 2024 are as follows:
Leakage of Private Key
According to the statistics of Q2 forms, many users store their private keys / mnemonic phrases in cloud storage such as Google Docs, Tencent Docs, Baidu Cloud, and Shimo Docs. Some users even send their private keys / mnemonic phrases to trusted friends via WeChat, and some even use WeChat's image recognition function to copy the mnemonic phrases to WPS spreadsheets, encrypt the spreadsheet, and enable cloud services, while also storing it on the local hard drive of the computer. These seemingly secure behaviors actually greatly increase the risk of information theft. Hackers often use "credential stuffing" to collect publicly leaked account password databases on the internet and attempt to log in to these cloud storage service websites. Although this is a probability-based behavior, once logged in successfully, hackers can easily find and steal information related to cryptocurrencies. These situations can be seen as passive information leakage. There are also cases of active leakage, such as victims being induced by scammers impersonating customer service to fill in mnemonic phrases, or being deceived by phishing links on platforms like Discord and then entering private key information. In this regard, MistTrack Team strongly reminds everyone not to disclose their private keys / mnemonic phrases to anyone under any circumstances.
In addition, fake wallets are also a major area of private key leakage. Although this has been discussed extensively, there are still a large number of users who inadvertently click on advertising links when using search engines, leading to the download of counterfeit wallet applications. Due to network reasons, many users choose to obtain related applications from third-party download sites. Although these sites claim that their applications are all mirrored downloads from Google Play, their actual security is questionable. Previously, the SlowMist security team analyzed wallet applications on the third-party app market apkcombo and found that the imToken 24.9.11 version provided by apkcombo is a non-existent version and is the most common fake imToken wallet version on the market.

We also tracked some backend management systems related to fake wallet teams, which include complex digital currency control functions such as user management, currency management, and recharge management. The advanced features and professionalism of these phishing behaviors have exceeded the imagination of many people.

For example, there was a relatively rare case in Q2: a user accidentally downloaded a counterfeit version of the Twitter application while searching for "Twitter" on a search engine. When the user opened this application, a prompt popped up, claiming that a VPN was required due to regional restrictions, and guided the user to download the fake VPN provided by the application, resulting in the theft of the user's private key / mnemonic phrase. Such cases once again remind us that careful scrutiny and verification should be carried out for any online applications and services to ensure their legitimacy and security.
Phishing
According to the analysis, the main reason for many stolen help requests in Q2 was phishing: users clicked on phishing links in comments posted under tweets of well-known projects. Previously, the SlowMist security team conducted targeted analysis and statistics: about 80% of well-known projects' first comments in the tweet's comment section were occupied by fraudulent phishing accounts. We also found a large number of groups on Telegram selling Twitter accounts, with varying numbers of followers, posting numbers, and registration times, allowing potential buyers to choose according to their needs. Historical records show that most of the accounts sold are related to the cryptocurrency industry or internet celebrities.
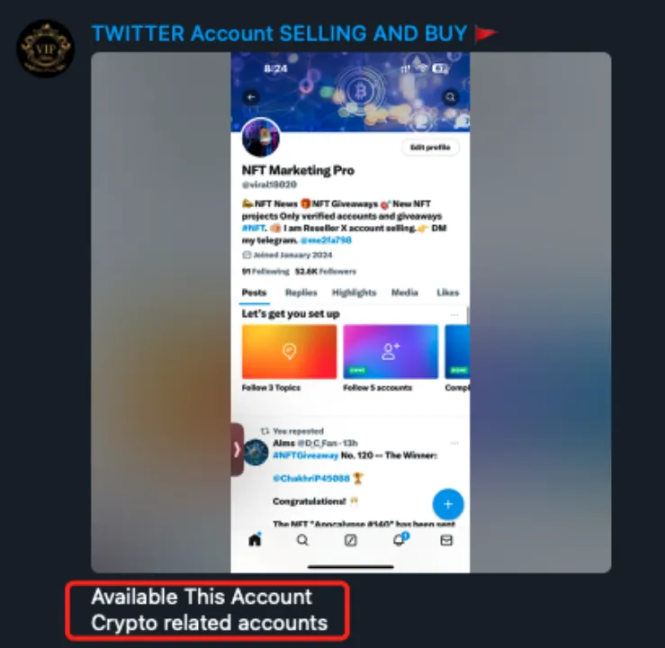
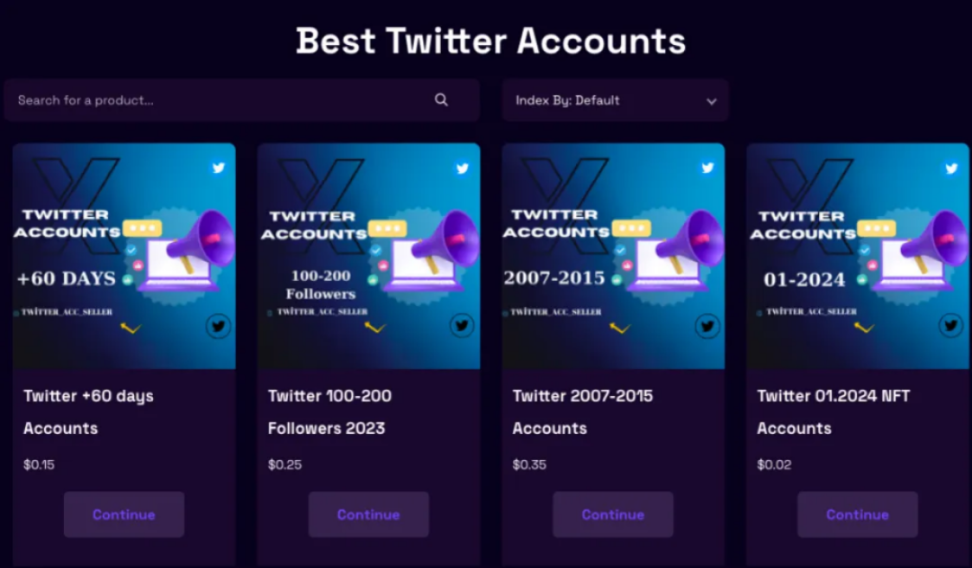
In addition, there are also some websites specifically selling Twitter accounts, selling accounts from various years, and even supporting the purchase of highly similar accounts. For example, the counterfeit account "Optimlzm" and the real account "Optimism" have a very high degree of similarity in appearance. After purchasing these highly similar accounts, phishing groups will use promotional tools to increase the account's interaction and number of followers, thereby increasing the account's credibility. These promotional tools not only accept cryptocurrency payments but also sell various social platform services including likes, retweets, and follower increases. Using these tools, phishing groups can obtain a Twitter account with a large number of followers and posts, and imitate the information release dynamics of the project party. Due to the high degree of similarity between the disguised accounts and the accounts of the project party, many users find it difficult to distinguish between the real and the fake, further increasing the success rate of phishing groups. Subsequently, phishing groups carry out phishing actions, such as using automated bots to follow the dynamics of well-known projects. When the project party tweets, the bot will automatically reply to seize the first comment, attracting more views. Given the high degree of similarity between the disguised accounts and the accounts of the project party, if users neglect to click on phishing links on fake accounts and then authorize and sign, it may lead to asset loss.
Overall, looking at phishing attacks in the blockchain industry, the main risks for individual users are in the "domain name" and "signature" core points. In order to achieve comprehensive security protection, we have always advocated for a dual defense strategy, which includes personnel security awareness defense + technical defense. Technical defense refers to using various hardware and software tools, such as the phishing risk-blocking plugin Scam Sniffer, to ensure the security of assets and information. When users open suspicious phishing pages, the tool will promptly display a risk warning, thereby blocking it at the first step of the risk formation. In terms of personnel security awareness defense, we strongly recommend that everyone thoroughly read and gradually master the "Blockchain Dark Forest Self-Rescue Handbook" (https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook/blob/main/README_CN.md). Only through the mutual coordination of these two defense strategies can we effectively combat the constantly changing and evolving phishing attack methods and safeguard asset security.
Scams
There are many scam methods, and the most common scam method in Q2 is the "Pixiu Coin". In legend, the Pixiu is considered a magical creature that can devour all things without excreting them. It is said that once gold and jewelry and other treasures are swallowed, they cannot be taken out of its body. Therefore, the Pixiu Coin is used to metaphorically describe digital currencies that cannot be sold once purchased.
One victim described their experience: "I asked a question in a Telegram group, and someone enthusiastically answered many of my questions and taught me a lot. After chatting privately for two days, I thought he was a nice person. So he suggested taking me to the primary market to buy a new token and provided me with a contract address for the token on PancakeSwap. After I purchased it, the token kept rising rapidly. He told me that this was a once-in-a-lifetime opportunity and advised me to increase my investment immediately. I felt that things were not that simple and did not accept his advice. He kept urging me, and when I realized I might be deceived, I asked other people in the group to help me check. The result was that it was indeed a Pixiu Coin, and I found out that I could only buy it and not sell it. When the scammer realized that I was not adding more funds, he also blocked me."
The experience of this victim actually reflects the typical pattern of Pixiu Coin scams:
- The scammer deploys a smart contract with a trap and offers bait promising high profits.
- The scammer strongly attracts the target to purchase the token. After the victim purchases it, they often see the token rapidly appreciate in value. As a result, the victim usually decides to wait until the token's increase is large enough before attempting to exchange it, only to find that they cannot sell the purchased token.
- Finally, the scammer withdraws the victim's investment funds.
It is worth mentioning that all the Pixiu Coin mentioned in the Q2 forms occurred on BSC. In the image below, you can see that there are many transactions involving the Pixiu Coin, and the scammer also sends the tokens held to wallets and exchanges, creating the illusion that many people are involved.
Due to the inherent concealment of Pixiu Coin scams, even experienced investors may find it difficult to see the truth. Nowadays, Meme coins are popular, and various types of "meme coins" have a certain impact on the market. Since the price of Pixiu Coin will rise rapidly, people often impulsively follow the trend to buy. Many market participants who are unaware of the truth eagerly chase this "meme coin frenzy", but inadvertently fall into the trap of Pixiu Coin and are unable to sell it after purchasing.
Therefore, MistTrack Team recommends that users take the following measures before trading to avoid financial losses due to participating in Pixiu Coin:
- Use MistTrack to view the risk situation of relevant addresses, or use GoPlus's Token Security Check tool to identify Pixiu Coins and make trading decisions.
- Check whether the code has been audited and verified on Etherscan and BscScan, or read related comments, as some victims will issue warnings on the scam token comments tab.
- Understand the relevant information of the cryptocurrency and consider the background of the project party to increase self-awareness and vigilance. Be wary of cryptocurrencies that offer extremely high returns, as extremely high returns usually indicate greater risks.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




